1. Introduction
The age of the Internet of Things (IoT) is forthcoming [
1]. It will give objects and even generated contents to the ability to communicate with other mediums. With the generated data from every object, the data will not remain raw as they are today but will be customized to the users based on their needs and even converge with other data. The concept of IoT is simple, although its capability is unlimited and its usage can change the entire paradigm of legacy technology. It is based on embedding a network interface into objects, enabling communications among them to provide various services for users. Consequently, each object will have its own identifier, such as an Internet Protocol address (IP address) in the current Internet that can connect and communicate with other objects through the IoT networking environment. Unlike the era before IoT, when the users could obtain data only from the service provider, the users can directly access the sensors and give commands to the actuators. With this capability, data from IoT applications will be utilized to provide a novel service to industry, academia, and even personal use.
To successfully manage IoT services, the IoT infrastructure must be well-designed. However, there are some limitations in the current research and development plan to create a complete IoT environment. First, the applications and services for IoT are sporadically developed from numerous vendors without the usage of the standard technology [
2]. Second, there is no standard networking protocol for IoT applications. Even today, there are diverse networking protocols such as Wi-Fi, Bluetooth, ZigBee, Z-wave, and Long Term Evolution (LTE). Nonetheless, there is no device that can communicate with all existing networking protocols. To overcome this issue, the gateway, or the IoT device that can support heterogeneous networks, is crucial to create one complete IoT network. Additionally, the increasing number of IoT devices and the necessity of Big Data processing will expand the number of packets, where this issue can be a critical problem to the legacy network architecture.
In this paper, we focus on the network layer of the IoT. Although many studies have already conducted surveys on IoT, some survey papers primarily focused on the service aspect of IoT. Moreover, surveys in [
3,
4,
5,
6,
7] present results on each focused subject. Nevertheless, many papers consider to maintain the legacy network infrastructure, since the modification of existing network infrastructure costs highly. Obviously, the concept of future network for IoT should be researched in a national scale, and this consideration is an essential prerequisite to realize IoT environment. Therefore, we will discuss the reason why the current network is insufficient as an IoT network. Furthermore, we will describe the needs for modification and argue in favor of creating a novel network infrastructure to support the IoT environment.
Structure of This Article
IoT is not limited to include the communication functionality of the things; rather, it is an integrated solution to share all manner of information among devices, users and services to provide user-preferred service. However, current research on the IoT network varies. In this paper, we specifically focus on the network issues in the IoT because the IoT network is the fundamental component that can enable IoT services. We categorize this paper as follows:
Overview of IoT,
Current market and research trend of IoT,
Research challenges of the IoT network,
Insights for the future IoT network.
In
Section 2, we introduce the overview of IoT and categorize it in terms of its technology. We introduce the market overview of IoT and its potential in
Section 3. We then investigate various world wide research programs on IoT and future network architectures of various nations. In addition, we analyze the current status and the limitations of the IoT network, such as SDN, heterogeneity, and service-oriented networking, in
Section 4. Finally, diverse inspirations that can solve the limitations of the current IoT network research described in the previous sections will be derived and analyzed in
Section 5. Specifically, we will introduce novel concepts for a flawless future IoT network. Finally, we conclude the paper in
Section 6.
2. IoT Overview
In this section, we briefly describe the overview of the IoT structure, which
Figure 1 presents. The structure of the IoT consists of four layers: service layer, platform layer, network layer, and device layer. Many research institutions adopt the IoT classification standard shown in
Figure 1 to maintain specialty and consistency for IoT development.
The service layer, which is on the surface, provides the interface and communicates with the users. Examples of the service layer are autonomous driving, health care, smart industry, personal devices, and door security. These services are connected with a platform layer to provide customized services to the users.
The next layer of the IoT structure is the platform layer. The platform layer is located under the service layer and supports the IoT applications and services. There are many types of platforms, including the device platform, data analysis platform, service development platform, and service platform. For instance, the device platform provides an execution environment of services and development for users. Context awareness and prediction, cooperation among things, and connection between the service layer and other layers with the translation of natural language to machine language are examples of the data analysis platform. Furthermore, the service development platform provides development toolkits to users for them to easily develop IoT services. Finally, the service platform supports the generation and execution of a variety of applications.
Along with the service and platform layers, one of the core layers of the IoT environment is the network layer. It serves to transmit the data among devices, contents, services and users. The network layer should be able to process, control, and manage enormous amounts of network traffic. A detailed elaboration of the network layer will be further described later in this paper.
Finally, the device layer is a layer that perceives the environment with various sensing devices, processes it to send to the sink node or gateway, and responds to it if necessary. The device itself must be smart by applying autonomic actuation and a smart control algorithm. The device layer should be able to acquire and control the IoT devices.
In addition to the four layers, security and privacy are important in IoT. Instead of identifying security as its own layer, each layer should incorporate a security solution to protect it from threats. Security issues should be handled as an important functional entity for each layer, and their current or prospective solutions should be customized according to specific properties and operations of each layer.
Each layer is important and has its own roles and capability to enable IoT. Although each layer of IoT is important and should be discussed in depth, the aim of this paper is to describe the IoT network in detail. We will primarily focus on the IoT network in terms of its challenges and provide insights for the future IoT network.
2.1. IoT Service
The features of the IoT services can be formulated in different ways. Many papers have proposed internal modeling of IoT services [
8,
9,
10,
11]. These studies proposed a semantic modeling approach to integrate the IoT framework into the IoT services by automatically obtaining the data from the mobile devices and the sensors [
9,
10]. Furthermore, the mechanism to interact between the IoT services and the sensors is discussed [
8]. However, the core components within the domain of IoT services are tacking behavior, achievement of real-time awareness of the physical environment, and assistance with human decision making through deep analysis and data visualization [
12]. IoT not only links sensor devices and generates the data for a purpose; rather, it focuses on the automation and optimization within the current systems [
12]. For example, automated control of closed systems, control of optimizing resource usage across the network, and automated control in an open environment with great uncertainty. In addition, the data must be searched in a manner of semantic modelling approach by understanding the meaning of the data. Consequently, the proposed IoT services, such as smart homes, smart cities, health monitoring, smart grids, and smart traffic systems, have already incorporated these fundamental models of automation and resource optimization for any environment.
2.2. IoT Platform
The role of the IoT platform is to support and execute IoT services. In the past, the platform was developed in a closed manner. However, industries and governments are developing assorted IoT platforms as open source platforms. One of the reasons for this trend is to enhance the speed to enter the market, reduce the development cost, and improve the quality of the software [
13]. By opening up the software platform, many developers are given the opportunity to contribute their work. This will eventually expedite the development process and reduce the cost. Specifically, Qualcomm developed the Alljoyn platform and is now under the process of turning it into as an open platform under the AllSeen Alliance [
14,
15]. Additionally, the European Union (EU) is operating the OpenIoT project to develop an open platform for IoT [
16].
Another notable aspect of the IoT platform is the way in which the services were developed. In the past, the services were executed and developed independently. Now, they are being transformed into one platform that can support various services. For example, Cisco, International Business Machines Corporation (IBM), Qualcomm, Intel, and Google are developing their home, environment, energy, and traffic supporting services as a cross-platform network that can support various services [
14]. Furthermore, the EU’s Seventh Framework Programme (FP7) project and the Horizon 2020, International Telecommunication Union Telecommunication Standardization Sector (ITU-T), and oneM2M platforms standardize the IoT platform as a cross-platform network.
