Mutual Authentication Protocol for Role-Based Access Control Using Mobile RFID
Abstract
:1. Introduction
2. Relative Works
2.1. RFID Security Requirements
- (1)
- Data integrity: The RFID should still be able to identify information even if the tag has been attacked and modified.
- (2)
- Confidentiality independence: Even if a tag has been compromised and the key is known, it cannot be used to forge other tags in order to deceive the back-end server.
- (3)
- User privacy: An attacker cannot use the information sent by a tag to retrieve all the data within the tag to determine its location.
- (4)
- Forward secrecy: Even if an attacker is able to compromise a tag and retrieve the data stored within the tag, that information cannot be used to find previously sent data.
- (5)
- Protection against replay attacks: Even if an attacker can obtain the legal information sent from a tag to a reader, repeated sending of this data cannot be used to deceive the back-end server.
- (6)
- Protection against denial of service attacks: Even if an attacker can intercept or block data to cripple the system, the RFID system can still identify tags normally.
- (7)
- Protection against forgery attacks: Even if an attacker illegally obtains some of the information within a tag, it cannot be used to forge a legal tag and deceive a legal reader.
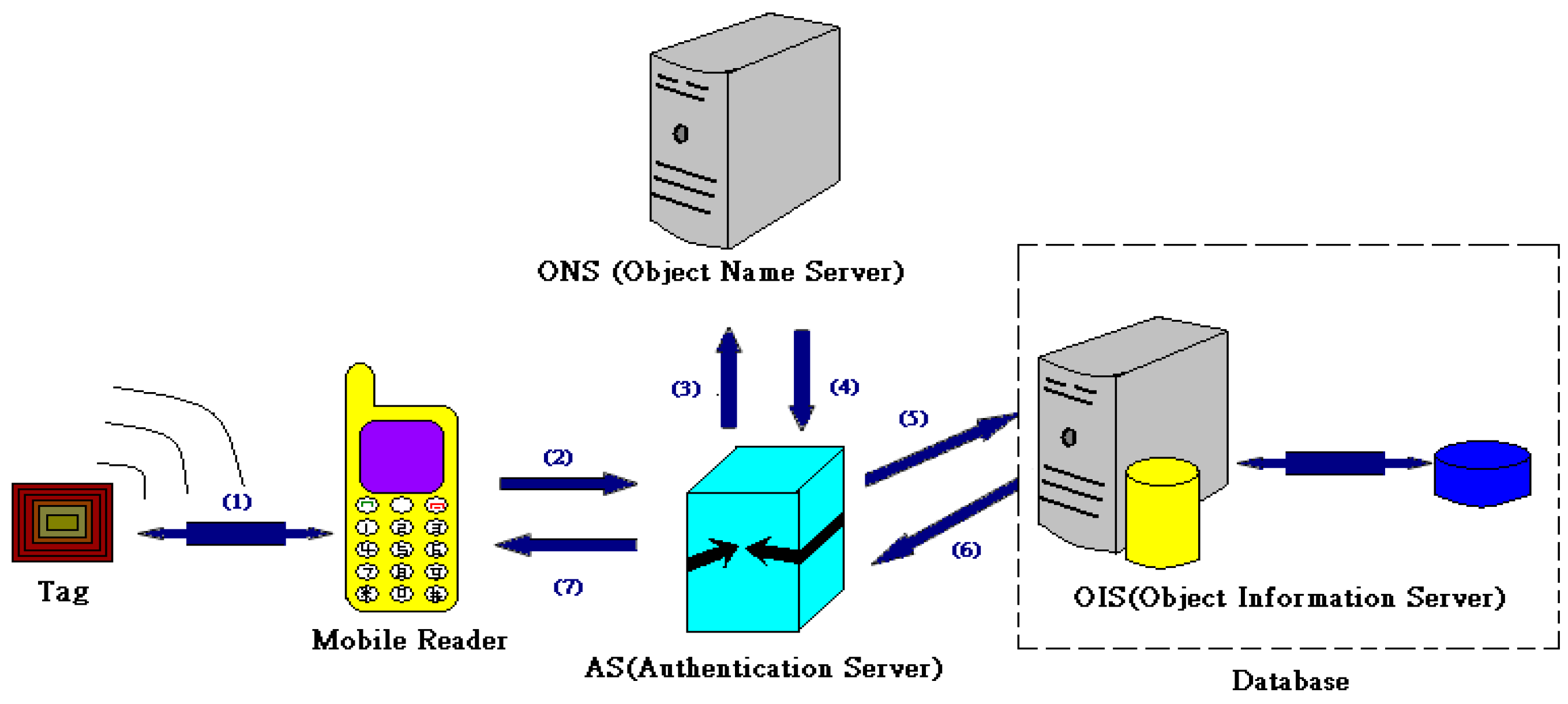
2.2. Mobile RFID Technology
- Step 1: The mobile reader requests to read the electronic tag and receives a reply.
