Privacy-Preserving Aggregation and Authentication of Multi-Source Smart Meters in a Smart Grid System
Abstract
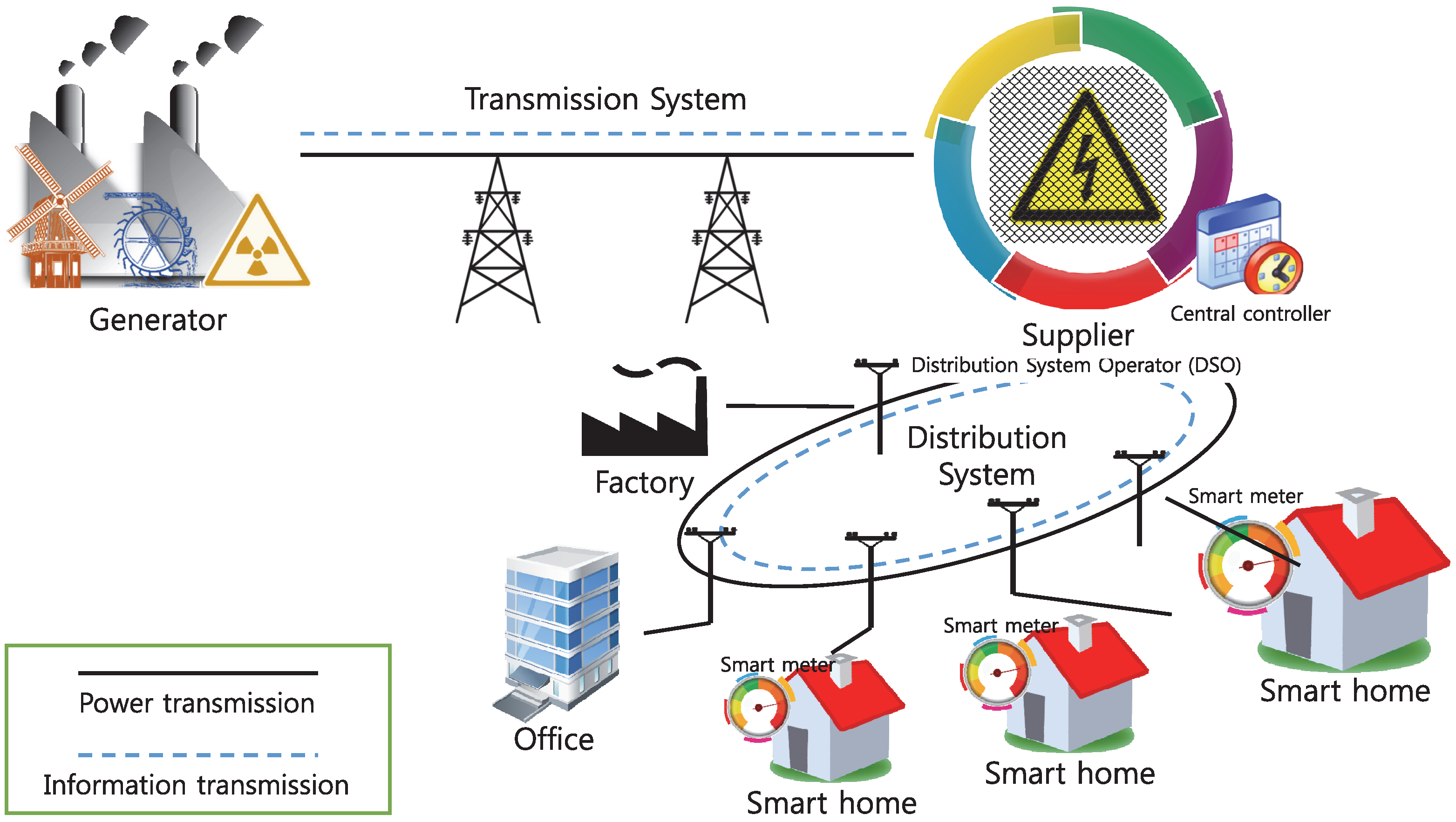
:1. Introduction
- Energy awareness: By providing users with periodic energy usage patterns, pre-planned power consumption can be enabled. This can lead to consumer power-saving behavior through the implementation of energy-aware systems. In addition, emissions can be reduced, and the need for surplus power generation in backup plants can be avoided, which is beneficial to the environment and economics, through continuous electrical load balancing.
