The Design and Analysis of a Secure Personal Healthcare System Based on Certificates
Abstract
:1. Introduction
2. Related Works
2.1. e-Healthcare Service
2.2. e-Healthcare Security
2.3. Previous Research on e-Healthcare
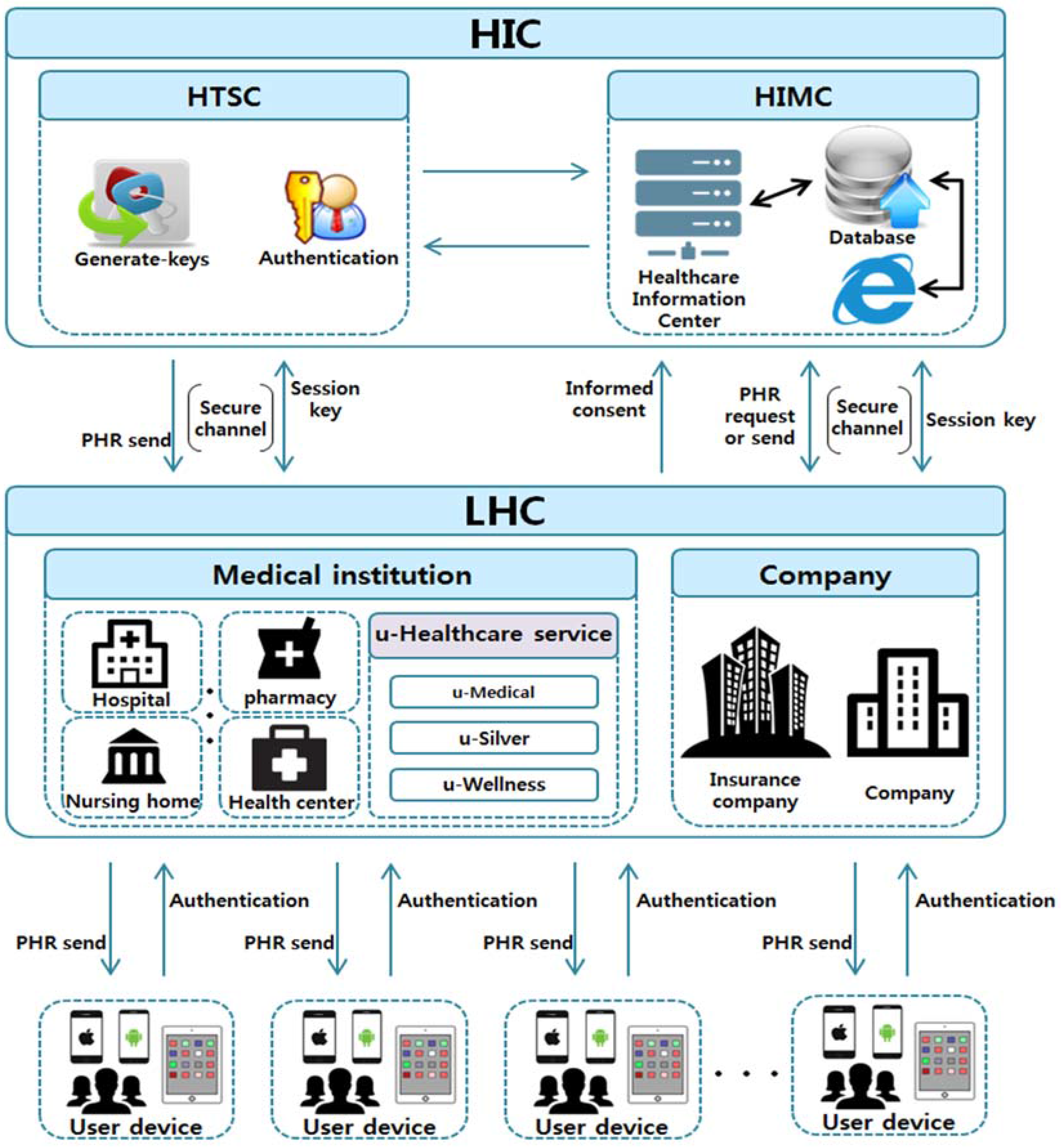
3. Proposed Infrastructure
3.1. Proposed e-Healthcare Service Infrastructure
3.2. Proposed Protocol
3.2.1. Mutual Authentication Protocol
- Step 1
- The LHC sends its own authentication to the HTSC and requests authentication from the HTSC.
