1. Introduction
With the development of computing technologies and the expansion of smart-devices and inter-network protocols, hospitals and healthcare organizations are adopting the Telecare Medical Information System (TMIS). The medical identification process has become more resourceful, trustworthy, and efficient by using TMIS. Some Telecare services have been projected in the modern age to ease the workload on the professionals, for example, by methods such as automated healthcare devices, distant health nursing, and patient’s health monitoring for remote areas. It is considered as a time-saving, economical, and easy way to access health care facilities remotely. TMIS can lower societal and medical operating cost with improved quality and efficiency [
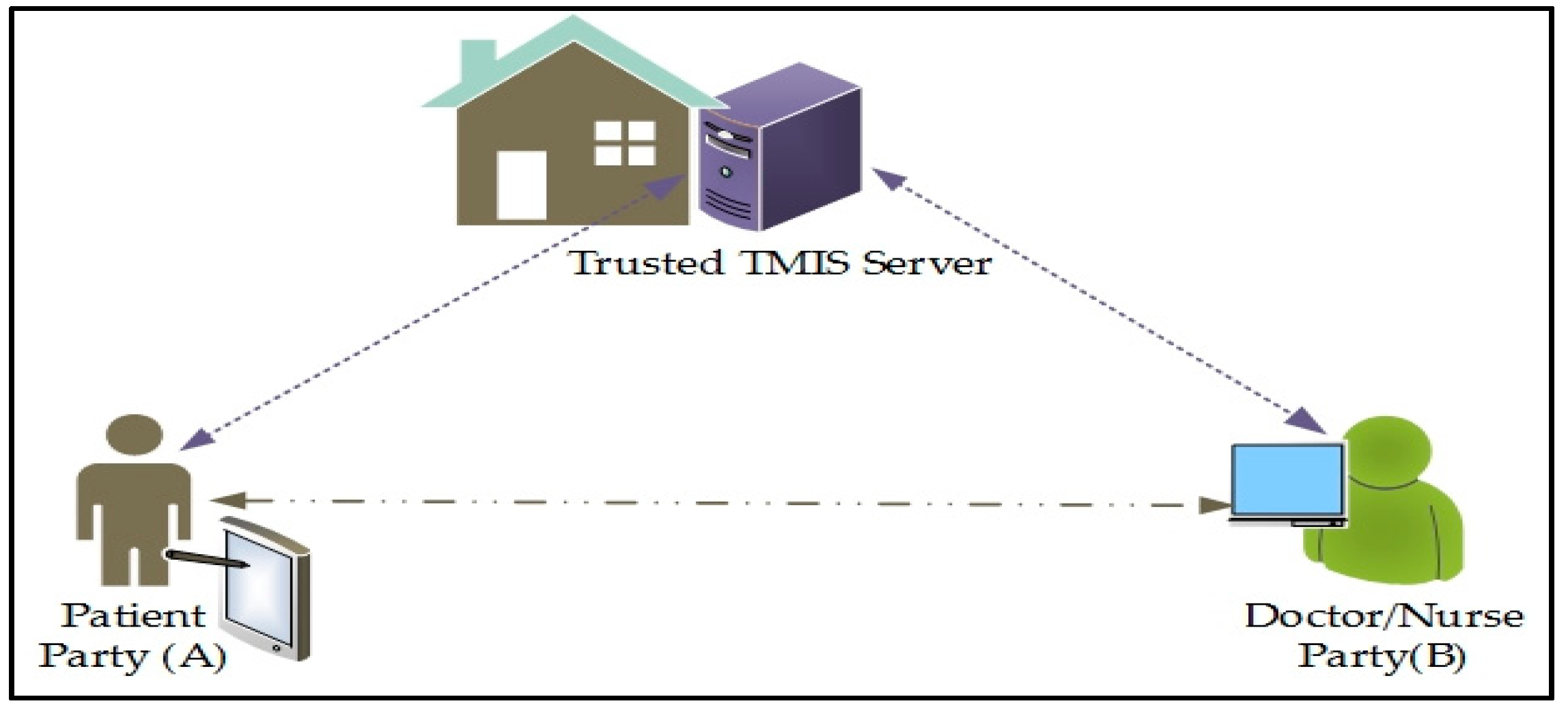
1]. Patient authentication is mandatory to guard against data forgery, misuse, and falsifying the original information by unauthorized active or passive parties. In TMIS, a trusted medical server is responsible for registering all participants, including doctors, nursing staff, and patients, as illustrated in
Figure 1. The remote healthcare server keeps the advanced clinical information of the register patients and gives different administrations like healthcare education, doctors, doctor’s facilities, remote medical aid, general healthcare, private care benefit, and the most important is medical prescription. Registered TMIS users for medical services can utilize smart cards to access medical devices and transmit collected statistics to the medical server using a public channel. An intruder may likewise find access over the public open channel. The adversary can eavesdrop, block service, modify, delete records, and can also reply to a message broadcasted over an open channel. Therefore, authentication is mandatory for providing information security, records honesty, and confidentiality of data. It is necessary to overcome all existing threats that are major hurdles and make TMIS trustworthy. A session key must be established for a short-time secure communication between two parties where a new key is established for every new session. We have considered various advanced cryptographic calculations like non-revertible one-way hash function, Rivest-Shamir-Adelman (RSA), Elliptic Curve Cryptography (ECC), and chaotic maps cryptosystem. Despite the fact that both ECC and RSA cryptosystems offer an equal level of security, ECC is additionally advantageous as compared to RSA with respect to computational efficiency [
2].
An Internet of Things (IoT) is composed of a vast number of small and large devices that are using the internet for sharing data across the nodes of different networks. In an IoT environment, TMIS can serve patients to save time by remotely accessing consultants and doctors by using the new generation of internet. IoT supports a collection of objects, devices, and networks in surroundings to develop a large number of smart applications. It can undeniably improve the identification and dissemination of information regarding emergency situations where appropriate medical aid is mandatory to save precious lives. IoT can also support integration mechanisms for all physical objects with embedded systems or cyber physical systems for monitoring patients at distant locations. It improves diagnosis at the patient’s home for better usefulness and effectiveness regarding medical services [
3]. IoT promises an attractive future networking prototype.
Secure authentication and session key establishment schemes enable secure communication for health care services. A three-party password authentication key exchange (3-PAKE) scheme provides mutual authentication between doctor-patient-TS at the same time and hides identities from the adversary [
4]. It helps in maintaining a secure link by using a common session key for specific communication. Schemes [
5,
6,
7] discuss secure session key establishment between participants but later [
8,
9,
10] identified that these plans are vulnerable to man-in-the-middle attack and undetectable online and offline dictionary attacks for guessing passwords. ECC-based schemes are also explored to evaluate the applicability of efficient solutions with desired security strengths using small key sizes as compared to preliminaries.
The main problem and common deficiency in these schemes are that user anonymity is not provided because the user’s identity is sent without encryption on an open channel. The participants’ credentials are insecure, causing a lack of anonymity and un-tractability [
11]. The scheme is also vulnerable to identification-guessing attacks and tracking attacks. Specifically, a participant’s identification might get exposed by an intruder when it gets disconnected from the internet. Furthermore, an adversary can tune into a selected user with the information the user provided within the login request message.