- Increased power consumer selectivity: By allowing choices among various electricity generators, suppliers, and communication services, more options can be given to energy consumers. It imposes a more active role on consumers of new products, services and markets.
- Improved reliability of power generation and consumption: Based on historical records of power usage, automatic power generation and consumption can be adjusted according to expected electricity demand. It also improves the resilience of the grid to natural disasters.
2. Status of Smart Grids
2.1. Popularization of the Smart Grid
2.1.1. Europe
2.1.2. North America
2.1.3. Oceania and Asia
2.2. Standardization and Regulations
2.2.1. North America
2.2.2. Europe
2.2.3. Oceania and Asia
2.2.4. South America
3. Privacy-Preserving Aggregation with Authentication
3.1. Efficiency and Scalability
4. Conclusions and Discussion on Future Directions of Smart Grids
- Privacy preservation: To achieve privacy protection during data transmission, semantically secure encryption algorithms are employed. Additionally, (additive) homomorphic encryption supporting evaluations on encrypted data such as ElGamal, Paillier, and lattice-based cryptosystems are being adopted in order to protect user privacy. Depending on the subject to be protected, all kinds of participating entities such as smart appliances, smart meters, (intermediate) gateways, and central controllers are taken into account.
- Authentication: To produce accurate aggregate results, various kinds of authentication algorithms are being adopted. According to the situation, sender authentication that validates data origin is considered. Some algorithms are used in upstream directions to check forwarding entities during the process of transferring metering data to the central controller, while others are used to identify the central controller in downstream directions during delivery of decisions made from aggregate data. On the other hand, data authentication is combined with the above approaches to avoid false data injection attacks from malicious adversaries or unintended malfunctions.
- Efficiency: In terms of computational efficiency, lightweight encryption algorithms are designed through modification of the existing homomorphic encryption schemes. Batch verification algorithms are also considered in the validation of received data authenticity. In terms of communication efficiency, data aggregation itself is devised to minimize the size of transmitted data with the modification of internal data structures. Furthermore, short signature schemes are also adopted in authentication mechanisms.
Acknowledgments
Conflicts of Interest
References
- International Data Corporation (IDC). Worldwide Spending on the Internet of Things Forecast to Reach Nearly $1.4 Trillion in 2021, According to New IDC Spending Guide. Available online: https://www.idc.com/getdoc.jsp?containerId=prUS42799917 (accessed on 27 September 2017).
- Pillitteri, V.Y.; Brewer, T.L. Guidelines for Smart Grid Cybersecurity. In NIST Interagency/Internal Report (NISTIR)-7628 Rev 1; 25 September 2014; pp. 1–668. Available online: http://nvlpubs.nist.gov/nistpubs/ir/2014/NIST.IR.7628r1.pdf (accessed on 29 September 2017).
- Baker, F.; Meyer, D. Internet Protocols for the Smart Grid. No. RFC 6272. June 2011, pp. 1–66. Available online: https://tools.ietf.org/html/rfc6272.txt.pdf (accessed on 27 September 2017).
- European Telecommunications Standards Institute (ETSI). Machine-to-Machine Communications (M2M); Threat Analysis and Counter-Measures to M2M Service Layer. ETSI TR 103 167 V1.1.1 (2011-08); Sophia Antipolis, France, 4 August 2011; pp. 1–62. Available online: http://www.etsi.org/deliver/etsi_tr/103100_103199/103167/01.01.01_60/tr_103167v010101p.pdf (accessed on 27 September 2017).
