A Comparison of RFID Anti-Collision Protocols for Tag Identification
Abstract
:1. Introduction
2. Background
2.1. The Collision Problem
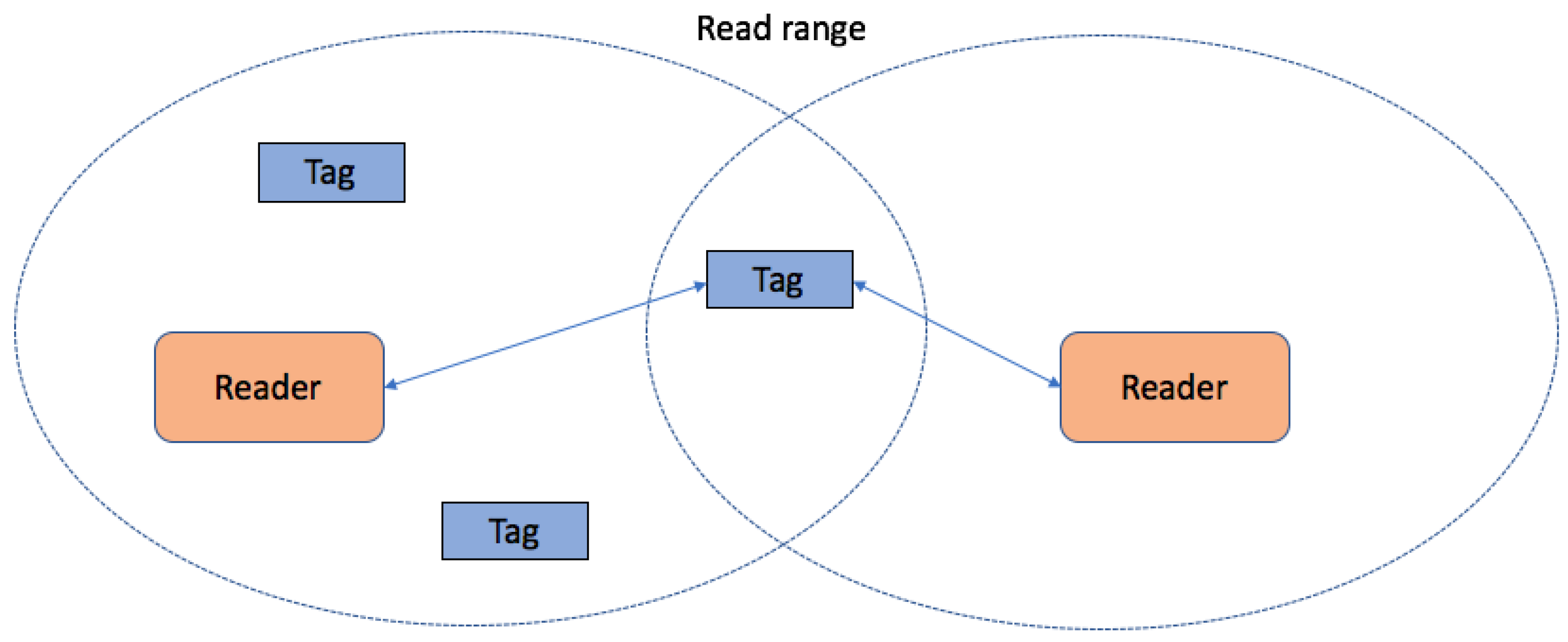
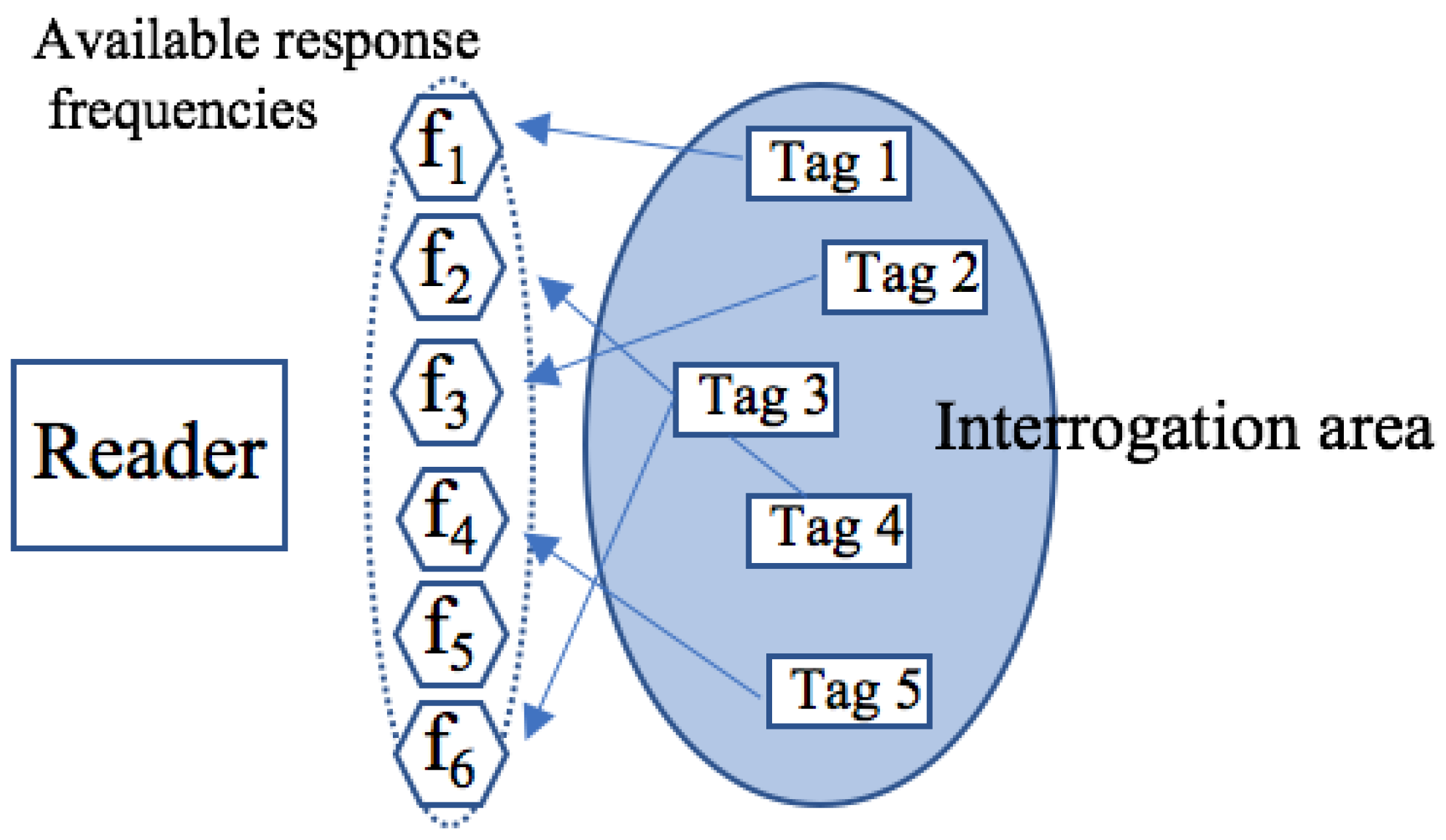
- Reader collision occurs when the reader attempts to make communication with tags that are in the coverage area of another reader [7]. This type of collision is shown in Figure 1. This collision causes two different problems:
- -
- Signal interference occurs when the fields of two or more readers overlap and interfere. This problem can be solved by programming all readers to read at fractionally different times.
- -
- Multiple reads of the same tag occur when the same tag is read once by every overlapping reader.
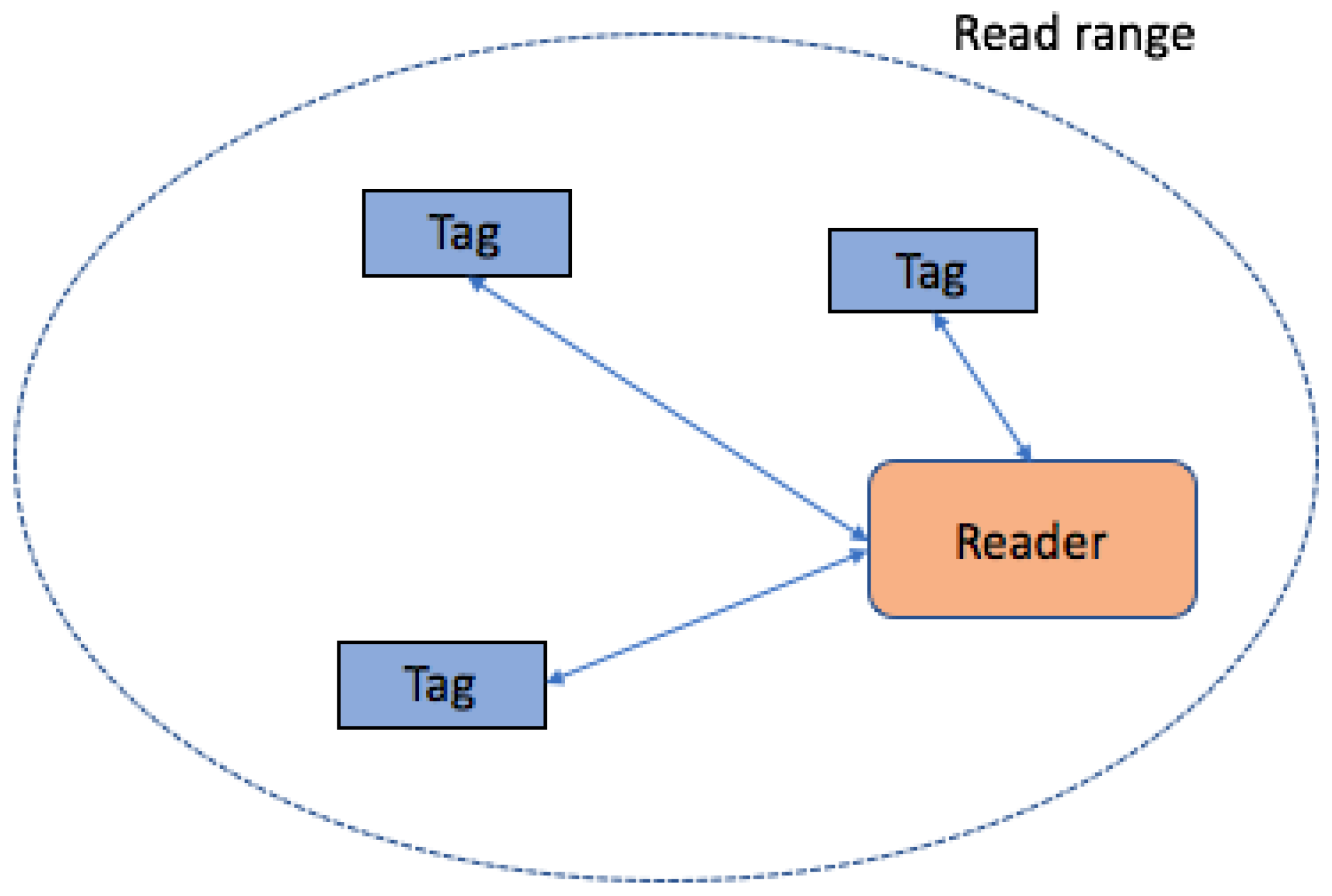
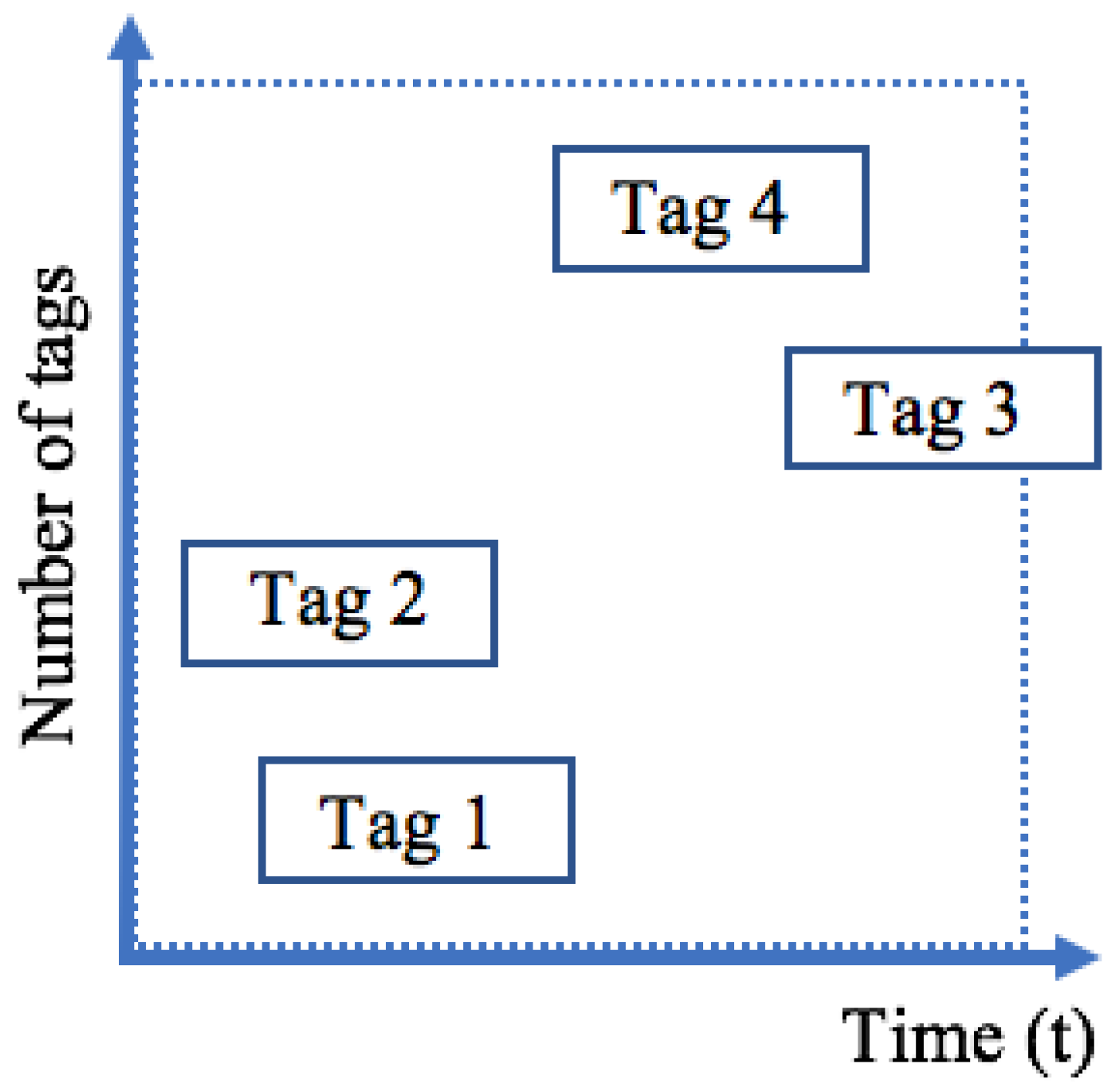
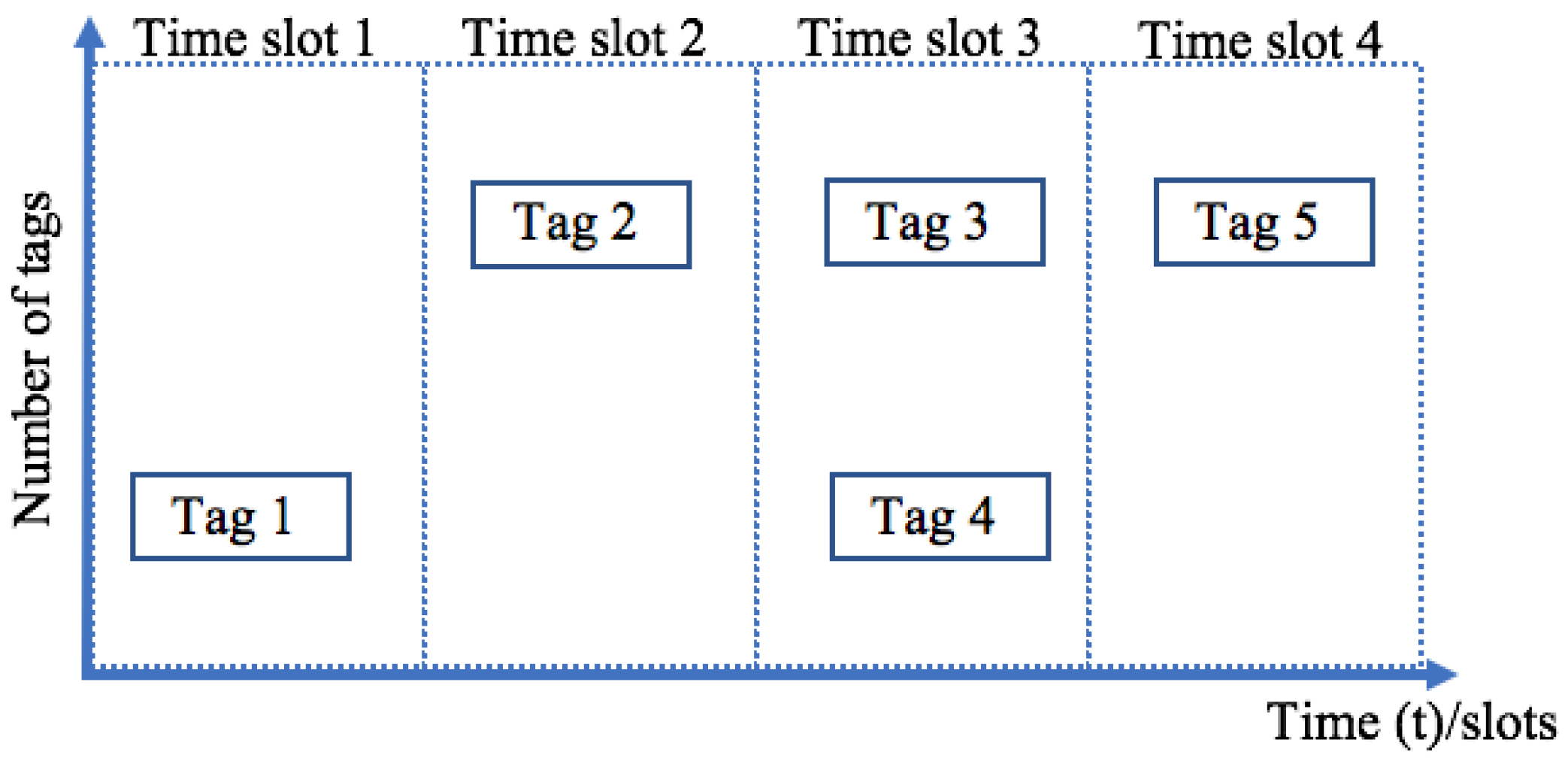
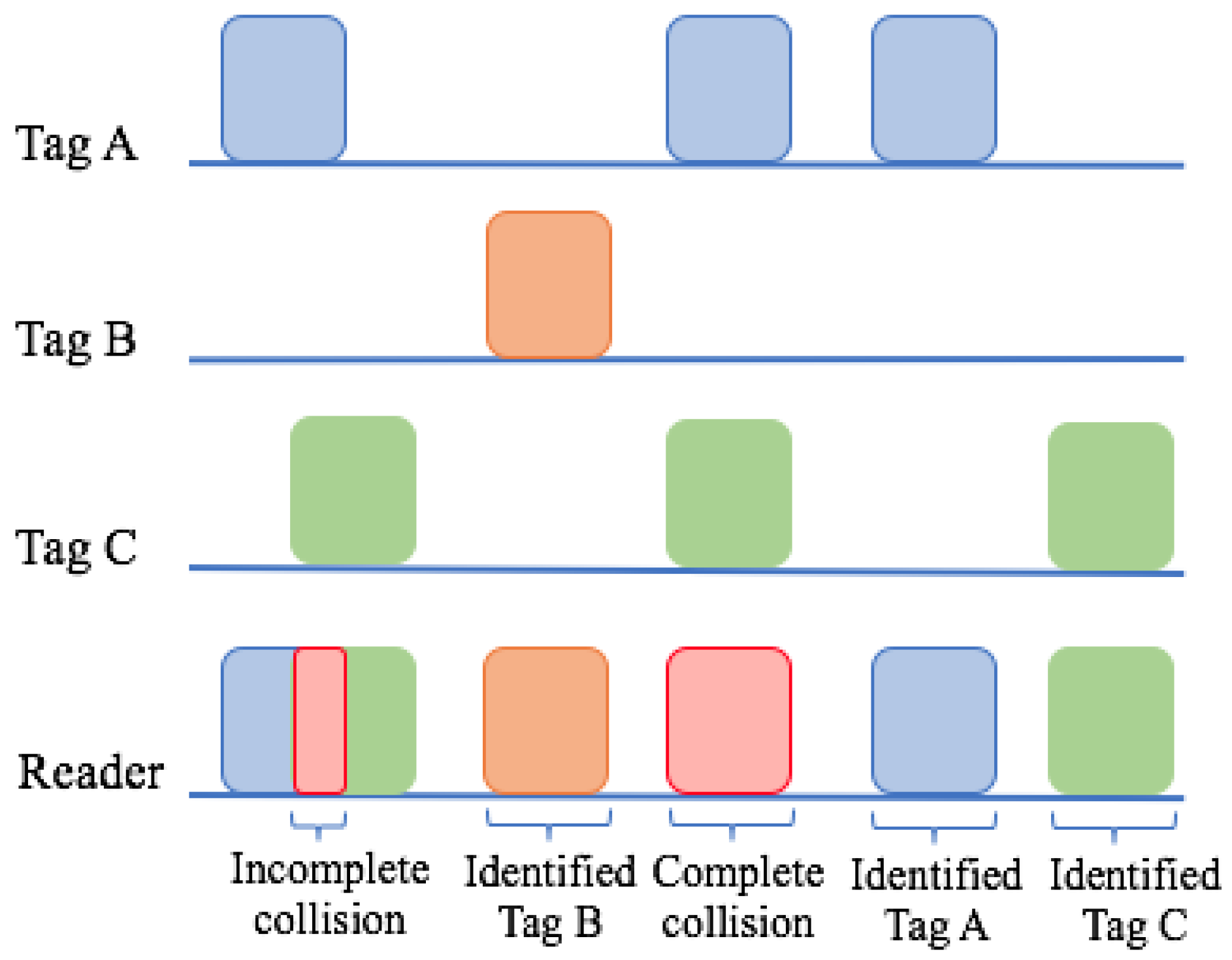