This paper presents a Secure Participant Authentication and Prescription Safety (SAPS) scheme for TMIS to accomplish participant’s anonymity and un-traceability. The process begins when the patient registers with the trusted server that validates the communicating parties and then establishes the session key. We have used ECC in this study; results showed that an anonymous ECC-based presented technique has secure and well-organized authentication protocols with foolproof security along with user confidentiality protection which is practical for TMIS. Formal protocol secure analysis using Rubin Logic was used to evaluate their safety performance and reliability. Using the proposed protocol patient can get a medical prescription from physician securely and interacts with health service provider anonymously using TMIS keeping identities secret.
The rest of paper is organized as follows;
Section 2 includes the previous work which has some related information regarding the present study and an overview of existing practices. The system model and problem statement are presented in
Section 3.
Section 4 explores the proposing anonymous SAPS scheme in details with formal steps. Formal analysis using Rubin Logic is presented along with security analysis in
Section 5. The performance measures and results have been included in
Section 6.
Section 7 presents the conclusions of the work and a future roadmap.
2. Literature Review
This section explores some well-known existing schemes related to the security of TMIS and health care services. In this regard, different 3-PAKE and ECC-based schemes are reviewed to analyze the effectiveness, usefulness, and security strengths for providing reliable security solutions. Xie et al. have proposed an ECC-based efficient 3-PAKE scheme [
12] that overcomes the flaws mentioned above but suffers from offline password guessing attacks. Che et al. have proposed modular exponentiation on an ECC-based 3-PAKE scheme [
13] to make it more complicated for the attacker, but these operations require huge computational cost as compared to existing counterparts. Wu et al. have presented the concept of the secret password and smart card-based verification protocol [
14] for TMIS by utilizing the discrete hard logarithm problem (DHLP). It pre-registers to stay away from the exponential mathematical computations during authentication stage. In three-party key exchanges (TPKE) [
15], He et al. has found some flaws in [
14] and presented an improved scheme that handles impersonation and insider attacks which made the existing scheme vulnerable. Later on, in scheme [
16], Wei et al. explored both [
14,
15] schemes and identified the vulnerability of these schemes for offline password guessing attacks, dictionary attacks, and inability to maintain user un-traceability. To overcome these drawbacks, Wei et al. have improved protocols and presented a user authentication scheme for TMIS that can uphold different attacks. Moreover, Zhu et al. [
17] also identified the offline password guessing attacks in these schemes. To overcome issues in [
17], Pu et al. [
18] has devised a new user authentication scheme applying smart care which is a user password-based identification that provides user anonymity. This scheme is based on an elliptic curve cryptosystem that provides the same security level as RSA with less key size.
Chen et al. [
11] highlighted the client anonymity of Khan et al.’s technique [
19] but it might be defenseless against insider attacks because all the lawful clients share the secret key. It presented an efficient and secret identity-based validation and secure protocol for TMIS that generates random identities for every exchange in a session to sustain a strategic distance bwetween individual data about the client and the danger of identity theft attack and ensured that their protocol accomplished client privacy. The scheme is a successor and much preferable to the previous responses for use on mobile devices. The scheme does not provide anonymity of the user and is vulnerable for identity guessing and tracking attacks.
In [
20] Kumar et al. has presented a smart device authentication scheme in a WSN environment and found that these schemes are suitable for TMIS and fulfill all prerequisites for medical device networks. Later on, He et al. [
21] found that some special insider attacks in medical device networks such as offline password guessing attacks occurred and the system was unable to handle anonymity in [
20]. A user anonymous authentication scheme has been presented to handle remote medical services applying in WSN to resolve this issues. Nam et al. [
22] pointed out some flaws in [
21] for user anonymity and smart card theft. By exploiting symmetric encryption and secure key management for message integrity, Xue et al. [
23] presented a temporary credential-based secure key using a one-way hash function and XOR operations. It enhances security fundaments without considerably expanding the memory requirements. In [
24], Li et al. pointed out that scheme [
23] is unable to protect against stolen-verifier attacks, denial of service attacks, smart card theft, and participant’s signing attacks. Turkanovic et al. presented a secure hash function-based user prediction and secure key management protocol [
25] that ensures security with low energy consumption. Amin et al. [
26] identified that the scheme [
25] is vulnerable to offline dictionary attacks, password guessing attacks, smart card theft, and has an inefficient authentication process.
IoT can be an appropriate approach to support health care systems by the technological advancements that enable the outlining of new advanced strategies for the treatment of many diseases, e.g., by the surveillance of chronic diseases to assist doctors to work out the best treatments, as projected by [
27]. Due to the ubiquitous computational nature of IoT, all the TMIS entities may be monitored and managed continually. Mobile healthcare (m-Healthcare) is an associate economic model to give patients with the right of entry to resources, about past and present health records, blood pressure, and heart rate measurements. Additionally, hospitals and healthcare associations offer on-demand services hosted in the cloud, reducing the equipped costs and overcoming the constraints of standard medical treatment. On the contrary, the privacy of private healthcare information continues to be a challenge to be faced [
28].
Rahimi et al. [
29,
30] introduced a more secure and powerful user authentication and key agreement technique for fitness-IoT structures which requires considerable processing power. It exploits the property of a sensible gateway in fog computing for critical and security services-associated organization. IoT technologies for healthcare achieve standardized medical care [
31] that is frequently improved by further automating the tasks that can be performed without human interaction. In this experience, IoT-based healthcare permits remote monitoring and management of large amounts of medical data using cloud services. Yeh et al. [
32] highlighted the idea of an ECC-based unique participant’s verification protocol to get higher performance and security in a smart medical information system. ECC was first presented in [
33,
34] by utilizing a logarithm problem that can do a much better job with a smaller key length as compared to well-known existing schemes with larger key sizes [
35]. By these assumptions, it is stated that ECC authentication schemes are very appropriate for resource-constrained and remotely accessible devices.
4. Secure Authentication and Prescription Safety Protocol
A novel protocol for TMIS is presented to protect patient’s privacy and satisfy the security requirements. Mutual authentication enables the communicating parties to verify each other’s identities. The proposed Secure Authentication and Prescription Safety (SAPS) protocol demonstrates that it is dynamic and overcomes the above-highlighted flaws in the existing schemes. In SAPS, user authentication and verification are performed by the trusted server (
TS). The patient and doctor/nurse are the sender and receiver nodes, respectively, in the proposed scenario to establish the secret keys using SAPS. In this section, all the protocol steps are elaborated on, along with a description of the message contents of a SAPS scenario. It includes a trusted server (
TS), patient (A), and a doctor/nurse (B). ASAP provides a secure link for the Patient (A) to communicate securely with a physician to obtain a medical opinion. We highlight that ECC-based mutual authentication is secure against numerous significant attacks and improves the communication and memory requirements of authentication. Considering the positive characteristics of ECC, such as the shorter secret key size and computational efficiency, it is attractive to establish an ECC-based anonymous 3-PAKE protocol to protect TMIS users. By exploring existing literature and studies, there is no such system based on ECC that gives anonymous 3-PAKE protocol to authenticate users without knowing their private information publicly. It achieves its security benefits due to the hardness property of the EC Discrete Logarithm Problem (ECDLP). A list of useful notation for SAPS is listed in
Table 1.
