A Practical Evaluation on RSA and ECC-Based Cipher Suites for IoT High-Security Energy-Efficient Fog and Mist Computing Devices
Abstract
:1. Introduction
2. Related Work
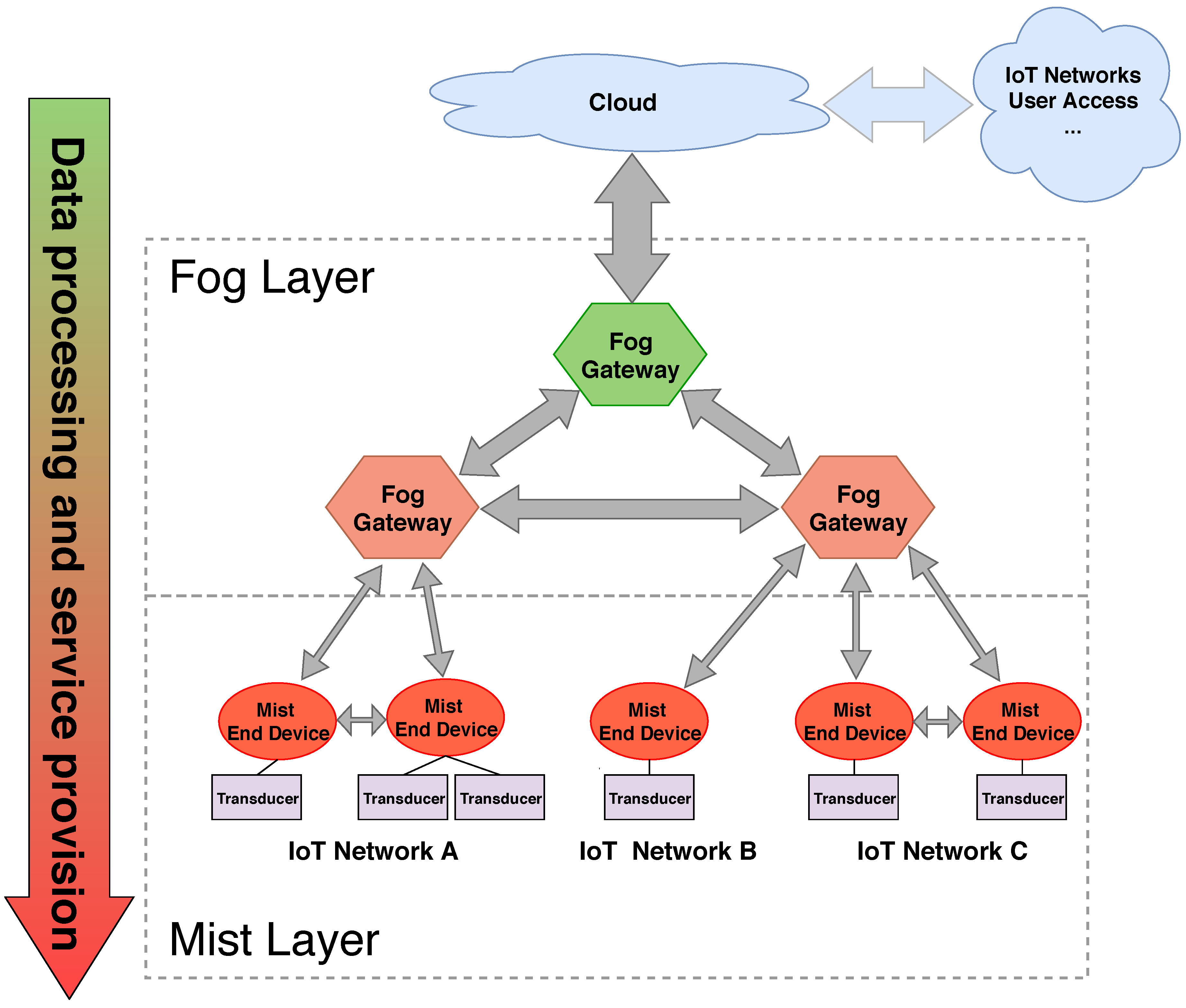
2.1. From Fog to Mist Computing
2.2. Hardware and Software for Mist Computing Devices
2.3. Main Security Threats for Mist Computing Devices
- Confidentiality: it disallows unwanted access to sensitive information.
- Integrity: it protects the transmitted data for unwanted modification or tampering.
- Availability: it is related to the ability of accessing the data when they are needed.
- Physical attacks: they target the physical device or the physical communication channel:
- –
- Node tampering: it consists on altering the mist device itself or the sensors or actuators connected to it to access or modify sensitive information or the device behavior [47].
- –
- Jamming: an attacker blocks mist device wireless communications by transmitting with a jammer device [48].
- –
- Radio Frequency (RF) interference: it consists in introducing devices on the network that generate signals or noise that interfere legitimate communications [49].
- –
- Malicious node injection: it consists on adding a malicious mist node to the mist layer with the intention of introducing tampered data or to access the data being transmitted between the victim mist devices [50].
- –
- Physical damage: an attacker can prevent a mist node from working properly or can neutralize it completely by totally or partially destroying it.
- –
- Malicious code injection: by physically accessing the mist node an attacker could change the code controlling the node and achieve total access to the mist layer [51].
- –
- Sleep deprivation attack: an attacker tries to maximize the energy consumption of a node, which can have a massive effect on the overall energy consumption of the mist layer and thus reduce the life of battery-operated nodes [52].
- Network attacks: they try to exploit some vulnerability on the way the communications are established on the mist layer:
- –
- Traffic analysis attacks: the attacker can somehow intercept the traffic transmitted over the mist network and analyze it to infer any type of useful information about how the network and the mist devices work [53].
- –
- Man-in-the-Middle (MitM) attacks: one of the most common network attacks where a third party captures the communications between two legitimate mist nodes and accesses or tampers the transmitted data [54].
- –
- Denial of Service (DoS) attack: an attacker tries to prevent legitimate access to mist nodes by flooding the mist layer communication network with fake traffic or by tampering with the normal functioning of the network [50].
- –
- Message replaying attack: an attacker can capture a command sent to a mist device and replay it at its convenience [55].
- –
- Sybil attack: a malicious mist node can spoof the identity of other legitimate nodes and act as them [56].
- Software attacks: malware attacks using viruses, worms or malicious scripts targeting mist devices:
- –
- Virus and Worms: attacks that consist on some type of code that can take partial or total control of the mist end-device firmware, and that can be easily replicated to other mist nodes in an autonomous way [57].
- –
- Malicious scripts: mist nodes are usually capable of executing arbitrary pieces of code. By introducing a malicious script, an attacker can gain control of a mist node while the node seems unaltered to the rest of the mist network.
- –
- DoS attacks: a DoS attack can be also performed at a software level, by disallowing the access to a service at an application level. It is usually performed by gaining control of mist nodes or fog gateways that provide such a service.
- Encryption attacks: the last type of attacks that can be performed against mist devices are the ones that try to break the encryption of the communications (in case encryption techniques are used to secure communications) by obtaining the private key of one of the involved parties:
- –
- Side-channel attacks: the attacker uses behavioral information of the device that is applying the cryptographic algorithms. By measuring the elapsed time required for signing or verifying on a public-key cryptographic scheme, or the energy consumption of a mist device during certain phases of the cryptographic protocol, an attacker can infer information and guess the encryption key being used without having a direct knowledge of the plaintext or the ciphertext [58].
- –
- Cryptanalysis attacks: an attacker can obtain the encryption key by obtaining the plaintext or the ciphertext [59].
- –
- MitM attacks: the attacker can intercept the communications between two legitimate parties when the key negotiation phase is performed. At such a point, the attacker would be able either to establish a spoofed shared secret or to obtain the negotiated shared secret and decrypt or tamper any messages transmitted between the two parties [60].
