Protection Method for Data Communication between ADS-B Sensor and Next-Generation Air Traffic Control Systems
Abstract
:1. Introduction
2. Related Work
2.1. ADS-B
2.1.1. Overview
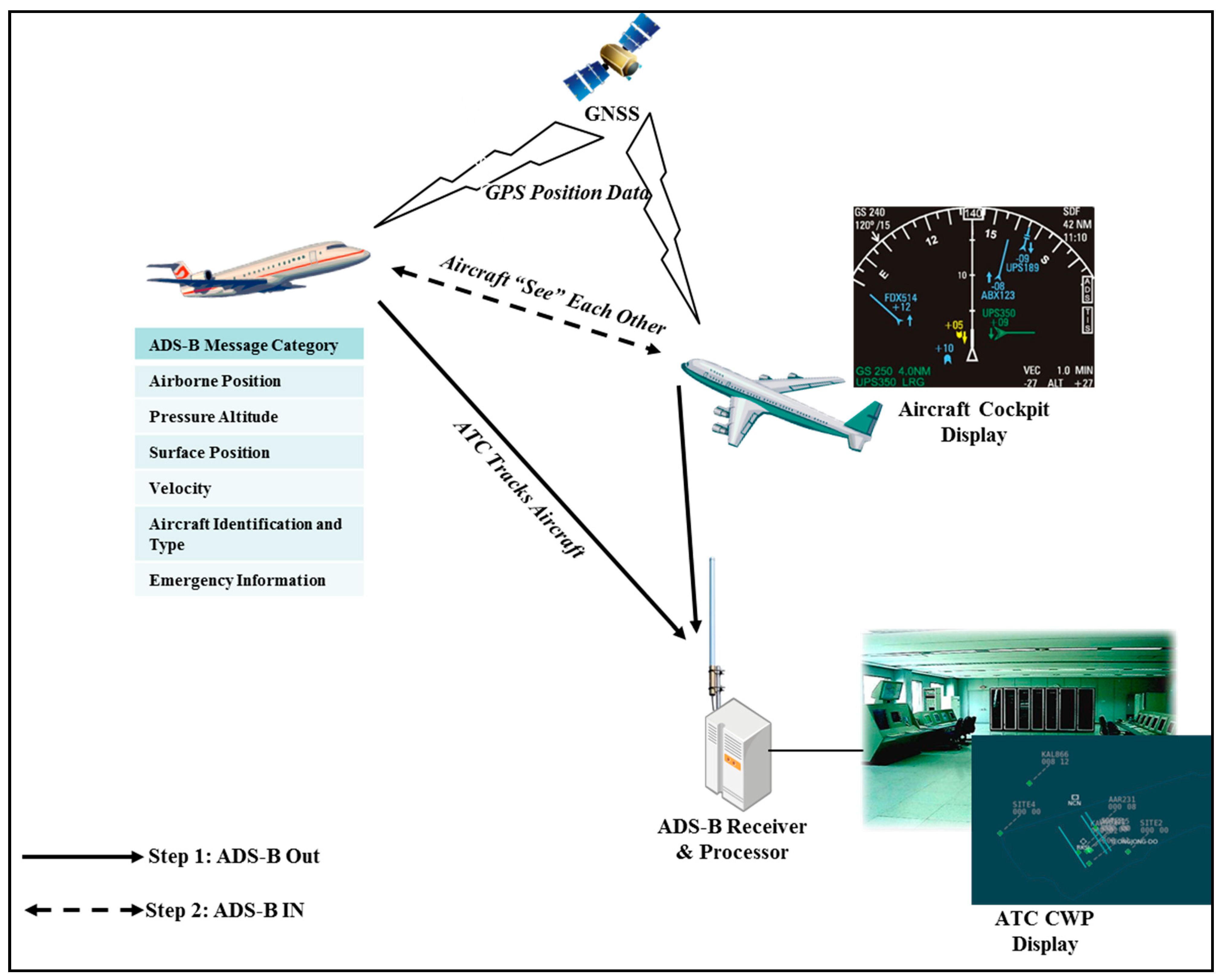
2.1.2. Security Threats
- -
- Eavesdropping
- -
- Jamming
- -
- Message Injection
- -
- Message Modification
- -
- Message Deletion
2.2. SPKI
- -
- AN SPKI certificate indicates the issuer and subject using the hash-value of the public key or the public key. Therefore, user anonymity is guaranteed.