- A tag collision occurs when more than one tag attempts to transmit its ID at the same time: the reader will receive a mixture of the tags’ signals and cannot understand it. This type of collision is shown in Figure 2.
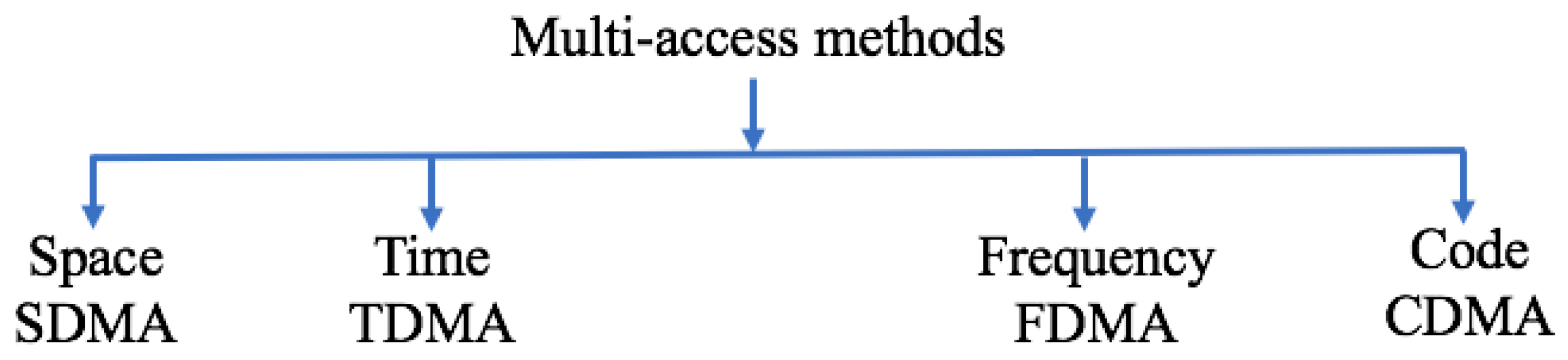
2.2. Multi-Access Methods
3. Aloha Protocols
3.1. Pure Aloha
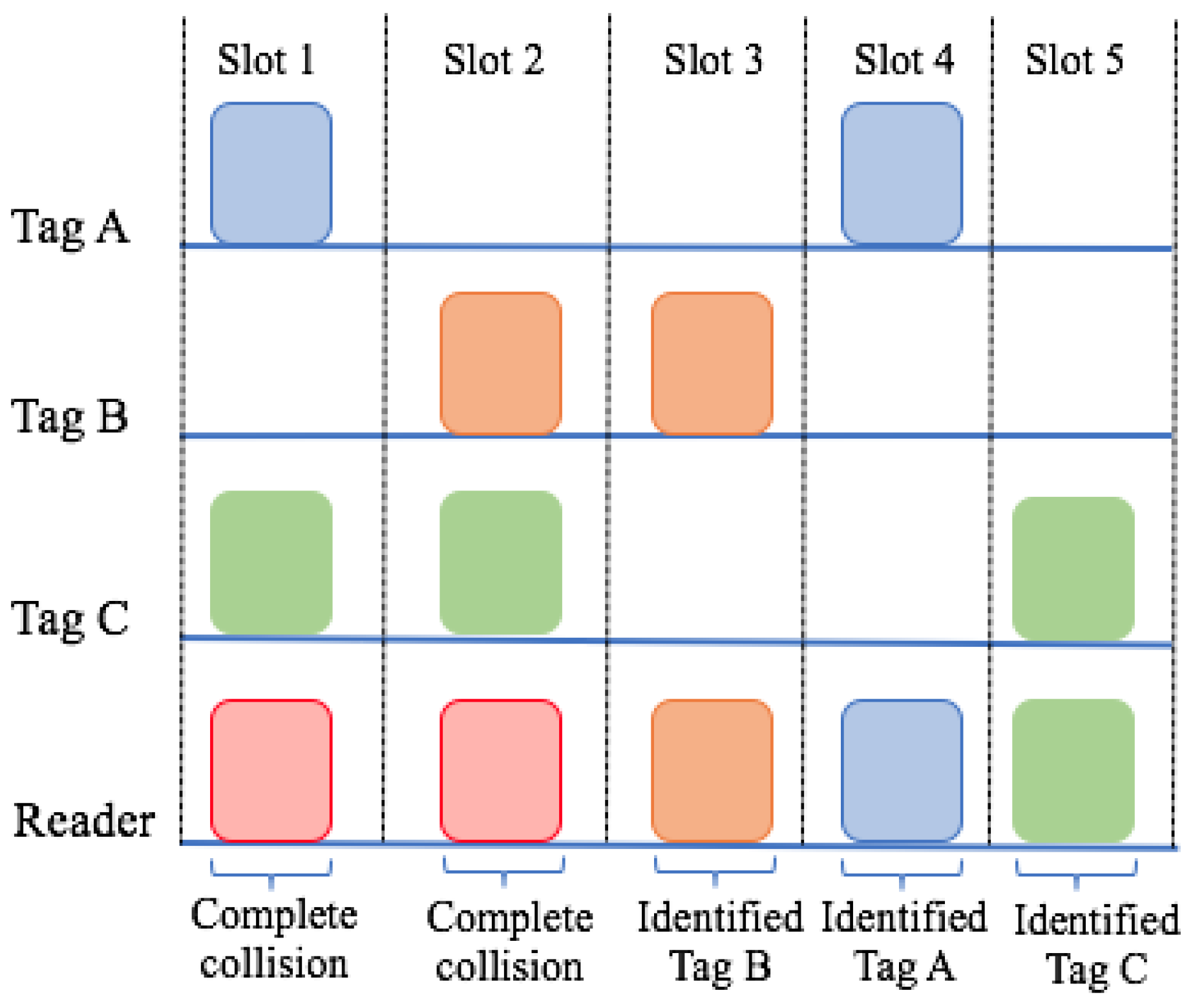
3.2. Slotted Aloha
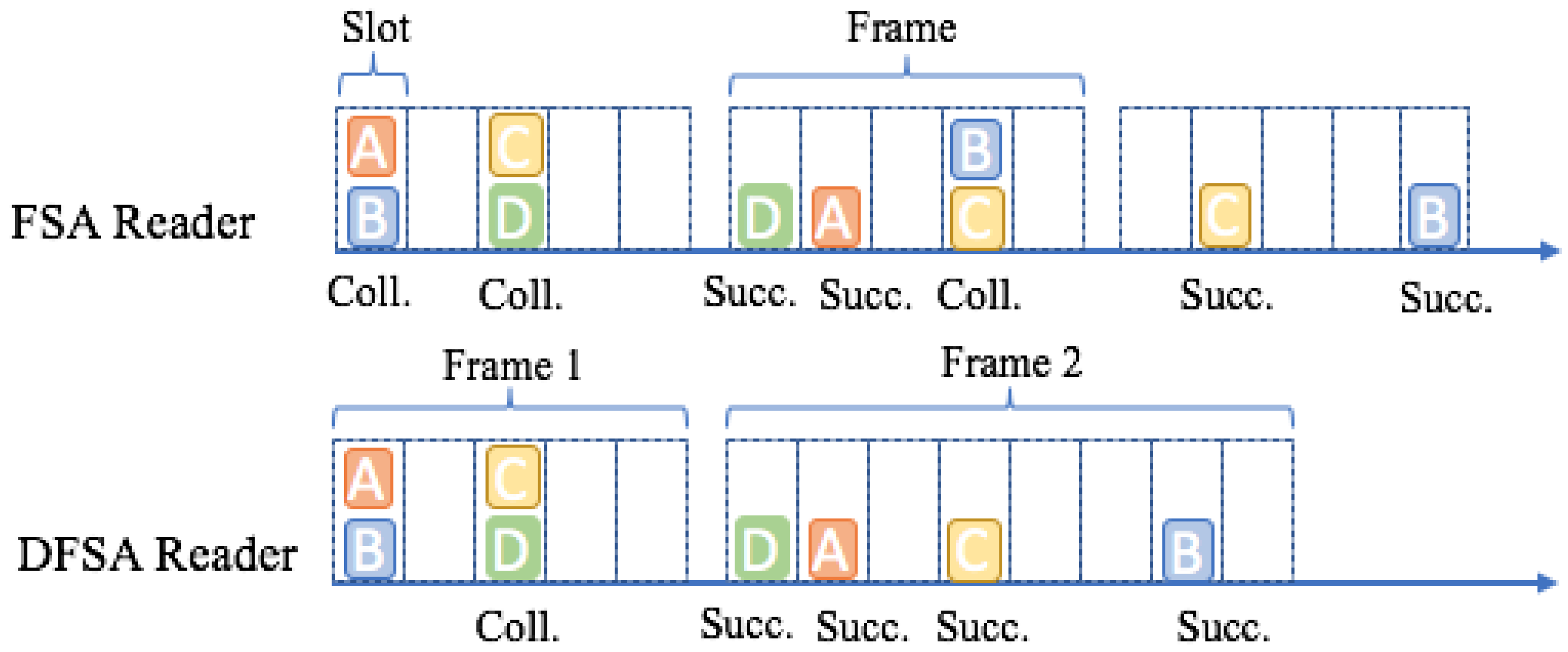
3.3. Framed Slotted Aloha and Dynamic Framed Slotted Aloha
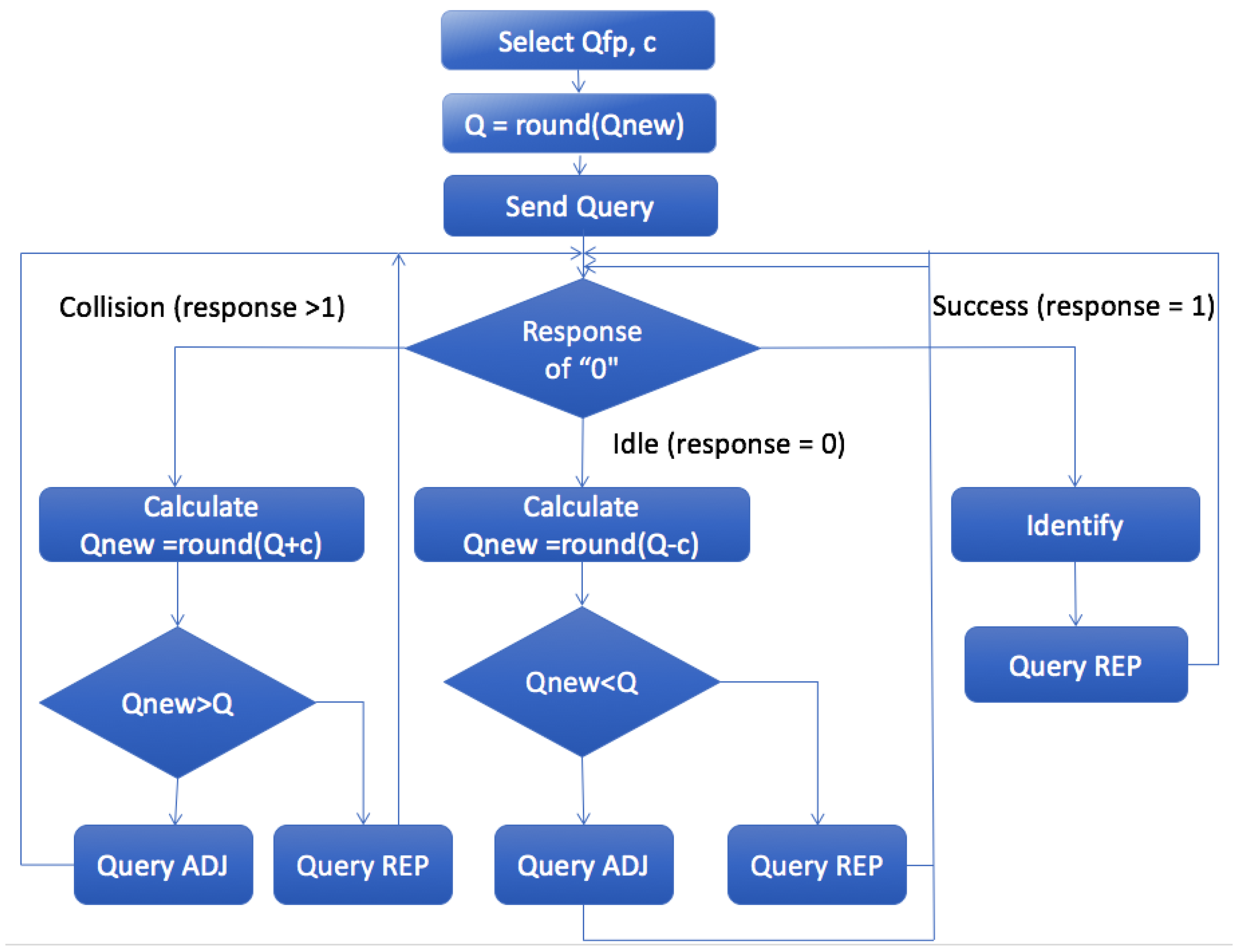
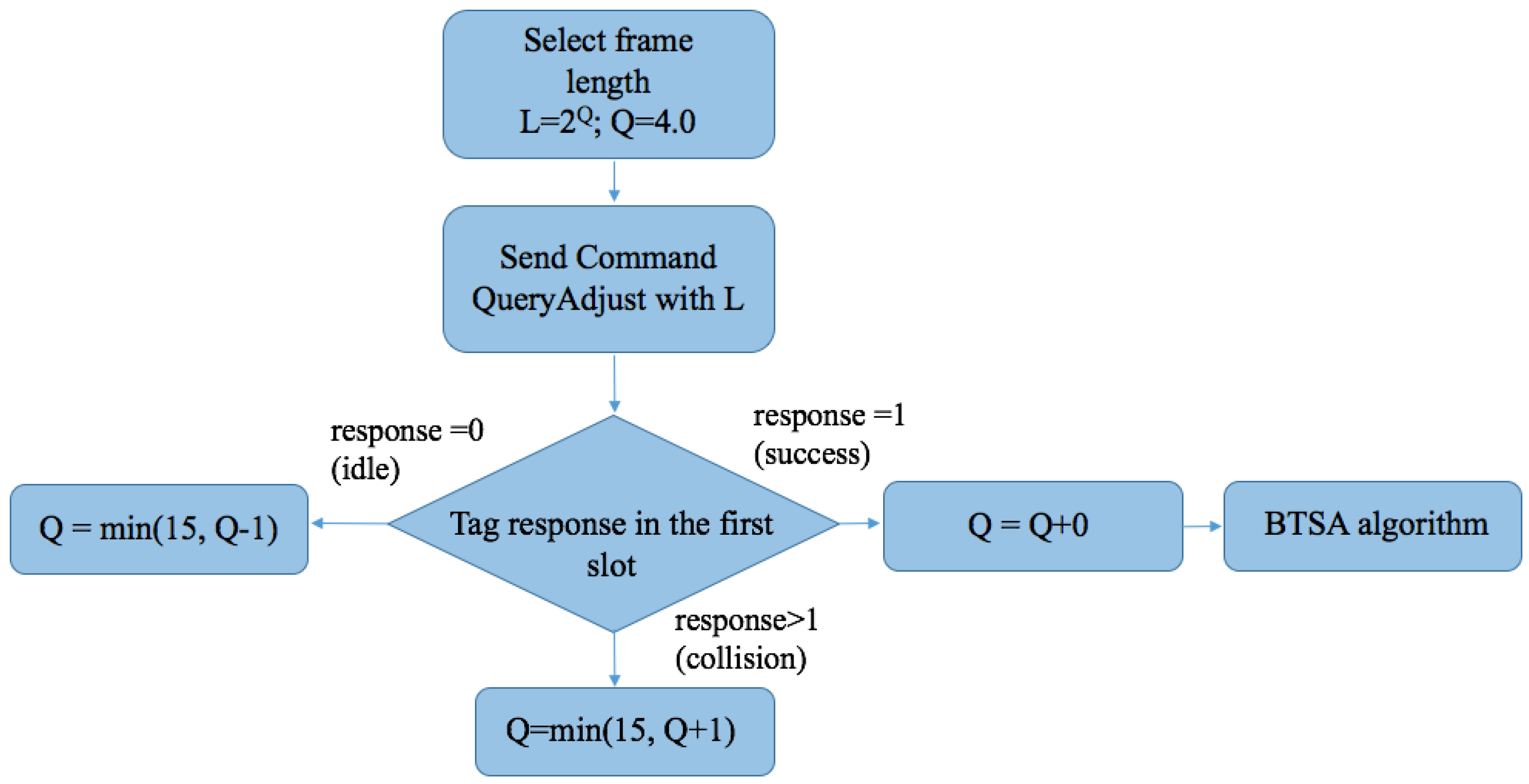
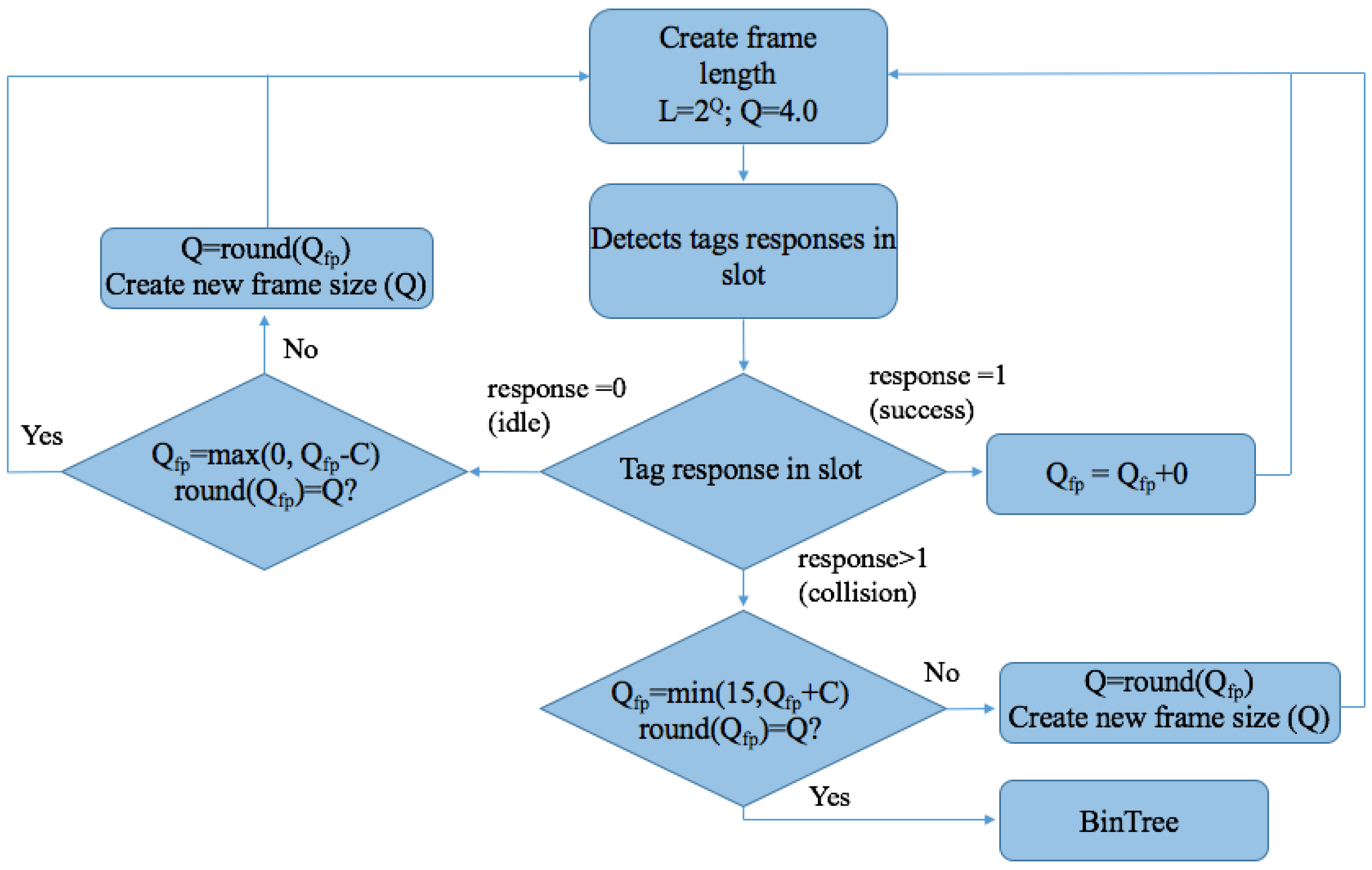
Q Protocol
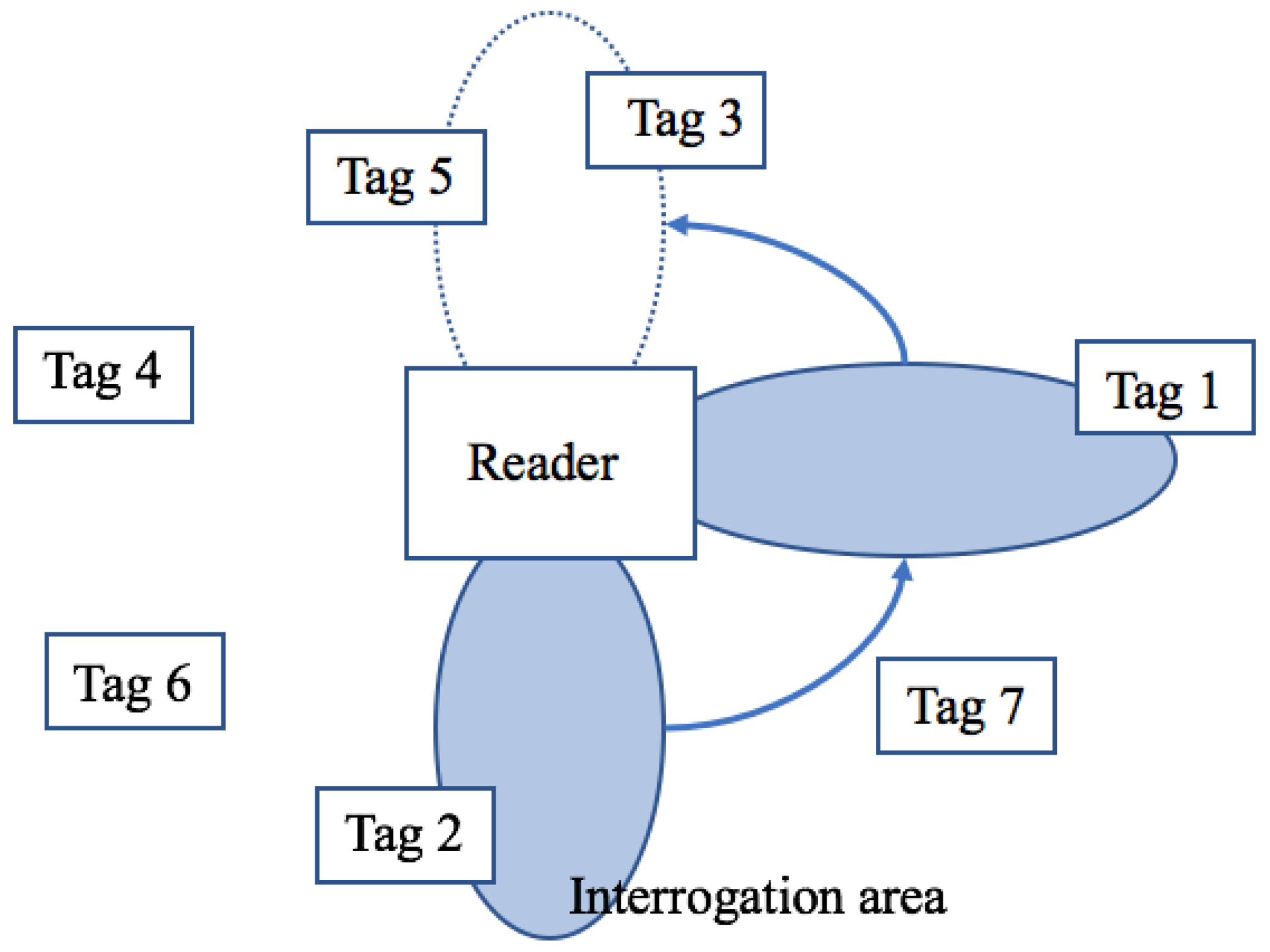
- Query command, transmitted by the reader to all tags in the interrogation area, in order to force all tags to choose a slot number (SN) from . This command initiates the identification process by providing a new value of Q.
- QueryAdjust is the command used to instruct all tags to increase, decrease, or maintain the Q value unchanged and to reselect their SN. denotes the last calculated Q. Accordingly, Q could be increased by c, decreased by c, or left unchanged, according to the algorithm.
