Bring Your Own Reputation: A Feasible Trust System for Vehicular Ad Hoc Networks
Abstract
:1. Introduction
2. Related Work
2.1. Decentralized Systems
2.2. Centralized Systems
2.3. Shortcomings in Current Proposals
2.4. Comparative Analysis of Schemes
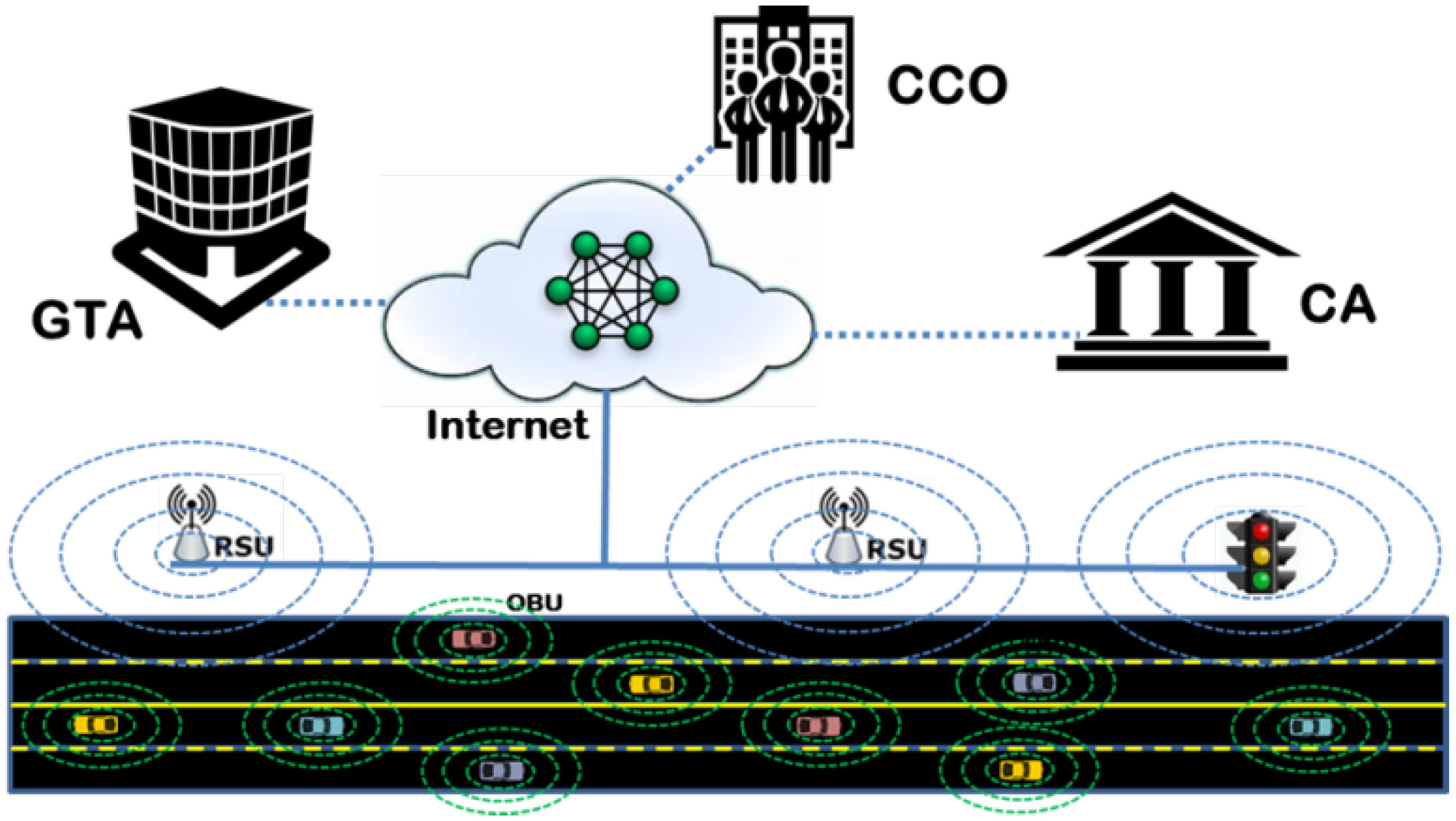
3. Proposed System
3.1. System Assumptions
3.2. Reputation System
- Simple Summation: obtained by adding the number of positive and negative reviews separately. Reputation is the difference between the total number of positives and negatives.
- Average of ratings: consists in calculating the average of all ratings.
- Average weighted by factors: based on the calculation of a weighted average of all ratings, considering factors such as the time of the evaluation, distance, context, role of the node in the network, reliability of nodes, etc.
- Bayesian system: consists in the calculation of the reputation by updating of statistical functions such as binomial beta or multinomial probability density of Dirichlet. The updated value is obtained by the combination of the previous value with the new evaluation.
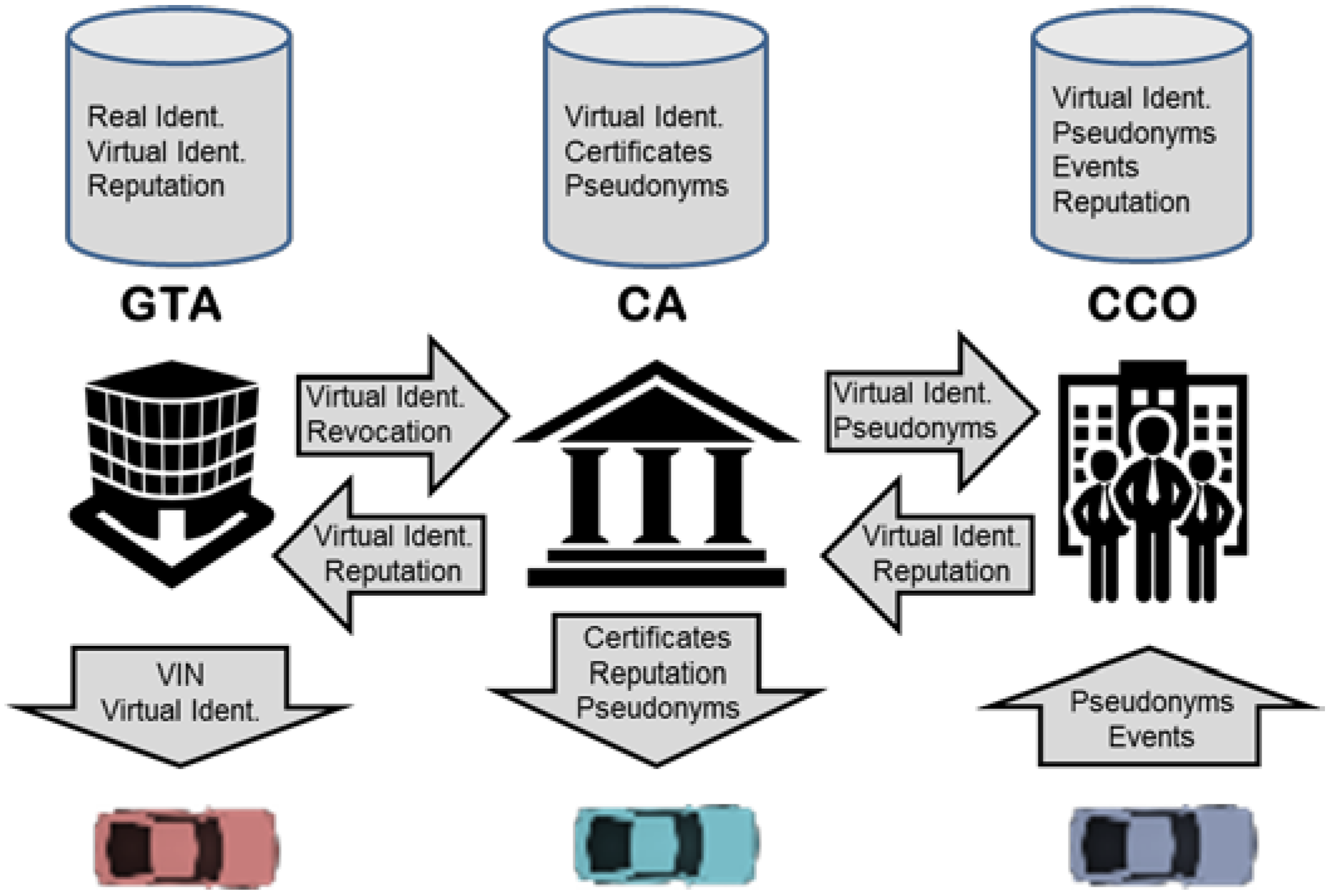
3.3. Roles of the Authorities GTA, CA, and CCO
3.4. Vehicular Decision Mechanism
4. Implementation of a Model
4.1. System Model
- Sybil attack: a single node attempts to create multiple identities or false pseudonyms to gain greater influence for their messages on the network.