- -
- An SPKI certificate operates without modifying the server database; authorization is easily delegated to the user.
- -
- An SPKI certificate can operate independently of any specific service.
- -
- Publication and management of SPKI certificates are relatively easy. Therefore, maintenance cost is expensive.
- -
- Restrictions and multiple delegations can be easily applied using an SPKI certificate.
2.2.1. ADS-B Sensor Identification Certificate
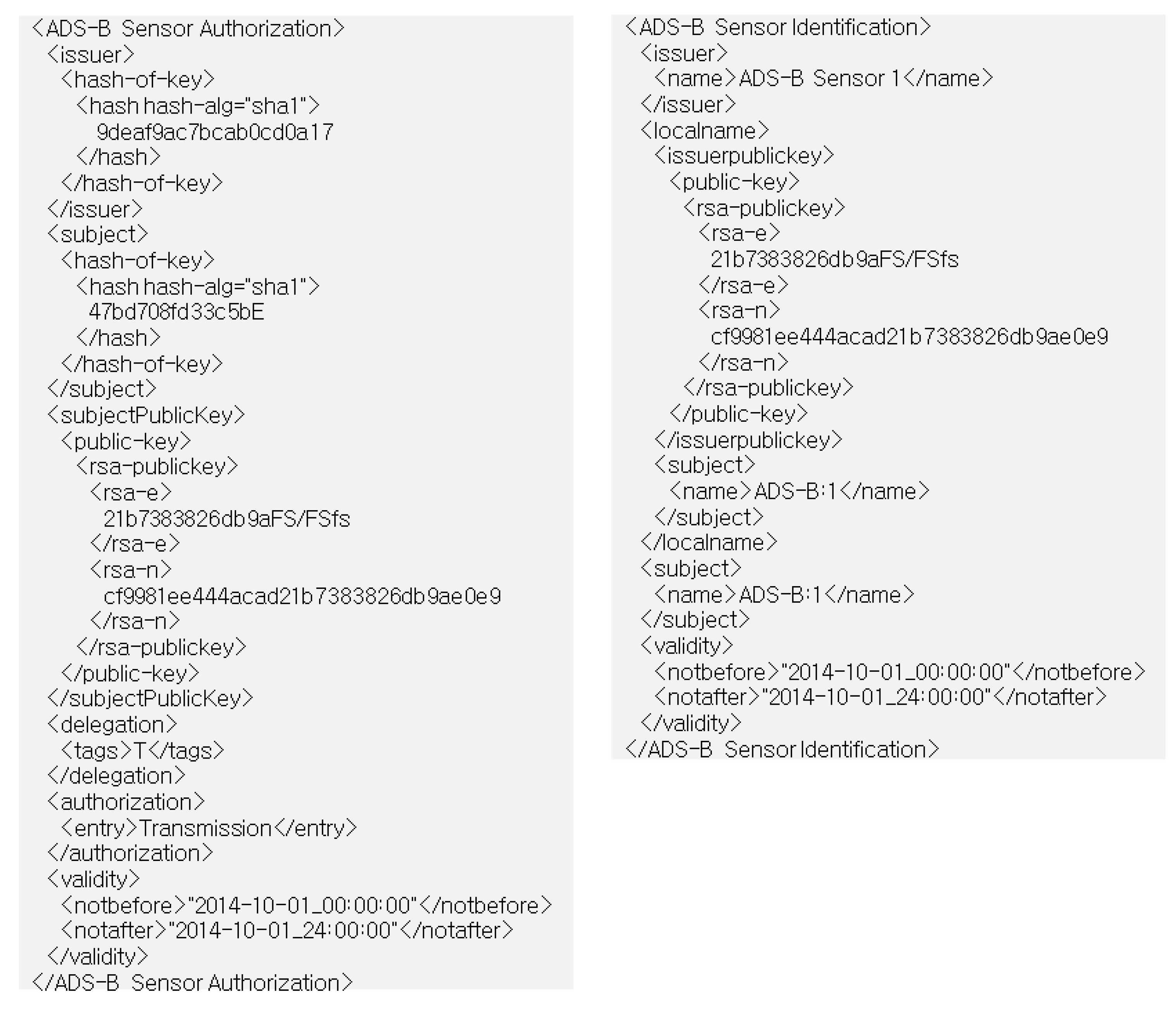
- <Issuer, Localname (Public Key Info), Subject (ADS-B ID), Validity (10/OCT/2014) > Signature (Issuer)
- - Issuer: The SPKI certificate issuer; the issuer signs the SPKI certificate with private keys.
