Reducing JPEG False Contour Using Visual Illumination
Abstract
:1. Introduction
2. Related Works
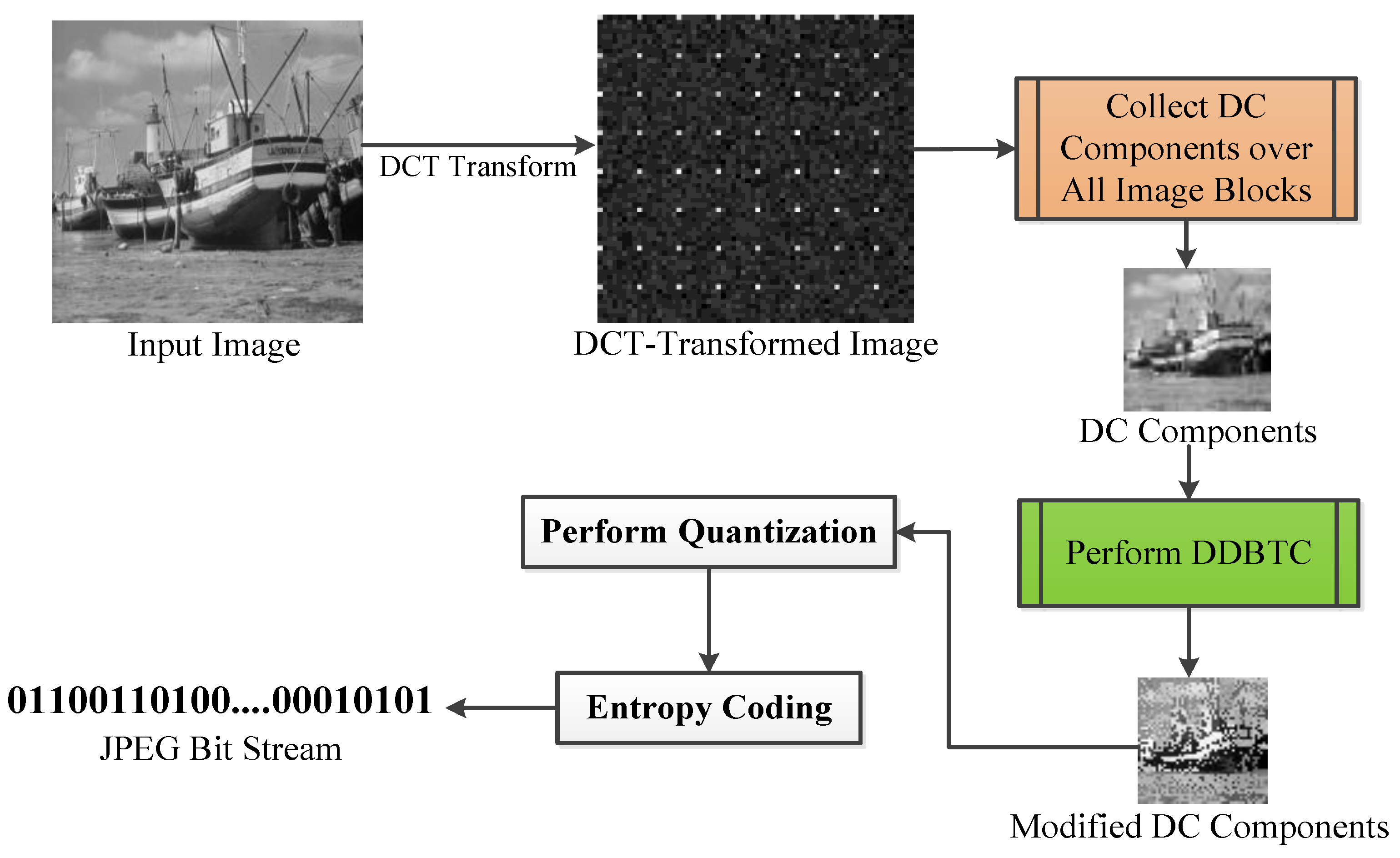
2.1. JPEG Image Compression
2.2. Error Diffused Method
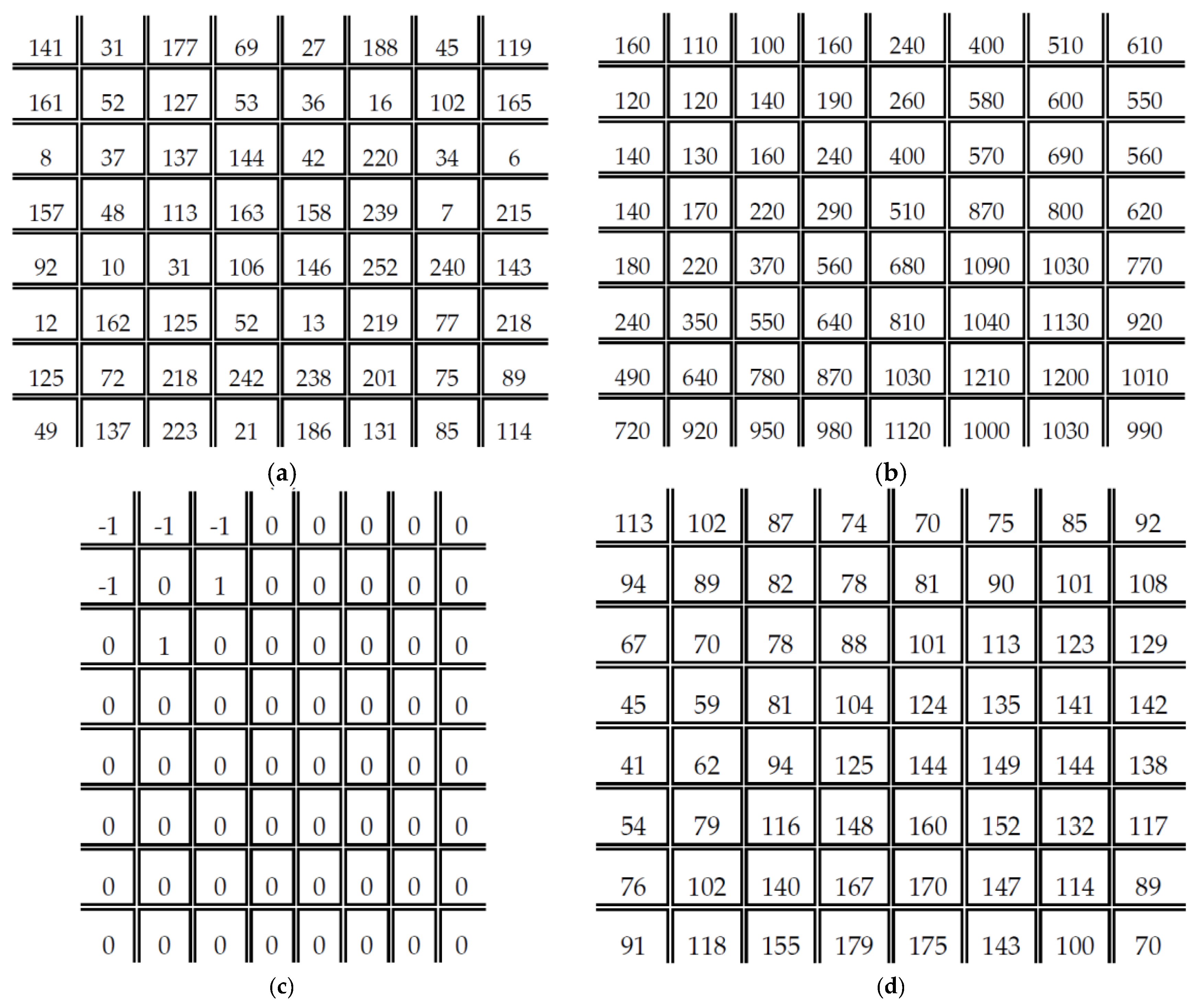
3. Proposed Method for Reducing JPEG False Contour
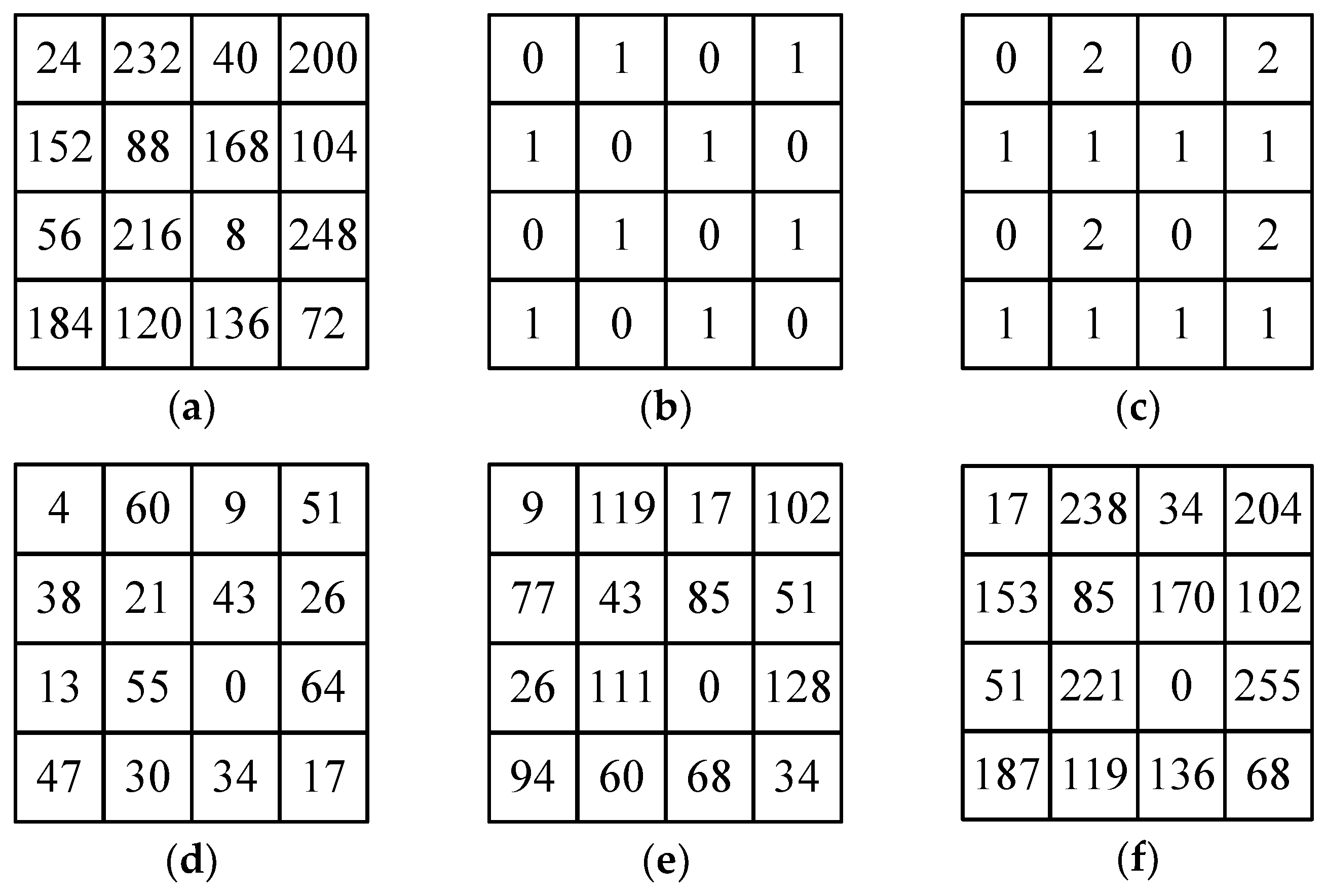
3.1. Ordered Dither Method
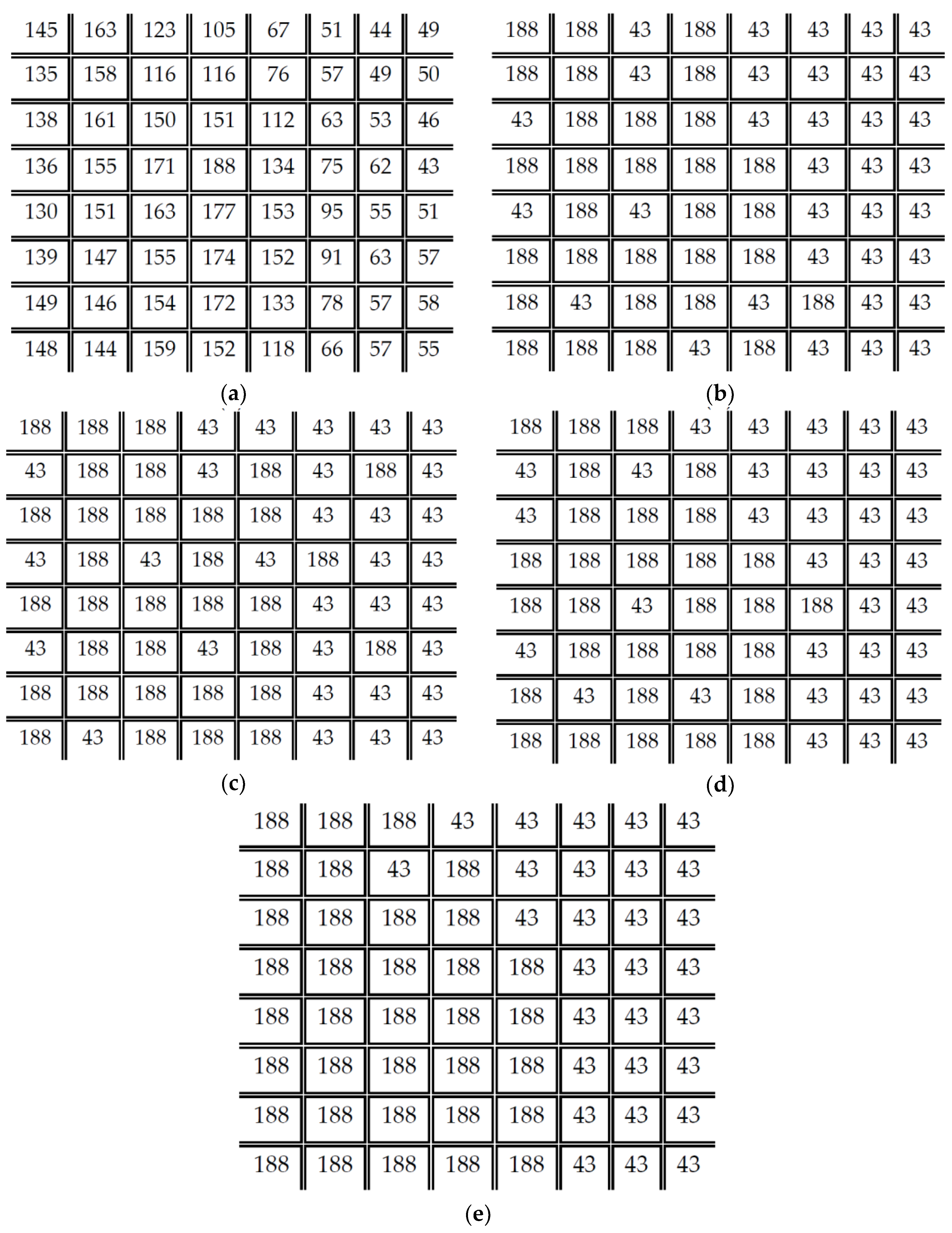
3.2. Dot Diffused Method
4. Experimental Results
4.1. Experimental Setup
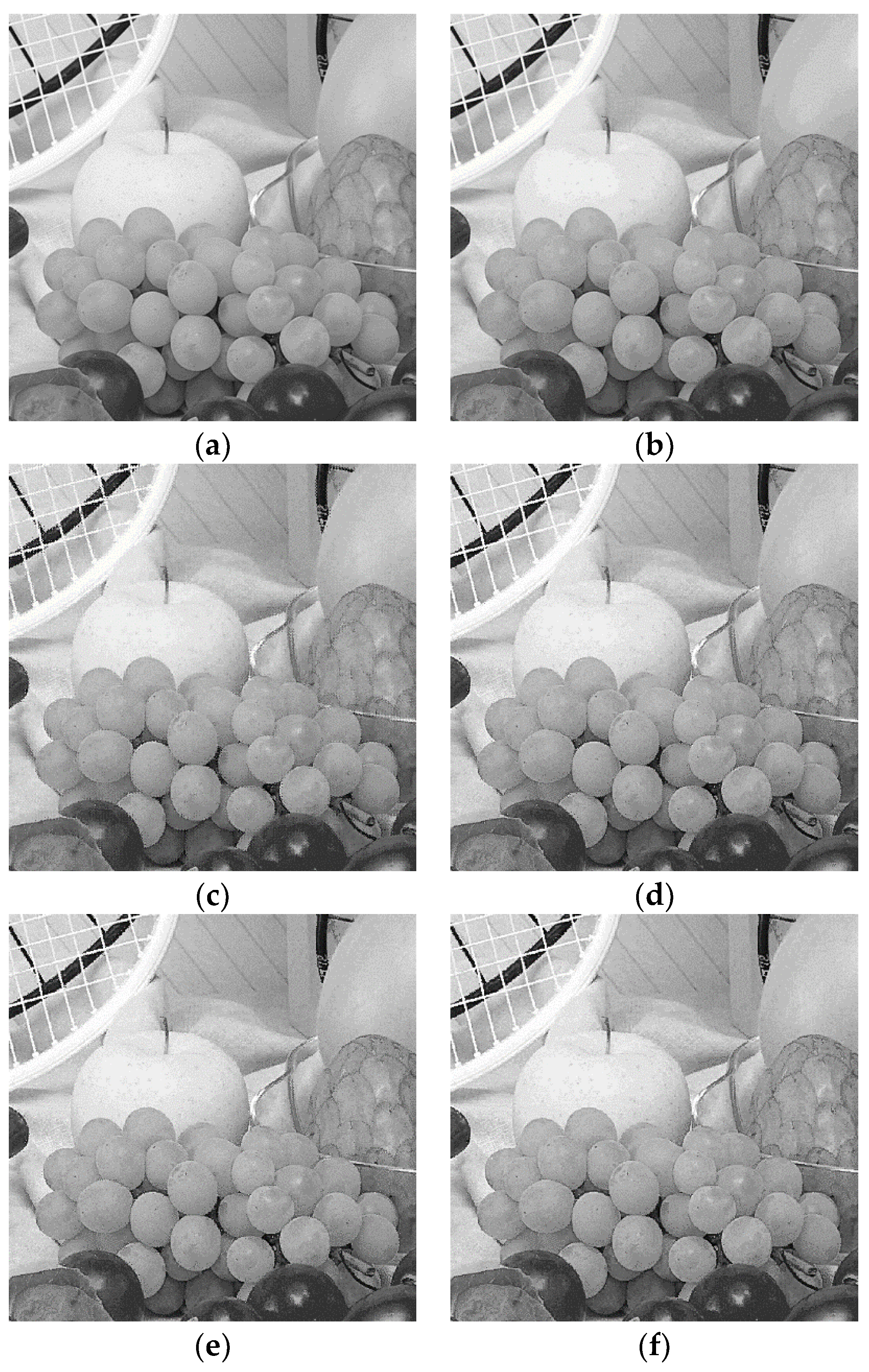
4.2. Visual Investigation of the Proposed Method
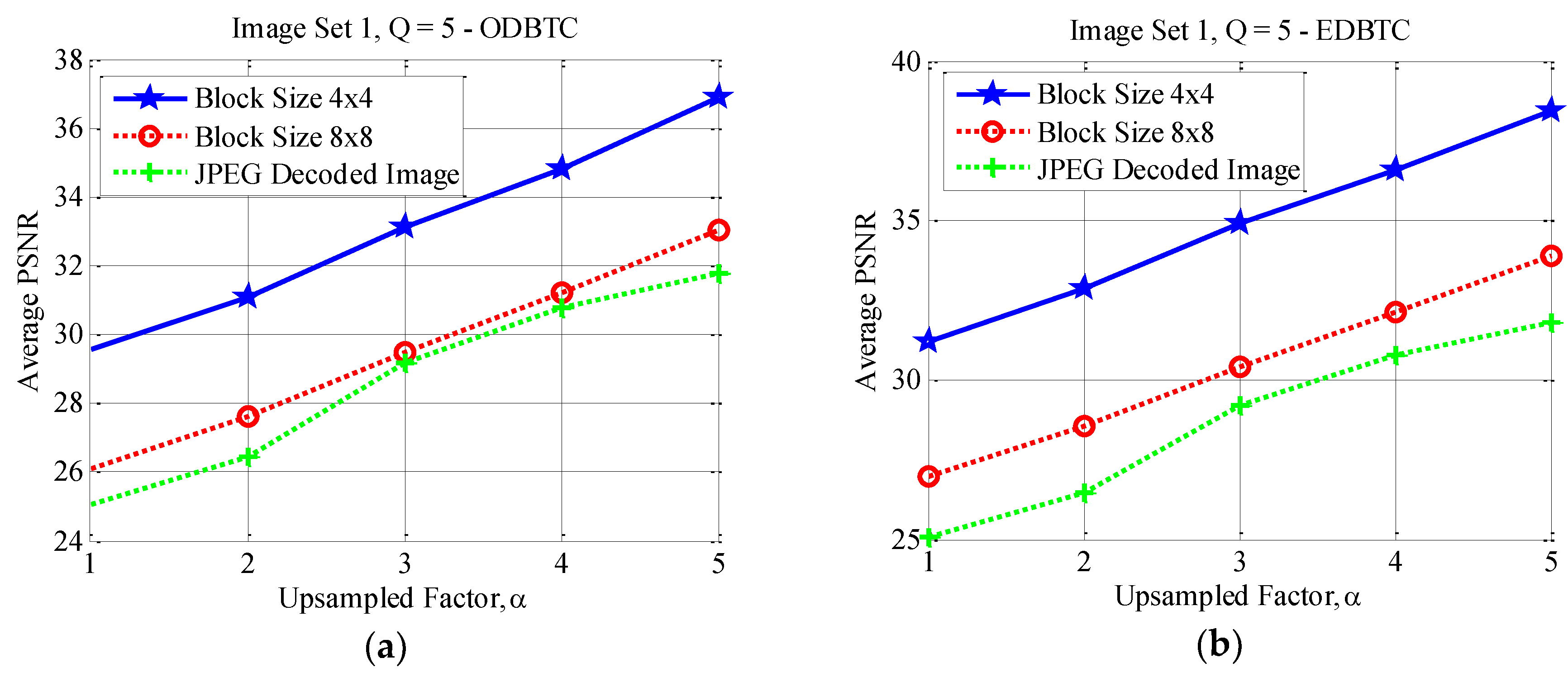
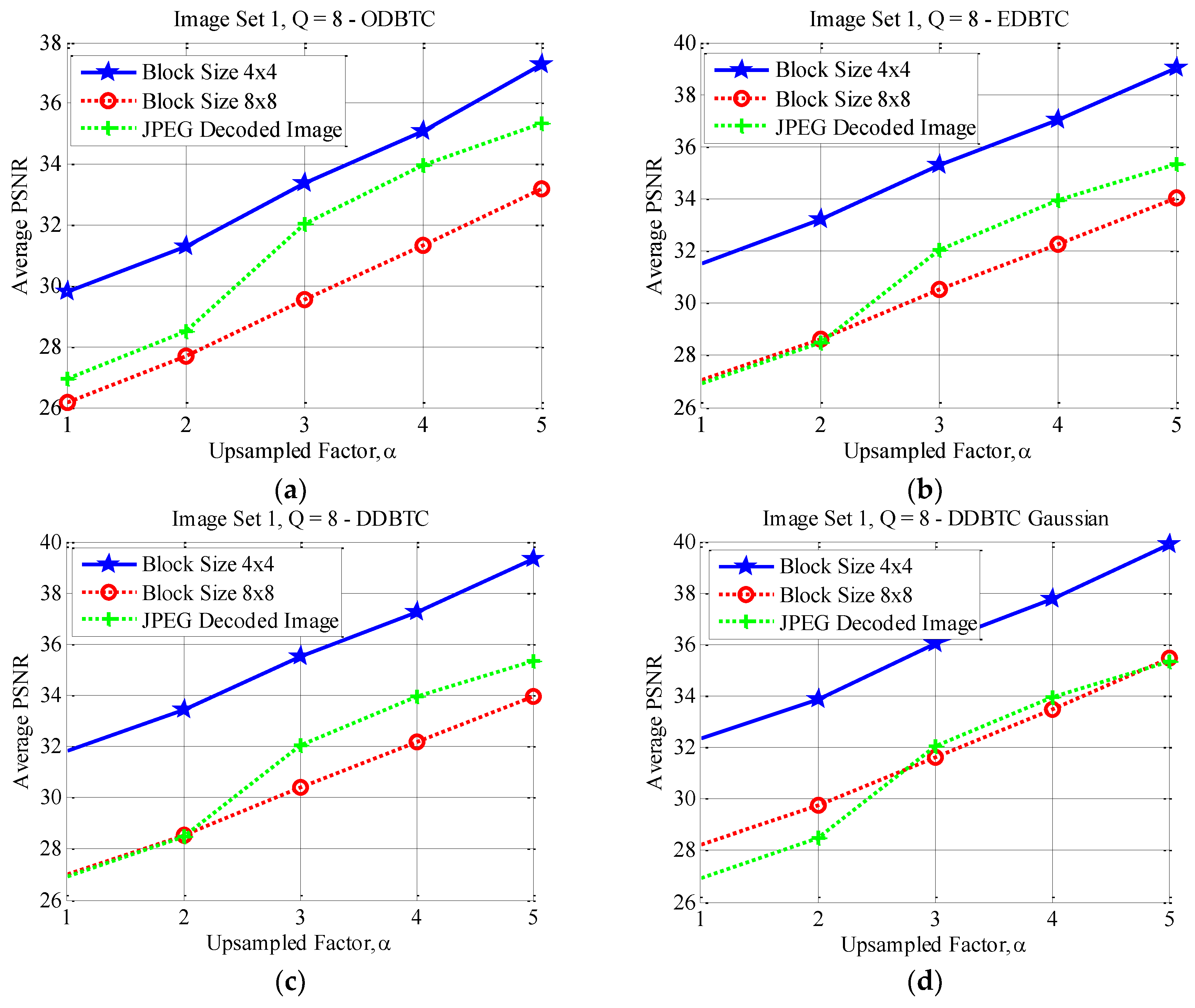
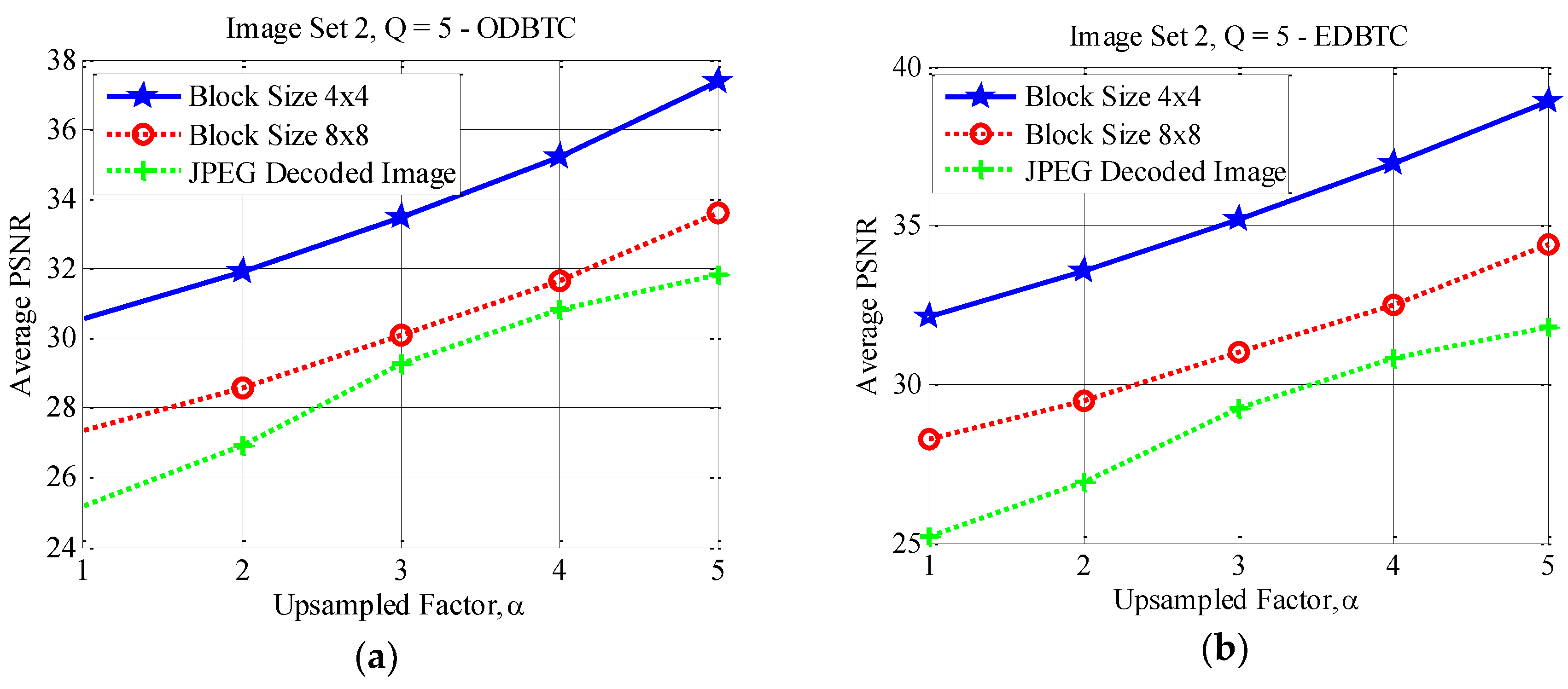
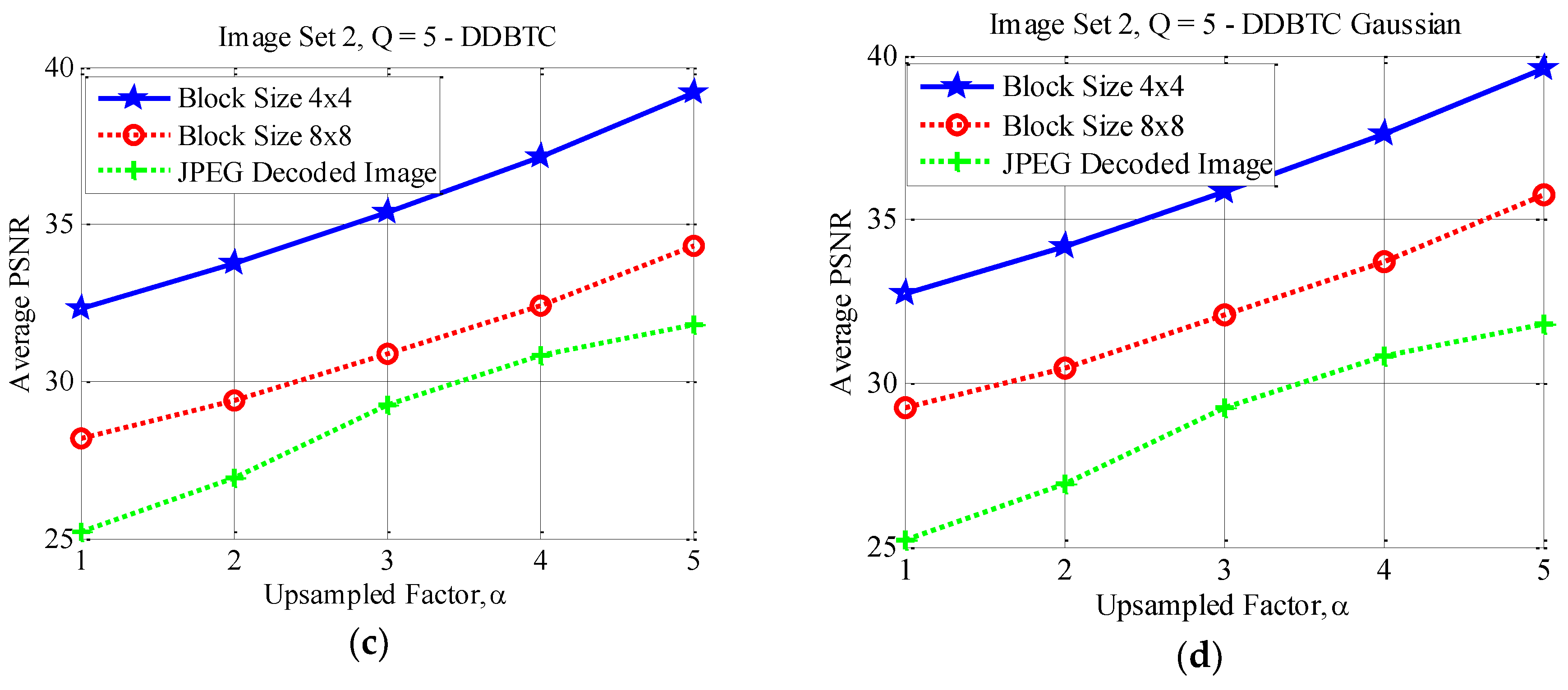
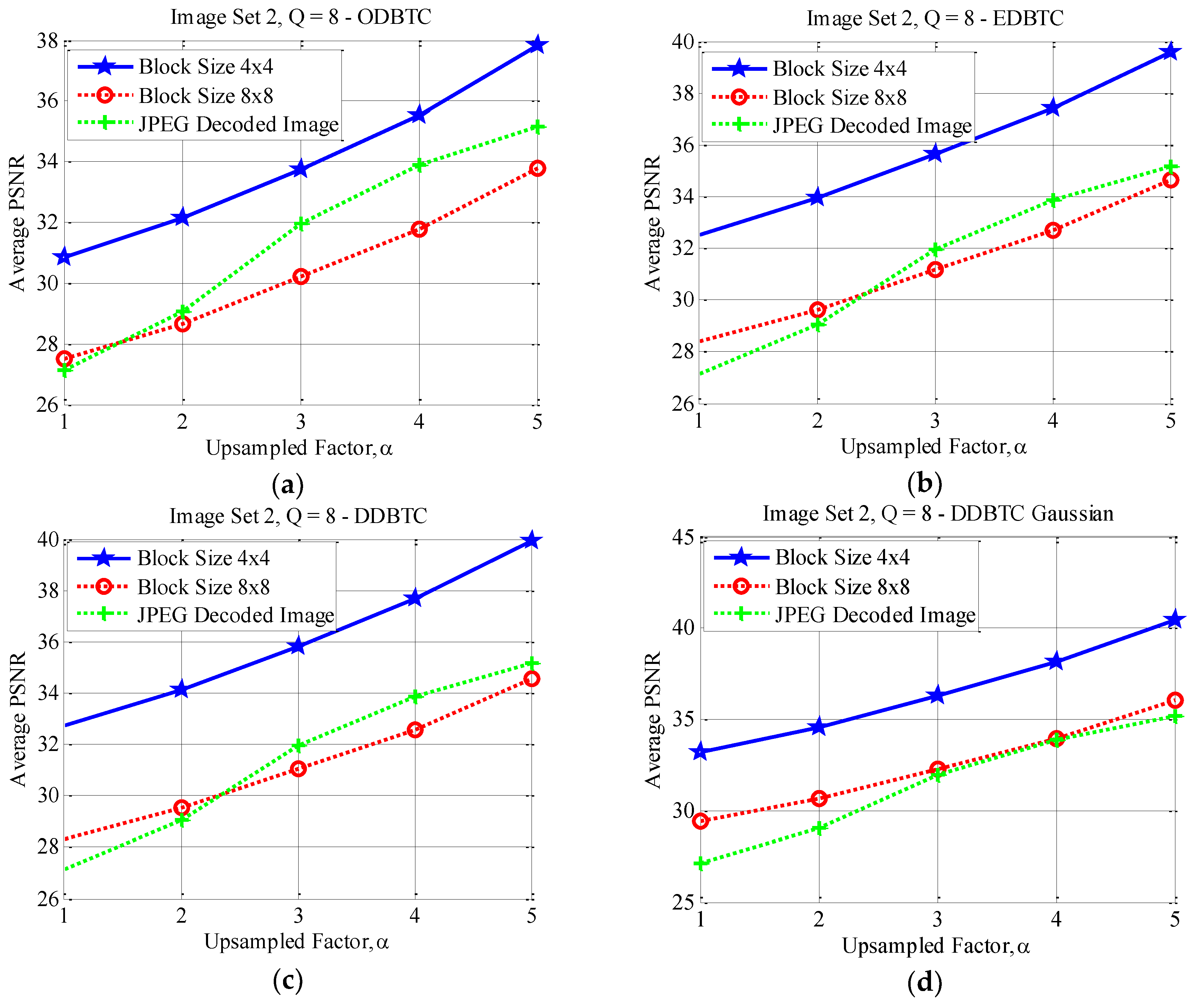
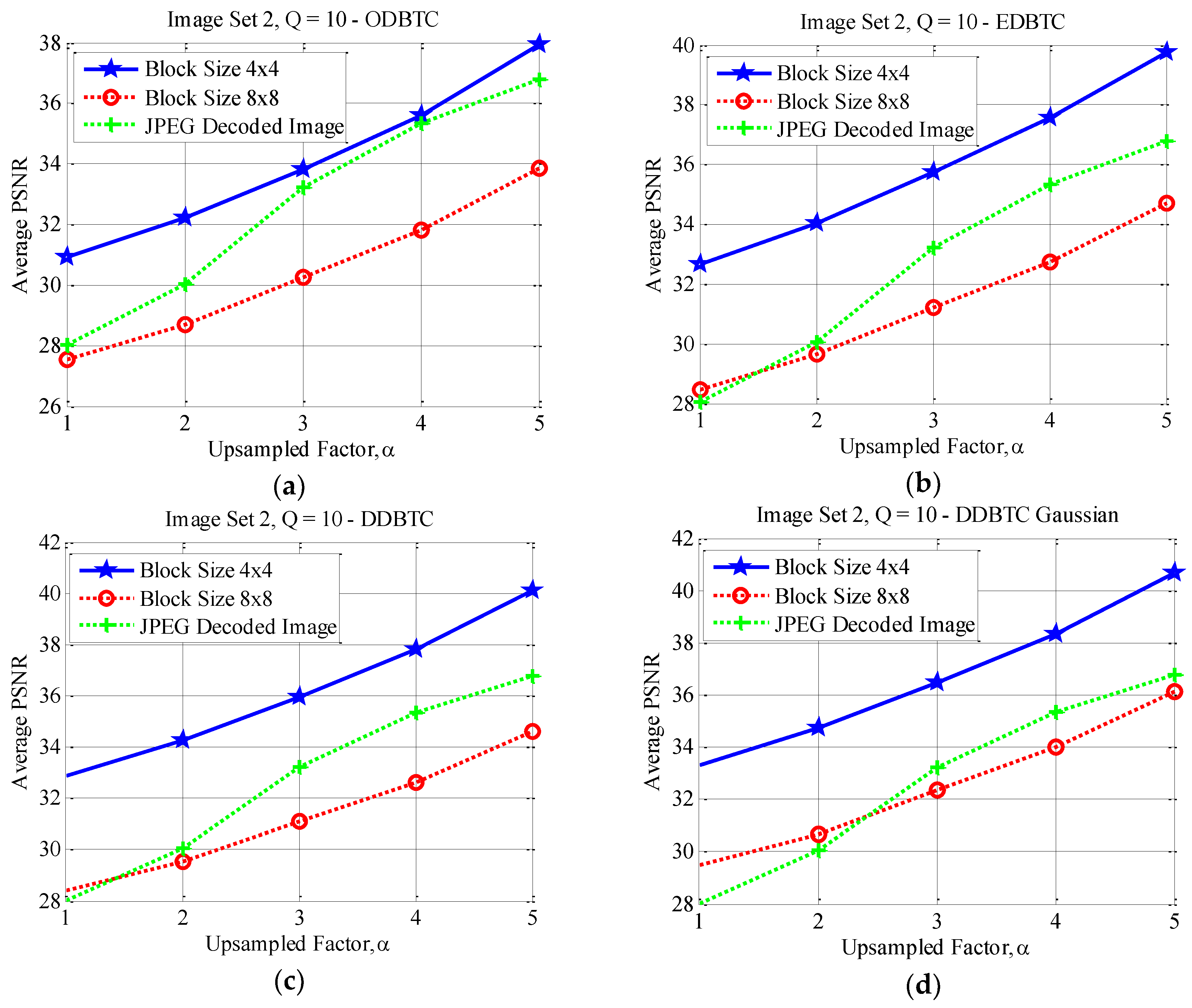