In addition, internal modeling of the IoT platform has been proposed [
17,
18]. The core idea of the internal modeling of the IoT platform is the publisher/subscriber model. For example, MAGIC Broker 2 is an IoT platform that provides a programming interface based on the publisher/subscriber model [
17]. The authors created this platform by utilizing the mobile devices, public displays, and a Web-based sensor actuator named Sense Tecnic [
17].
Finally, interaction between the platform and the devices is crucial to construct and design an IoT platform. Application Programming Interfaces (APIs) are the key components with which IoT devices can interact with the IoT platform. For example, an exemplary API for IoT platform has been developed [
19]. The authors proposed an API based on TinyOS [
20] named the Constrained Application Protocol (CoAP) that can enable both client and server to be integrated into the IoT environment.
Overall, the trend for the IoT platform is primarily based on the open source platform, cross-platform, publisher/subscriber model, and well-suited APIs.
2.3. IoT Devices
The role of IoT devices is not limited to collecting data; rather, they should also interact with heterogeneous networks to provide a broad variety of services. For instance, IoT devices need the ability to interact either node-to-node or node-to-Web based on whether the target node is in their own network [
21]. In addition, the same philosophy as the IoT platform is also applied to IoT devices. The trend for developing an IoT device is in open-source and/or open-hardware approaches for developers and manufacturers. For example, IoT device manufacturing companies such as Arduino, ioBridge iota, and ARM provide the baseline architecture. With the baseline architecture, users and developers can develop their own IoT devices.
3. Current Market and Research Trend of IoT
In this section, we describe the overview of the current market and the research overview of IoT. We believe that solely explaining the IoT network is insufficient. It is important to know the current viewpoint of IoT from both market and research perspectives to understand the future IoT network. Thus, we believe that it is worthwhile to discuss the market and the research overview of IoT.
3.1. Market Overview
IoT is expected to change human life and open a larger and even more innovative market than its predecessor [
22]. Although the number of devices that are currently connected to the Internet may look large given the population, we should note that the number of devices that are actually connected is small compared with the things with which we coexist in our daily lives. IoT is not limited to creating devices that can connect to the Internet it can provide novel services, applications, and even software toolkits to support its operations. The entities in the IoT market is not limited to the data providers; rather, it can expand to consumers, intermediaries and service providers and further change the pricing schemes [
23]. Additionally, the service will further expand to open the data market and customize services for users, industry, and academia [
22].
Furthermore, the IoT environment is not specifically considered at the device level. It should concentrate on the infrastructure side, such as gateways for billions of devices, services, user-centric information sharing services, Big Data, and customized data for the users. This will eventually induce improvements to both legacy communications and even service markets. For example, IoT services in the industry can be applied to manufacturing, the supply chain, energy, health, automotive, and insurance fields [
24]. Moreover, it can provide novel toolkits in terms of software, hardware, and data [
25]. Consequently, the technological paradigm will be shifted and further applied to a larger connected network with IoT.
3.2. Research Programs
Many research projects are currently operating in the field of IoT [
26,
27,
28,
29,
30,
31,
32,
33,
34,
35,
36,
37,
38]. We will focus on introducing IoT research in Europe, the United States, and Asia.
3.2.1. European Union
To expedite collaboration in the EU research and development program, Europe established the Cluster of European Research Projects on the Internet of Things (CERP-IoT) in 2010 to conduct research on IoT. The primary vision of the EU’s IoT is based on smart things and objects. Starting from the interactions with the smart objects and things, the committee extended the IoT vision to accommodate the domain of smart energy, smart buildings, smart living, smart health, smart cities, and smart transport [
26] and proposed a roadmap of IoT in 2011 [
26]. Based on this roadmap, the EU government initiated the Horizon 2020 program in 2011 by announcing multiple IoT R&BD programs that were focused on implementing IoT smart life service [
27]. Specific details of Europe’s Horizon 2020’s research goals are as follows. First, the program is not limited to IoT but also focuses on the future Internet, cloud computing, Big Data, and 5G networking. Each specific item of the program is designed not to work independently but to interact with each other. Second, the EU’s research programs mostly fund small and medium enterprises (SME). With the funding emphasis on SME, many companies can discover innovative IoT business models and IoT applications to invigorate IoT services. Finally, to distinguish itself from the previous disseminated research and services, Europe’s Horizon 2020 encouraged large global collaboration with other research institutions. Each specific member of Horizon 2020 should interact with the others and let the industry develop the business model, application, and services to enable IoT as a whole. The result [
28] for first two years is that the number and the quality of applications about IoT had been rapidly increased. This results mean that the Horizon 2020 project is on a cruise to close its purpose.
3.2.2. United States
The National Intelligence Council (NIC) of the United States selected IoT as one of six technologies that has potential impacts on national interests through 2025 [
31]. Specifically, industry giants such as Cisco and Qualcomm primarily focus on extending the current network infrastructure into the IoT and construct the hyper-connected infrastructure. Further, legacy sensor devices and radio frequency identification (RFID) are based on seamless connection. In terms of the government aspect, the National Institute for Standards and Technology (NIST) regards IoT as a basis technology for smart grid implementation. Moreover, the National Science Foundation has selected IoT as one of the technology areas in the Small Business Technology Transfer (STTR) program [
32].
3.2.3. Asia
In terms of Asia, China and Japan are the major nations that are currently investigating IoT vigorously.
China has gathered 5 billion Yuan as a fund for Chinese IoT investment. The Chinese government’s latest five-year plan primarily chose the smart grid, transportation, logistics, the home, environment and security, industry and automation, health, agriculture, finance, and military as principal service areas for developing IoT technologies [
33,
34]. In addition, the Chinese government has placed emphasis on a nation wide standardization strategy. Moreover, the Chinese government is establishing a demonstration test bed and IoT database. The Chinese government established a project named as “Internet Plus” strategy [
35], which is a plan to collaborate between IoT technology and manufacturing business.
Along with the Chinese government, Japan is currently conducting the “i-Japan Strategy 2015” research program as a part of IoT research [
36]. The Ministry of Internal Affairs and Communications (MIC) of Japan created a consortium that is based on mobile carrier service providers and system vendors [
37]. The Japanese government is concentrating on remote health-care and earthquake monitoring to enable a secure future digital society. The Ministry of Education, Culture, Sports, Science and Technology ordered the new project, “The Research Project for Information & Communication Technology (ICT) System Architecture in the Era of IoT” [
38] to get a foothold in IoT environment.
3.3. Current Research on Future Network Architecture
In this subsection, we present a survey on the future network architecture for IoT, in contrast to the IP-based conventional network architecture. The current network is based on the server-client model, and the number of nodes in the network has not been as enormous as it is today. In the server-client model, it is difficult to change the network functions and control the network with ease owing to an increase in network complexity. However, this will eventually become a larger problem in the era of IoT because the number of devices that will be connected to the IoT network is expected to increase exponentially.
Fortunately, some nations have recognized this problem and proposed novel network architectures [
39]. For instance, there are many research projects about the future network architecture under FP7 and Horizon 2020 in the EU. Specifically, the 4WARD and Scalable & Adaptive Internet Solutions (SAIL) project studies the future network architecture. Additionally, Future Internet Research and Experimentation (FIRE) is intended to construct the initiative test bed infrastructure for the future Internet technology. In Horizon 2020, FIRE+ [
40] is proposed to expand previous FIRE project by enabling experiments in any size, complexity, or networking technology. In addition to the EU, the Future INternet Design (FIND) project had been researched under the National Science Foundation (NSF) in the United States. Future Internet Architecture (FIA), which is the successor of FIND, has four main research topics to build the Internet architecture: Named Data Networking (NDN), MobilityFirst, NEBULA, and eXpressive Internet Architecture. Along with FIA, NSF sponsors the Global Environment for Network Innovation (GENI) project to construct the test bed environment. Currently, the Future Internet Architecture-Next Phase (FIA-NP) project is in progress to realize the research results of FIA. The overview of the future network architecture projects from the European Union is presented in
Table 1, and
Table 2 elaborates the research projects in the United States.
