BlendCAC: A Smart Contract Enabled Decentralized Capability-Based Access Control Mechanism for the IoT
Abstract
:1. Introduction
- Scalability: The fast growing number of devices and services also pose increasing management overload in access control systems that are based on ACL or RBAC models. Access control strategies are expected to be able to handle the scalability problem resulting from the distributed IoT networks.
- Heterogeneity: IoT systems normally integrate heterogeneous cyber physical objects with variant underlying technologies or in different application domains, and each domain or platform has its own specific requirements for identity authentication and authorization policy enforcement. Both RBAC and ABAC have been found to be inflexible in providing complex arrangements to support delegation and transitivity which are essential for efficient and effective intra-domain authorization and access control.
- Spontaneity: Traditional RBAC and ABAC systems envisage planned and long-lived patterns, while the IoT world is mainly characterized by short-lived, often casual and/or spontaneous interactions [5], in which an access control scheme is required to deal with dynamic challenges.
- Interoperability: IoT devices are usually resource-constrained and cannot support heavy computational and large storage-required applications. Smart devices connect to each other by low power and lossy networks. Consequently, the access control protocol should be lightweight and not impose significant overhead on devices and communication networks.
- By leveraging the blockchain protocol, a decentralized, federate access control scheme is proposed, which is a scalable, fine-grained, and lightweight solution for today’s IoT networks;
- A complete architecture of a federated capability-based authorization system is designed, which includes delegation authority, capability management, and access right validation;
- A capability-based federated delegation model is introduced, and the enforcement of polices is discussed in detail;
- A concept-proof prototype based on smart contracts is implemented on resource-constrained edge devices and more powerful devices and is deployed on a local private blockchain network; and
- A comprehensive experimental study is conducted that compares the proposed scheme with the well-known RBAC and ABAC models. The experimental results validate the feasibility of the BlendCAC approach in IoT environments without introducing significant overhead.
2. Background Knowledge and Related Work
2.1. Access Control Model in IoTs
2.2. Decentralized Access Control Mechanism for IoTs
2.3. Blockchain and Smart Contract
3. Federated Capability-Based Delegation and Revocation Model
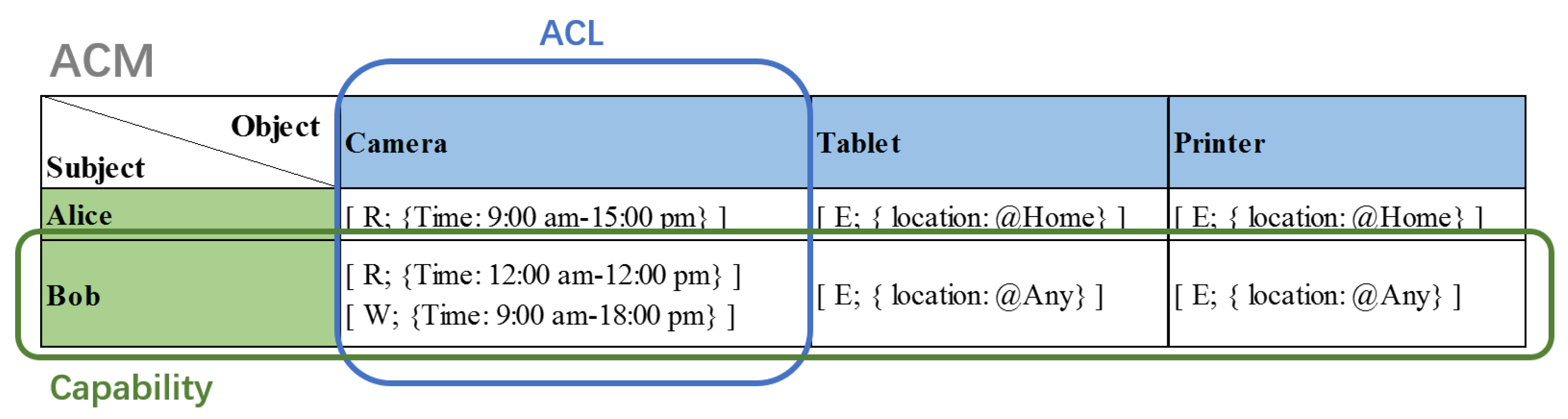
3.1. Capability Access Control Model
- The is a human being or device who applies for access right and interacts with the authorized service and resources on the service provider.
- An is an entity who works as a service provider to offer services or resources for authorized subjects, such as a printer, NetCam or sensor.
- An is an action that can be carried out by authorized subjects to access service or resource on a target object, such as read, write or execute.
- A is a set of attributes that defines an executable condition of an operation given a specific context or scenario, like time or location.
- is a access right which defines a one-to-many relation assignment by combining operation and constraints.
- S, O and P are sets of subjects, objects and permissions.
- is the internal capability which defines a one-to-many relationship assignment between an object and permissions.
- is the external capability which specifies a one-to-many relationship assignment by associating a subject with a subset of internal capabilities.
3.2. Federated Capability-Based Delegation Model
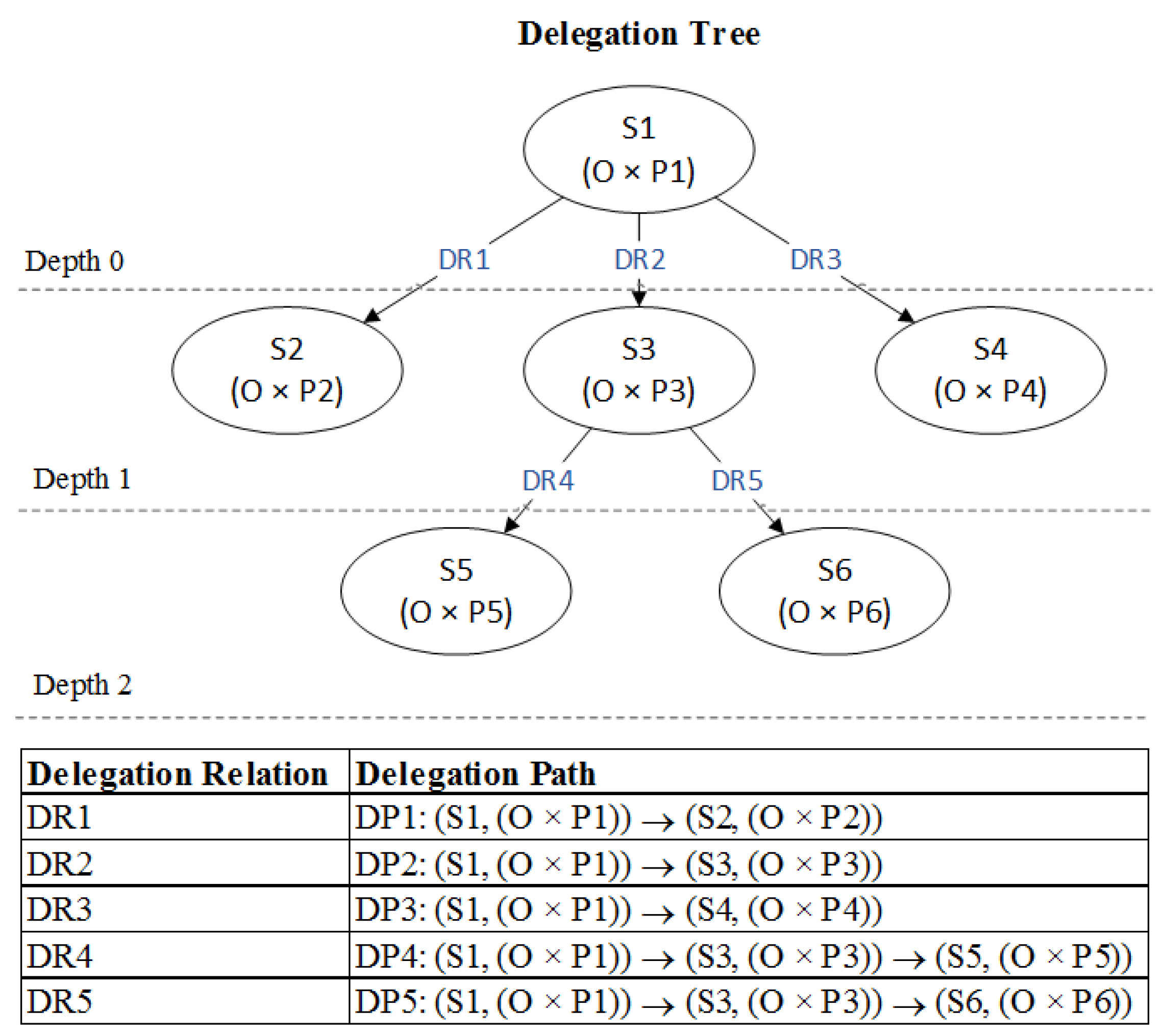
- is the one-to-many delegation relationship. A delegation relationship can be represented by , where P2⪯P1. It indicates that subject S1 delegates subset of P1 to subject S2 as P2.