- McDaniel, P.; McLaughlin, S. Security and Privacy Challenges in the Smart Grid. IEEE Secur. Priv. 2009, 7, 75–77. [Google Scholar] [CrossRef]
- Khurana, H.; Hadley, M.; Lu, N.; Frincke, D.A. Smart-grid security issues. IEEE Secur. Priv. 2010, 8, 81–85. [Google Scholar] [CrossRef]
- Liu, J.; Xiao, Y.; Li, S.; Liang, W.; Chen, C.L.P. Cyber Security and Privacy Issues in Smart Grids. IEEE Commun. Surv. Tutor. 2012, 14, 981–997. [Google Scholar] [CrossRef]
- Erol-Kantarci, M.; Mouftah, H.T. Smart grid forensic science: Applications, challenges, and open issues. IEEE Commun. Mag. 2013, 51, 68–74. [Google Scholar] [CrossRef]
- Fan, Z.; Kulkarni, P.; Gormus, S.; Efthymiou, C.; Kalogridis, G.; Sooriyabandara, M.; Zhu, Z.; Lambotharan, S.; Chin, W.H. Smart Grid Communications: Overview of Research Challenges, Solutions, and Standardization Activities. IEEE Commun. Surv. Tutor. 2013, 15, 21–38. [Google Scholar] [CrossRef]
- Delgado-Gomes, V.; Martins, J.F.; Lima, C.; Borza, P.N. Smart grid security issues. In Proceedings of the International Conference on Compatibility and Power Electronics (CPE), Lisbon, Portugal, 24–26 June 2015; pp. 534–538. [Google Scholar]
- The Global Smart Grid Federation (GSGF). Smart Meter Security Survey. Available online: http://www.globalsmartgridfederation.org/wp-content/uploads/2016/08/smart_meter_security_survey.pdf (accessed on 27 September 2017).
- Hahn, A.; Govindarasu, M. Cyber Attack Exposure Evaluation Framework for the Smart Grid. IEEE Trans. Smart Grid 2011, 2, 835–843. [Google Scholar] [CrossRef]
- Greveler, U.; Glösekötterz, P.; Justusy, B.; Loehr, D. Multimedia content identification through smart meter power usage profiles. In Proceedings of the International Conference on Information and Knowledge Engineering (IKE), Las Vegas, NV, USA, 16–19 July 2012. [Google Scholar]
- Erkin, Z.; Troncoso-pastoriza, J.R.; Lagendijk, R.L.; Perez-Gonzalez, F. Privacy-preserving data aggregation in smart metering systems: An overview. IEEE Signal Process. Mag. 2013, 30, 75–86. [Google Scholar] [CrossRef]
- Fang, X.; Misra, S.; Xue, G.; Dajun, Y. Smart Grid—The New and Improved Power Grid: A Survey. IEEE Commun. Surv. Tutor. 2012, 14, 944–980. [Google Scholar] [CrossRef]
- Pooranian, Z.; Nikmehr, N.; Najafi-Ravadanegh, S.; Mahdin, H.; Abawajy, J. Economical and environmental operation of smart networked microgrids under uncertainties using NSGA-II. In Proceedings of the International Conference on Software, Telecommunications and Computer Networks (SoftCOM), Split, Croatia, 22–24 September 2016; pp. 1–6. [Google Scholar]
- Shojafar, M.; Cordeschi, N.; Baccarelli, E. Energy-efficient Adaptive Resource Management for Real-time Vehicular Cloud Services. IEEE Trans. Cloud Comput. 2016, PP, 1–14. [Google Scholar] [CrossRef]
- SmartGrid Canada. Available online: http://www.sgcanada.org/ (accessed on 27 September 2017).
- Department of Planning, Transport and Infrastructure, Government of South Australia. Adelaide’s New Suburb—TONSLEY. Available online: https://dpti.sa.gov.au/tonsley (accessed on 27 January 2017).
- Standards Council of Canada. The Canadian Smart Grid Standards Roadmap: A Strategic Planning Document. Available online: https://www.scc.ca/sites/default/files/publications/Smart_Grid_Report_FINAL_EN_3.pdf (accessed on 27 September 2017).
- European Commission. Minutes—High level Roundtable on Main Challenges for Cyber Security in the Energy System. Available online: https://ec.europa.eu/energy/sites/ener/files/documents/detailed_minutes_rome_24.3_final.pdf (accessed on 27 September 2017).
- NobelGrid. Available online: http://nobelgrid.eu/ (accessed on 27 September 2017).
- SEGRID. Available online: https://segrid.eu/ (accessed on 27 September 2017).
- The SPARKS Project. Smart Grid Protection Against Cyber Attacks. Available online: https://project-sparks.eu/ (accessed on 27 September 2017).
- HyRiM. Hybrid Risk Management for Utility Providers. Available online: https://hyrim.net/ (accessed on 26 April 2017).
- Metering & Smart Energy International. Smart Grid Investments in Australia and New Zealand to Read $6.1bn. Available online: https://www.metering.com/news/smart-grid-investments-australia/ (accessed on 27 September 2017).
- Northeast Group, LLC. Smart Grid Infrastructure Investment in South America: $38.1bn by 2025. Available online: http://www.prnewswire.com/news-releases/smart-grid-infrastructure-investment-in-south-america-381bn-by-2025-300125709.html/ (accessed on 27 September 2017).