2.4. Impact on Energy Consumption of Securing Mist End-Device and Fog Gateway Communications
2.5. Security Levels
2.6. ECC Curve Implementations for Resource-Constrained Devices
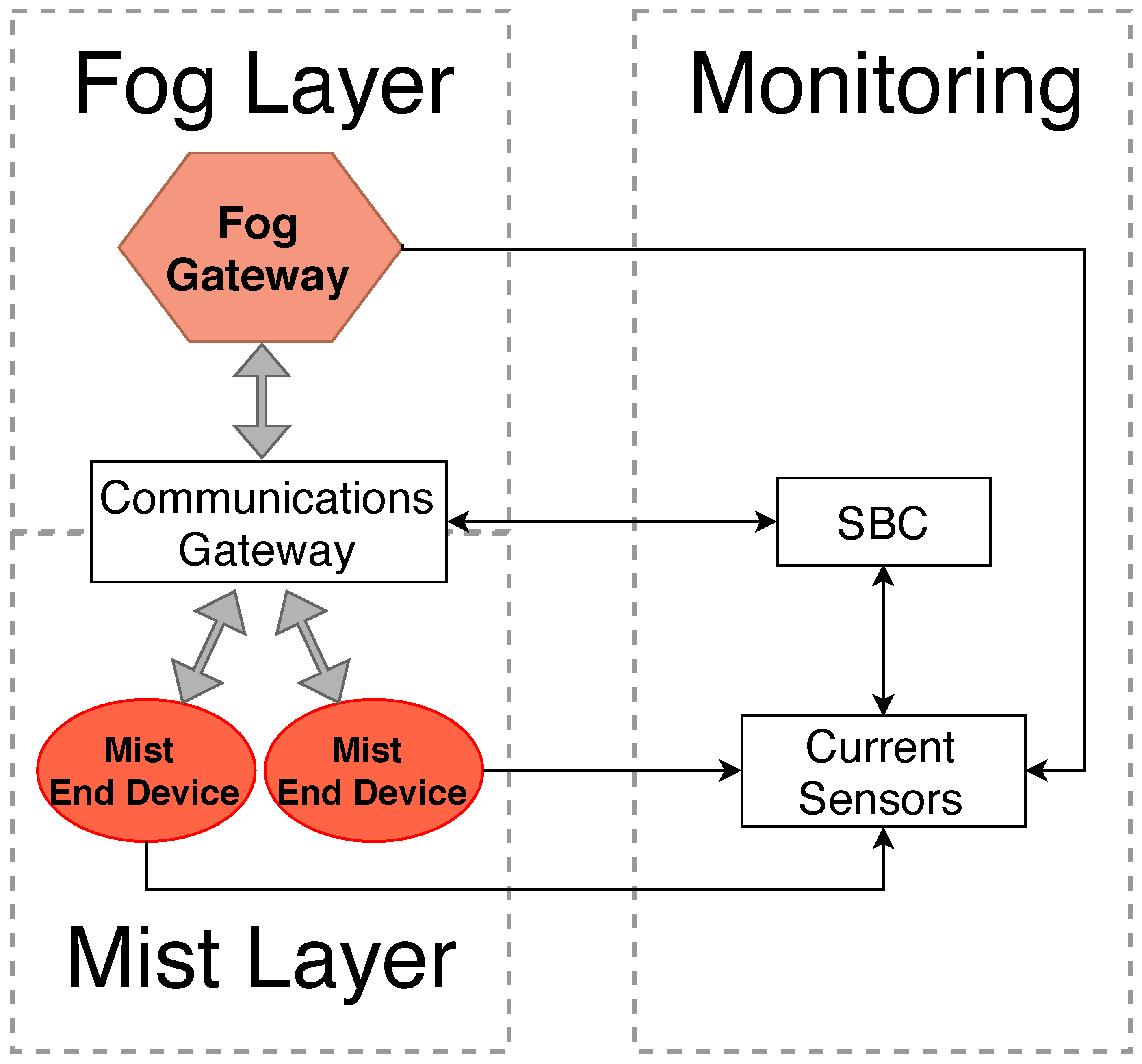
3. Design and Implementation of the Fog and Mist Computing Testbed
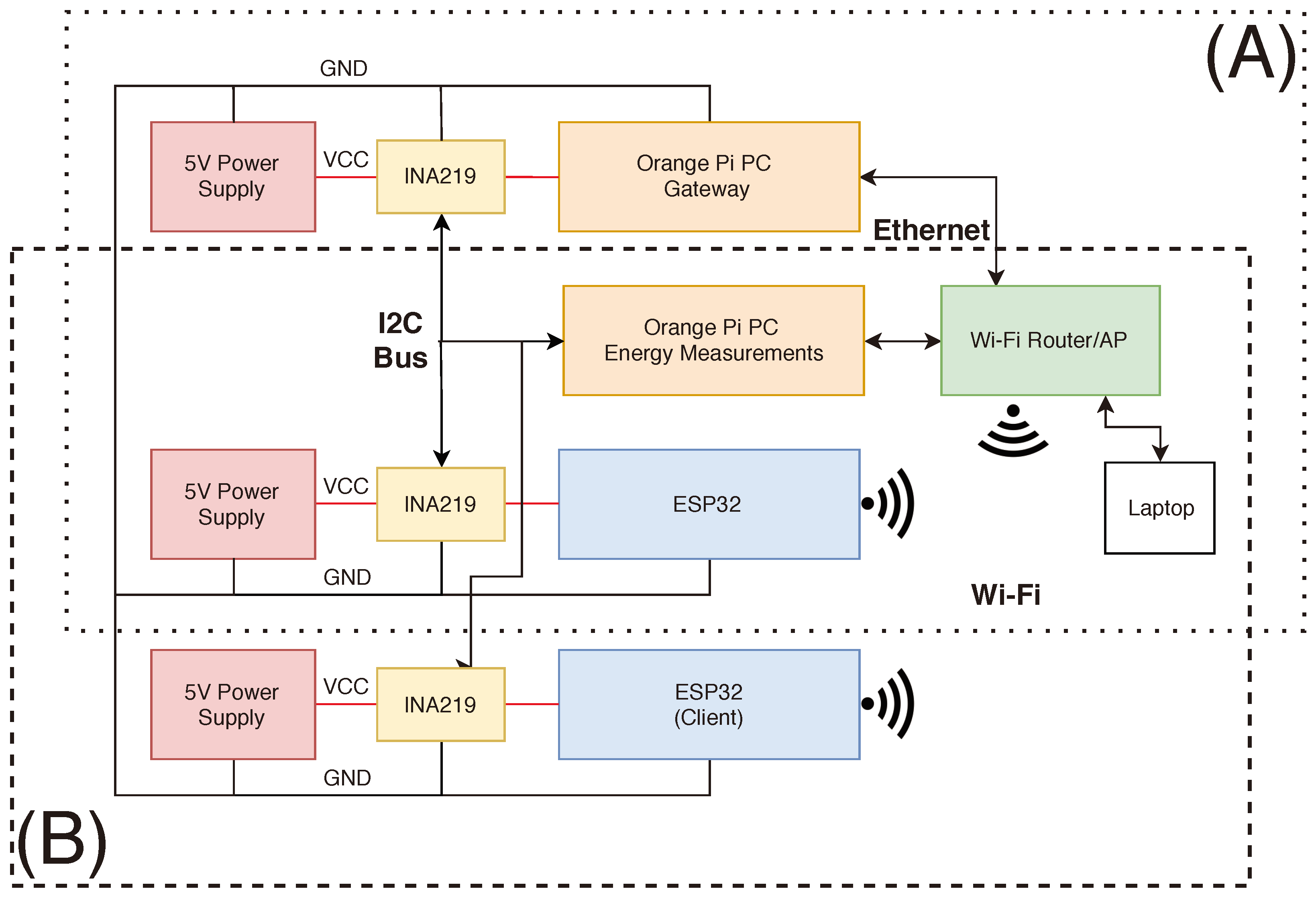
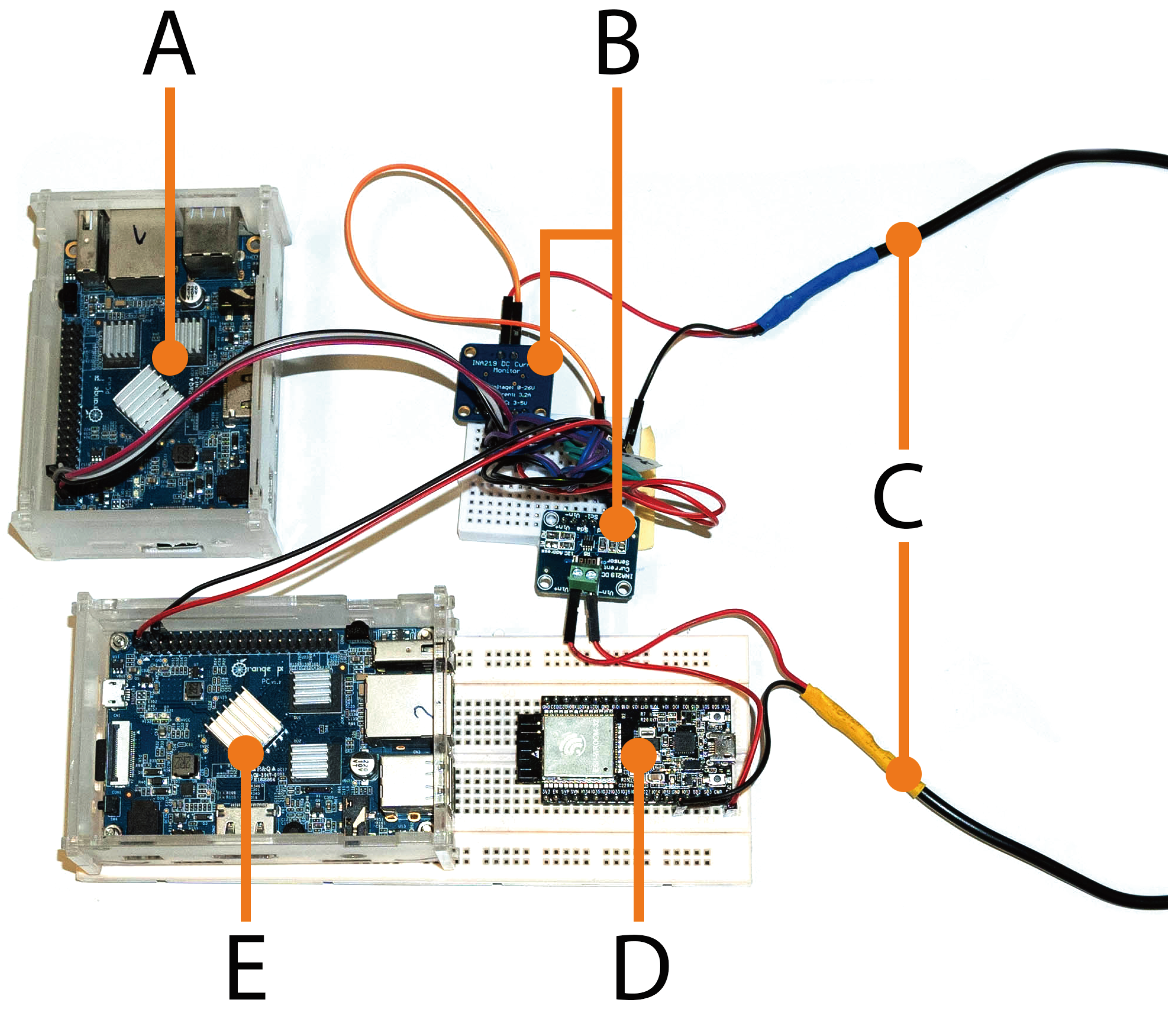
3.1. Selected Hardware
3.2. Software
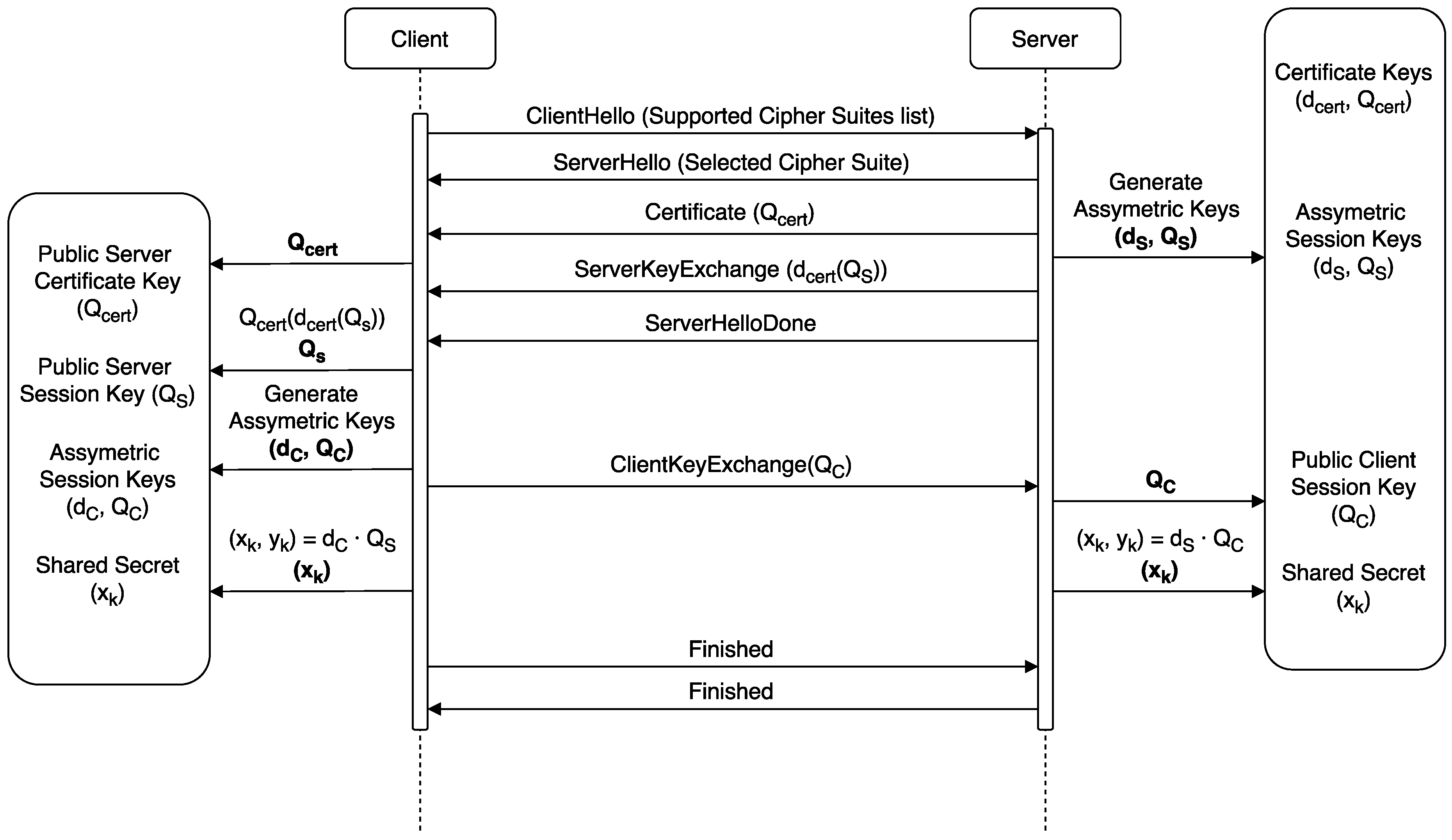
3.3. Selected Cipher Suites and Certificate Generation
- ECDHE-ECDSA-AES128-CBC-SHA256
- ECDHE-RSA-AES128-CBC-SHA256
- ECDHE-ECDSA-AES128-GCM-SHA256
- ECDHE-RSA-AES128-GCM-SHA256
4. Experiments
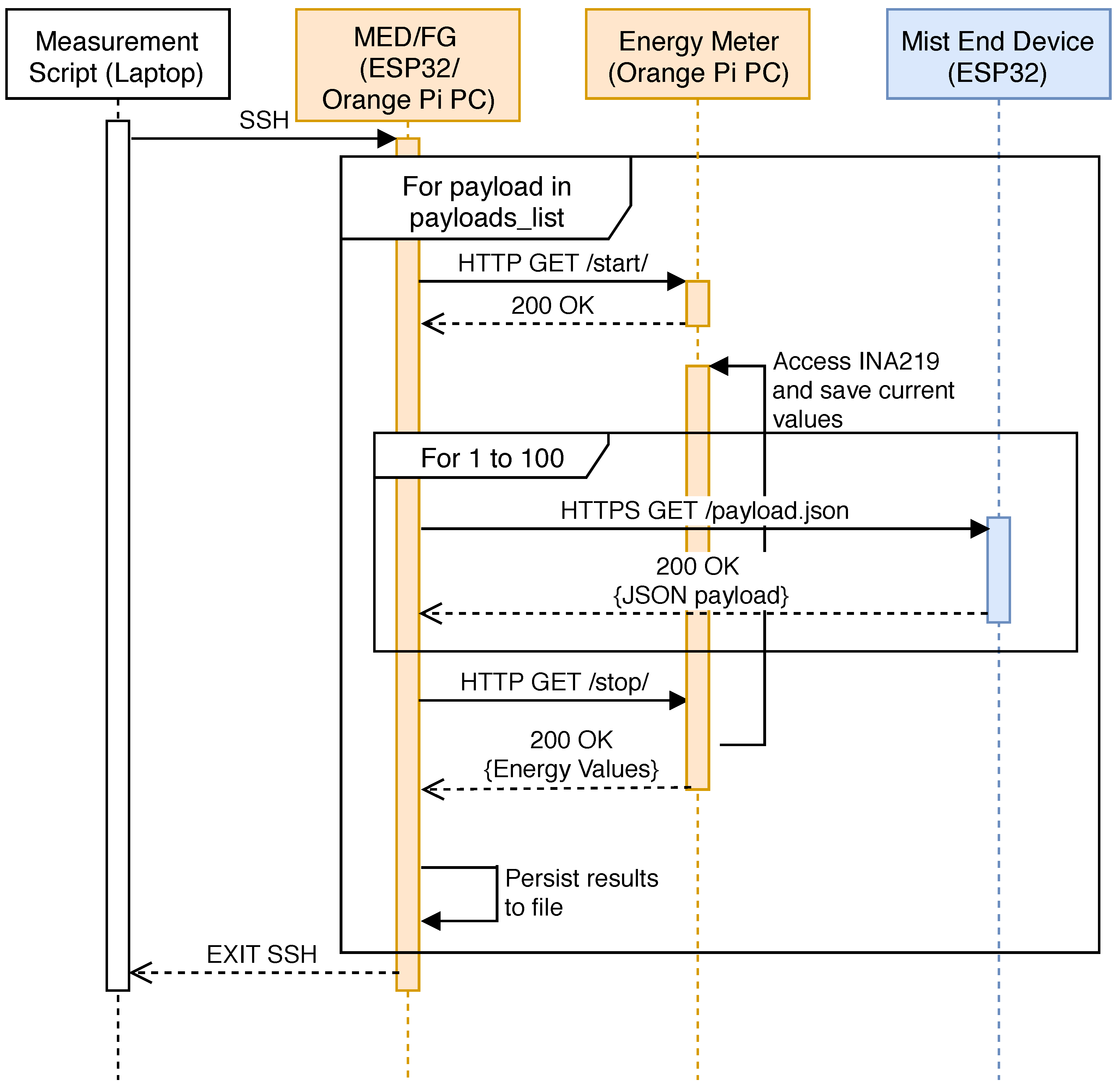
4.1. Testbed Setup
