1. Introduction
Worm attacks against sensor motes are realistic in sensor networks, as demonstrated by [
1,
2] In particular, they show that a worm could be propagated by exploiting code injection vulnerabilities in target sensor motes. Wide-spread worm dissemination makes it possible for an attacker to rapidly gain control over the network.
To defend against a worm, it is very important to understand how a worm is propagated. In the sense that epidemic model [
3] is good at modeling the spread of epidemic disease, researchers adapted it to worm propagation modeling in the internet and static sensor network [
4,
5,
6,
7]. However, these previous works do not consider node mobility which can greatly affect the worm infection capability and thus they are not appropriate for worm propagation in a mobile sensor network.
To mitigate this problem, we discuss a hop-by-hop worm propagation strategy in a mobile sensor network. In this strategy, worm infection is incurred only by neighbor-to-neighbor contact and thus node mobility will have little effect on worm propagation. Furthermore, we propose a carryover epidemic model in which the infection quota deficit in the current time slot is carried over to the next time slot. This model is adequate for the scenario where infection quota deficit occurs due to the frequent change of network topology and hence it is effective in the modeling of mobile sensor worm propagation. We analyze the cumulative number of infected nodes in the carryover epidemic model and derive Chernoff bounds on the number of time slots required for the whole network infection. Furthermore, we use an ns-2 simulator to evaluate the hop-by-hop worm propagation with carryover epidemic mode. The simulation results show that a worm infection quota deficit rarely occurs under the situation where a node’s maximum speed is at least 20 m/s and thus worm infection is not delayed but completed in time. This indicates that node mobility makes it possible for a mobile node to have enough neighbors, leading to expedition of worm infection.
The rest of paper is organized as follows. In
Section 2, we describe the related work. In
Section 4, we describe hop-by-hop worm propagation strategy and the carryover epidemic model in a mobile sensor network. In
Section 5, we analyze the hop-by-hop worm propagation with carryover epidemic model. In
Section 6, we simulate hop-by-hop worm propagation with carryover epidemic model in mobile sensor network and present the simulation results. In
Section 7, we conclude the paper.
2. Related Work
In this section, we first introduce the related work of sensor worm modeling and then bring up the worm modeling work in the literature of mobile networks.
In the context of sensor networks, several researchers [
4,
5,
6,
8] proposed worm propagation modeling in static sensor networks. More specifically, De
et al. [
4] modeled sensor worm propagation by using node deployment knowledge. De’s work investigated how group deployment strategy affects the worm propagation in a sensor network. Khayam
et al. [
6] applied the signal processing technique to model sensor worm propagation. Khayam
et al. explored the sensor worm propagation in terms of signal processing. Guo
et al. [
8] explored how to control worm propagation using the spatial correlation parameters. Feng
et al. [
5] examined the flux of worm dissemination using differential dynamical theory.
In the literature of mobile ad hoc networks, Mickens
et al. [
9,
10] investigated queue-based propagation of malicious software under random waypoint model in mobile ad hoc networks. Valler
et al. [
11] compute a general epidemic threshold in the SIS (Susceptible-Infectious-Susceptible) model and demonstrate that the epidemic threshold is not influenced by mobile node’s speed. Moreover, there are related works that apply the concept of epidemic mobility to broadcasting or ad hoc routing. Specifically, Karlsson
et al. [
12] proposed broadcasting system that utilizes delay-tolerant data forwarding together with node mobility. In [
13], the author proposed the combined version of AODV and DTN-based routing to take the benefits of both routing protocols.
Finally, Chen
et al. [
14] explored the worm propagation model in mobile smartphone. In a bluetooth environment, Yan
et al. [
15] worked the impact of mobility models on epidemic dissemination of a SIS virus.
4. Hop-By-Hop Worm Propagation in Mobile Sensor Networks
In this section, we describe a hop-by-hop worm propagation with carryover epidemic model in a mobile sensor network. Note that this model is also used as an assumption for worm detection in our previous work [
16].
Many researchers have adopted an epidemic model [
3] in order to model the infection quota, which is defined as the number of nodes that a worm infects per time slot in a network. This is because the epidemic model is useful at the quantification of infection quota in a series of time slots. The infection quota in the discrete time version of a simple epidemic model [
3] is calculated in units of time slots by the following equation:
where
θ is a pairwise infection rate [
3] and
N is the total number of nodes in the mobile sensor network.
indicates the number of worm originators. We define
as the cumulative infection quota from the 0th time slot to the
kth time slot. As a consequence, the infection quota in the
kth time slot is set to
.
