Security Property Validation of the Sensor Network Encryption Protocol (SNEP)
Abstract
:1. Introduction
- Data confidentiality confirms that a sensor network’s information, especially the readings of the sensors, is kept secret from other networks. Encryption is the most commonly-used technique for providing data confidentiality.
- Data authentication confirms that data were really sent by the claimed sender. A symmetric key (shared by the sender and the receiver)-based message authentication code (MAC) ensures data authenticity.
- Data integrity verifies that data have not been altered en route by any adversary. MAC-based data authentication includes data integrity.
- Data freshness ensures that data are recent and not replayed by an adversary. Nonces and counters are two ways to provide freshness.
- Replay protection prevents an adversary from reusing an old message.
- Low communication overhead is a basic security property that should be ensured by any WSN security protocols.
- Semantic security confirms that no two messages are identical. This could be confirmed by sending a counter or timestamp that is modified in every message.
2. Secure Network Encryption Protocol
- Unicast communication: Node to base station (e.g., sensor readings) and base station to node (e.g., specific requests) are kinds of unicast communication between the base station and a specific node. SNEP has been designed to secure all of these unicast communications.
- Multicast communication: Base station to all nodes (e.g., routing beacons, queries or reprogramming of the entire network) needs one to many multicast communication. Note that the TESLA protocol [9] was originally developed to secure multicast data transmission. However, TESLA is not designed for the limited computing environments commonly found in WSNs. To secure multicast communications in WSNs, a tiny and stripped version of the TESLA protocol has been proposed, which is referred to as μTESLA.
| Notation | Meaning |
|---|---|
| Principals, such as communicating nodes. | |
| Nonce generated by A. | |
| Counter generated and updated by A. | |
| Master secret key shared between A and B. | |
| Symmetric key between A and B used for encryption of messages. This is derived from . | |
| MAC key between A and B used for MAC calculation. This is derived from . | |
| Encryption of message M with the encryption key . | |
| Encryption of message M with the encryption key and the initialization vector . | |
| Computation of the message authentication code (MAC) of message M, with the key . |
2.1. Data Transmission with Weak Freshness
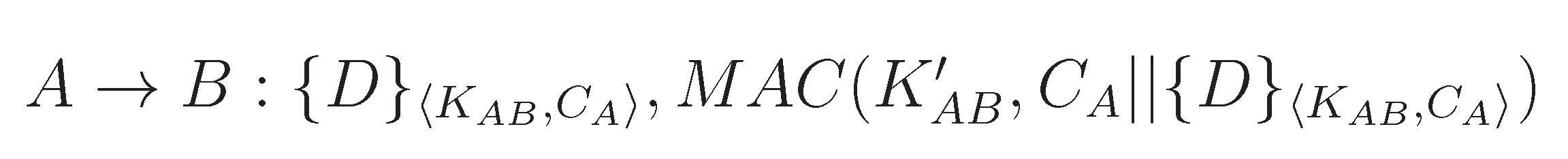
2.2. Data Transmission with Strong Freshness

2.3. Counter Exchange Sub-Protocol

2.4. Node to Node Key Agreement Sub-Protocol
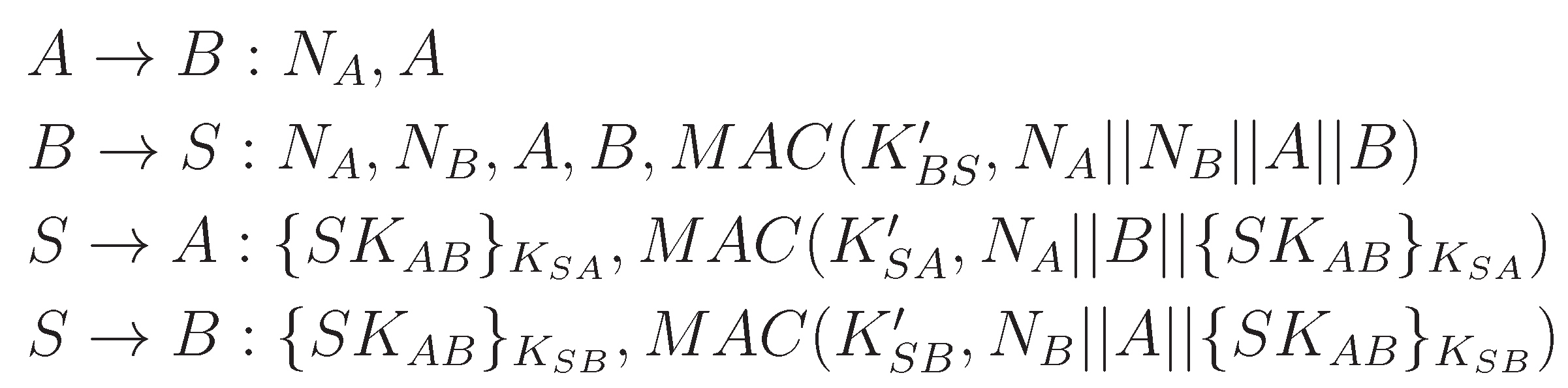
- Due to the use of and , two properties are guaranteed: (i) strong key freshness to both A and B; and (ii) authentication of S to A (at the end of the third message) and S to B (at the end of the fourth message).