In the SAPS protocol, we have assumed that during the registration phase, the TS provides masked identities for both the patient and doctors at the point of registration. Participants provide some secret credentials, such as biometrics, to verify their original identities and record the time of service request. The TS uses the parties’ secret credentials for future verification, keeping their original identities and private information secret. Besides this, the authentication protocol satisfies the following functions and security requirements to achieve credible and secure authentication and data sharing in TMIS.
Person anonymity: In an authentication mechanism, despite the fact that an attacker extracts some and can eavesdrop on the shared message within the communication network, the legal participant’s identity is kept anonymous from the intruder.
Identity proof: the process in which both the user and authentication server prove their identities before accessing each other. Numerous steps are performed to achieve mutual authentication to check the integrity of all transmitted messages.
Session key management: When the verification method is consummated, the consumer and server must present the consultation key to each other.
Password verification manner: If a person has entered an incorrect password within the authentication section, the password has to be detected earlier than the check phase.
Person cordiality: An authentication mechanism system provides a password change method through which an individual may facilely change their password without communicating with the server.
Robustness: An authenticated key acquisition mechanism has been engendered, and has to be resistant to extraordinary types of assaults, insider attacks, off-line password conjecturing attacks, replay assaults, and consumer impersonation assaults. Besides this, in the proposed protocol, the TS partially establishes a session key between each party. Using the secret credentials generated by the TS, the ends parties establish a session key for the particular session which helps to protect participant identities and ensure un-traceability.
During authentication, a new patient (A) and doctor (B) submit their original identity to the TS using a secure channel. After receiving their network joining request, the TS generates shadow-IDs for each participant and stores them in its database. The shadow-IDs of each participant is to establish anonymous joining of the patient and doctor and to keep prescriptions and private data secret. SAPS is explored in a stepwise manner as follows.
A. Step-I: Initialization by Patient (A)
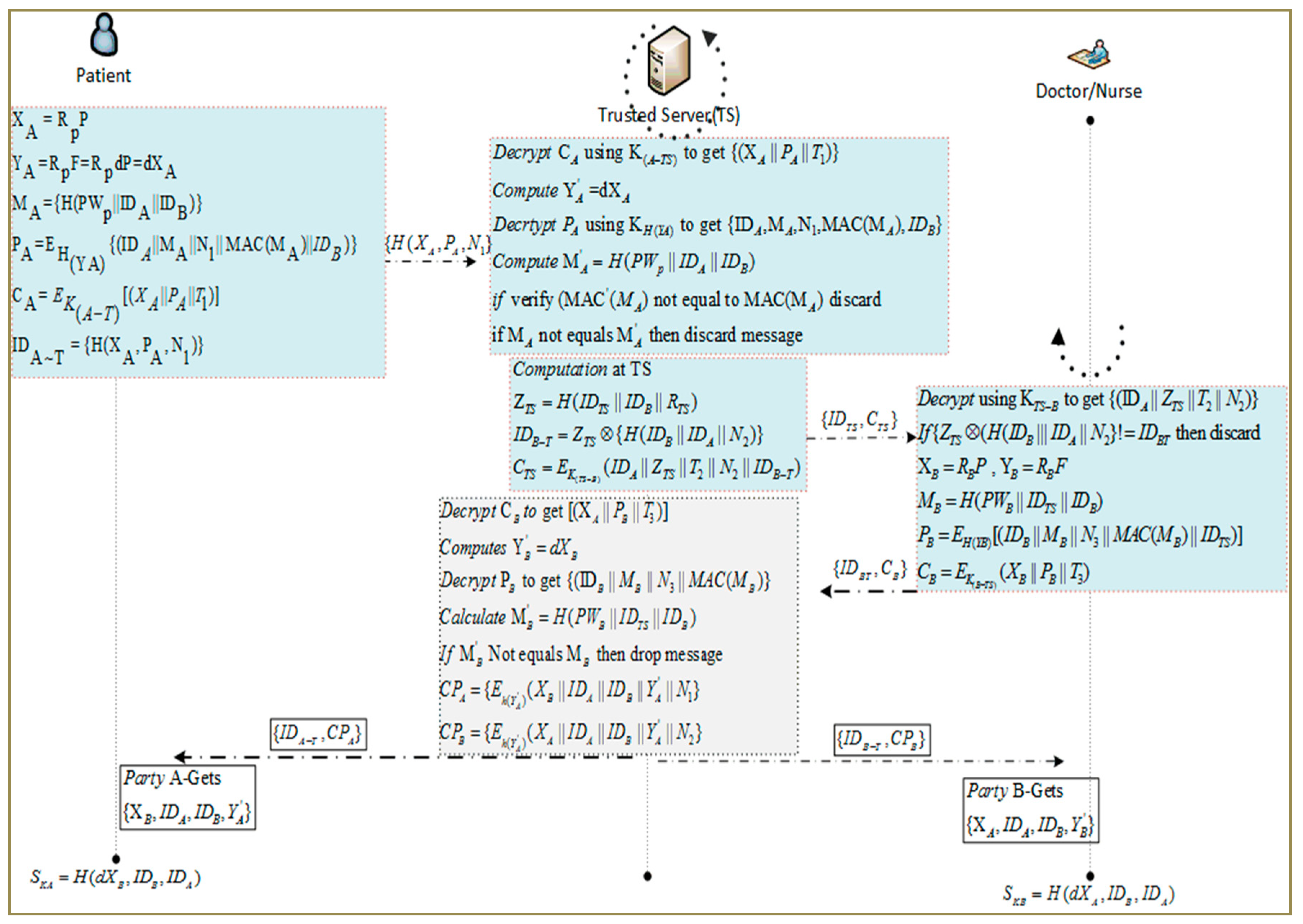
At the beginning, Patient (A) chooses a random number from a finite field and computes secret parameters. After that, is calculated by multiplying random number by an ECC-based generator of large order n. Similarly, is the resultant of and the TS’s public key F that is equal to , where is random number a from finite field selected by TS. For level 1 encryption of security credentials, a hash of is taken to prepare key . Patient (A) prepares a message that contains hash of IDs and as the patient’s password and Message Authentication Code (MAC) is used for providing message integrity on the server side. Patient (A) calculates and includes PWp to keep it more secure. In our proposed scheme, an intruder is not able to get the IDs of A and B but if in any case these values are exposed, then the exact hash value cannot be calculated because of the missing PWp that is held by the Patient (A) and TS only. For transmission to the server, the patient computes cipher text which is encrypted by the patient’s generated secret key as shown in step (iv). After that, a cipher text is generated using a pre-established key . In step (vi), a temporary ID as of the patient is obtained by taking the hash of the and is used for the current session only. The new is never transmitted and can be calculated at the TS using where can be extracted after decryption. It encrypts the parameters using where, is timestamp. Patient (A) transmits to trusted server {} for authentication.
- (i)
- (ii)
- (iii)
- (iv)
- (v)
- (vi)
B. Step-II: Verification at Trusted Server
Upon receiving form Patient (A), the TS decrypts the cipher text to get . It also checks the message freshness by taking the difference from to guard against replay attacks. After that, the TS computes the temporary key of the patient by multiplying the received with d which was pre-generated by the TS as . To verify whether the message is original, the TS computes the Patient’s (A) masked identity as . It also decrypts to obtain security credentials, including , N1, MAC (, and . The hash of these values is calculated as and is then compared to verify the equality of and to ensure message integrity. Otherwise, the message is discarded. The ( provides data integrity for . The trusted server computes the following steps.