Since the epidemic model only deals with the infection quota, there should be a model to describe how worm is spread through the mobile sensor network. To meet this need, we consider a a hop-by-hop worm dissemination strategy in mobile sensor network. Under this strategy, we assume that a sensor has susceptible or infectious state. All sensor nodes are initially set to the susceptible state except infectious worm originators. Each infectious node spreads worm to its one-hop neighboring susceptible nodes. Once a susceptible node is infected by a worm, it changes its state to infectious.
Although the epidemic model is good at modeling the infection quota, it may not be useful in the scenario in which infectious nodes in a time slot could have fewer neighboring susceptible nodes than the infection quota due to the network topology. To pacify this problem, we slightly change the discrete time version of simple epidemic model in such a way that we carry over the infection quota deficit in the current time slot to the next time slot, charging the total infection quota over the entire time period. More specifically, we denote the infection quota deficit in the kth time slot. The infection quota in the first time slot is calculated as and the infection quota in the kth time slot is accordingly computed as (). We call this modified version of epidemic model the carryover epidemic model. In the next section, we provide a quantitative analysis of the carryover epidemic model.
5. Analysis
In this section, we first present an analysis on the carryover epidemic model and then describe the analytical results on the number of time slots required for the entire network infection.
In the following Lemma, we first derive the cumulative number of infected nodes when the carryover epidemic model is used.
Lemma 1. In carryover epidemic model, the cumulative number of infected nodes from the 0th time slot to the τth time slot is .
Proof. Recall that
is the infection quota in the
th time slot (
) in carryover epidemic model, where
is the infection quota in the first time slot and
is the infection quota deficit in the
tth time slot. The number of infected nodes in a time slot is the difference between the infection quota and the quota deficit in a time slot. Hence, the cumulative number of infected nodes from the 0th time slot to the
τth time slot is given by:
☐
If the entire network infection is completed in the τth time slot, will be zero. Accordingly, by the Lemma 1, will be equal to the total number of nodes in the network.
Next, we compute the average number of time slots required for the entire network infection. To do this, we employ discrete Poisson distribution to model the number of time slots required to infect the entire network. This is reasonable in the sense that discrete Poisson distribution is generally useful for random data counting and thus can be applied to randomly count the number of time slots required for the entire network infection. Specifically, we define a discrete Poisson random variable X with parameter μ. X indicates a time slot in which the entire network infection is finished. Putting it in differently, X times slots are needed to infect all nodes in the network.
We define as the probability that the entire network infection is completed in the jth time slot. Accordingly, is the average number of time slots required for the entire network infection.
By the definition of discrete Poisson distribution,
is given by:
and
.
Then the probability that the entire network infection is completed at most the τth time slot is calculated as . Thus, 1- is the probability that more than τ time slots are consumed to infect all nodes in the network.
Finally, we derive the Chernoff bounds on the number of time slots required for the entire network infection.
Lemma 2. If and , then .
Proof. For any
, the Markov’s inequality is given by:
Since
is the moment generating function of the Poisson discrete random variable
X, we have
Given that
and
, by selecting
, we have
☐
We investigate how
j affects the Chernoff bound of Pr(
) when
. As shown in
Figure 1, the Chernoff bound of Pr(
) decreases as
j increases. From this observation, as
j is away from
τ, it decays the Chernoff bound on the probability that the number of time slots required for the entire network infection is at least
j. Given a fixed value of
j, the Chernoff bound of Pr(
) increases as
μ increases. This means that the Chernoff bound of Pr(
) rises as an average number of slots required for the entire network infection is close to
τ.
Figure 1.
Chernoff bound of Pr() vs. j.
Figure 1.
Chernoff bound of Pr() vs. j.