- is an ordered list of delegation relationships indicating a delegation path.
- is a delegation relationship hierarchy representing a delegation tree.
- is a natural number representing the maximum delegation depth.
- : is a function that maps a node to another parent node in the delegation tree.
- : is a function that maps an node to a delegation path. Path() = {}
- : is a function that returns a delegation depth in delegation tree given node, where N is a natural number set representing the delegation depth.
3.3. Capability-Based Delegation Authorization
- are sets of capability, subject and conditions for the authorization and maximum delegation depth, respectively.
- .
3.4. Capability-Based Delegation Revocation
- are sets of capability, subject and ancestor function, respectively.
- .
4. BlendCAC: A BLockchain-ENabled Decentralized Federated CapAC System
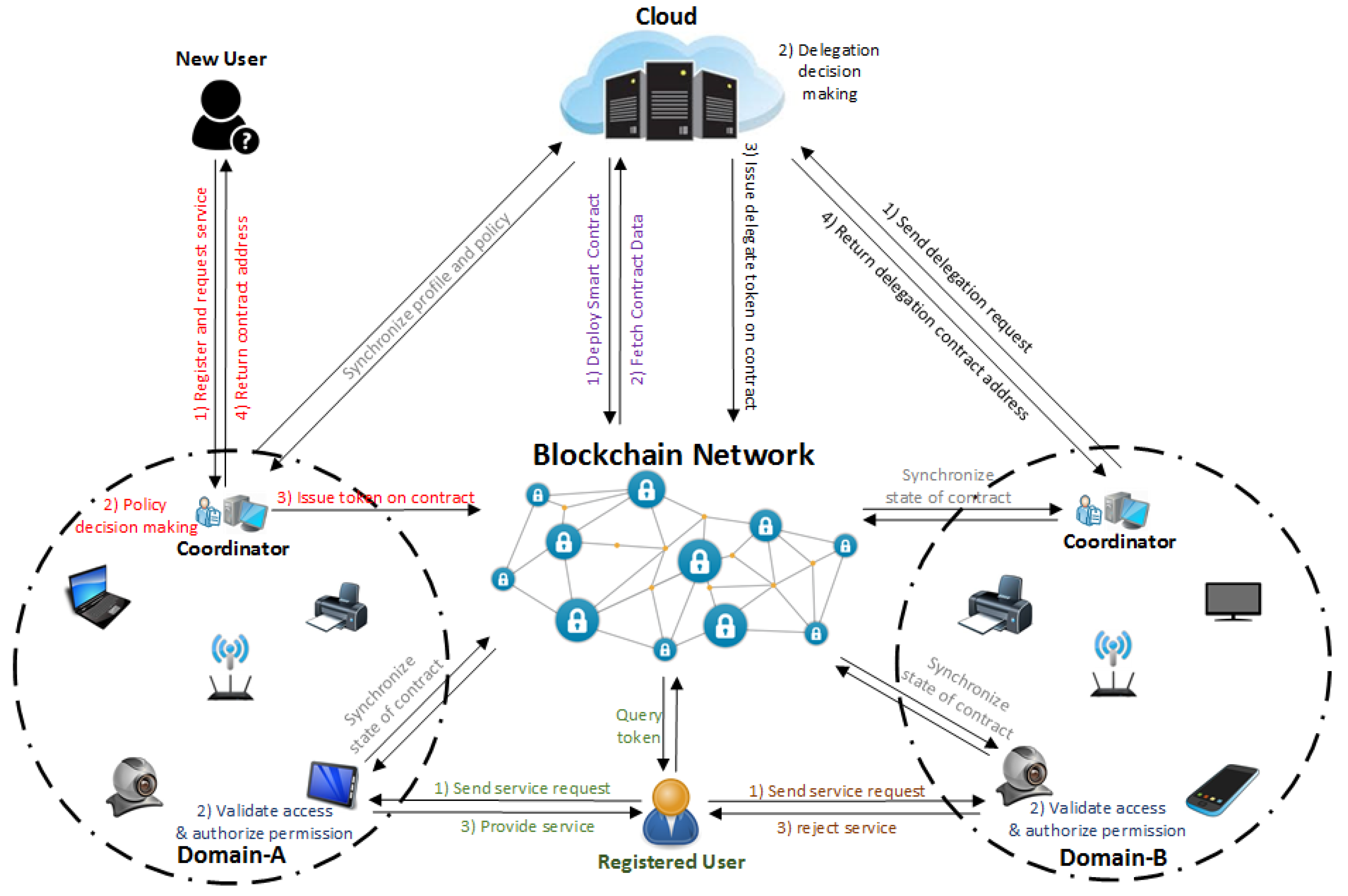
4.1. System Architecture of BlendCAC
- Registration: All entities must create at least one main account defined by a pair of keys to join the blockchain network. Each account is uniquely indexed by its address that is derived from his/her own public key. This account address is ideal for identity authentication in the BlendCAC system given the assumption that the authentication process is ensured by a blockchain network. In our scenario, the identity authentication account addresses used are Virtual Identities (VIDs) which are recored in profile database, and identity management is deployed on two levels: the cloud and the coordinator. The cloud server maintains a global profile database, and the domain coordinator maintains a local profile database, and regular synchronization between the cloud server and domain coordinator ensures data consistency. New users can either send a registration request to the cloud or to the delegated coordinator. Once the identity information related to users or IoT devices is verified, the profile of each registered entity is created using his/her account address in the blockchain for the authentication process when an access right request happens. As a result, the domain coordinators are able to enforce delegated authorization policies and perform decision-making to directly control their own devices or resources instead of depending on third parties.
- Smart Contract Deployment: A smart contract that manages the federated delegation relationship and capability tokens must be developed and deployed on the blockchain network by the policy owner. In our framework, the cloud acts as the data and policy owner which can deploy smart contracts encapsulating delegation and CapAC tokens. After a smart contract has been deployed successfully on the blockchain network, it becomes visible to the whole network owing to the transparency and publicity properties of the blockchain, which means that all participants in the blockchain network can access transactions and smart contracts recorded in chain data. Thanks to cryptographic and security mechanisms provided by the blockchain network, the smart contract can secure any algorithmically specifiable protocols and relationships from malicious interference by third parties under trustless network environment. After synchronizing the blockchain data, all nodes can access all transactions and recent states of each smart contract by referring to local chain data. Each node interacts with the smart contract through the provided contract address and the Remote Procedure Call (RPC) interface.