- The confidentiality of through encryption.
- The data authenticity and integrity of through keyed MAC, which confirms that it was generated by the base station.
- Defending the base station against the denial-of-service attack through the MAC in the second message; thus, the base station confirmed that the request has come from a legitimate node.
- Saving energy of the nodes by engaging base station to perform the major tasks, e.g., key generation and distribution.
3. AVISPA
3.1. Architecture

3.2. Security Goal Specification
4. Developing SNEP Model in AVISPA
4.1. Simplification of SNEP Protocols
4.1.1. Number of Keys
4.1.2. Replacing MAC with a Hash Function
4.1.3. Modeling with Regular Encryption
4.2. Node to Node Key Agreement with Strong Freshness
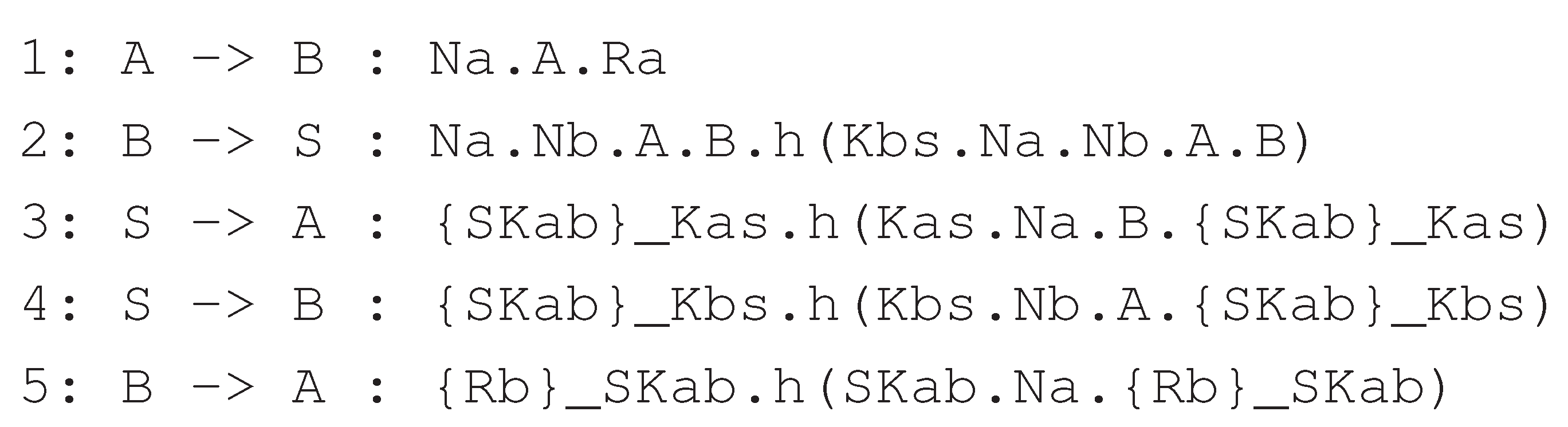
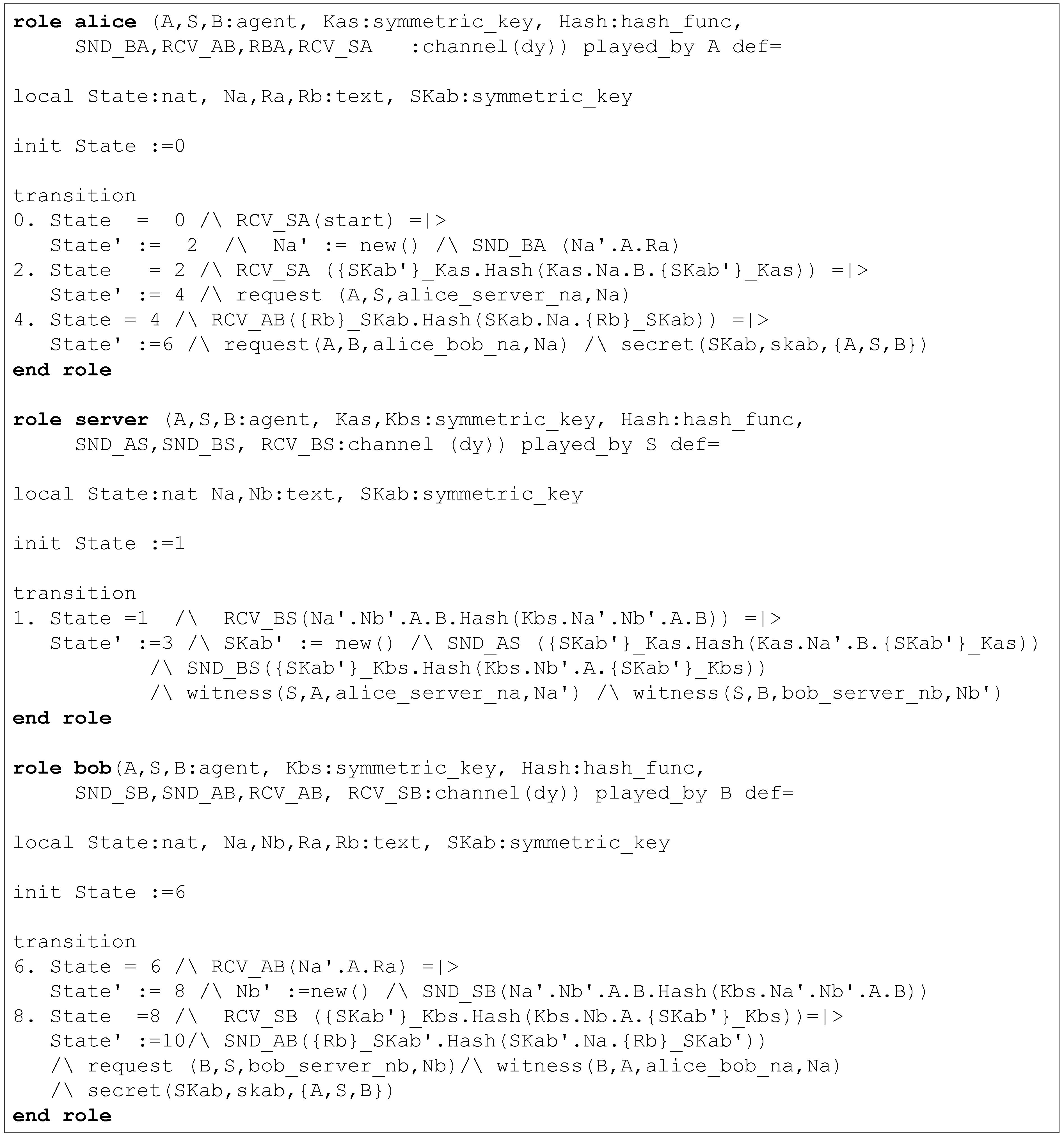
- We assume the scenario where node A sends a request Ra with a nonce Na to node B, but they do not have any shared key. However, A and B share master secrets and with the trusted third party S, from which symmetric keys Kas and Kbs are derived.
- B requests S to establish a symmetric key between A and B. While sending this request, B sends a fresh nonce, Nb with Na. Note that the keyed hash of the first part, i.e., h(Kbs.Na.Nb.A.B), is included for message authentication.
- Next, S generates a new symmetric key, SKab, and sends this to A and B through two separate messages. While sending A (B), this key is encrypted with Kas (Kbs). Moreover, the keyed hash is calculated using Kas (Kbs), which also includes the nonce Na (Nb).
