Beyond the Interconnections: Split Manufacturing in RF Designs
Abstract
:1. Introduction
2. Split Manufacturing in the Digital Domain
3. RF Design Flow
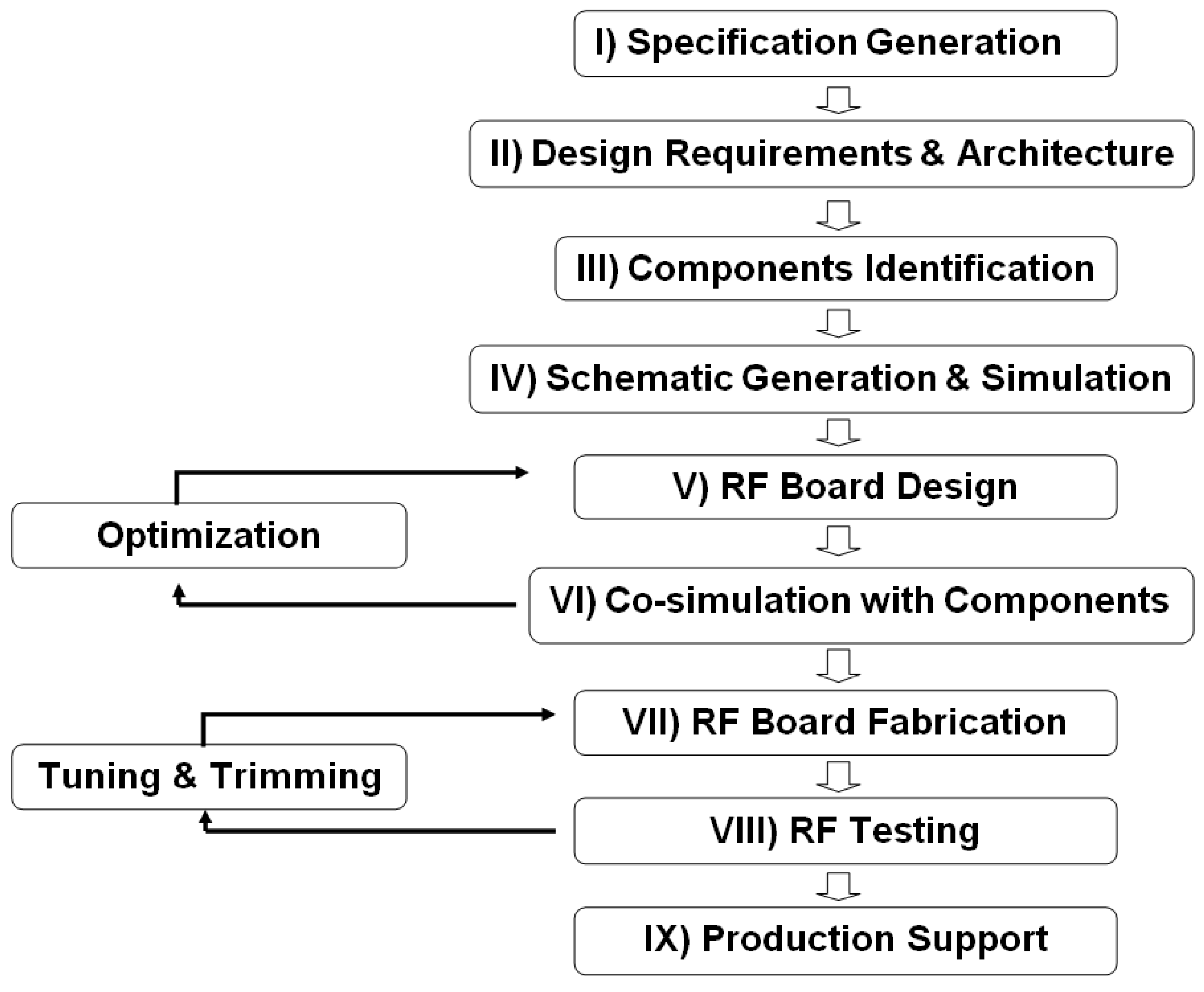
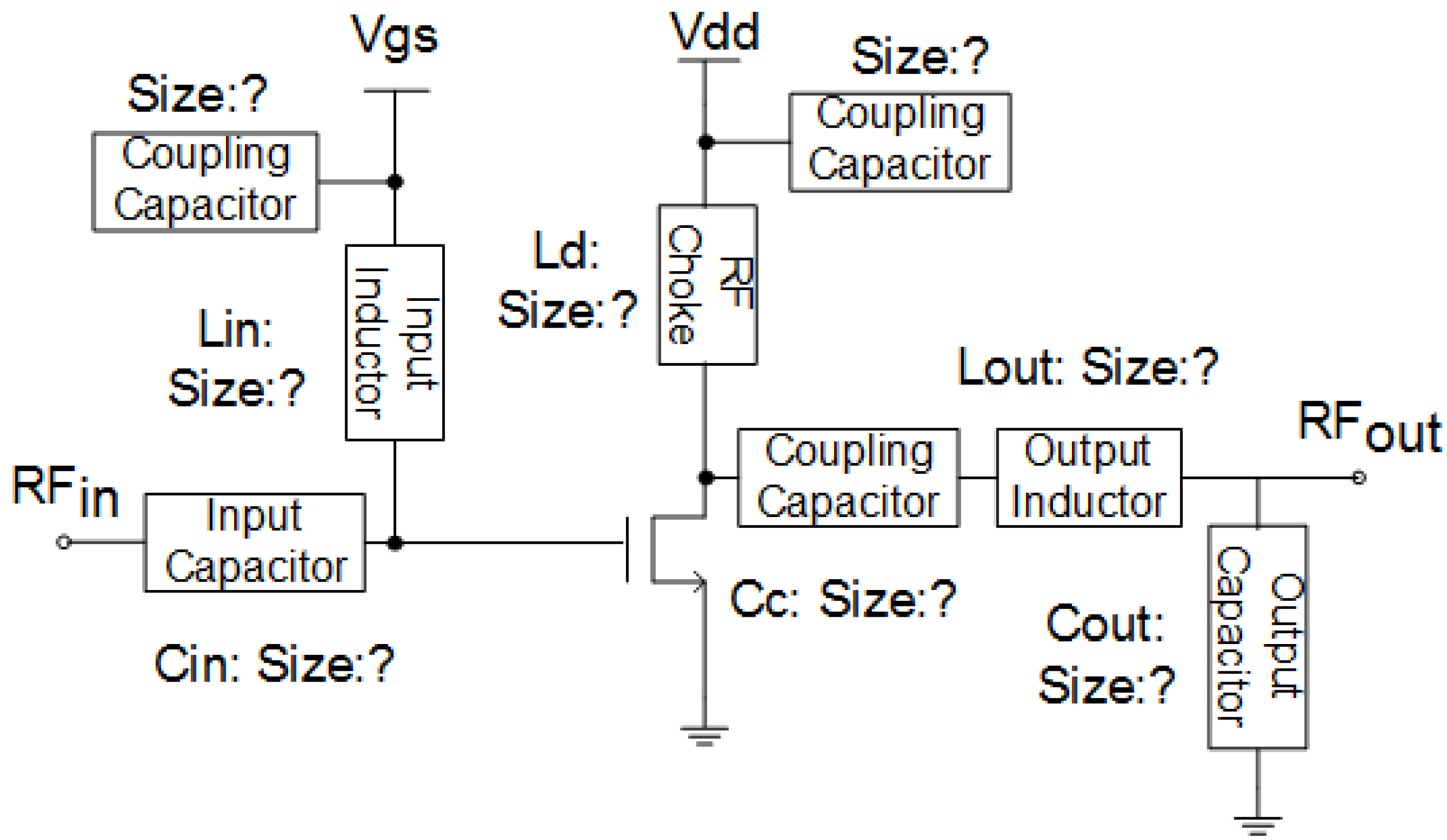
3.1. RF Design Procedures
