A Leak Zone Location Approach in Water Distribution Networks Combining Data-Driven and Model-Based Methods
Abstract
:1. Introduction
2. Materials and Methods
2.1. Network Modeling
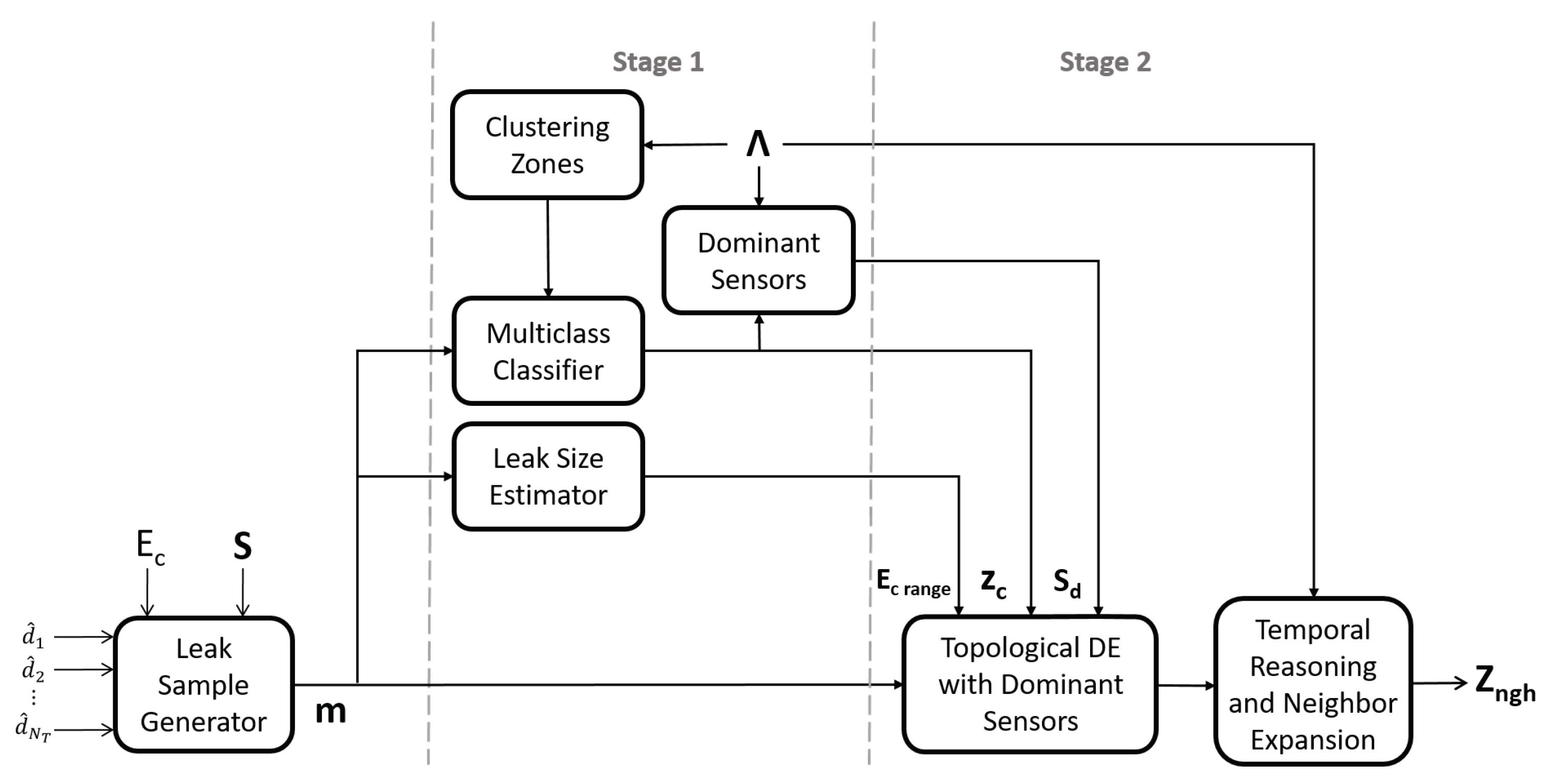
2.2. Leak Location Methodology
- A set of sensors installed in the network to capture the hydraulic information.
- A SCADA system for data acquisition and processing.
- A calibrated network hydraulic model.
- A processing unit (e.g., a personal computer (PC) or industrial PC) to implement and run the methodology.
