Development of a Social DTN for Message Communication between SNS Group Members
Abstract
:1. Introduction
2. Related Studies
2.1. DTN Routing
2.2. Creation of a Routing Table
2.3. How to Build an Ad Hoc Network among Android Terminals
2.4. Position of the Proposed Method
3. How to Build a Social DTN
3.1. Service Overview
3.2. DTN Architecture
3.3. How to Create and Share a Community Token
3.3.1. How to Create a Community Token
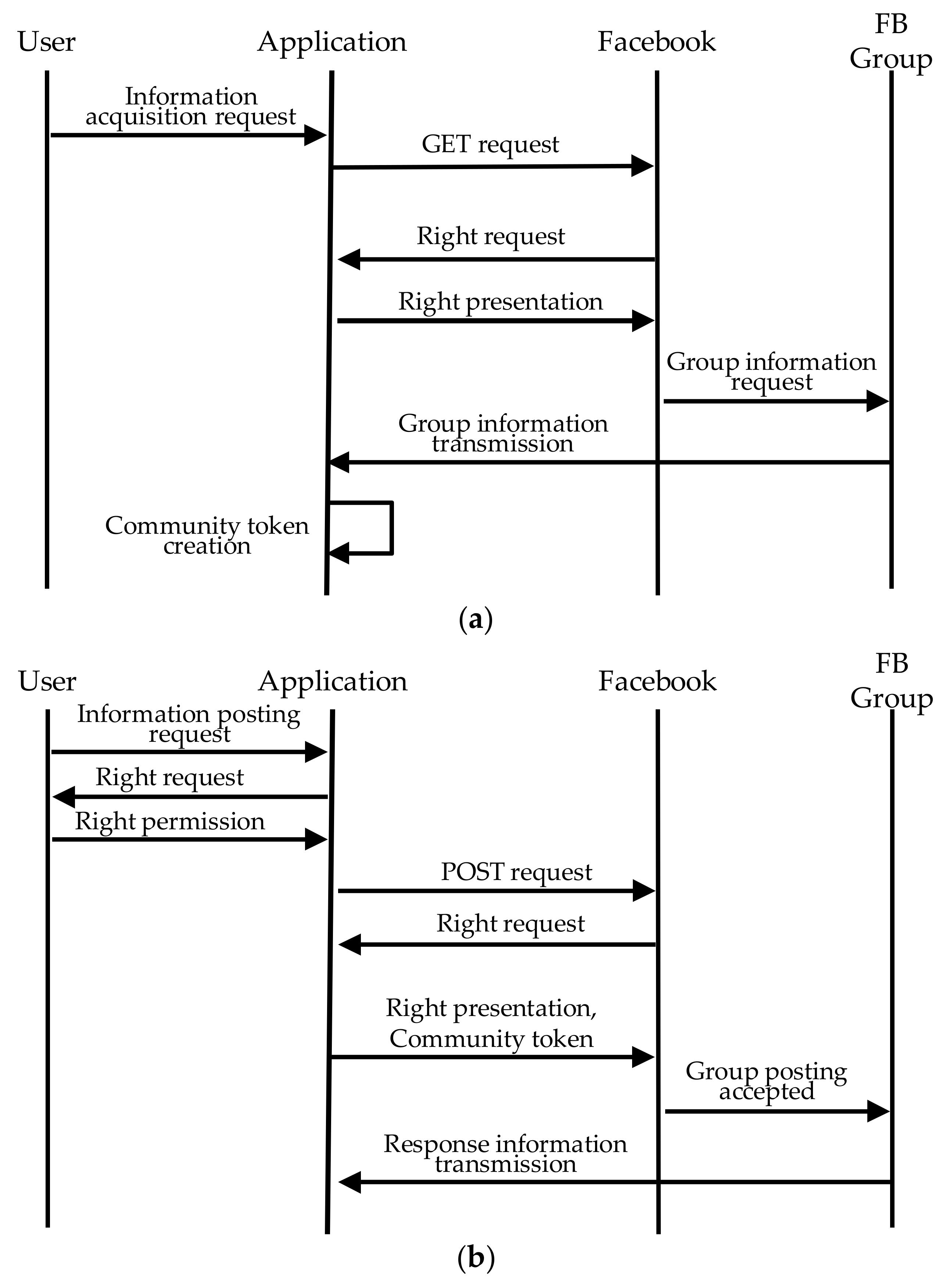