- - Localname: This comprises the SPKI certificate issuer’s public key and one or more identifiers.
- - Subject: The subject of the SPKI certificates issue, including the unique identifiers of the ADS-B sensor.
- - Validity: Indicates the expiration date of the SPKI certificate.
2.2.2. ADS-B Sensor Authorization Certificate
- <Issuer, Subject (ADS-B ID), SubjectPublicKeyInfo, Delegation, Authorization, Validity (10/Oct/2014)>Signature (Issuer)
- - SubjectPublicKeyInfo: SPKI certificate subject public key information.
- - Delegation: Indicates the existence of authorization to transmit ADS B-data with a value of True/False.
- - Authorization: Specifies the authorization granted by ATC to the ADS-B sensor.
3. Proposed ADS-B Security Framework
3.1. ADS-B Sensor Authorization and Symmetric Keys Exchange Using the Proposed ADS-B Framework
- -
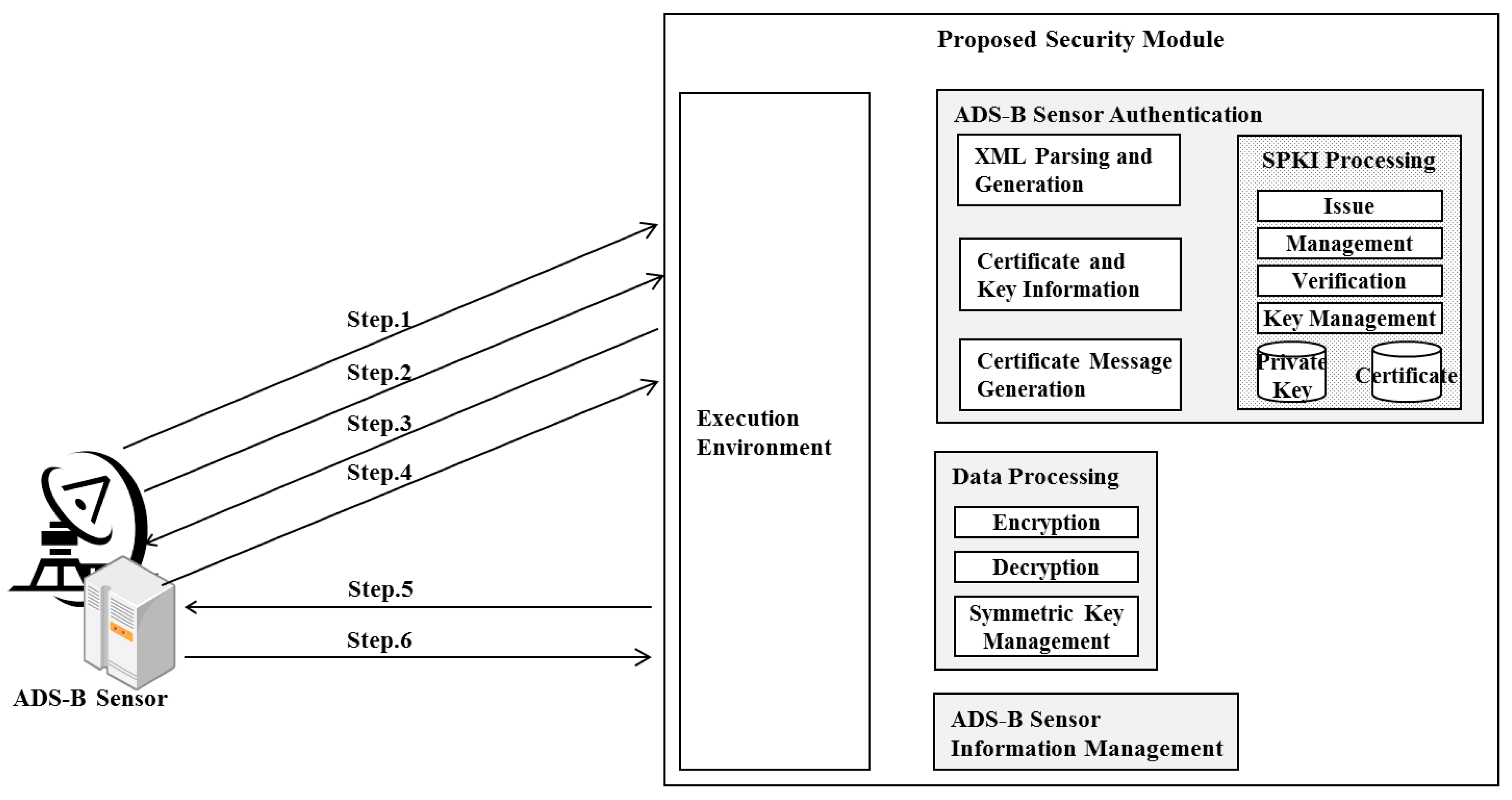
- Step 1: The ADS-B sensor generates a private/public key pair, and generates ADS-B sensor identification certificates signed with the private key in the data, and including ADS-B sensor identification information and the public key, then transmits them to ATC. An examples of the SPKI four tuple certificate generated in Figure 3 shown below:
- <ADS-B Sensor 1, ADS-B Sensor 1’s Public Key Info, ADS-B Sensor ID, 10/Oct/2014> Signature (ADS-B Sensor 1’s Private Key)
- -
- Step 2: To verify the authorization for the transmission of the received ADS-B data, the ADS-B sensor requests ADS-B sensor identification information from ATC.