2.3. Stage 1: Search Space Reduction and Dominant Sensor Selection
2.3.1. Clustering Zones
2.3.2. Support Vector Machine Classifier
2.3.3. Bayes Temporal Reasoning
2.3.4. Leak Size Estimation
2.3.5. Dominant Sensor Selection
2.4. Stage 2: Leak Location as an Inverse Problem
2.4.1. Temporal Reasoning and Neighbor Expansion
2.5. Performance Measures
2.5.1. Leak Location Accuracy
2.5.2. Leak Zone Size
2.5.3. Computational Cost
3. Case Study
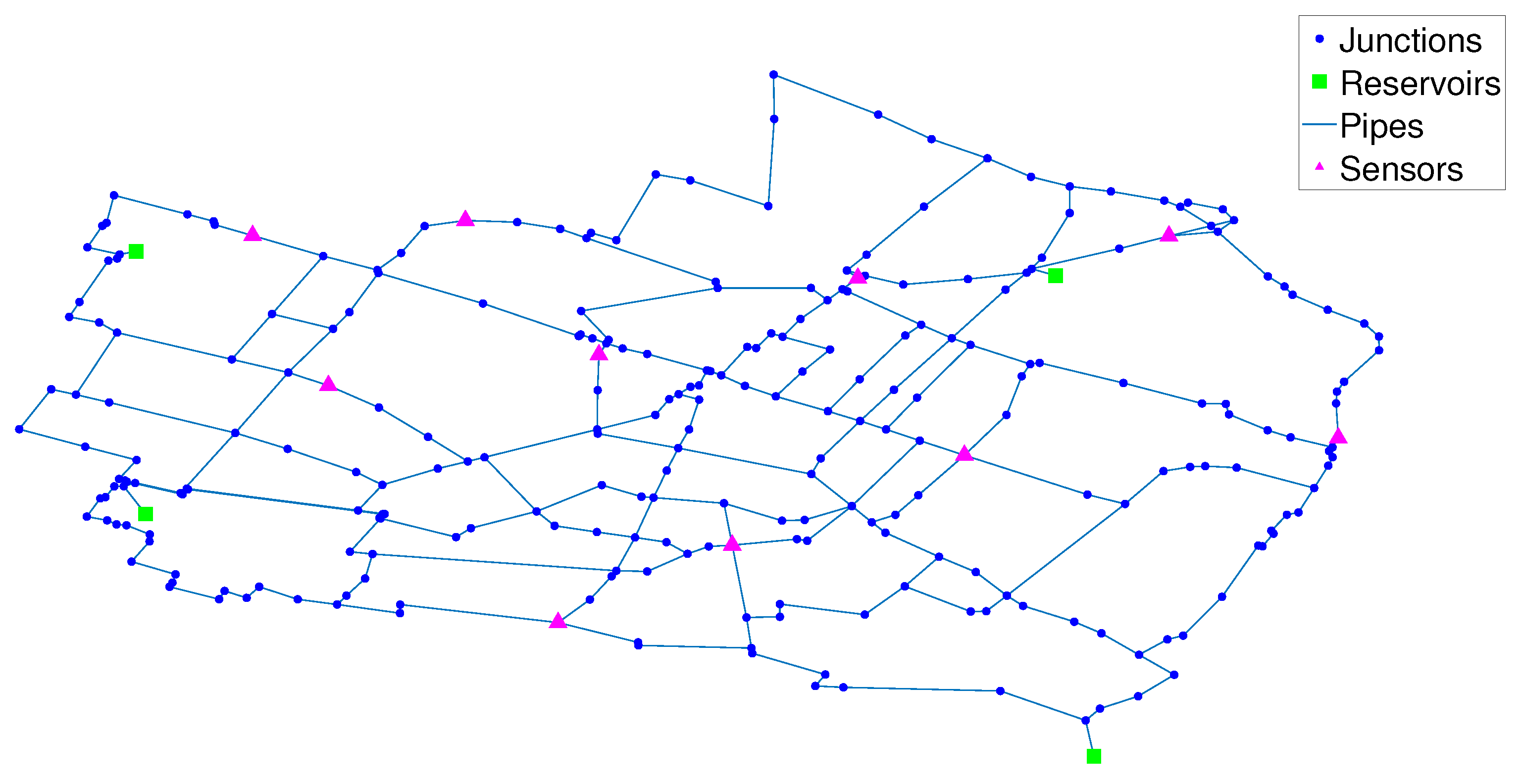
3.1. Modena Network
3.2. Realistic Sample Simulation—Uncertainty Modeling
- Minimum night flow regime is assumed, ranging from 2 a.m. to 6 a.m. At this time at night, variation in the demand patterns from consumers are very small, therefore, fixed nominal demands can be assumed. The characteristic reduction in demand variation at night time simplifies the location task, increasing its performance; however, this also means that the leak location can only be identified at night.
- Sensor sampling time is considered to be 15 min per sample, with 4 samples in one hour. This amounts to a total of 16 samples in a day under minimum night flow regime. An average between hourly samples is then calculated to filter uncertainties in the data, resulting in 4 filtered samples in a day. A leak scenario is defined as a set of 4 filtered samples from a single day, all of which are generated under the same conditions (leak location and size).