- Newcomer attack: in case a new node can easily sign up to join the network, a malicious node can erase its past by registering as a new participant.
- Betrayal attack: before initiating its attack, the node behaves honestly in the network to achieve a reputation of high level.
- Inconsistency attack: the attacker tries to degrade the efficiency of the mechanism, by repeatedly switching its behavior between honest and dishonest.
- Bad-mouthing/Ballot Stuffing attack: nodes can provide intentionally incorrect ratings on other nodes in a positive or negative way, trying to influence their reputation on the network.
- Collusion attack: a group of nodes act cooperatively to create fake messages or influence the reputation of other nodes.
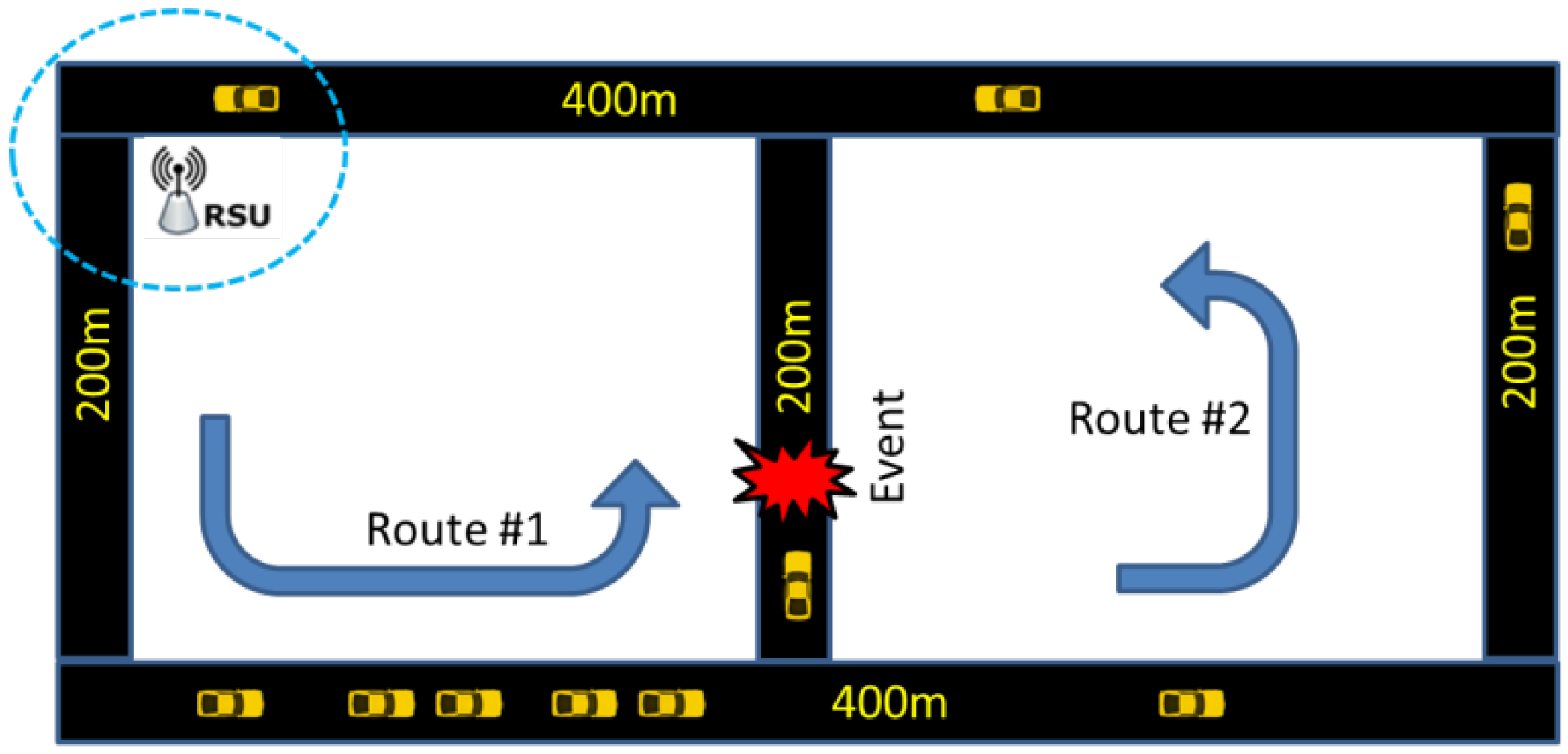
4.2. Description of the Restricted Scenario
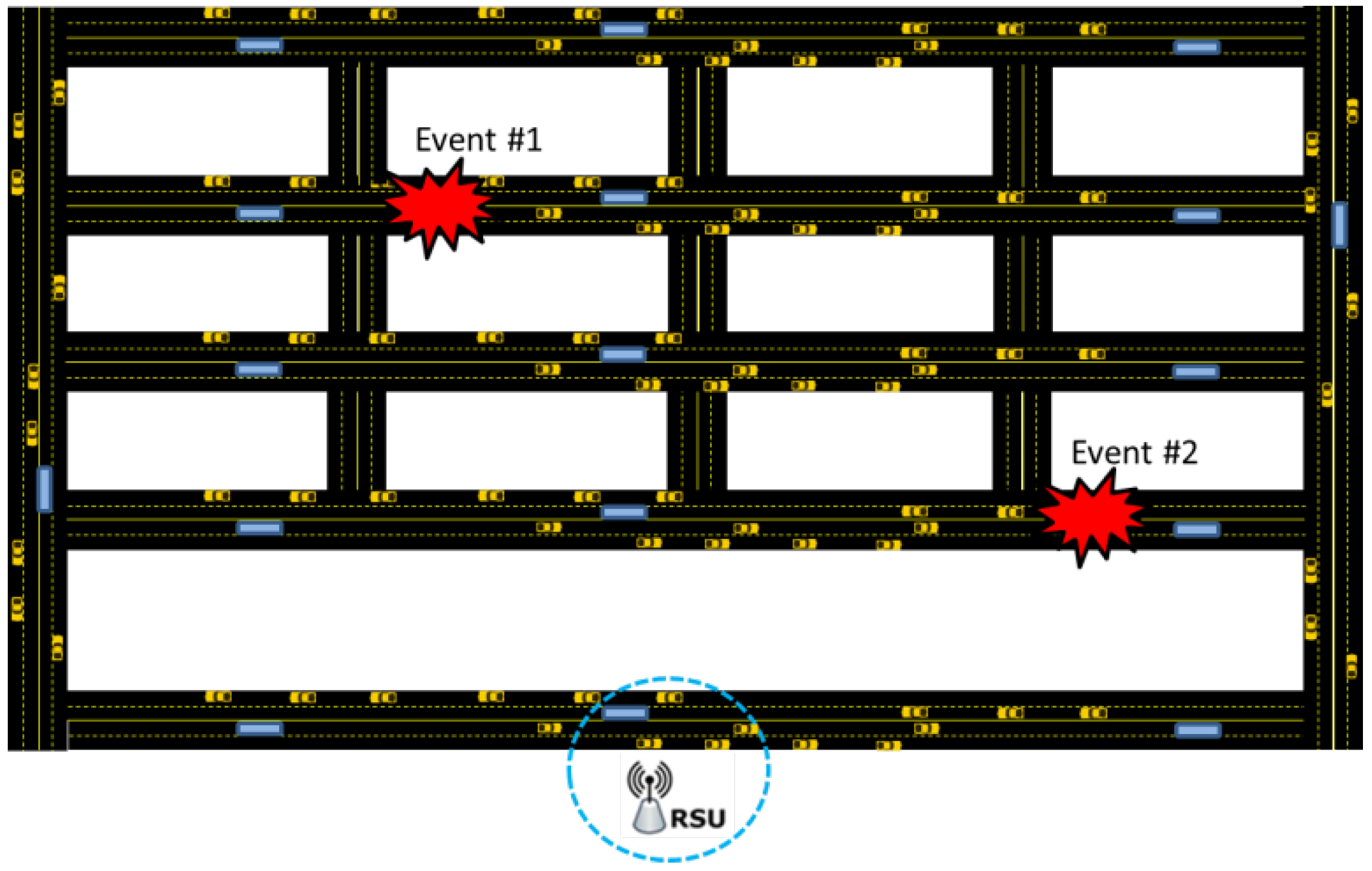
4.3. Description of the Manhattan-Grid Scenario
4.4. Reputation and Decision Mechanism
- Always Negative Decisions: the decision value will always be the lowest.