- Step 2: The mobile reader reads the information in the electronic tag and sends it to the AS.
- Step 3: After AS certification, it inquires the ONS for the detailed information storage address for the electronic tag.
- Step 4: The ONS receives the inquiry and sends the electronic tag URL to the AS.
- Step 5: The AS retrieves the information in the electronic tag from the object information server (OIS) via the URL.
- Step 6: The OIS sends the electronic tag information to the AS.
- Step 7: The AS sends the electronic tag information to the mobile RFID reader.
2.3. Role-Based Access Control
- USERS: Human beings that interact with the system or artificial intelligence, such as intelligent robots.
- ROLES: Work functions or work positions that can be seen as a role within an organization or access control mechanism and are used to determine permissions within a firm.
- PRMS: Authority regarding objects in an access machine, including methods of storage and retrieval or operations.
- SESSIONS: Duration of role assignment, indicating the start and end times that a user has a certain role.
- UA: Users can have more than one role and roles can be assigned to more than one user. Sessions are the unit for access control. During any session, users can only act in one role. Many different roles with different functions simultaneously participate in any session. Conferences include directors, operational managers, marketing managers, and project members. However, for this session, participants may have more than one role.
- PA: Roles can have more than one permission, and permissions can be assigned to more than one role. When maintaining the relationships between users and roles and between roles and permissions, users’ roles can be changed, added, or removed, effectively changing, adding, or removing permissions. This simplifies work for managers and work systems which, in turn, reduces costs.
- User_Sessions: When a user wishes to use the role assigned, a user session is created. A single user can create multiple sessions, but a user session can only correspond to one user.
