Task-Management Method Using R-Tree Spatial Cloaking for Large-Scale Crowdsourcing
Abstract
:1. Introduction
2. Related Works
3. R-Tree Spatial Cloaking-Based Task Assignment Method
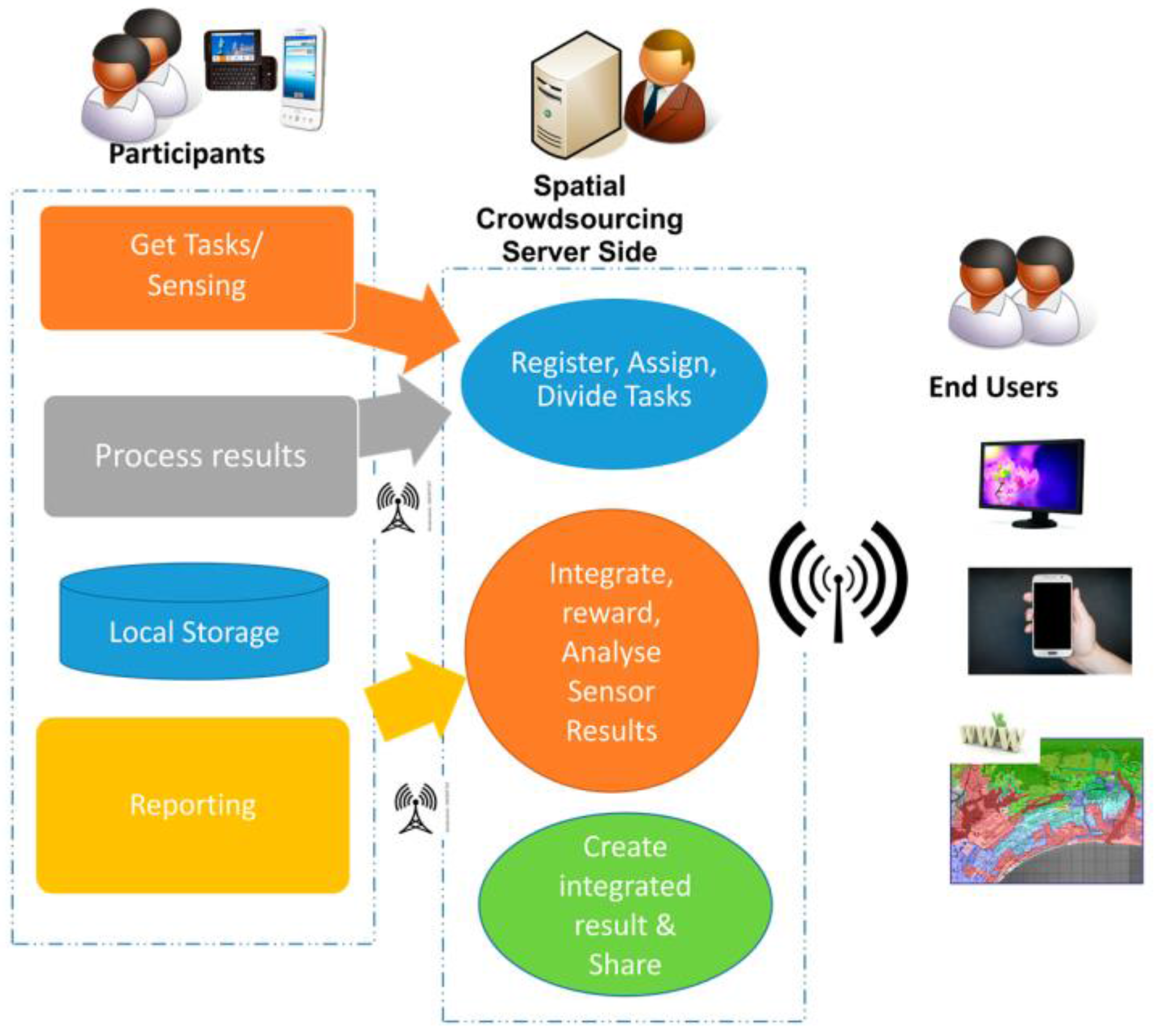
3.1. Spatial Task Management Process
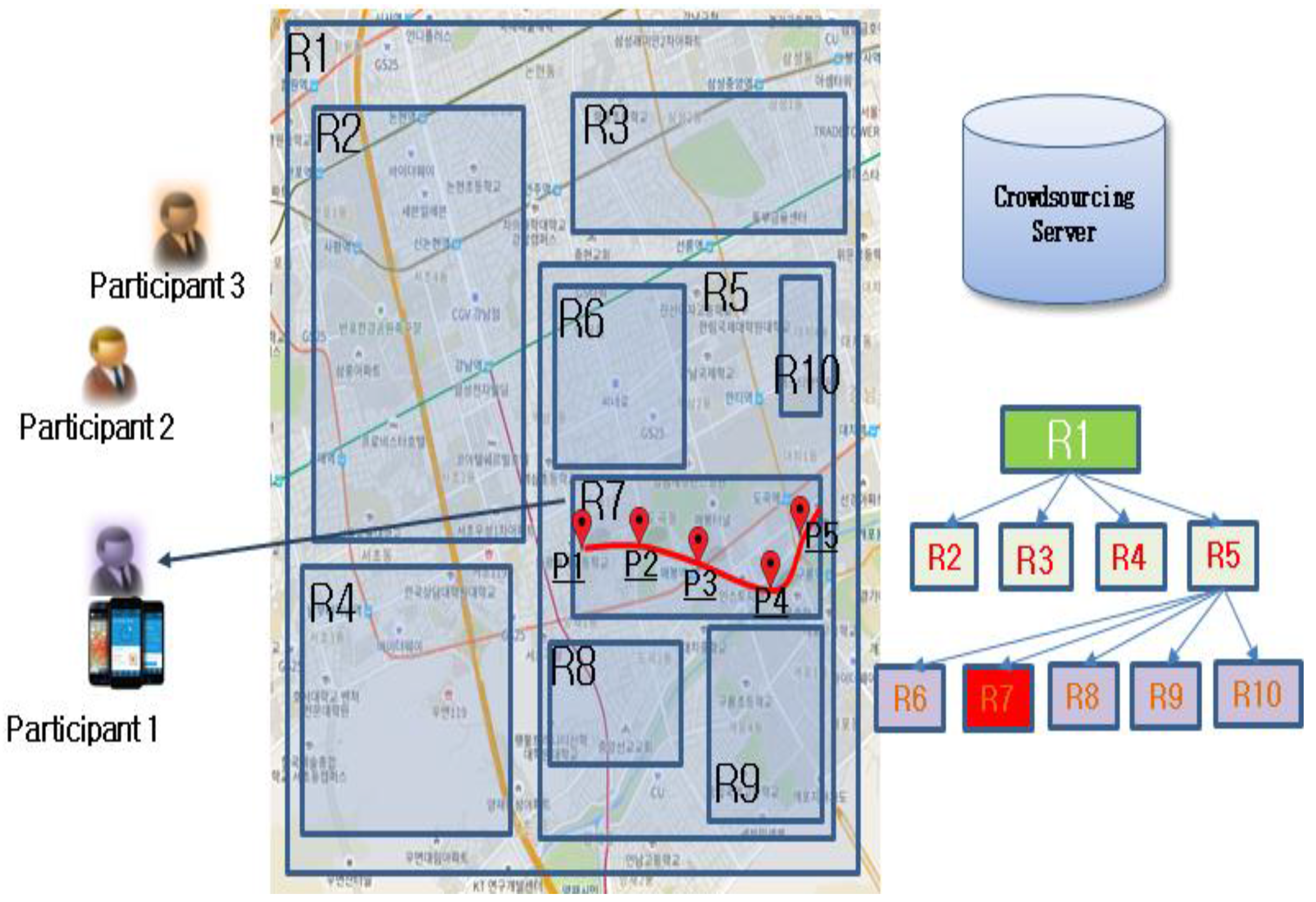
3.2. R-Tree-Based Task-Assignment Method
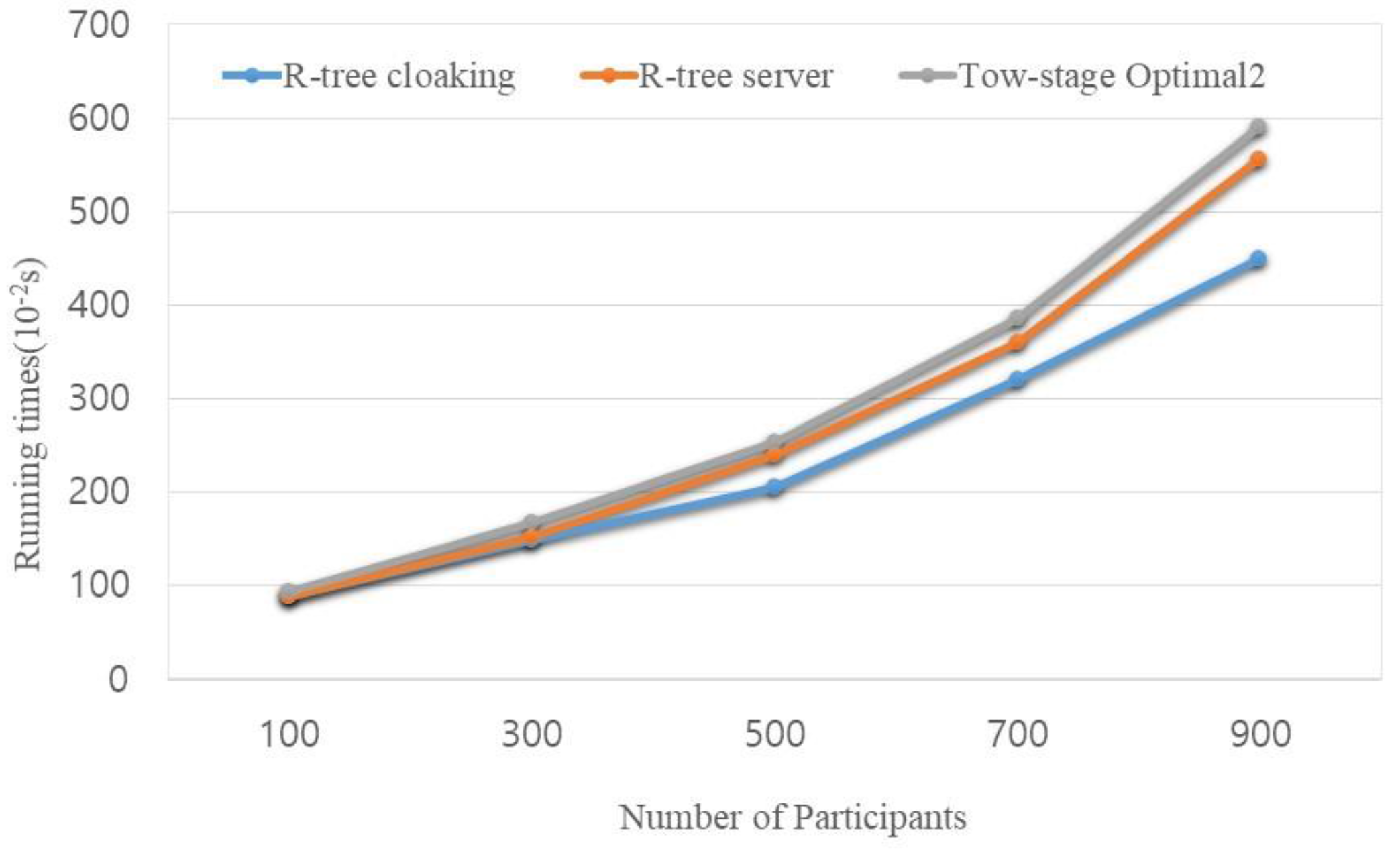
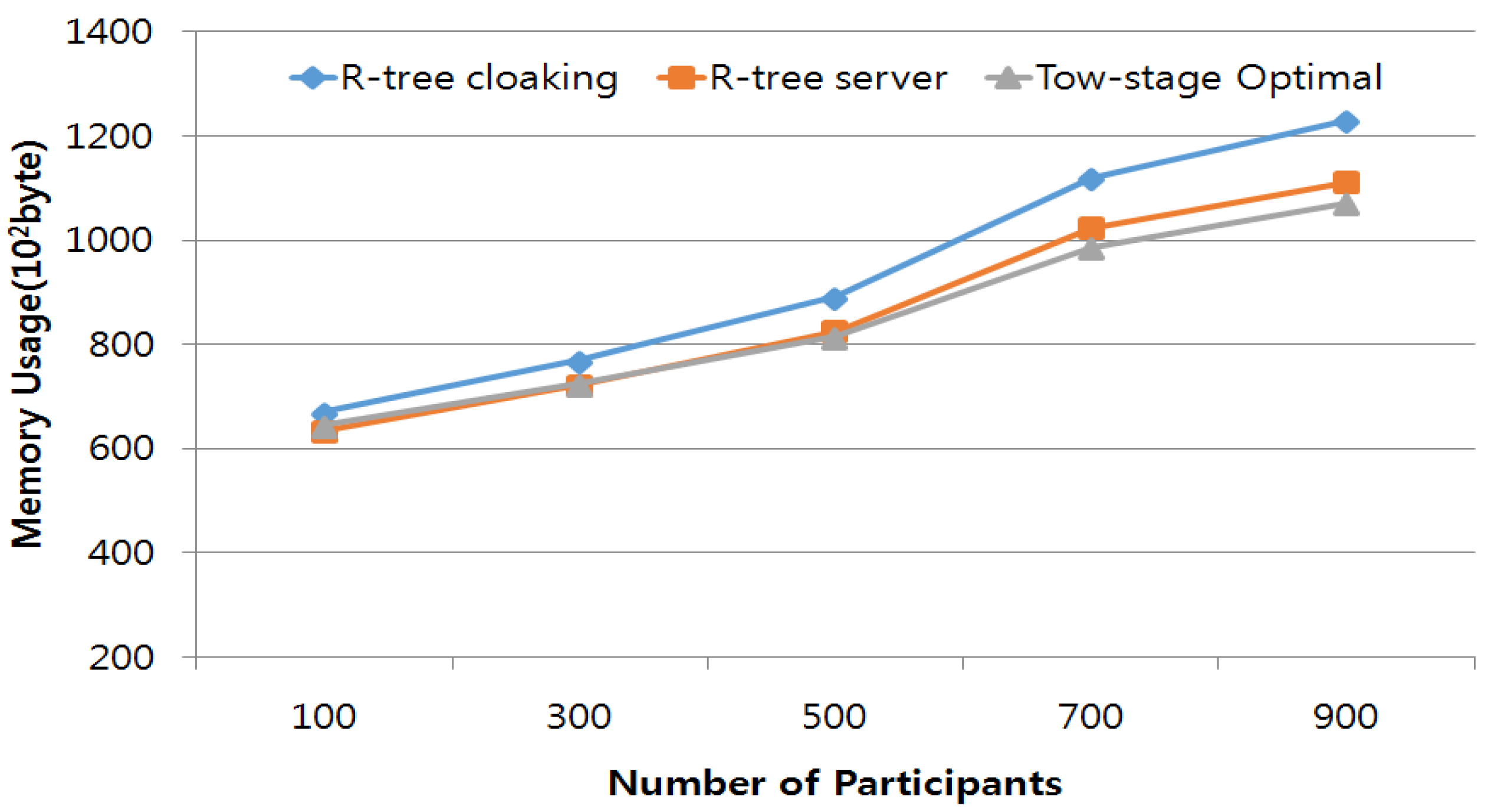
