A Survey on Situational Awareness of Ransomware Attacks—Detection and Prevention Parameters
Abstract
:1. Introduction
- Updated state of the art focused on analysis and prevention proposals and mechanisms that aid in preventing ransomware attacks in windows devices. It will be used as a starting point for future research.
- This paper is the first proposal that resumes the parameters that are taken into account in current investigations. This can lay the foundations to propose novel Ransomware Situational Awareness models.
- It provides open issues, challenges, and related methods that confront this kind of attacks.
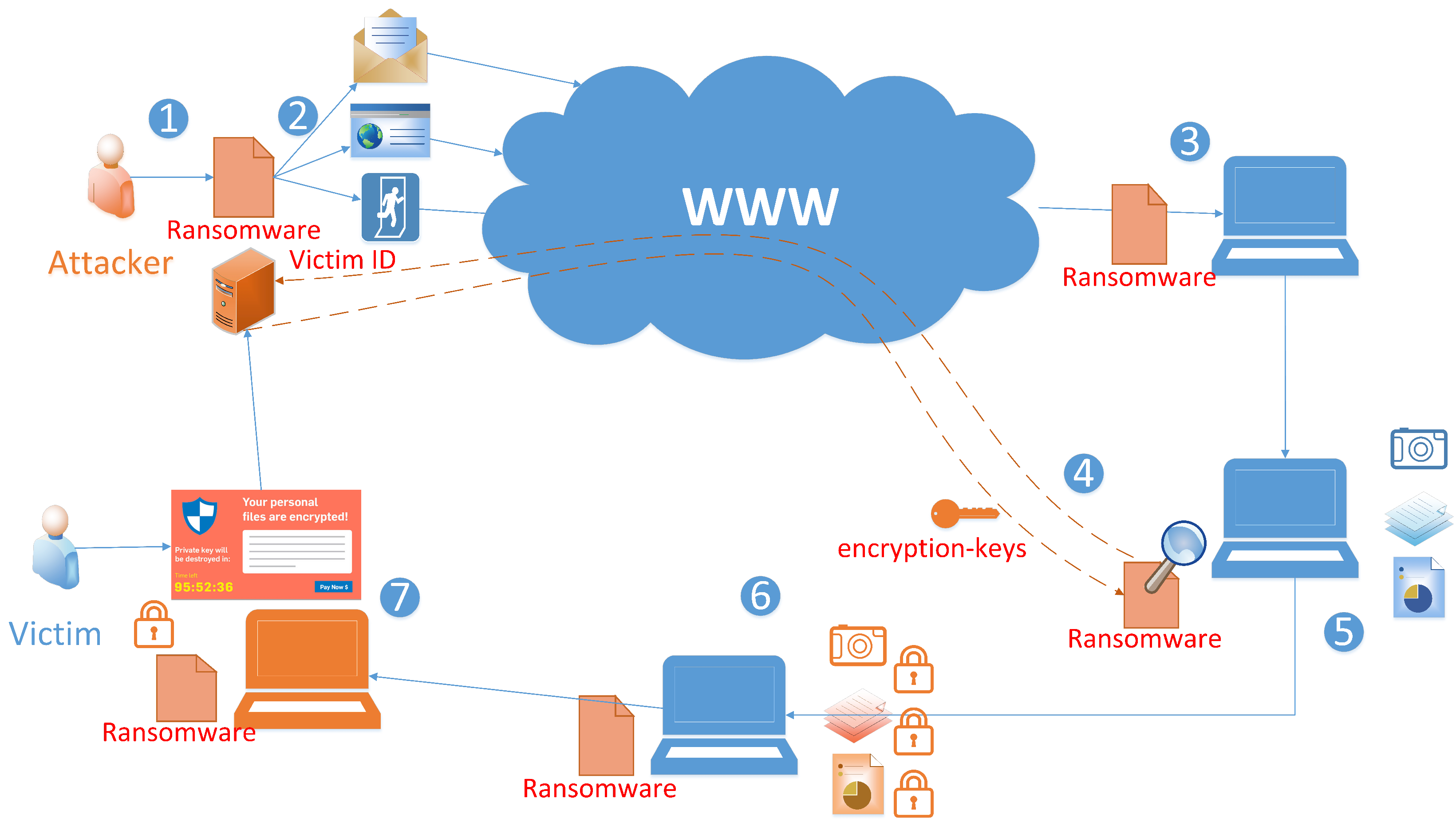
2. Ransomware Life Cycle and Situational Awareness Model
2.1. Ransomware Life Cycle
- Ransomware design
- Ransomware dissemination
- Ransomware arrival
- Command and Control communication (C&C)
- Search user’s information
- Encryption
- Extortion and financial claiming
2.2. Ransomware Situational Awareness Model
- Perception This stage identifies and monitors specific assets and network parameters. It also reports ordinary events as well as new incidents. The perception phase gathers raw data related to the protected system. Then, this information must be organized in individual structures in order to facilitate the management and access of it.
