A Low-Jitter Wireless Transmission Based on Buffer Management in Coding-Aware Routing
Abstract
:1. Introduction
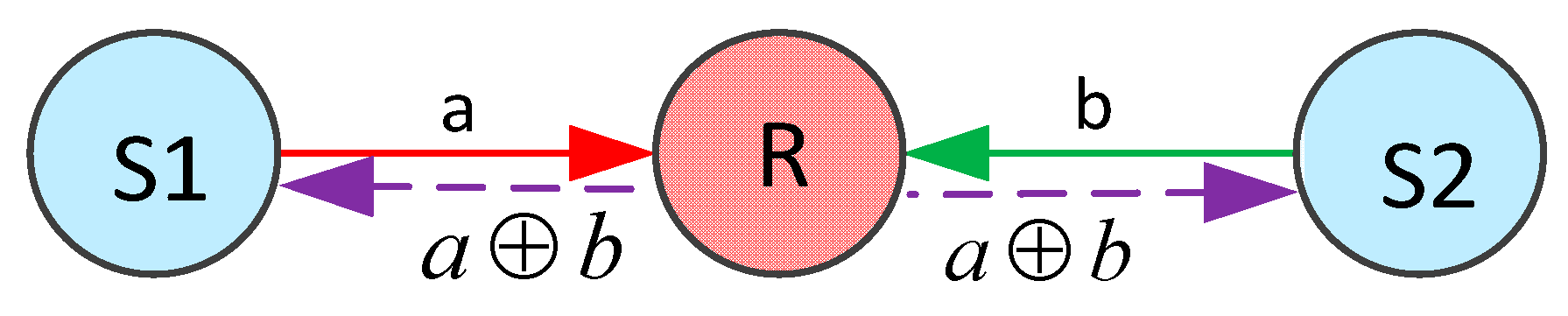
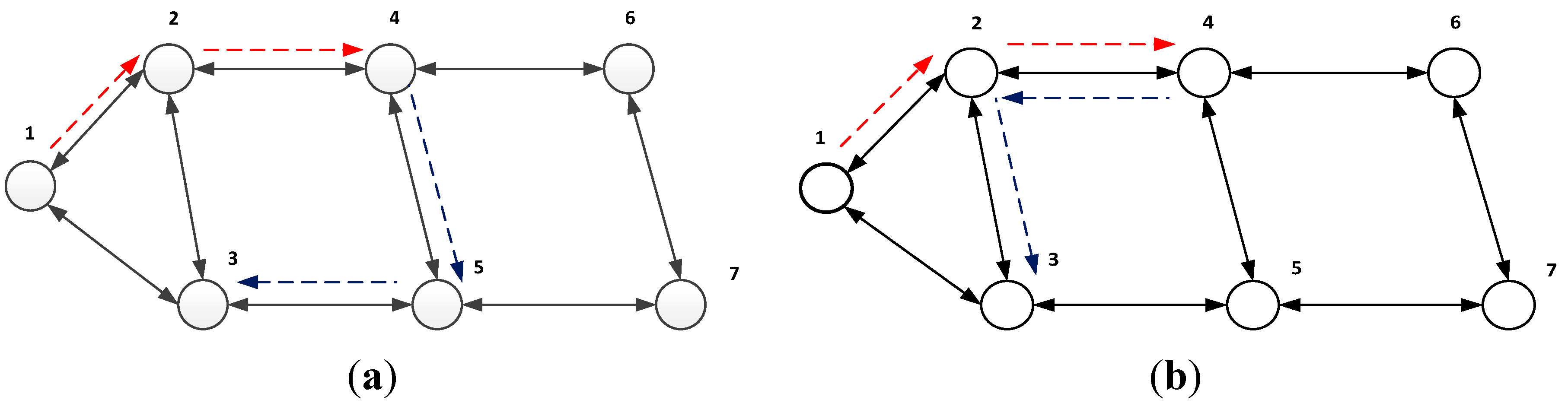