- Step 2
- After receiving a certificate from the LHC, the HTSC verifies it and requests the certificate from the HIMC and sends it to the LHC and the HTSC.
- Step 3
- After verifying the certificate of the LHC and the HTSC, it sends the certificate of the HTSC and the HIMC to the LHC.
- Step 4
- After receiving certificates from the HTSC and the HIMC, the LHC verifies them and requests encrypted random number and with a certificate of HTSC and sends policies needed to establish a session key.
- Step 5
- After the decryption with its own certificate, HTSC acquires a random number of the LHC and encrypts its own random number with a certificate of the LHC and sends it. After receiving a random number , the LHC hashes it with its own random number and produces a session key. The session key produced at this time is calculated with values that the HTSC knows. Therefore, it is possible to share the session key.
- Step 6
- In the same manner as Step 4, the HTSC requests random sampling numbers and encrypted with the certificate of the HIMC and sends policies together.
- Step 7
- requested after the decryption of random number with the certificate is sent after it is encrypted with the certificate of the HTSC. After acquiring random number , the HTSC hashes its own random numbers and in connection and produces the session key. Since the HIMC knows the session key produced at this time, it is possible to share the same session key.
- Step 8
- In the same procedure as Step 6, the HIMC requests its own random number encrypted with the certificate of the LHC and random number of the LHC, and sends policies with them.
- Step 9
- After the decryption with its own certificate, the LHS is requested with random numbers and of the HIMC and sends to the HIMC. After receiving , the HIMC hashes in connection with random number and produces the session key.
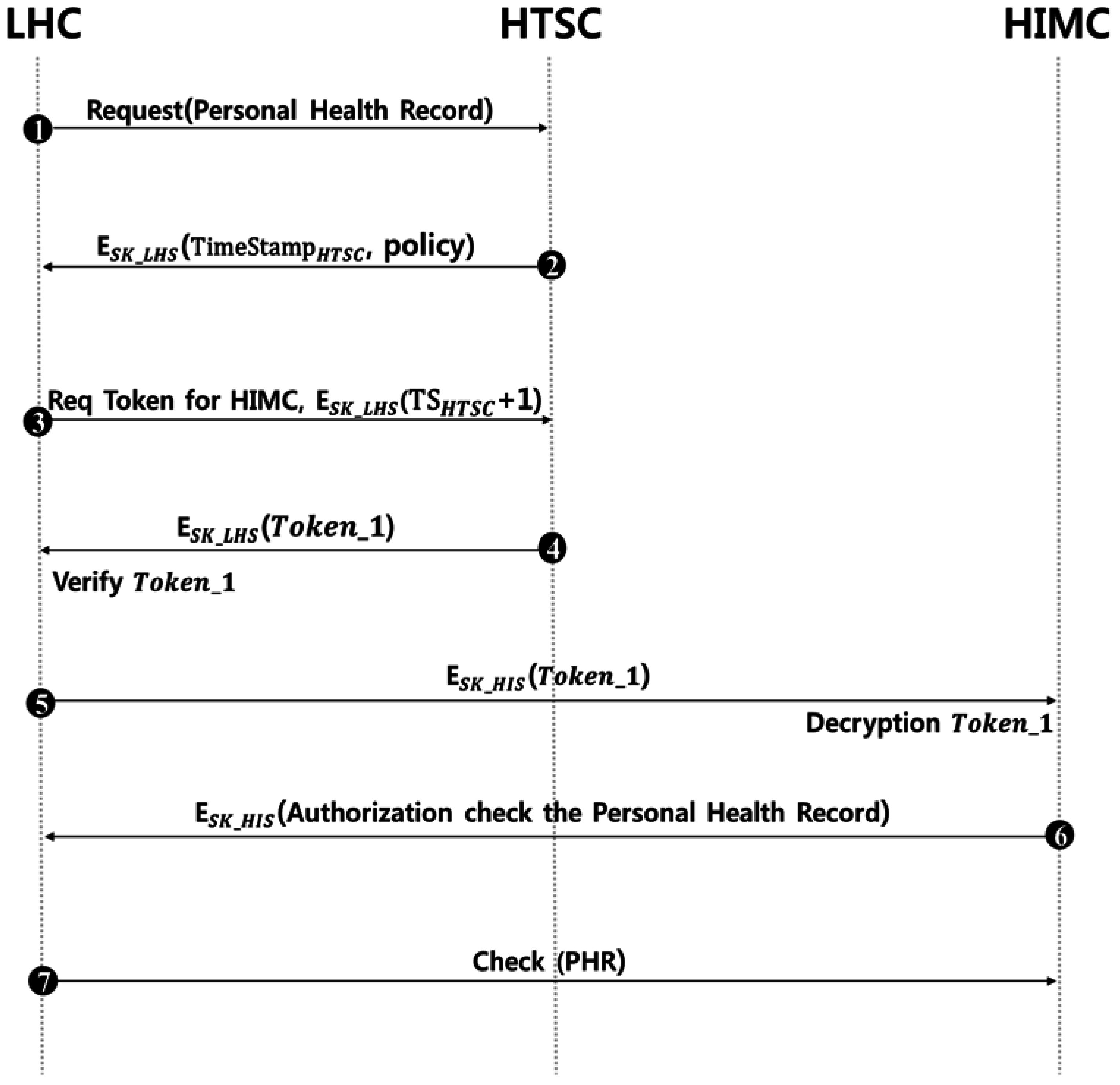
3.2.2. Information Transmission Phase
- Step 1
- The LHC requests a personal healthcare record to the HTSC.
- Step 2
- After requested for information, the HTSC uses SK_LHS, a session key shared in advance with the LHC, and sends encrypted policies to be used in the future in preparation for the replay attack.