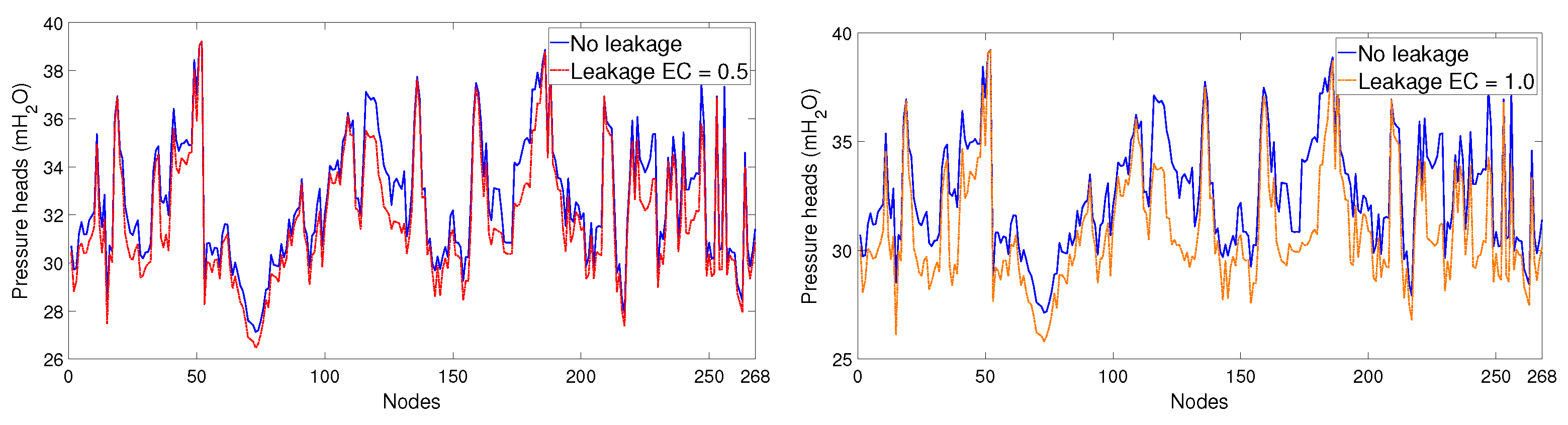
- The leak size for every scenario is sampled randomly from a uniform distribution within the interval . This results in leaks that range from 2.6 to 6.3 lps. A timely location and maintenance of leaks of this size can save from 1.1 to 2.6% of the network’s total nominal demands during minimum night flow regime. The leak size range selected could be described as matching medium sized leaks. Leaks higher than that interval are relatively easy to diagnose and sometimes result in pipe bursts visible at street level, which are most likely to be diagnosed by consumer reports. Leaks smaller than the selected interval are, however, mostly background leaks, which are often undetectable due to the uncertainties in network demands and measurements. Figure 3 shows the effect of different sized leaks on pressure head values for every node of the network, which are compared to nominal (no leak) patterns; no uncertainties are considered.
- In real WDNs, actual node demands differ from modeled nominal demands due to variations in consumer patterns. These demand uncertainties must be taken into account in order to achieve realistic simulations. Therefore, node demands were sampled from the following Gaussian distribution: , where is the nominal demand and is a demand uncertainty coefficient. Several uncertainty coefficients are explored in this work. Demand uncertainty is sampled as a Gaussian distribution centered around the nominal demand because the latter has been estimated as the most probable value. Furthermore, by defining demand uncertainty standard deviation as a factor of the nominal demand, nodes with higher nominal demand values are modeled with higher uncertainty.
- In order to guarantee a realistic simulation of the pressure sensors, measurement noise is sampled from the following uniform distribution mHO, and stacked additively with the pressure values simulated.
3.3. Experimental Design
3.3.1. Dataset Generation
3.3.2. Hybrid Methodology Implementation
- 1
- The WDN is partitioned into subzones to form classes.
- 2
- A classifier is trained using the training dataset presented in Section 3.3.1 and the labels generated in step 1.
- 2.1.
- For the SVM classifier in particular, hyperparameters are selected using grid search and 10-fold cross validation in the training set, with the following grid: , .
- 3
- The number of classes (), and zones, in the network is selected to guarantee a 95% classification accuracy for the multiclass classifier.
- 4
- Regarding the TDE algorithm, the mutation (F) and crossover () factors are also selected through grid search with the following grid: , .
- 5
- The number of dominant sensors is selected from the following values: , , aiming to maximize leak location accuracy; if location accuracy values are similar for different dominant sensor values, the number of dominant sensors that achieves the lowest computational cost will be selected.
- 6
- The stop criteria , , and , as well the population size , for the TDE algorithm are selected aiming to minimize the computational cost without resulting in loss of accuracy.
- 7
- Temporal reasoning time horizon is selected according to the sampling frequency and the number of samples in a minimum night flow regime scenario.
- 8
- Neighbor expansion distance is selected depending on the desired zone size.
- Classifier hyperparameters: .
- Classifier number of zones: = 5.
- Mutation factor: , and crossover factor: .
- Population size: .
- Maximum generations: .
- Stagnation iterations: .
- Cost tolerance: .
- Pipe distance for neighbors: = 250 m. An average zone size of approximately 6 nodes for the case was the desired zone size.
- Temporal reasoning time horizon: . All 4 samples in each scenario were selected for temporal reasoning for both the classifier and the TDE steps of the methodology.
- Dominant sensors: .
3.3.3. Comparing Leak Location Strategies
4. Results and Discussion
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Dominant Sensor Selection
| Algorithm A1: Selecting Dominant Sensor Location |
|
Appendix B. Topological Differential Evolution Algorithm
- InitializationIn the initialization step, an initial population with candidate solutions is produced by randomly sampling from the search space. The mutation and crossover coefficients are also defined at this stage [39]. Initialization is carried out only once for generation 0, while the other three operators are applied to every generation.