- Comprehension Collected information is correlated and aggregated in order to simplify analysis and prediction tasks. Firstly, non-sensitive and redundant data are discarded and then a preliminary analysis is done.
- Projection This stage applies analysis techniques to forecast the behavior of the system and tracks its evolution. This phase takes into account countermeasures previously applied and their impact on the environment. Combining historical and current information proactive and reactive actions or responses are executed.
2.3. Payment Methods
2.4. Current Research
3. Ransomware Analysis
- Prevention This area is related to actions that are being used to avoid or minimize the possibility of a ransomware attack. These actions can include an updated operating system, the installation or use of a specialized application, among others. It also includes making file backups to avoid the extortion. The main objective of this phase is to close system vulnerabilities or security holes that were used in the past.
- Detection This phase intends to apply different mechanisms in order to detect ransomware attacks during or after it happens. The key idea of detection is to diagnose the end devices and then discover suspicious events or conditions. In this way, it is possible to avoid a possible attack in its initial phase, minimizing the impact on the system. Detection could also include both proactive and reactive responses.
- Prediction This area has the purpose of avoiding the attack before it takes place, which is achieved by means the gathering of different parameters or connections in end devices, then this information will be analyzed and correlated in order to predict possible attacks. One of the main pillars of prediction is the introduction of intelligent techniques. Based on prediction, the users can apply countermeasure to stop or avoid the attack.
3.1. Detection And Prediction
3.2. Prevention
4. Evaluated Parameters on Current Research
- Content similarity and entropy It allows determining how similar the data is. Entropy is based on the degree of randomness of the bytes in a file. Typical file types, such as HTML or doc, have a lower entropy value compared with binary files (exe, dll). Encryption produces typically a high entropy. Therefore, if the file has been changed and it is too different in comparison with the expected average entropy, it can be considered a potential threat. It is important to note that a high entropy for itself is not a conclusive parameter to predict ransomware attacks because other normal processes like compression imply a high entropy value. Furthermore, newer versions of ransomware are reducing the entropy and, consequently, a lower value does not guarantee a possible infection. Entropy can be used as a part of an attack vector in order to predict ransomware threats.
- Monitoring C&C Communications In ransomware attacks, a C&C server propagates instructions in order to infect or take control of devices called bots. In this context, the monitoring of unusual or continuous communications with specific internet sites will be done. For this purpose, researches are using innovative technologies such as SDN in order to block the communication with the C&C server when it is happening. For instance, in [58] a system to monitor suspicious network traffic is proposed. It blocks infected devices, in a real-time manner, through rules applied by the SDN controller. Moreover, concepts like Network Function Virtualization (NFV) aid to mitigate this problem by means of the deployment of specialized network functions like Deep Packet Inspectors (DDI) or honeypots. Besides, Domain generation algorithms (DGA) generate a set of domain names that are used by the C&C server and leave a trace in network traffic [59]. It is important to note that some ransomware samples do not need an internet connection to encrypt files.
- Filesystem activity A ransomware inevitably uses function calls (e.g., I/O Requests) to execute malicious operations in the OS filesystem. The system under attack can exhibit an abnormal file system activity since a large number of equal file system access can be requested. The main suspicious activities related to the file system can include changes in Master File Table (MTF) and I/O Request Packets (IRP) [60]. During a ransomware attack, the MTF can be encrypted and the Master Boot Record (MBR) is overwritten. Thus, monitoring these elements is an effective strategy to detect ransomware.
- Monitoring registry values It has been observed that during a ransomware attack, several registry values are modified. For instance, many ransomware variants modify the values of HKEY_LOCAL_MACHINE\System\CurrentControlSet\control\N1s\ComputerName \ActiveComputerName and HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WindowsNT \CurrentVersion \WinLogon, HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows \CurrentVersion \Run. Similarly, the value of HKLM\Software\Microsoft\Cryptography \Defaults\Provider Types\Type 001 as the Microsoft Strong Cryptographic Provider is read [7]. Other variants remove the volume shadow copies (Volume Snapshot services VSS files) in order to avoid the use of these backups to recover the system. Finally, ransomware opens a txt instruction file and fills it with the image of attacker payment information and changes the desktop background to the bitmap image. In other words, the HKCU\Control Panel\Desktop\Wallpaper value is set to %CSIDL_DESKTOPDIRECTORY%\_Locky_recover_instructions.bmp [46]. In the case of encryption ransomware, crypto libraries and registers are used or accessed.