- Session_roles: Session_roles are the roles for the users included in a user session. User sessions can have more than one role and roles can be used in more than one user session.
3. System Architecture and Concept
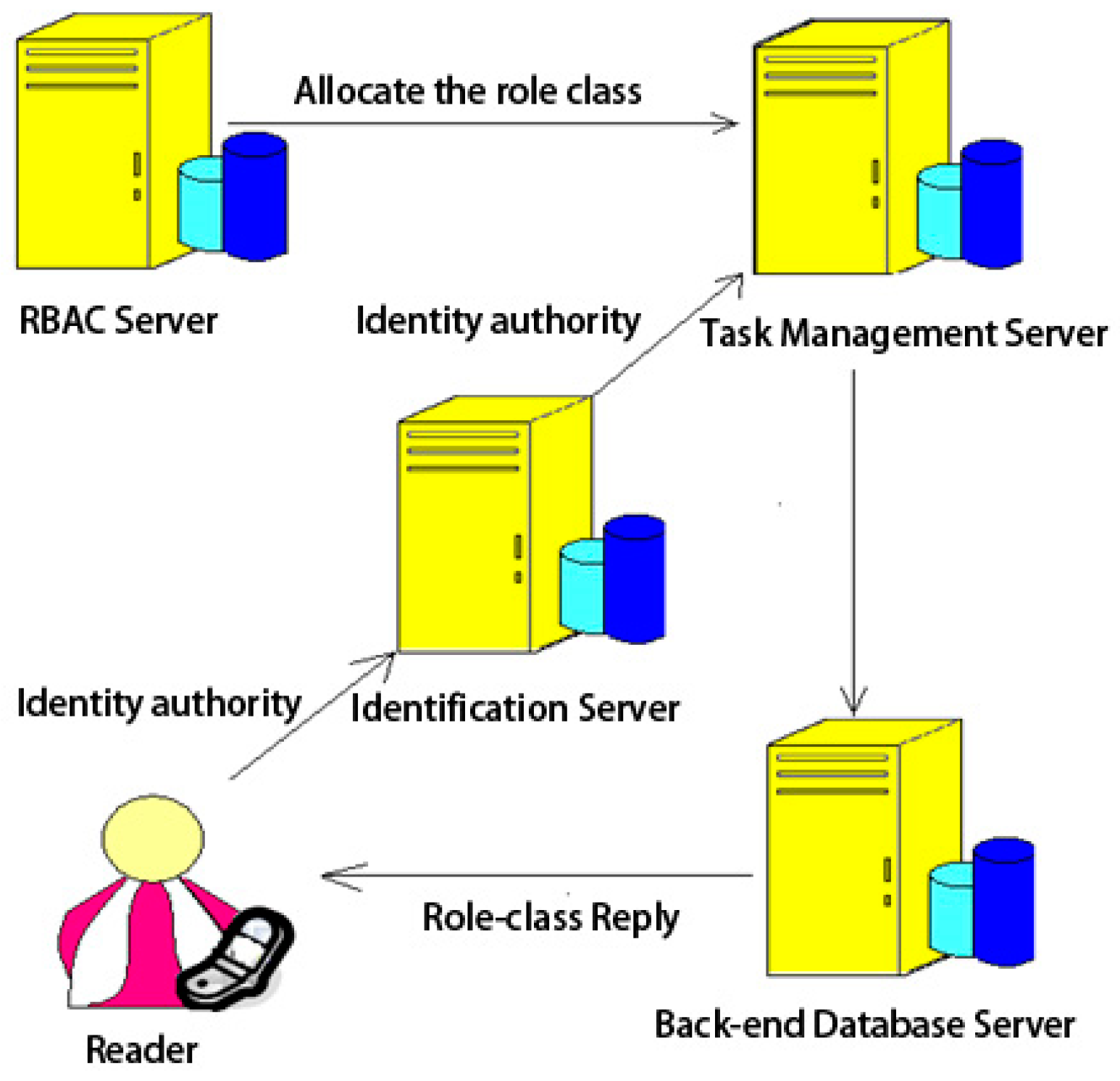
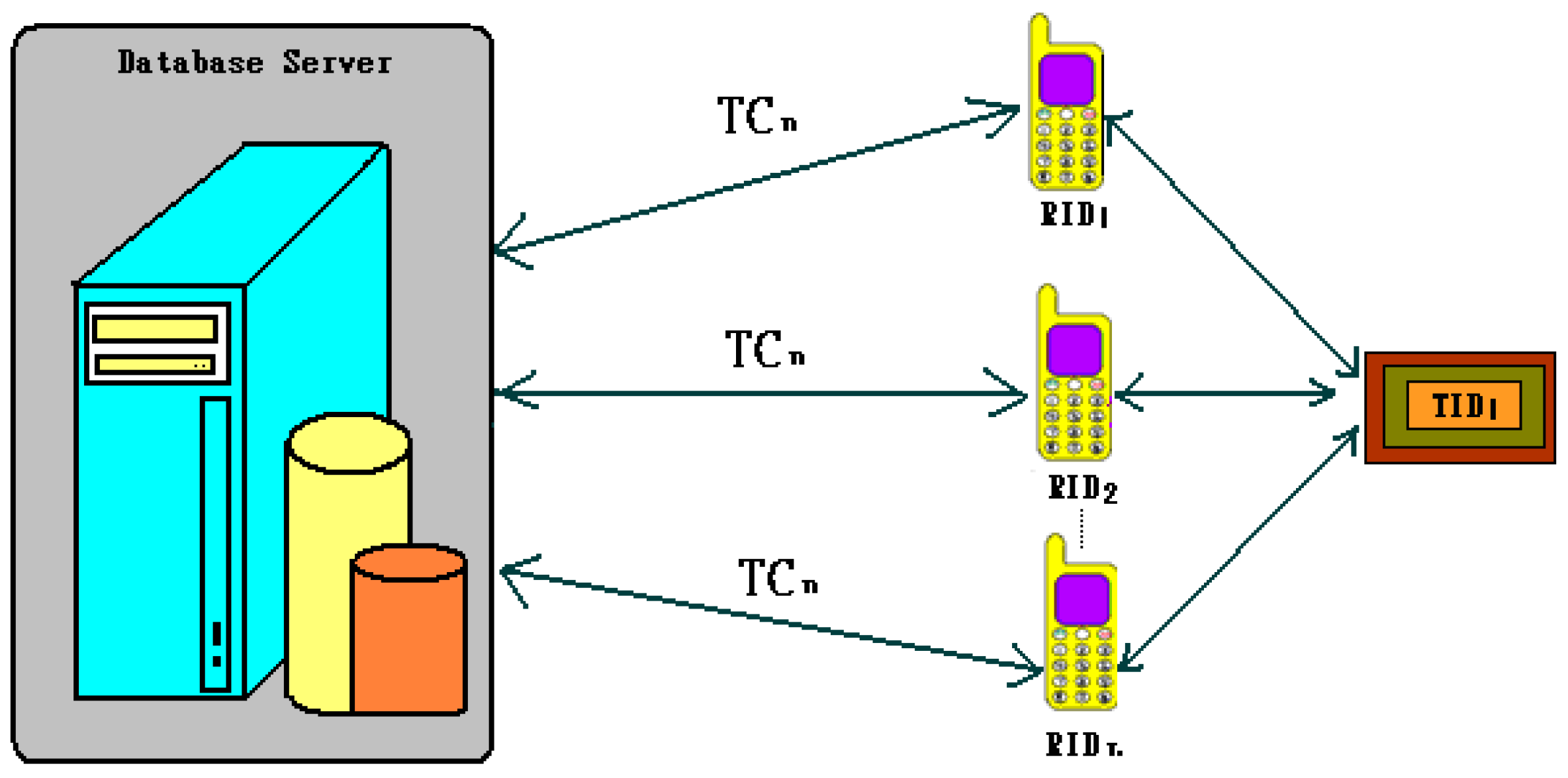
3.1. Mobile RFID System Architecture
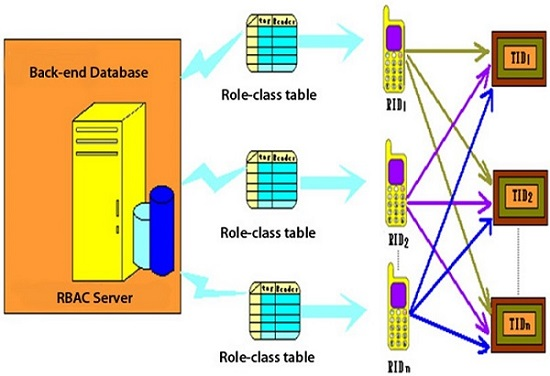
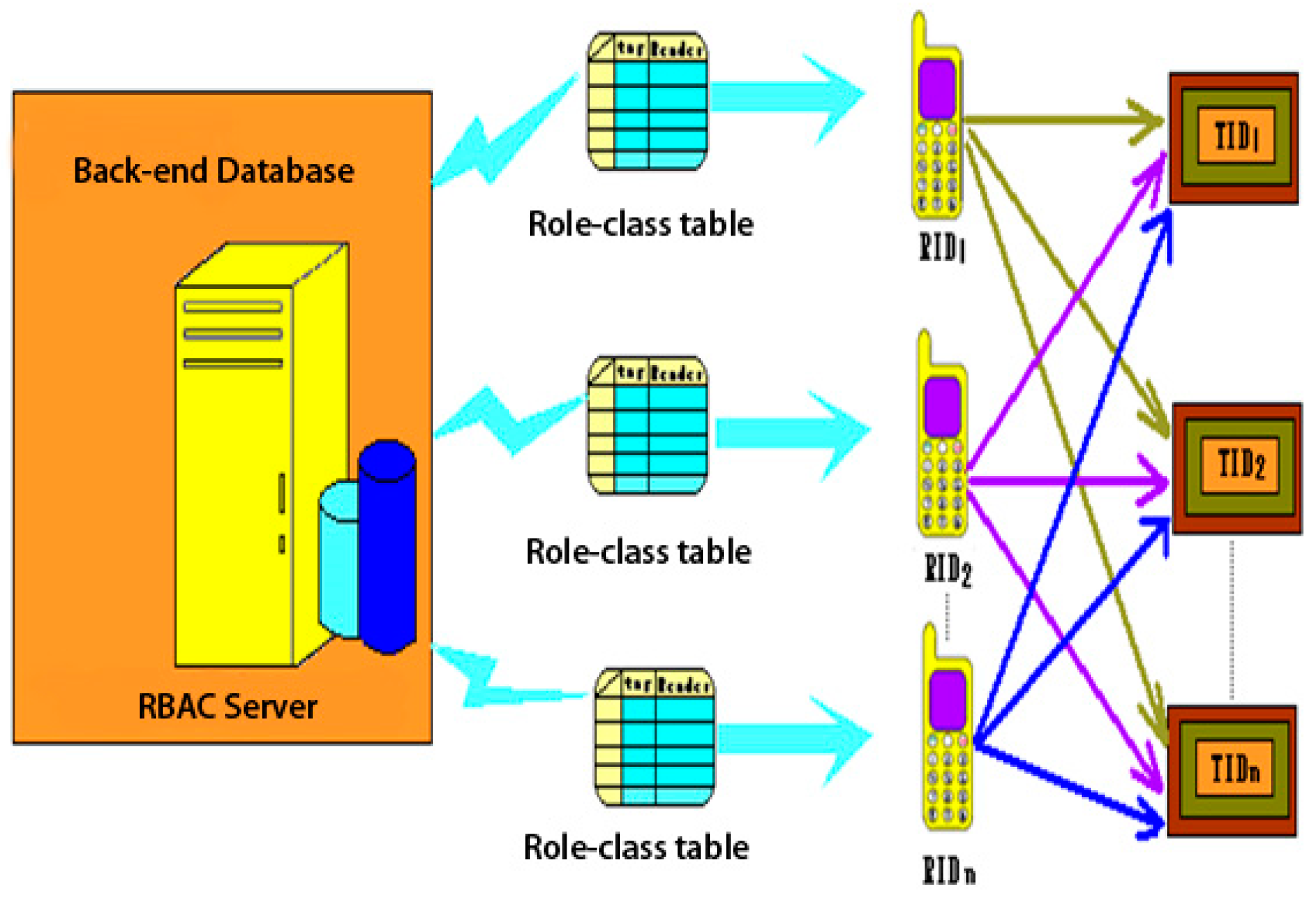
3.2. RBAC Server Architecture
3.3. Mobile RFID System Architecture
3.3.1. Reader Security Certificate and Role-Class Architecture
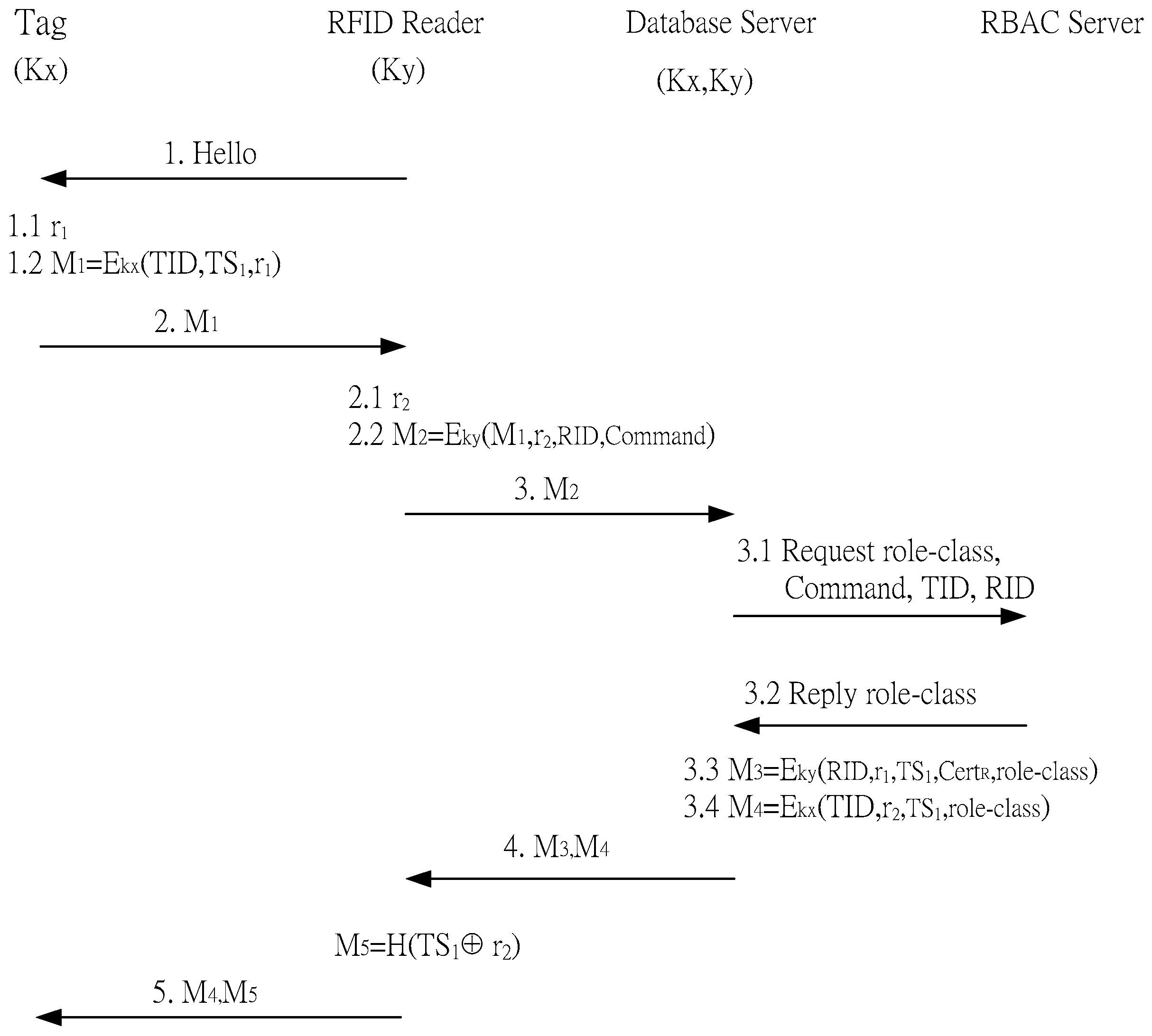
- Step 1: A reader reads an electronic tag by sending a HELO command to the tag
- Step 1.1: The tag creates a random number r1
- Step 1.2: The electronic tag ID TID, time stamp TS1, random number r1, and the shared key between the back-end database and the tag Kx are used to create an encrypted M1, which is sent to the reader
- Step 2: The electronic tag sends M1 to the reader
- Step 2.1: The reader receives M1 and creates a random number r2
- Step 2.2: The reader ID RID, tag read request, random number r2, M1, and the shared key between the back-end database and reader Ky are used to create an encrypted M2