4. Research Challenges of the IoT Network
In this section, we will discuss the current research challenges in the IoT network. Even if many researchers and governments have focused on implementing environment for IoT network, we think that there are some issues, which are important to IoT network but relatively unknown to major researches. The following contents will handle such important issues. Firstly, we will review various studies in terms of the IoT network. Afterwards, we will present the components that may be contained in the IoT network. Finally, we will analyze the research challenges in the IoT network.
4.1. Literature Review
In [
45], the authors proposed two network models, the man-like nervous (MLN) model and the social organization framework (SOF) model. The idea of MLN model is similar to a reverse tree, in which the sensors are in the low rank of the model, and it becomes a distributed node to send sensing data to the centralized data center. Additionally, the SOF model consists of local IoT, industrial IoT, and national IoT that manages the distributed nodes in the specific region and the data center. The theme of [
45] is that IoT is based on the data center and manages the data from the sensors based on the MLN model. However, the specific usage of the IoT network is not provided yet.
Another architecture of the IoT network was described by Catellani et al. [
46]. In this work, the authors created a test bed for an IoT environment by utilizing the legacy sensors and actuators by modifying it with TinyOS. The authors envisioned that the future IoT network would be based on Internet Protocol version 6 (IPv6), and every communication will be conducted with IP addresses. Moreover, instead of enumerating the future networking protocol, the authors categorized the nodes in terms of base station node (BSN), mobile node (MN), and specialized node (SN). BSN refers to the IPv6 sink and router, MN refers to wireless dongle to add wireless sensor network (WSN) connectivity to a standard laptop, and SN refers to nodes offering services such as temperature readings or actuation.
Finally, Gubbi et al. [
47] claimed that future IoT network will be based on the current WSN technology. The nodes are expected to be deployed in an ad-hoc manner, and a novel cyber infrastructure is based on a service-oriented architecture (SOA) and sensor networks to acquire the data from the sensors and the devices. Furthermore, the addressing schemes will be based on IPv6 and possible adaptation with the uniform resource name (URN) system for development of the IoT network. The authors claimed that cloud-based centralized storage is required to support the storage and analysis for IoT. Consequently, the authors noted that the future IoT network will be based on current WSN technology with the middleware to support heterogeneous devices and a centralized storage for the data.
In all, the current proposals for the IoT network are mostly based on WSN networks without creating a novel network architecture. Many studies have noted that there should be a centralized data center to store and provide customized data to the users. As we have already introduced in the previous sections, a network architecture of IoT environment has to be changed due to the amount of devices and different service type.
4.2. Service-Oriented Network
The service-oriented network (SON) is an important component of the IoT network, in which content distribution network (CDN) is one of the most discussed models to enable SON [
48,
49].
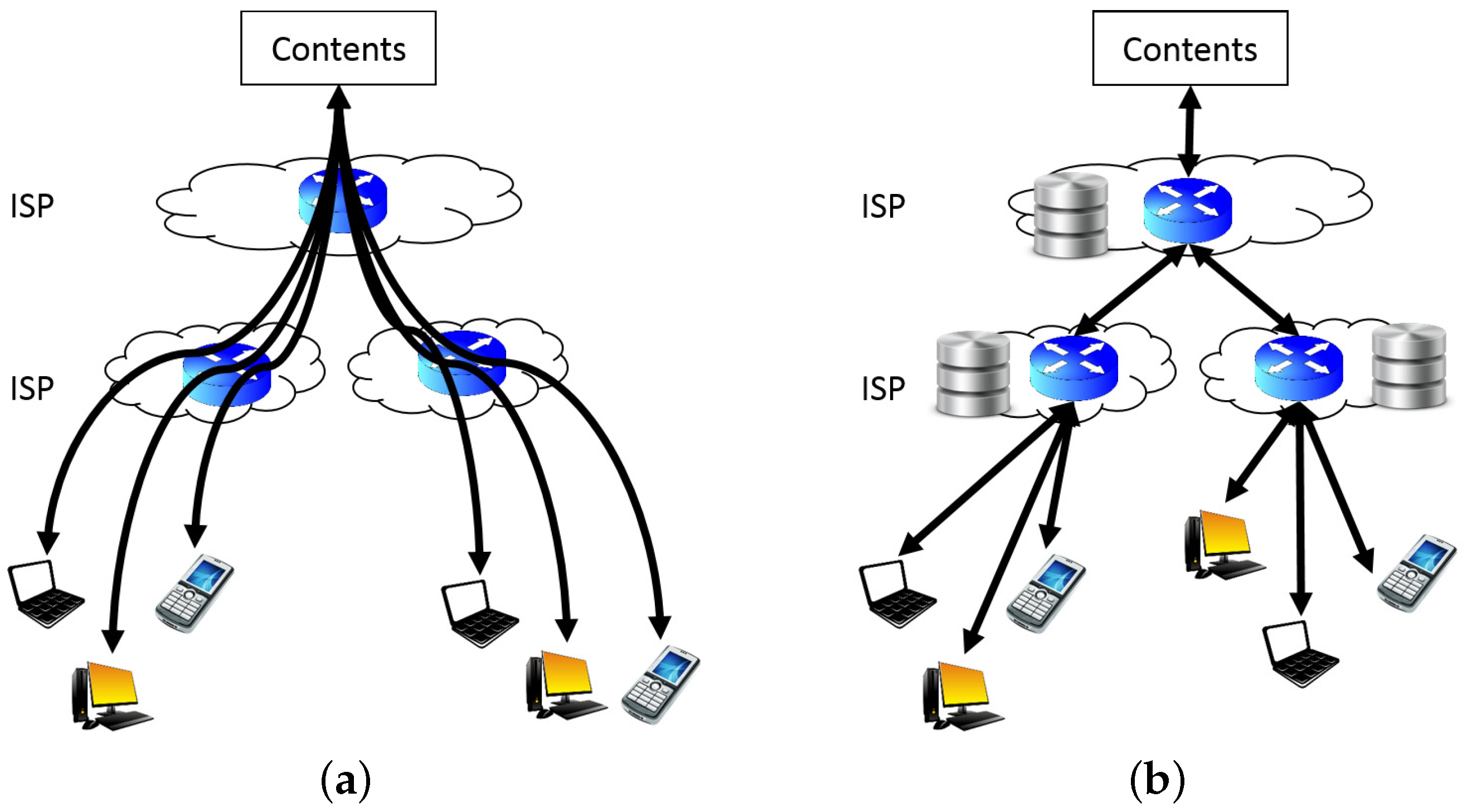
Figure 2 presents the concept of the CDN. The CDN is a system that stores the copies of contents in many distributed servers to deliver the content effectively [
50]. The CDN has an advantage that it can provide content and services to the user rapidly. Nonetheless, it is required to synchronize and distribute content [
51]. Currently, the CDN institutes a Peer-to-Peer network (P2P) technology to let nearby users directly exchange content with one another [
52] to improve the data exchange throughput. However, the CDN uses legacy network technology, and there are shortcomings that require an extra service to obtain the information of the content [
53].