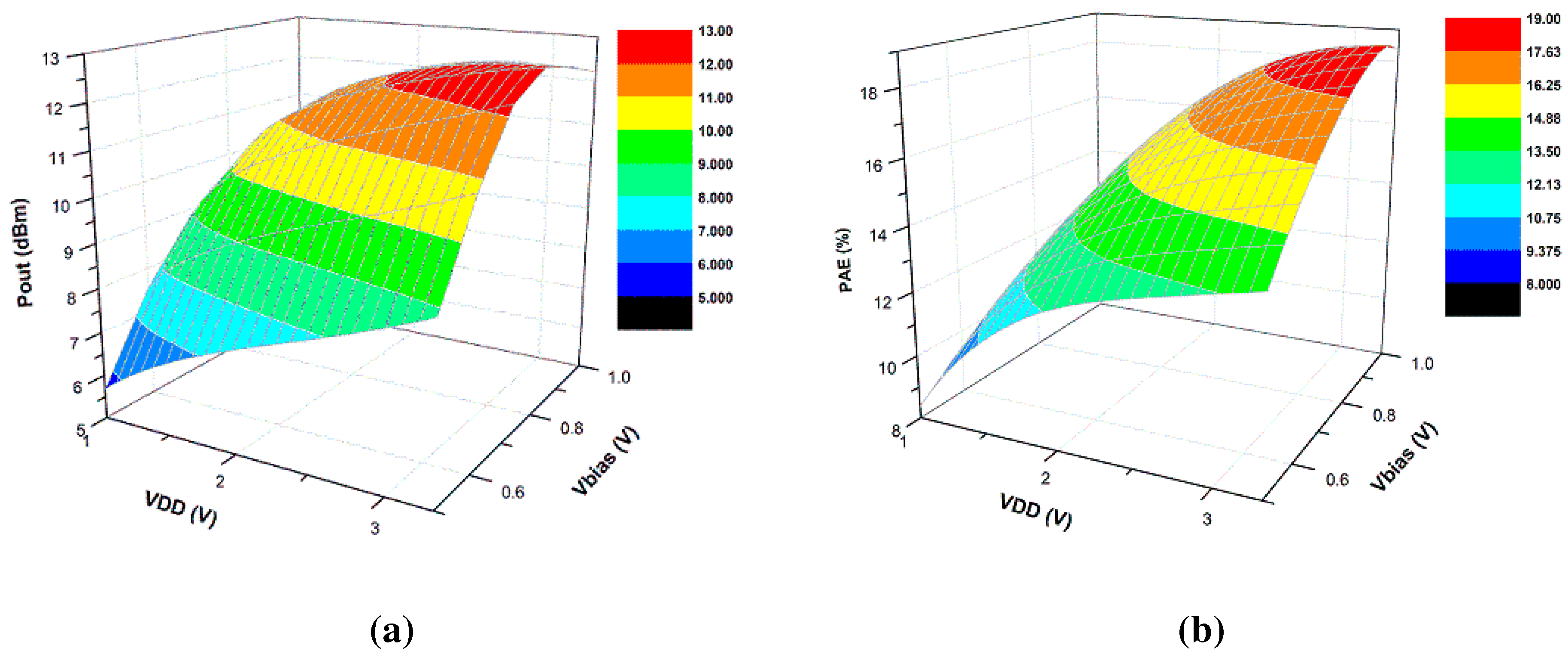
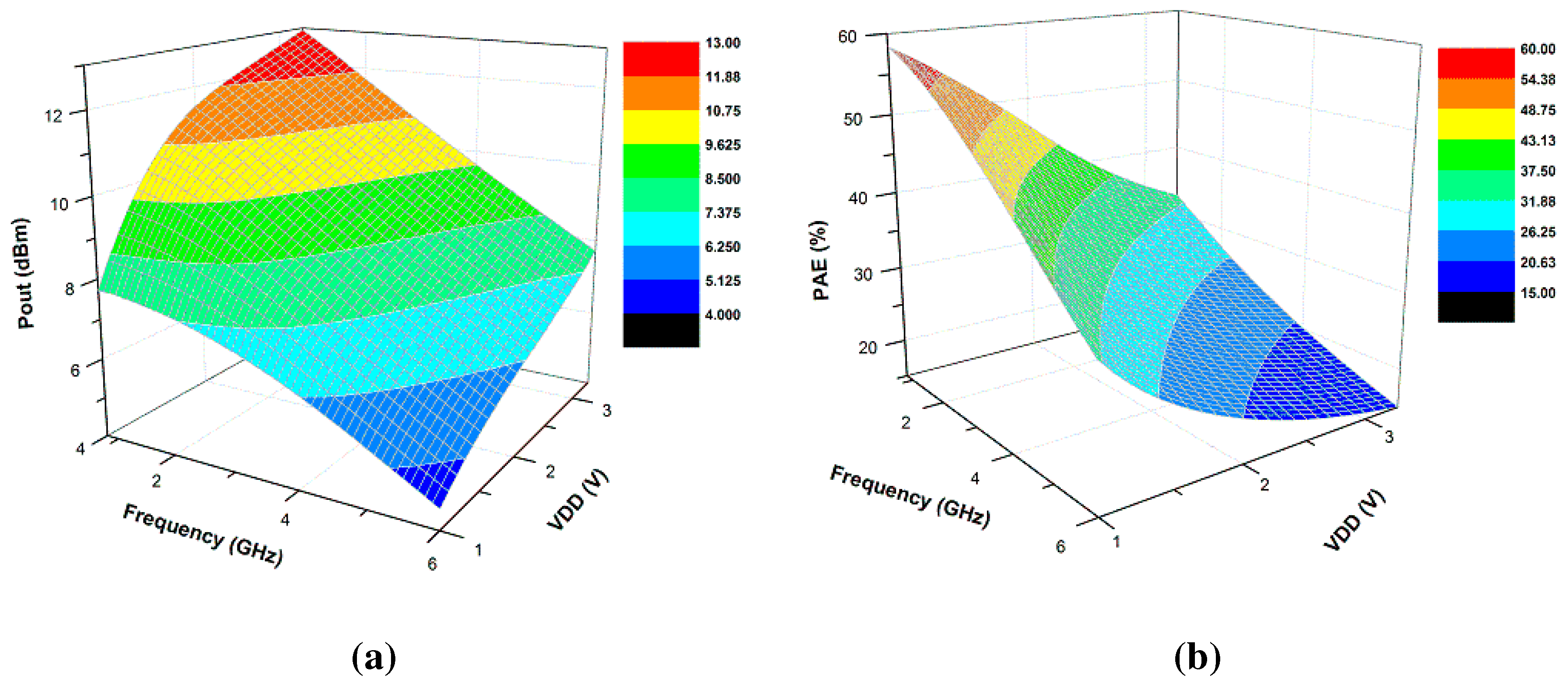
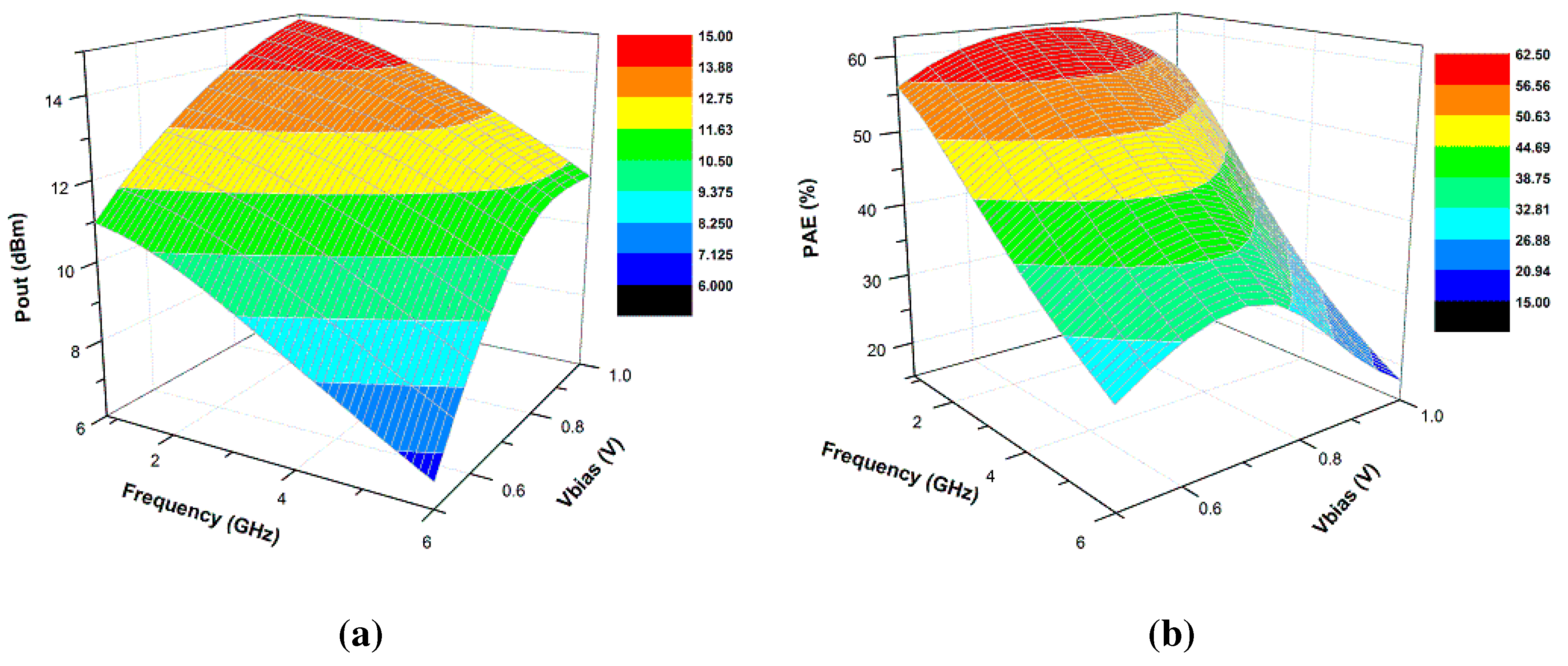
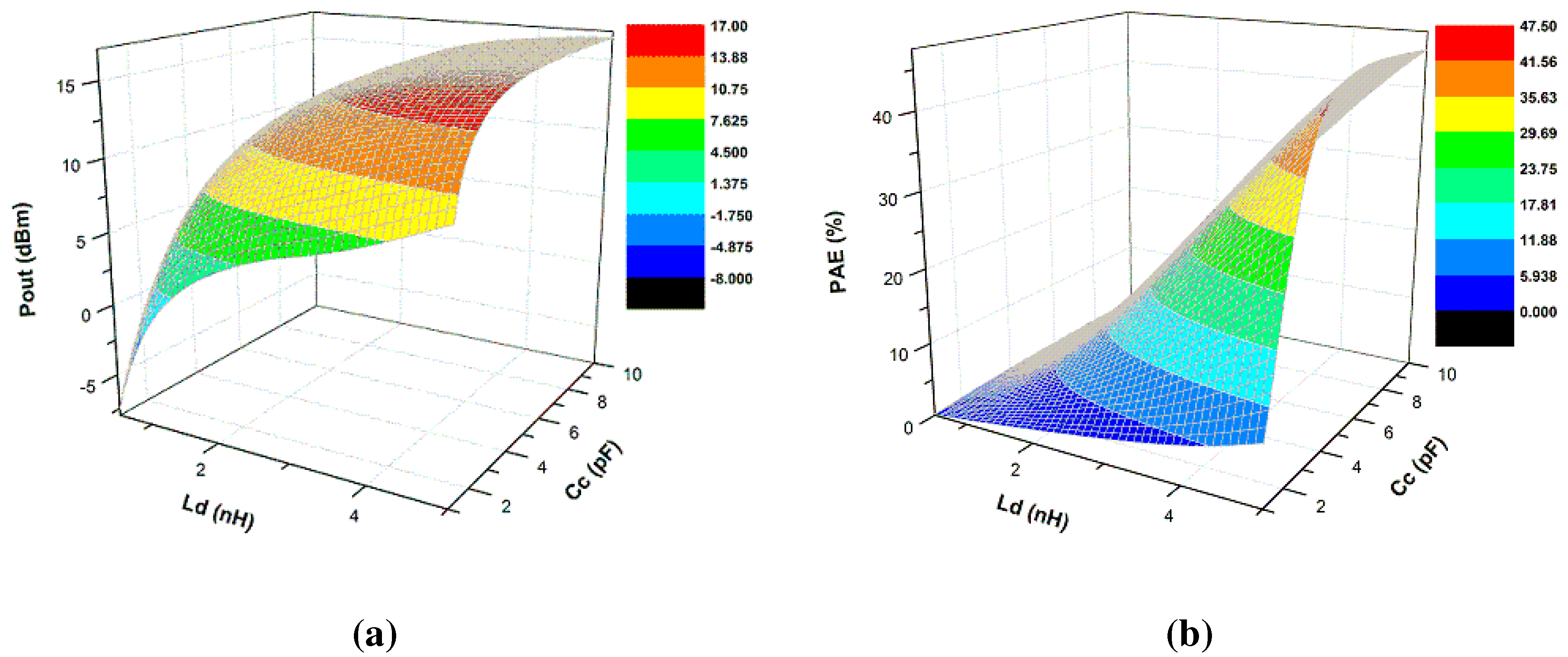
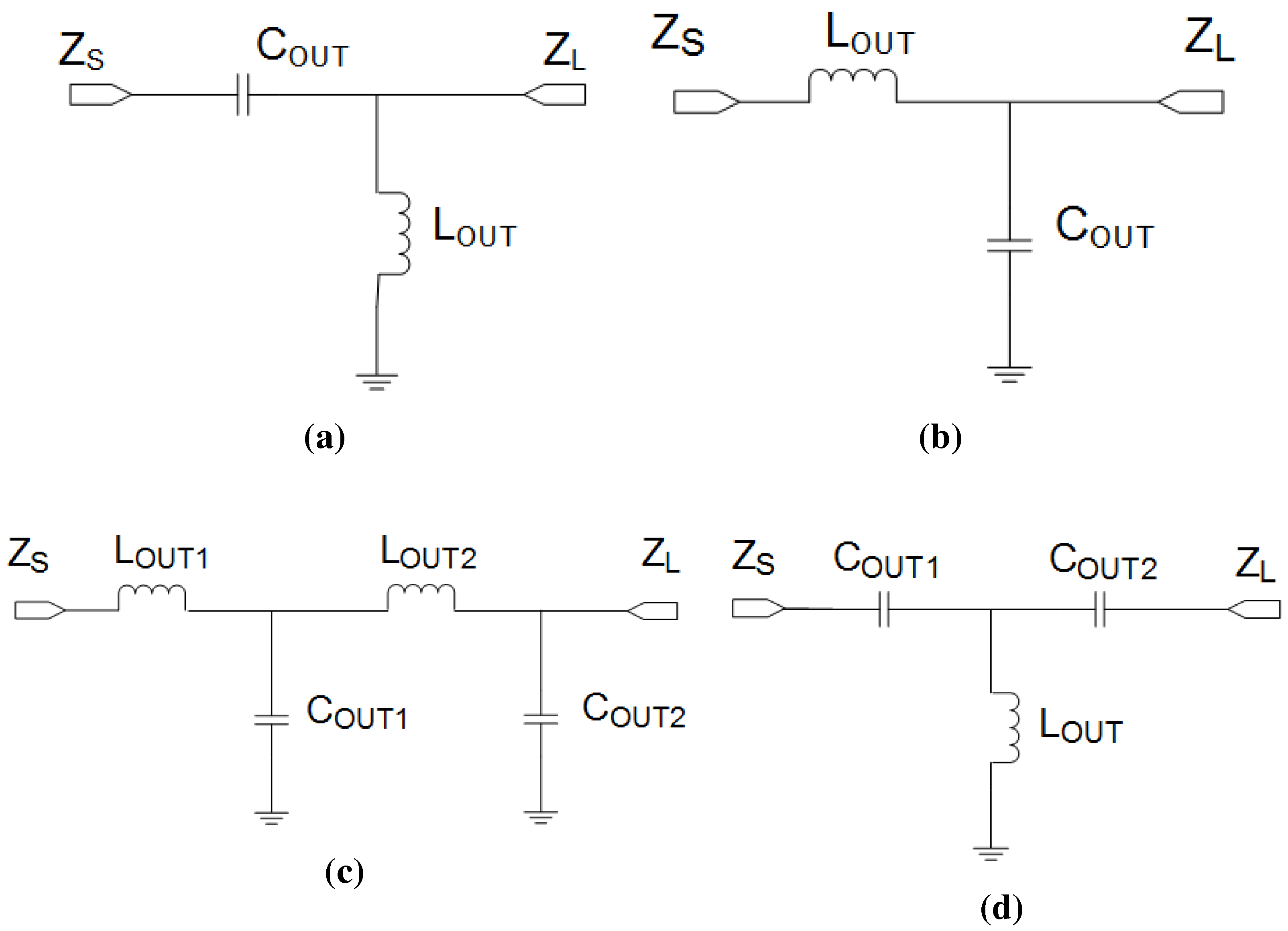
3.2. Power Amplifier Modeling and Analysis
4. Split Manufacturing in RF Circuits
- Scenario I: Remove only the top metal layer from the layers to generate FEOL. Since the inductors are often located in the top layer, the FEOL foundry does not have the information of interconnections through the top metal layer, as well as the inductor locations and sizes.