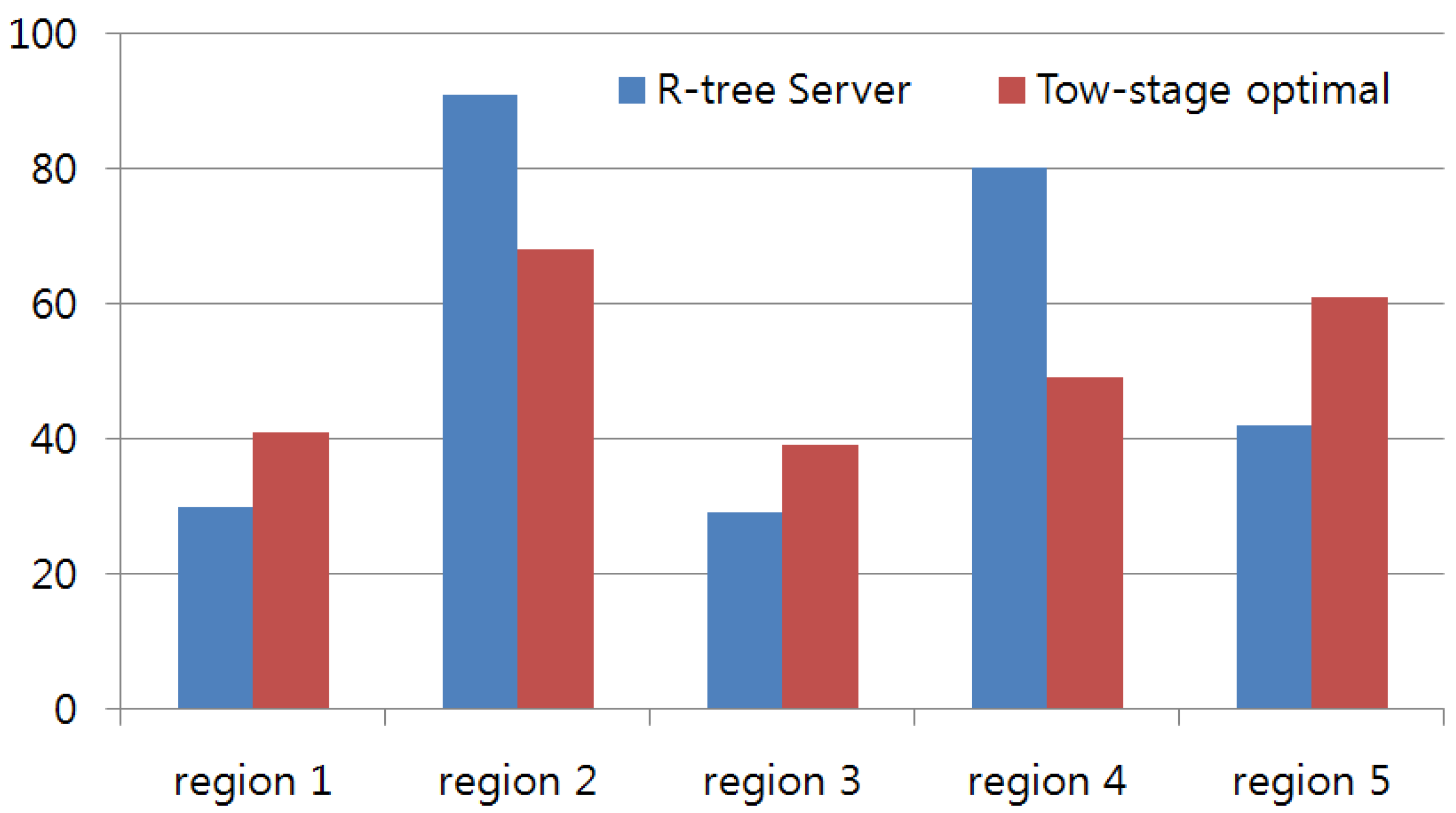
4. Experimental Results
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Tran, L.; To, H.; Fan, L.; Shahabi, C. A real-time framework for task assignment in hyperlocal spatial crowdsourcing. ACM Trans. Intell. Syst. Technol. 2017, arXiv:1704.06868. [Google Scholar]
- To, H. Task Assignment in Spatial Crowdsourcing: Challenges and Approaches. In Proceedings of the 3rd ACM SIGSPATIAL PhD Symposium, San Francisco, CA, USA, 26 June–1 July 2016. [Google Scholar]
- Sensorly. Available online: http://www.sensorly.com (accessed on 20 May 2017).