2. Coding Opportunity over a Wireless Network
2.1. Network Model
2.2. Coding Opportunity Analysis

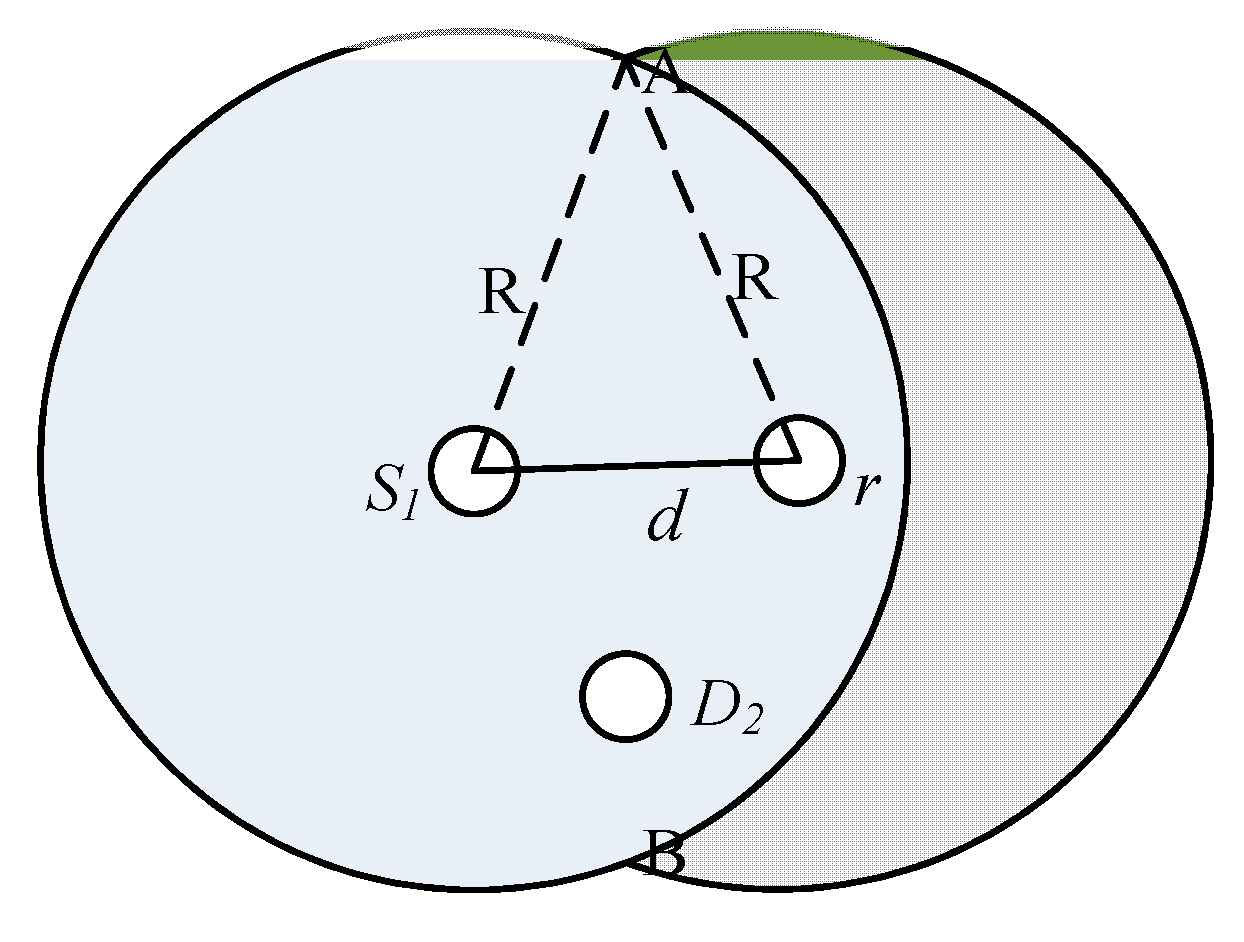
3. Analysis of Queue Length Policy at a Coding Node
3.1. Background