- Now, B sends Rb encrypted by SKab to A in response to the request it received in the first message. The keyed hash sent with this message is calculated using SKab, which includes Na.
- (1)
- Secrecy of the symmetric key SKab, which is validated using the HLPSL goal secrecy_of and the corresponding secret fact secret(SKab, skab, {A, S, B}). Here, the label skab identifies the goal, and {A, S, B} is the set of agents that are allowed to learn the value SKab.
- (2)
- Upon receiving the third message, A authenticates S through the nonce Na. We use the label alice_server_na to identify the goal. To validate this security goal, we add witness(S, A, alice_server_na, Na′) and request(A, S, alice_server_na, Na) statements inside the roles of S and A, respectively.
- (3)
- Upon receiving the fourth message, B authenticates S through the nonce Nb. We use the label bob_server_nb to identify the goal. To validate this security goal, we add witness(S, B, bob_server_nb, Nb′) and request(B, S, bob_server_nb, Nb) statements inside the roles of S and B, respectively.
- (4)
- Upon receiving the fifth message, A authenticates B through the nonce Na. We use the label alice_bob_na to identify the goal. To validate this security goal, we add witness(B, A, alice_bob_na, Na) and request(A, B, alice_bob_na, Na) statements inside the roles of B and A, respectively.
- (5)
- The secrecy of the response of B to A (i.e., Rb) is validated using the fact secret(Rb, rb, {A, B, S}). Here, the label rb identifies the goal, and {A, B, S} is the set of agents that are allowed to learn the value Rb.