Table 3 represents the comparison of introduced SON technologies.
4.3. Heterogeneity of Network Technologies
In IoT, it is prevalent that the devices are installed with different types of network protocols. Each network protocol has different service types and network conditions. To overcome the challenge of integrating different network protocols, there have been efforts to integrate heterogeneous networks [
54,
55,
56]. Further, direct communication among the devices is not always supported even if the devices are collocated and use the same radio technology [
57]. The IoT-A communication protocol model was proposed by [
58] and accepts standards such as Constrained Application Protocol (CoAP), User Datagram Protocol (UDP), Internet Engineering Task Force IPv6 Routing Protocol for Low-Power and Lossy Networks (IETF RPL), IPv6 over Low-Power Wireless Personal Area Networks. (6LoWPAN), IEEE 802.15.4e, and IEEE Std 802.15.4-2006. However, there is no standard or exemplary technology that can support different network protocols. Inter-operability encompassing these network protocols is expected be a major challenge for constructing the IoT network. Generally, a network translation gateway is required to connect devices that employ different communication protocols [
59,
60]. Nonetheless, forcing all communication through the gateway may result in overhead problems. These issues with integrating various network protocols must be addressed within the IoT network.
Table 4 compares the techniques related to support heterogeneity.
4.4. Software-Defined Network & Network Function Virtualization
In an IoT environment, devices and services have their own policies. To seamlessly operate the devices, services, and platforms, the network must manage the network flow. Specifically, the network manager must control and apply flow rules to the devices and platforms. One of the solutions for this issue is to modify the devices and improve the networking capability. Nonetheless, this approach may increase the cost, and it is time consuming. Specific functions of network equipment are not opened to the network manager, so the network manager cannot easily modify the existing flow rules as the manager wants. For instance, the network manager must access each of the devices to customize the network flow rule. Furthermore, in a conventional network configuration, the router or switch has customized hardware parts or chips that are suited for the network environment. To modify the network environment, all chips and parts of the switch must also be modified, and this process requires many efforts and costs to replace the hardware parts of a router or switch.
To overcome these challenges, the concept of the programmable network has been introduced as the software defined network (SDN). The fundamental idea of SDN is to provide a feature to manage the traffic of the network in a software manner. SDN can be an essential technical feature of IoT, and research related to institute SDN into an IoT environment is currently underway [
61,
62]. SDN separates the control plane and data plane from the network flow to enable programming of the network. SDN can substitute control software for hardware parts. Additionally, the network manager can modify the network configuration according to the current network status.
It is certain that the size of the IoT network will increase. In this particular case, a plurality of network equipment is needed to cover the network. When the network managers want to add network functions, they must buy the functions or new equipment to embed the wanted functions into the current network. To overcome this challenge, the concept of network virtualization [
63] was introduced to easily connect different clients without making a new physical connection. Further, network function virtualization (NFV) supports various services in the network device [
64,
65]. The concept of NFV is to virtualize various functions such as the firewall, DNS, and caching and operate these functions in a software manner. The NFV can provide a different service to each flow with ease, which reduces the network manager’s overhead and cost to change the network service.
4.5. Network Security
IoT devices may obtain visual and the sound information of the user without notice. This phenomenon is not limited to the private sector but also affects the public sector. Devices that monitor car traffic, surveillance, and mass transportation will be capable of communicate with one another. Thus, it is crucial to have a secure environment, in which personal information should not be leaked to other users, even if the user does not have malicious intent. Further, it is necessary to devise a scheme that can protect the devices from malicious attacks.
In [
66], IoT security can be summarized as follows: (i) resilience to attacks that may lead to system failure, (ii) data authentication to defend from forgery attacks such as changing sensor data modification, (iii) access control algorithm for information provider to control the access level of data, and (iv) user privacy preservation to protect the issue in which the server easily infers the user’s private information through the user’s data. With this in mind, the devices themselves should be equipped with a mechanism to protect their operations, and the network itself should be protected. In terms of networking, a security challenge may exist with the tight resource constraints in IoT devices, Distributed Denial-Of-Service attack (DDoS) resistance, and protocol translation and end-to-end security among multiple heterogeneous devices [
67]. It is necessary to devise a security scheme that can protect both the devices and the network to provide secure IoT services to the users.
4.6. Reconfigurable Networking Group
IoT devices should have the ability to devise a network based on their proximity and logical operation of the IoT service. Although the current network is based on the service provider, the future IoT network should have the capability of composing and maintaining a network that is based on location. For example, the devices must provide information that is based on that specific location. Based on the juxtaposed data from various devices, data from the devices in a specific location can provide information that is specific to the physical location of the user. Thus, grouping of the devices based on the specific location is needed. However, if the user wants a service that is not based on the specific location, the devices should be grouped based on the logical operation of the service.
4.7. IoT Gateway
The IoT gateway [
68] is believed to be an important component of the IoT network. The main functionality of the conventional gateway or router is to forward packets to the destination node. The main purpose of the IoT gateway is similar to that of a conventional gateway, but there are some additional features as follows.
First, heterogeneous network connectivity [
69,
70] must be guaranteed. A short-range communication technology is definitely required to provide connectivity to small sensors or devices. These nodes must send packets to the IoT gateway first, so the IoT gateway must support all of these short-range communication protocols. Further, the IoT gateway must support wired communications, high-performance communication protocols including Wi-Fi and LTE, and existing short-range communication protocols including ZigBee, Bluetooth, and Z-wave. Second, network manageability is crucial for the IoT gateway. A conventional gateway manages the nodes in the subnet. However, the concept of network manageability is larger in an IoT gateway than in a conventional gateway. The IoT gateway is not limited to supporting conventional network management functions; rather, it should even update the affiliated devices’ firmware or system. Consequently, the concept of manageability of the IoT gateway has expanded, and techniques to empower the network management is essential for the IoT gateway.
Finally, the IoT gateway must support the protocol or platform interworking. Many novel network concepts such as platforms and protocols, are developed to make IoT environment settle into traditional networks. Nonetheless, these can cause compatibility problems with conventional devices because legacy devices, such as household appliances, are not equipped with platforms and protocols. Thus, compatibility with the conventional platform and standard competition issues must be solved by allowing the IoT gateway to support platform interworking.
Table 5 shows the current research and implementations of the IoT gateway.
4.8. Discussions
The current research on the IoT network can be summarized as follows: Service-oriented network based on CDN and P2P, Platform-centric heterogeneity support, SDN, Object-to-object security, Location- and proximity-based grouping, IoT gateway. The similarity among current IoT network research is that they assume the IP-based client-server model for communication. These studies are essential components to realize the IoT on the current network. However, the existing research direction has some limitations. Most devices are still based on IPv4, which has the issue of a limited number of available addresses. As a result, IPv6 takes the spotlight for next-generation network addressing, and many research and development effort are underway based on IPv6. However, IP-based networking is based on one-to-one communication, in which a device attempts to connect with nearby devices one by one when it wants to receive content. This retrieval procedure may require additional resources and time. Therefore, a service provider with plenty of content is required to reduce this effort. In this case, the users must send the queries to access a content-providing server, which may lead to an overhead problem for the content server. Moreover, the availability of the content is related on the status of a server that has the content, despite the fact that the user has legitimate authority. An ID-based networking concept such as NDN is necessary to solve these limitations and realize a veritable service-oriented network. It is a great challenge to institute this concept into the real network infrastructure. Furthermore, novel technologies such as SDN, content-based routing, context-based multi-connection, naming management, and gateway-based communication that are suitable for the IoT environment are required because satisfaction of ID-based networking does not imply that it can satisfy the IoT environment.