- Federated Delegation: The PDC service at the cloud server is responsible for delegation policy definition and access right authorization enforcement. To reduce the overhead of the centralized cloud server and meet the scalability and heterogeneity requirements in each IoT domain, the domain coordinator delegates part of the policy decision making tasks and carries out domain specified authorization rules based on domain-specified policies. After receiving a delegation request from a coordinator candidate and executing a policy decision making task to delegate permissions to the coordinator, the PDC service on the cloud launches a transaction to issue a delegation certificate to the smart contract. Finally, the federated delegation relationship is established between the cloud server and the coordinator, and profile and policy data synchronization between the cloud and coordinator is periodically carried out to ensure data consistency on both sides.
- Capability Authorization: To successfully access services or resources at service providers, an entity initially sends an access right request to the domain coordinator to get a capability token. Given the registered entity information established in the profile database, a delegated policy decision making module running on the domain coordinator evaluates the access request by enforcing the delegated authorization policies. If the access request is granted, the domain coordinator issues the capability token encoding the access right and then launches a transaction to update the token data in the smart contract. After the transaction has been approved and recorded in a new block, the domain coordinator notifies the entity with a smart contract address for the querying token data. Otherwise, the access right request is rejected.
- Access Right Validation: The authorization validation process is performed at the object that works as the local service provider after receiving a service request from the subject. Through regularly synchronizing the local chain data with the blockchain network, a service provider just simply checks the current state of the contract in the local chain to get a capability token associated with the entity’s address. To determine the capability token validation and access authorization process result, if the access right policies and conditional constraints are satisfied, the service provider grants the access request and offers services to the requester. Otherwise, the service request is denied.
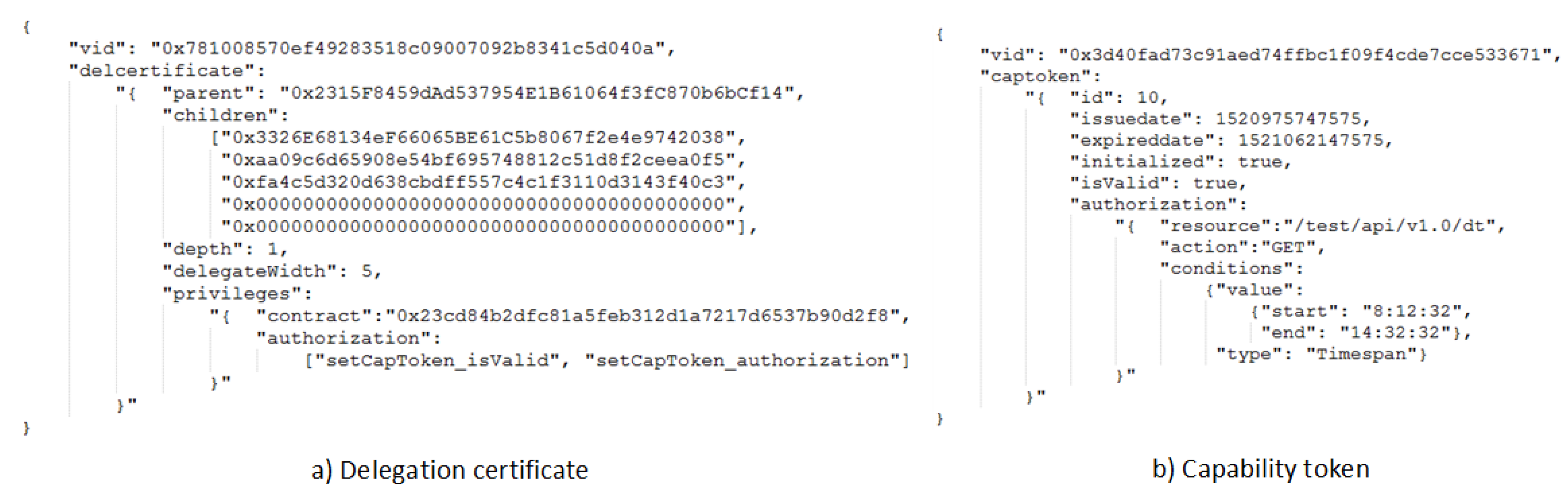
4.2. Capability Token Structure
- f: a one-way hash mapping function to establish relationship between the subject and authorized internal capability set;
- : the virtual ID of a subject that requests an access to a service or resource;
- : the virtual ID of an object that provides a service or resource;
- : a set of authorized operations, e.g., read, write and execute; and
- C: a set of context awareness information, such as time or location.
4.3. Delegation Certificate Structure
- f: a one-way hash mapping function to establish the relationship between a subject and a delegated permission set;
- : the Virtual ID of a subject who is the owner of the delegation token;
- : the Virtual ID of a parent subject that delegates the token to ;
- : a set of Virtual IDs of child subjects that records the delegated nodes;
- D: a natural number that indicates the current depth in the delegation tree;
- W: a natural number that defines the maximum delegation width to limit delegable child nodes in ; and
- : a set of delegated permissions for actions, e.g., authorize capability token.
- f: a one-way hash mapping function to establish a relationship between a subject and a delegation tree;
- : the Virtual ID of a subject who is the owner of the delegation tree;
- : a natural number that defines the maximum delegation depth; and
- : a delegation certificate that indicates the root node of the delegation tree.