4.2. Testbed Performance Analysis
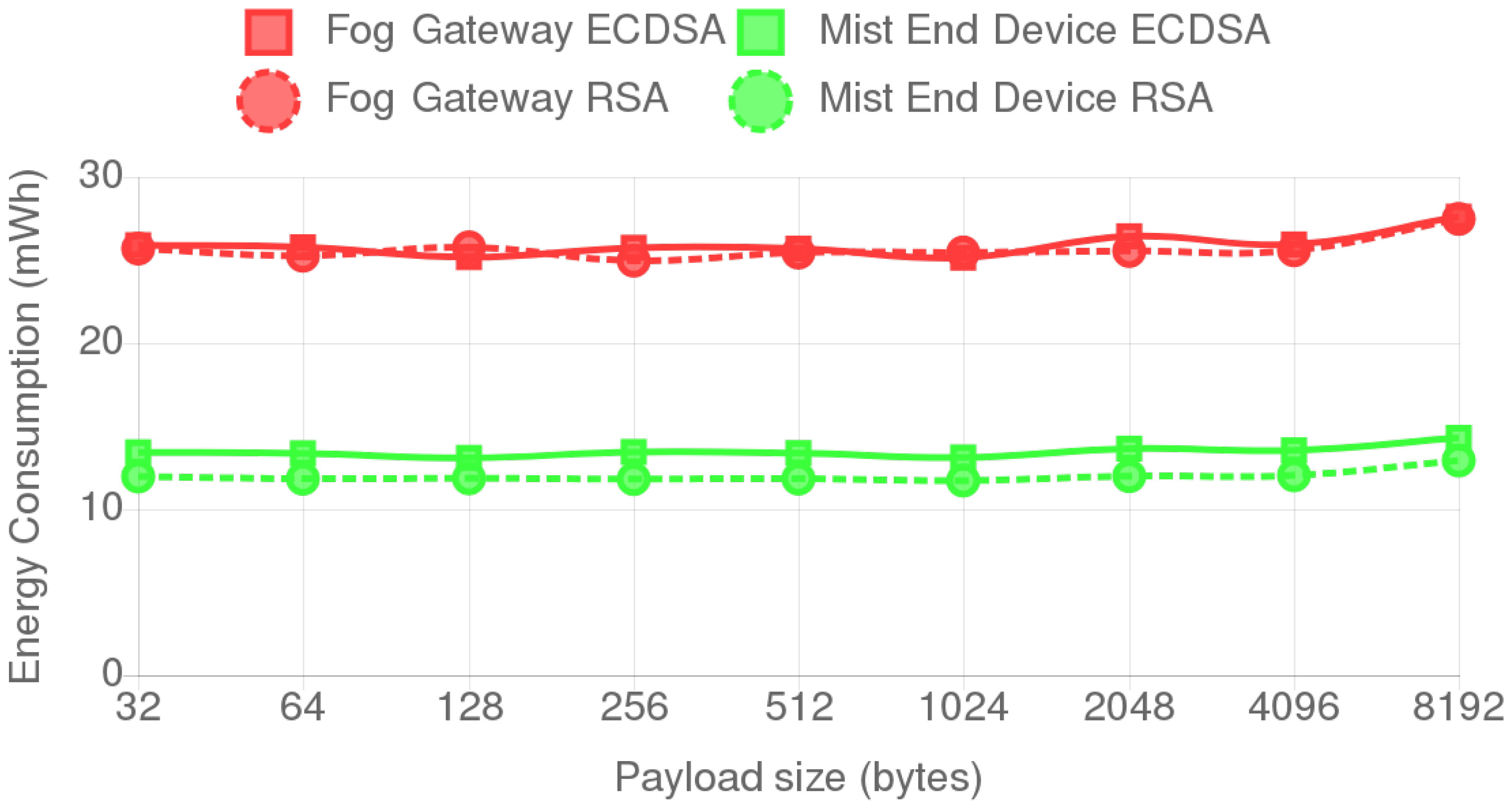
4.3. Influence of Payload Size on Energy Consumption
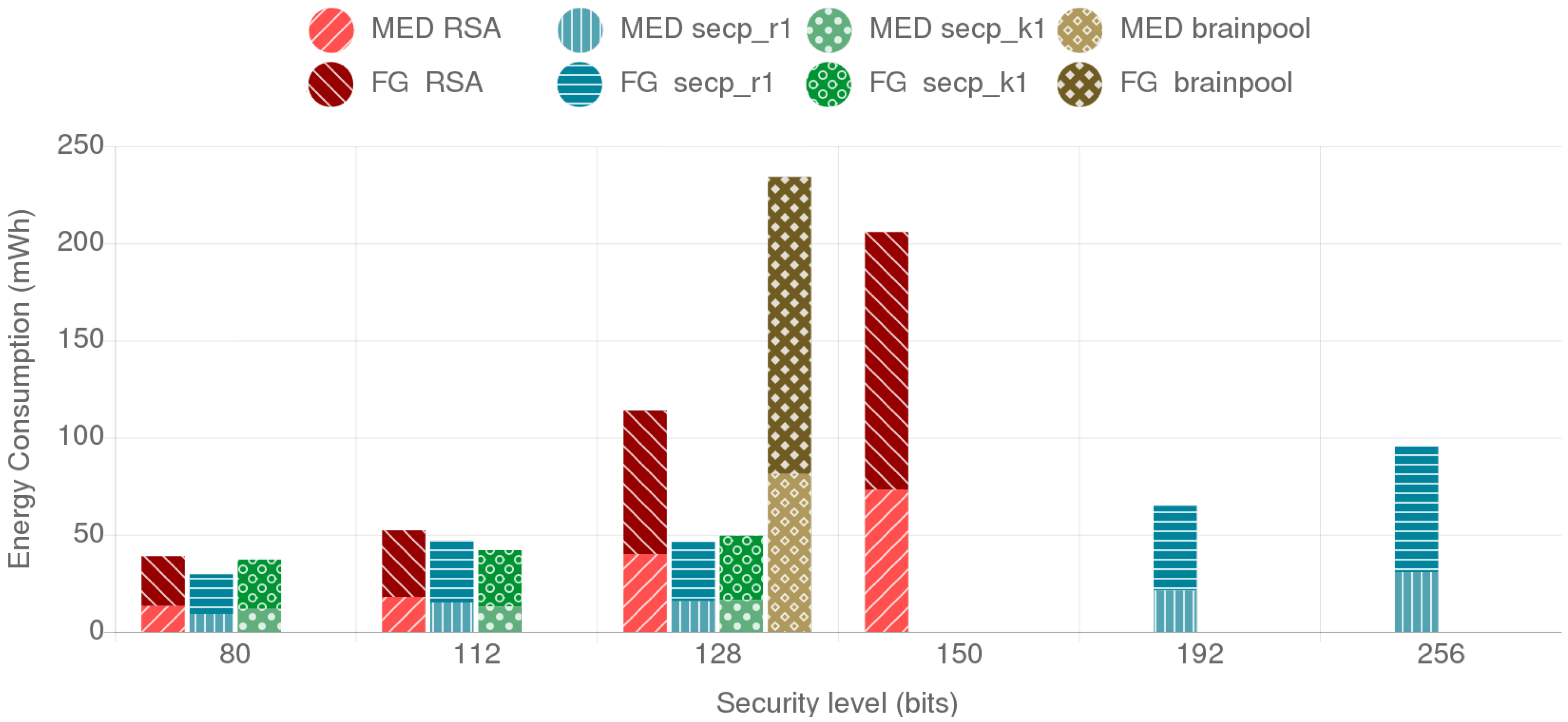
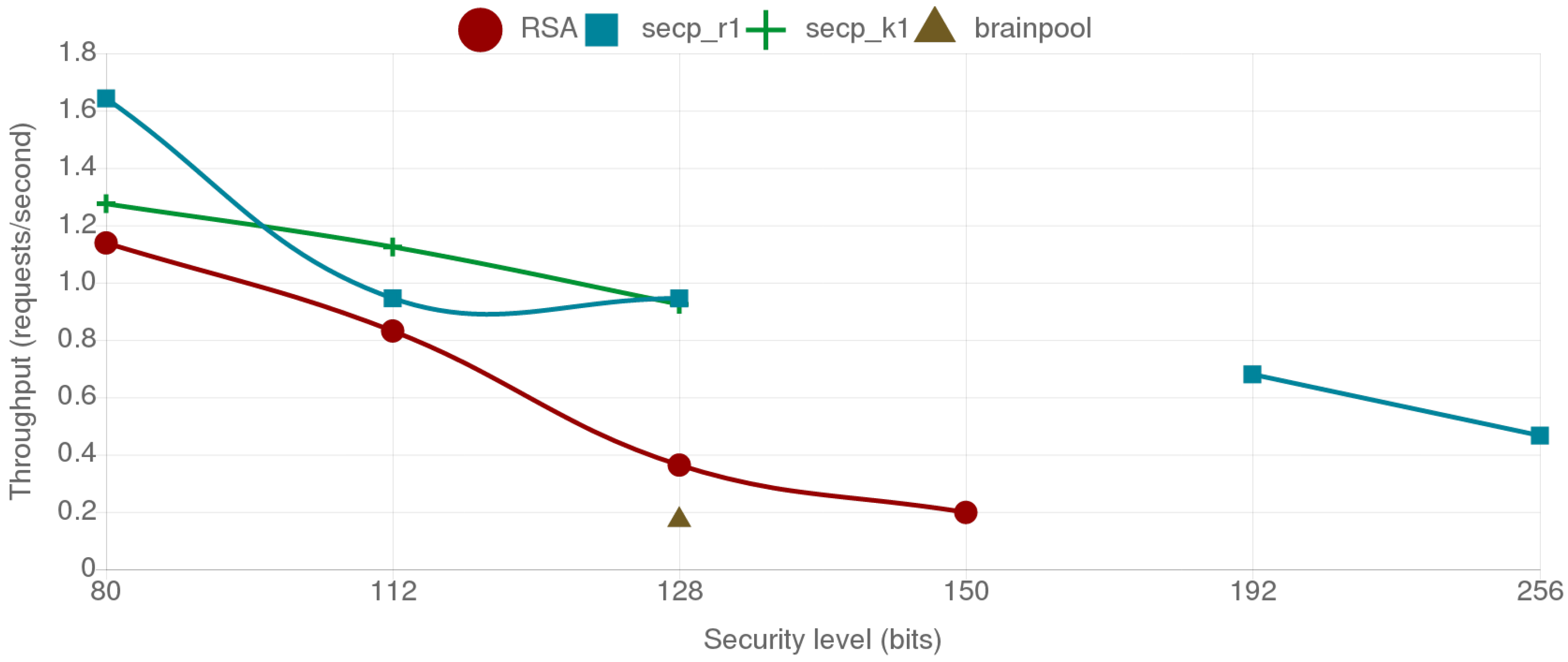
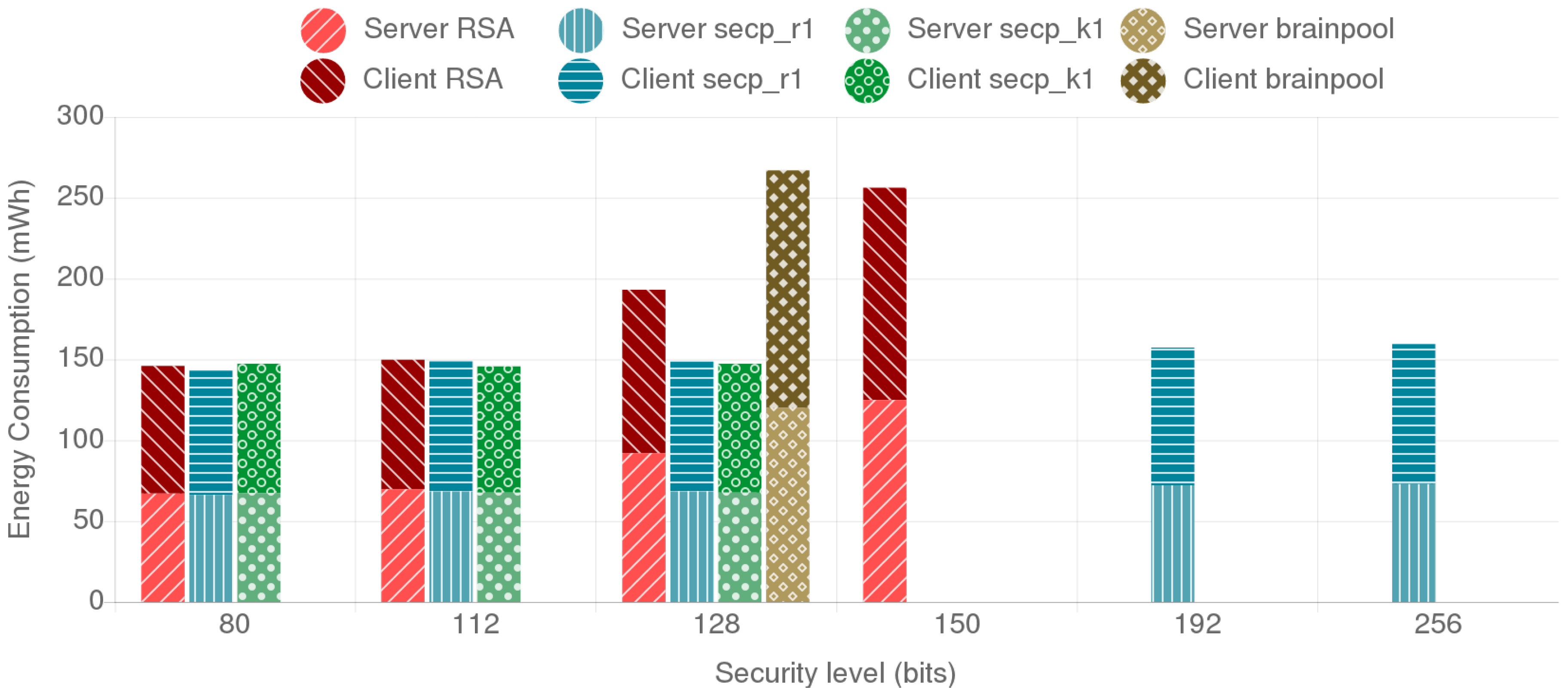
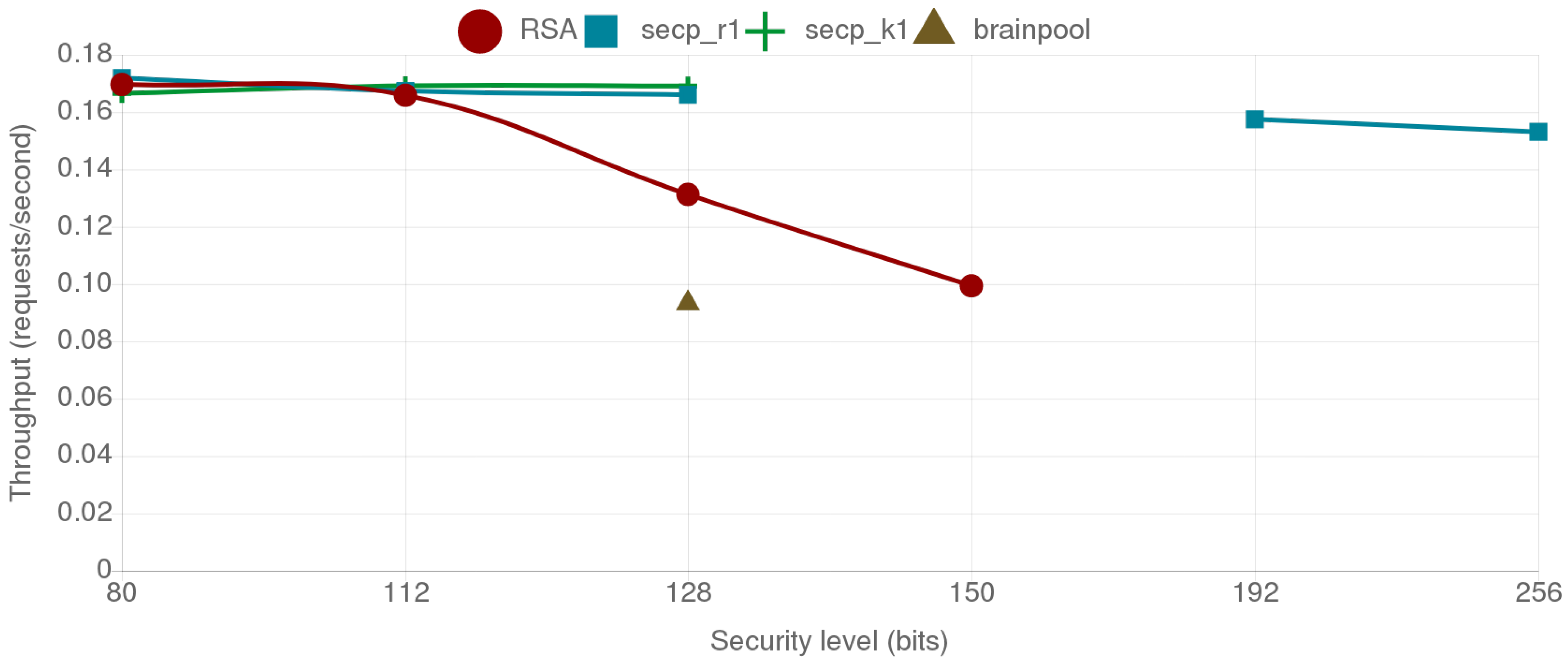
4.4. Comparative Analysis of the Provided Security Level, Energy Consumption and Data Throughput for the Selected Cipher Suites
4.4.1. Fog Gateway to Mist End-Device Scenario
4.4.2. Mist End-Device to Mist End-Device Scenario
4.5. Analysis of the Results
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| AES | Advanced Encryption Standard |
| BLE | Bluetooth Low Energy |
| CBC | Cipher Block Chaining |
| DDR | Double Data-Rate |