5. Future IoT Network
In this section, we describe and provide insights on our envisioned future IoT network in detail.
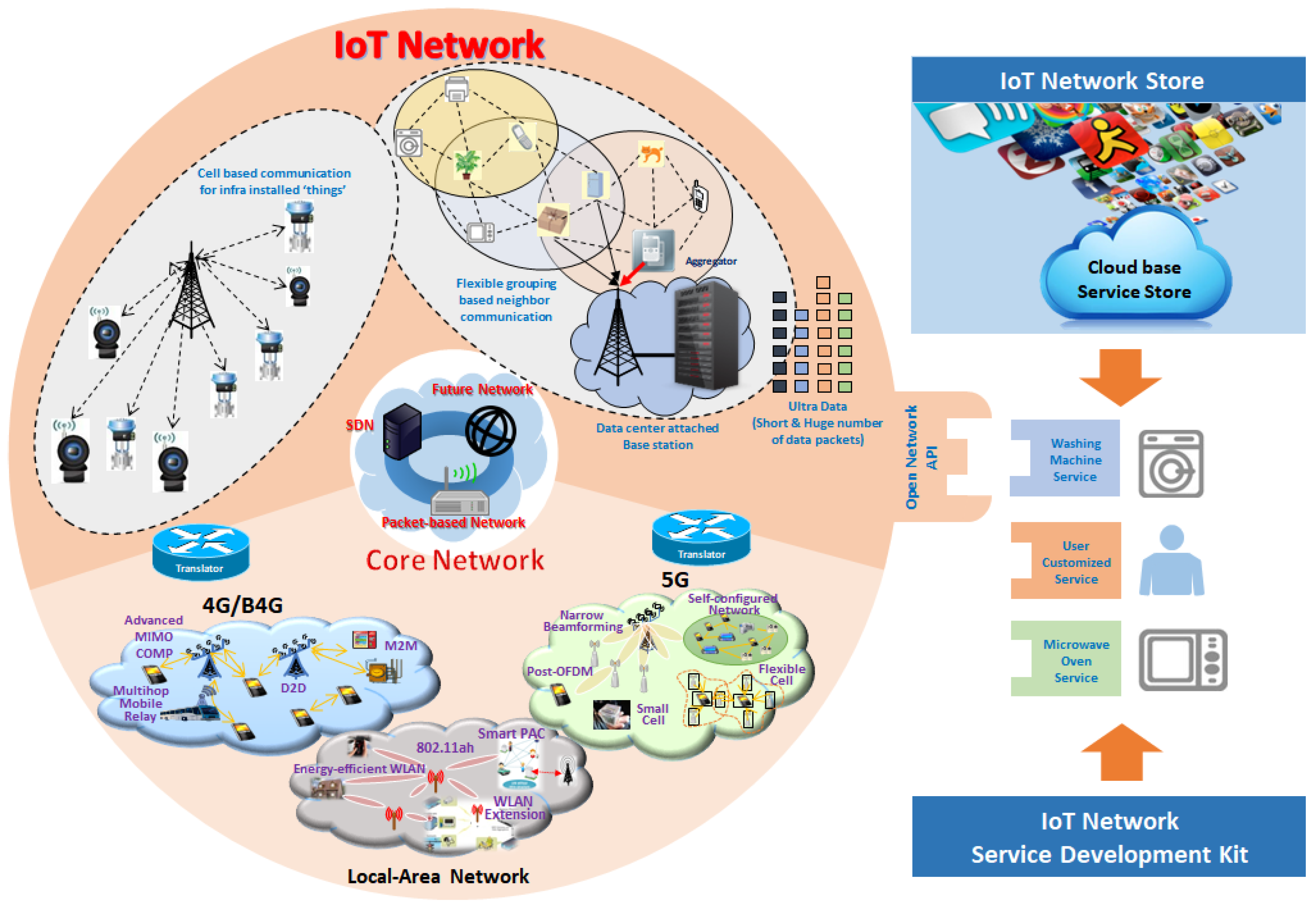
Figure 3 illustrates our vision of the future IoT network. Each component in the IoT network will be explained in detail in this section.
5.1. Software-Defined Network
The advantage of SDN is to enable the users to program the switch. As described previously, SDN has a technical feature that can enable programming of the network service devices [
74,
75,
76,
77,
78,
79]. One of the well-known SDNs is OpenFlow [
76]. It is a programmable network in which the users can program the switch to change the protocol and test a new protocol. There are various functionalities in OpenFlow, but it can be summarized in at least three parts: (i) a flow table with an action associated with each flow entry and to tell the switch how to process the flow, (ii) a secure channel that connects the switch to a remote control process and allows commands and packets to be sent between the controller and the switch, (iii) a protocol that can provide an open and standard way for a controller to communicate with any switch. Instead of relying on a vendor-specific switch, the SDN protocol can provide the feature to program the switch based on the service that the user wants to provide to the other users. Moreover, IoT service providers can use APIs to operate IoT services with SDN-enabled devices. Finally, SDN can be equipped with virtualization, with which the users can differentiate the service by virtualizing the router or the switch. Consequently, SDN can enable physical and virtual object control for IoT.
5.2. Management of IoT Devices on IoT Network
For IoT devices to access the IoT network, the IoT network itself should support a mechanism of plug-and-play for the IoT devices [
80]. Current devices are primarily controlled by users in terms of turning on the device and connecting the device to the network. However, the IoT device should not be configured manually by the users and should be automatically configured. To support this feature, the plug-and-play mechanism is crucial for the IoT network because it can automatically connect the IoT devices to the IoT network. For example, the authors in [
81] proposed plug-and-work to orchestrate numerous devices to automatically connect within industrial and production systems. Plug-and-work concentrates on self-configuration mechanisms by enabling a secure plug-and-work environment for IoT. Nonetheless, the IoT network should be able to provide a connectivity mechanism for connecting trillions of devices and managing networking addresses regardless of the type of network connection.
Furthermore, there are issues with assigning IP addresses to IoT devices and data. To efficiently manage IoT devices, an efficient and scalable addressing scheme for connecting IoT devices to the Internet is needed. One of the solutions to handle the addressing issue in the IoT network is to employ the IPv6 address allocation scheme [
82,
83]. The IPv6 addressing architecture defines two scopes for a unicast address, link-local and global. The link-local address is used for auto-discovery and auto-configuration. It is used for the local network and does not guarantee uniqueness in a larger network. Moreover, it will not be forwarded by the routers to the other links. The global scope address is expected to be used as a globally unique address. Thus, the device can utilize a global IP address to communicate over the Internet and utilize the link-local address to connect to the local area network. Specifically, the Unique Local Address (ULA) is designed for local networks larger than a single link but not for communication with the Internet [
84]. Globally unique addresses (GUA) are administered to provide a unique and routable address for the Internet communication. For devices that do not require Internet communication, the address schemes can be employed as a ULA. However, in case the IoT devices need to communicate in the global network, it can employ the GUA address. Consequently, the IPv6 will not only ease the issue of scalability of the networking address, but it can also be configured in an adaptive manner to increase the efficiency of the IoT network [
85]. Further, with the IPv6 technologies to maintain and allocate IP addresses for IoT devices, the IoT network can handle connectivity management from a local network to a global network.