- -
- Step 3: ATC validates the ADS-B sensor authorization using the ADS-B sensor identification certificates saved in Step 1 and ADS-B sensor identification information in Step 2. It then generates the ADS-B sensor authorization certificates for the ADS-B sensor whose authorization for transmission was validated, and transmits them to the ADS-B sensor. An example of the SPKI six tuple certificates generated in Figure 3 is shown below:
- <ATC, ADS-B Sensor 1, ADS-B Sensor 1’s Public Key Info, T, Transmission, 10/Oct/2014>Signature (ATC’s Private Key)
- -
- Step 4: The ADS-B that receives the ADS-B sensor authorization certificates requests symmetric keys for encryption from ATC in order to transmit the received ADS-B data.
- -
- Step 5: ATC generates symmetric keys for encrypting/decrypting the ADS-B data, signs the generated symmetric keys, encrypts the public keys of the ADS-B sensor, and then transmits them to the ADS-B sensor. Advanced Encryption Standard-128 (AES-128), for example, can be used as the symmetric cryptography algorithm.
- -
- Step 6: The ADS-B sensor validates the cryptography token received from ATC using its own private keys, acquires the symmetric keys and encryption algorithm, and encrypts and transmits the ADS-B data to ATC.
- -
- Step 7: Steps 1–6 are repeated over a predetermined period to authorize ADS-B continuously. To change the symmetric keys used to encrypt the ADS-B data, only Steps 4–6 need be repeated.
3.2. XML Signature Module

3.2.1. XML Signature Creation and Verification for Authentication
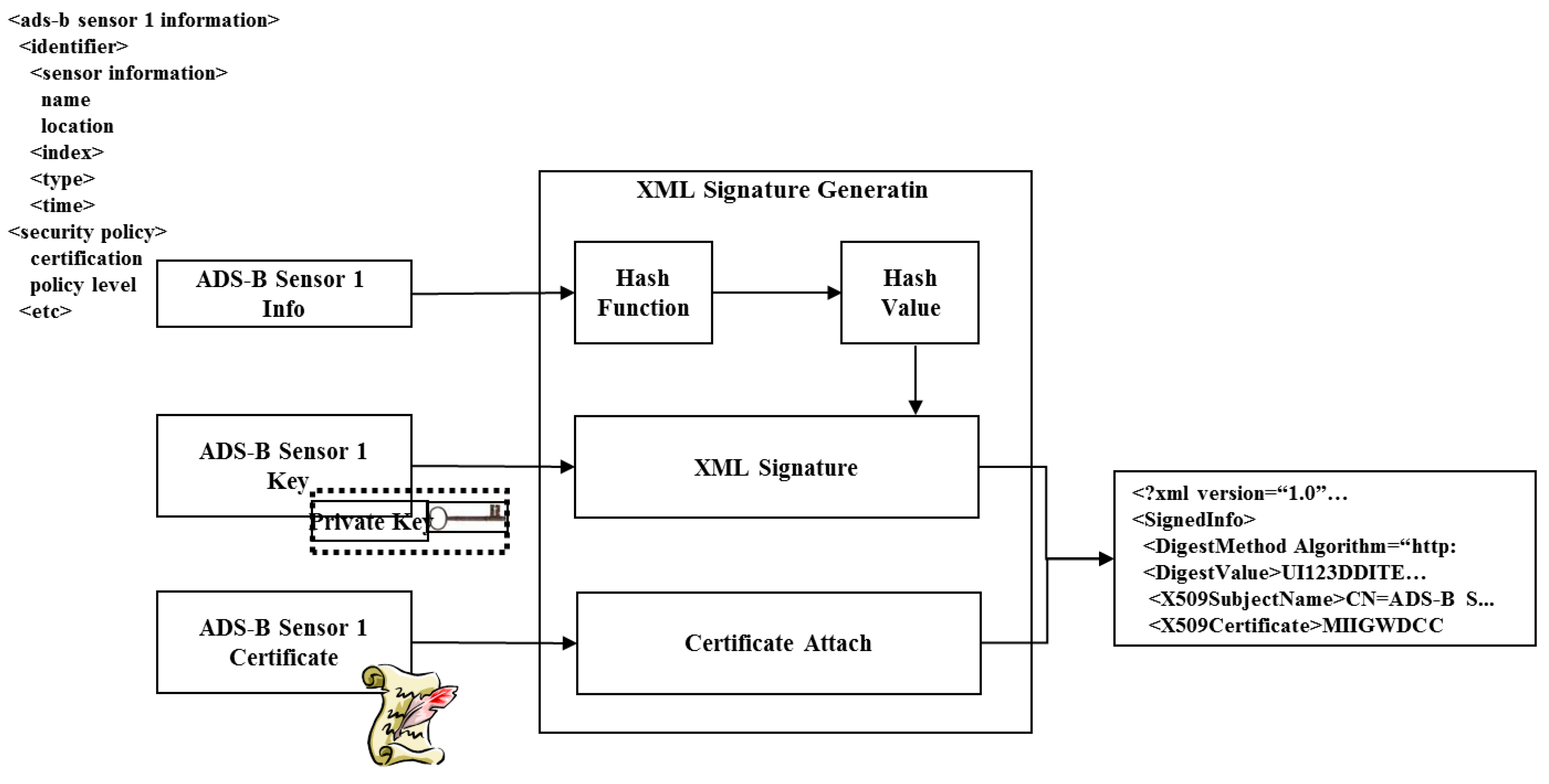
- (1)
- Create document by collecting ADS-B sensor data.
- (2)
- Sign with private key of ADS-B sensor certificate and add digest value.
- (3)
- Public key data for signature verification creates <KeyInfo> which includes SPKI certificate for the ADS-B sensor.
- (4)
- Create XML signature containing the value obtained from the above process.
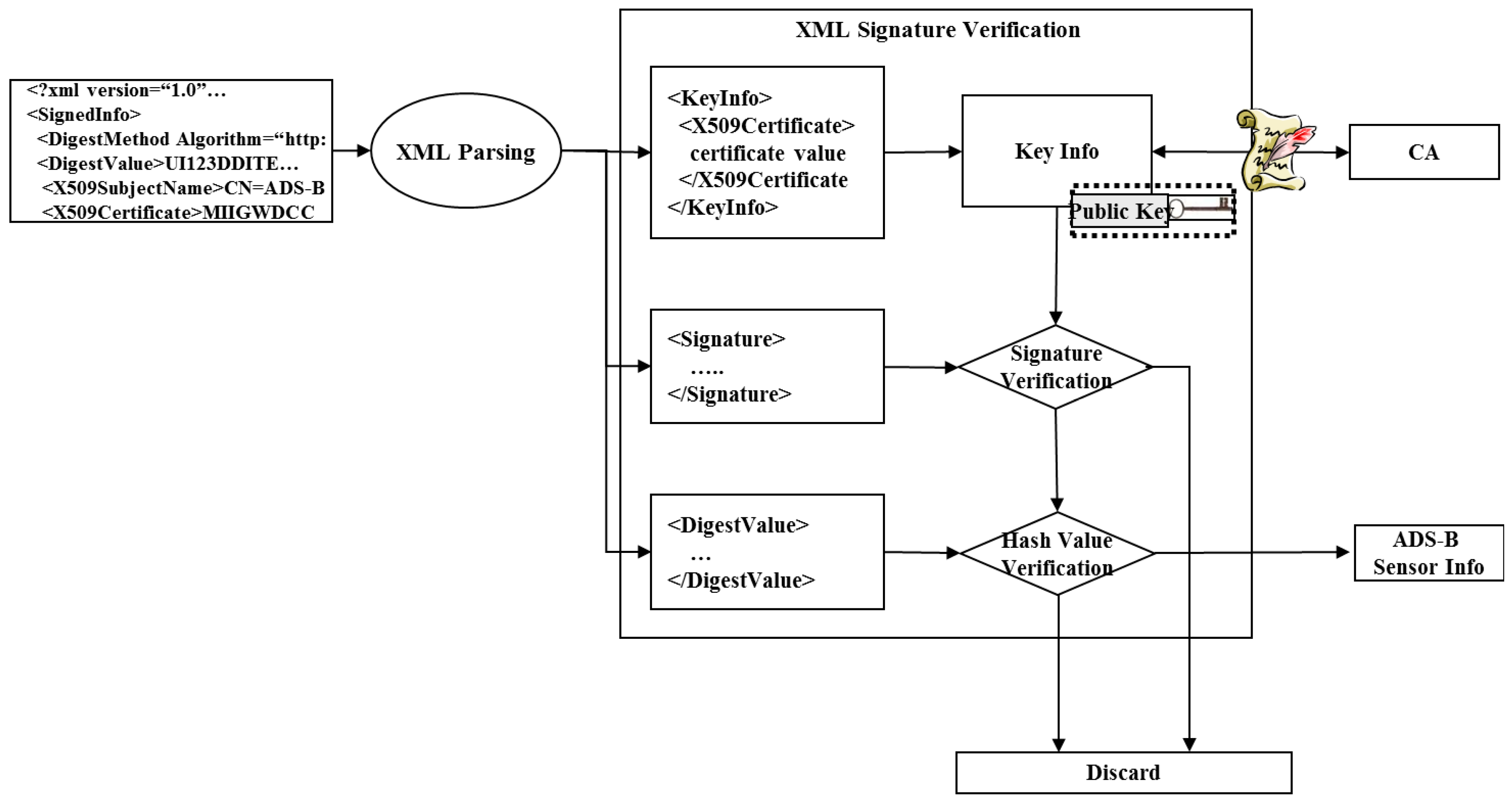
- (1)
- Separate XML signature of each attribute tag using a parser.
- (2)
- Examine the validity of the certificate contained in the <KeyInfo> tag through communication with the CA and acquire the public key value.
- (3)
- Verify the signature by decoding the signature value contained in the XML signature.
- (4)
- Verify the integrity of the signature by comparing the digest value contained in the XML signature with the hash value created through signature verification.
- (5)
- Acquire the ADS-B sensor data in the request for authentication.
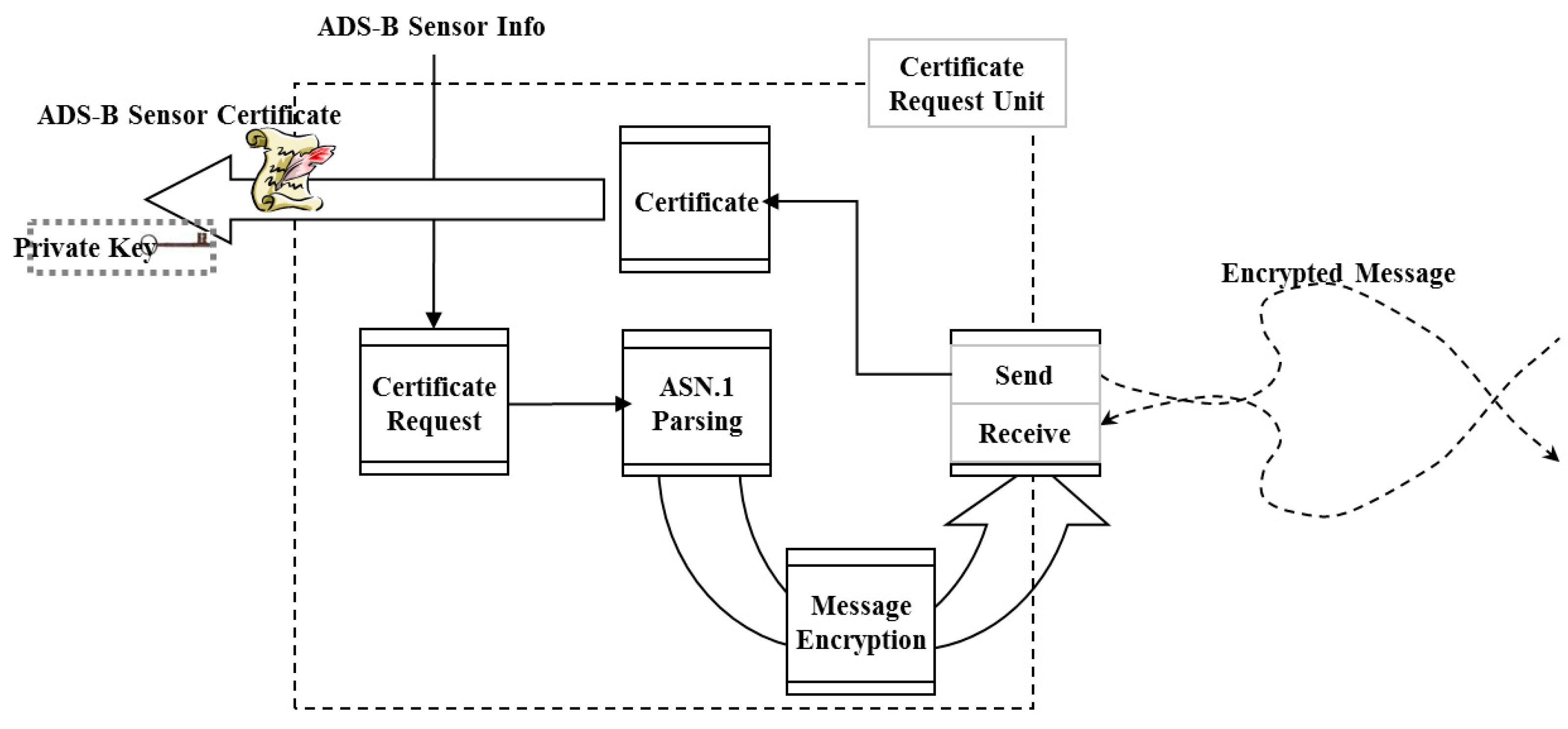