4.3. Effects of Different Block Sizes
4.4. Performance Comparison
4.5. JPEG False Contour Reduction for Color Image
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Guo, J.M. High efficiency ordered dither block truncation with dither array LUT and its scalable coding application. Digit. Signal Process. 2010, 20, 97–110. [Google Scholar] [CrossRef]
- Guo, J.M. Improved block truncation coding using modified error diffusion. Electron. Lett. 2008, 44, 7. [Google Scholar] [CrossRef]
- Guo, J.M.; Liu, Y.F. Improved Block Truncation Coding using Optimized Dot Diffusion. IEEE Trans. Image Process. 2014, 23, 1269–1275. [Google Scholar]
- Guo, J.M.; Prasetyo, H.; Lee, H.; Yao, C.C. Image retrieval using indexed histogram of void-and-cluster block truncation coding. Signal Process. 2016, 123, 143–156. [Google Scholar] [CrossRef]
- Guo, J.M.; Wu, M.F.; Kang, Y.C. Watermarking in conjugate ordered dither block truncation coding images. Signal Process. 2009, 89, 1864–1882. [Google Scholar] [CrossRef]
- Guo, J.M.; Prasetyo, H.; Su, H.S. Image indexing using the color and bit pattern feature fusion. J. Vis. Commun. Image Represent. 2013, 24, 1360–1379. [Google Scholar] [CrossRef]
- Guo, J.M.; Prasetyo, H. Content-Based Image Retrieval Using Features Extracted From Halftoning-Based Block Truncation Coding. IEEE Trans. Image Process. 2015, 24, 1010–1024. [Google Scholar] [PubMed]
- Guo, J.M.; Prasetyo, H.; Chen, J.H. Content-based image retrieval using error diffusion block truncation coding features. IEEE Trans. Circuits Syst. Video Technol. 2015, 25, 466–481. [Google Scholar]