5.3. Supporting Heterogeneity of Network Technologies
Many network protocols, including radio-frequency identification (RFID), Wi-Fi, Bluetooth, ZigBee, 3G, and LTE, work independently. A unifying architecture that can support heterogeneity of networking protocols, interoperability among network protocols and the devices is needed to enable the IoT network [
86]. In [
58], the authors proposed six layers for the IoT network, which are listed as follows : physical layer, link layer, ID layer, network layer, end-to-end layer, and data layer. This is different from the legacy networking stack, but the main problem with this protocol stack is that it is focused only on the LoWPAN networking technology. In terms of wide-range communications, a large proportion of the communication features of IoT is concentrated on wide-range coverage as stated in the Weightless open standard [
87]. It is true that IoT devices should support wide coverage; however, the current commodity network protocol requires additional technical features and chips that can support low power and yet increase communication coverage to support this feature. This will represent an additional cost for the manufacturers. To reduce the additional cost to enable IoT, the future IoT network should incorporate the idea of supporting interoperability among various network protocols. To encompass the feature to support different network protocols, the IoT network should be able to acquire the data from different networking protocols. Furthermore, the gateway for the IoT network should also support acquisition of various network protocols and connect the devices to the IoT network.
5.4. Connection Management
Each device may have different a communication protocol, so the connection management object may support different standards to nodes that belong to the user. The IoT home gateway or access point (AP) may manage the different standards, but there is a problem when the nodes are out of the communication range. For example, cellular communication, which provides a wide-range connection to the device, cannot be installed in the small sensors owing to the problems of price and battery consumption. Further, communication management is required in both the static and nomadic environment because a guest node that temporarily visits the network area may exist. The concept of grouping [
88,
89] can be a good candidate to manage the connectivity of the devices. For instance, grouping devices can be categorized as follows: physical grouping and logical grouping.
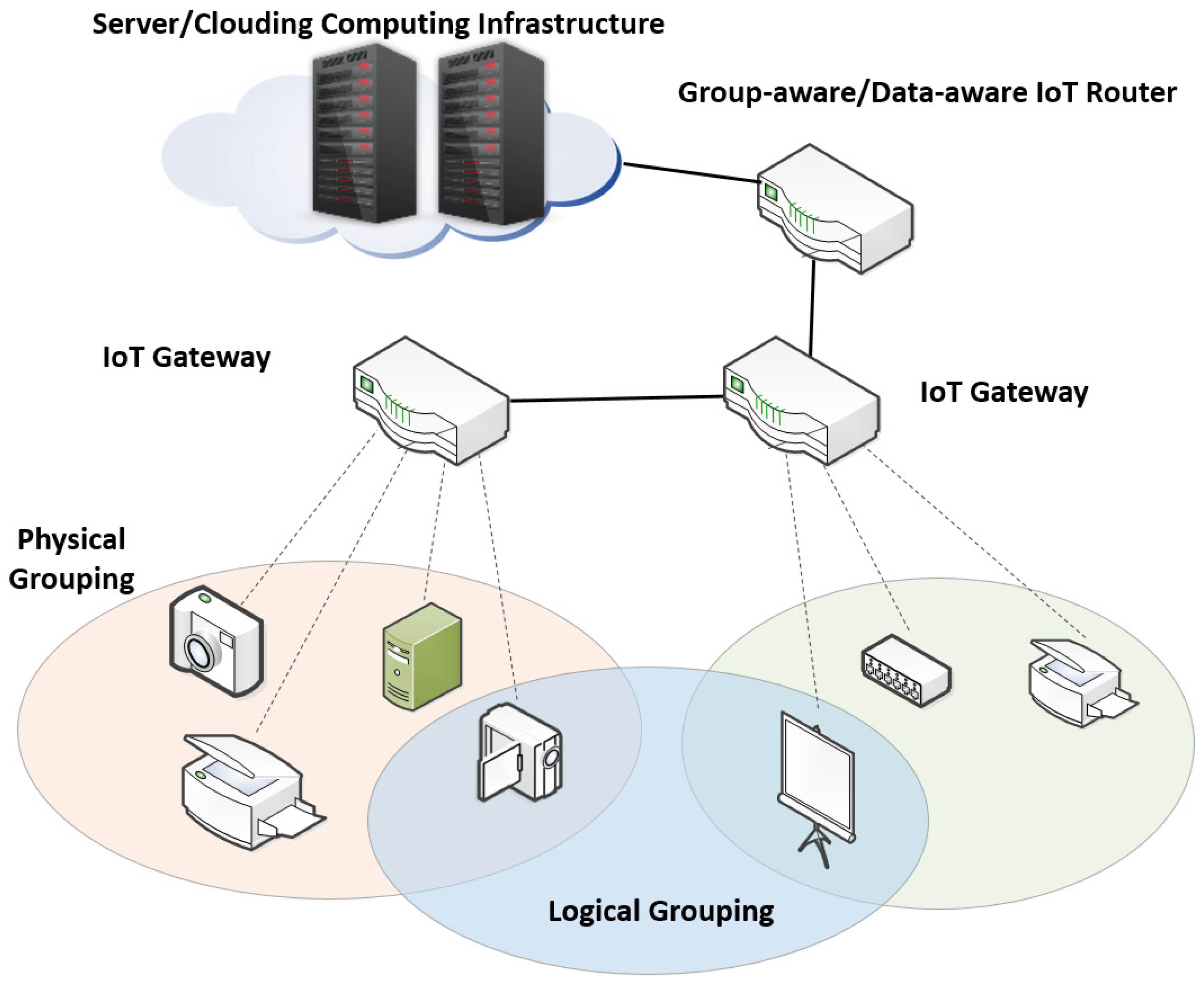
Figure 4 and
Table 6 elaborate the concept of physical and logical grouping in the IoT environment. In terms of physical grouping, devices can be grouped based on their physical proximity. Meanwhile, connection among equal IoT service task devices is needed to support the service-oriented network without establishing direct connections with one another. In this case, a new manager, which is the main agent of the service or network management-available device, must manage this group of devices, which can be classified as logical grouping. With these two categories of device grouping, any IoT service can provide effective services for users.
5.5. Network Security
Guaranteeing network security and privacy in the IoT network is an important component. In this subsection, we describe the security issue of the future IoT network [
90].
5.5.1. Data Security
Data security is one of the important issues in the security area. The confidentiality of the IoT data may not be regarded significantly because many IoT data can contain simple data such as temperature, humidity, and others. However, some of the data such as credit data or request data to control IoT devices may indirectly contain the user’s private information and affect the user’s daily patterns. For instance, when these data are forged or falsified, a malicious attacker can easily control the user’s IoT devices. In this situation, a malicious user can easily connect the user’s IoT device and obtain information without any restrictions. Furthermore, the attacker can easily change the user’s device to use it as an attack by utilizing the user’s cheap and disposable IoT device to conduct a DDoS attack [
91]. With IoT devices, DDoS attack can harmfully affect the IoT network and services. Consequently, a malicious attempt to control the things of the user can affect the user’s life and even the industry.
One of the simplest solutions to effectively secure data can be to utilize the existing techniques such as Public Key Infrastructure (PKI) or Elliptic Curve Cryptography (ECC) [
92,
93]. However, these techniques require enormous amounts of computational power and battery resources. Although current mobile devices may support the security schemes, many IoT devices have limited power and computational resources. Therefore, a light weight encryption algorithm [
94] and key management protocol are needed for IoT devices. Additionally, there are some DDoS-preventing algorithms [
95], which use null routing or unauthorized packet filtering. However, these solutions cannot defend the reduced throughput because the router must receive the DDoS packet and filter it. Furthermore, data requests from various light weight sensors may lead to similar behavior to a DDoS attack in the IoT environment. Specifically, if the user requests tremendous amounts of data from various light weight sensors, even if the data may be temperature or other light density data, receiving these data can cause behavior similar to a DDoS attack for the user. Thus, even if the user has not intended to receive a DDoS attack, similar behavior to a DDoS attack may occur if the data security and control algorithm is not researched.