- QueryRep is used in order to notify all tags to decrease their SN by 1.
- Successful reply. If only one tag responds and the reader successfully received RN16. Subsequently, the reader sends the ACK and only the tag that successfully responded recognizes the ACK and reports its EPC to the reader.
- Collided reply. If more than one tag transmits RN16, a collision occurs. Then, the tags will increase by the constant c. Typical values for c are 0.1 < c < 0.5. The value of c is adjusted according to the type of application. Higher values of c will provide more aggressive frame adjustments.
- No reply. When no tags respond in the slot, the reader decreases by c.
4. Tree-Based Protocols
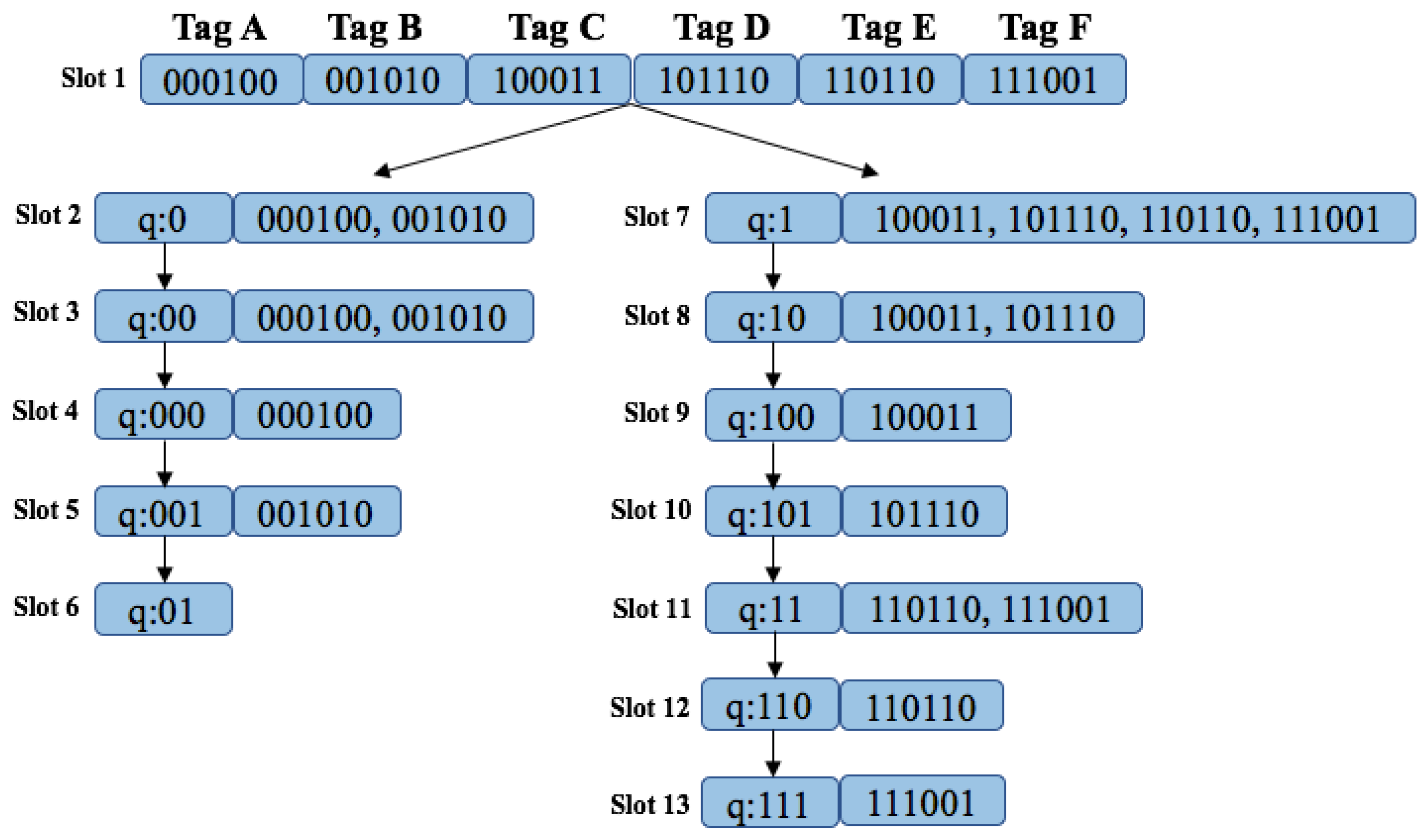
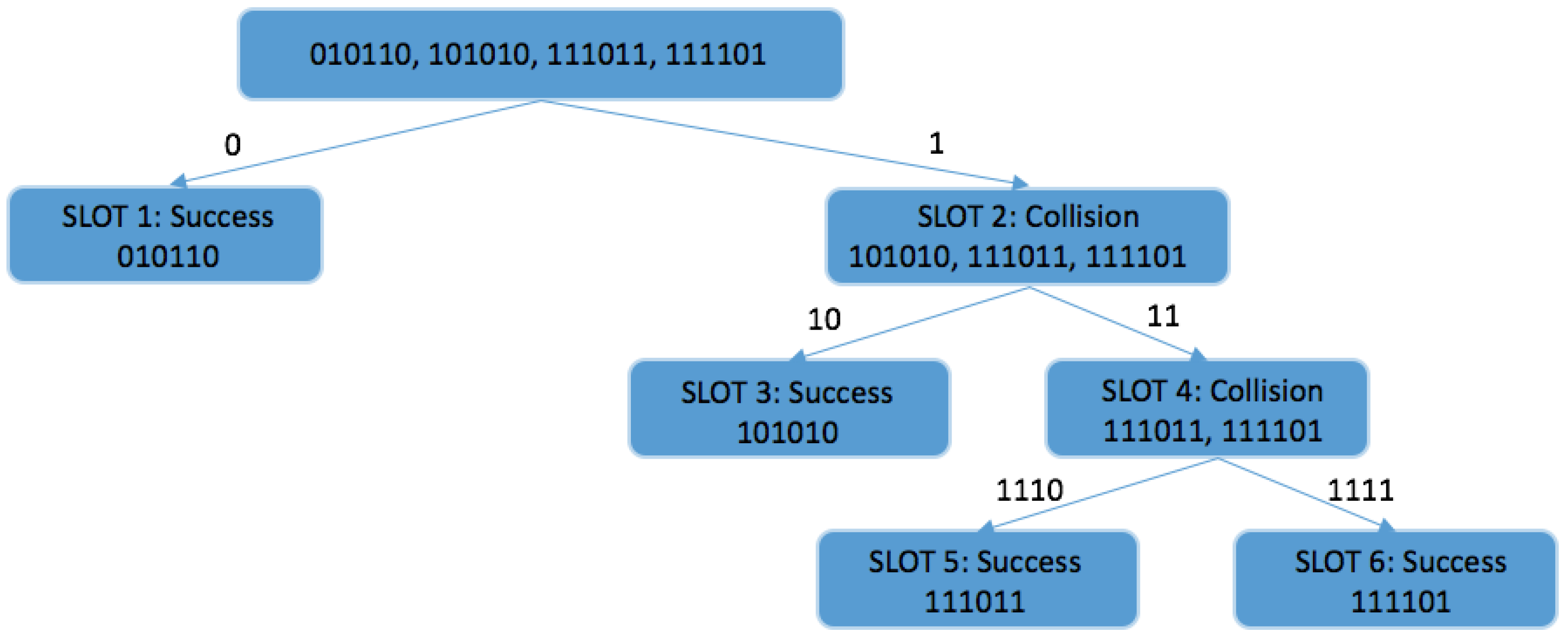
4.1. Query Tree Protocol
4.2. Smart Trend Traversal Protocol
- A collision occurs when the QTP is at too high a certain level and should be moved down by adding a longer prefix to the query. Consequently, the reader appends t bits of 0’s to the last query, where t = s + − 1. Let s denote the minimum increase, and be the number of consecutive colliding slots.
- An idle slot occurs when no tag responds to a reader query. QTP needs to traverse up just one level, which can lead to a new collision. This rule will be applied only to the right side. If the empty response comes from the left side of the tree, QTP must move horizontally to the right. The reader will decrease the query length by m bits, where m = s + − 1 and is the number of consecutive idle slots.
- Upon a successful response, a single node is visited, indicating that the tag has been successfully identified by the reader. Then QTP moves to the symmetric node if the query finishes with a 0, but it returns one level if the query finishes with a 1.