- Guo, J.M.; Prasetyo, H.; Wang, N.J. Effective image retrieval system using dot-diffused block truncation coding features. IEEE Trans. Multimed. 2015, 17, 1576–1590. [Google Scholar] [CrossRef]
- Liu, Y.F.; Guo, J.M.; Lee, J.D. Inverse halftoning based on the Bayesian theorem. IEEE Trans. Image Process. 2011, 20, 1077–1084. [Google Scholar] [PubMed]
- Liu, Y.F.; Guo, J.M. Dot-diffused halftoning with improved homogeneity. IEEE Trans. Image Process. 2015, 24, 4581–4591. [Google Scholar] [CrossRef] [PubMed]
- Liu, Y.F.; Guo, J.M. New class tilling design for dot-diffused halftoning. IEEE Trans. Image Process. 2013, 22, 1199–1208. [Google Scholar] [CrossRef] [PubMed]
- Guo, J.M.; Liu, Y.F. High capacity data hiding for error-diffused block truncation coding. IEEE Trans. Image Process. 2012, 21, 4808–4818. [Google Scholar] [PubMed]
- Guo, J.M.; Liu, Y.F. Halftone-image security improving using overall minimal-error searching. IEEE Trans. Image Process. 2011, 20, 2800–2812. [Google Scholar] [PubMed]
- Guo, J.M.; Hsia, C.H.; Chang, C.H. JPEG false contour reduction using error diffusion. Inform. Process. Lett. 2015, 115, 403–407. [Google Scholar] [CrossRef]
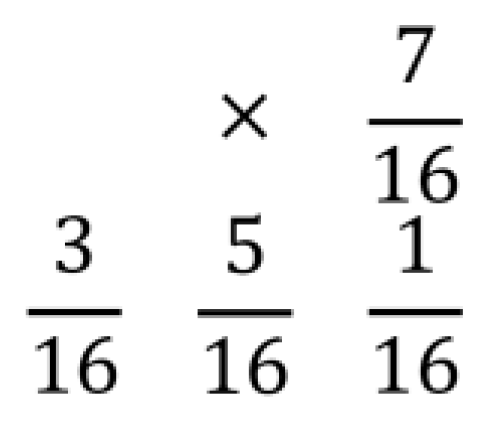

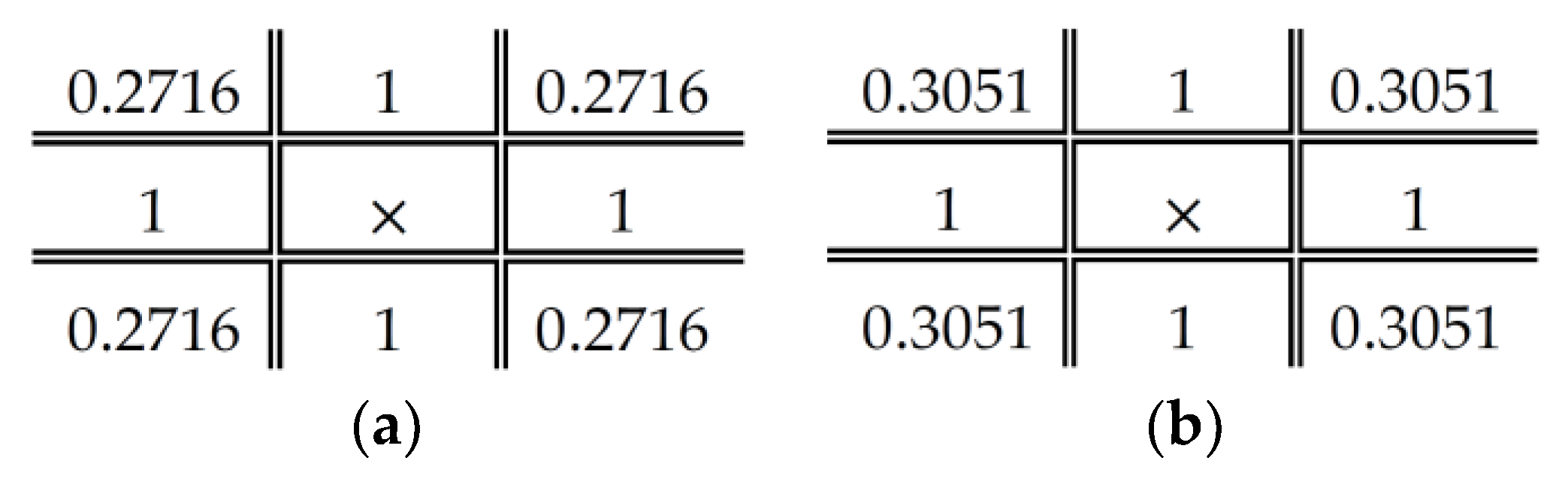














| HBTC Methods | Key Aspects of Algorithm |
|---|---|
| EDBTC | Employing the error kernel as shown in Figure 3 |
| ODBTC | Utilizing the dither arrays as shown in Figure 4 |
| DDBTC | Exploiting the class matrix and diffused kernel as given in Figure 5 and Figure 6, respectively |
| DDBTC Gaussian | Combining the class matrix as shown in Figure 5 with Gaussian diffused kernel in Figure 7 |