3.2. Computation of Threshold Policy
4. BLJCAR Mechanism
4.1. Network Jitter Training
4.2. Data Transmission
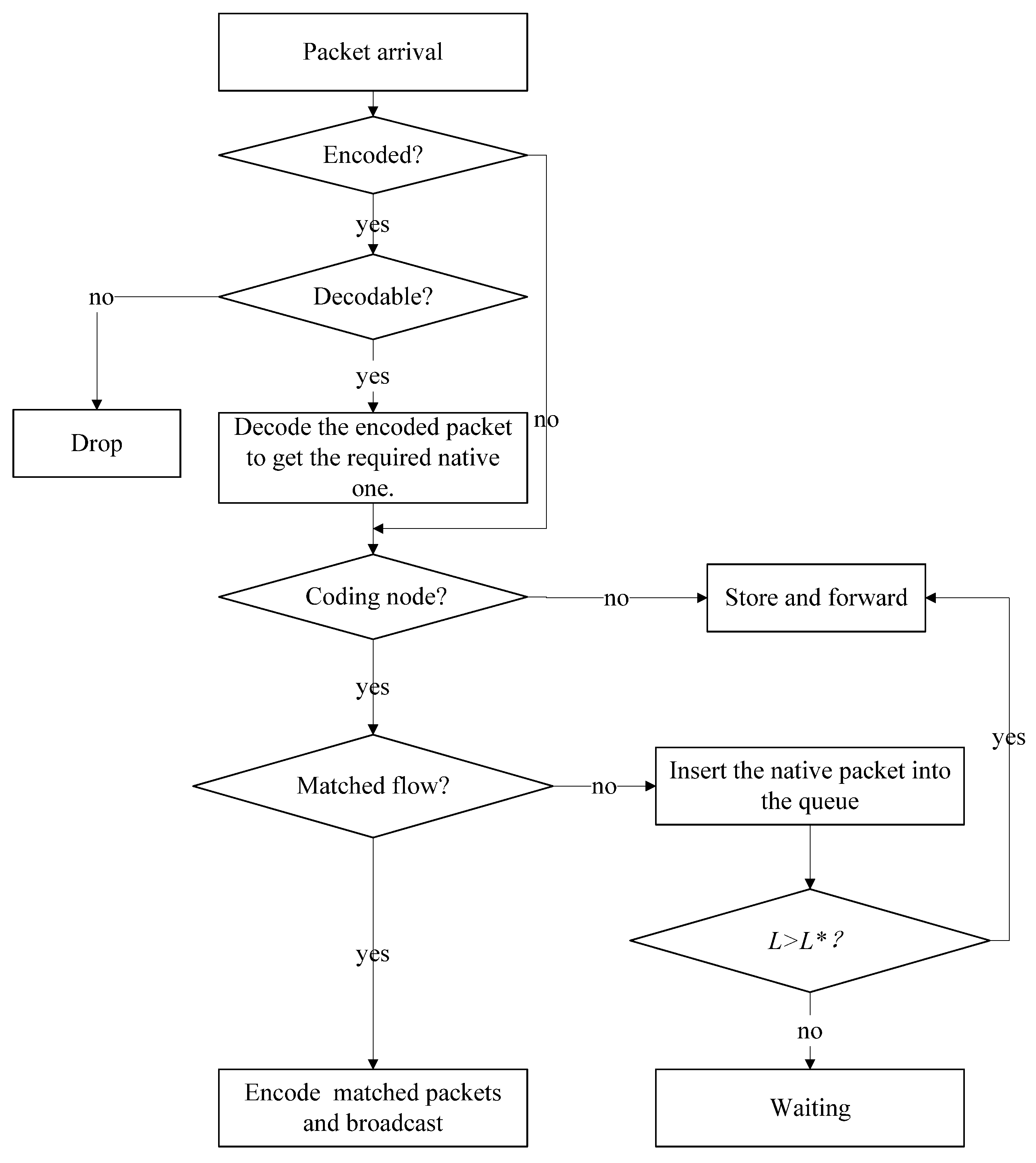
4.3. Performance Analysis
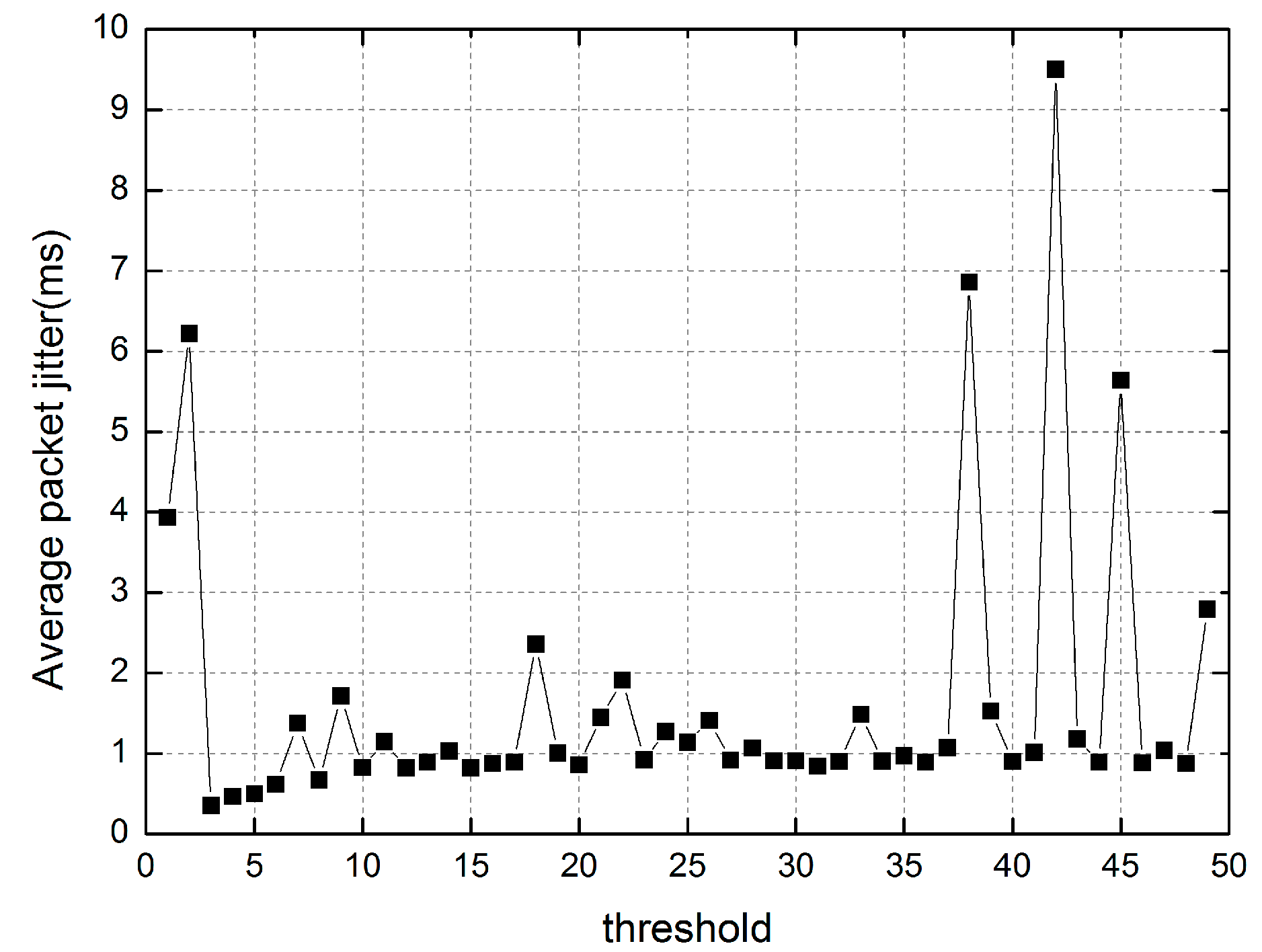