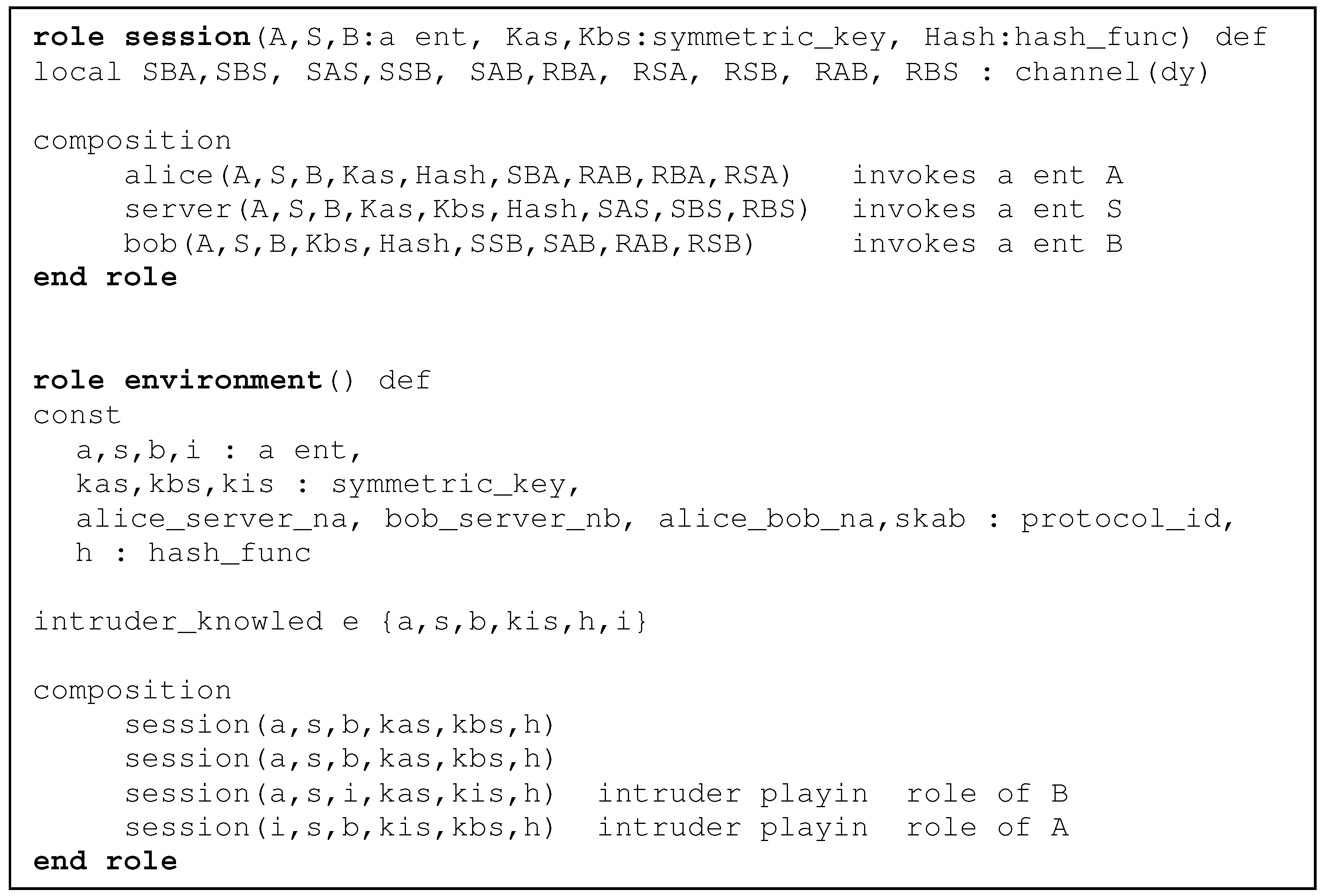
4.3. Counter Exchange Protocol with Strong Freshness

- (1)
- Upon receiving the second message, A authenticates B through the counter (nonce) Ca. We use the label alice_bob_ca to identify the goal. To validate this security goal, we add witness(B, A, alice_bob_ca, CA′) and request(A, B, alice_bob_ca, CA) statements inside the roles of B and A, respectively.
- (2)
- Upon receiving the third message, B authenticates A through the counter (nonce) Cb. We use the label bob_alice_cb to identify the goal. To validate this security goal, we add witness(A, B, bob_alice_cb, CB′) and request(B, A, bob_alice_cb, CB) statements inside the roles of A and B, respectively.
- (3)
- The secrecy of data, D sent to B from A. This goal is validated using the fact secret(D′, d, {A, B})). Here, the label d identifies the goal, and {A, B} is the set of agents that are allowed to learn the value D.