- Majority Voting: the decision value consists of the average of all recorded events that have been reported by other vehicles during the period of decision.
- Highest Reputation Level: the decision corresponds to the event reported by the vehicle with the highest reputation. If there is more than one vehicle with the highest reputation, the mechanism considers the average of them.
- Weighted Voting by Reputation: the decision value is calculated as the weighted average of the reputation and the event reported by each node during the period of decision.
- Always Positive decisions: the decision value will always be the highest.
4.5. Simulation Environment
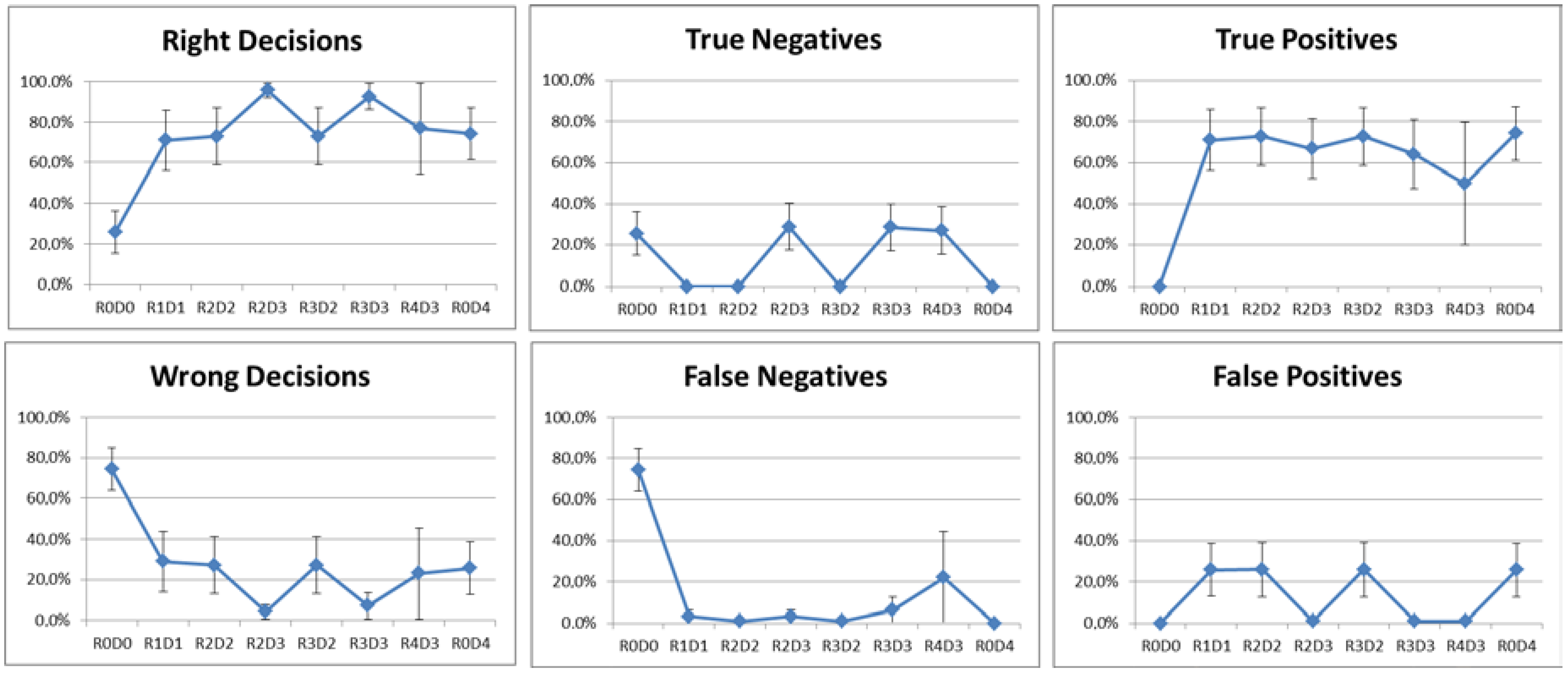
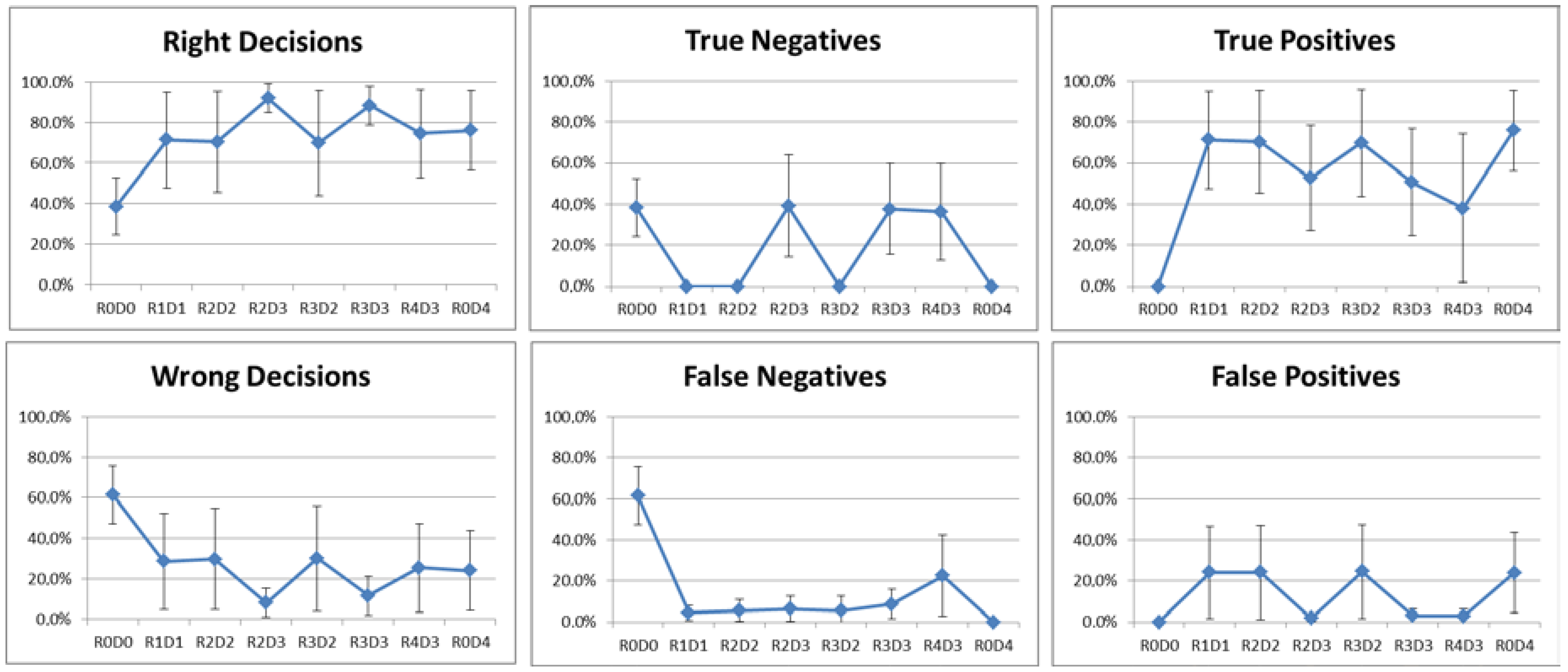
4.6. Metrics Definition
5. Performance Analysis
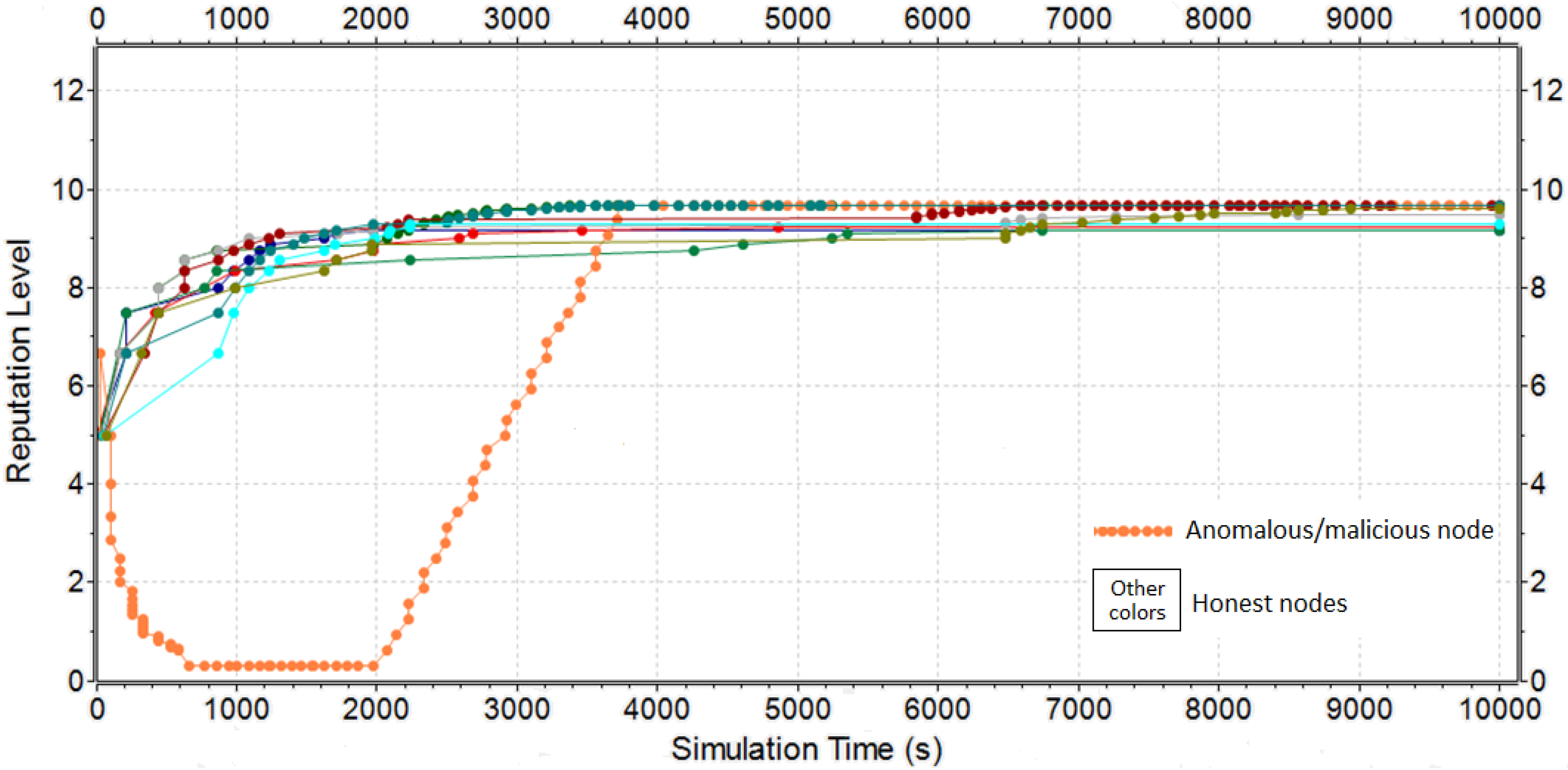
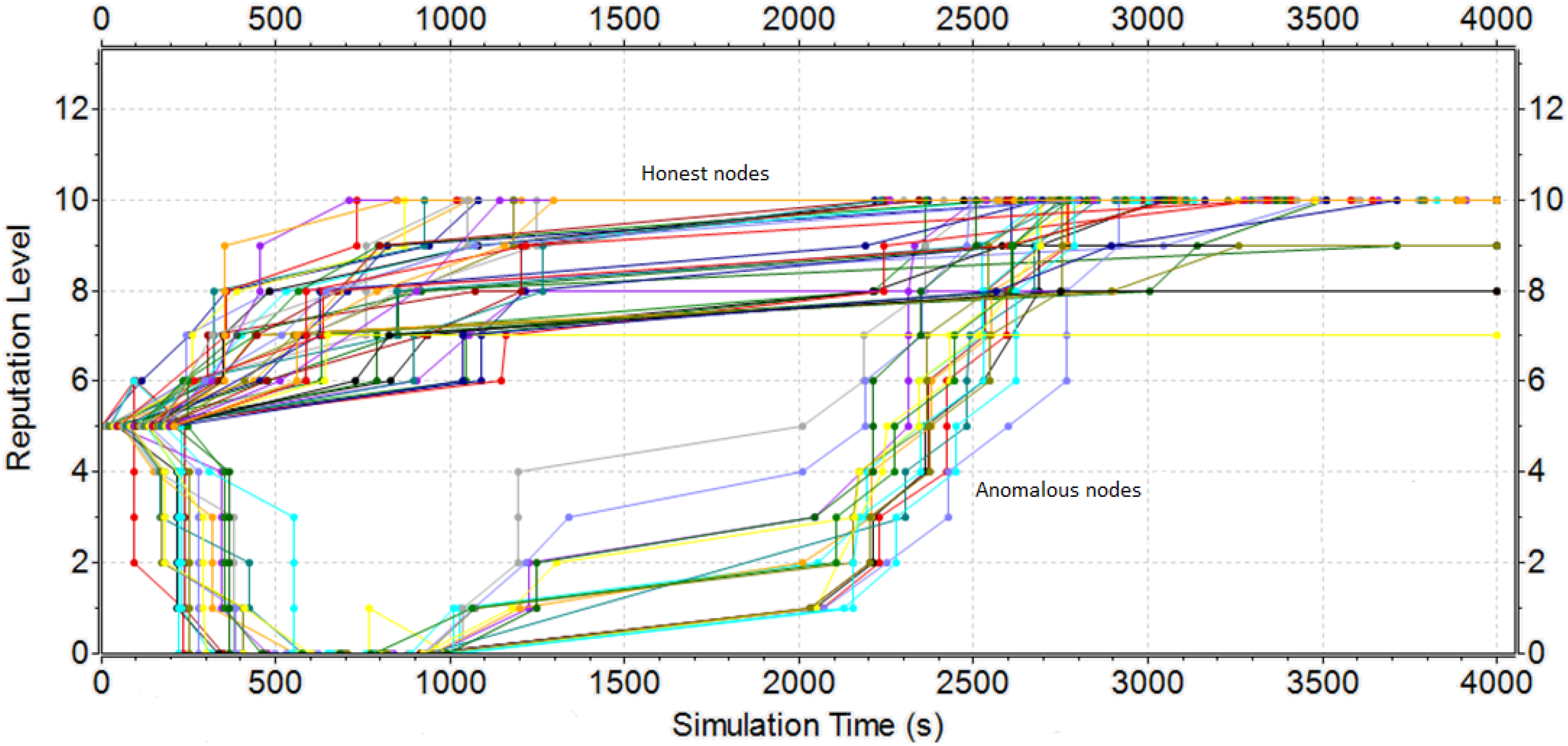
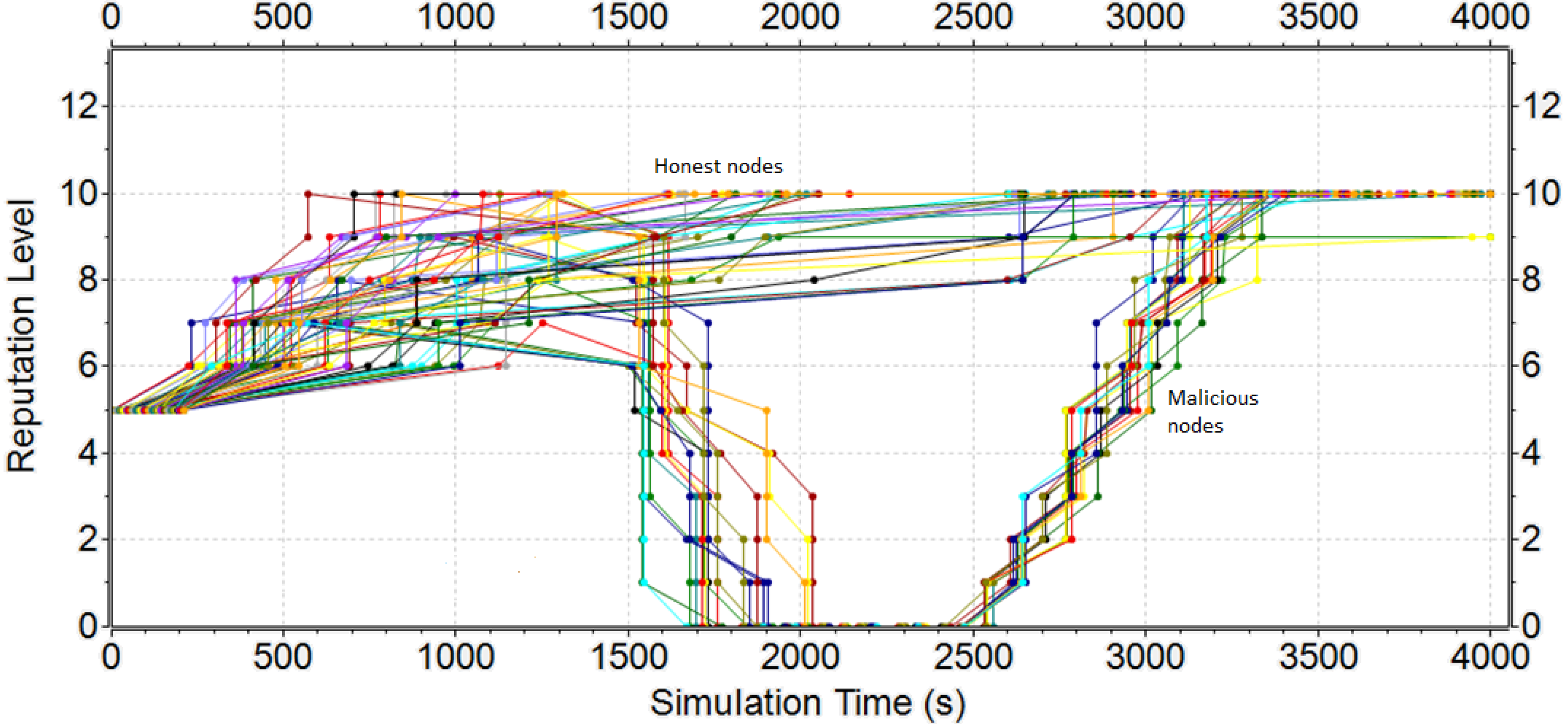
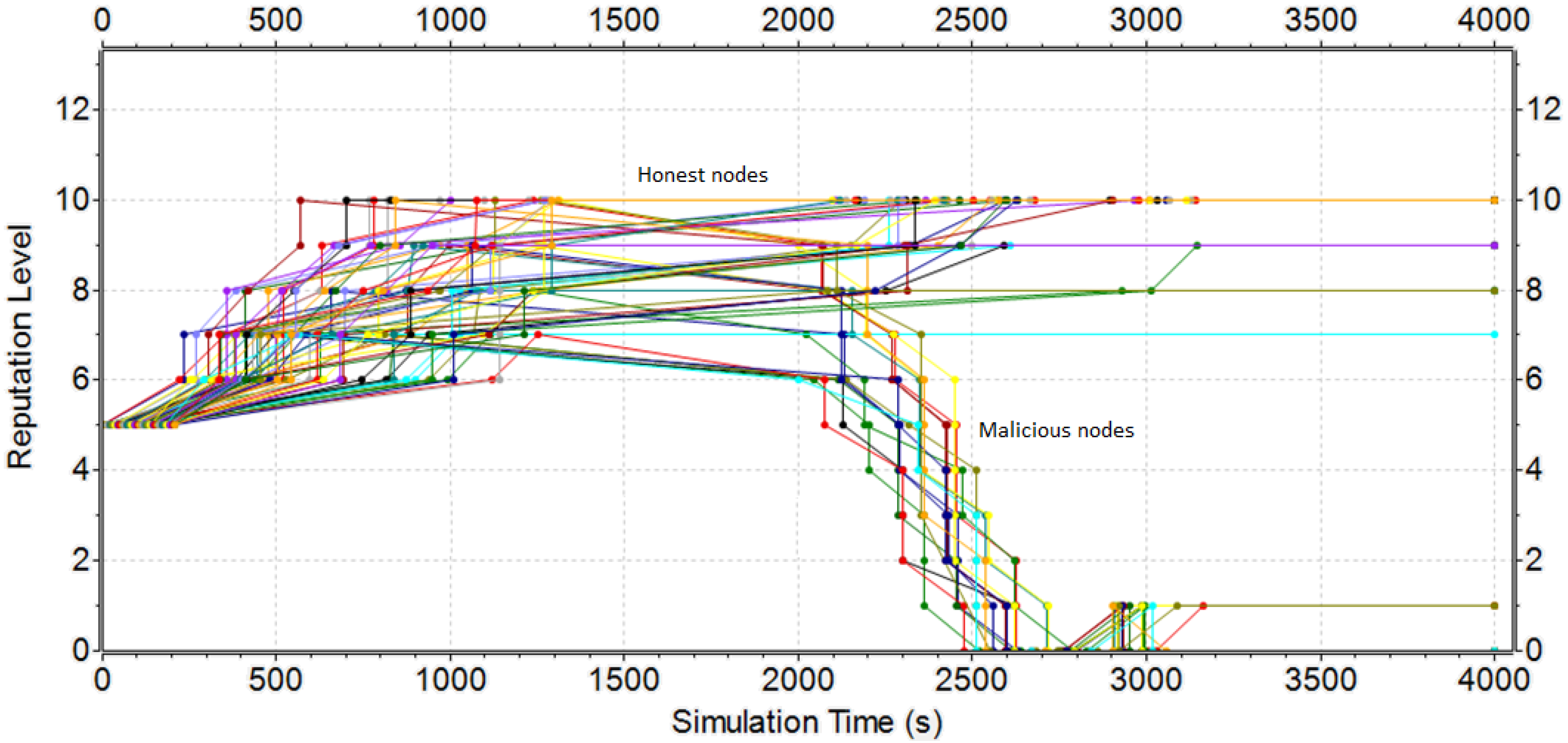
5.1. Results of the Restricted Scenario
- R0D0: without reputation and always negative decisions;
- R1D1: without reputation and majority voting;
- R2D2: Simple Summation and highest reputation level;
- R2D3: Simple Summation and weighted voting;
- R3D2: Bayesian Inference with longevity and highest reputation level;
- R3D3: Bayesian Inference with longevity and weighted voting;
- R4D3: Bayesian Inference without longevity and weighted voting;
- R0D4: without reputation and always positive decisions.