- Zhang, K.; Ni, J.; Yang, K.; Liang, X.; Ren, J.; Shen, X.S. Security and Privacy in Smart City Applications: Challenges and Solutions. IEEE Commun. Mag. 2017, 55, 122–129. [Google Scholar] [CrossRef]
- Khatoun, R.; Zeadally, S. Cybersecurity and Privacy Solutions in Smart Cities. IEEE Commun. Mag. 2017, 55, 51–59. [Google Scholar] [CrossRef]
- Salinas, S.; Li, M.; Li, P. Privacy-Preserving Energy Theft Detection in Smart Grids: A P2P Computing Approach. IEEE J. Sel. Areas Commun. 2013, 31, 257–267. [Google Scholar] [CrossRef]
- Bartoli, A.; Hernandez-Serrano, J.; Soriano, M.; Dohler, M.; Kountouris, A.; Barthel, D. Secure Lossless Aggregation Over Fading and Shadowing Channels for Smart Grid M2M Networks. IEEE Trans. Smart Grid 2011, 2, 844–864. [Google Scholar] [CrossRef]
- Liang, X.; Li, X.; Lu, R.; Lin, X.; Shen, X. UDP: Usage-Based Dynamic Pricing with Privacy Preservation for Smart Grid. IEEE Trans. Smart Grid 2013, 4, 141–150. [Google Scholar] [CrossRef]
- Cho, S.; Li, H.; Choi, B.J. PALDA: Efficient privacy-preserving authentication for lossless data aggregation in Smart Grids. In Proceedings of the IEEE International Conference on Smart Grid Communications (SmartGridComm), Venice, Italy, 3–6 November 2014; pp. 914–919. [Google Scholar]
- Paillier, P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes. In Advances in Cryptology—EUROCRYPT; Springer: Berlin/Heidelberg, Germany, 1999; pp. 223–238. Available online: https://www.researchgate.net/publication/221348062_Public-Key_Cryptosystems_Based_on_Composite_Degree_Residuosity_Classes (accessed on 4 February 2016).
- Erkin, Z.; Tsudik, G. Private Computation of Spatial and Temporal Power Consumption with Smart Meters. In Proceedings of the International Conference on Applied Cryptography and Network Security (ACNS), Singapore, 26–29 June 2012; pp. 561–577. [Google Scholar]
- Borges, F.; Muhlhauser, M. EPPP4SMS: Efficient Privacy-Preserving Protocol for Smart Metering Systems and Its Simulation Using Real-World Data. IEEE Trans. Smart Grid 2014, 5, 2701–2708. [Google Scholar] [CrossRef]
- Mustafa, M.A.; Zhang, N.; Kalogridis, G.; Fan, Z. DEP2SA: A Decentralized Efficient Privacy-Preserving and Selective Aggregation Scheme in Advanced Metering Infrastructure. IEEE Access 2015, 3, 2828–2846. [Google Scholar] [CrossRef]
- Garcia, F.D.; Jacobs, B. Privacy-Friendly Energy-Metering via Homomorphic Encryption. In Proceedings of the International Workshop on Security and Trust Management (STM), Copenhagen, Denamrk, 27–28 June 2011; pp. 226–238. [Google Scholar]
- Li, F.; Luo, B.; Liu, P. Secure Information Aggregation for Smart Grids Using Homomorphic Encryption. In Proceedings of the IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 327–332. [Google Scholar]
- Li, H.; Lin, X.; Yang, H.; Liang, X.; Lu, R.; Shen, X. EPPDR: An Efficient Privacy-Preserving Demand Response Scheme with Adaptive Key Evolution in Smart Grid. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 2053–2064. [Google Scholar] [CrossRef]
- Wang, X.F.; Mu, Y.; Chen, R.M. An efficient privacy-preserving aggregation and billing protocol for smart grid. Secur. Commun. Netw. 2016, 9, 4536–4547. [Google Scholar] [CrossRef]
- Li, D.; Aung, Z.; Williams, J.R.; Sanchez, A. Efficient and Fault-Diagnosable Authentication Scheme for Advanced Metering Infrastructure. Data and Network Analytics Research Group, Tech. Rep. January 2013. Available online: https://pdfs.semanticscholar.org/9fe3/d9aafc0e3017d768391c97d481fc4f960fa7.pdf (accessed on 27 September 2017).