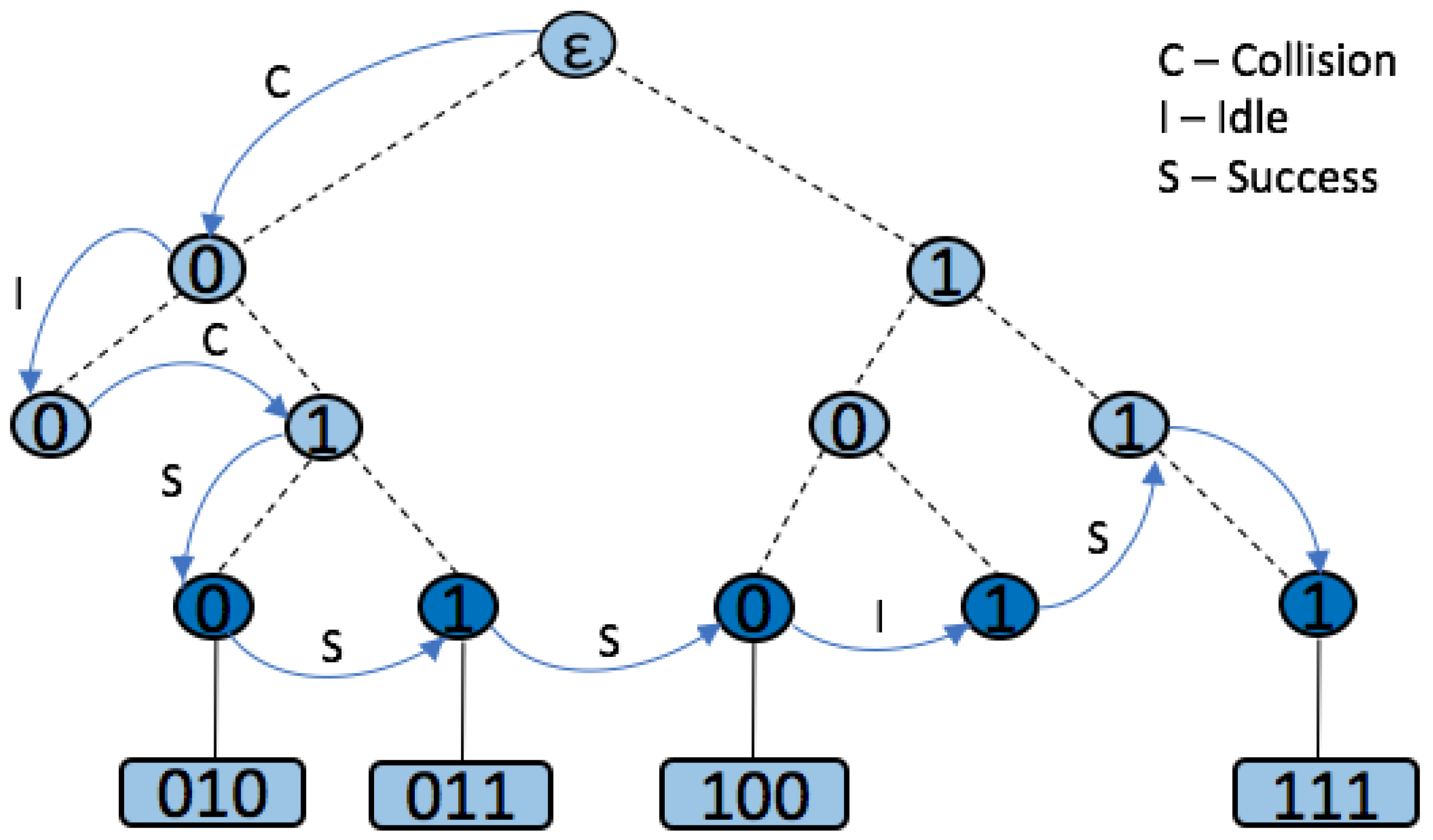
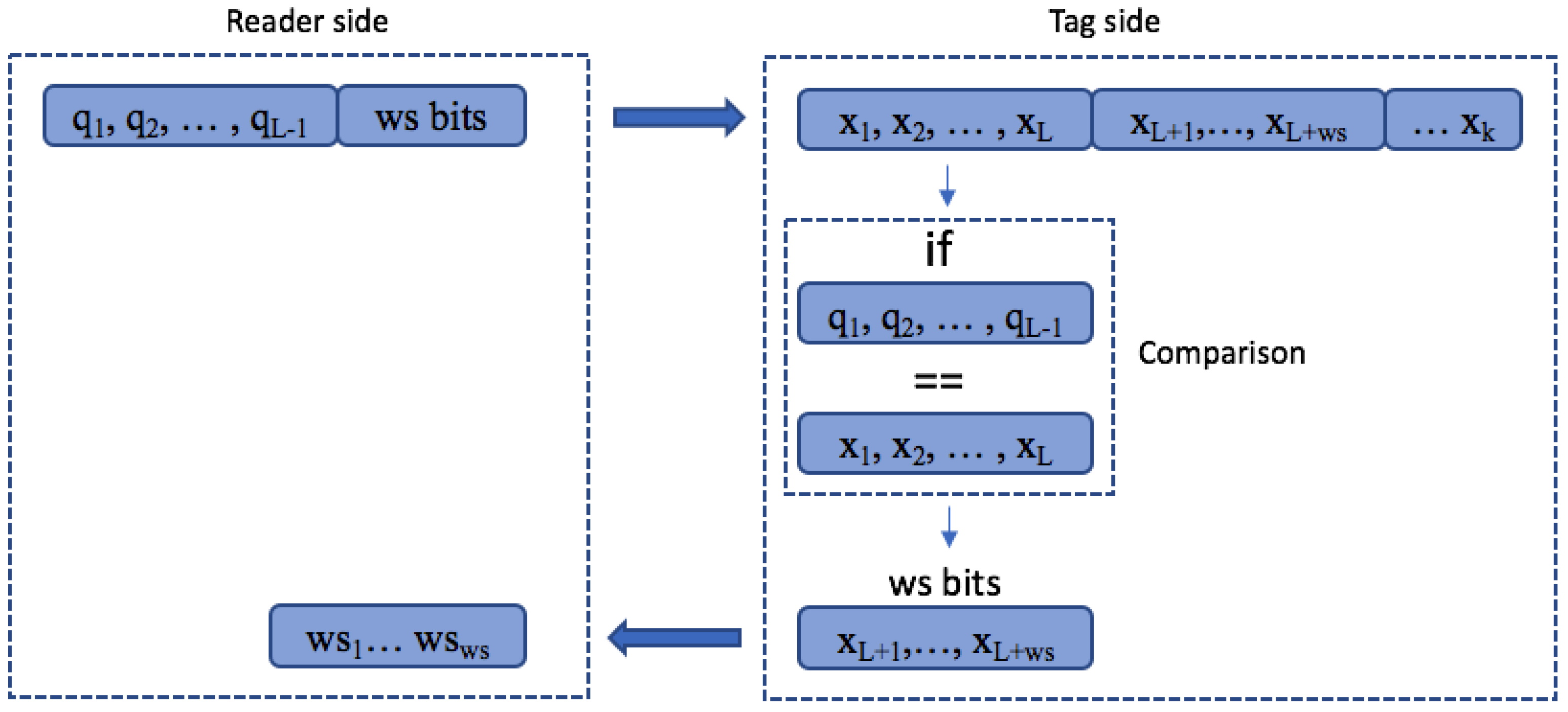
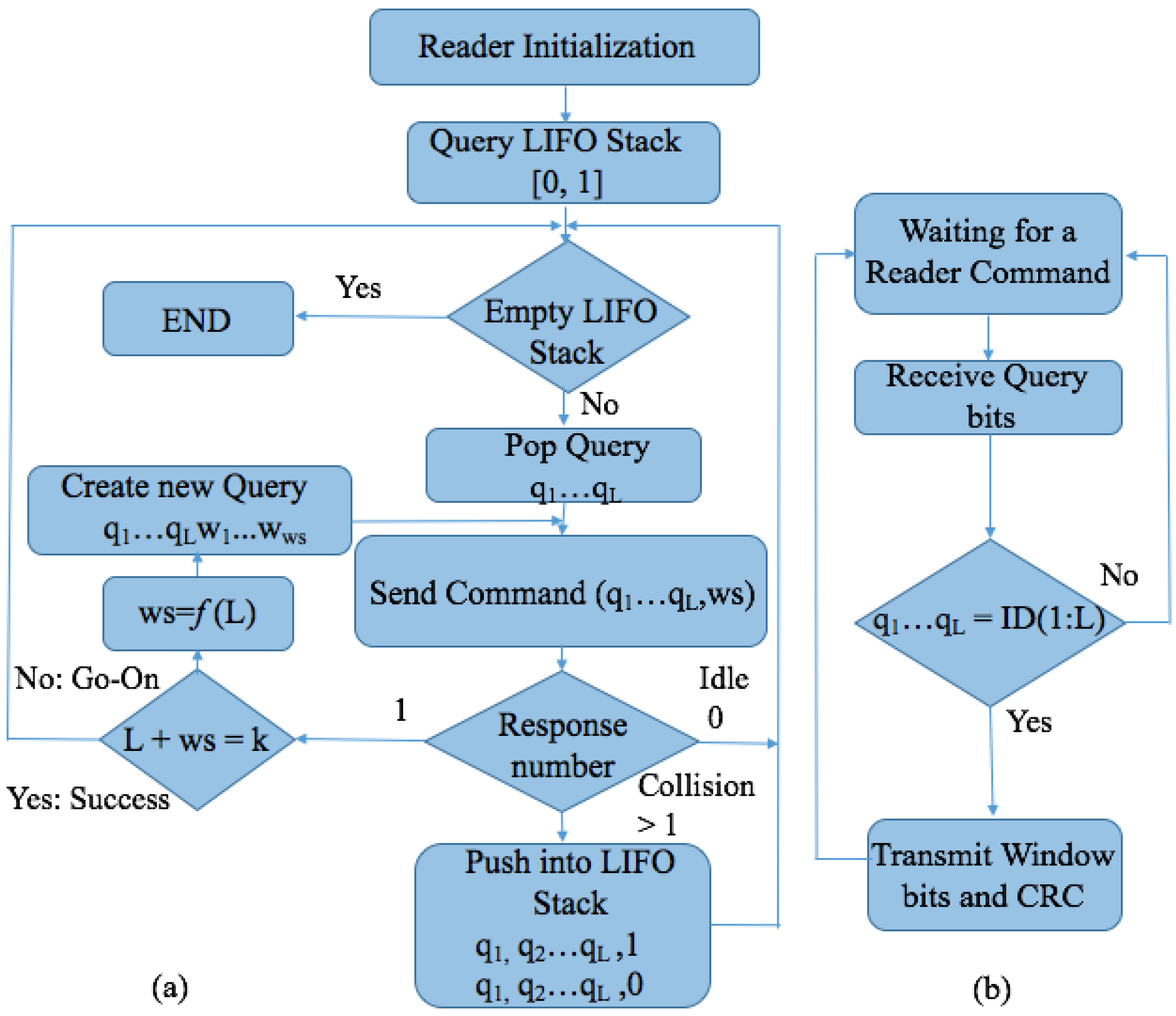
4.3. Window Based Protocols
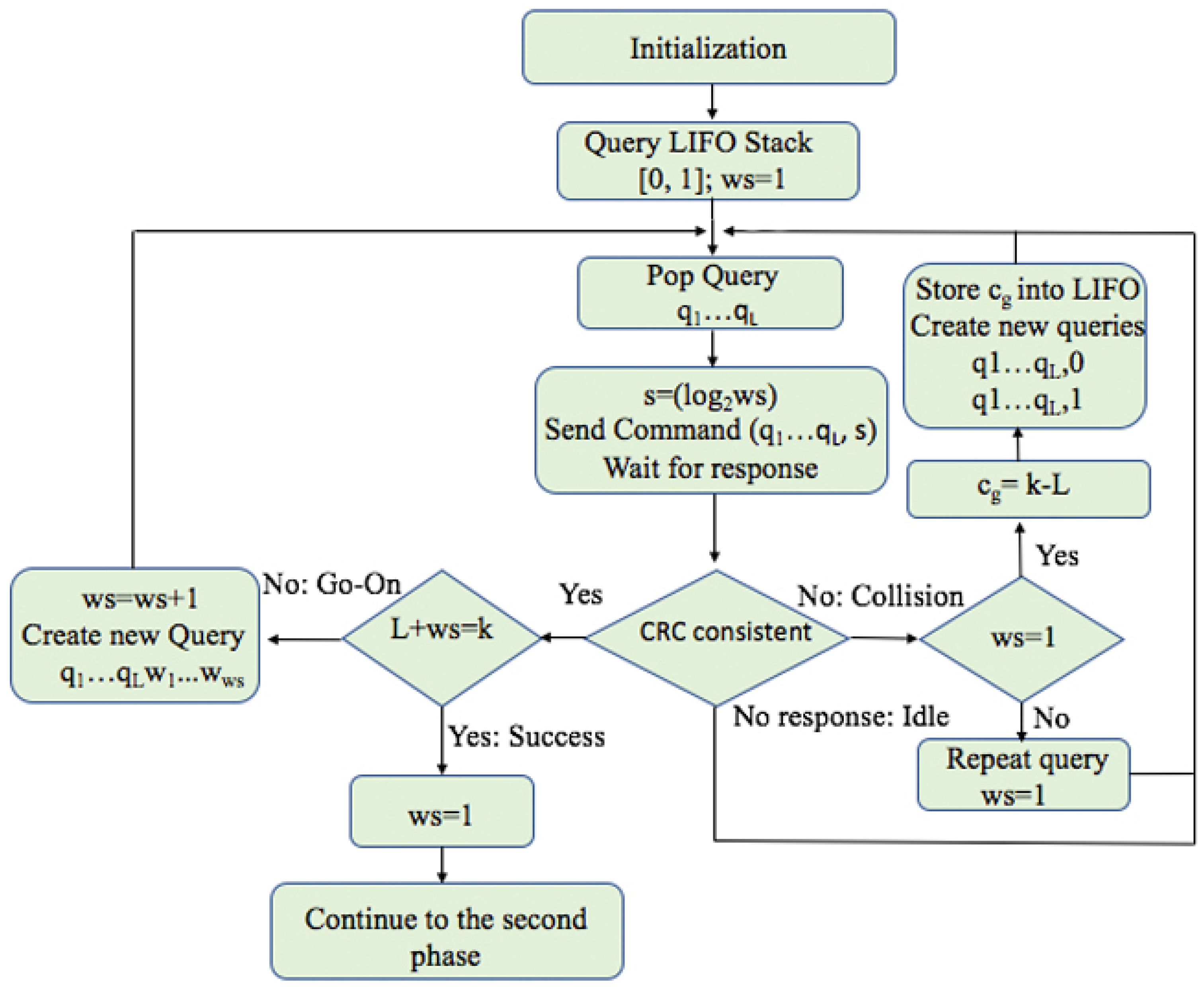
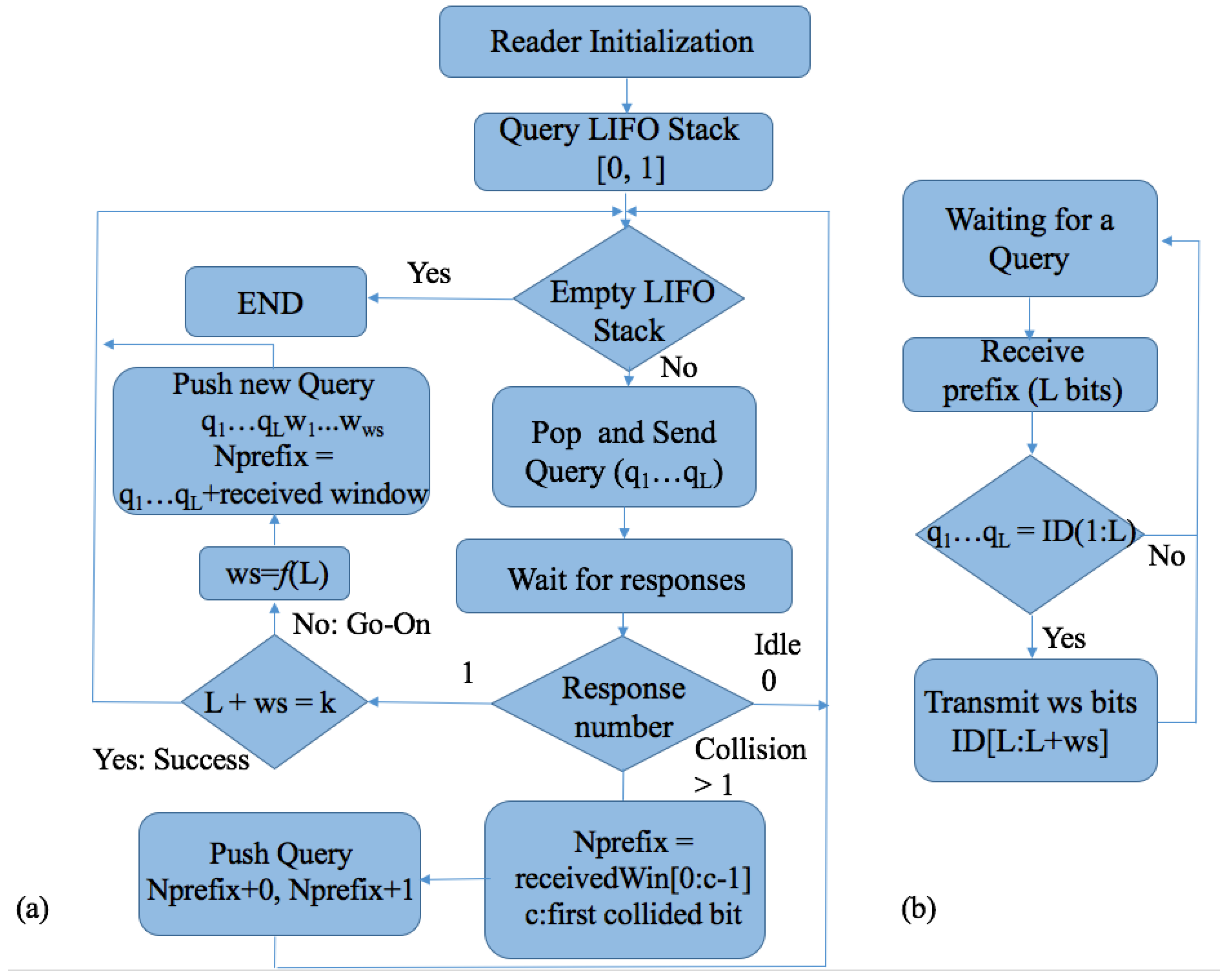
Query Window Tree Protocol
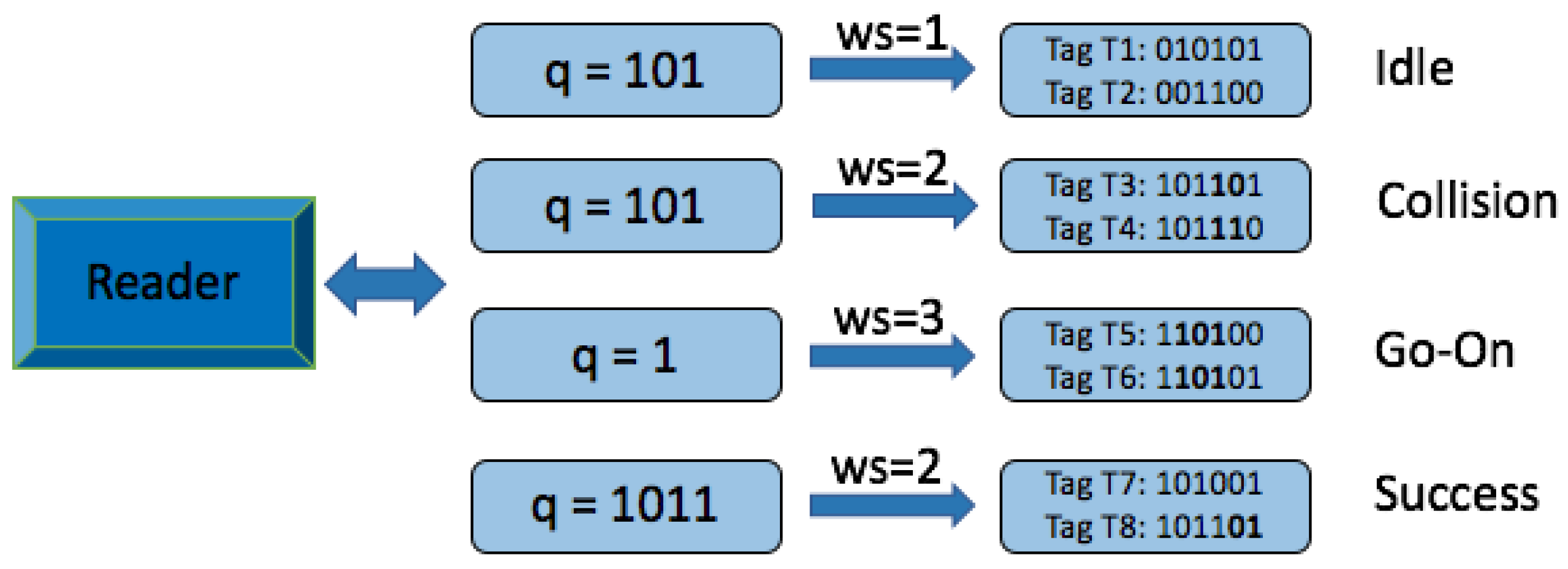
- Collision slot. When the reader cannot differentiate the answer, they will create two new queries by appending ‘0’ and ‘1’ to the former query [,...]. The window size , will remain unchanged, with the value used in the previous query.
- Idle slot. When there is no response, the reader will discard the query and retain the same as that of the last command.
- Go-on slot. This occurs when at least one tag responds with a window and the reader is able to understand it. If L + wsk is not true, the reader will transmit a new query created from the former query and received window. During this query, the reader will append an updated value.
- Success slot. This is a type of go-on slot where the reader successfully receives the last part of the tag ID and L + ws = k. Then, the reader can save the tag, calculate the new , and continue with the identification process.