- Koukoumidis, E.; Peh, L.-S.; Martonosi, M.R. Signalguru: Leveraging Mobile Phones for Collaborative Traffic Signal Schedule Advisory. In Proceedings of the ACM MobiSys, Bethesda, MD, USA, 28 June–1 July 2011; pp. 127–140. [Google Scholar]
- Mohan, P.; Padmanabhan, V.N.; Ramjee, R. Nericell: Rich Monitoring of Road and Traffic Conditions Using Mobile Smartphones. In Proceedings of the ACM SensSys, Raleigh, NC, USA, 5–7 November 2008; pp. 323–336. [Google Scholar]
- Thiagarajan, A.; Ravindranath, L.; LaCurts, K.; Madden, S.; Balakrishnan, H.; Toledo, S.; Eriksson, J. Vtrack: Accurate, Energy-aware Road Traffic Delay Estimation Using Mobile Phones. In Proceedings of the ACM SenSys, Berkeley, CA, USA, 4–6 November 2009; pp. 85–98. [Google Scholar]
- Rana, R.K.; Chou, C.T.; Kanhere, S.S.; Bulusu, N.; Hu, W. Earphone: An End-to-end Participatory Urban Noise Mapping System. In Proceedings of the ACM/IEEE IPSN, Stockholm, Sweden, 12–16 April 2010; pp. 105–116. [Google Scholar]
- Stevens, M.; Hondt, E.D. Crowdsourcing of Pollution Data Using Smartphones. In Proceedings of the ACM UbiComp, Copenhagen, Denmark, 26 September 2010; pp. 1–4. [Google Scholar]
- Zhao, D.; Li, X.-Y.; Ma, H. How to Crowdsource Tasks Truthfully without Sacrificing Utility: Online Incentive Mechanisms with Budget Constraint. In Proceedings of the IEEE, Toronto, ON, Canada, 27 April–2 May 2014. [Google Scholar]
- Singer, Y.; Mittal, M. Pricing Mechanisms for Crowdsourcing Markets. In Proceedings of the World Wide Web, Rio de Janeiro, Brazil, 13–17 May 2013; pp. 1157–1166. [Google Scholar]
- Singla, A.; Krause, A. Truthful Incentives in Crowdsourcing Tasks Using Regret Minimization Mechanisms. In Proceedings of the World Wide Web, Rio de Janeiro, Brazil, 13–17 May 2013; pp. 1167–1178. [Google Scholar]
- Kazemi, L.; Shahabi, C. Geocrowd: Enabling Query Answering with Spatial Crowdsourcing. In Proceedings of the 20th International Conference on Advances in Geographic Information Systems, Redondo Beach, CA, USA, 6–9 November 2012. [Google Scholar]
- To, H.; Ghinita, G.; Shahabi, C. A Framework for Protecting Worker Location Privacy in Spatial Crowdsourcing. Proc. VLDB Endow. 2014, 7, 919–930. [Google Scholar] [CrossRef]
- Hassan, U.; Curry, E. Efficient task assignment for spatial crowdsourcing: A combinatorial fractional optimization approach with semi-bandit learning. Expert Syst. Appl. 2016, 58, 36–56. [Google Scholar] [CrossRef]
- Tong, Y.; She, J.; Ding, B.; Wang, L.; Chen, L. Online Mobile Micro-Task Allocation in Spatial Crowdsourcing. In Proceedings of the 2016 IEEE 32nd International Conference on Data Engineering, Helsinki, Finland, 16–20 May 2016; pp. 49–60. [Google Scholar]
- Bugra, G.; Liu, L. Location privacy in mobile systems: A personalized anonymization model. In Proceedings of the 25th IEEE International Conference on Distributed Computing Systems, Columbus, OH, USA, 6–10 June 2005. [Google Scholar]
- Chow, C.-Y.; Mokbel, M.F.; Liu, X. Spatial cloaking for anonymous location-based services in mobile peer-to-peer environments. Geoinformatica 2011, 15, 351–380. [Google Scholar] [CrossRef]
- Pournajaf, L.; Xiong, L.; Sunderam, V.; Goryczka, S. Spatial Task Assignment for Crowd Sensing with Cloaked Locations. In Proceedings of the IEEE 15th International Conference on Mobile Data Management, Brisbane, Australia, 14–18 July 2014; pp. 73–82. [Google Scholar]