- Shen, H.; Zhang, M.; Shen, J. Efficient Privacy-Preserving Cube-Data Aggregation Scheme for Smart Grids. IEEE Trans. Inf. Forensics Secur. 2017, 12, 1369–1381. [Google Scholar] [CrossRef]
- Ruj, S.; Nayak, A. A Decentralized Security Framework for Data Aggregation and Access Control in Smart Grids. IEEE Trans. Smart Grid 2013, 4, 196–205. [Google Scholar] [CrossRef]
- He, X.; Pun, M.O.; Kuo, C.C.J. Secure and efficient cryptosystem for smart grid using homomorphic encryption. In Proceedings of the IEEE PES Innovative Smart Grid Technologies (ISGT), Washington, DC, USA, 16–20 January 2012; pp. 1–8. [Google Scholar]
- Deng, P.; Yang, L. A secure and privacy-preserving communication scheme for Advanced Metering Infrastructure. In Proceedings of the IEEE PES Innovative Smart Grid Technologies (ISGT), Washington, DC, USA, 16–20 January 2012; pp. 1–5. [Google Scholar]
- Hur, J.B.; Koo, D.Y.; Shin, Y.J. Privacy-Preserving Smart Metering with Authentication in a Smart Grid. Appl. Sci. 2015, 5, 1503–1527. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Zeadally, S.; Vinel, A.; Yang, L.T. Efficient and Privacy-Preserving Data Aggregation Scheme for Smart Grid against Internal Adversaries. IEEE Trans. Smart Grid 2017, 8, 2411–2419. [Google Scholar] [CrossRef]
- Abdallah, A.; Shen, X. A Lightweight Lattice-based Homomorphic Privacy-Preserving Data Aggregation Scheme for Smart Grid. IEEE Trans. Smart Grid 2016, PP, 1–10. [Google Scholar] [CrossRef]
- Li, F.; Luo, B. Preserving data integrity for smart grid data aggregation. In Proceedings of the IEEE International Conference on Smart Grid Communications (SmartGridComm), Tainan, Taiwan, 5–8 November 2012; pp. 366–371. [Google Scholar]
- Rial, A.; Danezis, G. Privacy-preserving Smart Metering. In Proceedings of the Annual ACM Workshop on Privacy in the Electronic Society (WPES), Chicago, IL, USA, 17 October 2011; pp. 49–60. [Google Scholar]
- Jawurek, M.; Johns, M.; Kerschbaum, F. Plug-In Privacy for Smart Metering Billing. In Proceedings of the International Symposium on Privacy Enhancing Technologies (PETS), Waterloo, ON, Canada, 27–29 July 2011. [Google Scholar]
- Chim, T.W.; Yiu, S.M.; Hui, L.C.K.; Li, V.O.K.; Mui, T.W.; Tsang, Y.H.; Kwok, C.K.; Yu, K.Y. Selling Power Back to the Grid in a Secure and Privacy-Preserving Manner. In Proceedings of the International Conference on Information and Communications Security (ICICS), Hong Kong, China, 29–31 October 2012; pp. 445–452. [Google Scholar]
- Cheung, J.C.L.; Chim, T.W.; Yiu, S.M.; Li, V.O.K.; Hui, L.C.K. Credential-Based Privacy-Preserving Power Request Scheme for Smart Grid Network. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM), Houston, TX, USA, 5–9 December 2011; pp. 1–5. [Google Scholar]
- Chu, C.K.; Liu, J.K.; Wong, J.W.; Zhao, Y.; Zhou, J. Privacy-preserving Smart Metering with Regional Statistics and Personal Enquiry Services. In Proceedings of the ACM SIGSAC Symposium on Information, Computer and Communications Security (ASIA CCS), Hangzhou, China, 8–10 May 2013; pp. 369–380. [Google Scholar]
- Zargar, S.H.M.; Yaghmaee, M.H. Privacy preserving via group signature in smart grid. In Proceedings of the Electric Industry Automation Congress (EIAC), Mashhad, Iran, 13–14 February 2013; pp. 1–5. [Google Scholar]
- Wang, H.; Wang, Z.; Domingo-Ferrer, J. Anonymous and secure aggregation scheme in fog-based public cloud computing. Future Gener. Comput. Syst. 2017, 1–8. [Google Scholar] [CrossRef]
- Zhang, P.; Li, W.; Sun, H. Cost-Efficient and Multi-Functional Secure Aggregation in Large Scale Distributed Application. PLoS ONE 2016, 11, e0159605. [Google Scholar] [CrossRef] [PubMed]