- Step 3: The reader sends M2 to the back-end database
- Step 3.1: The request role-class command, read tag command, TID, and RID are sent to the back-end database
- Step 3.2: A role-class is sent to the reader
- Step 3.3: The RID, random number r2, initial tag time stamp TS1, reader security certificate CertR, role-class, and Ky are used to create M3, which is sent to the reader. The RID, random number r1, role-class, and Kx are used to create M4, which is sent to the electronic tag
- Step 4: The reader receives M3 and uses Ky to decrypt random number r1, initial tag time stamp TS1, reader security certificate CertR, and the role-class. TS1 and r2 are used in a hash function to create M5
3.3.2. Number of Reads and Time Stamp Updating
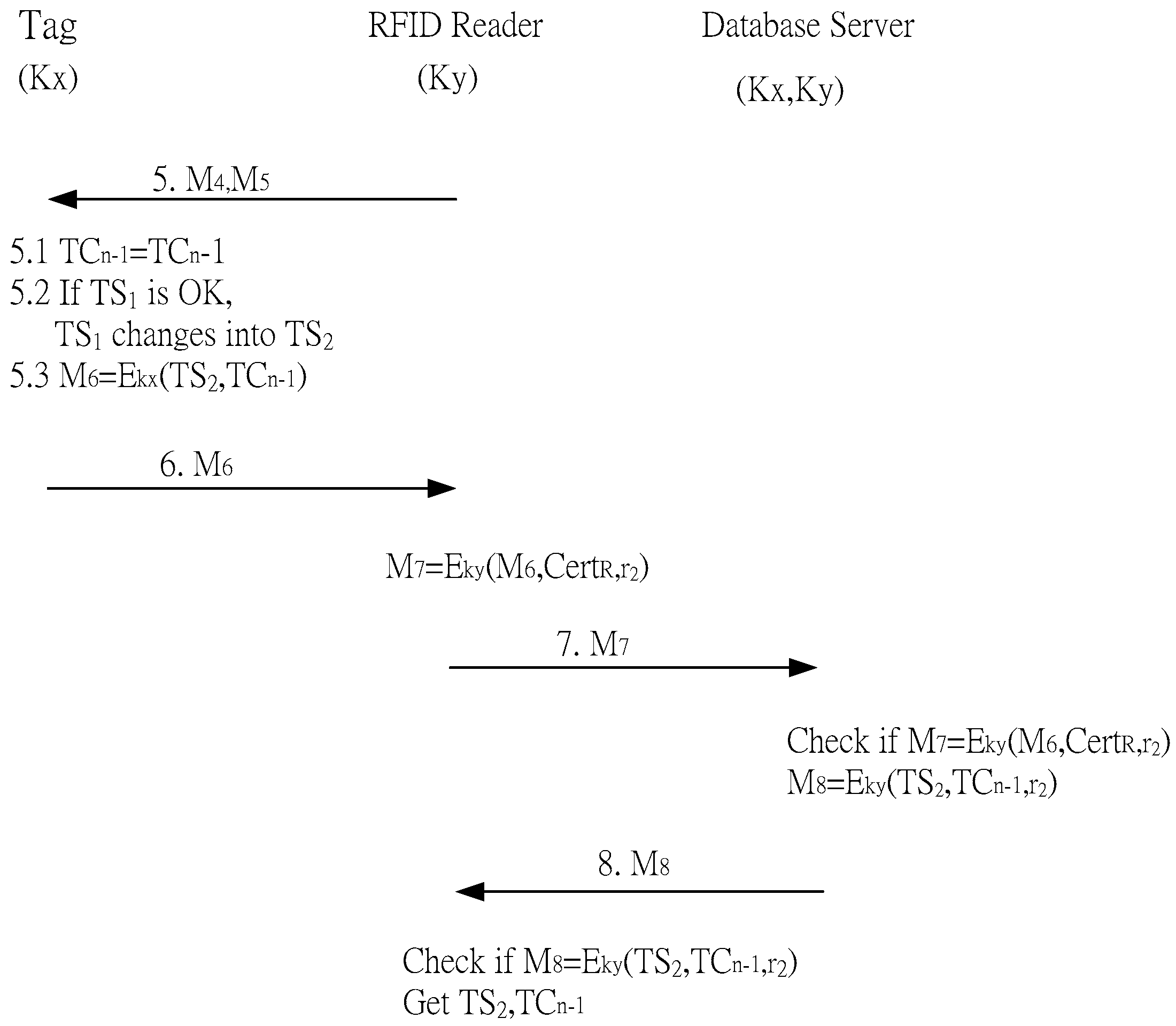
- Step 5: M4 and M5 are sent to the electronic tag. The tag can check the correctness of M5 using TS1 and r2 which were obtained by decrypting M4. Therefore, the tag can authenticate the reader
- Step 5.1: One is subtracted from TCn to become TCn−1