- MutationThe mutation operator generates a mutated candidate solution for every member of population by combining the characteristics of multiple population members. This operator promotes exploration of the search space by generating new characteristics in the mutated population . On one hand, the mutated leak size coefficient is generated through classic DE random mutation [39]:where , , and are the leak size coefficients from randomly selected members in population g. These randomly selected population members are different from each other and sampled from a uniform distribution.On the other hand, the mutated potential leak node, , is generated following the topology of the WDN [15]:where randi represents the random selection operator which yields a random (sampled from a uniform distribution) network node from the neighbor nodes vector: . A neighbor node is defined as a node that is connected to by a single pipe; and comprehends all the nodes neighboring within the topological search space.
- CrossoverThe crossover operator is applied to generation g once the mutation operator has been applied to every member in population . This operator yields a crossed member by combining characteristics from the corresponding mutated and pre-mutated population members. This operator is non-linear in nature, and promotes exploitation by combining characteristics from the previous and current generation into the crossed population .Binomial crossover is effected through a crossover probability index . This crossover probability index is sampled from a uniform distribution for every population member. The crossed candidate is then generated by comparing the probability index to the crossover coefficient :
- SelectionThe selection operator is applied in order to produce the next generation using a greedy criterion [39]. Every crossed member is compared to its corresponding candidate in population and the one with the smaller cost function is selected:
- Maximum number of generations: .
- Stagnation: the best candidate (the candidate with the smallest value of the cost function ) in the population has remained unchanged for generations.
- Tolerance: the smallest cost function value in the population is smaller than a threshold .
References
- Verde, C.; Torres, L. Modeling and Monitoring of Pipelines and Networks; Springer: Berlin, Germany, 2017; Volume 7. [Google Scholar] [CrossRef]