- Scenario II: Remove both the top and the second from the top metal layers. In this scenario, two upper metal layers are removed so that both inductors and capacitors are missing from the FEOL layout, because the capacitors are often built through the top two metal layers.
- Scenario III: Design obfuscation. For RF designs, inductors are always located in metal rings, and lower metal layers will be removed inside the rings for performance optimization. Therefore, the rings themselves, which contain multiple metal layers, would indicate the positions and approximate sizes of inductors. Similarly, the lower metal layers will not be used where capacitors are located. Therefore, attackers in both Scenarios I and II may learn the precise positions of the removed inductors/capacitors and may even further estimate their sizes. To further increase the security level, but still avoid performance overhead, we propose an obfuscation technique during the design phase to insert non-functional rings and to create empty zones in the original design. Using this method, it becomes more difficult for attackers to pin down the location, the count and the sizes of passive components.
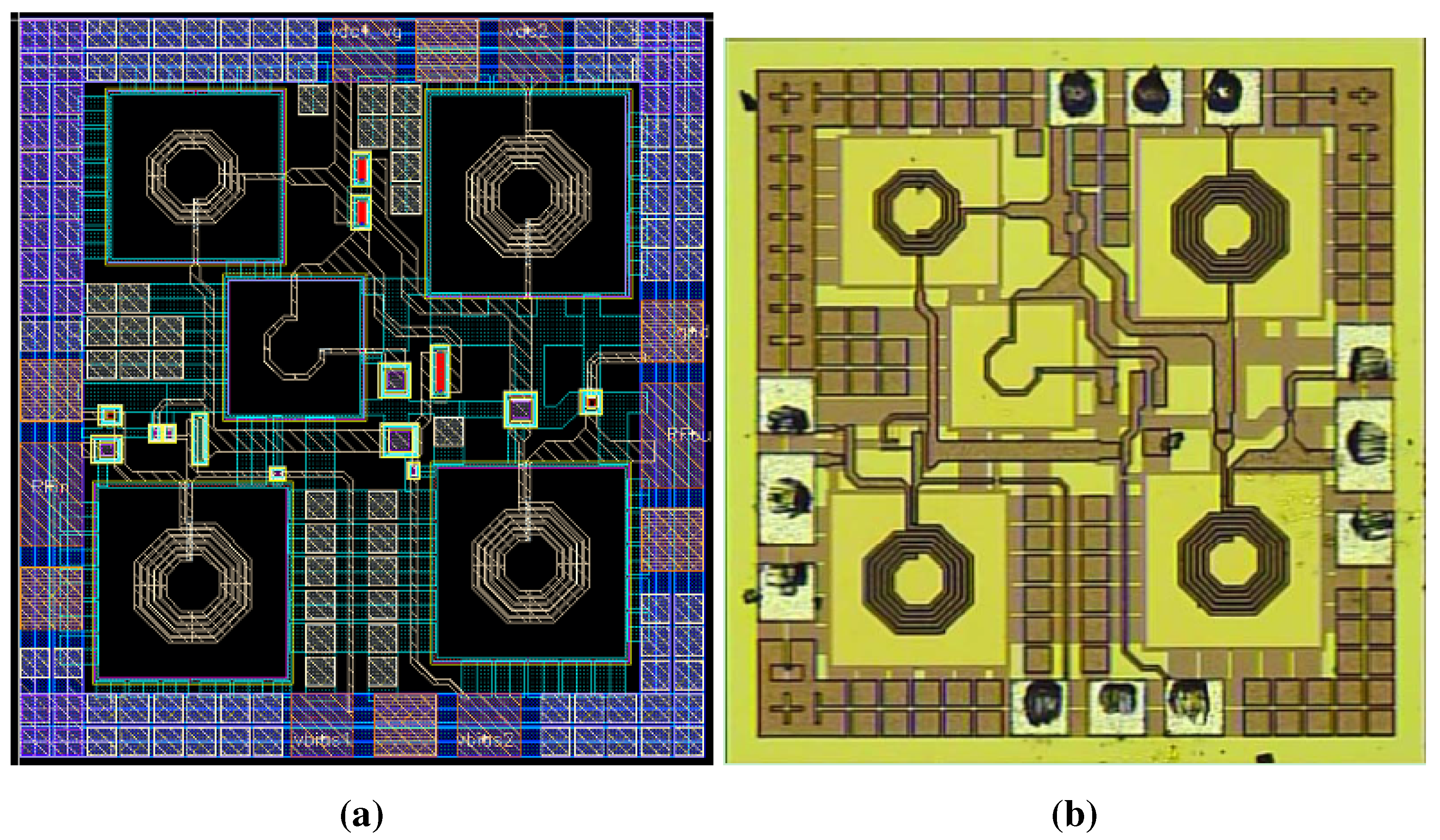
4.1. The First Example

4.1.1. Scenario I: Removal of Metal6 Layers (Inductors)

4.1.2. Scenario II: Removal of Metal5 and Metal6 Layers (Capacitors and Inductors)

4.1.3. Scenario III: Obfuscation Techniques
5. Experimentation

5.1. Scenario I: Removal of Metal6 Layers (Inductors)
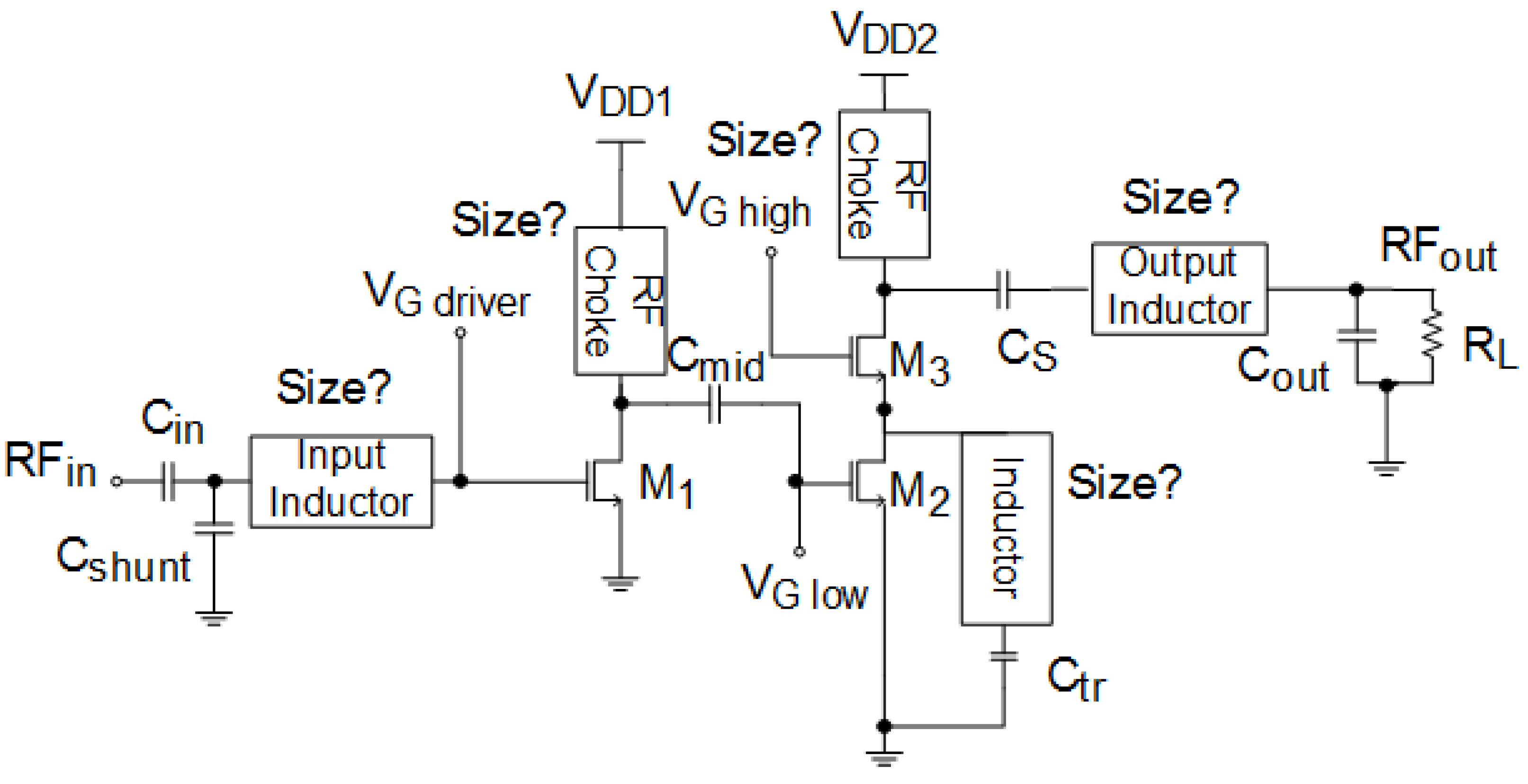

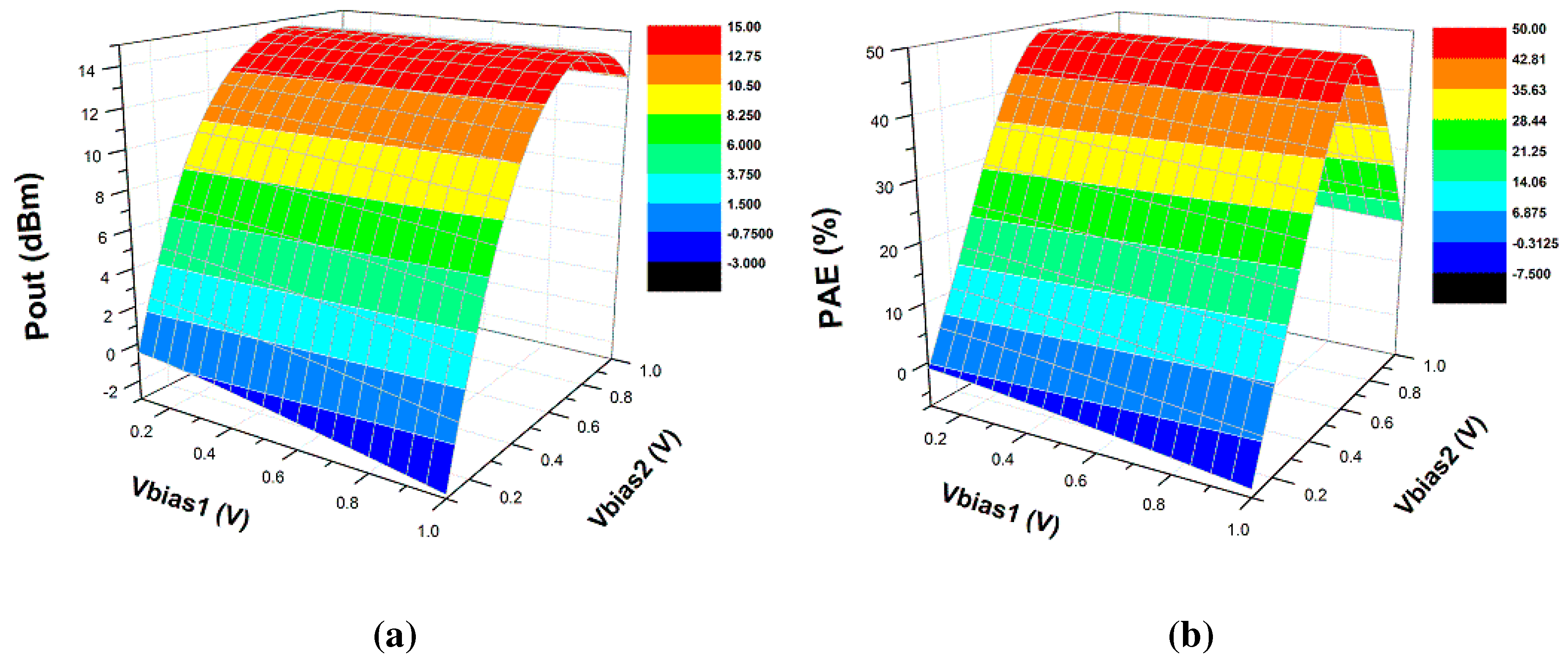
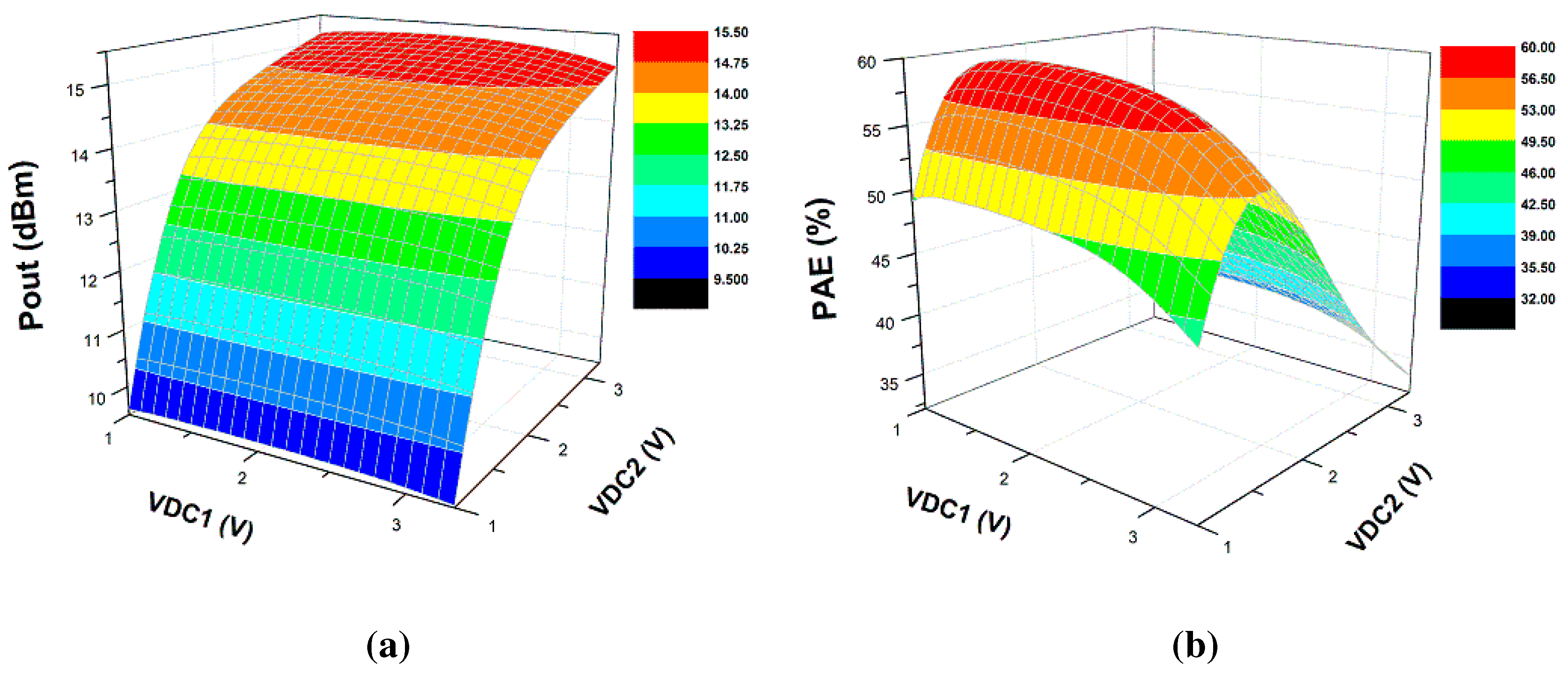