- (i)
Decrypt using to get {}
- (ii)
Computer
- (iii)
Decrypts using to get {, N1, MAC, }
- (iv)
Compute:
- (v)
If Verify then discard
- (vi)
If NOT equals then discard message
C. Step-III: TS-based Mutual Authentication of B&A
After verification, the TS picks a random number and then computes using identities of B and TS. It also generates a nonce number to get its hash with identities of communicating parties A and B. After that, TS calculates the XOR of hash value with to get a new temporary ID for B. The value of is obtained by encrypting using the pre-established key . The TS transmits the temporary identity and cipher text to B.
- (i)
- (ii)
- (iii)
Doctor/Nurse (B) receives the message {} and decrypts it to get the other party’s prescription details and TS validity by computing the set time stamp threshold value, nonce number, received masked-ID values, and decrypted message using the pre-share key from the TS. At each end, entity is used as a key to encrypt secure credentials in addition to MAC and the hash function application to make them more secure.
- (i)
Decrypt using to get
- (ii)
If NOT Equals then discard
- (iii)
,
- (iv)
- (v)
- (vi)
TS receives the message and decrypts it to get . After that, the TS computes which is equal to calculated at Doctor/Nurse (B). It further decrypts the to get and , as illustrated in steps below. After that, the TS verifies the message’s integrity by computing and comparing the hash of the message. Finally, it computes the common parameters and for both parties and forwards them to the Patient (A) and doctor/nurse (B) for session key computation.
- (i)
Decrypt to get []
- (ii)
Computes
- (iii)
Decrypt to get
- (iv)
Calculate
- (v)
If NOT equals then drop message
- (vi)
- (vii)
D. Step-IV: Participant Validation and Common Session Key Generation
Patient (A) decrypts
, verified by its own nonce and MAC which provide integrity and validity of the TS and the message. The common parameters generated by the trusted server are transmitted securely on each end. Upon receiving the secret credentials, the participating parties first verify message integrity and authority by verifying
and
, respectively. After that, MAC, nonce, TS-ID, and the time stamp are also used for double-checking the source’s integrity before processing secret credentials. After successful validation of both parties’ identities and that of the TS, participants start to compute the common key. The proposed protocol along with stepwise execution is elaborated in
Figure 3.
- a.
Party (A) gets:
- b.
Patient (A):
- a.
Party (B) gets:
- b.
Doctor/Nurse (B):
The novelty of our study is relying upon the creation of secret credentials of the session key for multiparty computing using ECC and symmetric parameters which have less computation cost and are hard to compromise. Upon successful authentication of end parties and common session key generation, both ends share private data securely and efficiently. SAPS attains shared verification, better forward privacy, un-traceability, and participant anonymity. It can launch a secure data sharing connection between the end user and a trusted authority. It also ensures that various attacks, such as offline password guessing, untraceable online secret parameters guessing, confidential insider attacks, card theft attacks, and replay attacks. Intruders cannot enter the system, and the user remains protected at all times.
5. Formal Modeling and Analysis of SAPS
We have performed formal modeling using a method known as Nonmonotonic Cryptographic Protocol (NCP), also called Rubin Logic [
39]. The analysis verification of the SAPS protocol is as per its previous terms and specification of NCP. NCP authenticates the proposed scheme as per the regular necessities of cryptographic procedures, considering parameters such as authenticity, data integrity, the freshness of received data, message encryption, and decryption, etc. This will also help identify the lack of certain properties in the presented scheme and for potential data compromising scenarios. This analysis is similar to the actual operation functionalities in a programming scenario. When we talk about Rubin Logic, the units are assigned specific roles, and a universal set of information is maintained. It also maintains current state of the parameters of users after each update operation. Global sets are accessible to all the member nodes and can be categorized into four types which are secret, observer, rule, and first sets. A detailed discussion of the formal specification for WSAN protocols is provided in [
26,
29], along with appropriate case studies. Entity or node contains a local set that can be categorized into ownership, represented as POSS (), a set of beliefs known as belief BEL (), and to represent the behavior, set BL (). Detailed specification of these sets can be explored in [
14,
30].
Table 2 represents the local set for the application scenario of Rubin logic on SAPS-AN. The details of SAPS, its verification, and analysis provide a detailed overview of all sets maintained under the category of the local set. All the participating entities, including sender, receiver, and Trusted Server are separately maintained locally. An ownership set, POSS (entity), contains all the parameters involved in encryption, decryption, and other processes accomplished in a local memory of each entity, as described in the section below. For the operations and input arguments that are performed in implementation steps, a Behavior List BL () is maintained. Local sets for the entities of the Trusted Server (TS), patient (A) as first party, and Doctor (B) as the second party are presented in
Table 2,
Table 3 and
Table 4, respectively.
5.1. SAPS Analysis and Verification
In this section, SAPS is analyzed for secure session key establishment for the patient to access their physicians anonymously for medical prescription, as discussed in section IV. In this scenario, the establishment request is initiated by the patient (A) by transmitting secret credentials generated using secure methodology established through the TS. After the sending operation, an update operation performed by the sender to refresh the security credentials for future sessions is as shown below.
Concat(IDA, MA, N1, MAC(MA), IDB) → QA
Encrypt({QA,HYA}) → PA
Encrypt({Concat(XA, PA, T1), K(A-TS)}) → CA
Send({IDA~T, CA}) to TS and Update(IDA~T)
Update()
To observe, a list of associated factors, messages, nonce numbers, actual key, ciphers, pseudo-dynamic, finite field, and one-way hash values, are kept in a possession set at the sender node, i.e., with the patient (A). In this case, during the authentication for key establishment phase, the following steps are performed.
POSS(A) = {IDA, P, Rp, KA-TS, F, PWp}
BEL(A) = {#(IDA), #(P), #(Rp), #(K(A-TS)), #(F), #(PWp)}
BL(A) = Mul(Rp, P) → XA, Mul(Rp, F) → YA
After sending messages to the other party and the authentication request is sent to the trusted authority, the TS decrypts the received message to get the secret credentials necessary for verification and to explore the request message. The freshness of the message is checked by comparing the timestamp threshold value, nonce number, and masked IDs value with set values. If we fulfill the threshold parameter and verify the answer, then further process calculations are processed. Otherwise, the message is discarded. MAC is calculated for message integrity and compared to hash values to ensure integrity. The participant verification and message integrity steps performed at the TS are as follows.
Receive(A, {CA})
Decrypt({IDA~T, CA}KTS-A) and Split to get [XA, PA, T1]
check(T’1–T1) ≥ ∆T then abort
Hash(h(.); Mul(d, XA)) → HY’A
Decrypt({PA}HY’A) and Split to get [IDA, MA, N1, MAC(MA), IDB]
Hash(h(.); Concat(PWp, IDA, IDB)) → M’A
if MAC(M’A) equals MAC(MA) else discard
if M’A NOT equals MA then discard
After Patient (A) verification, the TS calculates some parameters and generates a message for the other party that can provide medical services to the patient (A) as follows.