| DMA | Direct Memory Access |
| ECC | Elliptic Curve Cryptography |
| ECDHE | Elliptic curve Diffie–Hellman Ephemeral |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| GCM | Galois/Counter Mode |
| GPIO | General-Purpose Input/Output |
| HDMI | High-Definition Multimedia Interface |
| HMAC | Hash Message Authentication Code |
| HPC | High Performance Computing |
| HTTP | Hypertext Transport Protocol |
| HTTPS | Hypertext Transport Protocol Secure |
| IETF | Internet Engineering Task Force |
| I2C | Inter-Integrated Circuit |
| IoT | Internet of Things |
| LAN | Local Area Network |
| MAC | Message Authentication Code |
| MPI | Multi-Precision Integer |
| MQTT | Message Queuing Telemetry Transport |
| NIST | National Institute of Standards and Technology |
| NTP | Network Time Protocol |
| RSA | Rivest-Shamir-Adleman |
| SBC | Single Board Computer |
| SDK | Software Development Kit |
| SECG | Standards for Efficient Cryptography Group |
| SHA | Secure Hash Algorithm |
| SMEs | Small and Medium-sized Enterprise |
| SoC | System-on-Chip |
| TLS | Transport Layer Security |
| UART | Universal Asynchronous Receiver-Transmitter |
| USB | Universal Serial Bus |
References
- IHS. Internet of Things (IoT) Connected Devices Installed Base Worldwide from 2015 to 2025 (In Billions). Available online: https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/ (accessed on 15 October 2018).