- Step 5.2: TS1 is verified as the initial time stamp sent from the electronic tag. If it is, it is updated to TS2
- Step 5.3: TS2, TCn−1, r2, and Kx are used to create an encrypted M6, which is sent to the reader
- Step 6: The reader receives M6
- Step 6.1: Ky, CertR, r2, and M6 are encrypted to create M7, which is sent to the back-end database
- Step 7: The back-end database receives M7
- Step 7.1: After receiving M7, Ky is used to decrypt M6, CertR, and r2. If CertR verifies the reader is authorized, Kx is used to decrypt M6 to retrieve the updated time stamp TS2
- Step 7.2: The back-end database uses Ky to encrypt M8
- Step 8: The reader receives M8
- Step 8.1: The reader uses Ky to decrypt TS2, TCn−1 and r2. r2 is checked to ensure that the signal is sent from the back-end database
4. Security Analysis
- (1)
- User privacy: As the encrypted data sent was calculated using the random numbers generated from the electronic tag and reader, r1 and r2, the values were untraceable. Moreover, attackers cannot have the tag key to determine the tag identity. Data is anonymous and untraceable, providing user privacy.
- (2)
- Non-linkability: Tags create different random numbers for each reading. Thus, all response values are different, making it impossible for attackers to determine whether data was sent from the same tag.
- (3)
- Confidentiality: In the proposed mechanism, each tag’s key is shared with the back-end database. If the reader is not authorized, it cannot read the electronic tag because it does not have the tag key.
- (4)
- Data integrity: The tag reduces the number of reads based on the data sent from the reader and uses the shared key to encrypt this data before sending it to the reader. Readers must send a certificate to the back-end database to verify its legality. The time stamp and number of reads are only sent to the reader after verification to ensure data integrity.
- (5)
- Protection against replay attacks: As the data sent from the tag Mn is calculated using the random numbers generated from the reader r2 and the tag r1, and r2 is different during each read, even if an attacker captures data sent from a tag, they are unable to resend the captured data.