5. Performance Evaluation
5.1. Experiment 1

5.2. Experiment 2
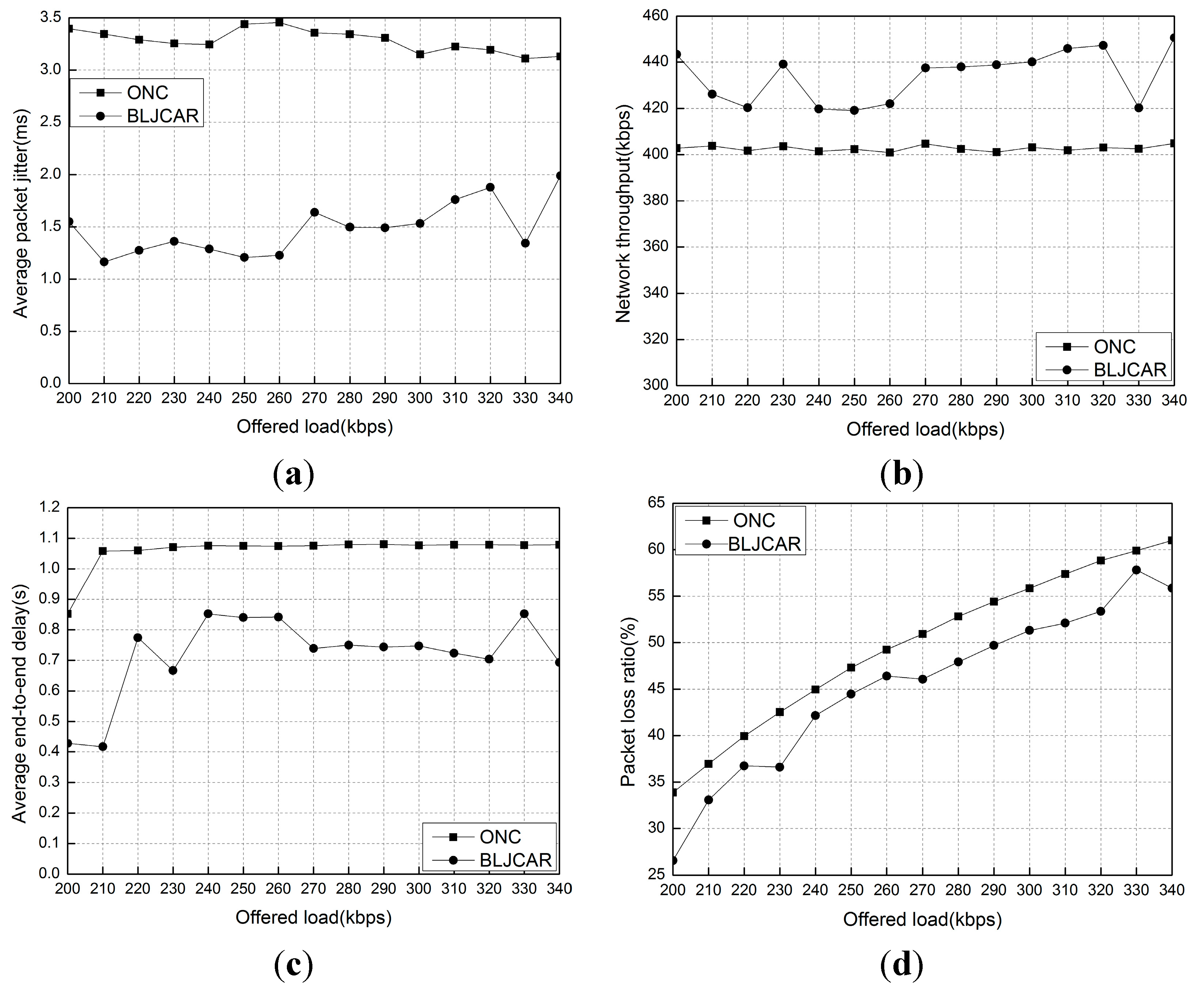
5.3. Experiment 3
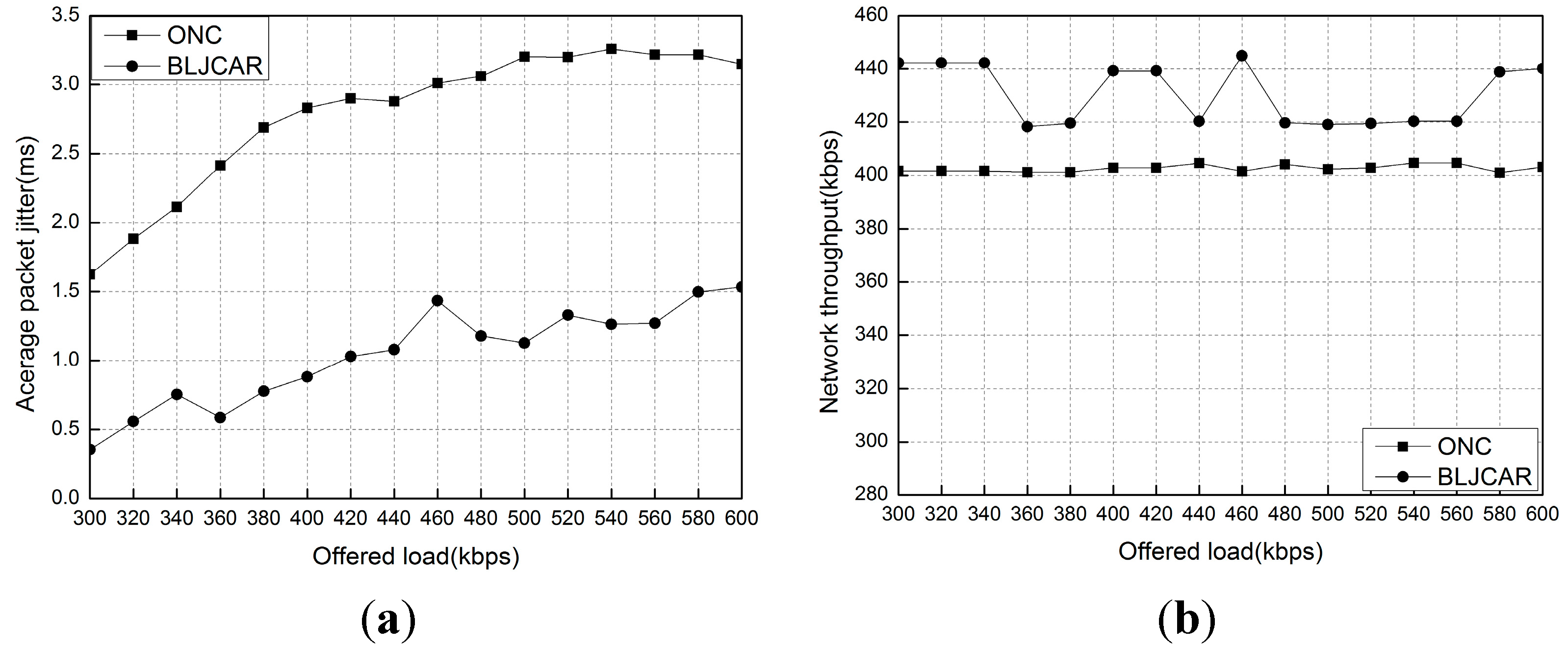

5.4. Experiment 4