- Shehabi, A.; Smith, S.; Sartor, D.; Brown, R.; Herrlin, M.; Koomey, J.; Masanet, E.; Horner, N.; Azevedo, I.; Lintner, W.; et al. United States Data Center Energy Usage Report; Number LBNL-1005775; Lawrence Berkeley National Laboratory: Berkeley, CA, USA, 2016. [Google Scholar]
- Avgerinou, M.; Bertoldi, P.; Castellazzi, L. Trends in Data Centre Energy Consumption under the European Code of Conduct for Data Centre Energy Efficiency. Energies 2017, 10, 1470. [Google Scholar] [CrossRef]
- O’Dwyer, K.J.; Malone, D. Bitcoin mining and its energy footprint. In Proceedings of the 25th IET Irish Signals Systems Conference 2014 and 2014 China-Ireland International Conference on Information and Communications Technologies (ISSC 2014/CIICT 2014), Limerick, Ireland, 26–27 June 2014; pp. 280–285. [Google Scholar]
- Pérez-Expósito, J.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. VineSens: An Eco-Smart Decision-Support Viticulture System. Sensors 2017, 17, 465. [Google Scholar] [CrossRef] [PubMed]
- Froiz-Míguez, I.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. Design, Implementation and Practical Evaluation of an IoT Home Automation System for Fog Computing Applications Based on MQTT and ZigBee-WiFi Sensor Nodes. Sensors 2018, 18, 2660. [Google Scholar] [CrossRef] [PubMed]
- Suárez-Albela, M.; Fraga-Lamas, P.; Fernández-Caramés, T.M.; Dapena, A.; González-López, M. Home Automation System Based on Intelligent Transducer Enablers. Sensors 2016, 16, 1595. [Google Scholar] [CrossRef] [PubMed]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Castedo, L. Towards the Internet of Smart Trains: A Review on Industrial IoT-Connected Railways. Sensors 2017, 17, 1457. [Google Scholar] [CrossRef] [PubMed]
- Hernández-Rojas, D.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Escudero, C. Design and Practical Evaluation of a Family of Lightweight Protocols for Heterogeneous Sensing through BLE Beacons in IoT Telemetry Applications. Sensors 2018, 18, 57. [Google Scholar] [CrossRef] [PubMed]
- Hernández-Rojas, D.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Escudero, C. A Plug-and-Play Human-Centered Virtual TEDS Architecture for the Web of Things. Sensors 2018, 18, 2052. [Google Scholar] [CrossRef] [PubMed]
- Fraga-Lamas, P.; Noceda-Davila, D.; Fernández-Caramés, T.M.; Díaz-Bouza, M.; Vilar-Montesinos, M. Smart Pipe System for a Shipyard 4.0. Sensors 2016, 16, 2186. [Google Scholar] [CrossRef] [PubMed]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on Human-Centered IoT-Connected Smart Labels for the Industry 4.0. IEEE Access 2018, 6, 25939–25957. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Suárez-Albela, M.; Castedo, L.; González-López, M. A Review on Internet of Things for Defense and Public Safety. Sensors 2016, 16, 1644. [Google Scholar] [CrossRef] [PubMed]
- Yeow, K.; Gani, A.; Ahmad, R.W.; Rodrigues, J.J.P.C.; Ko, K. Decentralized Consensus for Edge-Centric Internet of Things: A Review, Taxonomy, and Research Issues. IEEE Access 2018, 6, 1513–1524. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. A Review on the Use of Blockchain for the Internet of Things. IEEE Access 2018, 6, 32979–33001. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M. An intelligent power outlet system for the smart home of the Internet of Things. Int. J. Distrib. Sens. Netw. 2015, 11, 214805. [Google Scholar] [CrossRef] [PubMed]
- Blanco-Novoa, O.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. An Electricity Price-Aware Open-Source Smart Socket for the Internet of Energy. Sensors 2017, 17, 643. [Google Scholar] [CrossRef] [PubMed]
- Blanco-Novoa, O.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Vilar-Montesinos, M.A. A Practical Evaluation of Commercial Industrial Augmented Reality Systems in an Industry 4.0 Shipyard. IEEE Access 2018, 6, 8201–8218. [Google Scholar] [CrossRef]
- Fraga-Lamas, P.; Fernández-Caramés, T.M.; Blanco-Novoa, O.; Vilar-Montesinos, M.A. A Review on Industrial Augmented Reality Systems for the Industry 4.0 Shipyard. IEEE Access 2018, 6, 13358–13375. [Google Scholar] [CrossRef]
- Blanco-Novoa, O.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. A Cost-Effective IoT System for Monitoring Indoor Radon Gas Concentration. Sensors 2018, 18, 2198. [Google Scholar] [CrossRef] [PubMed]
- Fernández-Caramés, T.M.; Fraga-Lamas, P.; Suárez-Albela, M.; Castedo, L. A methodology for evaluating security in commercial RFID systems. In Radio Frequency Identification; Crepaldi, P.C., Pimenta, T.C., Eds.; IntechOpen: London, UK, 2017. [Google Scholar] [CrossRef]
- Burg, A.; Chattopadhyay, A.; Lam, K. Wireless Communication and Security Issues for Cyber-Physical Systems and the Internet-of-Things. Proc. IEEE 2018, 106, 38–60. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Fraga-Lamas, P.; Suárez-Albela, M.; Castedo, L. Reverse Engineering and Security Evaluation of Commercial Tags for RFID-Based IoT Applications. Sensors 2016, 17, 28. [Google Scholar] [CrossRef] [PubMed]
- Cleveland, F.M. Cyber security issues for Advanced Metering Infrastructure (AMI). In Proceedings of the 2008 IEEE Power and Energy Society General Meeting-Conversion and Delivery of Electrical Energy in the 21st Century, Pittsburgh, PA, USA, 20–24 July 2008; pp. 1–5. [Google Scholar]
- Ghena, B.; Beyer, W.; Hillaker, A.; Pevarnek, J.; Halderman, J.A. Green Lights Forever: Analyzing the Security of Traffic Infrastructure. In Proceedings of the 8th USENIX Workshop on Offensive Technologies (WOOT’14), San Diego, CA, USA, 19 August 2014. [Google Scholar]
- Langner, R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Secur. Priv. 2011, 9, 49–51. [Google Scholar] [CrossRef]
- Asplund, M.; Nadjm-Tehrani, S. Attitudes and perceptions of IoT security in critical societal services. IEEE Access 2016, 4, 2130–2138. [Google Scholar] [CrossRef]
- Assaderaghi, F.; Chindalore, G.; Ibrahim, B.; de Jong, H.; Joye, M.; Nassar, S.; Steinbauer, W.; Wagner, M.; Wille, T. Privacy and security: Key requirements for sustainable IoT growth. In Proceedings of the 2017 Symposium on VLSI Technology, Kyoto, Japan, 5–8 June 2017; pp. T8–T13. [Google Scholar]
- Suárez-Albela, M.; Fernández-Caramés, T.; Fraga-Lamas, P.; Castedo, L. A Practical Evaluation of a High-Security Energy-Efficient Gateway for IoT Fog Computing Applications. Sensors 2017, 17, 1978. [Google Scholar] [CrossRef] [PubMed]
- Fernández-Caramés, T.M.; Fraga-Lamas, P.; Suárez-Albela, M.; Díaz-Bouza, M. A Fog Computing Based Cyber-Physical System for the Automation of Pipe-Related Tasks in the Industry 4.0 Shipyard. Sensors 2018, 18, 1961. [Google Scholar] [CrossRef] [PubMed]
- Fernández-Caramés, T.M.; Fraga-Lamas, P.; Suárez-Albela, M.; Vilar-Montesinos, M. A Fog Computing and Cloudlet Based Augmented Reality System for the Industry 4.0 Shipyard. Sensors 2018, 18, 1798. [Google Scholar] [CrossRef] [PubMed]
- Oteafy, S.M.A.; Hassanein, H.S. IoT in the Fog: A Roadmap for Data-Centric IoT Development. IEEE Commun. Mag. 2018, 56, 157–163. [Google Scholar] [CrossRef]
- Preden, J.S.; Tammemäe, K.; Jantsch, A.; Leier, M.; Riid, A.; Calis, E. The Benefits of Self-Awareness and Attention in Fog and Mist Computing. Computer 2015, 48, 37–45. [Google Scholar] [CrossRef]
- MQTT Version 5.0, Committee Specification 02. Available online: http://docs.oasis-open.org/mqtt/mqtt/v5.0/cs02/mqtt-v5.0-cs02.html (accessed on 15 October 2018).