- Ni, J.; Zhang, K.; Alharbi, K.; Lin, X.; Zhang, N.; Shen, X. Differentially Private Smart Metering with Fault Tolerance and Range-Based Filtering. IEEE Trans. Smart Grid 2017, 8, 2483–2493. [Google Scholar] [CrossRef]
- Nandgaonkar, K.; Kamble, S. A survey on privacy-preserving data aggregation without secure channel. Int. Res. J. Eng. Technol. (IRJET) 2016, 3, 133–136. [Google Scholar]
- Li, S.; Xue, K.; Yang, Q.; Hong, P. PPMA: Privacy-Preserving Multi-Subset Aggregation in Smart Grid. IEEE Trans. Ind. Inform. 2017, PP, 1–10. [Google Scholar] [CrossRef]
- Gong, Y.; Cai, Y.; Guo, Y.; Fang, Y. A Privacy-Preserving Scheme for Incentive-Based Demand Response in the Smart Grid. IEEE Trans. Smart Grid 2016, 7, 1304–1313. [Google Scholar] [CrossRef]
- Ford, V.; Siraj, A.; Rahman, M.A. Secure and efficient protection of consumer privacy in Advanced Metering Infrastructure supporting fine-grained data analysis. J. Comput. Syst. Sci. 2017, 83, 84–100. [Google Scholar] [CrossRef]
- Mohassel, R.R.; Fung, A.; Mohammadi, F.; Raahemifar, K. A survey on Advanced Metering Infrastructure. Int. J. Electr. Power Energy Syst. 2014, 63, 473–484. [Google Scholar] [CrossRef]
- Murrill, B.J.; Liu, E.C.; Thompson, R.M. Smart meter data: Privacy and cybersecurity. Congressional Research Service, Library of Congress. 3 March 2012. Available online: http://marylandsmartmeterawareness.org/wp-content/uploads/2012/07/Congress-Research-Service-SM-privacy-and-cybersecurity.pdf (accessed on 27 September 2017).
- European Commission. My Energy Data—European Smart Grids Task Force Expert Group 1—Standards and Interoperability. Available online: https://ec.europa.eu/energy/sites/ener/files/documents/report_final_eg1_my_energy_data_15_november_2016.pdf (accessed on 1 September 2017).
- U.S. Energy Information Administration. An Assessment of Interval Data and Their Potential Application to Residential Electricity End-Use Modeling. Available online: https://www.eia.gov/consumption/residential/reports/smartmetering/pdf/assessment.pdf (accessed on 27 September 2017).
- World Energy Council. Energy Efficiency: A Recipe for Success. Available online: https://hub.globalccsinstitute.com/publications/energy-efficiency-recipe-success/ (accessed on 1 September 2017).
- Metering & Smart Energy International. Smart Grid Trends in Japan: 7 Things to Know. Available online: https://www.metering.com/smart-grid-trends-in-japan-7-things-to-know/ (accessed on 4 March 2015).
- Farah, S.; Javed, Y.; Shamim, A.; Nawaz, T. An experimental study on performance evaluation of asymmetric encryption algorithms. Recent Advances in Information Science. In Proceedings of the Proceeding of the 3rd European Conference of Computer Science, (EECS-12), Paris, France, 2–4 December 2012; pp. 121–124. [Google Scholar]
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Koo, D.; Shin, Y.; Hur, J. Privacy-Preserving Aggregation and Authentication of Multi-Source Smart Meters in a Smart Grid System. Appl. Sci. 2017, 7, 1007. https://doi.org/10.3390/app7101007
Koo D, Shin Y, Hur J. Privacy-Preserving Aggregation and Authentication of Multi-Source Smart Meters in a Smart Grid System. Applied Sciences. 2017; 7(10):1007. https://doi.org/10.3390/app7101007
Chicago/Turabian StyleKoo, Dongyoung, Youngjoo Shin, and Junbeom Hur. 2017. "Privacy-Preserving Aggregation and Authentication of Multi-Source Smart Meters in a Smart Grid System" Applied Sciences 7, no. 10: 1007. https://doi.org/10.3390/app7101007