- Step 3
- The LHC requests the token of the HIMC from the HTSC. At this time, the value added with 1 from the time stamp is encrypted with SK_LHS and sent together to prevent a replay attack.
- Step 4
- The HTSC sends the token of the HIMC requested with SK_LHS that was shared in advance with the LHC. After receiving the token, the LHC decrypts and verifies it.
- Step 5
- The HIMC proceeds with the decryption of SK_HIS shared in advance and acquires the token from the LHC. Then, the HIMC verifies that it is an authenticated LHC.
- Step 6
- After receiving the token and verifying that it is a valid LHC, the HIMC grants the LHC the authority to confirm the PHR.
- Step 7
- After being granted with authority, the LHC confirms the personal health record.
4. Security and Performance Analysis
4.1. Security Analysis
4.2. Computing Resource Analysis
4.3. Storage Resource Analysis
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Kim, J.-H.; Ahn, S.; Soh, J.; Chung, K. U-Health Platform for Health Management Service Based on Home Health Gateway. In IT Convergence and Security 2012; Springer: Dordrecht, The Netherlands, 2013; pp. 351–356. [Google Scholar]
- Jung, E.-Y.; Kim, J.-H.; Chung, K. Home Health Gateway Based Healthcare Services through U-Health Platform. Wirel. Pers. Commun. 2013, 73, 207–218. [Google Scholar] [CrossRef]
- Touati, F.; Tabish, R. U-Healthcare System: State-of-the-Art Review and Challenges. J. Med. Syst. 2013, 37, 1–20. [Google Scholar] [CrossRef] [PubMed]
- Kang, Y.; Lee, H. A Survey of Security Threats on U-Healthcare. In Proceedings of the Korean Society of Computer Information; Wonkwang Univ.: Iksan-si, Jeollabuk-do, Korea, 2012; Volume 20, pp. 55–58. [Google Scholar]
- Stanford Research Institute. A Trend and Prospect of a Sizeable Market—U-Healthcare, 2010; Stanford Research Institute: Menlo Park, CA, USA, 2010. [Google Scholar]
- Touati, F.; Tabish, R.; Mnaouer, A.B. Towards U-Health: An Indoor 6LoWPAN Based Platform for Real-Time Healthcare Monitoring. In Proceedings of the 2013 6th Joint IFIP Wireless and Mobile Networking Conference (WMNC), Dubai, UAE, 23–25 April 2013.