- A modification of the QwT is presented in [51] called Standardized Query window Tree protocol (SQwT). This protocol aims to reduce the number of bits that define by using a standardized value of 3 bits and approximating it to the nearest power of 2, using instead. Tags calculate the number of bits to respond by using . By using only 3 bits, SQwT can cover window size values from 1 to 128 bits.
- Another modification of QwT is presented in [52] and is called Flexible Query window Tree protocol (FQwT). This modification takes advantage of the window to perform an estimation of the tag ID distribution in the interrogation area and improve the identification time of the protocol. The functioning of the protocol is divided into two phases: the estimation of the distribution, and the identification process. During the former phase, the reader estimates the tag ID distribution until the first tag is identified (see Figure 17).
4.4. Manchester Coding
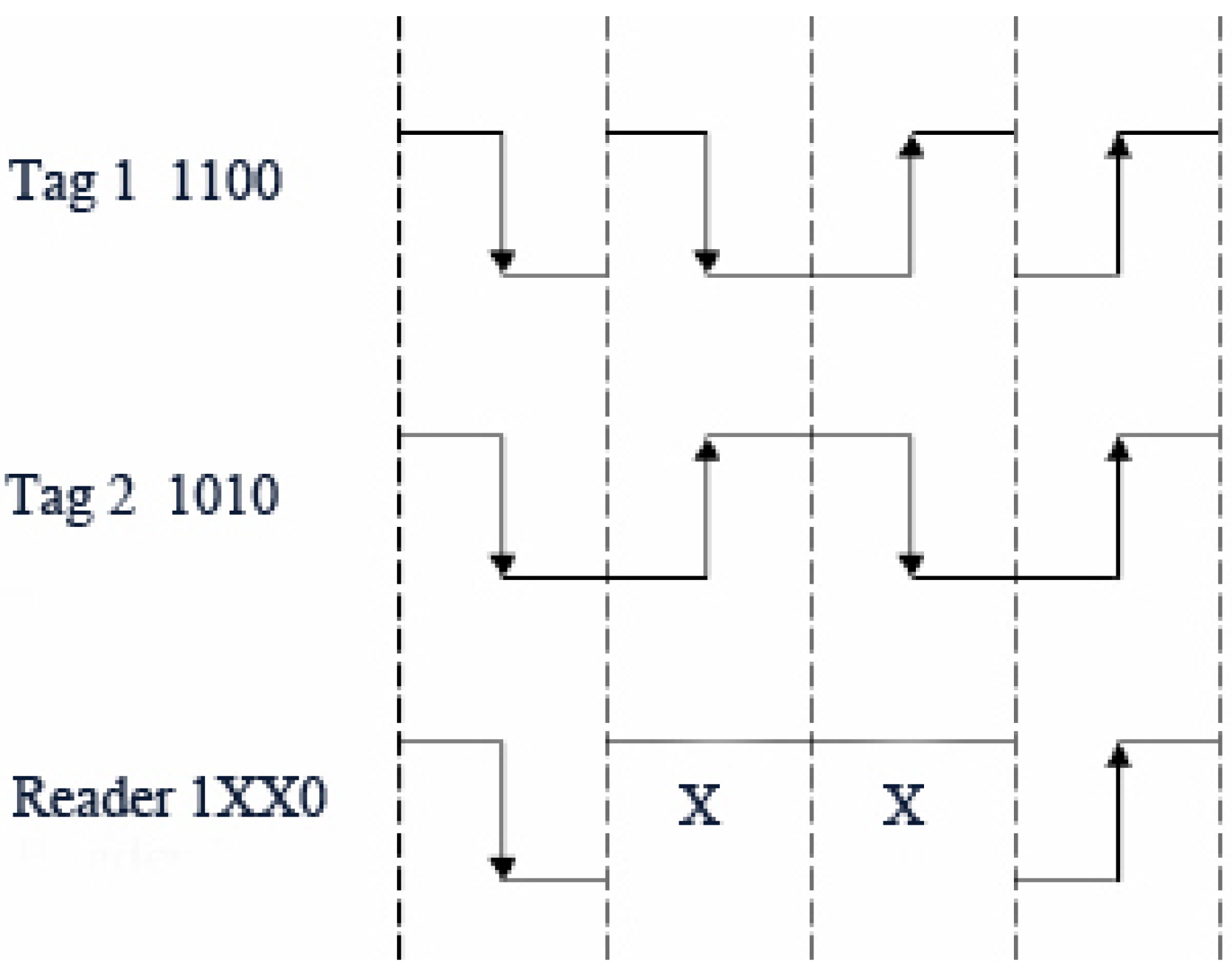
4.4.1. Binary Search Protocol
4.4.2. Collision Tree Protocol
4.4.3. Optimal Query Tracking Tree Protocol
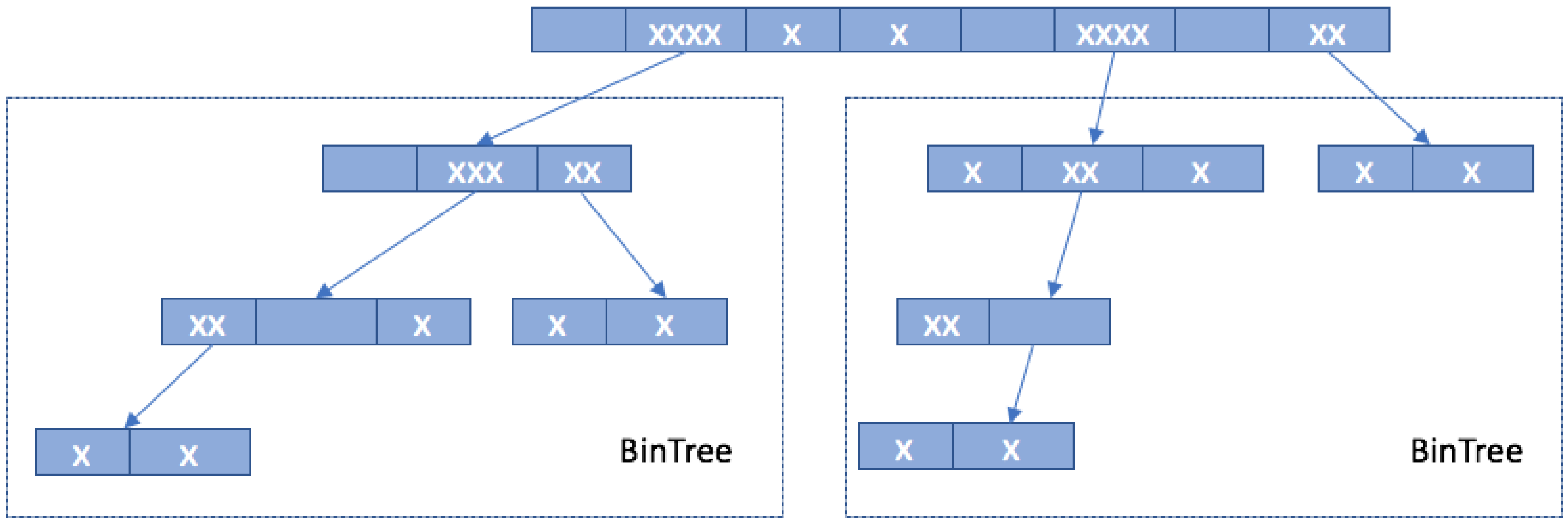
- A modification of the OQTT is presented in [59] called Optimal Binary Tracking Tree (OBTT). This modification implements the estimator of the OQTT with a simple Binary Tree (BT) protocol [60]. The estimator establishes the inital upper bound for tags’ counters. This produces a separation of the existing tags in groups avoiding excessive responses in the beginning of the interrogation procedure.