| Quality Factor | Downsampled Factor | JPEG Decoded Image | ODBTC | EDBTC [15] | DDBTC | DDBTC Gaussian |
|---|---|---|---|---|---|---|
| 25.07 | 29.59 | 31.21 | 31.49 | 31.99 | ||
| 26.44 | 31.08 | 32.88 | 33.05 | 33.49 | ||
| 29.19 | 33.11 | 34.91 | 35.10 | 35.57 | ||
| 30.79 | 34.82 | 36.60 | 36.80 | 37.25 | ||
| 31.78 | 36.88 | 38.45 | 38.69 | 39.18 | ||
| Average | 28.66 | 33.09 | 34.81 | 35.03 | 35.49 | |
| 26.93 | 29.79 | 31.51 | 31.82 | 32.35 | ||
| 28.49 | 31.30 | 33.23 | 33.41 | 33.89 | ||
| 32.05 | 33.36 | 35.30 | 35.51 | 36.03 | ||
| 33.97 | 35.10 | 37.03 | 37.25 | 37.76 | ||
| 35.34 | 37.28 | 39.04 | 39.31 | 39.88 | ||
| Average | 31.36 | 33.37 | 35.22 | 35.46 | 35.98 | |
| 27.78 | 29.82 | 31.57 | 31.89 | 32.43 | ||
| 29.38 | 31.38 | 33.34 | 33.54 | 34.02 | ||
| 33.32 | 33.43 | 35.41 | 35.62 | 36.16 | ||