- Privilege Escalation It is considered one of the most distinctive features of ransomware attacks. Once the malicious software is downloaded on the system, it monitors the environment to check their access capabilities and, if necessary, asks for administration rights. This access request is externalized as an app authorization button in Android devices or a malicious window requesting authorization in Windows elements (update patch). Once the attack obtains administrator privileges, it continues the attack by locking the victim device (Windows) or setting a new lock screen PIN (Android).
- Monitoring API and DLL calls The use of APIs is one of the most common ways of software development. Through it, a set of procedures, protocols, and tools is provided as logical building blocks. The programmer puts the blocks together according to their particular objective through API requests and API calls. Similarly, the attacker uses the available APIs for executing malicious activities. Therefore, some characteristics of API calls (e.g., time, type, number, sequence) can be used to model the application behavior. Then, a classifier can be trained in order to detect suspicious activities. For example, a suspicious sequence in API Windows is the use of GetThreadDesktop, CreateDesktopW, and SwitchDesktop [60]. Even though the attacker could avoid the use of API calls, the use of native APIs requires significant work due to lack of compatibility and available documentation.
- Modifications of Master Boot Record (MBR) A group of ransomware attacks is specialized in changing the Master Boot Record, which contains the executable boot code and the partition table. This attack takes advantage of the well-known position of the MBR (first sector of a hard disk) and the startup procedure. Then the system boot process loads the MBR instructions in memory and transfers it to the control system at boot time. In this context, the malicious software modifies the boot code with a bogus MBR that blocks the normal boot procedure and displays a message requesting a ransom.
- Monitoring specific file type, file path, or directories It includes monitoring modifications of files to find out an unusual increase of specific extensions, such as .locky. It also oversees the Volumen Shadow Copy service (VSC) in order to avoid that shadow copies of the systems can be erased. Moreover, it is crucial monitoring URLs and web pages.
5. Future Trends and Challenges
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| BN | Bayesian Network |
| BTC | Bitcoin |
| CA | Certificate Authority |
| C&C | Command and Control |
| DGA | Domain Generation Algorithms |
| FRSM | File Server Resource Manager |
| HPC | Hardware Performance Counter |
| IRP | I\O REquest Packets |
| MBR | Master Boot Record |
| MFT | Master File Table |
| NFV | Network Function Virtualization |
| RaaS | Ransomware as a Service |
| RF | Random Forest |
| RDP | Remote Desktop Protocol |
| RNN | Recurrent Neural Network |
| SA | Situational Awareness |
| SDN | Software Defined Networks |
| SMB | Server Message Block |
| SON | Self-organized Networking |
| SVM | Support Vector Machine |
| TDS | Traffic Distribution System |
| VSC | Volumen Shadow Copy |
References
- Cleary, G.; Cox, O.; Lau, H.; Nahorney, B.; Gorman, B.; O’Brien, D.; Wallace, S.; Wood, P.; Wueest, C. ISTR 2018. Internet Secur. Threat Rep.-Symantec 2018, 23, 80–89. [Google Scholar]
- Azmoodeh, A.; Dehghantanha, A.; Conti, M.; Choo, K.K.R. Detecting Crypto-ransomware in IoT Networks based on Energy Consumption Footprint. J. Ambient Intell. Hum. Comput. 2017, 9, 1141–1152. [Google Scholar] [CrossRef]
- Eset, E. ESET Security 2018; Technical Report; ESET: Bratislava, Slovakia, 2018. [Google Scholar]
- O’Brien, D. Ransomware 2017, An ISTR Special Report. Symantec. Available online: https://www.symantec.com/content/dam/symantec/docs/security-center/white-papers/istr-ransomware-2017-en.pdf (accessed on 5 April 2019).