5.5.2. Privacy
Privacy is a critical issue [
96,
97] in the IoT environment. Many users will realize that IoT can improve and even change their daily patterns. Nonetheless, most users are also concerned with the privacy issue of IoT. This concern is appropriate because anyone can connect to another user’s devices and collect information. In this case, user s’ private information can be leaked to the information collector. For example, when an application server wants to collect the temperature from all users in a specific area, this server sends a temperature collection query to all nodes in the area. The nodes that respond to this query may reply with their IP address, location information, and temperature data. Although some of the data may not be related to the privacy issue, other data, such as the user’s location, may violate the user’s privacy. Because the server can handle all types of user data, it can easily see the private information of the user. If this server acts maliciously, this information can be abused, and the replied user’s privacy is not guaranteed.
To overcome this challenge, we consider two simple methods that can use current privacy preservation techniques to prevent the leakage of users’ private data. In the first method, the user’s device ignores the query that needs privacy-sensitive data. This method can easily prevent privacy invasion, but it may not be suitable for the purpose of IoT. The second method is to construct the network architecture, in which the user’s device returns only the requested data without including privacy-sensitive data. However, essential data, such as IP address or location information in the location-based service, cannot be hidden or ignored to receive this service. From the server side, the integrity of the received data from the user’s device cannot be guaranteed with the second method. Therefore, research on a privacy-preserving cryptography solution that can maintain the concept of a service-based architecture and content-based networking, is required. Recently, work in [
98,
99] has attempted to follow this method with a fully decentralized anonymous authentication protocol [
98] or a novel framework for privacy preservation [
99]. However, it is difficult to implement them in the IoT environment because such algorithms do not consider content-based networking. Consequently, it is crucial to protect the user’s privacy in the IoT environment.
5.6. IoT Gateway
The IoT gateway is the core component in the future IoT network.
Figure 5 presents the overview of the IoT gateway.
In this subsection, we describe the key features to compose the IoT gateway.
5.6.1. Network-to-Network (N2N) Communication Support
In the IoT environment, it is crucial to manage the information such as affiliated node attributes, identification of holding contents, and network status, in the group by the network management object to successfully utilize an information-centric network (ICN) [
100,
101] or content-distributed network (CDN). Further, these types of information should be shared by the content management server or neighbor network management object to effectively conduct context-based multi-connection or content-based routing. We believe that network-to-network (N2N) communication is needed to share non-real-time data from the network to other networks without configuring an end-to-end connection across two or more networks. A network management object may become a good candidate to share the network information, and it can directly connect with the core network to share other network management objects. However, sharing this information through a newly constructed network connection may cause overhead problems, which can lead to throughput degradation at the core network side. A technique that can transmit the data without reconfiguring new networks among the networks is necessary to solve this problem. Consequently, an N2N communication protocol is needed for the IoT gateway, which can act as a network management object.
5.6.2. Routing
One of the important features of the IoT gateway is the routing algorithm, which includes not only the routing for the sub-network of the IoT gateway but also the routing for the affiliated core network. The routing for the internal network, which is the group of nodes in the same subnet, is based on a multi-hop network such as a sensor network [
102,
103]. This method seems to be sufficient because IoT nodes are primarily composed of the sensors. Nonetheless, it is still a problem to apply in the IoT environment. First, the IoT environment assumes that many sensors or devices may have high mobility. Following this property, devices that belong to the user will probably be connected to the near network management object when the user is in transit. Especially, some types of devices, such as sensors, have a higher probability than the other devices to connect to the nearby network management object owing to limited battery resources. A physical network group may break when a device attempts to connect to the nearby network management object, and managing the network is impossible. Thus, to prevent devices from connecting to different physical groups, a routing algorithm for the nodes attached to the IoT gateway is needed.
Regarding the routing issue within the core network, most of the existing routing algorithms are based on the target node’s IP address because a sender transmits to a specific destination node in the existing network. However, targetless requests to acquire information and connection availability is increasing in the IoT environment, as we introduced in
Section 4.2. There have already been some researches [
104,
105,
106] to overcome this challenge. A solution of Bhowmik et al. uses workload-based indexing technique to provide bandwidth-efficiency. Jin et al. [
105] selects reliable communication links to node to reduce redundant communication traffic, and Vural et al. [
106] caches transient data in the routers to reduce the delay by data item lifetime. However, we propose a new following algorithm, which utilizes the ID of the things rather than IP address-based routing from the core network, and it can be an example of possible suggestion to overcome this challenge.
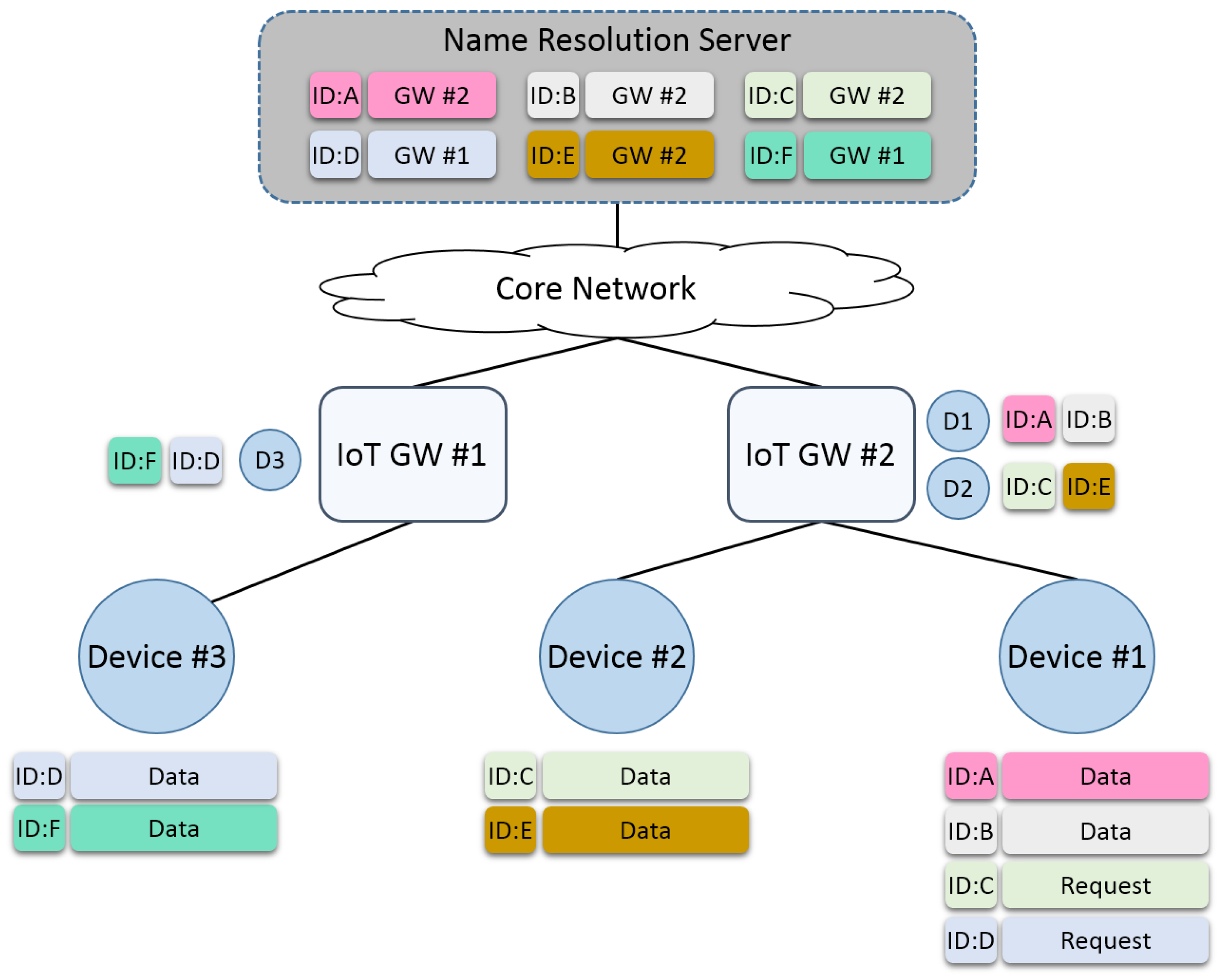
Figure 6 presents this scenario when an ID-based routing algorithm is needed.