- Duan, H.F.; Pan, B.; Wang, M.; Chen, L.; Zheng, F.; Zhang, Y. State-of-the-art review on the transient flow modeling and utilization for urban water supply system (UWSS) management. J. Water Supply Res. Technol.-AQUA 2020, 69, 858–893. [Google Scholar] [CrossRef]
- Levinas, D.; Perelman, G.; Ostfeld, A. Water Leak Localization Using High-Resolution Pressure Sensors. Water 2021, 13, 591. [Google Scholar] [CrossRef]
- Cody, R.A.; Tolson, B.A.; Orchard, J. Detecting Leaks in Water Distribution Pipes Using a Deep Autoencoder and Hydroacoustic Spectrograms. J. Comput. Civ. Eng. 2020, 34, 04020001. [Google Scholar] [CrossRef]
- Stephens, M.; Gong, J.; Zhang, C.; Marchi, A.; Dix, L.; Lambert, M.F. Leak-Before-Break Main Failure Prevention for Water Distribution Pipes Using Acoustic Smart Water Technologies: Case Study in Adelaide. J. Water Resour. Plan. Manag. 2020, 146, 05020020. [Google Scholar] [CrossRef]
- Alawadhi, A.; Boso, F.; Tartakovsky, D.M. Method of Distributions for Water Hammer Equations With Uncertain Parameters. Water Resour. Res. 2018, 54, 9398–9411. [Google Scholar] [CrossRef]
- Choura, O.; Capponi, C.; Meniconi, S.; Elaoud, S.; Brunone, B. A Nelder-Mead algorithm-based inverse transient analysis for leak detection and sizing in a single pipe. Water Supply 2021, 21, 1580–1593. [Google Scholar] [CrossRef]
- Ali, H.; Choi, J.h. A Review of Underground Pipeline Leakage and Sinkhole Monitoring Methods Based on Wireless Sensor Networking. Sustainability 2019, 11, 4007. [Google Scholar] [CrossRef] [Green Version]
- Puust, R.; Kapelan, Z.; Savic, D.; Koppel, T. A review of methods for leakage management in pipe networks. Urban Water J. 2010, 7, 25–45. [Google Scholar] [CrossRef]
- Jung, D.; Kang, D.; Liu, J.; Lansey, K. Improving the rapidity of responses to pipe burst in water distribution systems: A comparison of statistical process control methods. J. Hydroinform. 2014, 17, 307–328. [Google Scholar] [CrossRef]
- Quiñones Grueiro, M.; Verde, C.; Llanes-Santiago, O. Novel Leak Location Approach in Water Distribution Networks with Zone Clustering and Classification. In Pattern Recognition; Carrasco-Ochoa, J.A., Martínez-Trinidad, J.F., Olvera-López, J.A., Salas, J., Eds.; Springer International Publishing: Cham, Switzerland, 2019; pp. 37–46. [Google Scholar]
- Zhou, X.; Tang, Z.; Xu, W.; Meng, F.; Chu, X.; Xin, K.; Fu, G. Deep learning identifies accurate burst locations in water distribution networks. Water Res. 2019, 166, 115058. [Google Scholar] [CrossRef] [PubMed]
