A New Privacy-Preserving Handover Authentication Scheme for Wireless Networks
Abstract
:1. Introduction
2. Preliminaries
2.1. Bilinear Pairings and Complexity Assumptions
- Bilinearity: For and , we have .
- Non-degeneracy: , where 1 is the identity element of .
- Computability: There is an efficient algorithm to compute for and .
2.2. Pointcheval and Stern’s Blind Signature Scheme
- Setup: A trusted authority generates an elliptic curve group of prime order q with a generator P, and publishes domain parameters .
- KeyGen: The signer chooses , computes , sets the secret signing private key as x and the corresponding public verification key as Y.
- Sign: In order to get the signature of a message , a requester asks the signer to initiate a communication. The signer chooses , computes and sends the commitment to the requester. Upon receiving the commitment, the requester blinds it with two random elements into , computes and sends the challenge to the signer. Then, the signer returns a values to the requester. Finally, the requester verifies the following equation holds or not:If it holds, then the requester computes , and obtains a blind signature that is signed by the signer for the unknown message m.
- Verify: Anyone can verify that the pair is a valid Schnorr signature of m since it satisfies , where .
2.3. Improved Galindo and Garcia’s Identity-Based Signature Scheme
- Setup: A trusted authority named PKG first generates an elliptic curve group of prime order q with a generator P, chooses and computes . Finally, the PKG sets the master secret key and publishes the master public key .
- Extract: A user submits a private key request with his/her identity information to the PKG. Upon receiving the request, the PKG chooses , computes , and . Finally, the PKG sends to the user via a secure channel. Upon receiving the response message, the user computes and checks the following equation:If it holds, the user keeps the tuple as his/her identity-based signing private key. The corresponding public key can be computed as .
- Sign: To sign a message m, the signer with identity and signing private key chooses , computes , , and . Finally, the signer sets as his/her signature on m.
- Verify: Given the signer’s identity , a pair of message m and signature , anyone can compute and , check the following equation:If it holds, the verifier accepts the signature and outputs true. Otherwise, outputs ⊥.
2.4. Yasmin et al.’s Identity-Based One-Pass Authenticated Key Establishment Protocol
- Alice, the initiator of the protocol, chooses , computes , and , sets the shared session key . Then, Alice deletes L and ℓ. Finally, Alice sends to the receiver Bob, where is Alice’s identity-based signature on the ephemeral public key L together with Alice’s identity and Bob’s identity .
- Bob verifies the signature using and other public parameters. If the signature verification holds, Bob sets the common shared session key and deletes L. Otherwise, the protocol terminates here.
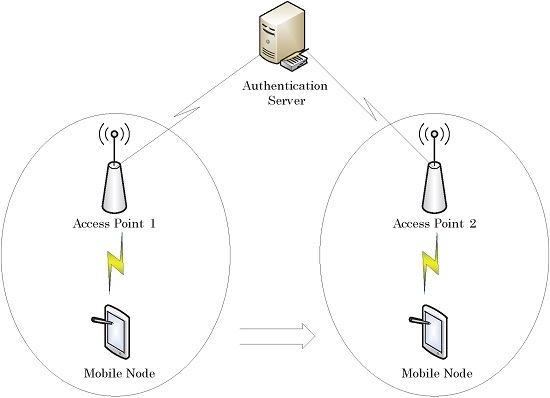
3. Cryptanalysis of He et al. PairHand
3.1. Review of He et al. PairHand
- For each AP with identity , the AS computes and . Then, the AS sends the AP’s identity-based private key to the AP via a secure channel.
- For an MN i with identity , the AS first checks MN i’s validity. If MN i is valid, the AS chooses a family of unlinkable pseudo-identities , and for each pseudo-identity , the AS computes as the MN j’s identity-based public key, and the associated private key . Then, the AS sends all tuples back to MN i via a secure channel.
- : MN i picks an unused pseudo-identity and the corresponding private key . Then MN i computes the signature , where , a time-stamp is added by MN i to counter replay attacks, and ‖ indicates message concatenation operation. Subsequently, MN i unicasts the access request message to the AP. After that, MN i computes the shared session key with the AP as .
- : Upon receiving , the AP firstly checks whether the time-stamp is valid. If is invalid, the request will be rejected. Otherwise, the AP verifies the signature by checking whether the following equation holds or not:If it holds, the AP further computes , and generates a message authentication code . Finally, the AP sends the tuple to MN i.
- Upon receiving the response from the AP, MN i generates a new message authentication code and compares it with . If matches , then MN i believes the AP is legitimate and has established the shared session key . Otherwise, MN i rejects the connection.
- : Finally, the AP securely transmits to the AS. Upon receiving this message, the AS can find the real identity of MN i according to the pseudo-identity included in .
3.2. Cryptanalysis of He et al. PairHand
4. Our Proposed Handover Authentication Scheme
- As shown in Figure 2, the AP registration phase is invoked whenever an AP, say j, registers to the AS. AP j picks an identity , and sends to the AS. Upon receiving the private key request from AP j, the AS first chooses , computes , , and . Then, the AS sends to the AP j via a secure channel. Upon receiving the response message from the AS, the AP j computes and checks the following equation:If it holds, the AP j stores the tuple .