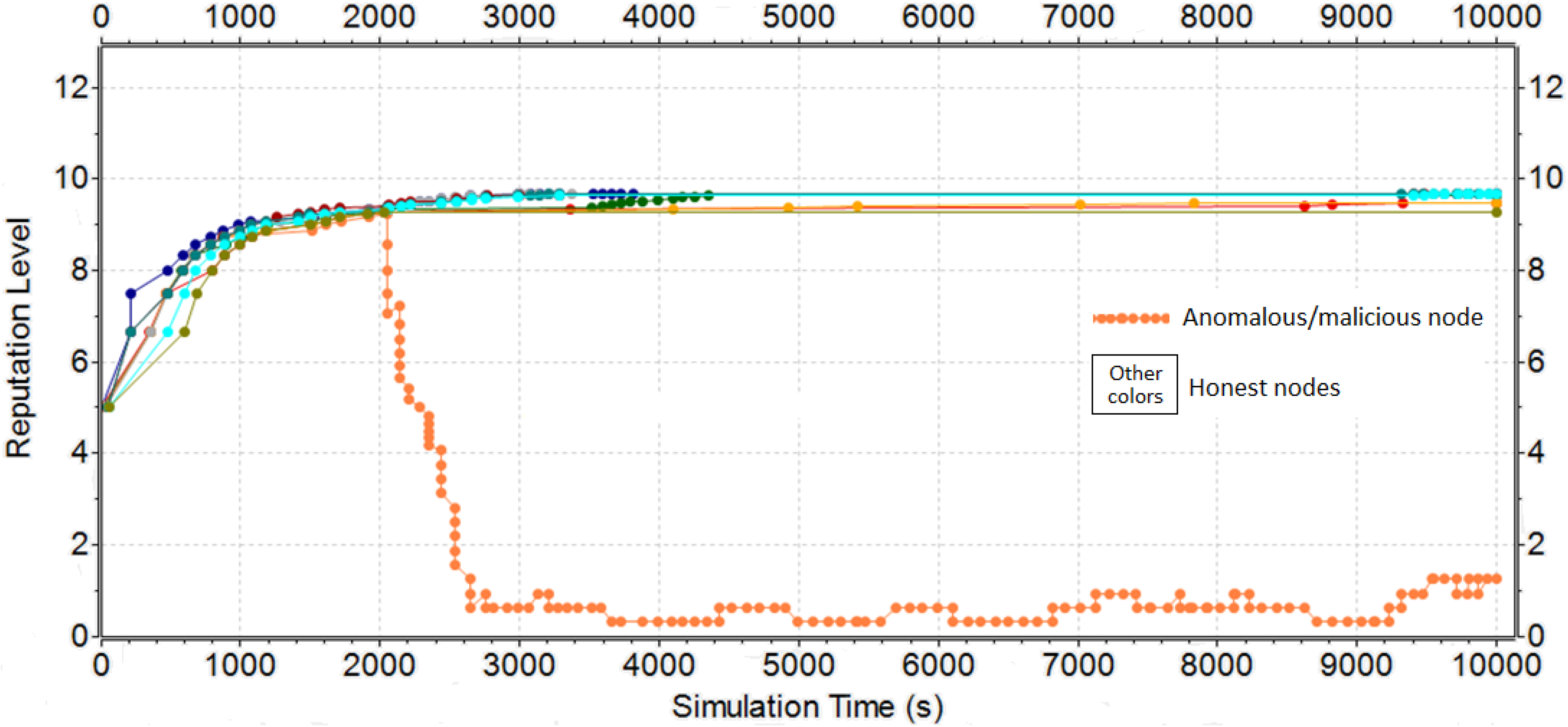
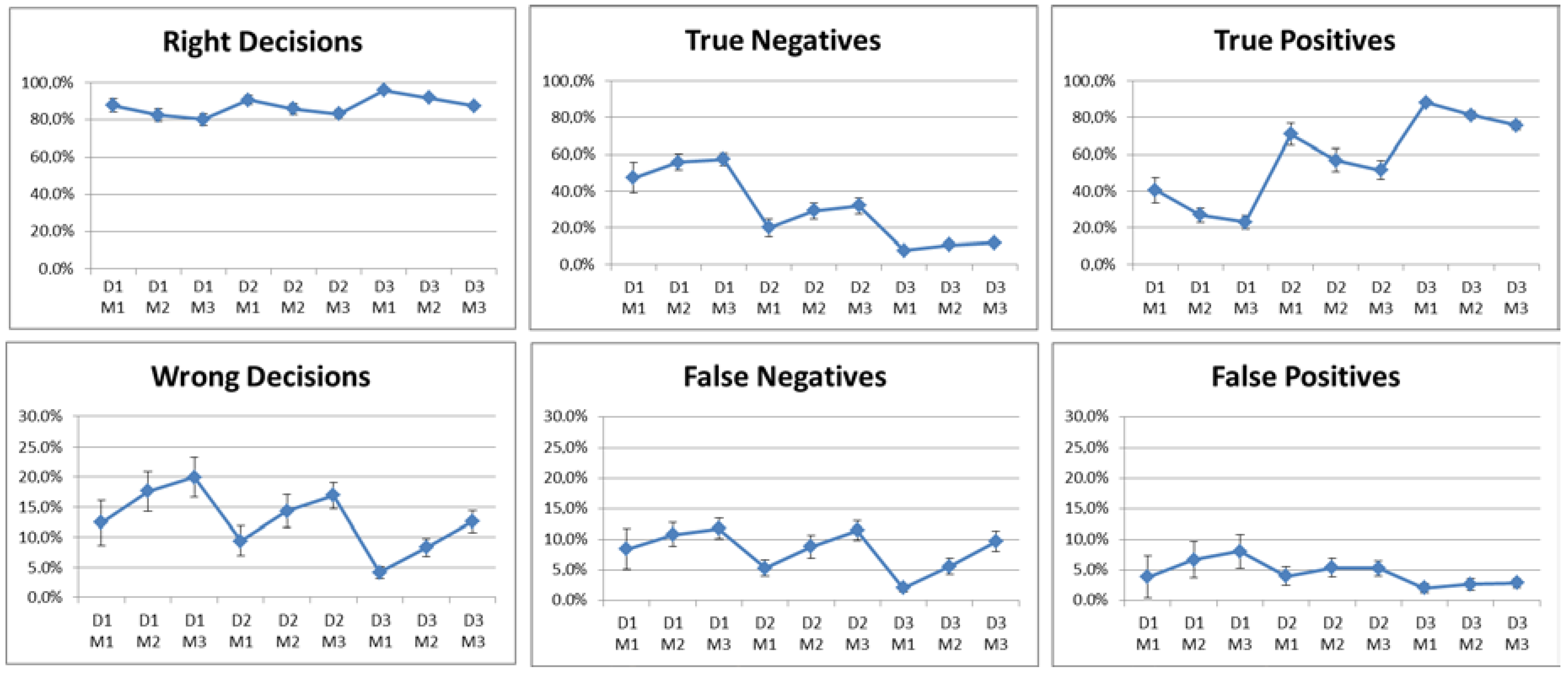
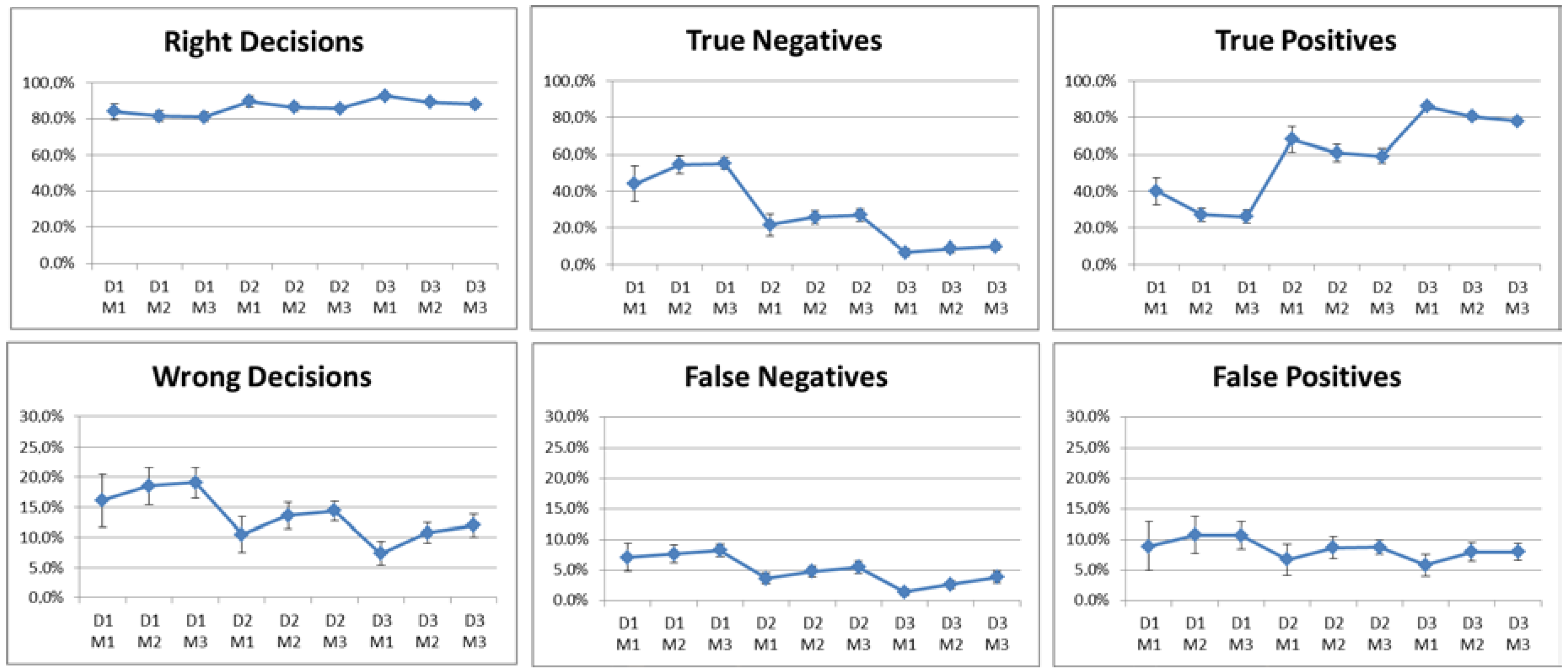
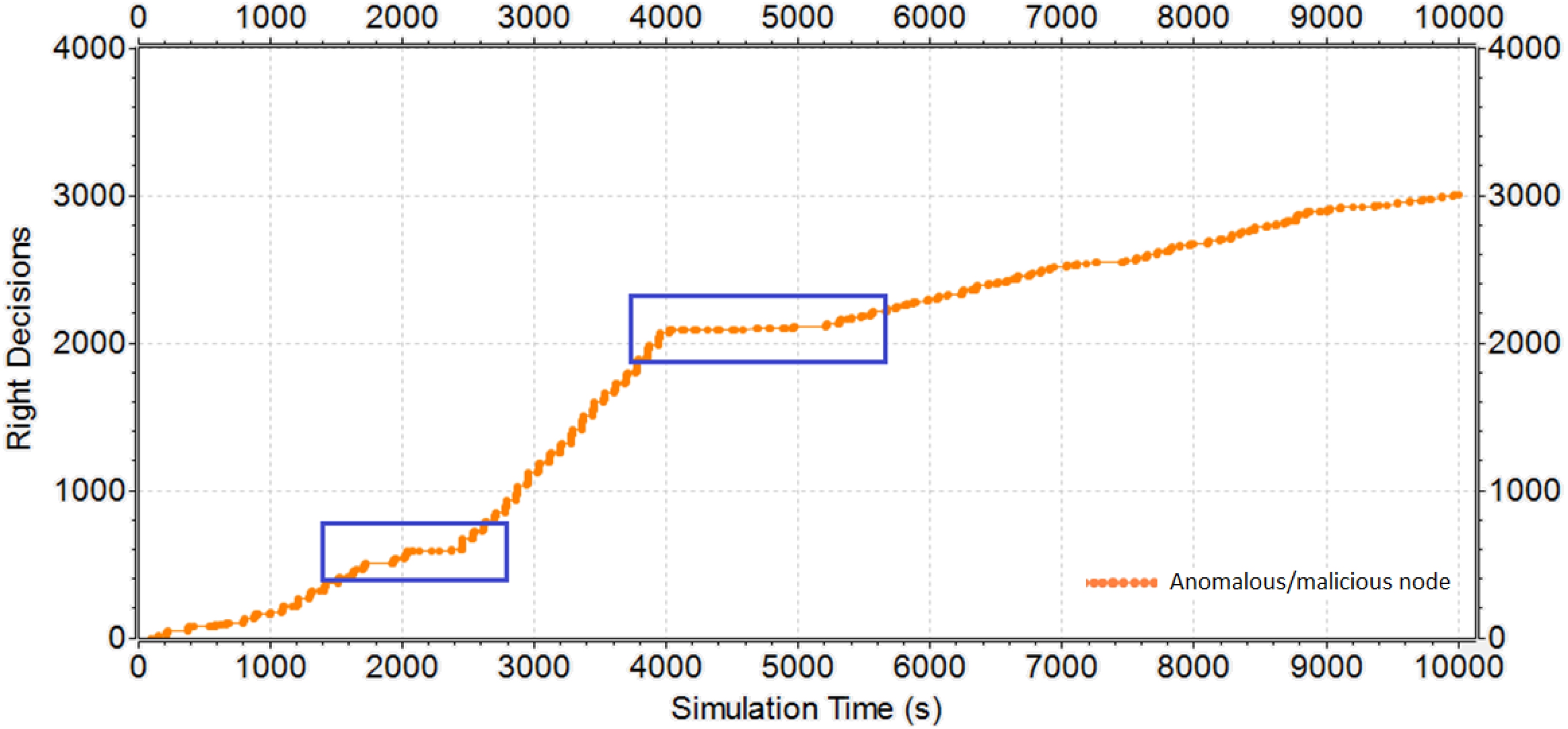
5.2. Results of the Manhattan-Grid Scenario
- D1M1: low density and 10% of malicious nodes;
- D1M2: low density and 30% of malicious nodes;
- D1M3: low density and 50% of malicious nodes;
- D2M1: medium density and 10% of malicious nodes;
- D2M2: medium density and 30% of malicious nodes;
- D2M3: medium density and 50% of malicious nodes;
- D3M1: high density and 10% of malicious nodes;
- D3M2: high density and 30% of malicious nodes;
- D3M3: high density and 50% of malicious nodes.
5.3. Response of the Reputation Mechanisms
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Hartenstein, H.; Laberteaux, K.P. A Tutorial Survey on Vehicular Ad Hoc Networks. IEEE Commun. Mag. 2008, 46, 164–171. [Google Scholar] [CrossRef]
- Jøsang, A. Trust and Reputation Systems. In Foundations of Security Analysis and Design IV, FOSAD 2006/2007 Tutorial Lectures, 1st ed.; Aldini, A., Gorrieri, R., Eds.; Springer: Bertinoro, Italy, 2007; Volume 4677, pp. 209–245. ISBN 978-3-642-23082-0. [Google Scholar]
- Raya, M. Data-Centric Trust in Ephemeral Networks. Ph.D. Thesis, École Polytechnique Fédéral de Lausanne, Lausanne, Switzerland, June 2009. [Google Scholar]
- Dötzer, F. Security Concepts for Robust and Highly Mobile Ad-Hoc Networks. Ph.D. Thesis, Institut für Informatik der Technischen Universität München, München, Germany, March 2008. [Google Scholar]
- Hendrikx, F.; Bubendorfer, K.; Chard, R. Reputation Systems: A Survey and Taxonomy. J. Parallel Distrib. Comp. 2015, 75, 184–197. [Google Scholar] [CrossRef]
- Raya, M.; Papadimitratos, P.; Gligor, V.; Hubaux, J. On Data-Centric Trust Establishment in Ephemeral Ad Hoc Networks. In Proceedings of the 27th Conference on Computer Communications, Phoenix, AZ, USA, 13–18 April 2008. [Google Scholar]
- Ding, Q.; Jiang, M.; Li, X.; Zhou, X. Reputation Management in Vehicular Ad Hoc Networks. In Proceedings of the International Conference on Multimedia Technology (ICMT), Ningbo, China, 29–31 October 2010; pp. 1–5. [Google Scholar]
- Hartenstein, H.; Laberteaux, K.P. Past and Ongoing VANET Activities. In VANET Vehicular Applications and Internetworking Technologies, 1st ed.; Hartenstein, H., Laberteaux, K., Eds.; Wiley: Chichester, UK, 2010; Volume 3, pp. 1–4. ISBN 978-0-470-74056-9. [Google Scholar]
- Park, S.; Aslam, B.; Zou, C. Long-term Reputation System for Vehicular Networking based on Vehicle’s Daily Commute Routine. In Proceedings of the 8th Annual IEEE Consumer Communications and Networking Conference, Las Vegas, NV, USA, 12–15 January 2018; pp. 426–441. [Google Scholar]
- Li, Q.; Malip, A.; Martin, K.M.; Zhang, J. A Reputation-Based Announcement Scheme for VANETs. IEEE Trans. Veh. Technol. 2012, 61, 4095–4108. [Google Scholar] [Green Version]
- Liao, C.; Chang, J.; Lee, I.; Venkatasubramanian, K. A Trust Model for Vehicular Network-Based Incident Reports. In Proceedings of the 5th IEEE International Symposium on Wireless Vehicular Communications WiVeC, Dresden, Germany, 2–3 June 2013; pp. 1–5. [Google Scholar]
- Huynh, T.D.; Jennings, N.R.; Shadbolt, N.R. Certified Reputation: How an Agent Can Trust a Stranger. In Proceedings of the Fifth International Joint Conference on Autonomous Agents and Multiagent Systems, Hakodate, Japan, 8–12 May 2006; pp. 1217–1224. [Google Scholar]
- Ostermaier, B.; Dötzer, F.; Strassberger, M. Enhancing the Security of Local Danger Warnings in VANETs—A Simulative Analysis of Voting Schemes. In Proceedings of the Second International Conference on Availability, Reliability and Security, Vienna, Austria, 10–13 April 2007; pp. 422–431. [Google Scholar]
- Lo, N.W.; Tsai, H.C. A Reputation System for Traffic Safety Event on Vehicular Ad Hoc Networks. EURASIP J. Wirel. Commun. Netw. 2009, 2009. [Google Scholar] [CrossRef]