- Chen, J.; Xin, F.; Xiao, S. An iterative method for leakage zone identification in water distribution networks based on machine learning. Struct. Health Monit. 2020, 20, 1938–1956. [Google Scholar] [CrossRef]
- Romero, L.; Blesa, J.; Puig, V.; Cembrano, G.; Trapiello, C. First Results in Leak Localization in Water Distribution Networks using Graph-Based Clustering and Deep Learning. IFAC-PapersOnLine 2020, 53, 16691–16696. [Google Scholar] [CrossRef]
- Quiñones Grueiro, M.; Ares-Milián, M.J.; Sánchez-Rivero, M.; Silva-Nieto, A.J.; Llanes-Santiago, O. Robust leak localization in water distribution networks using computational intelligence. Neurocomputing 2021, 438, 195–208. [Google Scholar] [CrossRef]
- Sanz, G.; Pérez, R. Sensitivity Analysis for Sampling Design and Demand Calibration in Water Distribution Networks Using the Singular Value Decomposition. J. Water Resour. Plan. Manag. 2015, 141, 04015020. [Google Scholar] [CrossRef]
- Moser, G.; Paal, S.G.; Smith, I.F.C. Leak Detection of Water Supply Networks Using Error-Domain Model Falsification. J. Comput. Civ. Eng. 2018, 32, 04017077. [Google Scholar] [CrossRef] [Green Version]
- Li, X.; Chu, S.; Zhang, T.; Yu, T.; Shao, Y. Leakage localization using pressure sensors and spatial clustering in water distribution systems. Water Supply 2021, ws2021219. [Google Scholar] [CrossRef]
- Steffelbauer, D.; Günther, M.; Fuchs-Hanusch, D. Leakage Localization with Differential Evolution: A Closer Look on Distance Metrics. Procedia Eng. 2017, 185, 444–451. [Google Scholar] [CrossRef]
- Zhang, Q.; Wu, Z.Y.; Zhao, M.; Qi, J. Leakage Zone Identification in Large-Scale Water Distribution Systems Using Multiclass Support Vector Machines. J. Water Resour. Plan. Manag. 2016, 142, 04016042. [Google Scholar] [CrossRef]
- Sun, C.; Parellada, B.; Puig, V.; Cembrano, G. Leak Localization in Water Distribution Networks Using Pressure and Data-Driven Classifier Approach. Water 2019, 12, 54. [Google Scholar] [CrossRef] [Green Version]
- Shekofteh, M.; Jalili-Ghazizadeh, M.; Yazdi, J. A methodology for leak detection in water distribution networks using graph theory and artificial neural network. Urban Water J. 2020, 17, 525–533. [Google Scholar] [CrossRef]
- Kleijnen, J.P.C. Regression and Kriging metamodels with their experimental designs in simulation: A review. Eur. J. Oper. Res. 2016, 257, 1–16. [Google Scholar]