| 35.32 | 35.17 | 37.15 | 37.37 | 37.90 | ||
| 36.82 | 37.39 | 39.20 | 39.49 | 40.08 | ||
| Average | 32.53 | 33.44 | 35.34 | 35.58 | 36.12 |
| Quality Factor | Downsampled Factor | JPEG Decoded Image | ODBTC | EDBTC [15] | DDBTC | DDBTC Gaussian |
|---|---|---|---|---|---|---|
| 25.20 | 30.58 | 32.15 | 32.33 | 32.73 | ||
| 26.91 | 31.89 | 33.56 | 33.75 | 34.16 | ||
| 29.26 | 33.46 | 35.21 | 35.40 | 35.83 | ||
| 30.82 | 35.20 | 36.94 | 37.16 | 37.59 | ||
| 31.81 | 37.37 | 38.90 | 39.19 | 39.62 | ||
| Average | 28.80 | 33.70 | 35.35 | 35.57 | 35.99 | |
| 27.13 | 30.86 | 32.54 | 32.74 | 33.18 | ||
| 29.06 | 32.14 | 33.94 | 34.15 | 34.59 | ||
| 31.96 | 33.74 | 35.63 | 35.83 | 36.32 | ||
| 33.89 | 35.52 | 37.44 | 37.68 | 38.17 | ||
| 35.17 | 37.83 | 39.57 | 39.91 | 40.42 | ||
| Average | 31.44 | 34.02 | 35.82 | 36.06 | 36.54 | |
| 28.04 | 30.94 | 32.66 | 32.88 | 33.32 | ||
| 30.05 | 32.22 | 34.06 | 34.27 | 34.73 | ||
| 33.23 | 33.82 | 35.75 | 35.96 | 36.46 | ||
| 35.34 | 35.61 | 37.57 | 37.83 | 38.33 | ||
| 36.79 | 37.96 | 39.78 | 40.13 | 40.67 | ||
| Average | 32.69 | 34.11 | 35.96 | 36.21 | 36.70 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Prasetyo, H.; Kurniawan, H. Reducing JPEG False Contour Using Visual Illumination. Information 2018, 9, 41. https://doi.org/10.3390/info9020041
Prasetyo H, Kurniawan H. Reducing JPEG False Contour Using Visual Illumination. Information. 2018; 9(2):41. https://doi.org/10.3390/info9020041
Chicago/Turabian StylePrasetyo, Heri, and Hendra Kurniawan. 2018. "Reducing JPEG False Contour Using Visual Illumination" Information 9, no. 2: 41. https://doi.org/10.3390/info9020041