- De Paula, W.P.; Oliveira, S.; Nogueira, J.M. Um Mecanismo de Reputação para Redes Veiculares Tolerantes a Atrasos e Desconexões. In Proceedings of the 28th Brazilian Symposium on Computer Networks and Distributed Systems (SBRC), Gramado, Brazil, 22 December 2009; pp. 1–8. [Google Scholar]
- Huang, Z. On Reputation and Data-Centric Misbehavior Detection Mechanisms for VANET. Master’s Thesis, University of Ottawa, Ottawa, ON, Canada, 2011. [Google Scholar]
- Marmol, F.; Perez, G. TRIP, a trust and reputation infrastructure-based proposal for vehicular ad hoc networks. J. Netw. Comp. Appl. 2012, 35, 934–941. [Google Scholar] [CrossRef]
- Jalali, M.; Aghaee, N. A Fuzzy Reputation System in Vehicular Ad hoc Networks. In Proceedings of the 2nd International Conference on Ambient Systems, Networks and Technologies (ANT-2011)/the 8th International Conference on Mobile Web Information Systems (MobiWIS 2011), Niagara Falls, ON, Canada, 19–21 September 2011; pp. 951–956. [Google Scholar]
- Fernandes, C.P.; Simas, I.; Wangham, M. Um Sistema de Reputação Descentralizado para Avaliar a Confiança dos Nós em Redes Veiculares. In Proceedings of the 13th Brazilian Symposium on Information and Computational Systems Security (SBSeg), Manaus, Brazil, 30 August 2013; pp. 1–8. [Google Scholar]
- Yang, N.A. Similarity based Trust and Reputation Management Framework for VANETs. Int. J. Fut. Gen. Commun. Netw. 2013, 6, 25–34. [Google Scholar]
- Marti, S.; Garcia-Molina, H. Identity Crisis: Anonymity vs. Reputation in P2P Systems. In Proceedings of the Third International Conference on Peer-to-Peer Computing, Linkoping, Sweden, 1–3 September 2003; pp. 134–141. [Google Scholar]
- Seigneur, J.M.; Jensen, C.D. Trading Privacy for Trust. In Proceedings of the Second International Conference iTrust, Oxford, UK, 29 March–1 April 2004; pp. 93–107. [Google Scholar]
- Yao, Y.; Ruohomaa, S.; Xu, F. Addressing Common Vulnerabilities of Reputation Systems for Electronic Commerce. J. Theor. Appl. Electron. Commer. Res. 2012, 7, 1–20. [Google Scholar] [CrossRef]
- Dingledine, R.; Mathewson, N.; Syverson, P. Reputation in P2P Anonymity Systems. In Proceedings of the Workshop on Economics of Peer-to-Peer Systems, Berkeley, CA, USA, 5–6 June 2003. [Google Scholar]
- Wang, Y.; Vassileva, J. Bayesian Network-Based Trust Model in Peer-to-Peer Networks. In Proceedings of the Second International Workshop Peers and Peer-to-Peer Computing, Melbourne, Australia, 14 July 2003; pp. 23–34. [Google Scholar]
- De Fuentes, J.M.; Gonzalez-Manzano, L.; Gonzalez-Tablas, A.I.; Blasco, J. Security Models in Vehicular Ad Hoc Networks: A Survey. IETE Tech. Rev. 2013, 31, 47–64. [Google Scholar] [CrossRef] [Green Version]
- Picone, M.; Busanelli, S.; Amoretti, M.; Zanichelli, F.; Ferrari, G. Standardization History and Open Issues. In Advanced Technologies for Intelligent Transportation Systems; Springer International Publishing: Basel, Switzerland, 2015; pp. 1–19. [Google Scholar]
- Papadimitratos, P.; Buttyan, L.; Holczer, T.; Schoch, E.; Freudiger, J.; Raya, M.; Zhendong, M.; Kargl, F.; Kung, A.; Hubaux, J.P. Secure Vehicular Communication Systems: Design and Architecture. IEEE Commun. Mag. 2008, 46, 100–109. [Google Scholar] [CrossRef]
- Young, C.P.; Chang, B.R.; Lin, J.J.; Fang, R.Y. Cooperative Colision Warning Based Highway Vehicle Accident Reconstruction. In Proceedings of the Eighth International Conference on Intelligent Systems Design and Applications, Kaohsiung, Taiwan, 26–28 November 2008; pp. 561–565. [Google Scholar]
- Zhang, J. A Survey on Trust Management for VANETs. In Proceedings of the 2011 IEEE International Conference on Advanced Information Networking and Applications, Singapore, 22–25 March 2011; pp. 105–112. [Google Scholar]
- Jøsang, A.; Ismail, R. The Beta Reputation System. In Proceedings of the 15th Bled Electronic Commerce Conference, Bled, Slovenia, 17–19 June 2002. [Google Scholar]