- Fazai, R.; Mansouria, M.; Abodayehb, K.; Puig, V.; Noori-Raoufe, M.; Nounoua, H.; Nounou, M. Multiscale Gaussian process regression-based generalized likelihood ratio test for fault detection in water distribution network. Eng. Appl. Artif. Intell. 2019, 85, 474–491. [Google Scholar] [CrossRef]
- Ormsbee, L.E.; Lingireddy, S. Calibration of Hydraulic Network Models. J. Am. Water Work. Assoc. 1997, 89, 42–50. [Google Scholar] [CrossRef]
- Houghtalen, R.; Akan, A.; Hwang, N. Fundamentals of Hydraulic Engineering Systems, 4th ed.; Prentice Hall: Hoboken, NJ, USA, 2010. [Google Scholar]
- Rossman, L.A. Epanet 2 Users Manual; National Risk Management Research Laboratory; U.S. Environmental Protection Agency: Cincinati, OH, USA, 2000.
- Ye, G.; Fenner, R.A. Kalman Filtering of Hydraulic Measurements for Burst Detection in Water Distribution Systems. J. Pipeline Syst. Eng. Pract. 2011, 2, 14–22. [Google Scholar] [CrossRef]
- Kaufman, L.; Rousseeuw, P.J. Finding Groups in Data. An Introduction to Cluster Analysis; John Wiley & Sons: Hoboken, NJ, USA, 2005. [Google Scholar]
- Soldevila, A.; Fernández-canti, R.; Blesa, J.; Tornil-sin, S.; Puig, V. Leak localization in water distribution networks using bayesian classifiers. J. Process. Control. 2017, 55, 1–9. [Google Scholar] [CrossRef] [Green Version]
- Jung, Y.; Park, H.; Du, D.Z.; Drake, B.L. A Decision Criterion for the Optimal Number of Clusters in Hierarchical Clustering. J. Glob. Optim. 2002, 25, 91–111. [Google Scholar] [CrossRef]
- Schölkopf, B.; Smola, A.J. Learning with Kernels; MIT Press: Cambridge, MA, USA, 2002. [Google Scholar]
- Vapnik, V.N. Statistical Learning Theory; John Wiley & Sons: Hoboken, NJ, USA, 1998. [Google Scholar]
- Quiñones Grueiro, M.; Bernal-de Lázaro, J.M.; Verde, C.; Prieto-Moreno, A.; Llanes-Santiago, O. Comparison of Classifiers for Leak Location in Water Distribution Networks. IFAC-PapersOnLine 2018, 51, 407–413. [Google Scholar] [CrossRef]
- Camps-Echevarría, L.; Llanes-Santiago, O.; Fraga-de Campos-Velho, H.; da Silva-Neto, A.J. Fault Diagnosis Inverse Problems: Solution with Metaheuristics; Studies in Computational Intelligence; Springer International Publishing: Berlin, Germany, 2019; Volume 763. [Google Scholar]
- Wang, Q.; Guidolin, M.; Savic, D.; Kapelan, Z. Two-Objective Design of Benchmark Problems of a Water Distribution System via MOEAs: Towards the Best-Known Approximation of the True Pareto Front. J. Water Resour. Plan. Manag. 2015, 141, 04014060. [Google Scholar] [CrossRef] [Green Version]