Hash(h(.); Concat(IDTS, IDB, RTS)) → ZTS
Hash(h(.); Concat(IDA, IDB, N2)) → QTS
XOR(ZTS, QTS) → IDB~T
Encrypt({Concat (IDA, ZTS, T2, N2, IDB~T), K(TS-B)}) → CTS
Send({IDTS, CTS}) to B and Update (IDB~T)
Upon receiving the secret credentials sent by the TS, Doctor (B) verifies the message integrity and the TS as follows:
Decrypt({IDB~T, CTS}KB-TS) and Split to get [IDA, ZTS, T2, N2]
Hash(h(.); Concat (IDA, IDB, N2)) → Q′TS
check(XOR(ZTS,Q′TS) ! equals IDB~T) then abort
Following the authentication and verification of Party (B) by the TS, party (B) also computes some secret credentials and provides a reply message for the TS. The secret credentials are used by both parties to generate a secret key, and the transmission is secured using the shared key, as well as by calculating the hash, adding a nonce, and MAC. The steps performed at the physician’s side for session key establishing are as follows:
Mul(RB, P) → XB, Mul(RB, F) → YB
Hash(h(.); Concat (PWB, IDTS, IDB)) → MB
Concat(IDB,MB, N3, MAC(MB), IDTS) → QB
Hash(h(.);YB) → HYB
Encrypt({QB, HYB}) → PB
Encrypt({Concat(XB, PB,T3), K(B-TS)}) → CB
Send({IDB~T, CB}) to TS and Update (IDB~T)
For verification and checking of message integrity of party (B), the TS performs the same steps as Party (A). The TS securely generates secret credentials based on the information gathered from both ends, and distributes a common key which is partially completed. Secure parameter distribution steps are shown as below, which are transmitted securely to the participants.
Encrypt({Concat (XB, IDA,IDB,Y’A, N1), HY’A}) → CPA
Send({IDA~T, CPA}) to A
Encrypt({Concat (XA, IDA,IDB, Y’B, N2), HY’B}) → CPB
Send({IDB~T, CPB}) to B
Although data/credentials transmission is performed using strong encryption techniques by the TS to increase security and un-traceability of participants, the proposed scheme has a novel approach in its partial session key mechanism. After successful authentication and session key establishment, a “Forget Operation” performed at each participating entity will result in removing temporary values like nonce value, time stamp, temporary encryption key H*, and MAC calculating parameters. These operations ensure security against forwarding secrecy and user traceability issues.
5.2. User Anonymity
The user’s identity, ID, cannot be stored in plaintext at the user level, nor at the TS, and it can be transmitted via the login request. In our scheme, user identity is masked in both and , after the original identity registration, session request, and end-user joining request is sent to the TS in the encrypted form. The secret parameters are generated by party and party by choosing secret number , respectively, from with large order as shown in steps I–III. It is not feasible for any third party to get these secret parameters and it is almost impossible to recover messages to get identities without knowing the one-way hash function. It is not viable for an adversary to compute the original identities of the participant. The TS has private and public key pairs and the participants use their MAC for message integrity, masked-IDs, nonce number, and time stamp for message freshness. At the trusted sever, a randomized symmetric encryption technique is used to conceal the random number generated by the instead of using the XOR. Before communicating the session request of party(A) to party(B), the TS first verifies the original identity of the requested party and the message freshness by computing the inverse functions as shown in Protocols II and III. It generates a temporary public ID of each participant instead of using their original identities. The public identity, say IDV, can run the protocol. Therefore, on the basis of the above analysis, it is impossible for the adversary to get the user’s identity from the proposed protocol during authentication, forwarding, the joining request, or the session key computing procedure. Therefore, we know that the proposed protocol is able to provide user anonymity.
5.3. User Un-Traceability
In our scheme, each session-based communication contains parameters based on and that are dynamic for each authentication/verification session of all participants and are different for each transmission. Moreover, a timestamp is appended to every session. The value of ( and , as shown in the proposed protocols to fulfill the requirements for common session key establishment, are executed in a distributed manner. Consequently, the adversary is unable to figure out that two procedures have the same users involved. It ensures that our proposal accomplishes user un-traceability. According to the pattern of the projected protocol, the participant generates a new random number to compute and in each session. Due to the randomness of the secret parameters, the adversary cannot find and link among messages sent by the end parties or the trusted server, and therefore is unable to follow their actions. Therefore, the proposed protocol is able to provide un-traceability during authentication, session key management, and the following data transmission procedures.
5.4. Offline Password Guessing Attacks
In offline password guessing, the adversary tries to capture the entire communication between party (A) and the TS or between the TS and party (B), but is unable to get the password. The next adversary attack may be possible.
{} → {TS} from party(A) to TS, {,} are TS parameters, Party(B) to TS and are the communications between A, B, and the TS known by the adversary. To commence the offline secret password estimating attack, the adversary tries to regenerate , an inverse password of party (A) and computes . Still, if the adversary gets the IDs of both participants, it is not possible for the adversary to compute and they are unable to verify the as used in the protocols which contains the message and the identities of the participants.
Appropriate to the un-traceability of the Computational Diffie-Hellman assumption (CDH) a difficult adversary does not get { → } and it is impossible for the adversary to get the password.
If an adversary gets party B’s password to compute the random number generated by the TS, as shown in protocol-III, to compute the parameters after the received connection establishing request from party (A), it is not possible for the adversary to compute B’s password without knowing because and has ECDLP, as shown in step-3 of protocol-III.
As a result, the proposed protocol can oppose offline password guessing attacks. To deal with online password guessing attack, the TS detects the encounter during the message validation process and the freshness procedure at the beginning of the communication.
5.5. Perfect Forward Secrecy
In our scheme, the un-traceability of CDH plays a vital role in resisting guessing previous session keys by the adversary. The session key is generated using , where are nonce numbers chosen by both participants specially for the specific session and are different from the nonce numbers used during the authentication process, such as , , . In the proposed protocol, the end parties compute the session key, SK, as and , where and are computed by randomly chosen numbers by both parties at their end with the help of the trusted server. Knowing the secret key of the server and the password does not help the adversary to compute a previously established session key, because the secret credentials used to compute the secure key are not based on the password and server’s public key. If the adversary wants to know an old session key he /she must compute , . However, since the adversary does not know the due to the hardness of ECDLP, the adversary cannot compute the secret credentials. Therefore, the proposed scheme provides perfect forward secrecy.
5.6. Replay Attack
Replay attacks can be launched while an attacker replays the original message parameters at some other time to impersonate any legal participant. In the proposed scheme, messages between the IDA, TS, and IDB are transmitted on the public channel. An attacker might try to use these conversations to launch a replay attack. However, in our protocol, replay attacks can be easily thwarted because an adversary cannot produce an updated timestamp. Both end parties and the TS verify message freshness with a threshold for timestamp and nonce number. If the difference exceeds this threshold, it will abort the session. It is not easy for an adversary to impersonate participants’ reply messages because the nonce numbers , , during the authentication process, for key session key generation and used by the TS are newly chosen for every session. For this scenario, an adversary cannot compute the {}, = , and communication patterns of the entire network.
5.7. Forgery Attacks and Impersonation
In our scheme, TS has a pair of public-private secret keys (d, F = dP), and if an adversary attempts to impersonate the participants or the TS and sends a message to the TS acting as the participants or tries to establish a connection with any party, they will remain unable to verify themself. For the verification process, it is necessary for an adversary to know the password or private key of the TS, d.