4.4.4. Collision Window Tree Protocol
- A collision slot occurs when at least one colliding bit is found. Then the reader creates two additional queries [, ..., ... 1, 0] and [, …, ... 1, 1], using bit tracking. The supplementary queries are made from the last transmitted query [...] appended with the received bits [, … 1] indicating the first colliding bit.
- A go-on slot occurs when at least one tag responds and the expression L + ws k is met. Then, the reader creates a new query based on the former one and the received window from the last slot. The next is calculated using the heuristic function in Equation (1).
- A success slot occurs when the reader checks the expression L + ws = k and if it matches, the tag is successfully identified.
5. Hybrid Protocols
5.1. Tree Slotted Aloha
5.2. Binary Tree Slotted Aloha
5.2.1. Dynamic Binary Tree Slotted Aloha
5.2.2. Adaptive Binary Tree Slotted Aloha
6. Discussion
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- RFID-Journal. That Internet of Things. 2017. Available online: http://www.rfidjournal.com/articles/ (accessed on 15 April 2018).
- Finkenzeller, K. RFID Handbook; Wiley: Hoboken, NJ, USA, 2010. [Google Scholar]
- Azambuja, M.; Marcon, C.; Hessel, F. Survey of Standardized ISO 18000-6 RFID Anti-collision Protocols. In Proceedings of the 2008 Second International Conference on Sensor Technologies and Applications (sensorcomm 2008), Cap Esterel, France, 25–31 August 2008; pp. 468–473. [Google Scholar]
- Shih, D.; Sun, P.; Yen, D.; Huang, S. Taxonomy and survey of RFID anti-collision protocols. Comput. Commun. 2006, 29, 2150–2166. [Google Scholar] [CrossRef]
- Klair, D.; Chin, K.; Raad, R. A Survey and Tutorial of RFID Anti-Collision Protocols. IEEE Commun. Surv. Tutor. 2010, 12, 400–421. [Google Scholar] [CrossRef]
- Abraham, C.; Ahuja, V.; Ghosh, A.; Pakanati, P.P. Inventory Management Using Passive RFID Tags: A Survey; Department of Computer Science, The University of Texas at Dallas: Richardson, TX, USA, 2002; pp. 1–16. [Google Scholar]
- Leong, K.; Ng, M.; Cole, P. The reader collision problem in RFID systems. In Proceedings of the 2005 IEEE International Symposium on Microwave, Antenna, Propagation and EMC Technologies for Wireless Communications, Beijing, China, 8–12 August 2005; pp. 658–661. [Google Scholar]
- Burdet, L.A. RFID Multiple Access Methods. Smart Environments Seminar: Zurich, 2004. Available online: http://www.vs.inf.ethz.ch/edu/SS2004/DS/reports/06RFID-macreport.pdf (accessed on 20 April 2018).
- Yu, J.; Liu, K.; Yan, G. A Novel RFID Anti-Collision Algorithm Based on SDMA. In Proceedings of the 2008 4th International Conference on Wireless Communications, Networking and Mobile Computing, Dalian, China, 12–17 October 2008; pp. 1–4. [Google Scholar]
- Sayeed, M.; Kim, Y. A Simple LMS Algorithm Based Smart Antenna to Solve the Reader Collision Problems in RFID System. In Proceedings of the 2009 International Conference on Information and Multimedia Technology, Jeju Island, Korea, 16–18 December 2009; pp. 426–430. [Google Scholar]
- Banks, J.; Pachano, M.; Thompson, L.; Hanny, D. RFID Anti-Collision System Using the Spread Spectrum Technique; Technical Report; Georgia Institute of Technology: Atlanta, GA, USA, 2005. [Google Scholar]
- Liu, H.C.; Ciou, J. Performance analysis of multi-carrier RFID systems. In Proceedings of the 2009 International Symposium on Performance Evaluation of Computer Telecommunication Systems, Istanbul, Turkey, 13–16 July 2009; Volume 41, pp. 112–116. [Google Scholar]
- Loeffler, A.; Schuh, F.; Gerhaeuser, H. Realization of a CDMA-based RFID System Using a Semi-active UHF Transponder. In Proceedings of the 2010 6th International Conference on Wireless and Mobile Communications, Valencia, Spain, 20–25 September 2010; pp. 5–10. [Google Scholar]
- Tang, Z.; He, Y. Research of Multi-access and Anti-collision Protocols in RFID Systems. In Proceedings of the 2007 International Workshop on Anti-Counterfeiting, Security and Identification (ASID), Xiamen, China, 16–18 April 2007; pp. 377–380. [Google Scholar]
- Wang, W.; Zhang, Y.; Sang, Y.; Wang, S. Analysis of anti-collision algorithms in RFID system. In Proceedings of the 2009 IEEE International Conference on Communications Technology and Applications, Boston, MA, USA, 16–18 October 2009; pp. 58–62. [Google Scholar]
- Schoute, F. Dynamic Frame Length Aloha. IEEE Trans. Commun. 2010, 31, 565–568. [Google Scholar] [CrossRef]
- Zhu, L.; Yum, T. The Optimal Reading Strategy for EPC Gen-2 RFID Anti-Collision Systems. IEEE Trans. Commun. 2010, 58, 2725–2733. [Google Scholar] [CrossRef]
- Maguire, Y.; Pappu, R. An Optimal Q-Algorithm for the ISO 18000-6C RFID Protocol. IEEE Trans. Autom. Sci. Eng. 2009, 6, 16–24. [Google Scholar] [CrossRef] [Green Version]
- Zhu, L.; Yum, T. Optimal Framed Aloha Based Anti-Collision Algorithms for RFID Systems. IEEE Trans. Commun. 2010, 58, 3583–3592. [Google Scholar] [CrossRef]
- Chen, W.T. An Accurate Tag Estimate Method for Improving the Performance of an RFID Anticollision Algorithm Based on Dynamic Frame Length Aloha. IEEE Trans. Autom. Sci. Eng. 2009, 6, 9–15. [Google Scholar] [CrossRef]
- Abramson, N. THE ALOHA SYSTEM: Another alternative for computer communications. In Proceedings of the Fall Joint Computer Conference, Houston, TX, USA, 17–19 November 1970; pp. 281–285. [Google Scholar]
- Roberts, L. ALOHA packet system with and without slots and capture. ACM SIGCOMM Comput. Commun. Rev. 1975, 5, 28–42. [Google Scholar] [CrossRef]
- Klair, D.; Chin, K.; Raad, R. An Investigation into thie Energy Eficiency of Pure and Slotted Aloha Based REID Anti-Collision Protocols. In Proceedings of the 2007 IEEE International Symposium on a World of Wireless, Mobile and Multimedia Networks, Espoo, Finland, 18–21 June 2007; pp. 1–4. [Google Scholar]
- Namboodir, V.; DeSilva, M.; Deegala, K.; Ramamoorthy, S. An extensive study of slotted Aloha-based RFID anti-collision protocols. Comput. Commun. 2012, 35, 1955–1966. [Google Scholar] [CrossRef]
- Bueno-Delgado, M.; Vales-Alonso, J.; Gonzalez-Castaño, F. Analysis of DFSA anti-collision protocols in passive RFID environments. In Proceedings of the 2009 35th Annual Conference of IEEE Industrial Electronics, Pisa, Italy, 3–5 November 2009; pp. 2610–2617. [Google Scholar]
- Vogt, H. Efficient object identification with passive RFID tags. In Proceedings of the 2002 International Conference on Pervasive Computing, Zürich, Switzerland, 26–28 August 2002. [Google Scholar]
- Vogt, H. Multiple object identification with passive RFID tags. In Proceedings of the 2002 IEEE International Conference on Systems, Man and Cybernetics, Hammamet, Tunisia, 6–9 October 2002; Volume 3, pp. 1–6. [Google Scholar]
- Cha, J.R.; Kim, J.H. Novel Anti-collision Algorithms for Fast Object Identification in RFID System. In Proceedings of the 11th International Conference on Parallel and Distributed Systems (ICPADS’05), Fuduoka, Japan, 22–25 July 2005; Volume 2, pp. 63–67. [Google Scholar]
- Hwang, T.W.; Lee, B.G.; Kim, Y.S.; Suh, D.Y.; Kim, J.S. Improved Anti-collision Scheme for High Speed Identification in RFID System. In Proceedings of the First International Conference on Innovative Computing, Information and Control, Beijiang, China, 30 August–1 September 2006; Volume 2, pp. 449–452. [Google Scholar]
- Wieselthier, J.; Ephremides, A.; Michaels, L. An exact analysis and performance evaluation of framed Aloha with capture. IEEE Trans. Commun. 1989, 37, 125–137. [Google Scholar] [CrossRef]
- Yan, F.; Shao, X.; Sun, Q. The dynamic anti-collision algorithm based on the similar binary in RFID system. In Proceedings of the 2008 2nd International Conference on Anti-Counterfeiting, Security and Identification, Guiyang, China, 20–23 August 2008; pp. 444–447. [Google Scholar]
- Lin, C.; Lin, F. Efficient Estimation and Collision-Group-Based Anti-collision Algorithms for Dynamic Frame-Slotted Aloha in RFID Networks. IEEE Trans. Autom. Sci. Eng. 2010, 7, 840–848. [Google Scholar] [CrossRef]
- EPCglobal. Radio-Frequency Identity Protocols Class-1 Generation-2 UHF RFID Protocol for Communications at 860–960 MHz, Version 1.2.0; EPC EPCglobal: Beijing, China, 2008. [Google Scholar]
- Wang, C.; Daneshmand, M.; Sohraby, K.; Li, B. Performance analysis of RFID Generation-2 protocol. IEEE Trans. Wirel. Commun. 2009, 8, 2592–2601. [Google Scholar] [CrossRef]
- Lee, D.; Kim, K.; Lee, W. Q+-Algorithm: An Enhanced RFID Tag Collision Arbitration Algorithm. In Proceedings of the 4th International Conference on Ubiquitous Intelligence and Computing (UIC 2007), Hong Kong, China, 11–13 July 2007; pp. 23–32. [Google Scholar]
- Peeters, G.; Houdt, B. Interference Cancellation Tree Algorithms with k-Signal Memory Locations. IEEE Trans. Commun. 2010, 58, 3056–3061. [Google Scholar] [CrossRef] [Green Version]
- Yeh, M.; Jiang, J.; Huang, S. Parallel Response Query Tree Splitting for RFID Tag Anti-collision. In Proceedings of the 2011 40th International Conference on Parallel Processing Workshops, Taipei, Taiwan, 13–16 September 2011; pp. 6–15. [Google Scholar]
- Myung, J.; Lee, W.; Shih, T. An Adaptive Memoryless Protocol for RFID Tag Collision Arbitration. IEEE Trans. Multimed. 2006, 8, 1096–1101. [Google Scholar] [CrossRef]
- Gou, H.; Jeong, H.; Yoo, Y. A Bit collision detection based Query Tree protocol for anti-collision in RFID system. In Proceedings of the 2010 IEEE 6th International Conference on Wireless and Mobile Computing, Networking and Communications, Chengdu, China, 23–25 September 2010; pp. 421–428. [Google Scholar]
- Zein, W.; Shaaban, E. An enhanced binary tree anti-collision technique for dynamically added tags in RFID systems. In Proceedings of the 2010 2nd International Conference on Computer Engineering and Technology, Cengdu, China, 16–18 April 2010; Volume 7, pp. 349–353. [Google Scholar]
- Law, C.; Lee, K.; Siu, K. Efficient memoryless protocol for tag identification. In Proceedings of the 4th International Workshop on Discrete Algorithms and Methods for Mobile Computing and Communications, Boston, MA, USA, 11 August 2000. [Google Scholar]
- Choi, J.; Lee, D.; Youn, Y.; Jeon, H.; Lee, H. Scanning-Based Pre-Processing for Enhanced Tag Anti-Collision Protocols. In Proceedings of the 2006 International Symposium on Communications and Information Technologies, Damascus, Syria, 24–28 April 2006; pp. 1207–1211. [Google Scholar]
- Zhou, F.; Chen, C.; Jin, D.; Huang, C.; Min, H. Evaluating and Optimizing Power Consumption of Anti-Collision Protocols for Applications in RFID Systems. In Proceedings of the 2004 International Symposium on Low Power Electronics and Design, Newport Beach, CA, USA, 9–11 August 2004; pp. 357–362. [Google Scholar]