4.4. Federated Delegation Mechanism
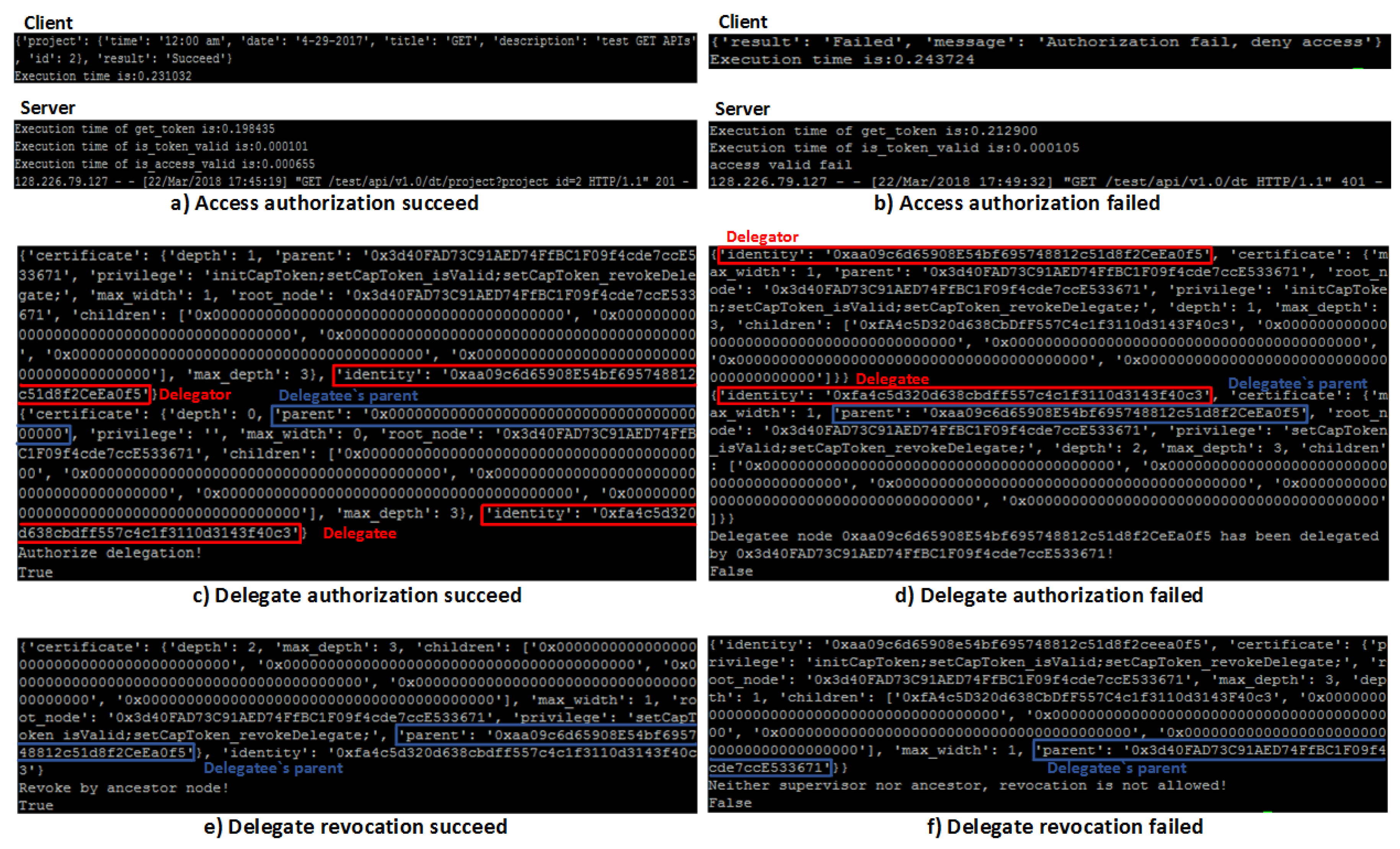
- Request Authentication: The delegatee sends a delegation request to the delegator to ask for the . On receiving the request from the delegator, the DAC verifies the identity of delegatee by referring to the identity management service. If the delegatee’s identity is valid, the identity management service returns a Virtual ID (VID) of the delegatee to the DAC. Then, the DAC sends back the authentication result to the delegator. Otherwise, the DAC rejects the delegation request by returning a failure notification.
- Delegation Authorization: After receiving the verification result from the DAC, the delegator is capable of assigning delegable permissions to trusted delegatees given pre-defined delegation policies. In our proposal, the federated delegation mechanism is implemented by modifying the delegation certificate, , to assign the delegated permissions or to change the delegation relationship. As the smart contract has received an updated DC transaction from the delegator, it checks the delegator’s to validate the delegation right. If the delegation status can match the relationship, the delegator can delegate a subset of his/her delegated permissions to the delegatee entity by modifying delegatee’s and appending the delegatee’s address to the delegator’s child node set, , to set up the delegation relationship. Otherwise, the capability delegation request is rejected.
- Delegation Revocation: The delegation revocation considers two scenarios: delegated permission P revocation and delegation certificate revocation. According to the revocation mechanism defined in FCDM, only entities who meet the relationship can carry out revocation operations over a smart contract. In the delegated permission revocation process, the delegator can nullify part of the assigned permissions by simply removing access right elements from in the delegatee’s . In the case of revocation, through cascading, all subsequent delegate relationships are removed from the . By starting from the delegator and destructing the delegatee’s , the delegator can tear down all delegation relationships that are associated with delegatee, including those assigned by the delegatee.
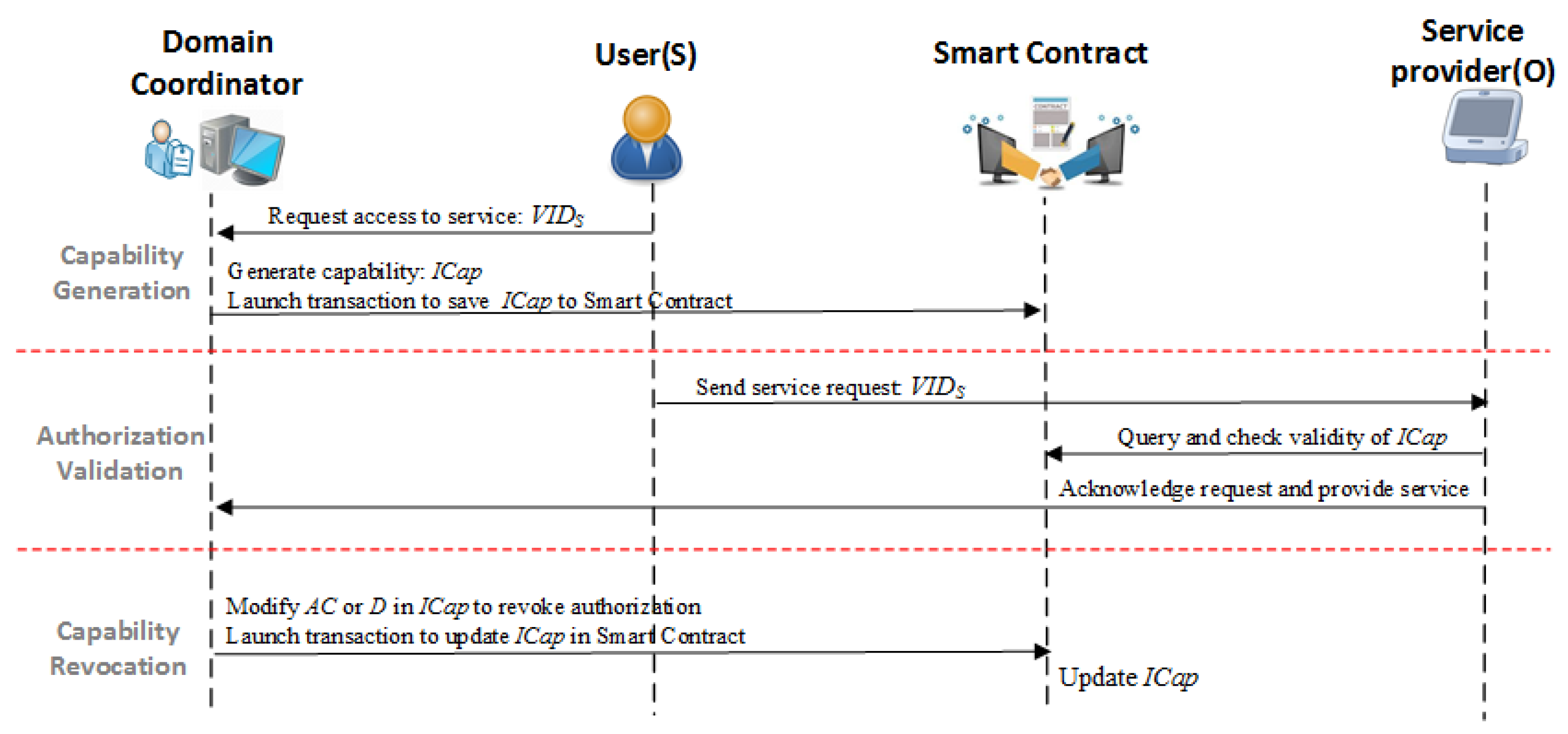
4.5. Capability-Based Access Right Authorization
- Capability Generation: As one type of meta data that represents the access rights, the capability, , can be generated by associating a VID with an AR; thus, the has the identified property to prevent forgery. After receiving an access request from a user, the domain coordinator generates a capability token based on the delegated access right authorization policy, and launches transactions to save a new token data to a smart contract. A large number of ’s are grouped into the capability pools on the smart contract which can be proofed and synchronized among the nodes across the blockchain network.