5.8. Man in the Middle Attack
An adversary may intercept the messages sent between the parties and the TS and replace them with their own messages. These forged messages need to be verified by the TS before getting the session key. However, it is not feasible as the adversary does not know the TS secret key and secret passwords of the parties. So, our scheme resists a man in middle attack.
6. Results and Analysis
We have simulated the SAPS protocol by deploying nodes for the patient, doctor/nurse, and the trusted server using TCL script in NS 2.35.The simulation parameter and system setting defined in
Table 5. We have separately configured the patient and doctor/nurse for low power devices. The server is configured for high residual and transmission power. In the TCL file, communication messages are initiated and traffic sources are also configured along with packet sizes. Moreover, C/C++ files are developed for providing device-level functionalities, including send, receive, hash, encrypt, and decrypt functions. Results are extracted from the trace file by executing the AWK scripts. We have used a 160-bit key along with
where the tuple
. The performance of SAPS is evaluated regarding storage, computation, and communication costs for the base scheme TPKE [
15], A-TMIS [
16], EAKA [
40], and AAS [
41]. A list of simulation parameters is shown in
Table 4.
6.1. Storage Overhead
In the proposed protocol, we outlined the storage overhead and memory requirement, including the public/private key of the TS and the communication parties, IDs, random number, timestamp, and resultant length of the session key, as shown in
Figure 4. In the view of the used parameters between the patient (A), TS, and Doctor (B), we have analyzed and compared the storage cost of TPKE [
15], the smart card keeps
and thus the storage overhead is
. A-TMIS [
16] stores
and an efficient authentication and key agreement EAKA protocol [
40] requires
in the smart card for basics parameters. The AAS [
41] scheme improves the protocol for TMIS and consumes 960-bits storage to process authentication and authorization which contains
.
In our SAPS protocol, the end parties need to keep {PW, ID, XA, Ni, Ti, } for identification, authentication, and session key establishment. From an evaluation point of view, it has been supposed that secret identity, one-way hash operation, and timestamps are 160-bits in size, whereas the ECC recommended size by NIST for a key is 160-bits and 64-bit for the secret key for encrypting passwords generated using the TS’s shared credentials. So, the total storage overheads of proposed scheme are , which is stored at both ends and the TS has more computation and storage capabilities. In our scenario, more parameters such as ID masking, public/private key and pseudorandom generation processes are accomplished at the TS.
6.2. Communication Overhead