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Ailisto, H.; Matinmikko, T.; Haihio, J.; Ylisaukko-Oja, A.; Strommer, E.; Hillukkala, M.; Wallin, A.; Siira, E.; Poyry, A.; Tormanen, V.; et al. Physical Browsing with NFC Technology. Available online: http://www.vtt.fi/inf/pdf/tiedotteet/2007/T2400.pdf (accessed on 26 July 2016).
- Zhang, C.; Zhang, W.; Mu, H. A Mutual Authentication Security RFID Protocol Based on Time Stamp. In Proceedings of the First International Conference on Computational Intelligence Theory, Systems and Applications, Yilan, Taiwan, 10–12 December 2015; pp. 166–170.
- Rahman, M.; Sampangi, R.V.; Sampalli, S. Lightweight protocol for anonymity and mutual authentication in RFID systems. In Proceedings of the IEEE 12th Consumer Communications and Networking Conference, Las Vegas, NV, USA, 9–12 January 2015; pp. 910–915.
- Nyikes, Z. Information security issues of RFID. In Proceedings of the IEEE 14th International Symposium on Applied Machine Intelligence and Informatics, Herl’any, Slovakia, 21–23 January 2016; pp. 111–114.
- Kim, I.J.; Choi, E.Y.; Lee, D.H. Secure Mobile RFID system against privacy and security problems. In Proceedings of the Third International Workshop on Security, Privacy and Trust in Pervasive and Ubiquitous Computing, Istanbul, Turkey, 19 July 2007.
- Ferraiolo, D.; Kuhn, R. Role-Based Access Control. In Proceedings of the 15th NIST-NCSC National Computer Security Conference, Baltimore, MD, USA, 13–16 October 1992.
- Sandu, R.; hamidipati, B. Role-based administration of user-role Assignment: The URA97 Model and its Oracle Implementation. J. Comput. Secur. 1999, 7, 317–332. [Google Scholar] [CrossRef]
- Gavrila, S.I.; Barkly, J.F. Formal specification for role based access control user/role relationship management. In Proceedings of the Third ACM workshop on Role-Based Access Control, Fairfax, VA, USA, 22–23 October 1998; pp. 81–90.
- Tari, Z.; Chan, S.H. A role-based control for intranet security. IEEE Internet Comput. 1997, 1, 24–34. [Google Scholar] [CrossRef]
- Coyne, R.S.E.; Feinstein, H.; Yourman, C. Role-Based Access Control Modes. IEEE Comput. 1996, 29, 38–47. [Google Scholar]
- Choi, S.H.; Yang, B.; Cheung, H.H.; Yang, Y.X. Data management of RFID-based track and trace anti-counterfeiting in apparel supply chain. In Proceedings of the 8th Internation Conference for Internet Technology and Secured Transactions, London, UK, 9–12 December 2013; pp. 265–269.
| r1, r2, r3 | Random numbers generated by the electronic tag reader and back-end database |
| TID, RID | Electronic tag identification number and reader identification number |
| TS1…TSn−1 | Time stamp |
| command | Reading command sent from reader to electronic tag |
| role-class | Role and permissions |
| CertR | Security certificate given to the reader by the back-end database |
| TCn | Number of times n a reader can retrieve information |
| Kx | Shared back-end database key for an electronic tag |
| Ky | Shared back-end database key for a reader |
| Mn | Encrypted value using the shared keys Kx and Ky |
| Computation\Role | Tag | Reader | Database |
|---|---|---|---|
| Random number | 1/0 | 1/0 | 0/0 |
| Encryption | 1/1 | 1/1 | 2/1 |
| Decryption | 0/1 | 1/1 | 1/1 |
| Hash | 0/0 | 0/0 | 0/0 |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, B.-C.; Yang, C.-T.; Yeh, H.-T.; Lin, C.-C. Mutual Authentication Protocol for Role-Based Access Control Using Mobile RFID. Appl. Sci. 2016, 6, 215. https://doi.org/10.3390/app6080215
Chen B-C, Yang C-T, Yeh H-T, Lin C-C. Mutual Authentication Protocol for Role-Based Access Control Using Mobile RFID. Applied Sciences. 2016; 6(8):215. https://doi.org/10.3390/app6080215
Chicago/Turabian StyleChen, Bing-Chang, Cheng-Ta Yang, Her-Tyan Yeh, and Ching-Chao Lin. 2016. "Mutual Authentication Protocol for Role-Based Access Control Using Mobile RFID" Applied Sciences 6, no. 8: 215. https://doi.org/10.3390/app6080215