- Access Right Validation: After receiving the service request from a subject, the service provider first fetches the capability token from the smart contract using the subject’s address and then makes decisions on whether or not to grant an access to the service according to the local access control policy. Implementing access right validation at the local service provider allows smart objects to be involved in the AC decision making tasks, which provides a flexible and fine-grained AC service in IoT networks.
- Capability Revocation: The capability revocation considers two scenarios: partial access right revocation and revocation. In our proposal, only the entities with delegated capability management permissions are allowed to perform revocation operations on capability tokenized smart contracts. In the partial access right revocation process, the delegated entities can remove part of the entries from to revoke the selected access rights. In cases of revocation, through directly clearing the in , the whole capability token becomes unavailable to all associated entities.
5. Prototype Design
5.1. Delegation Certificate and Capability Token Structure
- : a 20-byte value to represent the address of certificate owner in the blockchain network;
- : a 20-byte value to represent the address of the parent entity in the blockchain network;
- : a queue to record all address of delegated entities;
- : a natural number to indicate the depth of the current delegation certificate in the delegation tree;
- : a natural number to constrain horizontal delegation times;
- : a set of delegated access rights that the delegator has assigned to the delegatee, including
- -
- : a 20-byte value to indicate the address of the delegated smart contract; and
- -
- : a set of delegated functions for which the operations are granted.
- : a 20-byte value to represent the address of the capability owner in the blockchain network;
- : the auto-incremented prime key to identify a capability token;
- : a bool flag used for checking the token’s initialized status;
- : a bool flag signifying the enabled status to show whether a token is valid or not;
- : to identify the date and time when the token was issued;
- : the date and time when the token becomes expired;
- : a set of access right rules that the issuer has granted to the subject, including
- -
- : to identify a specific granted operation over a resource;
- -
- : the resource in the service provider for which the operation is granted. In this case, the resource is defined as granted REST-ful API; and
- -
- : a set of conditions which must be fulfilled locally on the service provider to grant the corresponding operation.
5.2. Federated Delegation Policy Service
| Algorithm 1 Authorize Delegation. | |
| Require:, , | |
| 1: | |
| 2: | |
| 3: | |
| 4: | if == then |
| 5: | |
| 6: | end if |
| 7: | ifthen |
| 8: | |
| 9: | end if |
| 10: | ifthen |
| 11: | |
| 12: | end if |
| 13: | ifthen |
| 14: | |
| 15: | end if |
| 16: | ifthen |
| 17: | for in do |
| 18: | if in then |
| 19: | |
| 20: | end if |
| 21: | end for |
| 22: | else |
| 23: | |
| 24: | for in do |
| 25: | if in then |
| 26: | |
| 27: | end if |
| 28: | end for |
| 29: | end if |
| 30: | if == Empty then |
| 31: | |
| 32: | end if |
| 33: | |
| 34: | |
| 35: | |
| 36: | |
| Algorithm 2 Revoke Delegation. | |
| Require: | |
| 1: | |
| 2: | |
| 3: | ifthen |
| 4: | if then |
| 5: | |
| 6: | else |
| 7: | |
| 8: | end if |
| 9: | else |
| 10: | if then |
| 11: | |
| 12: | end if |
| 13: | if and then |
| 14: | |
| 15: | end if |
| 16: | |
| 17: | end if |
| 18: | |
5.3. Access Authorization Service
- Check cached token data: After receiving a service request from a user, the service provider firstly checks whether or not the token data associated with the user’s address exists in the local database. If the search for token data fails, the service provider can fetch the token data from the smart contract by calling an exposed contract method and saving the token data to the local database. Otherwise, the token data is directly reloaded from the local token database for further validation processes. The service provider regularly synchronizes the local database with the smart contract to ensure token data consistency.
- Verify token status: As a capability token has been converted to JSON data, the first step of token validation is checking the current capability status of the token, such as the initialized, isValid, issuedate, and expireddate functions. If any status of a token is not valid, the authorization process stops and a deny access request is sent back to the subject.