We assume that device #1 needs some content, whose IDs are C and D. Device #1 sends a request to IoT gateway #2 that it needs content C and D. Gateway #2 then knows that device #2 has content C, so it sends a message to device #2 to obtain content C. However, it does not know the location of content D. There are three solutions by which gateway #2 can act to obtain content D.
The first method is that gateway #2 performs N2N communication with IoT gateway #1; it may know that gateway #1 has content D. Therefore, it sends a request to gateway #1 for content D. However, this solution is unavailable when gateway #1 is too far from gateway #2 to perform N2N communication. Another method is that gateway #2 sends a request to a name resolution server that has numerous IDs and locations of content. Gateway #2 can obtain the information that gateway #1 knows the location of content D. This solution is simple to realize, but the overhead of maintaining the server is high. The last idea is that gateway #2 performs ID-based routing to find the location of content D. In this case, gateway #2 forwards the request packets to nearby networks. When gateway #1 receives the request packet, it replies with the messages and content to gateway #2 using a backward technique. This example is simple to directly embed in the core network, so many novel studies are needed for the content-based routing algorithm.
5.6.3. Mobility Control
Mobility is already an important issue in legacy networking and communications. Various devices including cell phones have attributes of mobility, and many studies have proposed mobility control in both the cellular network and IP network. The cellular network, which is proposed to provide plenary communication anywhere, solves some critical problems by reporting its location to the mobility management server. Nonetheless, a cellular network is based on mobility control, which is possible only with an enormous number of servers and extra-large infrastructure. In addition, there is a problem that cellular-based devices consume significant battery resources to maintain connectivity.
In terms of IP networking, some solutions [
107,
108] such as mobile IP, have been proposed to support mobility. These solutions are difficult to adopt because of message authentication, connection delay, and the complicated management of IP. Thus, mobility control in an IP network is performed only when the client attempts to reconnect when the connection is broken. Although it is a very simple solution, seamless handover and connectivity are not guaranteed. Further, this may lead to degradation of network performance and Quality Of Service (QoS) in the end.
Therefore, a novel concept of mobility support is required. Moreover, it is advantageous to support mobility control by the network management object in terms of reliability instead of constructing a mass server or new infrastructure such as a cellular network. Because the device normally maintains continuity when it moves except during power-off, the nearby network management object can control the mobile devices with ease. For example, when a mobile device identifies that it is moved, it sends the mobility message to its network management object. The network management object then forwards the server’s data to nearby objects, and the mobile device can receive the data seamlessly.
5.6.4. Packet Forwarding
As we previously mentioned, searching an appropriate node for content and sending a connection request may cause a considerable delay in a targetless connection. For example, if the user wants to adjust the temperature of the room, every sensor in the room must check the temperature and the number of people within the room. With this information, the sensors send the sensing data to the administrator server in the existing network. Further, the administrator server analyzes the received data to select the rooms in which temperature control is requested and establishes every connection to send the temperature control order. This process is time consuming because it requires numerous steps to merely control the temperature of the time.
To reduce the time delay and improve the efficiency to control the sensors, a targetless connection is required to solve the delay problem in the IoT environment. Additionally, packet forwarding [
109,
110] or a multi cast technique is appropriate for this type of connection because these algorithms can send multiple data to multiple destinations simultaneously. However, these techniques basically generate many packets for communication, and some technique to improve network efficiency is needed.
5.6.5. SDN for Convergence (C-SDN)
In the IoT environment, SDN is needed from the end-level because each device needs a different traffic rate to satisfy QoS, and guest devices that demand a connection to the IoT gateway must be managed. Further, the content not only uses the data of the local area’s sensors or actuators but also needs the data from various networks. In this case, the IoT gateway must provide the data convergence concept to rapidly collect required data and not maintain the expired data or content. For the IoT gateway to be deployed, it is crucial that it have a data convergence unit to process the tremendous volume of data and provide the customized data to the users. It is crucial to have a feature of data aggregation to collect multi modal data, converge with the legacy sensor network’s information, and transform the acquired data into transmittable data. However, it is not limited only to collecting the data; rather, it should be able to filter and analyze the data based on the aggregated data to enable the users receive accurate and comfortable service.
5.6.6. Security of IoT gateway
Basically, the IoT gateway manages the IoT devices that are connected to the gateway. The IoT gateway can serve to reply to the query because it has already saved and collected the data from the connected IoT devices. In this case, the IoT device is not required to consider the confidentiality of its data. However, data confidentiality must be considered between the IoT gateway and the requester [
111]. The IoT gateway has better computational performance and battery power than the IoT device, so employing a well-known security algorithm is possible. To guarantee privacy, a novel privacy-preserving security algorithm seems to be the best candidate, which can hide private data but allow the receiver to operate without revealing it. As we previously introduced, this algorithm still does not exist.
Further, the communication medium of the IoT gateway and the IoT device is usually based on wireless communication, where eavesdropping can be possible. Nonetheless, the IoT device is based on a battery, so adoption of a security algorithm can be an overhead. Therefore, a simple and light weight security algorithm or adaptive encryption scheme that can distinguish the data to be encrypted is needed to protect the IoT data.
Node registration and authentication [
112] is also an important issue in the security of the IoT gateway. Basically, owing to the mobility of the node and to guarantee connectivity with all devices, there may be many registration types, such as guest, master, and so on. For instance, a guest node is a foreigner of the group with limited communication. The master node can manage all nodes in the group and control the networking of the group even if it is out of the home network. Finally, a member node can be a user’s thing and can utilize the network in general. Therefore, flexible node authentication is required to support the various devices that have a connection with the gateway.
6. Conclusions
Current IoT research has been classified in terms of layers of service, platform, network, and device. In this paper, we focused on the network layer, which we believe is the most important part of realizing the IoT environment. We surveyed the IoT network and presented insights about the future IoT network. The success of IoT will be based on the novel architecture of the IoT network. Without a well-designed network architecture for the IoT, IoT services and devices will not seamlessly operate and provide necessary services to the users. To give insight to researchers, we introduced a novel architecture for the IoT network and some techniques that are predictable or certain in such an architecture, such as IoT network management, connection management, grouping and privacy.