To appraise the message exchanging overhead of the presented protocol, the data that is transmitted between the participating parties and the TS during the identification and session key generation phase need to be considered. It is identified that the secret key of size 160-bit using ECC can yield equal security to a 1024-bit RSA secret key. For the evaluation phase, we believe that the resultant one-way hash function, participant’s identities, timestamp, and nonce number are 160 bits in length. The end party sends three parameters which are
to the TS for authentication, and their lengths are
. On the other side, in the party verification phase, the TS sends an encrypted packet
using a 160-bit ECC key to the end party for session key establishment and its length is
. On the basis of these computations in the proposed SAPS protocol, Patient (A) and Doctor (B) have the same communication cost during their end user confirmation and secure key generation processes. On the other hand, existing ECC- and RSA-based schemes have greater communication overheads, as depicted in
Figure 5.
TPKE [
15] is based on RSA which requires 1344 bits for the authentication method and 1344 bits for server to end party communication. Similarly, A-TMIS [
16] consumes the same communication cost as TPKE for the whole procedure. In the login phase of Xu et al.’s protocol for EAKA [
40], the server requires 640 bits of communication cost, and the server to the user requires 480-bits. AAS [
41] requires 640 bits and 480 bits communication from the user to server and the server to user, respectively. By the above analysis, the proposed scheme has less communication cost by ensuring user anonymity.
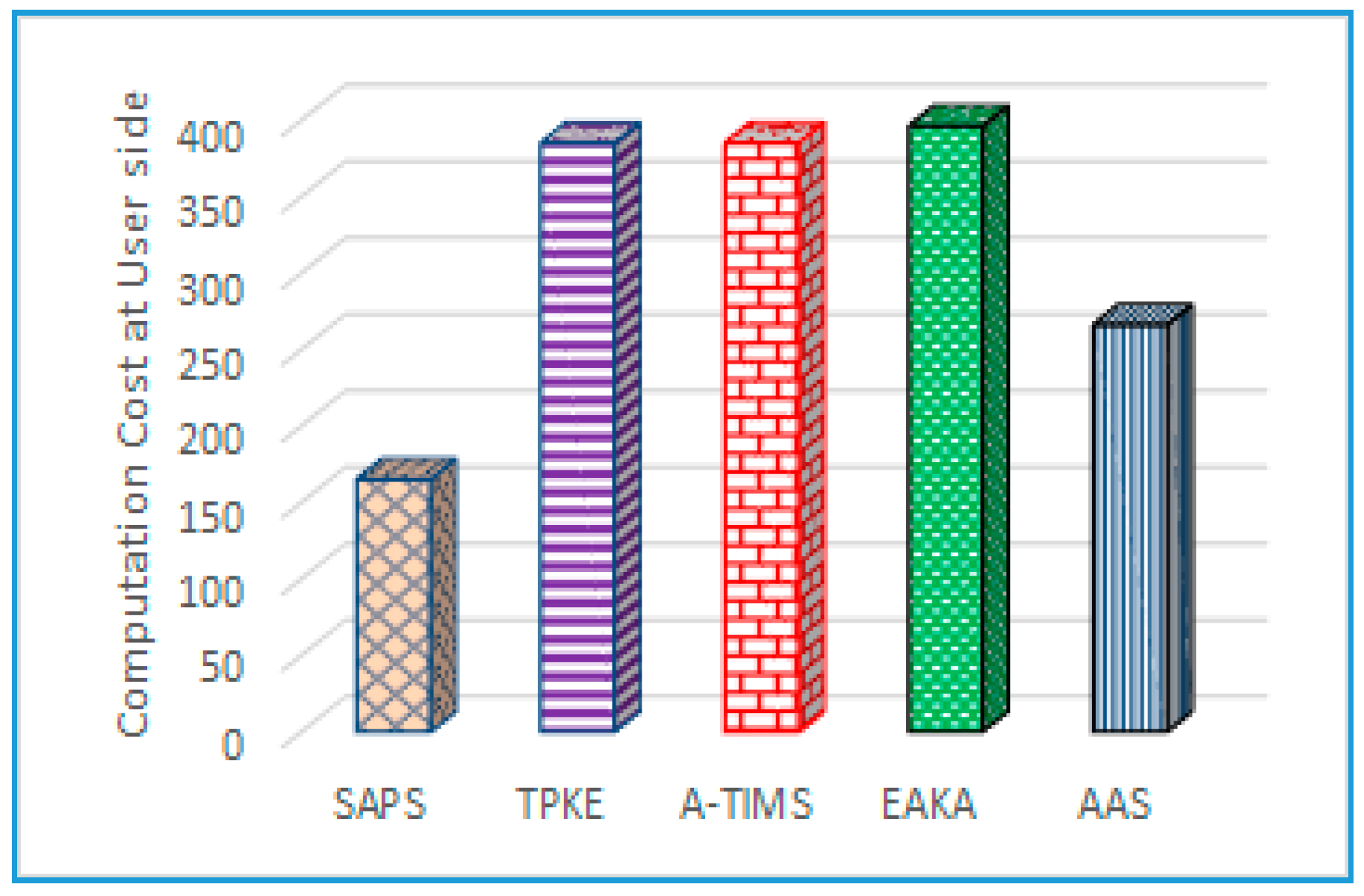
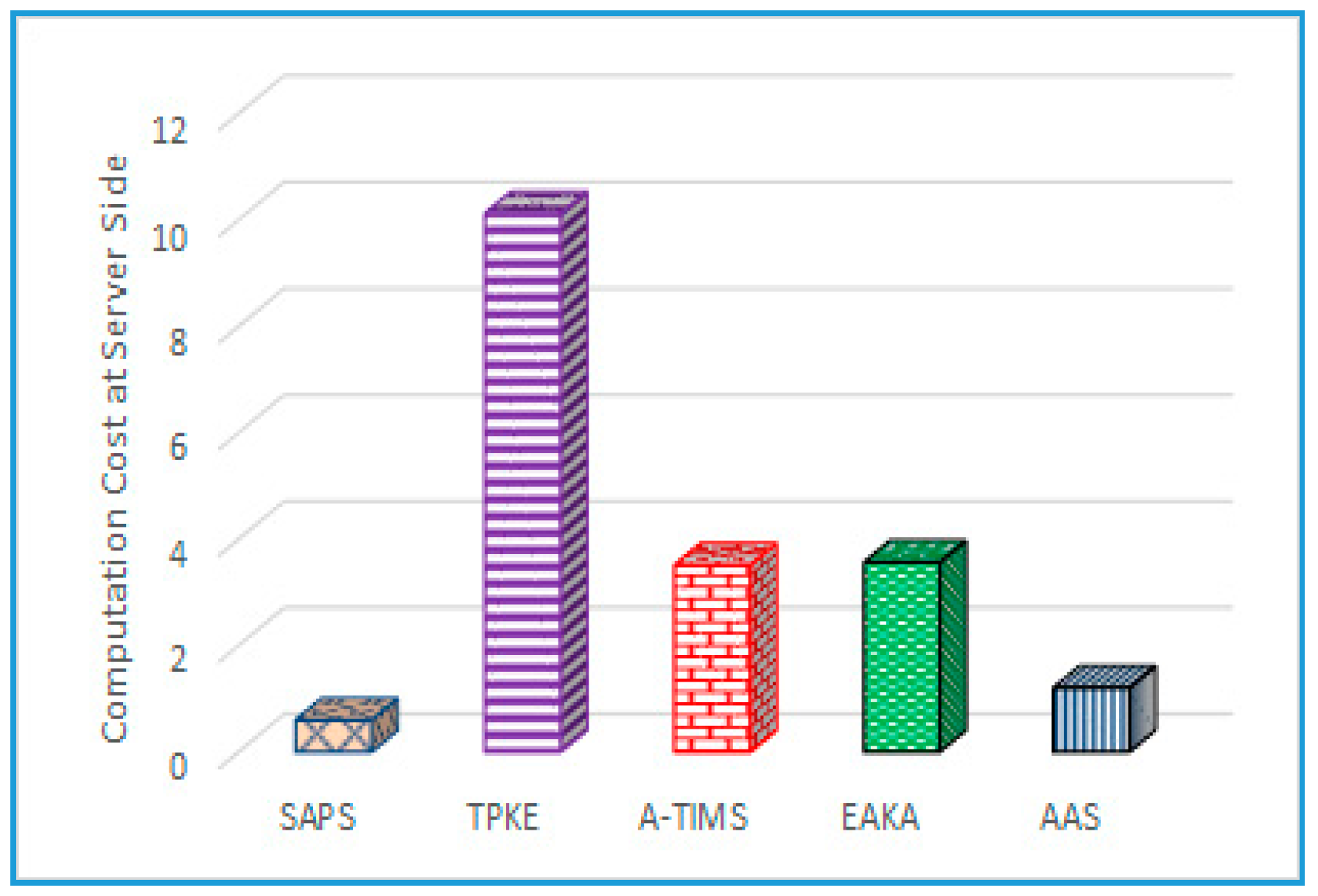
6.3. Computation Complexity
Based on the simulation results and defined parameters, a 5 MHz frequency is required to compute the 160-bit elliptic curve, where 5 MHz is for one small data module in which multiple modules are included in the calculation of the elliptic curve and related mathematical operations. To elaborate in detail, we have defined some notations to describe the function of protocol like, which are the time for performing an exponential operation, time for performing an elliptic curve point multiplication operation, time for computing EC point multiplication function, symmetric encryption/decryption operation time, the one way hash function computation time, and XOR operation, respectively.
According to [
42,
43], the computation time for an exponential operation is 0.522 ms, EC point multiplication process consumes 0.063075 ms, one-way hash operation implementation time is 0.0005 ms, and the encryption/decryption operation time is 0.0087 ms. On the user’s side, the proposed scheme has lower computational overheads, as shown in
Figure 6 and
Figure 7. Our SAPS protocol is more suitable for a mobile scenario when compared to existing schemes, because it has fewer rounds needed for authentication. Computing complexity for the adversary is high, whereas fewer communication rounds make it more efficient and secure.