| Author | Administration | Reputation Mechanism | Privacy | Robustness | Network Impact | Vehicular Decision |
|---|---|---|---|---|---|---|
| Ostermaier et al. (2007) | Decentralized | Not Addressed | Not Addressed | Not Addressed | Not Addressed | Voting |
| Raya et al. (2008) | Decentralized | Dempster-Shafer | Pseudonym | Not Addressed | Not Addressed | Data Centered |
| Dötzer (2008) | Decentralized | Summation | Fixed Pseudonym | Not Addressed | Not Addressed | Voting |
| Lo et al. (2009) | Decentralized | Summation | Not Addressed | Not Addressed | Not Addressed | Confidence Threshold |
| De Paula (2010) | Decentralized | Discrete | Fixed Identity | Partially Addressed | Addressed | Voting |
| Ding et al. (2010) | Decentralized | Fuzzy | Fixed Identity | Not Addressed | Not Addressed | Fuzzy |
| Huang (2011) | Decentralized | Not Addressed | Pseudonym | Partially Addressed | Not Addressed | Data Centered |
| Marmol et al. (2011) | Decentralized | Summation | Not Addressed | Partially Addressed | Not Addressed | Confidence Threshold |
| Jalali (2011) | Decentralized | Fuzzy | Not Addressed | Not Addressed | Not Addressed | Confidence Threshold |
| Fernandes (2013) | Decentralized | Bayesian Beta | Fixed Identity | Not Addressed | Addressed | Voting |
| Yang (2013) | Decentralized | SummationSimilarity | Fixed Identity | Not Addressed | Not Addressed | Confidence Threshold |
| Park et al. (2011) | Centralized | Summation | Fixed Identity | Partially Addressed | Not Addressed | Not Addressed |
| Li et al. (2012) | Centralized | Summation | Pseudonym | Addressed | Addressed | Reputation Level |
| Liao et al. (2013) | Centralized | Probabilistic Bayesian | Fixed Identity | Not Addressed | Not Addressed | Confidence Threshold |
| Mühlbauer (2018) | Centralized | Summation or Probabilistic | Pseudonym | Addressed | Addressed | High Reputation or Voting |
| Factor/Level | 0 | 1 | 2 | 3 | 4 |
|---|---|---|---|---|---|
| Reputation Mechanism | Without Reputation | Without Reputation | Simple Summation | Bayesian Inference with Longevity | Bayesian Inference without Longevity |
| Decision Mechanism | Always Negative Decisions | Majority Voting | Highest Reputation Level | Weighted Voting by Reputation | Always Positive Decisions |
| Attack Types | ------ | Newcomer | Betrayal | Inconsistency | ------ |
| Factor/Level | 1 | 2 | 3 |
|---|---|---|---|
| Malicious Nodes | 10% | 30% | 50% |
| Vehicular Density | 20 vehicles | 60 vehicles | 100 vehicles |
| Attack Types | Newcomer | Betrayal | Inconsistency |
| Parameter | Value |
|---|---|
| Vehicle Size—Cars | 5 m |
| Vehicle Size—Bus, Trucks | 10 m |
| Minimum Distance Between Vehicles | 2 m |
| Maximum Acceleration | 3 m/s2 |
| Maximum Deceleration | 6 m/s2 |
| Velocity of Vehicles | 12 m/s |
| Distribution Variation of Velocity | Normal |
| Sumo Speed Factor | 1 |
| Sumo Speed Deviation | 0.5 |
| Entry Probability of Cars | 90% |
| Entry Probability of Bus, Trucks | 10% |
| Results | Event Occurrence | ||
|---|---|---|---|
| Absence | Presence | ||
| Decision | Negative | True Negative (TN) | False Negative (FN) |
| Positive | False Positive (FP) | True Positive (TP) | |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Mühlbauer, R.; Kleinschmidt, J.H. Bring Your Own Reputation: A Feasible Trust System for Vehicular Ad Hoc Networks. J. Sens. Actuator Netw. 2018, 7, 37. https://doi.org/10.3390/jsan7030037
Mühlbauer R, Kleinschmidt JH. Bring Your Own Reputation: A Feasible Trust System for Vehicular Ad Hoc Networks. Journal of Sensor and Actuator Networks. 2018; 7(3):37. https://doi.org/10.3390/jsan7030037
Chicago/Turabian StyleMühlbauer, Ricardo, and João Henrique Kleinschmidt. 2018. "Bring Your Own Reputation: A Feasible Trust System for Vehicular Ad Hoc Networks" Journal of Sensor and Actuator Networks 7, no. 3: 37. https://doi.org/10.3390/jsan7030037