- Sen, S.; Koo, J.; Bagchi, S. TRIFECTA: Security, Energy Efficiency, and Communication Capacity Comparison for Wireless IoT Devices. IEEE Internet Comput. 2018, 22, 74–81. [Google Scholar] [CrossRef] [Green Version]
- The Intel Edison Module | IoT. Available online: https://software.intel.com/en-us/iot/hardware/edison (accessed on 15 October 2018).
- Arduino TIAN. Available online: https://www.arduino.cc/en/Main/ArduinoBoardTian (accessed on 15 October 2018).
- Arduino MKR WIFI 1010. Available online: https://store.arduino.cc/arduino-mkr-wifi-1010 (accessed on 15 October 2018).
- LightBlue Bean. Available online: https://punchthrough.com/products/bean (accessed on 15 October 2018).
- ESP32 Overview | Espressif Systems. Available online: https://espressif.com/en/products/hardware/esp32/overview (accessed on 15 October 2018).
- Particle Photon (Wi-Fi). Available online: https://www.particle.io/products/hardware/photon-wifi-dev-kit (accessed on 15 October 2018).
- Liu, Z.; Großschädl, J.; Hu, Z.; Järvinen, K.; Wang, H.; Verbauwhede, I. Elliptic Curve Cryptography with Efficiently Computable Endomorphisms and Its Hardware Implementations for the Internet of Things. IEEE Trans. Comput. 2017, 66, 773–785. [Google Scholar] [CrossRef]
- Gielata, A.; Russek, P.; Wiatr, K. AES hardware implementation in FPGA for algorithm acceleration purpose. In Proceedings of the 2008 International Conference on Signals and Electronic Systems, Krakow, Poland, 14–17 September 2008; pp. 137–140. [Google Scholar]
- Chaves, R.; Kuzmanov, G.; Sousa, L.; Vassiliadis, S. Cost-Efficient SHA Hardware Accelerators. IEEE Trans. Very Large Scale Integr. Syst. 2008, 16, 999–1008. [Google Scholar] [CrossRef] [Green Version]
- Suárez-Albela, M.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. A Practical Performance Comparison of ECC and RSA for Resource-Constrained IoT Devices. In Proceedings of the 2018 Global Internet of Things Summit (GIoTS), Bilbao, Spain, 4–7 June 2018. [Google Scholar]
- Deogirikar, J.; Vidhate, A. Security Attacks in IoT: A Survey. In Proceedings of the 2017 International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Palladam, India, 10–11 February 2017; pp. 32–37. [Google Scholar]
- Uke, S.N.; Mahajan, A.R.; Thool, R.C. UML Modeling of Physical and Data Link Layer Security Attacks in WSN. Int. J. Comput. Appl. 2013, 70, 25–28. [Google Scholar]
- Sagduyu, Y.E.; Berryt, R.A.; Ephremidesi, A. Wireless jamming attacks under dynamic traffic uncertainty. In Proceedings of the 8th International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks, Avignon, France, 31 May–4 June 2010; pp. 303–312. [Google Scholar]
- Tsiropoulou, E.E.; Baras, J.S.; Papavassiliou, S.; Qu, G. On the Mitigation of Interference Imposed by Intruders in Passive RFID Networks. In Decision and Game Theory for Security; Zhu, Q., Alpcan, T., Panaousis, E., Tambe, M., Casey, W., Eds.; Springer International Publishing: Cham, Switzerland, 2016; pp. 62–80. [Google Scholar]
- Sagduyu, Y.E.; Ephremides, A. A Game-theoretic Analysis of Denial of Service Attacks in Wireless Random Access. Wirel. Netw. 2009, 15, 651–666. [Google Scholar] [CrossRef]
- Shwartz, O.; Mathov, Y.; Bohadana, M.; Oren, Y.; Elovici, Y. Reverse Engineering IoT Devices: Effective Techniques and Methods. IEEE Internet Things J. 2018, 1. [Google Scholar] [CrossRef]
- Das, K.; Taggu, A. A comprehensive analysis of DoS attacks in Mobile Adhoc Networks. In Proceedings of the 2014 International Conference on Advances in Computing, Communications and Informatics (ICACCI), New Delhi, India, 24–27 September 2014; pp. 2273–2278. [Google Scholar]
- Liu, J.; Zhang, C.; Fang, Y. EPIC: A Differential Privacy Framework to Defend Smart Homes Against Internet Traffic Analysis. IEEE Internet Things J. 2018, 5, 1206–1217. [Google Scholar] [CrossRef]
- Li, C.; Qin, Z.; Novak, E.; Li, Q. Securing SDN Infrastructure of IoT–Fog Networks From MitM Attacks. IEEE Internet Things J. 2017, 4, 1156–1164. [Google Scholar] [CrossRef]
- Chen, B.; Ho, D.W.C.; Hu, G.; Yu, L. Secure Fusion Estimation for Bandwidth Constrained Cyber-Physical Systems Under Replay Attacks. IEEE Trans. Cybern. 2018, 48, 1862–1876. [Google Scholar] [CrossRef] [PubMed]
- Zhang, K.; Liang, X.; Lu, R.; Shen, X. Sybil Attacks and Their Defenses in the Internet of Things. IEEE Internet Things J. 2014, 1, 372–383. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and Other Botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Park, J.; Tyagi, A. Using Power Clues to Hack IoT Devices: The power side channel provides for instruction-level disassembly. IEEE Consum. Electron. Mag. 2017, 6, 92–102. [Google Scholar] [CrossRef]
- Limbasiya, T.; Karati, A. Cryptanalysis and improvement of a mutual user authentication scheme for the Internet of Things. In Proceedings of the 2018 International Conference on Information Networking (ICOIN), Chiang Mai, Thailand, 10–12 January 2018; pp. 168–173. [Google Scholar]
- Gupta, D.S.; Biswas, G.P.; Nandan, R. Security weakness of a lattice-based key exchange protocol. In Proceedings of the 2018 4th International Conference on Recent Advances in Information Technology (RAIT), Dhanbad, India, 15–17 March 2018; pp. 1–5. [Google Scholar]
- Maier, A.; Sharp, A.; Vagapov, Y. Comparative analysis and practical implementation of the ESP32 microcontroller module for the internet of things. In Proceedings of the 2017 Internet Technologies and Applications (ITA), Wrexham, UK, 12–15 September 2017; pp. 143–148. [Google Scholar]
- Allafi, I.; Iqbal, T. Design and implementation of a low cost web server using ESP32 for real-time photovoltaic system monitoring. In Proceedings of the 2017 IEEE Electrical Power and Energy Conference (EPEC), Saskatoon, SK, Canada, 22–25 October 2017; pp. 1–5. [Google Scholar]
- Kodali, R.K.; Yerroju, S. IoT based smart emergency response system for fire hazards. In Proceedings of the 2017 3rd International Conference on Applied and Theoretical Computing and Communication Technology (iCATccT), Tumkur, India, 21–23 December 2017; pp. 194–199. [Google Scholar]
- Jalali, F.; Hinton, K.; Ayre, R.; Alpcan, T.; Tucker, R.S. Fog Computing May Help to Save Energy in Cloud Computing. IEEE J. Sel. Areas Commun. 2016, 34, 1728–1739. [Google Scholar] [CrossRef]
- Biason, A.; Pielli, C.; Rossi, M.; Zanella, A.; Zordan, D.; Kelly, M.; Zorzi, M. EC-CENTRIC: An Energy- and Context-Centric Perspective on IoT Systems and Protocol Design. IEEE Access 2017, 5, 6894–6908. [Google Scholar] [CrossRef]
- Arshad, R.; Zahoor, S.; Shah, M.A.; Wahid, A.; Yu, H. Green IoT: An Investigation on Energy Saving Practices for 2020 and Beyond. IEEE Access 2017, 5, 15667–15681. [Google Scholar] [CrossRef]
- Pan, J.; Jain, R.; Paul, S.; Vu, T.; Saifullah, A.; Sha, M. An Internet of Things Framework for Smart Energy in Buildings: Designs, Prototype, and Experiments. IEEE Internet Things J. 2015, 2, 527–537. [Google Scholar] [CrossRef]
- Brown, M.; Hankerson, D.; López, J.; Menezes, A. Software Implementation of the NIST Elliptic Curves Over Prime Fields. In Topics in Cryptology—CT-RSA 2001; Naccache, D., Ed.; Springer: Berlin/Heidelberg, Germany, 2001; pp. 250–265. [Google Scholar]
- Wenger, E.; Hutter, M. Exploring the Design Space of Prime Field vs. Binary Field ECC-Hardware Implementations. In Information Security Technology for Applications; Laud, P., Ed.; Springer: Berlin/Heidelberg, Germany, 2012; pp. 256–271. [Google Scholar]
- Jankowski, K.; Laurent, P.; O’Mahony, A. Intel Polynomial Multiplication Instruction and its Usage for Elliptic Curve Cryptography. Available online: https://www.intel.com/content/dam/www/public/us/en/documents/white-papers/polynomial-multiplication-instructions-paper.pdf (accessed on 15 October 2018).