- Kumar, M.S.; Ben-Othman, J.; Srinivasagan, K. An Investigation on Wannacry Ransomware and its Detection. In Proceedings of the 2018 IEEE Symposium on Computers and Communications (ISCC), Natal, Brazil, 25–28 June 2018; pp. 1–6. [Google Scholar]
- Sgandurra, D.; Muñoz-González, L.; Mohsen, R.; Lupu, E.C. Automated Dynamic Analysis of Ransomware: Benefits, Limitations and Use for Detection. arXiv 2016, arXiv:1609.03020. [Google Scholar]
- Monika; Zavarsky, P.; Lindskog, D. Experimental Analysis of Ransomware on Windows and Android Platforms: Evolution and Caracterization. Procedia Comput. Sci. 2016, 94, 465–472. [Google Scholar] [CrossRef]
- Bajpai, P.; Sood, A.K.; Enbody, R. A Key-management-based Taxonomy for Ransomware. In Proceedings of the 2018 APWG Symposium on Electronic Crime Research (eCrime), San Diego, CA, USA, 15–17 May 2018; pp. 1–12. [Google Scholar]
- Kelley, D. Cybesecurity in the Cognitive Era: Priming your Digital Immune System; Technical Report; IBM: Somers, NY, USA, 2016. [Google Scholar]
- Endsley, M.R. Design and Evaluation for Situation Awareness Enhancement. Proc. Hum. Factors Soc. Annu. Meet. 1988, 32, 97–101. [Google Scholar] [CrossRef]
- Conti, M.; Gangwal, A.; Ruj, S. On the Economic Significance of Ransomware Campaigns: A Bitcoin Transactions Perspective. Comput. Secur. 2018. [Google Scholar] [CrossRef]
- Hernandez-Castro, J.; Cartwright, E.; Stepanova, A. Economic Analysis of Ransomware. arXiv 2017, arXiv:1703.06660. [Google Scholar] [CrossRef] [Green Version]
- Gangwar, K.; Mohanty, S.; Mohapatra, A. Analysis and Detection of Ransomware Through Its Delivery Methods. In Proceedings of the International Conference on Recent Developments in Science, Engineering and Technology, Gurgaon, India, 13–14 October 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 353–362. [Google Scholar]
- Moore, C. Detecting Ransomware with Honeypot Techniques. In Proceedings of the 2016 Cybersecurity and Cyberforensics Conference (CCC), Amman, Jordan, 2–4 August 2016; pp. 77–81. [Google Scholar]
- Zahra, A.; Shah, M.A. IoT based Ransomware Growth Rate Evaluation and Detection using Command and Control Blacklisting. In Proceedings of the 2017 23rd International Conference on Automation and Computing (ICAC), Huddersfield, UK, 7–8 September 2017; pp. 1–6. [Google Scholar]
- Alhawi, O.M.; Baldwin, J.; Dehghantanha, A. Leveraging Machine Learning Techniques for Windows Ransomware Network Traffic Detection. In Cyber Threat Intelligence; Springer: Heidelberg, Germany, 2018; pp. 93–106. [Google Scholar]
- Hampton, N.; Baig, Z.; Zeadally, S. Ransomware Behavioural Analysis on Windows Platforms. J. Inf. Secur. Appl. 2018, 40, 44–51. [Google Scholar] [CrossRef]
- Lu, T.; Zhang, L.; Wang, S.; Gong, Q. Ransomware Detection based on V-detector Negative Selection Algorithm. In Proceedings of the 2017 International Conference on Security, Pattern Analysis, and Cybernetics (SPAC), Shenzhen, China, 15–17 December 2017; pp. 531–536. [Google Scholar]
- Jung, S.; Won, Y. Ransomware Detection Method based on Context-aware Entropy Analysis. In Soft Computing; Springer: Heidelberg, Germany, 2018; pp. 1–10. [Google Scholar]
- Al-rimy, B.A.S.; Maarof, M.A.; Prasetyo, Y.A.; Shaid, S.Z.M.; Ariffin, A.F.M. Zero-Day Aware Decision Fusion-Based Model for Crypto-Ransomware Early Detection. Int. J. Integr. Eng. 2018, 10, 82–88. [Google Scholar] [CrossRef]
- Alam, M.; Bhattacharya, S.; Mukhopadhyay, D.; Chattopadhyay, A. RAPPER: Ransomware Prevention via Performance Counters. arXiv 2018, arXiv:1802.03909. [Google Scholar]
- Gómez-Hernández, J.; Álvarez-González, L.; García-Teodoro, P. R-Locker: Thwarting Ransomware Action through a Honeyfile-based Approach. Comput. Secur. 2018, 73, 389–398. [Google Scholar] [CrossRef]
- Cabaj, K.; Gregorczyk, M.; Mazurczyk, W. Software-defined Networking-based Crypto Ransomware Detection using HTTP Traffic Characteristics. Comput. Electr. Eng. 2018, 66, 353–368. [Google Scholar] [CrossRef]