- Choi, J.; Lee, D.; Lee, H. Query tree-based reservation for efficient RFID tag anti-collision. IEEE Commun. Lett. 2007, 11, 85–87. [Google Scholar] [CrossRef]
- Bhandari, N.; Sahoo, A.; Iyer, S. Intelligent Query Tree (IQT) Protocol to Improve RFID Tag Read Efficiency. In Proceedings of the 9th International Conference on Information Technology, Orissa, India, 18–21 December 2006; pp. 46–51. [Google Scholar]
- Pan, L.; Wu, H. Smart Trend-Traversal Protocol for RFID Tag Arbitration. IEEE Trans. Wirel. Commun. 2011, 10, 3565–3569. [Google Scholar] [CrossRef]
- Yan, X.; Zhang, R.; Li, B. Smart Trend-Traversal Protocol with Shortcutting for Memoryless RFID Tag Collision Resolution. In Proceedings of the 2012 9th International Conference on Ubiquitous Intelligence and Computing and 9th International Conference on Autonomic and Trusted Computing, Fukuoka, Japan, 4–7 September 2012; pp. 857–862. [Google Scholar]
- Landaluce, H.; Perallos, A.; Zuazola, I. A Fast RFID Identification Protocol with Low Tag Complexity. IEEE Commun. Lett. 2013, 17, 1704–1706. [Google Scholar] [CrossRef]
- Landaluce, H.; Perallos, A.; Angulo, I. Managing the Number of Tag Bits Transmitted in a Bit-Tracking RFID Collision Resolution Protocol. Sensors 2014, 14, 1010–1027. [Google Scholar] [CrossRef] [PubMed]
- Landaluce, H.; Perallos, A.; Onieva, E.; Arjona, L.; Bengtsson, L. An Energy and Identification Time Decreasing Procedure for Memoryless RFID Tag Anticollision Protocols. IEEE Trans. Wirel. Commun. 2016, 15, 4234–4247. [Google Scholar] [CrossRef]
- Cmiljanic, N.; Landaluce, H.; Perallos, A.; Arjona, L. Reducing Transmitted Bits in a Memoryless RFID Anti-Collision Protocol. IEEE Commun. Lett. 2016, 14, 713–715. [Google Scholar]
- Cmiljanic, N.; Landaluce, H.; Perallos, A.; Arjona, L. Influence of the Distribution of Tag IDs on RFID Memoryless Anti-Collision Protocols. Sensors 2017, 17, 1891. [Google Scholar] [CrossRef] [PubMed]
- Rohatgi, I.; Durgin, G. RFID Applied; John Wiley & Sons: Hoboken, NJ, USA, 2007. [Google Scholar]
- Jia, X.; Feng, Q.; Yu, L. Stability Analysis of an Efficient Anti-Collision Protocol for RFID Tag Identification. IEEE Trans. Commun. 2012, 60, 2285–2294. [Google Scholar] [CrossRef]
- Wang, T.P. Enhanced binary search with cut-through operation for anti-collision in RFID systems. IEEE Commun. Lett. 2006, 10, 236–238. [Google Scholar] [CrossRef]
- Yu, S.; Zhan, Y.; Wang, Z.; Tang, Z. Anti-collision algorithm based on jumping and dynamic searching and its analysis. Comput. Eng. 2005, 31, 19–20. [Google Scholar]
- Jia, X.; Feng, Q.; Ma, C. An Efficient Anti-Collision Protocol for RFID Tag Identification. IEEE Commun. Lett. 2010, 14, 1014–1016. [Google Scholar] [CrossRef]
- Lai, Y.; Hsiao, L.; Chen, H.; Lai, C.; Lin, J. A Novel Query Tree Protocol with Bit Tracking in RFID Tag Identification. IEEE Trans. Mob. Comput. 2013, 12, 2063–2075. [Google Scholar] [CrossRef]
- Lai, Y.C.; Hsiao, L.Y.; Lin, B.S. Optimal Slot Assignment for Binary Tracking Tree Protocol in RFID Tag Identification. IEEE/ACM Trans. Netw. 2015, 23, 255–268. [Google Scholar] [CrossRef]
- Hush, D.; Wood, C. Analysis of tree algorithms for RFID arbitration. In Proceedings of the 1998 IEEE International Symposium on Information Theory, Cambridge, MA, USA, 16–21 August 1998; pp. 107–125. [Google Scholar]
- Zhang, L.; Zhang, J.; Tang, X. Assigned Tree Slotted Aloha RFID Tag Anti-Collision Protocols. IEEE Trans. Wirel. Commun. 2013, 12, 5493–5505. [Google Scholar] [CrossRef]
- Bonuccelli, M.; Lonetti, F.; Martelli, F. Tree slotted aloha: A new protocol for tag identification in RFID networks. In Instant Collision Resolution for Tag Identification in RFID Networks; Elsevier: New York, NY, USA, 2007; pp. 1220–1232. [Google Scholar]
- Qian, C.; Liu, Y.; Ngan, H.; Ni, L. ASAP: Scalable Identification and Counting for Contactless RFID Systems. In Proceedings of the 2010 IEEE 30th International Conference on Distributed Computing Systems, Genova, Italy, 21–25 June 2010; pp. 52–61. [Google Scholar]
- Myung, J.; Lee, W.; Srivastava, J. Adaptive binary splitting for efficient RFID tag anticollision. IEEE Commun. Lett. 2006, 10, 144–146. [Google Scholar] [CrossRef]
- Wu, H.; Zeng, Y.; Feng, J.; Gu, Y. Binary Tree Slotted Aloha for Passive RFID Tag Anticollision. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 19–31. [Google Scholar] [CrossRef]
- Porta, T.L.; Maselli, G.; Petrioli, C. Anticollision Protocols for Single-Reader RFID Systems: Temporal Analysis and Optimization. IEEE Trans. Mob. Comput. 2011, 10, 267–279. [Google Scholar] [CrossRef]
| Protocol Name | PA | SA | FSA | DFSA | Q |
|---|---|---|---|---|---|
| Protocol feature | Tags transmit after random time to the reader. In the case of a collision tags will retransmit after a random delay. | Tags transmit their ID in synchronous time slots. In case of a collision, tags retransmit after a random delay. | Each tag responds only once per frame. | Tags transmit once per frame. The reader uses a tag estimation function to vary the frame size. | The reader dynamically adjust critical parameter (Q) based on the type of replies from tags. |
| Disadvantages | In a dense tag environment the the number of collision increases significantly. | In a dense tag environment the the number of collision increases significantly. The reader requires synchronization with tags. | It uses a fixed frame size and does not change the size during the identification process. | It cannot move into the next frame at any time based on the situation of collision without finishing the current frame. | This protocol may encounter some problems (lower throughput) on adjusting Q, especially when the frame size is larger than the number of tags. |
| RTF/TTF | TTF | RTF | RTF | RTF | RTF |
| Efficicency | 18.4% | 36.8% | 36.8% | 42.6% | 36.8% |
| System cost | Very low | Low | Expensive | Expensive | Expensive |
| Complexity | Very simple | Simple | Medium | High | Medium |
| Protocol Name | QT | STT | QwT |
|---|---|---|---|
| Protocol feature | Tags respond when their ID match the query transmitted by the reader. | Defines the generation of the new queries according the several predefined rules. These rules take into account the number of consecutive collisions and slots. | The reader transmits the number of bits tags must respond in addition to the query. This number is calculated using an heuristic function at the reader side. |
| Disadvantages | It produces a high number of collisions, particularly in the beginning of the identification procedure. | It transmits the full tag ID with each response, therefore a high number of bits are wasted with every collision. | The reader command needs a high number of bits to represent the size of the tags’ responses. |
| Efficiency | 34.6% | 34% | 35% |
| System cost | Very low | Expensive | Medium |
| Complexity | Low | High | Medium |
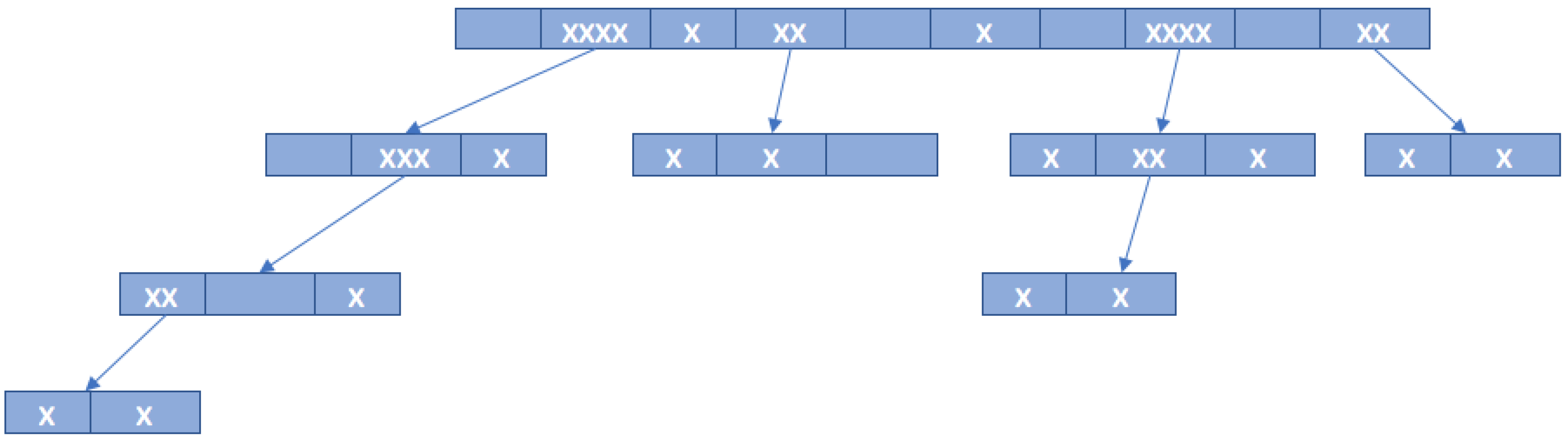
| Slot Number | Reader Command | Tag A (010) | Tag B (011) | Tag C (100) | Tag D (110) | Result | Type of Slot |
|---|---|---|---|---|---|---|---|
| Slot 1 | 111 | 010 | 011 | 100 | 110 | XXX | Collision |
| Slot 2 | 011 | 010 | 011 | 01X | Collision | ||
| Slot 3 | 010 | 010 | 010 | Success | |||
| Slot 4 | 111 | 011 | 100 | 110 | XXX | Collision | |
| Slot 5 | 011 | 011 | 011 | Success | |||
| Slot 6 | 111 | 100 | 110 | 1X0 | Collision | ||
| Slot 7 | 101 | 100 | 100 | Success | |||
| Slot 8 | 111 | 110 | 110 | Success |
| Slot | Query | Tag Response | ||||||
|---|---|---|---|---|---|---|---|---|
| Tag A (1010) | Tag B (1100) | Tag C (0100) | Tag D (0010) | Tag E (0111) | Status | Stack | ||
| Est. | 00,01,1 | |||||||
| 1 | 00 | 10 | Identified | 01,1 | ||||
| 2 | 01 | 00 | 11 | Collision | 010,011,1 | |||
| 3 | 010 | 0 | Identified | 011,1 | ||||
| 4 | 011 | 1 | Identified | 1 | ||||
| 5 | 1 | 010 | 100 | Collision | 10,11 | |||
| 6 | 10 | 10 | Identified | 11 | ||||
| 7 | 11 | 00 | Identified | empty |
| Protocol Name | OQTT | BS | CT | CwT |
|---|---|---|---|---|
| Protocol feature | The reader performs an initial estimation to split the tags in groups. These groups are identified using the CT protocol. | The reader transmits a serial number. Only tags having an equal or lower ID value than the received serial number will respond on request. | It is an improvement of QT which uses Bit tracking technology in order to find which bits collided as well as where they are. | The reader is able to identify the collided bits from the tags’ responses, and uses them to calculate the new tag response size. |
| Disadvantages | Very complex protocol. Hard to be physically implemented. | The reader restarts the reading process after a tag is identified. | It wastes a high number of tag bits on every collision, increasing the energy consumed by the reader during the process. | The reader command needs a high number of bits to represent the size of the tags’ responses. |
| Efficiency | 61.4% | 30% | 50% | 35% |
| System cost | Very expensive | Low | Medium | Medium |
| Complexity | Very high | Low | Medium | Medium |
| Criterion | Aloha Protocols | Tree-Based Protocols | Hybrid Protocols |
|---|---|---|---|
| Protocol feature | They use random multi-access means to identify tags. In the case of collision, tags will be asked to send data later with a random time relay. | They identify the total number of tags in the interrogation zone. The reader controls every step of the protocol, using commands or queries to split colliding tags into subsets, and further repeatedly split those subsets until identifying all of the tags. | Tree-based protocols. They use two methods. The first uses randomized divisions in tree-based algorithms, and another uses tree strategies after a collision in Aloha algorithms. |
| Number of tags to reader commands | Low | High | Medium |
| Usage | Aloha protocols are commonly used in LF, HF and UHF RFID (18000-6C) systems. | Tree-based protocols are commonly used in HF, UHF and microwave (18000-6B and 18000-7) RFID systems. | Not implemented on any standard |
| Method | Probabilistic | Deterministic | Mixture (Aloha and Tree-based) |
| Tag starvation | Yes | No | No |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cmiljanic, N.; Landaluce, H.; Perallos, A. A Comparison of RFID Anti-Collision Protocols for Tag Identification. Appl. Sci. 2018, 8, 1282. https://doi.org/10.3390/app8081282
Cmiljanic N, Landaluce H, Perallos A. A Comparison of RFID Anti-Collision Protocols for Tag Identification. Applied Sciences. 2018; 8(8):1282. https://doi.org/10.3390/app8081282
Chicago/Turabian StyleCmiljanic, Nikola, Hugo Landaluce, and Asier Perallos. 2018. "A Comparison of RFID Anti-Collision Protocols for Tag Identification" Applied Sciences 8, no. 8: 1282. https://doi.org/10.3390/app8081282