- Galbraith, S.D.; Gebregiyorgis, S.W. Summation Polynomial Algorithms for Elliptic Curves in Characteristic Two. In Progress in Cryptology—INDOCRYPT 2014; Meier, W., Mukhopadhyay, D., Eds.; Springer: Cham, Switzerland, 2014; pp. 409–427. [Google Scholar]
- SSL Library Mbed TLS/PolarSSL. Available online: https://tls.mbed.org/ (accessed on 15 October 2018).
- Mbed TLS Core Features. Available online: https://tls.mbed.org/core-features (accessed on 15 October 2018).
- SEC 2: Recommended Elliptic Curve Domain Parameters. Available online: http://www.secg.org/SEC2-Ver-1.0.pdf (accessed on 15 October 2018).
- National Institute of Standards and Technology. Available online: https://www.nist.gov/ (accessed on 15 October 2018).
- Bernstein, D.J.; Lange, T.; Niederhagen, R. Dual EC: A Standardized Back Door. In The New Codebreakers: Essays Dedicated to David Kahn on the Occasion of His 85th Birthday; Ryan, P.Y.A., Naccache, D., Quisquater, J.J., Eds.; Springer: Berlin/Heidelberg, Germany, 2016; pp. 256–281. [Google Scholar]
- Standards for Efficient Cryptography Group. Available online: http://www.secg.org/ (accessed on 15 October 2018).
- Elliptic Curve Cryptography (ECC) Brainpool Standard Curves and Curve Generation. Available online: https://tools.ietf.org/html/rfc5639 (accessed on 15 October 2018).
- IETF | Internet Engineering Task Force. Available online: https://www.ietf.org/ (accessed on 15 October 2018).
- Elliptic Curve Performance: NIST vs Brainpool. Available online: https://tls.mbed.org/kb/cryptography/elliptic-curve-performance-nist-vs-brainpool (accessed on 15 October 2018).
- Open SSL. Available online: https://www.openssl.org/ (accessed on 15 October 2018).
- Orange Pi Pc. Available online: http://www.orangepi.org/orangepipc/ (accessed on 15 October 2018).
- Crypto Engine Support. Available online: http://sunxi.montjoie.ovh/ (accessed on 15 October 2018).
- Espressif IoT Development Framework. Official development framework for ESP32. Available online: https://github.com/espressif/esp-idf (accessed on 15 October 2018).
- MinGW | Minimalist GNU for Windows. Available online: http://www.mingw.org/ (accessed on 15 October 2018).
- FreeRTOS—Market leading RTOS (Real Time Operating System) for Embedded Systems with Internet of Things Extensions. Available online: https://www.freertos.org/ (accessed on 15 October 2018).
- Armbian: Linux for ARM Development Boards. Available online: https://www.armbian.com/ (accessed on 15 October 2018).
- Python.org. Available online: https://www.python.org/ (accessed on 15 October 2018).
- Pi-ina219 1.2.0. Available online: https://pypi.org/project/pi-ina219/ (accessed on 15 October 2018).
- Polk, T.; McKay, K.; Chokhani, S. Guidelines for the Selection and Use of Transport Layer Security (TLS) Implementations. Available online: https://csrc.nist.gov/publications/detail/sp/800-52/archive/2005-06-09 (accessed on 15 October 2018).
- The Transport Layer Security (TLS) Protocol Version 1.3 draft-ietf-tls-tls13-28. Available online: https://tools.ietf.org/html/draft-ietf-tls-tls13-28 (accessed on 15 October 2018).
- Suárez-Albela, M.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. Impact of Clock Frequency on the Performance and Consumption of a Secure IoT Node. In Proceedings of the XXXIII Simposium Nacional de la Union Científica Internacional de Radio (URSI), Granada, Spain, 5–7 September 2018. [Google Scholar]
- Faker Webpage. Available online: https://pypi.python.org/pypi/Faker/0.7.3 (accessed on 15 October 2018).
- Xu, R.; Li, Z.; Wang, C.; Ni, P. Impact of data compression on energy consumption of wireless-networked handheld devices. In Proceedings of the 23rd International Conference on Distributed Computing Systems, Providence, RI, USA, 19–22 May 2003. [Google Scholar]
- NTP: The Network Time Protocol. Available online: http://www.ntp.org/ (accessed on 15 October 2018).

| Name | Clock Rate | Cores | RAM Size | Max. Power | Connectivity | References |
|---|---|---|---|---|---|---|
| Intel Edison Module * | 500 MHz | 2 | 1 GB | 1 W | Wi-Fi/BLE | [36] |
| Arduino Tian | 560 MHz/48 MHz | 1/1 | 64 MB/32 KB | 1.551 W | Wi-Fi | [37] |
| Arduino MKR WiFi 1010 | 48 MHz | 1 | 32 KB | 2.31 W | Wi-Fi/BLE | [38] |
| LightBlue Bean+ | 8 MHz | 1 | 2 KB MB | 3.5 W | BLE | [39] |
| ESP32 | 240 MHz | 2 | 512 KB | 1.65 W | Wi-Fi/BLE | [40] |
| Particle Photon | 120 MHz | 1 | 128 KB | 1.419 W | Wi-Fi | [41] |
| Security Level | RSA Key Size | ECDSA Key Size | ESP-IDF Curves |
|---|---|---|---|
| 80 | 1024 bits | 160–223 bits | secp192r1, secp192k1 |
| 112 | 2048 bits | 224–255 bits | secp224r1, secp224k1 |
| 128 | 3072 bits | 256–383 bits | secp256r1, secp256k1, bp256r1 |
| 192 | 7680 bits | 384–511 bits | secp384r1, bp384r1 |
| 256 | 15,360 bits | 512+ bits | secp521r1, bp521r1 |
| RSA Key Size or ECC Curve | Time Difference (%) |
|---|---|
| rsa1024 | 0.016 |
| rsa2048 | 0.013 |
| rsa3072 | 0.005 |
| rsa4096 | 0.003 |
| secp192k1 | 0.018 |
| secp192r1 | 0.023 |
| secp224k1 | 0.016 |
| secp224r1 | 0.013 |
| secp256k1 | 0.013 |
| secp256r1 | 0.015 |
| bp256r1 | 0.003 |
| secp384r1 | 0.009 |
| secp521r1 | 0.006 |
| ESP32 Server | ESP32 Client | |
|---|---|---|
| SYN to SYN-ACK | 0.27745 | 0.00003 |
| Server Hello Done to Client Key Exchange | 0.00189 | 0.97986 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Suárez-Albela, M.; Fraga-Lamas, P.; Fernández-Caramés, T.M. A Practical Evaluation on RSA and ECC-Based Cipher Suites for IoT High-Security Energy-Efficient Fog and Mist Computing Devices. Sensors 2018, 18, 3868. https://doi.org/10.3390/s18113868
Suárez-Albela M, Fraga-Lamas P, Fernández-Caramés TM. A Practical Evaluation on RSA and ECC-Based Cipher Suites for IoT High-Security Energy-Efficient Fog and Mist Computing Devices. Sensors. 2018; 18(11):3868. https://doi.org/10.3390/s18113868
Chicago/Turabian StyleSuárez-Albela, Manuel, Paula Fraga-Lamas, and Tiago M. Fernández-Caramés. 2018. "A Practical Evaluation on RSA and ECC-Based Cipher Suites for IoT High-Security Energy-Efficient Fog and Mist Computing Devices" Sensors 18, no. 11: 3868. https://doi.org/10.3390/s18113868