- Kharraz, A.; Arshad, S.; Mulliner, C.; Robertson, W.K.; Kirda, E. UNVEIL: A Large-Scale, Automated Approach to Detecting Ransomware. In Proceedings of the USENIX Security Symposium, Austin, TX, USA, 10–12 August 2016; pp. 757–772. [Google Scholar]
- Chen, Z.G.; Kang, H.S.; Yin, S.N.; Kim, S.R. Automatic Ransomware Detection and Analysis Based on Dynamic API Calls Flow Graph. In Proceedings of the International Conference on Research in Adaptive and Convergent Systems, Krakow, Poland, 20–23 September 2017; pp. 196–201. [Google Scholar]
- Kardile, A.B. Crypto Ransomware Analysis and Detection Using Process Monitor. Ph.D. Thesis, UT-Arlington, Arlington, TX, USA, 2017. [Google Scholar]
- Maniath, S.; Ashok, A.; Poornachandran, P.; Sujadevi, V.; Sankar, A.P.; Jan, S. Deep Learning LSTM based Ransomware Detection. In Proceedings of the 2017 Recent Developments in Control, Automation & Power Engineering (RDCAPE), Noida, India, 26–27 October 2017; pp. 442–446. [Google Scholar]
- Kolodenker, E.; Koch, W.; Stringhini, G.; Egele, M. PayBreak: Defense against Cryptographic Ransomware. In Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security, Abu Dhabi, UAE, 2–6 April 2017; pp. 599–611. [Google Scholar]
- Takeuchi, Y.; Sakai, K.; Fukumoto, S. Detecting Ransomware using Support Vector Machines. In Proceedings of the 47th International Conference on Parallel Processing Companion, Eugene, OR, USA, 13–16 August 2018; p. 1. [Google Scholar]
- Thomas, J.; Galligher, G. Improving Backup System Evaluations in Information Security Risk Assessments to Combat Ransomware. In Computer and Information Science; CCSE: Richmond Hill, ON, Canada, 2018; Volume 11, ISSN 1913-8989. [Google Scholar]
- Vinayakumar, R.; Soman, K.; Velan, K.S.; Ganorkar, S. Evaluating shallow and deep networks for ransomware detection and classification. In Proceedings of the 2017 International Conference on Advances in Computing, Communications and Informatics (ICACCI), Udupi, India, 13–16 September 2017; pp. 259–265. [Google Scholar]
- Kwon, I.; Im, E.G. Extracting the Representative API Call Patterns of Malware Families Using Recurrent Neural Network. In Proceedings of the International Conference on Research in Adaptive and Convergent Systems, Krakow, Poland, 20–23 September 2017; pp. 202–207. [Google Scholar]
- O’Kane, P.; Sezer, S.; Carlin, D. Evolution of Ransomware. IET Netw. 2018, 7, 321–327. [Google Scholar] [CrossRef]
- Mauraya, A.; Kumar, N.; Agrawal, A.; Khan, R. Ransomware: Evolution, Target and Safety Measures. Int. J. Comput. Sci. Eng. 2017, 6, 80–85. [Google Scholar] [CrossRef]
- Sotelo, M.; Maestre, J.; García, L. A novel Self-Organizing Network solution towards Crypto-ransomware Mitigation. In Proceedings of the 13th International Conference on Availability, Reliability and Security, Hamburg, Germany, 27–30 August 2018; pp. 40–48. [Google Scholar]
- Al-rimy, B.A.S.; Maarof, M.A.; Shaid, S.Z.M. A 0-day aware Crypto-ransomware early Behavioral Detection Framework. In Proceedings of the International Conference of Reliable Information and Communication Technology, Johor Bahru, Malaysia, 23–24 April 2017; Springer: Berlin/Heidelberg, Germany, 2017; pp. 758–766. [Google Scholar]
- Zhang, H.; Xiao, X.; Mercaldo, F.; Ni, S.; Martinelli, F.; Sangaiah, A.K. Classification of Ransomware Families with Machine Learning based on N-gram of Opcodes. Future Gener. Comput. Syst. 2019, 90, 211–221. [Google Scholar] [CrossRef]
- Cimitile, A.; Mercaldo, F.; Nardone, V.; Santone, A.; Visaggio, C.A. Talos: No more Ransomware Victims with Formal Methods. Int. J. Inf. Secur. 2018, 17, 719–738. [Google Scholar] [CrossRef]
- Huang, D.Y.; Aliapoulios, M.M.; Li, V.G.; Invernizzi, L.; Bursztein, E.; McRoberts, K.; Levin, J.; Levchenko, K.; Snoeren, A.C.; McCoy, D. Tracking Ransomware End-to-end. In Proceedings of the 2018 IEEE Symposium on Security and Privacy (SP), San Francisco, CA, USA, 20–24 May 2018; pp. 618–631. [Google Scholar]
- Cohen, A.; Nissim, N. Trusted Detection of Ransomware in a Private Cloud using Machine Learning Methods leveraging Meta-features from Volatile Memory. Expert Syst. Appl. 2018, 102, 158–178. [Google Scholar] [CrossRef]