3.2.2. Creation and Transmission of SPKI Certificate
- -
- ASN.1 Parsing Unit: A data structure creation unit that creates data for certification in the international standard regulation certificate request message format.
- -
- Encryption Unit: A unit that encrypts data for the security service for certificate request data.
- -
- Transmission Unit: A send/receive unit for encrypted data.
- -
- Certificate & Private Key: A unit to acquire the created SPKI certificate and private key for ADS-B from CA and transmit them to the ADS-B sensor.
4. Conclusion
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Global Air Navigation Plan for CNS/ATM Systems (Doc 9550 AA/963), 2nd ed.; ICAO: Chicago, IL, USA, 2002.
- Wikipedia: Automatic Dependent surveillance-broadcast. Available online: http://en.wikipedia.org/wiki/Automatic_dependent_surveillance-broadcast (accessed on 18 November 2014).
- Vigier, C. Automatic Dependent Surveillance Broadcast (ADS-B): Communication development for Air Traffic Management. AIRBUS FAST 2011, 47, 8–13. [Google Scholar]
- Australian Government Civil Aviation Safety Authority, ADS-B; Civil Aviation Safety Authority: Woden, Australia, 2012.
- Lee, S.-H.; Kim, Y.-K.; Lee, D.-G. Conformance monitoring method based 4D trajectory modeling using aircraft performance data. J. Converg. 2014, 5, 28–36. [Google Scholar]