- Check whether access is granted or not: The service provider goes through all access rules in the access right set to guarantee that the request operation is permitted. The process checks whether or not the REST-ful method used by the requester matches the authorized action of current access rules and that the value of resource field is the same as the Request-Uniform Resource Identifiers (URI) option used by the requester. If the current access rule verification fails, the process skips to the next access rule for evaluation. If none of the access rules successfully pass the verification process, the authorization validation process stops and the access request is denied.
- Verify the conditions: Even though the action on a target resource is permitted after the access validation, it is necessary to evaluate the context-awareness constraints on the local device by verifying whether or not the specified conditions in the token are satisfied. The condition verification process goes through all constraints in the condition set to find the matched ones. If no condition is fulfilled in the given local environment, the access right validation process stops and the access request is denied.
6. Experiment and Evaluation
6.1. Testbed Setup
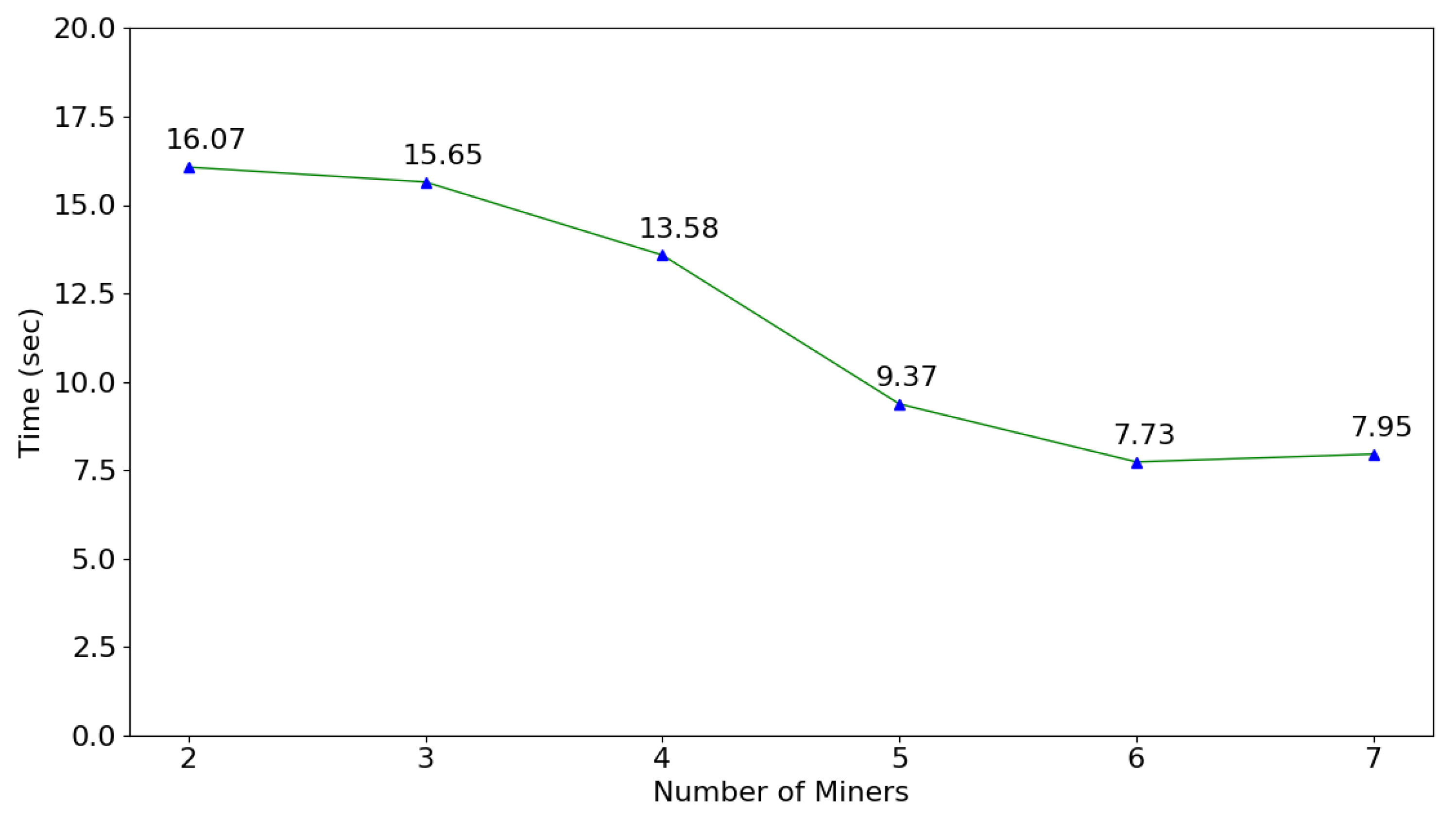
6.2. Experimental Results
6.3. Performance Evaluation
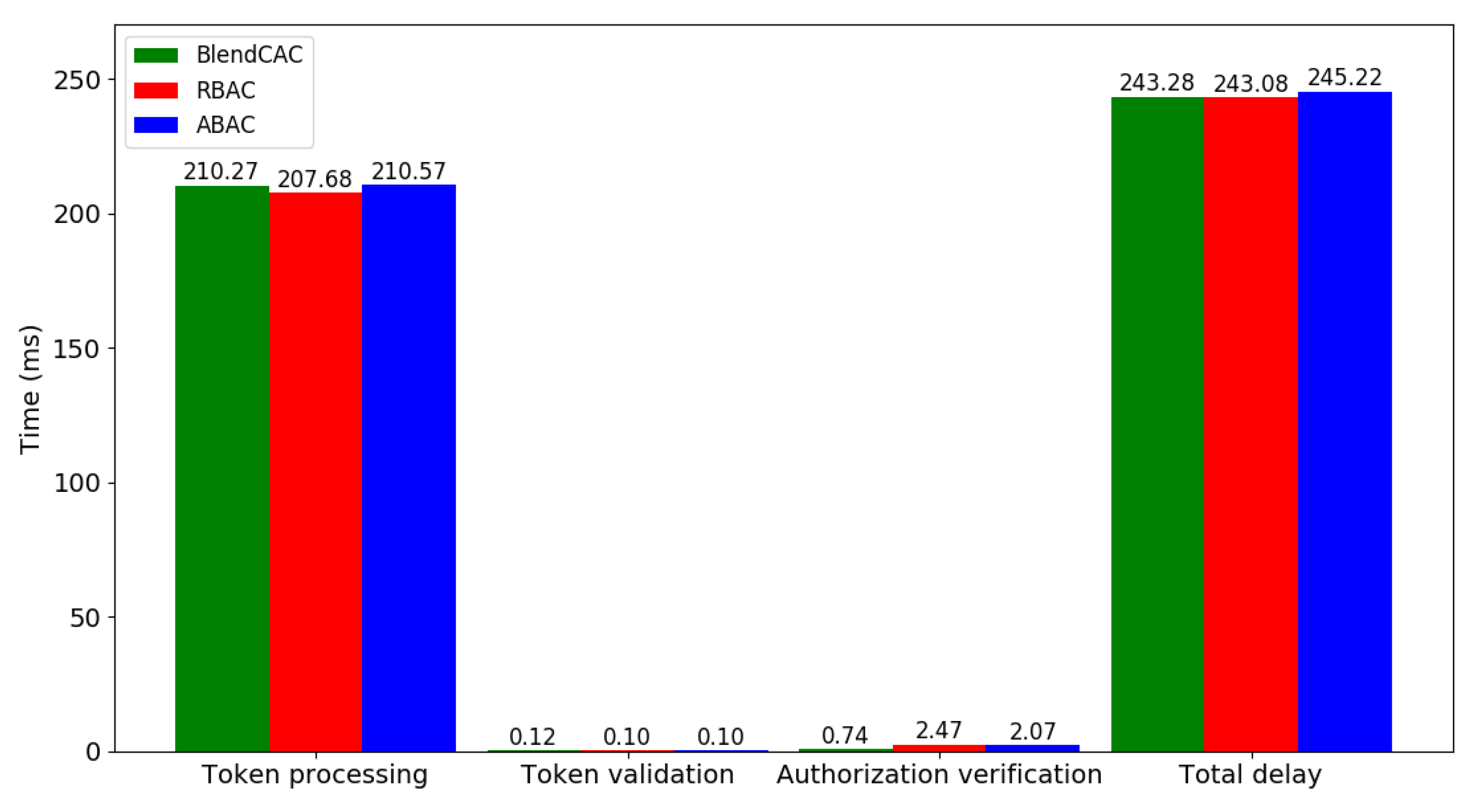
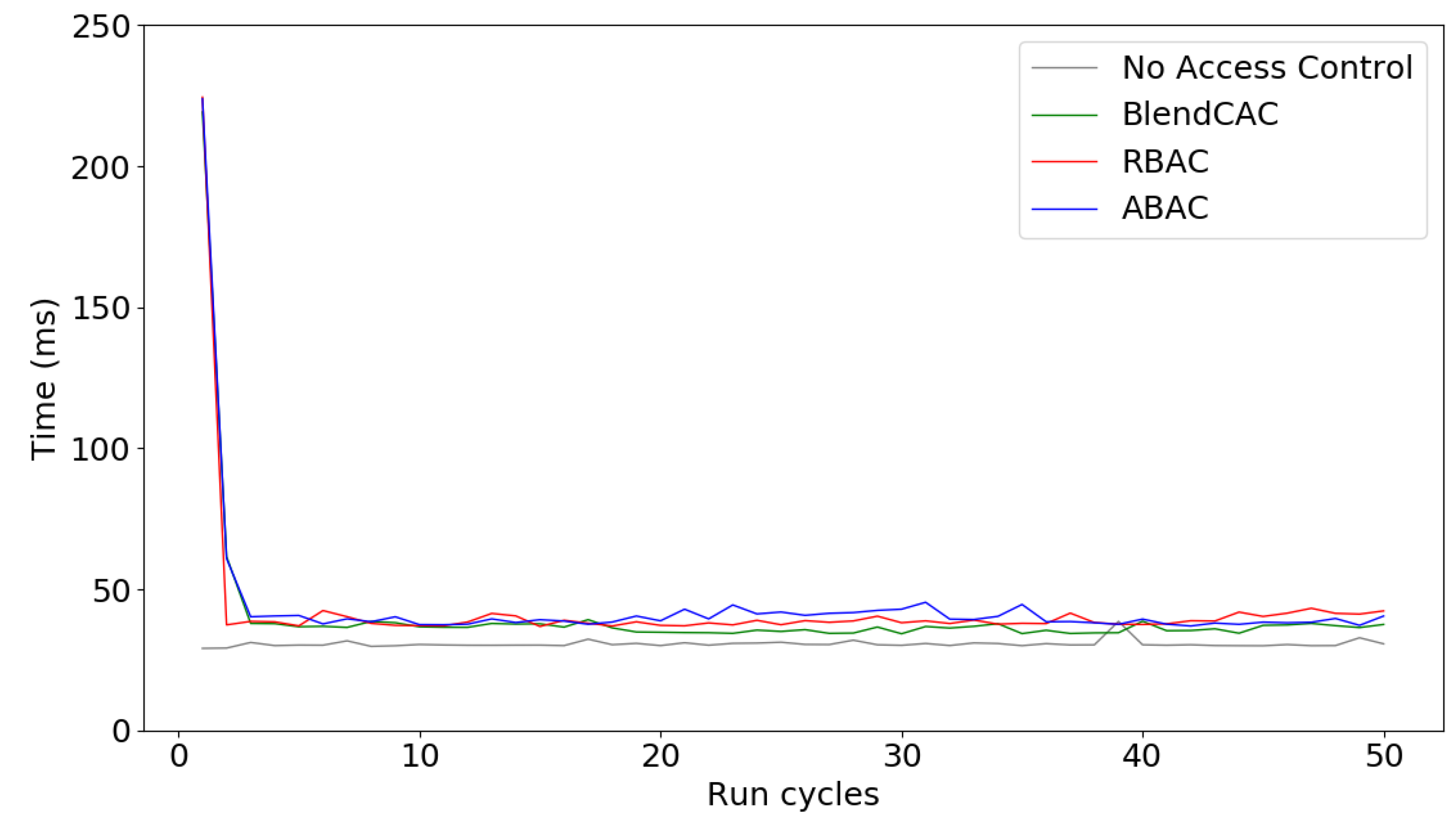
6.3.1. Computational Overhead
6.3.2. Communication Overhead
6.3.3. Processing Overhead
6.4. Discussion
- Load balance: The BlendCAC framework takes advantage of a delegation mechanism to distribute the load of the centralized PDC server to separate local domain coordinators, such that the bottleneck effect of PDC is mitigated and the risk of malfunction resulting from centralized system is reduced. Even in the worst case when the PDC crashes for a short period of time, a large number of domain coordinators still work normally on behalf of the PDC to provide services;
- Decentralized authorization: By leveraging the blockchain technique, the proposed BlendCAC scheme allows users to control their devices and resources without depending on a third centralized authority to establish the trust relationship with unknown nodes; instead, it can define a domain-specific access authorization policy which is meaningful to distributive, scalable, heterogeneous and dynamic IoT-based applications;
- Edge computing-driven intelligence: Thanks to the federated delegation mechanism and blockchain technology, the BlendCAC framework provides a device-driven access control strategy that is suitable for the distributed nature of the IoT environment. Through transferring power and intelligence from the centralized cloud server to the edge of the network, the risk of performance bottleneck and single point of failure are mitigated, and smart things are capable of protecting their own resources and privacy by enforcing a user-defined security mechanism;
- Fine granularity: Enforcing access right validation to local service providers empowers smart devices to decide whether or not to grant access to certain services according to local environmental conditions. Fine-grained access control with a lease privilege access principle prevents privilege escalation, even if an attacker steals the capability token;
- Lightweight: Compared to XML-based language for access control, such as XACML, JSON is a lightweight technology that is suitable for resource-constrained platforms. Given the experimental results, our JSON based capability token structure introduces a small overhead on the general performance.
7. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| ABAC | Attribute-based Access Control |
| AC | Access Control |
| ACL | Access Control List |
| ACM | Access Control Matrix |
| BlendCAC | BLockchain-ENabled Decentralized Federated Capability-based Access Control |
| CAC/CapAC | Capability-based Access Control |
| FCDM | Federated Capability-based Delegation Model |
| IoT | Internet of Things |
| RBAC | Role-based Access Control |
| RTT | Round Trip Time |
| QoS | Quality of Service |
References
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Snidaro, L.; Garcia-Herrera, J.; Llinas, J.; Blasch, E. Context-Enhanced Information Fusion; Springer: Berlin, Germany, 2016. [Google Scholar]
- Blasch, E.; Kadar, I.; Grewe, L.L.; Brooks, R.; Yu, W.; Kwasinski, A.; Thomopoulos, S.; Salerno, J.; Qi, H. Panel summary of cyber-physical systems (CPS) and Internet of Things (IoT) opportunities with information fusion. In Proceedings of the International Society for Optics and Photonics, Signal Processing, Sensor/Information Fusion, and Target Recognition XXVI, Anaheim, CA, USA, 11–12 April 2017; Volume 10200, p. 102000O. [Google Scholar]