- Lee, Y.; Jeong, D.; Lee, H. Empirical Analysis of the Reliability of Low-Rate Wireless U-Healthcare Monitoring Applications. Int. J. Commun. Syst. 2013, 26, 505–514. [Google Scholar] [CrossRef]
- Kim, J.; Chung, K. Ontology-Based Healthcare Context Information Model to Implement Ubiquitous Environment. Multimed. Tools Appl. 2014, 71, 873–888. [Google Scholar] [CrossRef]
- Kelly, S.D.T.; Suryadevara, N.K.; Mukhopadhyay, S.C. Towards the Implementation of IoT for Environmental Condition Monitoring in Homes. IEEE Sens. J. 2013, 13, 3846–3853. [Google Scholar] [CrossRef]
- Niewolny, D. How the Internet of Things Is Revolutionizing Healthcare; Healthcare Segment Manager, Freescale Semiconductor: Austin, TX, USA, 2013; pp. 2–6. [Google Scholar]
- Kim, Y.J.; Kim, C.Y.; Shin, Y.J. The Effects of Ubiquitous Healthcare Service on the South Korean Economy: Using Input-Output Analysis. Inf. Syst. Front. 2016, 1–12. [Google Scholar] [CrossRef]
- Jeong, C.; Shin, C.; Joo, S. Construction of Multi-Agent-Based Distributed Framework for Application Services of u-Hospital Information Systems. J. KIISE Comput. Pract. Lett. 2009, 15, 861–865. [Google Scholar]
- Kim, S.; Kim, S.; Jung, J. Design of Operating Room Patients Location System for u-Hospital. J. Korea Soc. Comput. Inf. 2013, 18, 103–110. [Google Scholar] [CrossRef]
- Jang, S.H.; Kim, R.H.; Lee, C.W. Effect of U-Healthcare Service Quality on Usage Intention in A Healthcare Service. Technol. Forecast. Soc. Chang. 2016. [Google Scholar] [CrossRef]
- Lim, S.; Kang, S.M.; Kim, K.M.; Moon, J.H.; Choi, S.H.; Hwang, H.; Jung, H.S.; Park, K.S.; Ryu, J.O.; Jang, H.C. Multifactorial Intervention in Diabetes Care Using Real-Time Monitoring and Tailored Feedback in Type 2 Diabetes. Acta Diabetol. 2016, 53, 189–198. [Google Scholar] [CrossRef] [PubMed]
- Shin, D.; Shin, D.; Shin, D. Ubiquitous Healthcare Platform for Chronic Patients. In Proceedings of the 2016 International Conference on Platform Technology and Service (PlatCon), Jeju, Korea, 15–17 February 2016.
- Nam, I.; Kang, H.; Woo, D.H. Bio-Signal Acquisition Circuit With High Signal-to-Noise Ratio for U-Healthcare System. Electron. Lett. 2014, 50, 1671–1673. [Google Scholar] [CrossRef]
- Fahim, M.; Lee, S.; Yoon, Y. SUPAR: Smartphone as a Ubiquitous Physical Activity Recognizer for U-Healthcare Services. In Proceedings of the 2014 36th Annual International Conference of the IEEE Engineering in Medicine and Biology Society, Chicago, IL, USA, 26–30 August 2014.