4.4. Freshness, Replay and MitM Attacks
4.5. Model Validation and Analysis

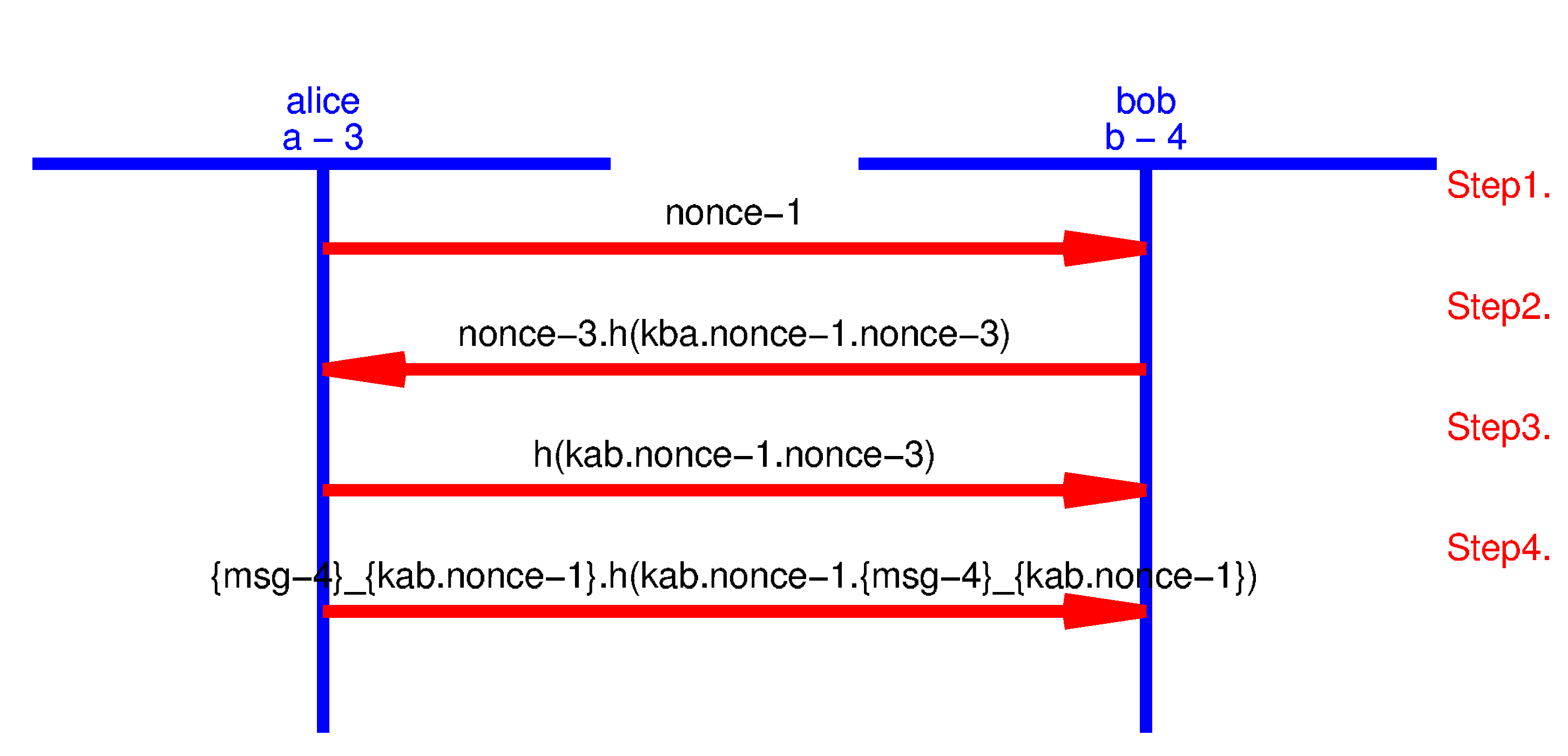
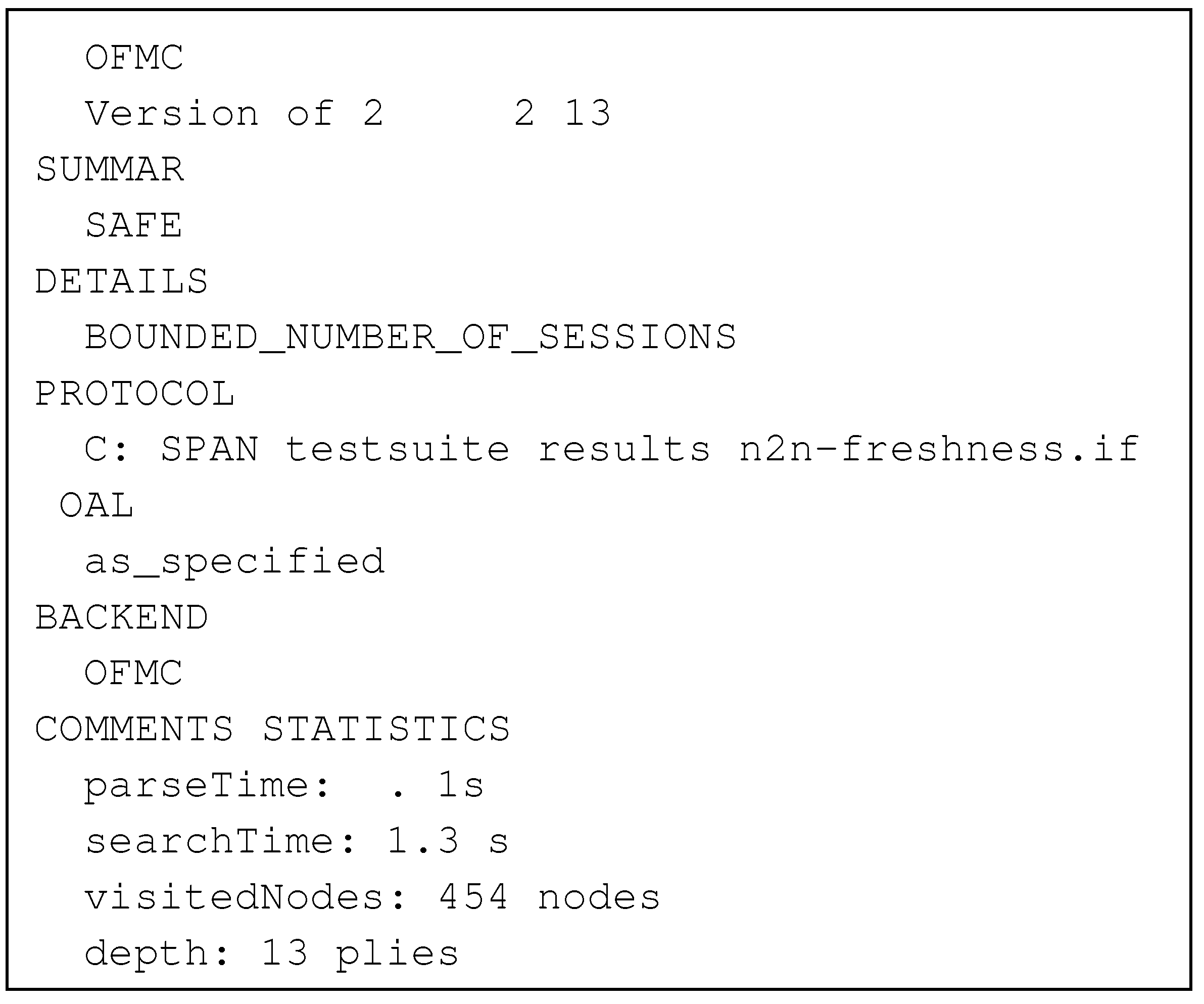
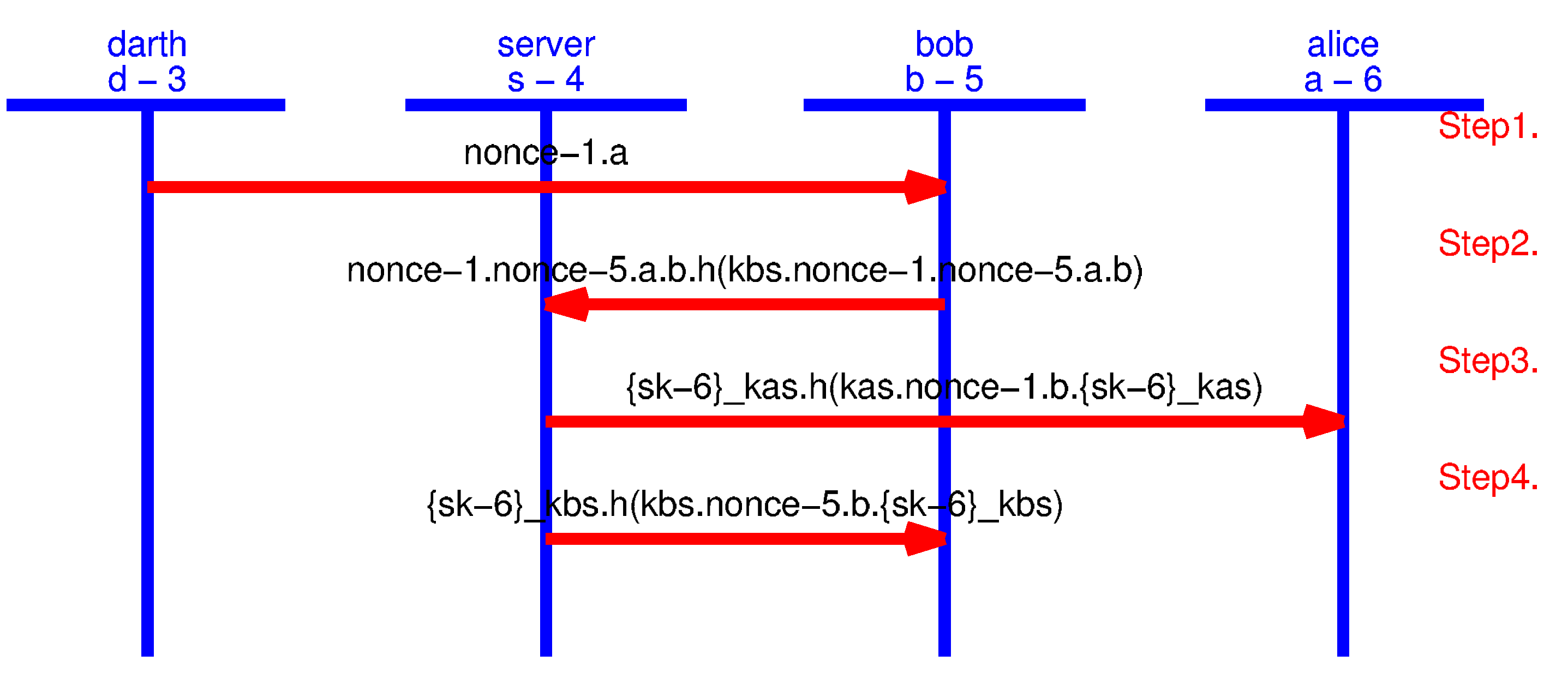
5. Denial-of-Service Attack on Node to Node Key Agreement Protocol
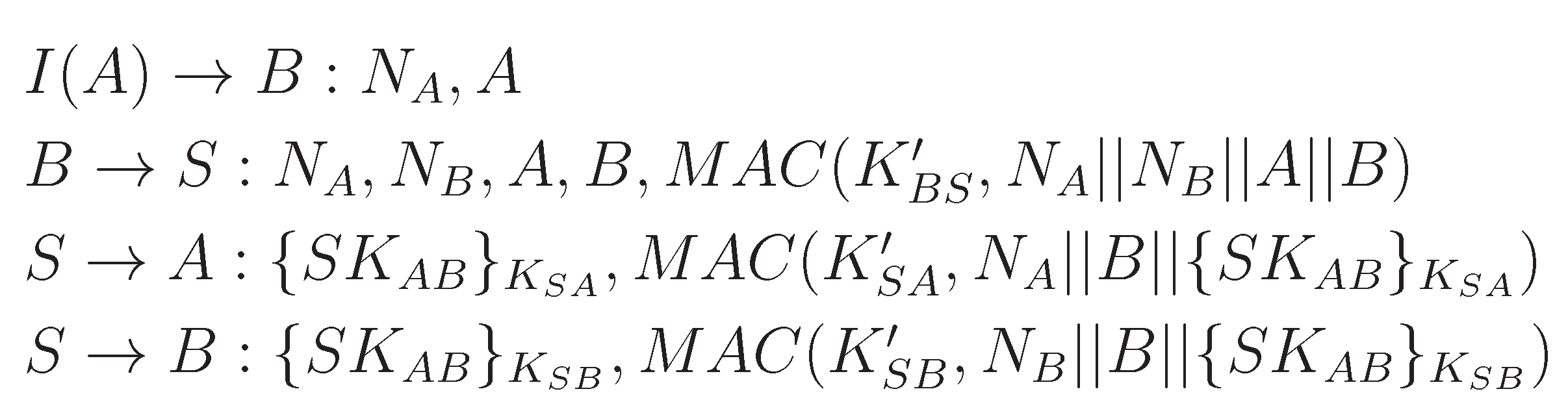
5.1. Simulating a DoS Attack in AVISPA
5.2. Preventing the DoS Attack
- the first message it receives from A, i.e., ;
- B adds its nonce and identity, i.e., ;
- finally, B appends the MAC of the first two components using the MAC key, , shared between B and S.

6. Related Work
- (1)
- We develop the model of the counter exchange protocol with strong freshness, which they did not.
- (2)
- They develop a node to node key distribution followed by data transmission (in total, six messages are being exchanged), while we develop an integrated model (in total, five messages are being exchanged).