6.4. Resilience
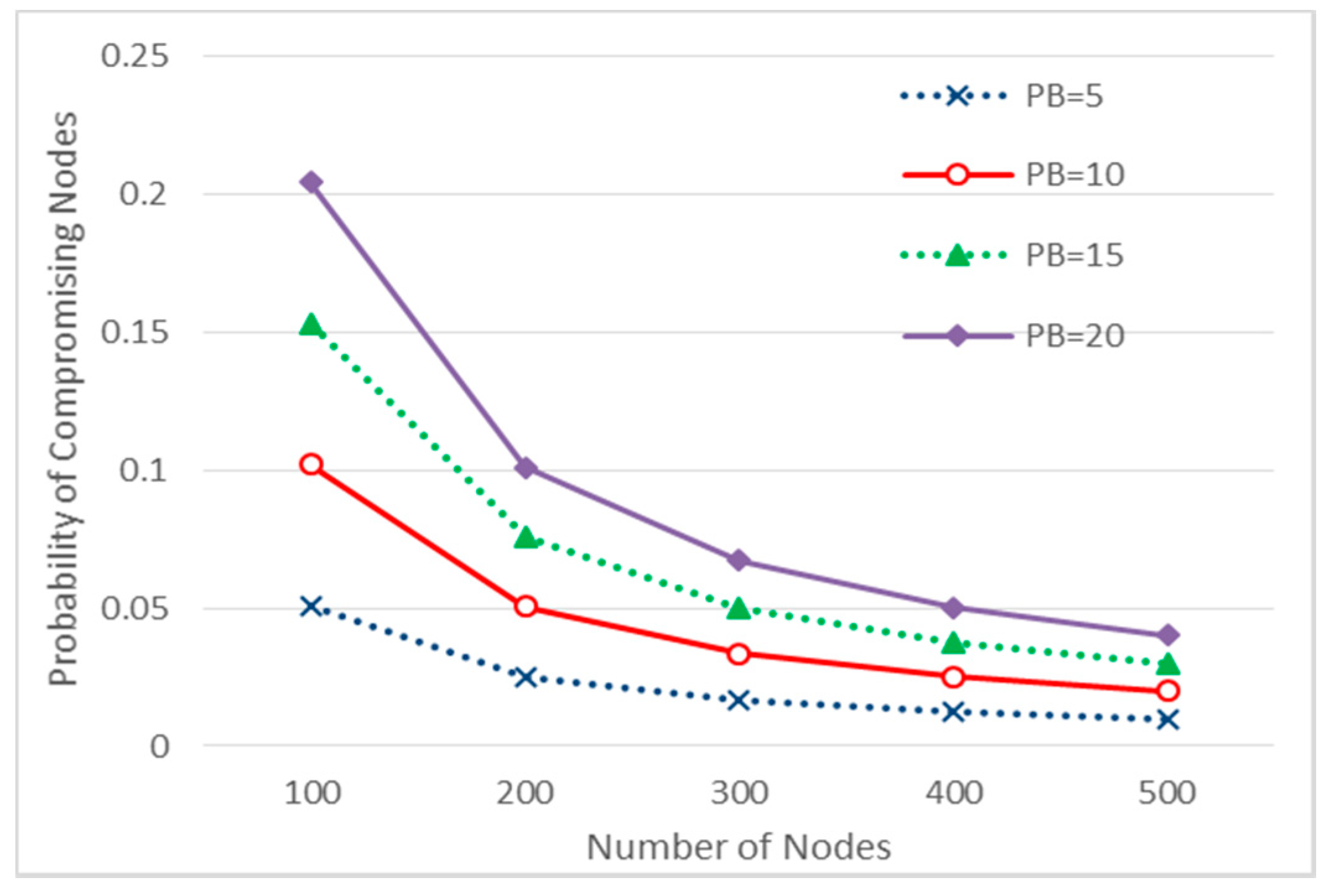
During secure communication between the patient and doctor, devices from different regions communicate using intermediate devices. The chance of compromised devices in the path exists. The probability that an intermediate node is compromised is given in Equation (1), where N is the number of devices in the network and β is number of devices compromised by adversary. The term N−2 represents that sender and receiver are considered uncompromised, whereas N−3 means to exclude one more intermediate device which is a direct neighbor of the sender.
Figure 8 elucidates the scenario for measuring the impact of compromising intermediate devices by calculating the probability
when the number of devices in the network varies from 100 to 500. In the case of 300 devices, the probability is 0.0167, 0.033, 0.050, and 0.067 for
and
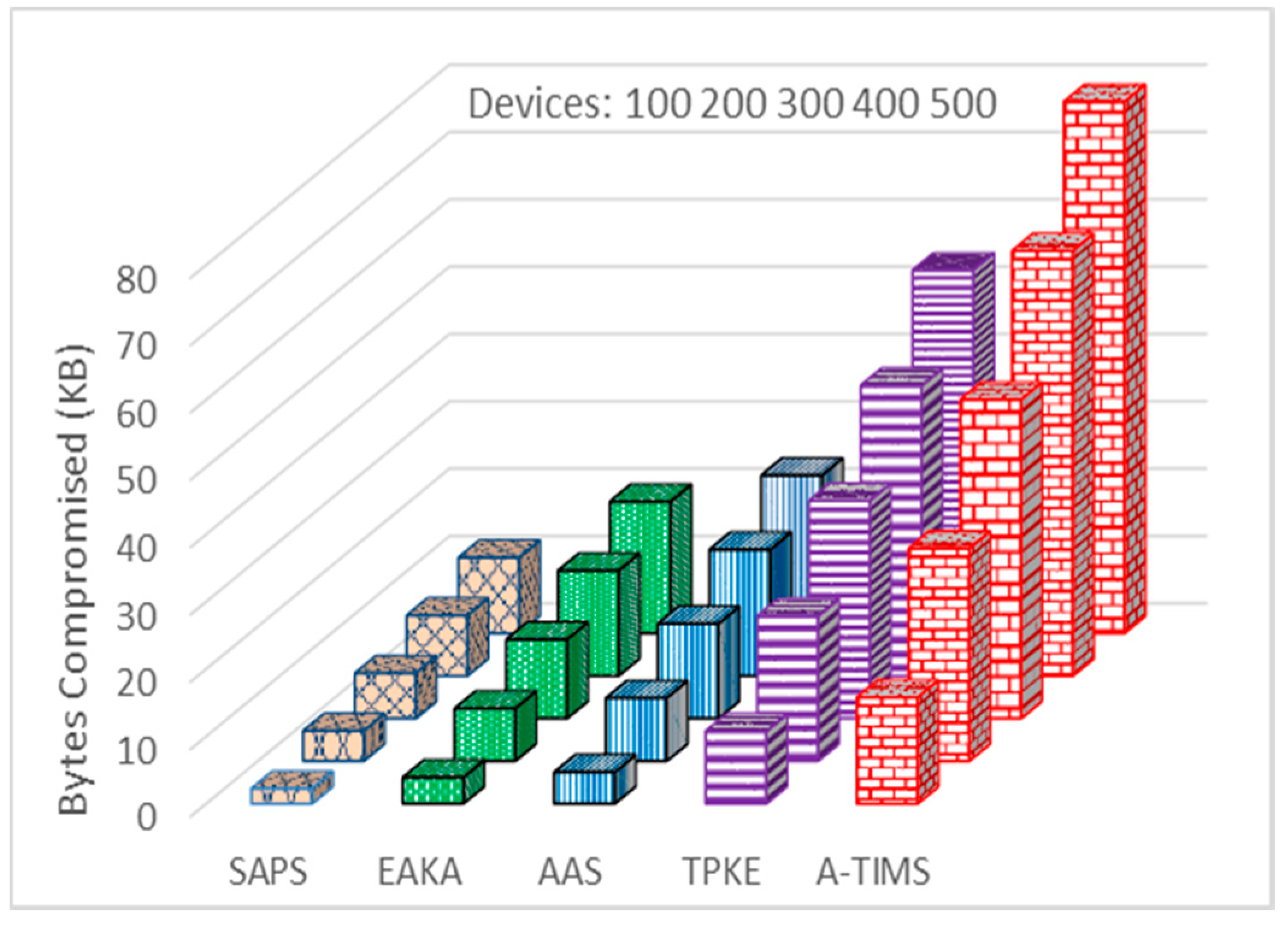
compromised devices, respectively. If an intermediate device is compromised, then data and security credentials stored in that device are exposed. Moreover, the probability
that a particular session key and its related credentials are compromised is given in Equation (2), where ω credentials are compromised out of a total of M devices in the network.
Figure 9 shows that different security credentials stored in devices can be revealed to intruders when the devices are compromised. We have considered the scenario where the number of devices is varied from 100 to 500, and the number of compromised nodes is varied from 5 to 25, respectively. In the case of 400 devices in the network where 20 of them are compromised, the number of compromised bytes are 15.62 KB, 18.75 KB, 43.12 KB, and 63.12 KB for EAKA, AAS, TPKE, and A-TIMS respectively. Our proposed SAPS method dominates and achieves better resilience against node capture attack by revealing only 8.98 KB.