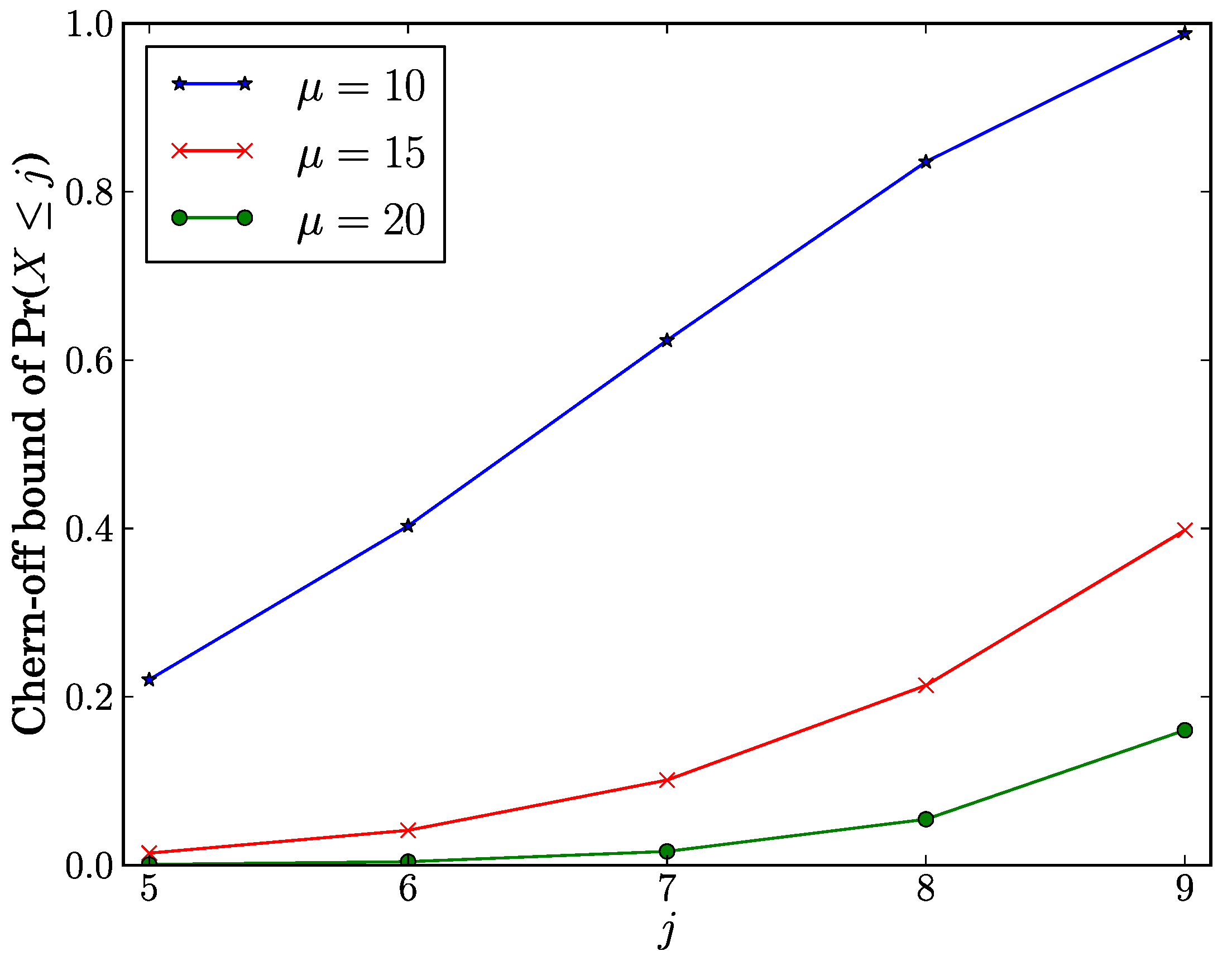
Lemma 3. If and , then .
Proof. For any
, the Markov’s inequality is given by:
Since
is the moment generating function of the Poisson discrete random variable
X, we have
Given that
and
, by selecting
, we have
☐
We investigate how
j affects the Chernoff bound of Pr(
) when
. As shown in
Figure 2, the Chernoff bound of Pr(
) increases as
j increases. From this observation, as
j is close to
τ, it rises the Chernoff bound on the probability that the number of time slots required for the entire network infection is at most
j. Given a fixed value of
j, the Chernoff bound of Pr(
) increases as
μ decreases. This means that the Chernoff bound of Pr(
) rises as an average number of slots required for the entire network infection is close to
τ.
Figure 2.
Chernoff bound of Pr() vs.j.
Figure 2.
Chernoff bound of Pr() vs.j.