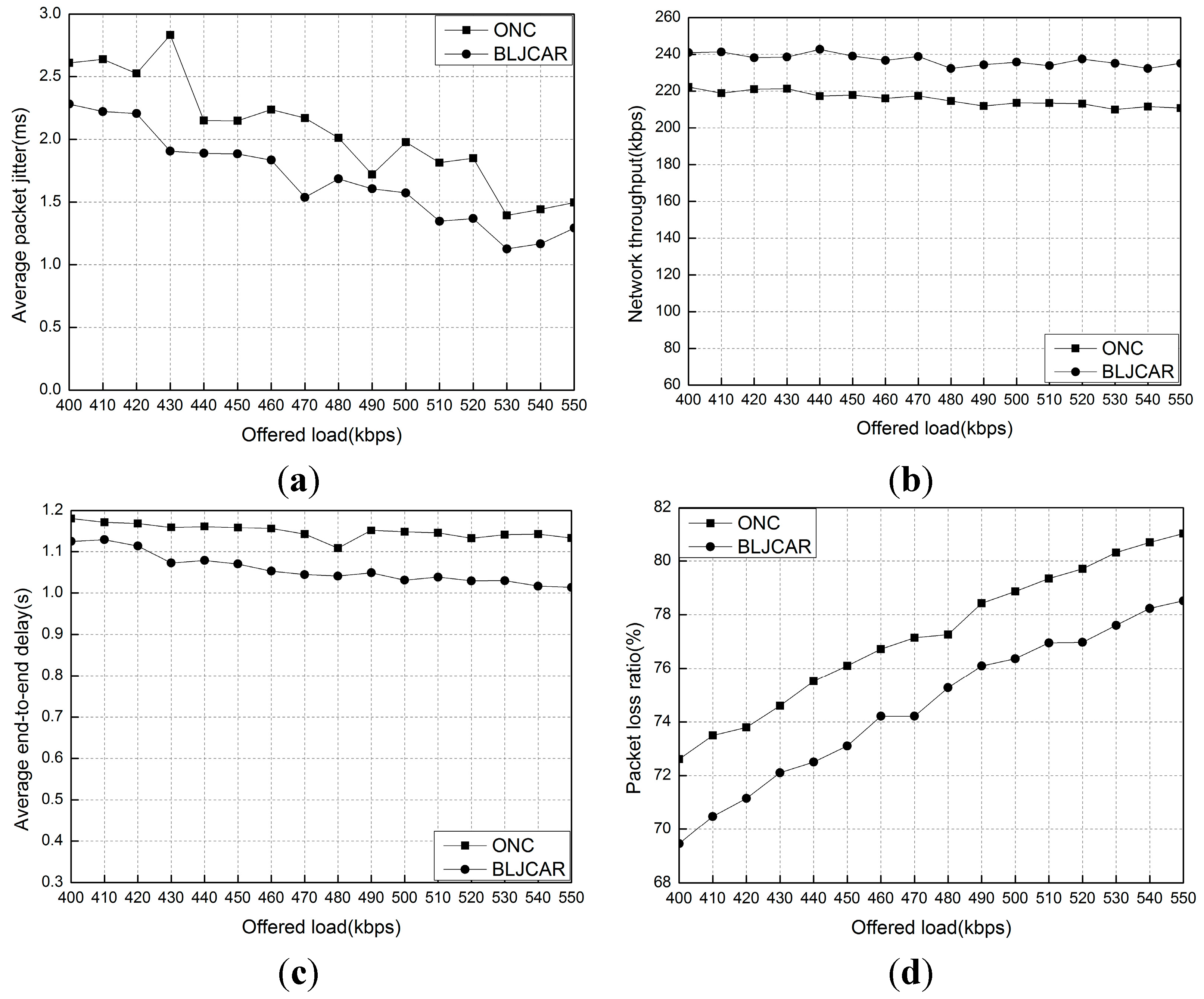
5.5. Experiment 5


5.6. Experiment 6
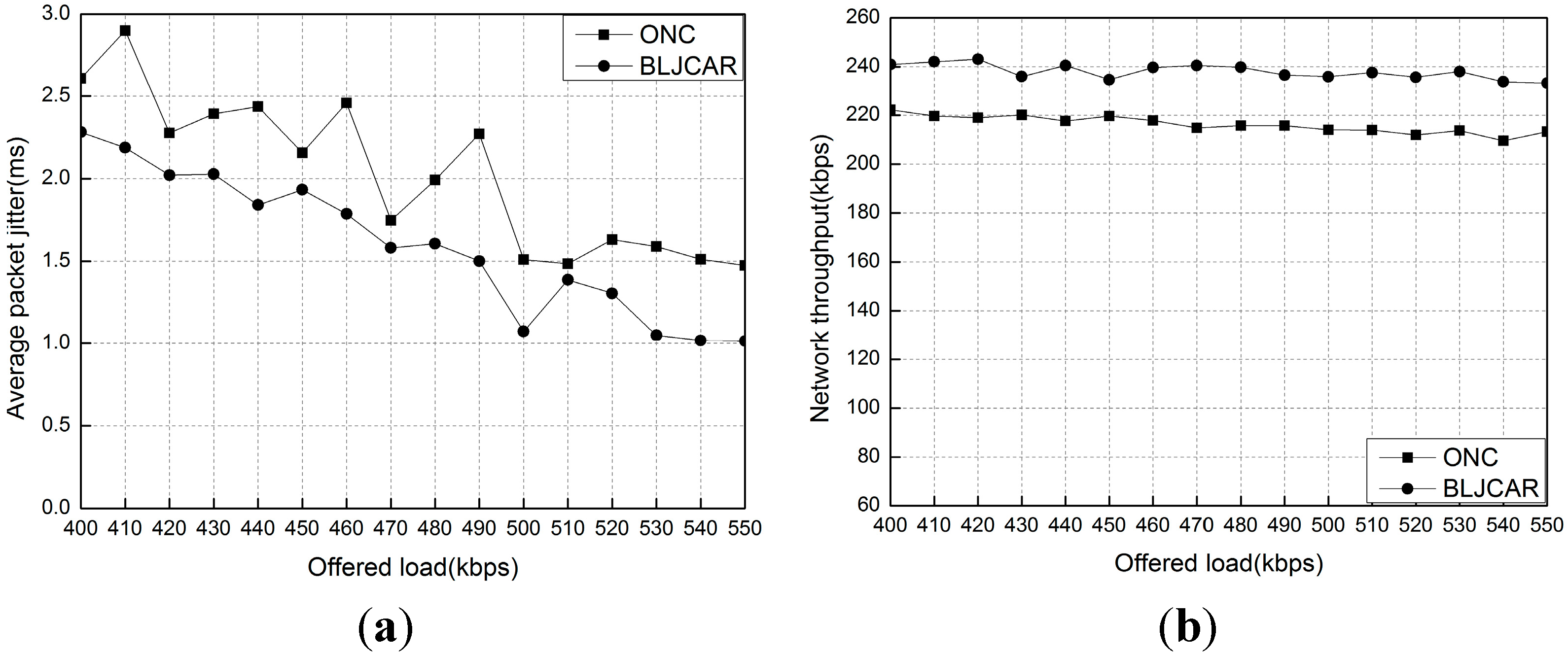
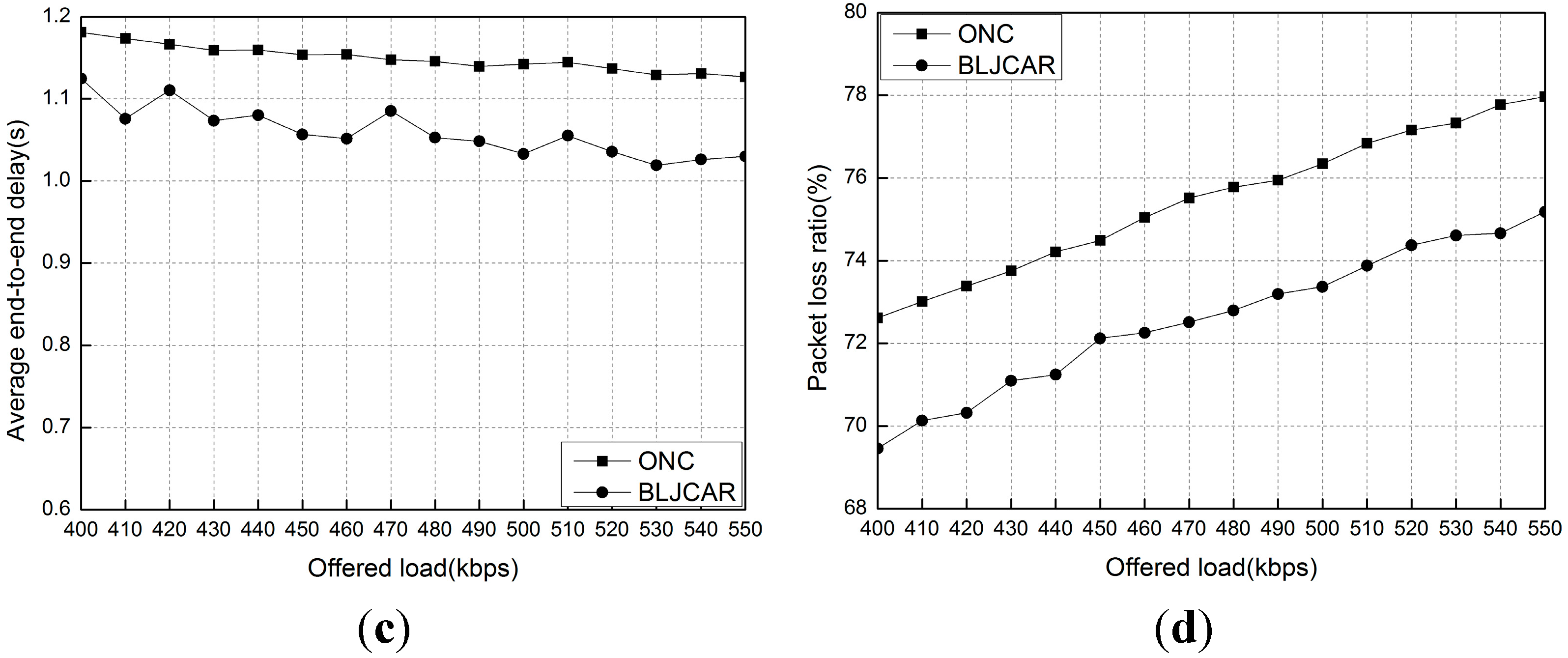
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Ahlswede, R.; Cai, N.; Li, S.Y.R.; Yeung, R.W. Network information flow. IEEE Trans. Inf. Theory 2000, 46, 1204–1216. [Google Scholar] [CrossRef]
- Liu, J.; Goeckel, D.; Towsley, D. Bounds on the gain of network coding and broadcasting in wireless networks. In Proceedings of 26th IEEE International Conference on Computer Communications (INFOCOM), Anchorage, AK, USA, 6–12 May 2007; pp. 724–732.