- As shown in Figure 3, the MN registration phase is invoked whenever an MN, say i, registers to the AS with an identity , the AS first checks MN i’s validity. If MN i is valid, the AS chooses , computes and sends the commitment to MN i. Upon receiving the commitment, MN i chooses a pseudonym , blinds with two random elements and , into , computes and sends the challenge to the AS. Then, the AS returns a values to MN i. Finally, MN i verifies the following equation:If it holds, MN i computes , and obtains MN i’s identity-based signing private key and public key , which is actually a blind signature that has been signed by the AS for the unknown pseudonym .Notice that the MN i can choose a family of unlinkable pseudo-identities , and get the corresponding identity-based signing private keys from the AS by choosing and , where . Thus, the MN i can constantly change its pseudo-ID to achieve identity privacy and location privacy in the handover authentication phase.
- : MN i with a tuple of pseudo-identity and private key first chooses and , computes , and . Then, MN i sets message , where is the time-stamp of the MN i. Subsequently, MN i computes , , and sets the signature . At the same time, MN i can compute , and sets the session key . Finally, MN i sends the handover authentication request to the target AP j.
- : Upon receiving the handover authentication request from an MN i, the target AP j checks the time-stamp . If is fresh, the AP computes and , the AP j is able to verify the signature by checking the following equation:If the above equation does not hold, it implies the message may not sent by a valid MN. Hence, the protocol is terminated at this stage. Otherwise, the AP j accepts the message. Finally, the AP j computes the symmetric session key using its own private key .
5. Security and Efficiency Analysis
- MN’s Anonymity and Untraceability: In existing handover authentication schemes using identity-based signature schemes, to guarantee MN’s privacy, the AS chooses a family of pseudo-identities and generates associated private keys for each MN. Undoubtedly, the AS knows the relationship between each MN’s pseudonyms and real identity. More seriously, the AS knows MN’s private keys, this is known as the key escrow problem in identity-based cryptography. In our proposed scheme, each MN can choose a family of pseudonyms and and obtain associated private keys by running Pointcheval and Stern’s blind signature scheme with the AS in the registration phase. Although the handover authentication request messages must include a pseudonym of the roaming MN; however, there is no linkage between these pseudonyms, anyone, even the AS, does not know the MN’s private keys, is unable to identify the MN or to link two sessions initiated by the same MN (i.e., trace the movement routes of the MN). Thus, our proposed handover authentication scheme is escrow-free and achieves MN’s anonymity and untraceability.
- MN’s Key Compromise Security: In the handover authentication phase, the access request sent by MN i to AP j is actually a signature that generated by MN i with its signing private key on the message , which is used to prove to AP j that MN i is the private key holer corresponding to the pseudonym . Here, we use the GG-IBS scheme. One reason for this is its efficiency and simplicity, and another more important reason is that it has been proved to be EUF-ID-CMA secure in the random oracle model under the ECDLA. Even if an adversary gets messages and their corresponding signatures generated by the same MN i, he can not forge a valid signature of MN i, let alone get MN i’s private key. Thus, our proposed scheme can resist MN’s key compromise attack.
- MN’s Forward Secrecy: The session key calculated by MN i is equal to the session key calculated by Ap j. According to the ECCDHA, there is no probabilistic polynomial-time adversary can compute the session key without MN i’s private key or AP j’s private key. Unlike PairHand, where the session key is fixed, the session key in our proposed scheme is random that depends on two random elements and chosen by MN i. Thus, our proposed scheme achieves MN’s forward secrecy.