- Homayoun, S.; Dehghantanha, A.; Ahmadzadeh, M.; Hashemi, S.; Khayami, R.; Choo, K.K.R.; Newton, D.E. DRTHIS: Deep Ransomware Threat Hunting and Intelligence System at the Fog Layer. Future Gener. Comput. Syst. 2019, 90, 94–104. [Google Scholar] [CrossRef]
- Wang, Z.; Liu, C.; Qiu, J.; Tian, Z.; Cui, X.; Su, S. Automatically Traceback RDP-Based Targeted Ransomware Attacks. Wirel. Commun. Mob. Comput. 2018, 2018. [Google Scholar] [CrossRef]
- Al-rimy, B.A.S.; Maarof, M.A.; Shaid, S.Z.M. Ransomware threat Success Factors, Taxonomy, and Countermeasures: A Survey and Research Directions. Comput. Secur. 2018, 74, 144–166. [Google Scholar] [CrossRef]
- El-Kosairy, A.; Azer, M.A. Intrusion and Ransomware Detection System. In Proceedings of the 2018 1st International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 4–6 April 2018; pp. 1–7. [Google Scholar]
- Kim, D.Y.; Choi, G.Y.; Lee, J.H. White list-based Ransomware Real-time Detection and Prevention for User Device Protection. In Proceedings of the 2018 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 12–14 January 2018; pp. 1–5. [Google Scholar]
- Honda, T.; Mukaiyama, K.; Shirai, T.; Ohki, T.; Nishigaki, M. Ransomware Detection Considering User’s Document Editing. In Proceedings of the 2018 IEEE 32nd International Conference on Advanced Information Networking and Applications (AINA), Pedagogical University of Cracow, Cracow, Poland, 16–18 May 2018; pp. 907–914. [Google Scholar] [CrossRef]
- Saleem, J.; Adebisi, B.; Ande, R.; Hammoudeh, M. A State of the Art Survey-impact of Cyber Attacks on SME’s. In Proceedings of the International Conference on Future Networks and Distributed Systems (ICFNDS), Cambridge, UK, 19–20 July 2017; Art. No. 52. ISBN 978-1-4503-4844-7. [Google Scholar]
- RAMSES. RAMSES: Internet Forensic Platform for Tracking the Money Flow of Financially-motivated Malware. 2016. Available online: https://ramses2020.eu (accessed on 5 January 2019).
- CYBECO. Supporting Cyberinsurance from a Behavioural Choice Perspective. 2017. Available online: https://www.cybeco.eu/ (accessed on 9 January 2019).
- Pillai, A.; Kadikar, R.; Vasanthi, M.; Amutha, B. Analysis of AES-CBC Encryption for Interpreting Crypto-Wall Ransomware. In Proceedings of the 2018 International Conference on Communication and Signal Processing, Chennai, India, 3–5 April 2018; pp. 599–604, ISBN 978-1-5386-3522-3. [Google Scholar]
- Gonzalez, D.; Hayajneh, T. Detection and Prevention of Crypto-Ransomware. In Proceedings of the 2017 IEEE 8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference, New York, NY, USA, 19–21 October 2017; pp. 472–478, ISBN 978-1-5386-1105-0. [Google Scholar]
- Richardson, R.; North, M. Ransomware: Evolution, Mitigation and Prevention. Int. Manag. Rev. 2017, 13, 10–21. [Google Scholar]
- Mehmood, S. Enterprise Survival Guide for Ransomware Attacks. SANS Information Security Training| Cyber Certifications|Research. 2016. Available online: www.sans.org (accessed on 24 October 2018).
- TechNet, M. Microsoft Protection Center: Security Tips to Protect Against Ransomware. Technical Report, Last Revision 2017. Available online: https://social.technet.microsoft.com/wiki/contents/articles/29787.microsoft-protection-center-security-tips-to-protect-against-ransomware.aspx (accessed on 30 January 2019).
- Frenz, C.; Diaz, C. Anti-Ransomware Guide. Technical Report; OWASP Anti-Ransomware Guide Project, Version 1.7. 2018. Available online: https://www.owasp.org/index.php/OWASP_Anti-Ransomware_ Guide_Project (accessed on 30 January 2019).
- Ahmadian, M.M.; Shahriari, H.R.; Ghaffarian, S.M. Connection-Monitor & Connection-Breaker: A Novel Approach for Prevention and Detection of High Survivable Ransomwares. In Proceedings of the 2015 12th International Iranian Society of Cryptology Conference on Information Security and Cryptology, Iran, Rasht, 8–10 September 2015; pp. 79–84. [Google Scholar]
- cuckoosandbox. Automated Malware Analysis. Available online: https://cuckoosandbox.org/ (accessed on 12 December 2018).