- Lee, S.-H.; Lee, D. A Study on Review and Consideration of Medical Industry Convergence Based on U-healthcare. J. Digit. Converg. 2013, 11, 193–197. [Google Scholar]
- Hur, J.-Y.; Lee, K.Y.; Lee, D.H.; Kang, J.J. Design and Development of Smart Monitoring System for U-Healthcare. J. Converg. Cult. Technol. 2015, 1, 107–111. [Google Scholar] [CrossRef]
- Tyagi, R.R.; Lee, K.-D.; Aurzada, F.; Kim, S.; Reisslein, M. Efficient Delivery of Frequent Small Data for U-Healthcare Applications over LTE-Advanced Networks. In Proceedings of the 2nd ACM International Workshop on Pervasive Wireless Healthcare, Hilton Head, SC, USA, 11–14 June 2012; ACM: New York, NY, USA, 2012. [Google Scholar]
- Ryu, G.-T.; Choi, H. Implementation of U-Healthcare System for Chronic Disease Management. J. Inst. Electron. Inf. Eng. 2014, 51, 233–240. [Google Scholar] [CrossRef]
- Lee, S.-C.; Chung, W. A Robust Wearable U-Healthcare Platform in Wireless Sensor Network. J. Commun. Netw. 2014, 16, 465–474. [Google Scholar] [CrossRef]
- Choi, K.; Kim, J. Analysis of the Efficiency of the U-Healthcare Industry. Indian J. Sci. Technol. 2015, 8, 471–481. [Google Scholar] [CrossRef]
- Kim, D.; Kim, S. Design of Key Tree-Based Management Scheme for Healthcare Information Exchange in Convergent U-Healthcare Service. J. Korea Converg. Soc. 2015, 6, 81–86. [Google Scholar] [CrossRef]
- Song, C.-G.; Lee, K.; Ryu, G. Process of the Encryption Key Using a Physical Information in the U-Healthcare Service. J. Digit. Converg. 2014, 12, 573–578. [Google Scholar] [CrossRef]
- Lee, K.-D.; Kim, S.G.; Yi, B.K. Random Access Parameter Control for Reliable U-Healthcare Services with Highly Loaded BAN Traffic. Int. J. Auton. Adapt. Commun. Syst. 2013, 6, 240–252. [Google Scholar] [CrossRef]
- Mtonga, K.; Yang, H.; Yoon, E.; Kim, H. Identity-Based Privacy Preservation Framework over U-Healthcare System. In Multimedia and Ubiquitous Engineering; Springer: Dordrecht, The Netherlands, 2013; pp. 203–210. [Google Scholar]
- Son, J.; Kim, S.; Park, G.; Cha, J.; Park, K. Security Requirements for the Medical Information Used by U-Healthcare Medical Equipment. Int. J. Secur. Appl. 2013, 7, 169–180. [Google Scholar]
- Cho, G.-Y.; Lee, S.; Lee, T. Research on a Solution for Efficient ECG Data Transmission in U-Healthcare Environment. J. Digit. Converg. 2014, 12, 397–403. [Google Scholar] [CrossRef]
- Kim, J.T. Authentication Process between RFID tag and Mobile Agent Under U-healthcare System. Int. J. Bio-Sci. Bio-Technol. 2014, 6, 109–116. [Google Scholar] [CrossRef]
- Sok, Y.; Kim, S. Integrated Medical Information System Implementation for the U-Healthcare Service Environment. J. Korea Contents Assoc. 2014, 14, 1–7. [Google Scholar] [CrossRef]
- Jung, Y.-S. Implementation Plan of Integrated Medical Information System for Ubiquitous Healthcare Service. J. Korea Ind. Inf. Syst. Soc. 2010, 15, 115–126. [Google Scholar]
- Shin, M.S.; Jeon, H.S.; Ju, Y.W.; Lee, B.J.; Jeong, S. Constructing RBAC Based Security Model in U-Healthcare Service Platform, Hindawi Publishing Corporation. Sci. World J. 2015, 2015, 1–13. [Google Scholar] [CrossRef] [PubMed]
- Jeong, Y.; Lee, S. A Study of Patient’s Privacy Protection in U-Healthcare. J. Korea Inst. Inf. Secur. Cryptol. 2012, 22, 913–921. [Google Scholar]
- Conejar, R.J.; Bae, J.; Kim, H. A Study of an IP-based Mobile U-Healthcare System. Adv. Sci. Technol. Lett. 2015, 97, 120–124. [Google Scholar]
- Bang, G.H.; Lee, D.J.C.D.K. Monitoring Human Blood Pressure for U-Healthcare Using ISO/IEEE PHD Standard. In Proceedings of the Fourth International Conference on Digital Information Processing and Communications (ICDIPC2014), Kuala Lumpur, Malaysia, 18–20 March 2014.