- Alaba, F.A.; Othman, M.; Hashem, I.A.T.; Alotaibi, F. Internet of Things security: A survey. J. Netw. Comput. Appl. 2017, 88, 10–28. [Google Scholar] [CrossRef]
- Gusmeroli, S.; Piccione, S.; Rotondi, D. A capability-based security approach to manage access control in the internet of things. Math. Comput. Model. 2013, 58, 1189–1205. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 12 July 2018).
- Crosby, M.; Pattanayak, P.; Verma, S.; Kalyanaraman, V. Blockchain technology: Beyond bitcoin. Appl. Innov. 2016, 2, 6–10. [Google Scholar]
- Ouaddah, A.; Mousannif, H.; Elkalam, A.A.; Ouahman, A.A. Access control in the Internet of things: Big challenges and new opportunities. Comput. Netw. 2017, 112, 237–262. [Google Scholar] [CrossRef]
- Gong, L. A secure identity-based capability system. In Proceedings of the 1989 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 1–3 May 1989; pp. 56–63. [Google Scholar]
- Sandhu, R.S.; Coyne, E.J.; Feinstein, H.L.; Youman, C.E. Role-based access control models. Computer 1996, 29, 38–47. [Google Scholar] [CrossRef] [Green Version]
- Samarati, P.; de Vimercati, S.C. Access control: Policies, models, and mechanisms. In International School on Foundations of Security Analysis and Design; Springer: Berlin/Heidelberg, Germany, 2000; pp. 137–196. [Google Scholar]
- De Souza, L.M.S.; Spiess, P.; Guinard, D.; Köhler, M.; Karnouskos, S.; Savio, D. Socrades: A web service based shop floor integration infrastructure. In The Internet of Things; Springer: Berlin/Heidelberg, Germany, 2008; pp. 50–67. [Google Scholar]
- Spiess, P.; Karnouskos, S.; Guinard, D.; Savio, D.; Baecker, O.; De Souza, L.M.S.; Trifa, V. SOA-based integration of the internet of things in enterprise services. In Proceedings of the 2009 IEEE International Conference on Web Services, Los Angeles, CA, USA, 6–10 July 2009; pp. 968–975. [Google Scholar]
- Zhang, G.; Tian, J. An extended role based access control model for the Internet of Things. In Proceedings of the 2010 International Conference on Information Networking and Automation (ICINA), Kunming, China, 18–19 October 2010; Volume 1, pp. V1-319–V1-323. [Google Scholar]
- Yuan, E.; Tong, J. Attributed based access control (ABAC) for web services. In Proceedings of the 2005 IEEE International Conference on Web Services (ICWS 2005), Orlando, FL, USA, 11–15 July 2005. [Google Scholar]
- Smari, W.W.; Clemente, P.; Lalande, J.F. An extended attribute based access control model with trust and privacy: Application to a collaborative crisis management system. Future Gener. Comput. Syst. 2014, 31, 147–168. [Google Scholar] [CrossRef]
- Ye, N.; Zhu, Y.; Wang, R.C.; Malekian, R.; Qiao-min, L. An efficient authentication and access control scheme for perception layer of internet of things. Appl. Math. Inf. Sci. 2014, 8, 1617–1624. [Google Scholar] [CrossRef]
- Liu, B.; Chen, Y.; Hadiks, A.; Blasch, E.; Aved, A.; Shen, D.; Chen, G. Information fusion in a cloud computing era: A systems-level perspective. IEEE Aerosp. Electron. Syst. Mag. 2014, 29, 16–24. [Google Scholar] [CrossRef]
- Gusmeroli, S.; Piccione, S.; Rotondi, D. IoT@ Work automation middleware system design and architecture. In Proceedings of the 2012 IEEE 17th Conference on Emerging Technologies & Factory Automation (ETFA), Krakow, Poland, 17–21 September 2012; pp. 1–8. [Google Scholar]
- Anggorojati, B.; Mahalle, P.N.; Prasad, N.R.; Prasad, R. Capability-based access control delegation model on the federated IoT network. In Proceedings of the 2012 15th International Symposium on Wireless Personal Multimedia Communications (WPMC), Taipei, Taiwan, 24–27 September 2012; pp. 604–608. [Google Scholar]
- Skinner, G.D. Cyber security management of access controls in digital ecosystems and distributed environments. In Proceedings of the 6th International Conference on Information Technology and Applications (ICITA 2009), Hanoi, Vietnam, 9–12 November 2009; pp. 77–82. [Google Scholar]
- Pal, S.; Hitchens, M.; Varadharajan, V. Towards a Secure Access Control Architecture for the Internet of Things. In Proceedings of the 2017 IEEE 42nd Conference on Local Computer Networks (LCN), Singapore, 9–12 October 2017; pp. 219–222. [Google Scholar]
- Hernández-Ramos, J.L.; Jara, A.J.; Marin, L.; Skarmeta, A.F. Distributed capability-based access control for the internet of things. J. Int. Serv. Inf. Secur. 2013, 3, 1–16. [Google Scholar]
- Hernández-Ramos, J.L.; Jara, A.J.; Marín, L.; Skarmeta Gómez, A.F. DCapBAC: Embedding authorization logic into smart things through ECC optimizations. Int. J. Comput. Math. 2016, 93, 345–366. [Google Scholar] [CrossRef]
- Databox Project. Available online: https://www.databoxproject.uk/publications/ (accessed on 12 July 2018).