- Cabaj, K.; Mazurczyk, W. Using Software-defined Networking for Ransomware Mitigation: The Case of Cryptowall. IEEE Netw. 2016, 30, 14–20. [Google Scholar] [CrossRef]
- Pletinckx, S.; Trap, C.; Doerr, C. Malware Coordination using the Blockchain: An Analysis of the Cerber Ransomware. In Proceedings of the 2018 IEEE Conference on Communications and Network Security, Beijing, China, 30 May–1 June 2018; pp. 1–9. [Google Scholar]
- Kharraz, A.; Robertson, W.; Balzarotti, D.; Bilge, L.; Kirda, E. Cutting the Gordian Knot: A Look under the Hood of Ransomware Attacks. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Milan, Italy, 9–10 July 2015; pp. 3–24. [Google Scholar]
- Hu, F.; Hao, Q.; Bao, K. A Survey on Software-defined Network and Openflow: From Concept to Implementation. IEEE Commun. Surv. Tutorials 2014, 16, 2181–2206. [Google Scholar] [CrossRef]
- Mijumbi, R.; Serrat, J.; Gorricho, J.L.; Bouten, N.; De Turck, F.; Boutaba, R. Network Function Virtualization: State-of-the-art and Research Challenges. IEEE Commun. Surv. Tutorials 2016, 18, 236–262. [Google Scholar] [CrossRef]
- Imran, A.; Zoha, A.; Abu-Dayya, A. Challenges in 5G: How to Empower SON with Big Data for enabling 5G. IEEE Netw. 2014, 28, 27–33. [Google Scholar] [CrossRef]

| Reference | Year | Keywords/Topics | Kind of Research | ||
|---|---|---|---|---|---|
| Review | Proposal | Testing | |||
| [6] | 2016 | Detection, machine learning, Support Vector Machine (SVM), regularized logistic regression | X | ||
| [7] | 2016 | Ransomware evolution, datasets | X | X | |
| [11] | 2018 | Ransomware economic impact, bitcoin trace | X | ||
| [12] | 2017 | Economic analysis | X | ||
| [13] | 2017 | Prevention, pattern, random forest, exploit kits, supervised machine learning | X | ||
| [14] | 2016 | Honeypot, detection | X | X | |
| [15] | 2017 | C&C, IoT attacks | X | X | |
| [16] | 2018 | Detection methods, Decision Tree Classifier | X | X | |
| [17] | 2018 | API calls, detection | X | ||
| [18] | 2017 | Detection, V-detector negative selection algorithm, feature extraction | X | ||
| [19] | 2018 | Detection, prevention, entropy information | X | ||
| [20] | 2018 | Ransomware taxonomy, state of the art on prevention, detection and prediction. | X | ||
| [21] | 2018 | Unsupervised detection method, artificial neural networks, Hardware Performance Counter (HPC). | X | ||
| [22] | 2018 | Detection, honey file, protection | X | ||
| [23] | 2018 | Detection, mitigation, Software Defined Networking (SDN) | X | ||
| [24] | 2016 | Detection mechanism | X | ||
| [25] | 2017 | Analysis and detection, simple Logic (SP), SVM | X | ||
| [26] | 2017 | Cryptoanalysis, detection | X | X | |
| [27] | 2017 | Deep learning, Long-short term memory (LSTM) | X | ||
| [28] | 2017 | Crypto model, encryption keys, proactive prevention | X | ||
| [29] | 2018 | Dynamic analysis, anomaly detection, SVM | X | ||
| [30] | 2018 | Backups, disaster recovery, risk assessment | X | ||
| [31] | 2017 | Deep networks, detection | X | ||
| [32] | 2017 | Recurrent neural network (RNN), detection | X | ||
| [33] | 2018 | Mitigation, detection | X | X | |
| [34] | 2017 | Ransomware evolution, safety measures | X | ||
| [35] | 2018 | Detection, mitigation, SDN, NFVs | X | ||
| [36] | 2017 | Crypto-Ransomware, bitcoin, Cybercurrency | X | ||
| [37] | 2019 | Static analysis, opcode, Machine learning | X | ||
| [38] | 2018 | Security, model checking, android | X | ||
| [39] | 2018 | Bitcoin, crypto-currency, payment | X | ||
| [40] | 2018 | Volatile memory forensics memory dumps | X | ||
| [41] | 2019 | Deep learning, convolutional neural network, LSTM | X | ||
| [42] | 2018 | Remote Desktop Protocol (RDP), detection | X | ||
| [43] | 2018 | Behavioral detection, anomaly | X | ||
| [44] | 2018 | Detection, deception systems | X | ||