- Goldberg, D.E. Genetic Algorithms in Search, Optimization, and Machine Learning; Addison-Wealey: Reading, MA, USA, 1989. [Google Scholar]
- Luengo, J.; García, S.; Herrera, F. A study on the use of statistical tests for experimentation with neural networks: Analysis of parametric test conditions and non-parametric tests. Expert Syst. Appl. 2009, 36, 7798–7808. [Google Scholar] [CrossRef]
- Storn, R.; Price, K. Differential Evolution: A Simple and Efficient Heuristic for Global Optimization over Continuous Spaces. J. Glob. Optim. 1997, 11, 341–359. [Google Scholar] [CrossRef]
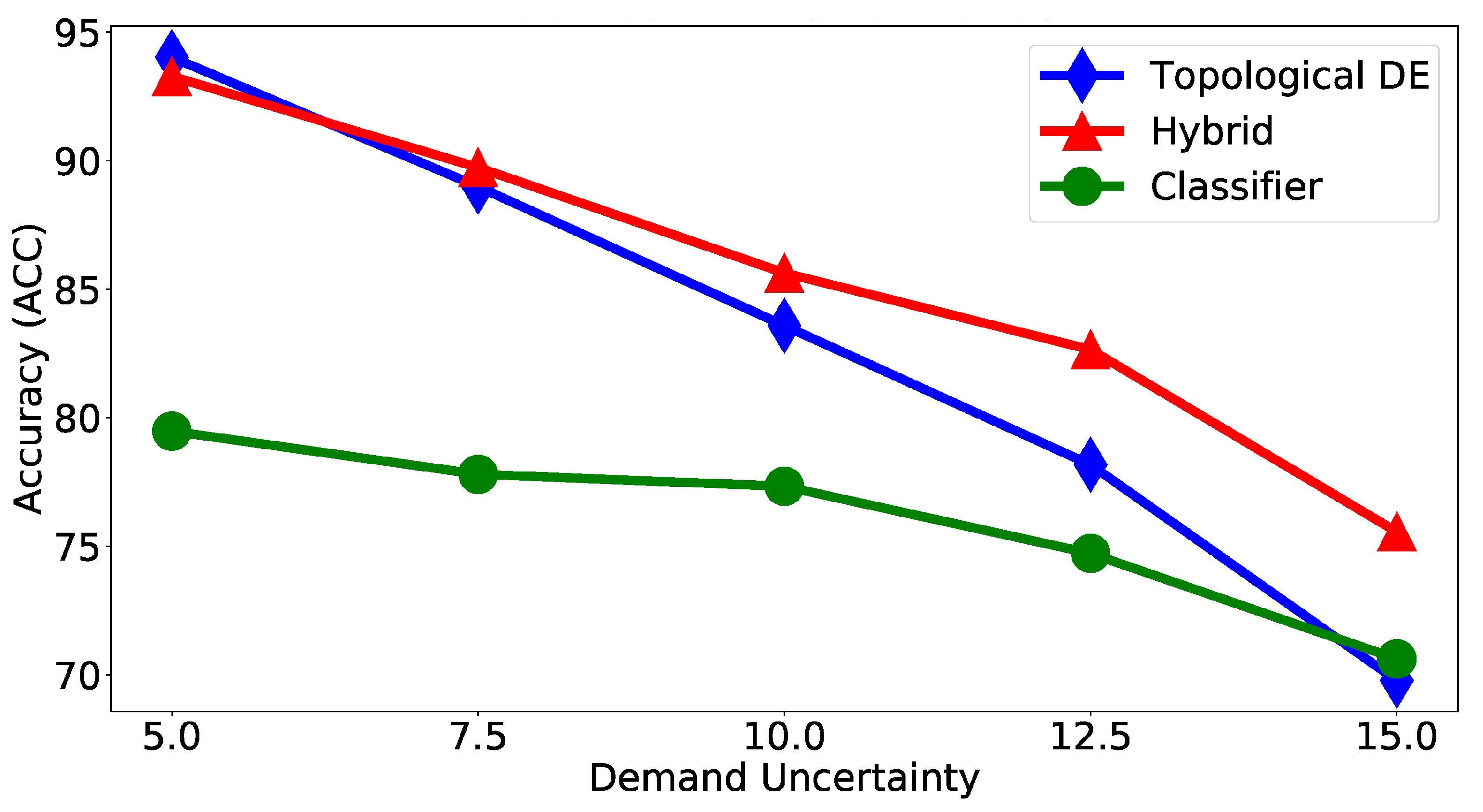
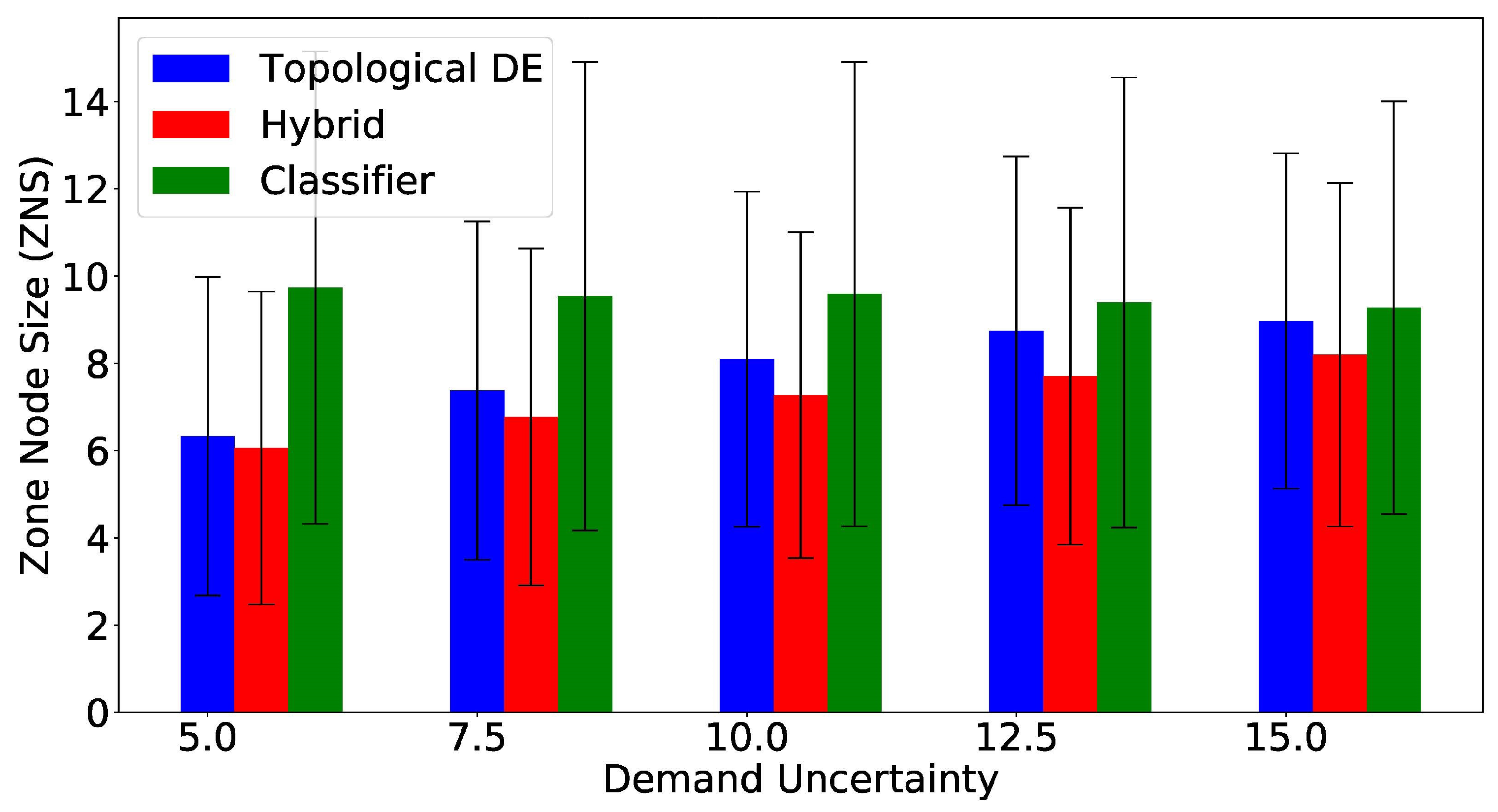

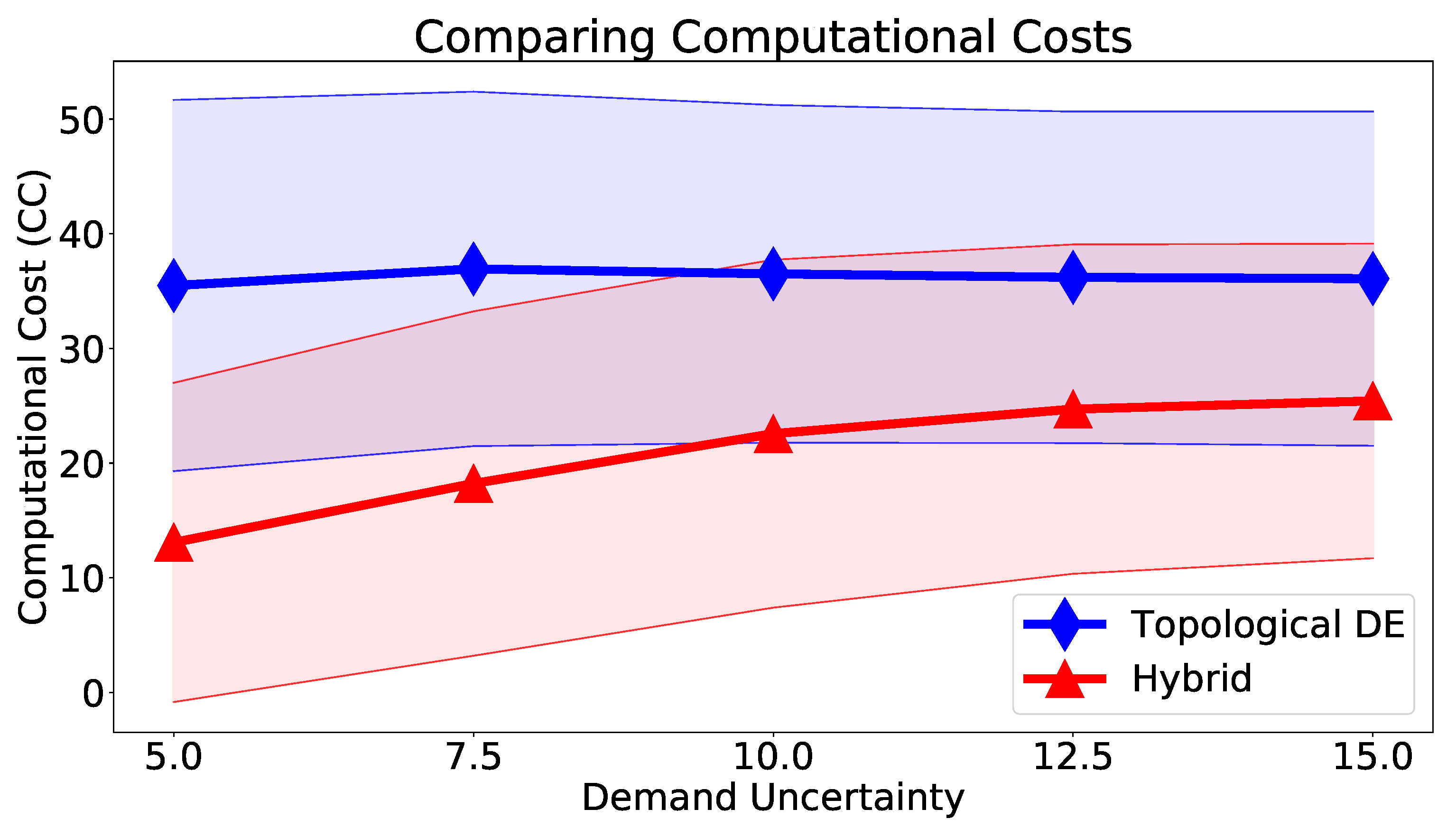

| Method | Demand Uncertainty | ||||
|---|---|---|---|---|---|
| 5% | 7.5% | 10% | 12.5% | 15% | |
| Classifier | 79.48 | 77.80 | 77.33 | 74.72 | 70.62 |
| TDE | 88.99 | 83.58 | 78.17 | 69.78 | |
| Hybrid | 93.28 | ||||
| Method | Demand Uncertainty | ||||
|---|---|---|---|---|---|
| 5% | 7.5% | 10% | 12.5% | 15% | |
| Classifier | 9.73(5.41) | 9.54(5.37) | 9.58(5.32) | 9.39(5.16) | 9.27(4.74) |
| TDE | 6.33(3.65) | 7.38(3.88) | 8.10(3.84) | 8.74(3.99) | 8.97(3.84) |
| Hybrid | |||||
| Method | Demand Uncertainty | ||||
|---|---|---|---|---|---|
| 5% | 7.5% | 10% | 12.5% | 15% | |
| Classifier | 1365.19(693.03) | 1344.93(681.82) | 1347.05(676.68) | 1324.39(670.07) | 1318.58(630.44) |
| TDE | 773.61(456.10) | 864.30(485.54) | 935.00(503.47) | 923.68(463.24) | |
| Hybrid | |||||
| Method | Demand Uncertainty | ||||
|---|---|---|---|---|---|
| 5% | 7.5% | 10% | 12.5% | 15% | |
| TDE | 35.48(16.18) | 36.94(15.45) | 36.50(14.72) | 36.20(14.45) | 36.08(14.57) |
| Hybrid | |||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ares-Milián, M.J.; Quiñones-Grueiro, M.; Verde, C.; Llanes-Santiago, O. A Leak Zone Location Approach in Water Distribution Networks Combining Data-Driven and Model-Based Methods. Water 2021, 13, 2924. https://doi.org/10.3390/w13202924
Ares-Milián MJ, Quiñones-Grueiro M, Verde C, Llanes-Santiago O. A Leak Zone Location Approach in Water Distribution Networks Combining Data-Driven and Model-Based Methods. Water. 2021; 13(20):2924. https://doi.org/10.3390/w13202924
Chicago/Turabian StyleAres-Milián, Marlon Jesús, Marcos Quiñones-Grueiro, Cristina Verde, and Orestes Llanes-Santiago. 2021. "A Leak Zone Location Approach in Water Distribution Networks Combining Data-Driven and Model-Based Methods" Water 13, no. 20: 2924. https://doi.org/10.3390/w13202924