- (3)
- Finally, the attack we discovered was not reported by the previous model.
7. Conclusions
Conflicts of Interest
References
- Akyildiz, I.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. Wireless sensor networks: A survey. Comput. Netw. 2002, 38, 393–422. [Google Scholar] [CrossRef]
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- Stankovic, J.; Wood, A.; He, T. Realistic Applications for Wireless Sensor Networks. In Theoretical Aspects of Distributed Computing in Sensor Networks; Nikoletseas, S., Rolim, J.D., Eds.; Monographs in Theoretical Computer Science; An EATCS Series; Springer: Berlin, Germany, 2011; pp. 835–863. [Google Scholar]
- Sen, J. Security in Wireless Sensor Networks. In Wireless Sensor Networks: Current Status and Future Trends; Khan, S., Pathan, A.S.K., Alrajeh, N.A., Eds.; CRC Press: Boca Raton, FL, USA, 2012; pp. 407–460. [Google Scholar]
- Perrig, A.; Stankovic, J.; Wagner, D. Security in Wireless Sensor Networks. Commun. ACM 2004, 47, 53–57. [Google Scholar] [CrossRef]
- Karlof, C.; Wagner, D. Secure routing in wireless sensor networks: Attacks and countermeasures. Ad Hoc Netw. 2003, 1, 293–315. [Google Scholar] [CrossRef]
- Rivest, R.L.; Shamir, A.; Adleman, L. A method for obtaining digital signatures and public-key cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Perrig, A.; Szewczyk, R.; Tygar, J.D.; Wen, V.; Culler, D.E. SPINS: Security Protocols for Sensor Networks. Wirel. Netw. 2002, 8, 521–534. [Google Scholar] [CrossRef]
- Perrig, A.; Canetti, R.; Tygar, J.; Song, D. Efficient authentication and signing of multicast streams over lossy channels. In Proceedings of IEEE Symposium on Security and Privacy, Berkeley, CA, USA, 14–17 May 2000; pp. 56–73.