| [45] | 2018 | Real time detection, access control, file operation | X | ||
| [46] | 2018 | Encryptor, file protection, document editing | X | ||
| [47] | 2017 | Cyber threats, security audit, penetration testing, IoT, privacy | X | ||
| Reference | Year | Evaluated Parameters | Tools/Datasets |
|---|---|---|---|
| [6] | 2016 | API invocations, registry keys, file directory operations, dropped files. | VirusShare, Cuckoo sandbox, VirusTotal, Matlab |
| [7] | 2016 | Filesystem and registry in Windows; checking the MD5 hash values from Virus, file system and register activity, network communications | PEiD, PEView tool, Cuckoo, Anubis |
| [14] | 2016 | Honeypot folder monitored with an FSRM File Screen | EventSentry, FSRM |
| [24] | 2016 | File path, time attributes, filesystem I/O activity | Cuckoo, OpenSSL, VirusTotal |
| [13] | 2017 | Listing of the file path and dropped file, ransom note, network activity, analyzing application payload | Cuckoo, Wireshark, tracewrangle3, Dionaea Honeypot |
| [15] | 2017 | C&C communication, public key, the connection established between victims and the C&C server. | Framework Proposal |
| [18] | 2017 | Hard disk reading and writing, the encryption and deletion of files, crypto APIs. Three types of features: API functions, behavioral expression (count IP address, ports, etc) and memory feature. | Cuckoo Sandbox, Volatility |
| [25] | 2017 | API calls (GetModuleFileNameA, NtCreateSection, NtCreateFile, NtMapViewOfSection, NtWriteFile) | API Monitor tool, Weka |
| [26] | 2017 | File system, registry, process activity, entropy, API functions (ReadFile, QueryInformation), Master File Tables, System Service Descriptor Table | bCuckoo, VirusTotal, Process Monitor |
| [27] | 2017 | API calls, registry values | Cuckoo Sandbox |
| [28] | 2017 | Crypto Function Hooking, CryptoAPI, File recovery, SHA1 functions | Cuckoo sandbox, Raddar, VirusTotal |
| [31] | 2017 | 121 API call functions (NtEnumerateValueKey, NtOpenSection, closesocket, CryptDecodeObjectEx, GetFileAttributesW) | Cuckoo sandbox, TensorFlow, Open Malware, VirusTotal |
| [32] | 2017 | API call sequences (NtOpenFile, RegOpenKeyExA, ioctlsocket, NtResumeThread, etc) | Cuckoo sandbox, VirusTotal |
| [16] | 2018 | Network features (Protocol, source and destination address, ports, packets, duration) | Tshark, Weka, Kali Linux |
| [17] | 2018 | API calls (CopyFile, CreateDirectory), InternetOpen, CryptoDeriveKey, SetFileAttributes, GetFileType, GetFileSize, CryptoGenKey, CryptoDecodeObject) | Windows Power Shell, bash scripts, ProcMon |
| [19] | 2018 | The entropy value, of the file, was calculated (its format) | Watchdog Module |
| [21] | 2018 | Cache-references, cache-misses, branch-misses and branches. | iperf tool, sandbox, Kera, |
| [22] | 2018 | FIFO files, infinitive files | Bash-ransomware, linux suite, linux encoder, OpenSSL |
| [23] | 2018 | HTTP message sequences and their corresponding sizes. | Cuckoo, Alexa websites, POX |
| [29] | 2018 | API calls | Cuckoo sandbox |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Herrera Silva, J.A.; Barona López, L.I.; Valdivieso Caraguay, Á.L.; Hernández-Álvarez, M. A Survey on Situational Awareness of Ransomware Attacks—Detection and Prevention Parameters. Remote Sens. 2019, 11, 1168. https://doi.org/10.3390/rs11101168
Herrera Silva JA, Barona López LI, Valdivieso Caraguay ÁL, Hernández-Álvarez M. A Survey on Situational Awareness of Ransomware Attacks—Detection and Prevention Parameters. Remote Sensing. 2019; 11(10):1168. https://doi.org/10.3390/rs11101168
Chicago/Turabian StyleHerrera Silva, Juan A., Lorena Isabel Barona López, Ángel Leonardo Valdivieso Caraguay, and Myriam Hernández-Álvarez. 2019. "A Survey on Situational Awareness of Ransomware Attacks—Detection and Prevention Parameters" Remote Sensing 11, no. 10: 1168. https://doi.org/10.3390/rs11101168