- Liu, Y.; Niu, J.; Liu, X. Comprehensive tempo-spatial data collection in crowd sensing using a heterogeneous sensing vehicle selection method. Pers. Ubiquitous Comput. 2016, 20, 397–411. [Google Scholar] [CrossRef]
- Cheng, P.; Lian, X.; Chen, Z.; Fu, R.; Chen, L.; Han, J.; Zhao, J. Reliable Diversity-based Spatial Crowdsourcing by Moving Workers. Proc. VLDB Endow. 2015, 8, 1022–1033. [Google Scholar] [CrossRef]
- Gardner, Z.; Leibovici, D.; Basiri, A.; Foody, G. Trading-off location accuracy and service quality: Privacy concerns and user profiles. In Proceedings of the International Conference on Location and GNSS, ICL-GNSS 2017 Conference, Nottingham, UK, 27–29 June 2017. [Google Scholar]
- Wang, L.; Yang, D.; Han, X.; Wang, T.; Zhang, D.; Ma, X. Location Privacy-Preserving Task Allocation for Mobile Crowdsensing with Differential Geo-Obfuscation. Proceeding of the 26th International Conference on World Wide Web, Perth, Australia, 3–7 April 2017; pp. 627–636. [Google Scholar]
- Alfarrarjeh, A.; Emrich, T.; Shahabi, C. Scalable Spatial Crowdsourcing: A Study of Distributed Algorithms. In Proceedings of the 16th IEEE International Conference on Mobile Data Management, Pittsburgh, PA, USA, 15–18 June 2015. [Google Scholar]
- Oleson, D.; Sorokin, A.; Laughlin, G.; Hester, V.; Le, J.; Biewald, L. Programmatic gold: Targeted and scalable quality assurance in crowdsourcing. Hum. Comput. 2011, 11, 43–48. [Google Scholar]
- Van Pelt, C.; Sorokin, A. Designing a Scalable Crowdsourcing Platform. In Proceedings of the 2012 ACM SIGMOD International Conference on Management of Data, Scottsdale, AZ, USA, 20–24 May 2012. [Google Scholar]
- Guttman, A. R-trees: A dynamic index structure for spatial searching. In Proceedings of the 1984 ACM SIGMOD International Conference on Management of Data, Boston, MA, USA, 18–21 June 1984. [Google Scholar]
- Cheng, P.; Lian, X.; Chen, L.; Han, J.; Zhao, J. Task assignment on multi-skill oriented spatial crowdsourcing. IEEE Trans. Knowl. Data Eng. 2016, 28, 2201–2215. [Google Scholar] [CrossRef]
- To, H.; Ghinita, G.; Fan, L.; Shahabi, C. Differentially private location protection for worker datasets in spatial crowdsourcing. IEEE Trans. Mob. Comput. 2017, 16, 934–949. [Google Scholar] [CrossRef]
- Deng, D.; Shahabi, C.; Demiryurek, U.; Zhu, L. Task selection in spatial crowdsourcing from worker’s perspective. Geoinformatica 2016, 20, 529–568. [Google Scholar] [CrossRef]
- Pournajaf, L.; Xiong, L.; Sunderam, V. Dynamic data driven crowd sensing task assignment. Procedia Comput. Sci. 2014, 29, 1314–1323. [Google Scholar] [CrossRef]
- Cho, E.; Myers, S.A.; Leskovec, J. Friendship and mobility: User movement in location-based social networks. In Proceedings of the 17th ACM SIGKDD International Conference on Knowledge Discovery and Data Mining, San Diego, CA, USA, 21–24 August 2011. [Google Scholar]
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Li, Y.; Shin, B.-S. Task-Management Method Using R-Tree Spatial Cloaking for Large-Scale Crowdsourcing. Symmetry 2017, 9, 311. https://doi.org/10.3390/sym9120311
Li Y, Shin B-S. Task-Management Method Using R-Tree Spatial Cloaking for Large-Scale Crowdsourcing. Symmetry. 2017; 9(12):311. https://doi.org/10.3390/sym9120311
Chicago/Turabian StyleLi, Yan, and Byeong-Seok Shin. 2017. "Task-Management Method Using R-Tree Spatial Cloaking for Large-Scale Crowdsourcing" Symmetry 9, no. 12: 311. https://doi.org/10.3390/sym9120311