- Armando, A.; Basin, D.; Boichut, Y.; Chevalier, Y.; Compagna, L.; Cuellar, J.; Drielsma, P.H.; Heám, P.; Kouchnarenko, O.; Mantovani, J.; et al. The AVISPA Tool for the Automated Validation of Internet Security Protocols and Applications. In Computer Aided Verification; Lecture Notes in Computer Science; Etessami, K., Rajamani, S., Eds.; Springer-Verlag: Berlin, Germany, 2005; Volume 3576, pp. 281–285. [Google Scholar]
- Vigan, L. Automated Security Protocol Analysis With the AVISPA Tool. Electron. Notes Theor. Comput. Sci. 2006, 155, 61–86. [Google Scholar] [CrossRef]
- Islam, S. Security Analysis of LMAP Using AVISPA. Int. J. Secur. Netw. 2014, 9, 30–39. [Google Scholar] [CrossRef]
- Heen, O.; Genet, T.; Geller, S.; Prigent, N. An Industrial and Academic Joint Experiment on Automated Verification of a Security Protocol. In Proceedings of the IFIP Networking Workshop on Mobile and Networks Security, Singapore, Singapore, 5–9 May 2008; pp. 39–53.
- Glouche, Y.; Genet, T.; Houssay, E. SPAN: A Security Protocol ANimator for AVISPA; User Manual; IRISA/Université de Rennes 1: Rennes, France, 2006. [Google Scholar]
- Dolev, D.; Yao, A. On the Security of Public-Key Protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Wood, A.; Stankovic, J. Denial of service in sensor networks. Computer 2002, 35, 54–62. [Google Scholar] [CrossRef]
- Tobarra, L.; Cazorla, D.; Cuartero, F. Formal Analysis of Sensor Network Encryption Protocol (SNEP). In Proceedings of the IEEE International Conference on Mobile Adhoc and Sensor Systems (MASS’07), Pisa, Italy, 8–11 October 2007; pp. 1–6.
- Holzmann, G.J. The SPIN Model Checker: Primer and Reference Manual; Addison-Wesley: Boston, MA, USA, 2004. [Google Scholar]
- Chen, W.; Xiao, W. Model checking and analyzing the security protocol for wireless sensor networks. In Proceedings of the International Conference on Electronic and Mechanical Engineering and Information Technology (EMEIT), Harbin, Heilongjiang, China, 12–14 August 2011; Volume 8, pp. 4093–4096.
- Li, Y.; Newe, T. On the Formal Verification of the SNEP Key Agreement Protocol for Wireless Sensor Networks. In Proceedings of the International Conference on Sensor Technologies and Applications (SensorComm’07), Valencia, Spain, 14–20 October 2007; pp. 186–191.
- Macedonio, D.; Merro, M. A Semantic Analysis of Key Management Protocols for Wireless Sensor Networks. Sci. Comput. Program. 2014, 81, 53–78. [Google Scholar] [CrossRef]
- Newe, T.; Coffey, T. Formal verification logic for hybrid security protocols. Int. J. Comput. Syst. Sci. Eng. 2003, 18, 17–25. [Google Scholar]
- Ouranos, I.; Stefaneas, P.; Ogata, K. Formal Modeling and Verification of Sensor Network Encryption Protocol in the OTS/CafeOBJ Method. In Leveraging Applications of Formal Methods, Verification, and Validation; Lecture Notes in Computer Science; Margaria, T., Steffen, B., Eds.; Springer-Verlag: Berlin, Germany, 2010; Volume 6415, pp. 75–89. [Google Scholar]
- Karlof, C.; Sastry, N.; Wagner, D. TinySec: A Link Layer Security Architecture for Wireless Sensor Networks. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems (SenSys’04), Baltimore, MD, USA, 3–5 November 2004; pp. 162–175.
- Tobarra, L.; Cazorla, D.; Cuartero, F.; Díaz, G.; Cambronero, E. Model checking wireless sensor network security protocols: TinySec+ LEAP+ TinyPK. Telecommun. Syst. 2009, 40, 91–99. [Google Scholar] [CrossRef]
- Luk, M.; Mezzour, G.; Perrig, A.; Gligor, V. MiniSec: A Secure Sensor Network Communication Architecture. In Proceedings of the 6th International Conference on Information Processing in Sensor Networks, Cambridge, MA, USA, 25–27 April 2007; pp. 479–488.
- Tobarra, L.; Cazorla, D.; Cuartero, F.; Díaz, G. Analysis of security protocol minisec for wireless sensor networks. In Proceedings of the IV Congreso Iberoamericano de Seguridad Informatica (CIBSI’07), Mar del Plata, Argentina, 26–28 November 2007; pp. 1–13.
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Islam, S. Security Property Validation of the Sensor Network Encryption Protocol (SNEP). Computers 2015, 4, 215-233. https://doi.org/10.3390/computers4030215
Islam S. Security Property Validation of the Sensor Network Encryption Protocol (SNEP). Computers. 2015; 4(3):215-233. https://doi.org/10.3390/computers4030215
Chicago/Turabian StyleIslam, Salekul. 2015. "Security Property Validation of the Sensor Network Encryption Protocol (SNEP)" Computers 4, no. 3: 215-233. https://doi.org/10.3390/computers4030215