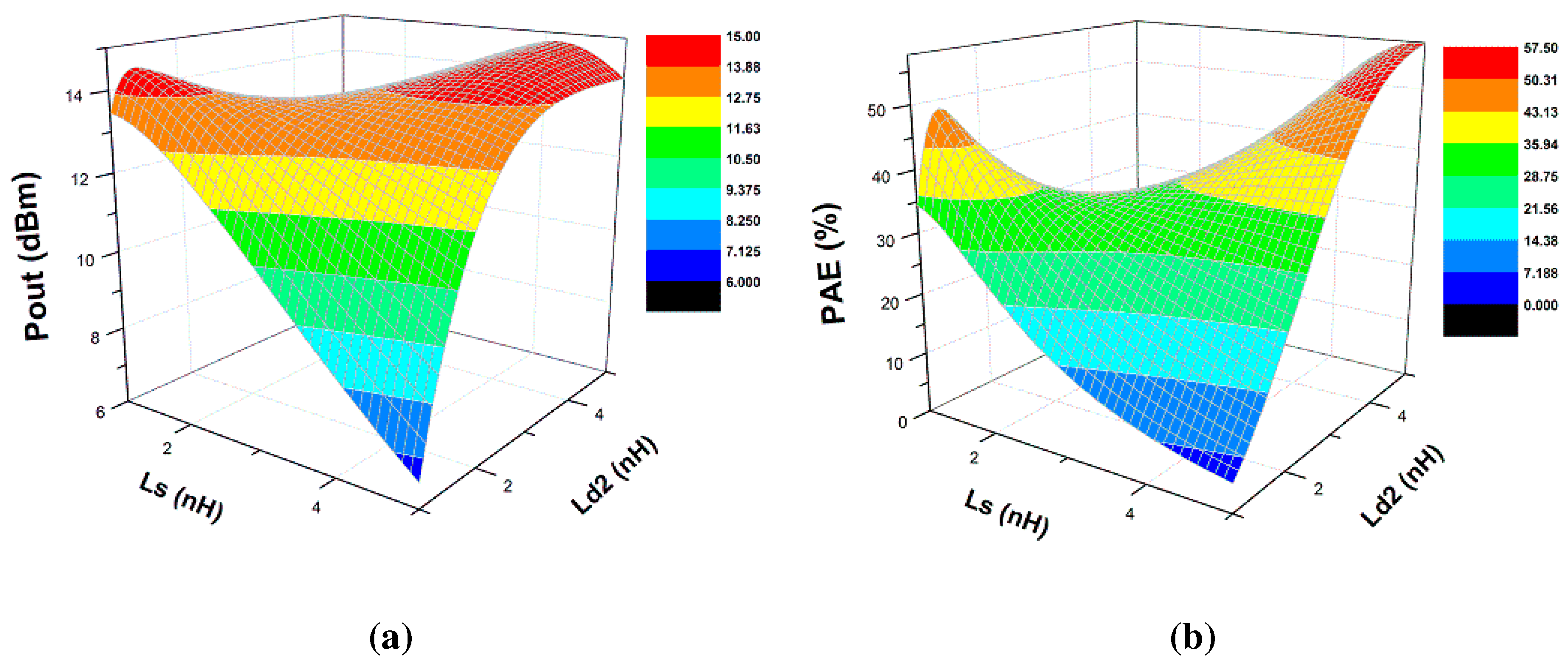
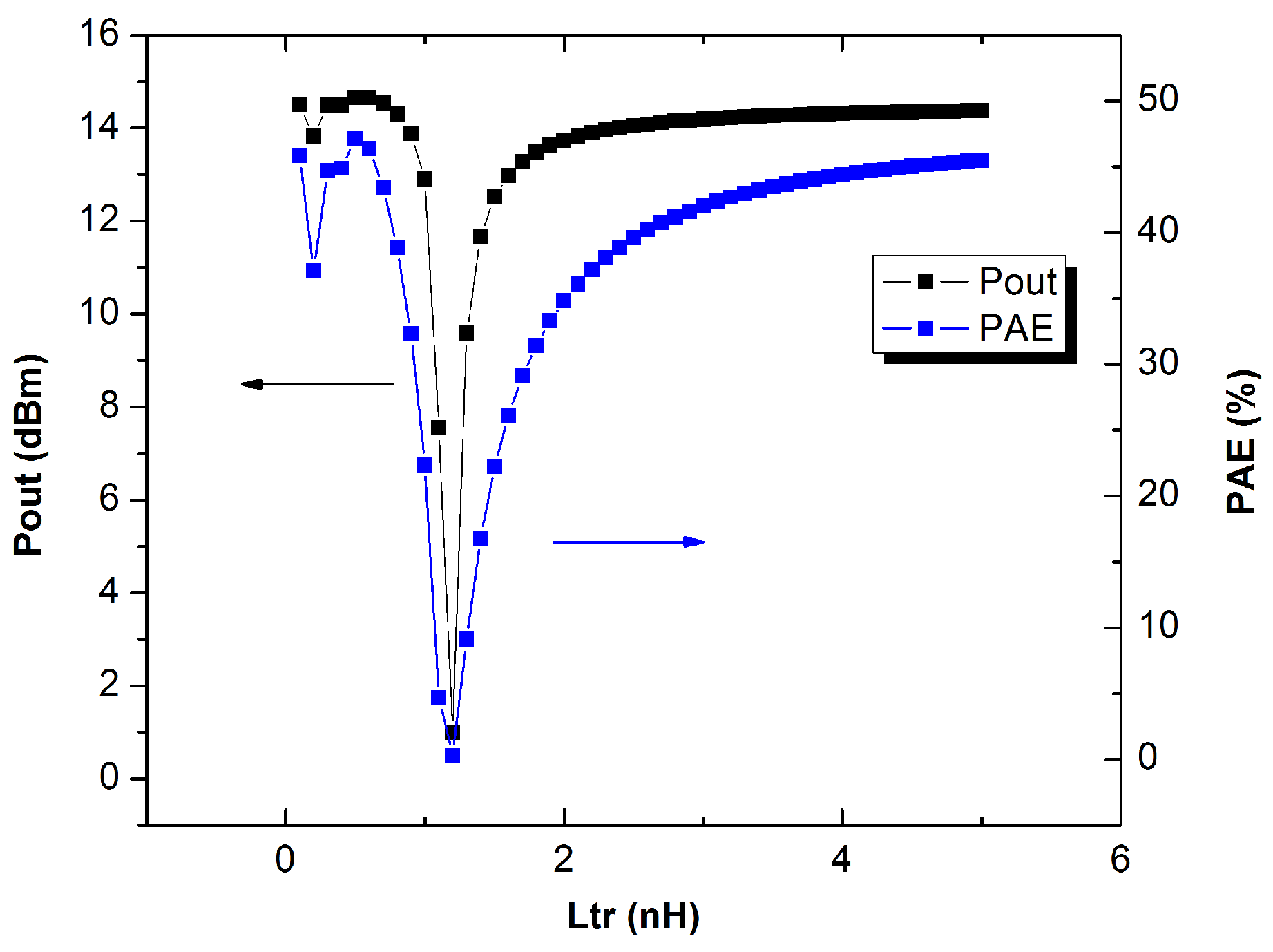
5.2. Scenario II: Removal of Metal5 and Metal6 Layers (Capacitors and Inductors)
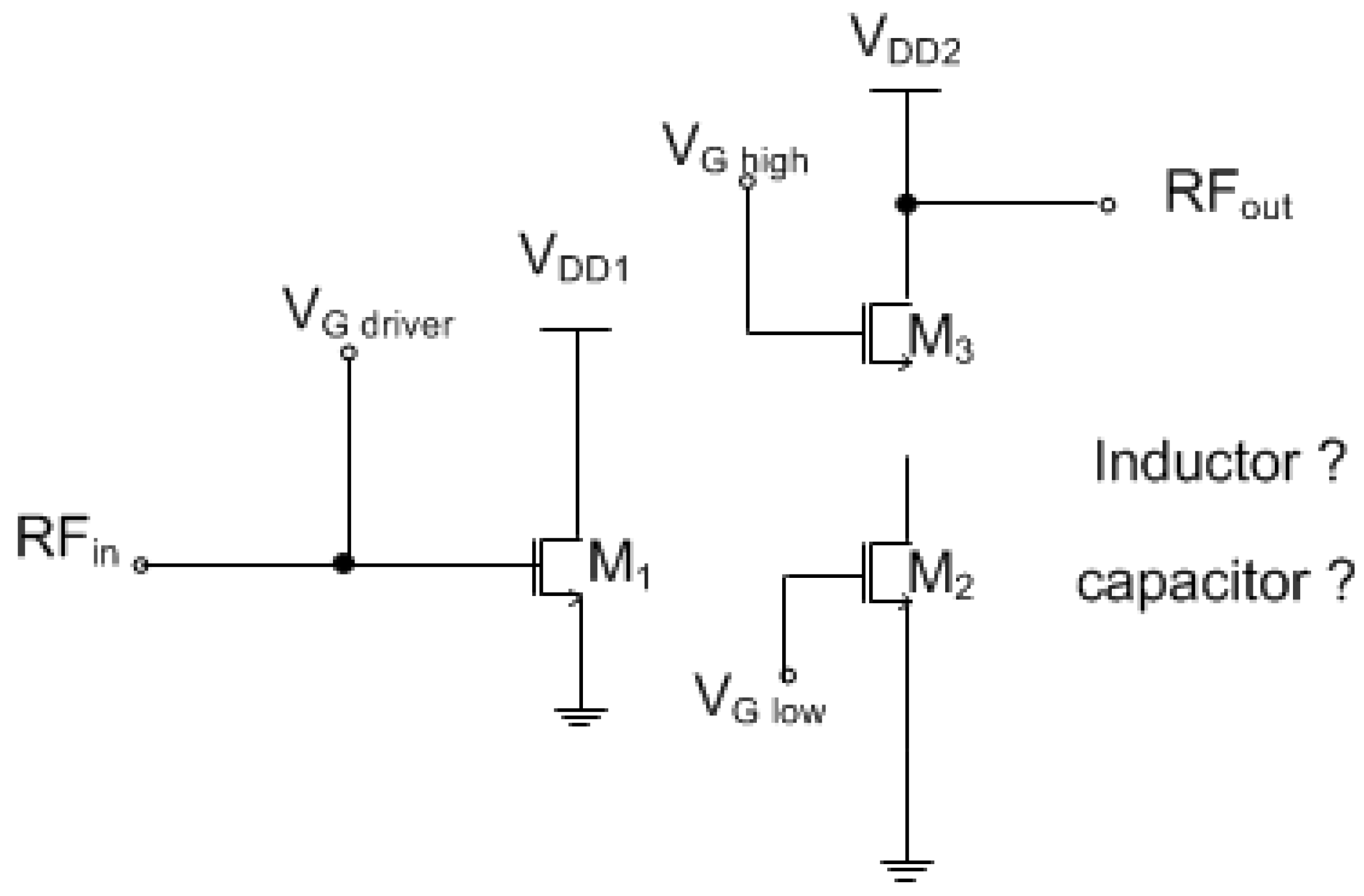

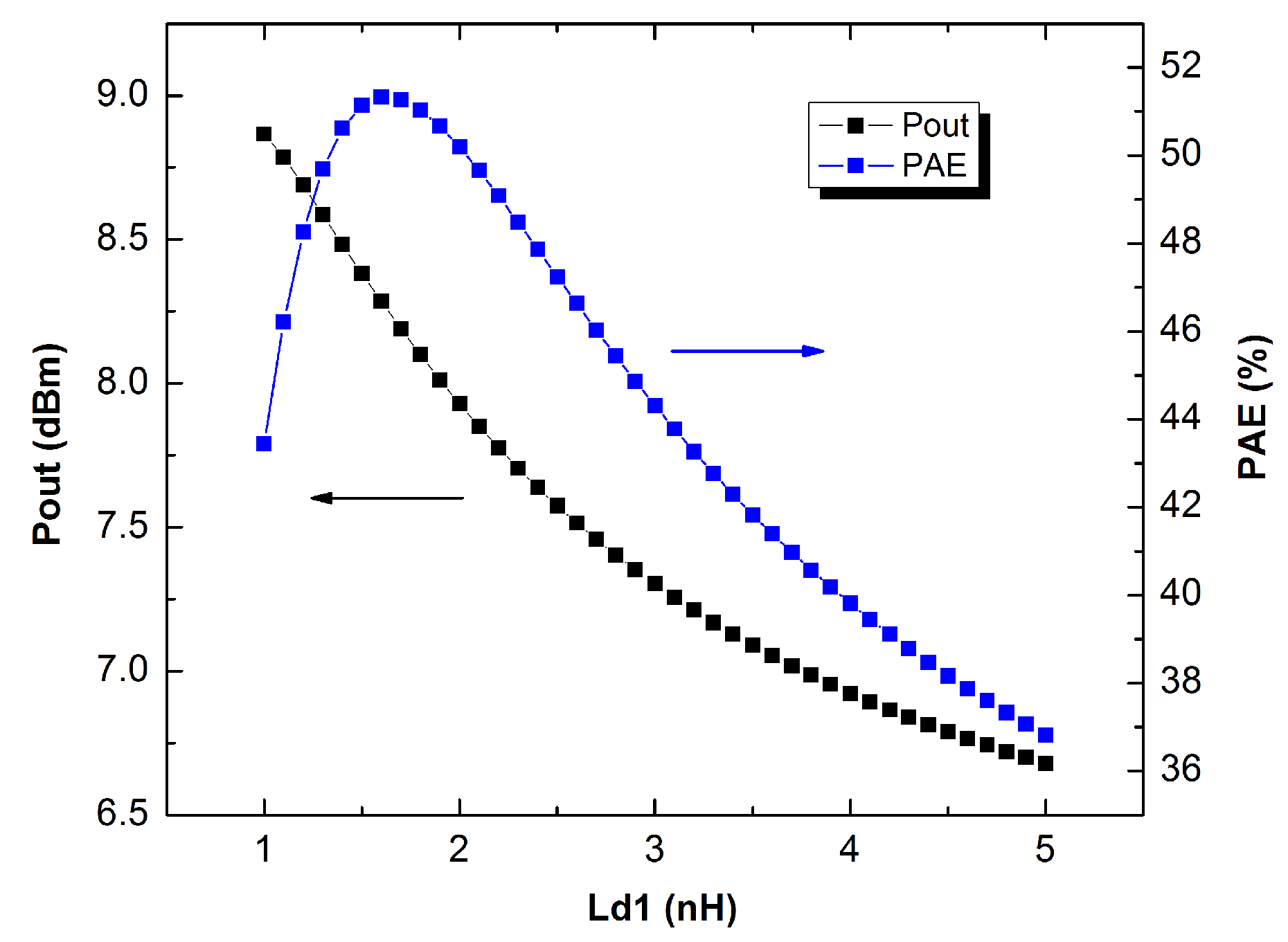

5.3. Scenario III: Obfuscation Techniques
6. Discussion
7. Conclusions
Author Contributions
Conflicts of Interest
References
- Defense Science Board (DSB) study on High Performance Microchip Supply. Available online: http://www.cra.org/govaffairs/images/2005-02-HPMS_Report_Final.pdf (accessed on 15 August 2005).