- Birgisson, A.; Politz, J.G.; Erlingsson, U.; Taly, A.; Vrable, M.; Lentczner, M. Macaroons: Cookies with Contextual Caveats for Decentralized Authorization in the Cloud; Network and Distributed System Security Symposium, Internet Society: Reston, VA, USA, 2014. [Google Scholar]
- Maesa, D.D.F.; Mori, P.; Ricci, L. Blockchain based access control. In Proceedings of the IFIP International Conference on Distributed Applications and Interoperable Systems, Neuchâtel, Switzerland, 19–22 June 2017; pp. 206–220. [Google Scholar]
- Ouaddah, A.; Abou Elkalam, A.; Ait Ouahman, A. FairAccess: A new Blockchain-based access control framework for the Internet of Things. Secur. Commun. Netw. 2016, 9, 5943–5964. [Google Scholar] [CrossRef]
- Trust, confidence and Verifiable Data Audit. Available online: https://deepmind.com/blog/trust-confidence-verifiable-data-audit/ (accessed on 12 July 2018).
- Swan, M. Blockchain: Blueprint for a New Economy; O’Reilly Media, Inc.: Newton, MA, USA, 2015. [Google Scholar]
- Szabo, N. Formalizing and securing relationships on public networks. First Monday 1997, 2. [Google Scholar] [CrossRef]
- Gomi, H.; Hatakeyama, M.; Hosono, S.; Fujita, S. A delegation framework for federated identity management. In Proceedings of the 2005 workshop on Digital identity management, Fairfax, VA, USA, 11 November 2005; pp. 94–103. [Google Scholar]
- Aura, T. Distributed access-rights management with delegation certificates. In Secure Internet Programming; Springer: Berlin/Heidelberg, Germany, 1999; pp. 211–235. [Google Scholar]
- Zhang, L.; Ahn, G.J.; Chu, B.T. A rule-based framework for role-based delegation and revocation. ACM Trans. Inf. Syst. Secur. 2003, 6, 404–441. [Google Scholar] [CrossRef] [Green Version]
- Chen, N.; Chen, Y.; You, Y.; Ling, H.; Liang, P.; Zimmermann, R. Dynamic urban surveillance video stream processing using fog computing. In Proceedings of the 2016 IEEE Second International Conference on Multimedia Big Data (BigMM), Taipei, Taiwan, 20–22 April 2016; pp. 105–112. [Google Scholar]
- Chen, N.; Chen, Y.; Blasch, E.; Ling, H.; You, Y.; Ye, X. Enabling Smart Urban Surveillance at The Edge. In Proceedings of the 2017 IEEE International Conference on Smart Cloud (SmartCloud), New York, NY, USA, 3–5 November 2017; pp. 109–119. [Google Scholar]
- Chen, N.; Chen, Y.; Song, S.; Huang, C.T.; Ye, X. Smart Urban Surveillance Using Fog Computing. In Proceedings of the 2016 IEEE/ACM Symposium on Edge Computing (SEC), Washington, DC, USA, 27–28 October 2016; pp. 95–96. [Google Scholar]
- Xu, R.; Chen, Y.; Blasch, E.; Chen, G. A Federated Capability-based Access Control Mechanism for Internet of Things (IoTs). In Proceedings of the Conference on Sensors and Systems for Space Applications, SPIE Defense & Commercial Sensing 2018 (DCS), Orlando, FL, USA, 17 April 2018. [Google Scholar]
- Ethereum Homestead Documentation. Available online: http://www.ethdocs.org/en/latest/index.html (accessed on 12 July 2018).
- Solidity. Available online: http://solidity.readthedocs.io/en/latest/ (accessed on 12 July 2018).
- Truffle. Available online: http://truffleframework.com/docs/ (accessed on 12 July 2018).
- Crockford, D. JavaScript Object Notation (JSON). Available online: https://tools.ietf.org/html/rfc4627 (accessed on 12 July 2018).
- Flask: A Pyhon Microframework. Available online: http://flask.pocoo.org/ (accessed on 12 July 2018).
- SQLite. Available online: https://www.sqlite.org/index.html (accessed on 12 July 2018).
- BlednCAC Project. Available online: https://github.com/samuelxu999/Blockchain_dev/ (accessed on 12 July 2018).
- Go-Ethereum. Available online: https://ethereum.github.io/go-ethereum/ (accessed on 12 July 2018).
- Xu, R.; Nikouei, S.Y.; Chen, Y.; Song, S.; Polunchenko, A.; Deng, C.; Faughnan, T. Real-Time Human Object Tracking for Smart Surveillance at The Edge. In Proceedings of the IEEE International Conference on Communications, Selected Areas in Communications Symposium Smart Cities Track, Kansas City, MO, USA, 20–24 May 2018. [Google Scholar]



© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, R.; Chen, Y.; Blasch, E.; Chen, G. BlendCAC: A Smart Contract Enabled Decentralized Capability-Based Access Control Mechanism for the IoT. Computers 2018, 7, 39. https://doi.org/10.3390/computers7030039
Xu R, Chen Y, Blasch E, Chen G. BlendCAC: A Smart Contract Enabled Decentralized Capability-Based Access Control Mechanism for the IoT. Computers. 2018; 7(3):39. https://doi.org/10.3390/computers7030039
Chicago/Turabian StyleXu, Ronghua, Yu Chen, Erik Blasch, and Genshe Chen. 2018. "BlendCAC: A Smart Contract Enabled Decentralized Capability-Based Access Control Mechanism for the IoT" Computers 7, no. 3: 39. https://doi.org/10.3390/computers7030039