- Kim, Y.-K.; Lee, D.-G.; Han, J.-W.; Park, H.-D. Ground speed calculation using wind component information for trajectory prediction. J. Converg. 2013, 4, 1–5. [Google Scholar]
- Singh, R.; Singh, P.; Duhan, M. An effective implementation of security based algorithmic approach in mobile adhoc networks. Hum.-centric Comput. Inf. Sci. 2014, 4. [Google Scholar] [CrossRef]
- Cho, M.; Lee, I.-H. Optical image encryption and decryption considering wireless communication channels. J. Inf. Process. Syst. 2014, 10, 215–222. [Google Scholar]
- Peng, K. A secure network for mobile wireless service. J. Inf. Process. Syst. 2013, 9, 247–258. [Google Scholar] [CrossRef]
- Strohmeier, M.; Lenders, V.; Martinovic, I. Security of ADS-B: State of the art and beyond. 2013; arXiv:1307.3664v1. [Google Scholar]
- McCallie, D.; Butts, J.; Mills, R. Security analysis of the ADS-B implementation in the next generation air transportation system. Int. J. Crit. Infrastruct. Prot. 2011, 4, 78–87. [Google Scholar] [CrossRef]
- Wilhelm, M.; Martinovic, I. Short paper: Reactive jamming in wireless networks: How realistic is the threat? In Proceedings of the Fourth ACM Conference on Wireless Network Security, Hamburg, Germany, 14–17 June 2011; pp. 47–52.