- Adee, S. The Hunt For The Kill Switch. IEEE Spectr. 2008, 45, 34–39. [Google Scholar] [CrossRef]
- Yeh, A. Trends in the Global IC Design Service Market; DIGITIMES Research: Taipei, Taiwan, 2007. [Google Scholar]
- Jin, Y.; Yang, B.; Makris, Y. Cycle-accurate information assurance by proof-carrying based signal sensitivity tracing. In Proceedings of the IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Austin, TX, USA, 2–3 June 2013; pp. 99–106.
- Tehranipoor, M.; Koushanfar, F. A Survey of Hardware Trojan Taxonomy and Detection. IEEE Des. Test Comput. 2010, 27, 10–25. [Google Scholar] [CrossRef]
- Bi, Y.; Gaillardon, P.-E.; Hu, X.; Niemier, M.; Yuan, J.-S.; Jin, Y. Leveraging Emerging Technology for Hardware Security—Case Study on Silicon Nanowire FETs and Graphene SymFETs. In Proceedings of the 2014 IEEE 23rd Asian Test Symposium (ATS), Hangzhou, China, 16–19 November 2014; pp. 342–347.
- Intelligence Advanced Research Projects Activity. Trusted Integrated Chips (TIC) Program. Available online: https://www.fbo.gov/notices/36a51487427786930733999edc40f321 (accessed on 15 August 2011).
- Rajendran, J.; Sinanoglu, O.; Karri, R. Is split manufacturing secure? In Proceedings of the Design, Automation Test in Europe Conference Exhibition (DATE), Grenoble, France, 18–22 March 2013; pp. 1259–1264.
- Imeson, F.; Emtenan, A.; Garg, S.; Tripunitara, M. Securing Computer Hardware Using 3D Integrated Circuit (IC) Technology and Split Manufacturing for Obfuscation. In Proceedings of the 22nd USENIX Security Symposium, Washington, DC, USA, 14–16 August 2013; pp. 495–510.
- Hill, B.; Karmazin, R.; Otero, C.T.O.; Tse, J.; Manohar, R. A split-foundry asynchronous FPGA. In Proceedings of the Custom Integrated Circuits Conference (CICC), San Jose, CA, USA, 22–25 September 2013; pp. 1–4.
- Vaidyanathan, K.; Das, B.P.; Sumbul, E.; Liu, R.; Pileggi, L. Building Trusted ICs using Split Fabrication. In Proceedings of the 2014 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Arlington, VA, USA, 6–7 May 2014.
- Vaidyanathan, K.; Liu, R.; Sumbul, E.; Zhu, Q.; Franchetti, F.; Pileggi, L. Efficient and Secure Intellectual Property (IP) Design with Split Fabrication. In Proceedings of the 2014 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Arlington, VA, USA, 6–7 May 2014.
- Jagasivamani, M.; Gadfort, P.; Sika, M.; Bajura, M.; Fritze, M. Split-Fabrication Obfuscation: Metrics and Techniques. In Proceedings of the 2014 IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), Arlington, VA, USA, 6–7 May 2014.
- Vaidyanathan, K.; Das, B.P.; Pileggi, L. Detecting Reliability Attacks During Split Fabrication Using Test-only BEOL Stack. In Proceedings of the 51st Annual Design Automation Conference on Design Automation Conference, San Francisco, CA, USA, 1–5 June 2014; pp. 156–161.
- Bi, Y.; Yuan, J.S.; Jin, Y. Split Manufacturing in Radio-Frequency Designs. In Proceedings of the International Conference on Security and Management (SAM), Las Vegas, NV, USA, 27–30 July 2015; pp. 204–210.
- Yuan, J.S.; Xu, Y.; Yen, S.D.; Bi, Y.; Hwang, G.W. Hot Carrier Injection Stress Effect on a 65 nm LNA at 70 GHz. IEEE Trans. Device Mater. Reliab. 2014, 14, 931–934. [Google Scholar] [CrossRef]
- Yuan, J.S.; Bi, Y. Process and temperature robust voltage multiplier design for RF energy harvesting. Microelectron. Reliab. 2015, 55, 107–113. [Google Scholar] [CrossRef]
- Carls, J.; Eickhoff, R.; Sakalas, P.; von der Mark, S.; Wehrli, S. Design of a C-Band CMOS class AB power amplifier for an ultra low supply voltage of 1.9 V. In Proceedings of the SBMO/IEEE MTT-S International Microwave and Optoelectronics Conference, Brazil, 29 October–1 November 2007; pp. 786–789.
- Yuan, J.-S.; Yen, H.D.; Chen, S.; Wang, R.L.; Huang, G.W.; Juang, Y.Z.; Tu, C.H.; Yeh, W.K.; Ma, J. Experimental Verification of RF Stress Effect on Cascode Class-E PA Performance and Reliability. IEEE Trans. Device Mater. Reliab. 2012, 12, 369–375. [Google Scholar] [CrossRef]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bi, Y.; Yuan, J.S.; Jin, Y. Beyond the Interconnections: Split Manufacturing in RF Designs. Electronics 2015, 4, 541-564. https://doi.org/10.3390/electronics4030541
Bi Y, Yuan JS, Jin Y. Beyond the Interconnections: Split Manufacturing in RF Designs. Electronics. 2015; 4(3):541-564. https://doi.org/10.3390/electronics4030541
Chicago/Turabian StyleBi, Yu, Jiann S. Yuan, and Yier Jin. 2015. "Beyond the Interconnections: Split Manufacturing in RF Designs" Electronics 4, no. 3: 541-564. https://doi.org/10.3390/electronics4030541