- Bravo Santisteban, R.D.; Youm, S.; Park, S. U-Healthcare Center Service in Busan City, South Korea: An Empirical Analysis and the Results of 1 Year of Service. Telemed. e-Health 2015, 21, 774–781. [Google Scholar] [CrossRef] [PubMed]
- Conejar, R.J.; Kim, H. Proposed Architecture for U-Healthcare Systems. Int. J. Softw. Eng. Appl. 2015, 9, 213–218. [Google Scholar] [CrossRef]
- Yang, Y.; Kim, M. Analysis of User Requirement on U-Healthcare System. Int. J. Bus. Tour. Appl. Sci. 2013, 1, 1–10. [Google Scholar]


| Notation | Meaning |
|---|---|
| Req | Request |
| Resp | Response |
| LHC | Local Healthcare Center |
| HTSC | Healthcare Trusted Service Center |
| HIMC | Healthcare Information Management Center |
| Cert | Cerificate |
| R[] | Random Number |
| Pri | Private Key |
| Pub | Public Key |
| E() | Encryption |
| D() | Decryption |
| SK | Session Key |
| TS | Time Stamp |
| H | Hash Function |
| Verify() | Verification |
| PHR | Personal Health Record |
| Security requirment | Yun-Yong Sok [32] | Yong Sik Jung [33] | Moon Sun Shin [34] | Yoon-Su Jeong [35] | Proposed Scheme |
|---|---|---|---|---|---|
| Certification | X | X | X | X | O |
| Encryption | X | X | O | O | O |
| Security | X | X | Δ | O | O |
| Privacy | X | X | O | O | O |
| Eavesdropping | X | X | O | O | O |
| Forward Security | X | X | O | X | O |
| Authentication | X | X | O | O | O |
| Relay Attack | X | X | X | X | O |
| Denial-of-Service Attck | X | X | X | O | O |
| Operation | LHC | HTSC | HIMC |
|---|---|---|---|
| Hash | 1 | 1 | 1 |
| Encryption | 4 | 4 | 3 |
| Decryption | 5 | 3 | 3 |
| Session key generation | 2 | 2 | 2 |
| Nonce generation | 2 | 2 | 2 |
| Token generation | - | 1 | - |
| Operation | LHC | HTSC | HIMC |
|---|---|---|---|
| Random value | 2 | 2 | 2 |
| Certificate | 3 | 3 | 3 |
| Session key | 2 | 2 | 2 |
| Timestamp | 2 | 2 | - |
| Token | 1 | 1 | 1 |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kang, J.; Chung, H.; Lee, J.; Park, J.H. The Design and Analysis of a Secure Personal Healthcare System Based on Certificates. Symmetry 2016, 8, 129. https://doi.org/10.3390/sym8110129
Kang J, Chung H, Lee J, Park JH. The Design and Analysis of a Secure Personal Healthcare System Based on Certificates. Symmetry. 2016; 8(11):129. https://doi.org/10.3390/sym8110129
Chicago/Turabian StyleKang, Jungho, Hague Chung, Jeongkyu Lee, and Jong Hyuk Park. 2016. "The Design and Analysis of a Secure Personal Healthcare System Based on Certificates" Symmetry 8, no. 11: 129. https://doi.org/10.3390/sym8110129