- Schäfer, M.; Lenders, V.; Martinovic, I. Experimental analysis of attacks on next generation air traffic communication. In Applied Cryptography and Network Security, Proceedings of 11th International Conference, ACNS 2013; Banff, Canada, 25–28 June 2013, Jacobson, M., Locasto, M., Mohassel, P., Safavi-Naini, R., Eds.; Lecture Notes in Computer Science, Volume 7954; Springer: Berlin/Heidelberg, Germany, 2013; pp. 253–271. [Google Scholar]
- Pöpper, C.; Tippenhauer, N.O.; Danev, B.; Capkun, S. Investigation of signal and message manipulations on the wireless channel. In Computer Security-ESORICS 2011, Proceedings of 16th European Symposium on Research in Computer Security; Leuven, Belgium, 12–14 September 2011, Atluri, V., Diaz, C., Eds.; Lecture Notes in Computer Science, Volume 6879; Springer: Berlin/Heidelberg, Germany, 2011; pp. 40–59. [Google Scholar]
- Wilhelm, M.; Schmitt, J.B.; Lenders, V. Practical message manipulation attacks in IEEE 802.15.4 wireless networks. In Proceedings of MMB & DFT 2012, Kaiserslautern, Germany, 19–21 March 2012.
- Costin, A.; Francillon, A. Ghost in the Air (Traffic): On insecurity of ADS-B protocol and practical attacks on ADS-B devices. In Proceedings of Black Hat USA 2012, Las Vegas, NV, USA, 21–26 July 2012.
- Renderlab. Hackers + Airplanes = No Good Can Come Of This. In Proceedings of Defcon 20, Las Vegas, NV, USA, 26–29 July 2012.
- Orlando, V.A. Automatic Dependent Surveillance Broadcast (ADS-B). MIT Lincoln Laboratory. Available online: http://adsb.tc.faa.gov/WG3_Meetings/Meeting8/Squitter-Lon.pdf (accessed on 20 November 2014).
- Gnanaraj, J.W.K.; Ezra, K.; Rajsingh, E.B. Smart card based time efficient authentication scheme for global grid computing. Hum-centric Comput. Inf. Sci. 2013, 3, 1–14. [Google Scholar] [CrossRef]
- Chung, Y.; Choi, S.; Won, D. Lightweight anonymous authentication scheme with unlink ability in global mobility networks. J. Converg. 2013, 4, 23–29. [Google Scholar]
- Ellison, C.; Frantz, B.; Lampson, B.; Rivest, R.; Thomas, B.; Ylonen, T. SPKI Certificate Theory (RFC 2693). IETF, 1999. Available online: http://www.ietf.org/rfc/rfc2693.txt (accessed on 20 November 2014).
- Lee, Y.-L.; No, B.-N. SPKI/SDSI HTTP secure server to support role-based access control & confidential communication. J. Korea Inst. Inf. Secur. Cryptol. 2002, 12, 29–46. [Google Scholar]
© 2014 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lee, S.-H.; Kim, Y.-K.; Han, J.-W.; Lee, D.-G. Protection Method for Data Communication between ADS-B Sensor and Next-Generation Air Traffic Control Systems. Information 2014, 5, 622-633. https://doi.org/10.3390/info5040622
Lee S-H, Kim Y-K, Han J-W, Lee D-G. Protection Method for Data Communication between ADS-B Sensor and Next-Generation Air Traffic Control Systems. Information. 2014; 5(4):622-633. https://doi.org/10.3390/info5040622
Chicago/Turabian StyleLee, Seoung-Hyeon, Yong-Kyun Kim, Jong-Wook Han, and Deok-Gyu Lee. 2014. "Protection Method for Data Communication between ADS-B Sensor and Next-Generation Air Traffic Control Systems" Information 5, no. 4: 622-633. https://doi.org/10.3390/info5040622