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Park, S.; Ganz, A.; Ganz, Z. Security protocol for IEEE 802.11 wireless local area network. Mob. Netw. Appl. 1998, 3, 237–246. [Google Scholar] [CrossRef]
- Zekri, D.; Defude, B.; Delot, T. Building, sharing and exploiting spatio-temporal aggregates in vehicular networks. Mob. Inf. Syst. 2014, 10, 259–285. [Google Scholar] [CrossRef]
- Oliveira, L.M.L.; Rodrigues, J.; Elias, A.G.F.; Zarpelao, B.B. Ubiquitous monitoring solution for wireless sensor networks with push notifications and end-to-end connectivity. Mob. Inf. Syst. 2014, 10, 19–35. [Google Scholar] [CrossRef]
- He, D.; Ma, M.; Zhang, Y.; Chen, C.; Bu, J. A strong user authentication scheme with smart cards for wireless communications. Comput. Commun. 2011, 34, 367–374. [Google Scholar] [CrossRef]
- He, D.; Bu, J.; Chan, S.C.; Chen, C.; Yin, M. Privacy-preserving universal authentication protocol for wireless communications. IEEE Trans. Wirel. Commun. 2011, 10, 431–436. [Google Scholar] [CrossRef]
- He, D.; Chen, C.; Chan, S.; Bu, J. Secure and efficient handover authentication based on bilinear pairing functions. IEEE Trans. Wirel. Commun. 2012, 11, 48–53. [Google Scholar] [CrossRef]
- He, D.; Chen, C.; Chan, S.; Bu, J. Analysis and improvement of a secure and efficient handover authentication for wireless networks. IEEE Commun. Lett. 2012, 16, 1270–1273. [Google Scholar] [CrossRef]
- Yeo, S.L.; Yap, W.-S.; Liu, J.K.; Henricksen, M.H. Comments on “Analysis and improvement of a secure and efficient handover authentication based on bilinear pairing functions”. IEEE Commun. Lett. 2013, 17, 1521–1523. [Google Scholar]
- Tsai, J.; Lo, N.; Wu, T. Secure handover authentication protocol based on bilinear pairings. Wirel. Pers. Commun. 2013, 73, 1037–1047. [Google Scholar] [CrossRef]
- Wang, W.; Hu, L. A Secure and efficient handover authentication protocol for wireless networks. Sensors 2014, 14, 11379–11394. [Google Scholar] [CrossRef] [PubMed]
- Li, G.; Jiang, Q.; Wei, F.; Ma, C. A new privacy-aware handover authentication scheme for wireless networks. Wirel. Pers. Commun. 2015, 80, 581–589. [Google Scholar] [CrossRef]
- Chaudhry, S.A.; Farash, M.S.; Naqvi, H.; Islam, S.K.H.; Shon, T. A robust and efficient privacy aware handover authentication scheme for wireless networks. Wirel. Pers. Commun. 2017, 93, 311–335. [Google Scholar] [CrossRef]
- Pointcheval, D.; Stern, J. Provably secure blind signature schemes. In Advances in Cryptology—ASIACRYPT 1996; LNCS 1163; Springer: Berlin/Heidelberg, Germany, 1996; pp. 252–265. [Google Scholar]
- Chatterjee, S.; Kamath, C.; Kumar, V. Galindo-Garcia identity-based signature revisited. In Information Security and Cryptology—ICISC 2012; LNCS 7839; Springer: Berlin/Heidelberg, Germany, 2013; pp. 456–471. [Google Scholar]
- Yasmin, R.; Ritter, E.; Wang, G. Provable security of a pairing-free one-pass authenticated key establishment protocol for wireless sensor networks. Int. J. Inf. Secur. 2014, 13, 453–465. [Google Scholar] [CrossRef]
- Galindo, D.; Garcia, F.D. A Schnorr-like lightweight identity-based signature scheme. In Progress in Cryptology—AFRICACRYPT 2009; LNCS 5880; Springer: Berlin/Heidelberg, Germany, 2009; pp. 135–148. [Google Scholar]
- LaMacchia, B.; Lauter, K.; Mityagin, A. Stronger security of authenticated key exchange. In Provable Security; LNCS 4784; Springer: Berlin/Heidelberg, Germany, 2007; pp. 1–16. [Google Scholar]
- Barr, K.C.; Asanovic, K. Energy-aware lossless data compression. ACM Trans. Comput. Syst. 2006, 24, 250–291. [Google Scholar] [CrossRef]




| Symbol | Description |
|---|---|
| Security parameter | |
| Pick an element x uniformly at random from the set | |
| A cryptographic secure hash function | |
| A cryptographic secure hash function | |
| A cryptographic secure hash function | |
| A cryptographic secure hash function | |
| A cryptographic secure message authentication code function | |
| A cryptographic secure session key derivation function |
| [7] | [9] | [10] | [11] | [12] | Ours | |
| MN Computational Cost | ||||||
| AP Computational Cost | ||||||
| Communication Round | 2 | 2 | 2 | 2 | 2 | 1 |
| Communication Cost | 3872 bits | 1312 bits | 1312 bits | 2080 bits | 1824 bits | 1312 bits |
| Batch Verification | Yes | Yes | Yes | No | No | Yes |
| Group Order | Composite | Prime | Prime | Prime | Prime | Prime |
| MN Anonymity & Untraceability | Weak | Weak | Weak | Weak | Weak | Strong |
| MN Key Compromise Security | No | Yes | Yes | Yes | Yes | Yes |
| MN Forward Secrecy | No | No | No | Yes | Yes | Yes |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, C.; Yuan, Y.; Wu, J. A New Privacy-Preserving Handover Authentication Scheme for Wireless Networks. Sensors 2017, 17, 1446. https://doi.org/10.3390/s17061446
Wang C, Yuan Y, Wu J. A New Privacy-Preserving Handover Authentication Scheme for Wireless Networks. Sensors. 2017; 17(6):1446. https://doi.org/10.3390/s17061446
Chicago/Turabian StyleWang, Changji, Yuan Yuan, and Jiayuan Wu. 2017. "A New Privacy-Preserving Handover Authentication Scheme for Wireless Networks" Sensors 17, no. 6: 1446. https://doi.org/10.3390/s17061446