- Le, J.; Lui, J.C.S.; Chiu, D.M. How many packets can we encode?-an analysis of practical wireless network coding. In Proceedings of 27th IEEE International Conference on Computer Communications (INFOCOM), Phoenix, AZ, USA, 13–18 April 2008; pp. 13–18.
- YuGupta, S.; Vazquez-Castro, M.A. Physical Layer Network Coding Based on Integer Forcing Precoded Computer and Forward. Future Internet 2013, 5, 439–459. [Google Scholar]
- Katti, S.; Rahul, H.; Hu, W.; Katabi, D.; Medard, M.; Crowcroft, J. XORs in the air: Practical wireless network coding. IEEE/ACM Trans. Netw. 2008, 16, 497–510. [Google Scholar] [CrossRef]
- Ni, B.; Santhapuri, N.; Zhong, Z.; Nelakuditi, S. Routing with opportunistically coded exchanges in wireless mesh networks. In Proceedings of Second IEEE Workshop on Wireless Mesh Networks (WiMesh), Reston, VA, USA, 25 September 2006; pp. 157–159.
- Yan, Y.; Zhao, Z.; Zhang, B.T.; Mouftah, H.; Ma, J. Rate-adaptive coding-aware multiple path routing for wireless mesh networks. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), New Orleans, LA, USA, 30 November–4 December 2008; pp. 1–5.
- Le, J.; Lui, J.C.S.; Chiu, D.M. DCAR: Distributed coding-aware routing in wireless networks. IEEE Trans. Mob. Comput. 2010, 9, 596–608. [Google Scholar]
- Peng, Y.; Yang, Y.; Lu, X.; Ding, X. Coding-aware routing for unicast sessions in multi-hop wireless networks. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Miami, FL, USA, 6–10 December 2010; pp. 1–5.
- Yue, H.; Zhu, X.; Zhang, C.; Fang, Y. CPTT: A high-throughput coding-aware routing metric for multi-hop wireless networks. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Anahelm, CA, USA, 3–7 December 2012; pp. 5687–5692.
- Wang, W.; Wu, W.; Guan, Q.; Wang, J. TCAR: A new network coding-aware routing mechanism based on local topology detection. J. Cent. South Univ. 2014, 21, 3178–3185. [Google Scholar] [CrossRef]
- Shao, X.; Wang, C.; Rao, Y. Network Coding Aware QoS Routing for Wireless Sensor Network. J. Commun. 2015, 10, 24–32. [Google Scholar] [CrossRef]
- Shao, X.; Wang, R.; Huang, H.; Sun, L. Load Balanced Coding Aware Multipath Routing for Wireless Mesh Networks. Chin. J. Electron. 2015, 24, 8–12. [Google Scholar] [CrossRef]
- Zhang, J.; Fan, P. Optimal Scheduling for Network Coding: Delay vs. Efficiency. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Miami, FL, USA, 6–10 December 2010; pp. 1–5.
- Chen, W.; Letaief, K.B.; Cao, Z. Buffer-aware network coding for wireless networks. IEEE/ACM Trans. Netw. 2012, 20, 1389–1401. [Google Scholar] [CrossRef]
- Hsu, Y.P.; Abedini, N.; Ramasamy, S.; Gautam, N.; Sprintson, A.; Shakkttai, S. Opportunities for network coding: To wait or not to wait. In Proceedings of the IEEE International Symposium on Information Theory (ISIT), Saint Petersburg, Russia, 31 July–5 August 2011; pp. 791–795.
- Ramasamy, S. Delay-aware Scheduling in Wireless Coding Networks: To Wait or Not to Wait. Master’s Thesis, Texas A&M University, College Station, TX, USA, December 2010. [Google Scholar]
- Mohapatra, A.; Gautam, N.; Shakkottai, S.; Sprintson, A. Network Coding Decisions for Wireless Transmissions with Delay Consideration. IEEE Trans. Commun. 2014, 62, 2965–2976. [Google Scholar] [CrossRef]
- Yen, L.-H.; Cheng, Y.-M. Clustering coefficient of wireless ad hoc networks and the quantity of hidden terminals. IEEE Commun. Lett. 2005, 9, 234–236. [Google Scholar]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lu, C.; Wan, L. A Low-Jitter Wireless Transmission Based on Buffer Management in Coding-Aware Routing. Future Internet 2015, 7, 307-328. https://doi.org/10.3390/fi7030307
Lu C, Wan L. A Low-Jitter Wireless Transmission Based on Buffer Management in Coding-Aware Routing. Future Internet. 2015; 7(3):307-328. https://doi.org/10.3390/fi7030307
Chicago/Turabian StyleLu, Cunbo, and Liangtian Wan. 2015. "A Low-Jitter Wireless Transmission Based on Buffer Management in Coding-Aware Routing" Future Internet 7, no. 3: 307-328. https://doi.org/10.3390/fi7030307