3.3.2. How to Obtain Group Information and Share a Community Token
3.4. DTN Routing Protocol
3.4.1. Routing Message Type and Creation of a Routing Table
3.4.2. Algorithm for Sending Messages
| Algorithm 1. Algorithm for Sending Messages |
|
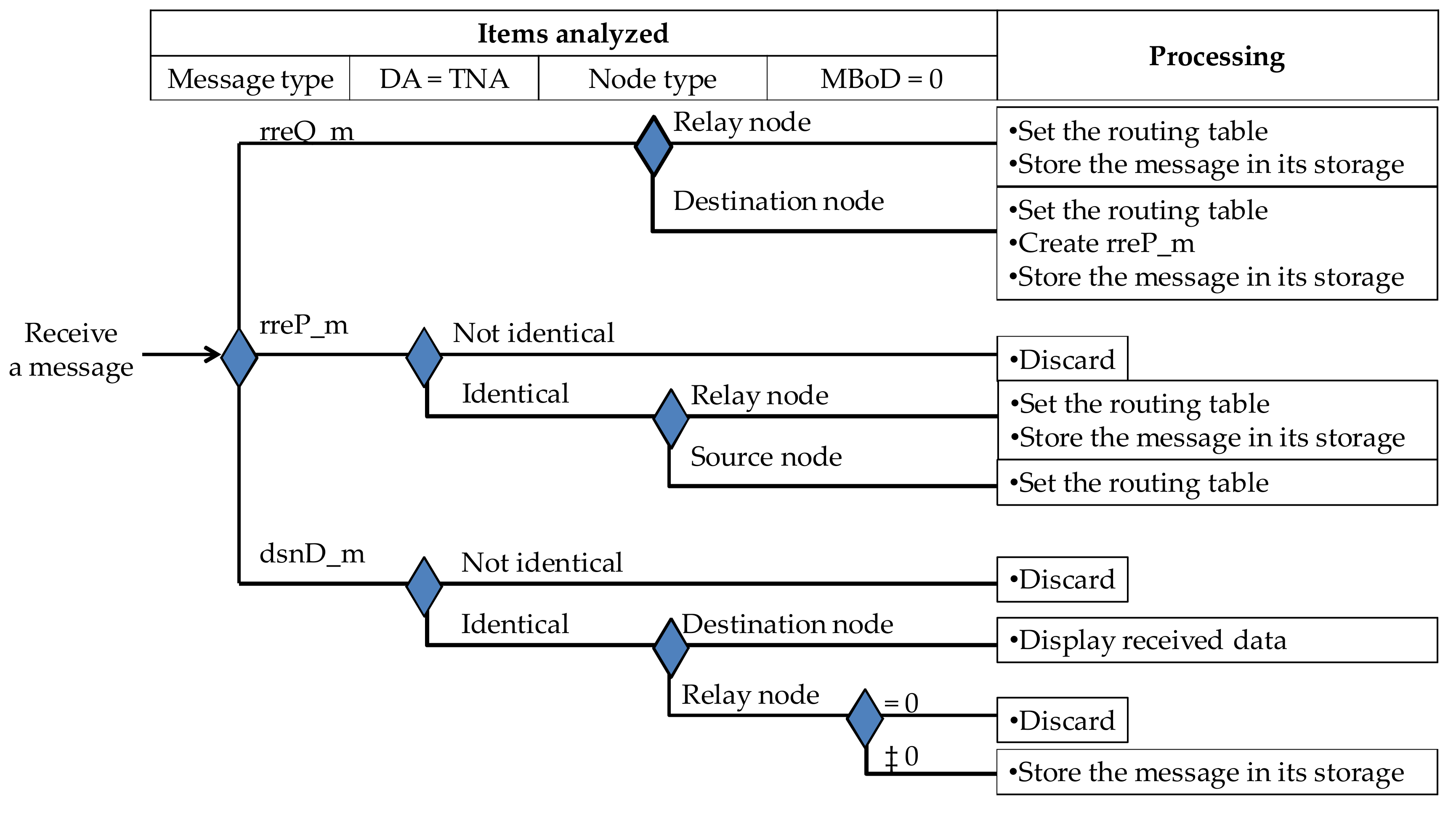
3.4.3. Algorithm for Receiving Messages
| Algorithm 2. Algorithm for Receiving Messages |
|
3.5. Message Sequence for Establishing a Route
4. Development of an Experimental Social DTN Manager Application
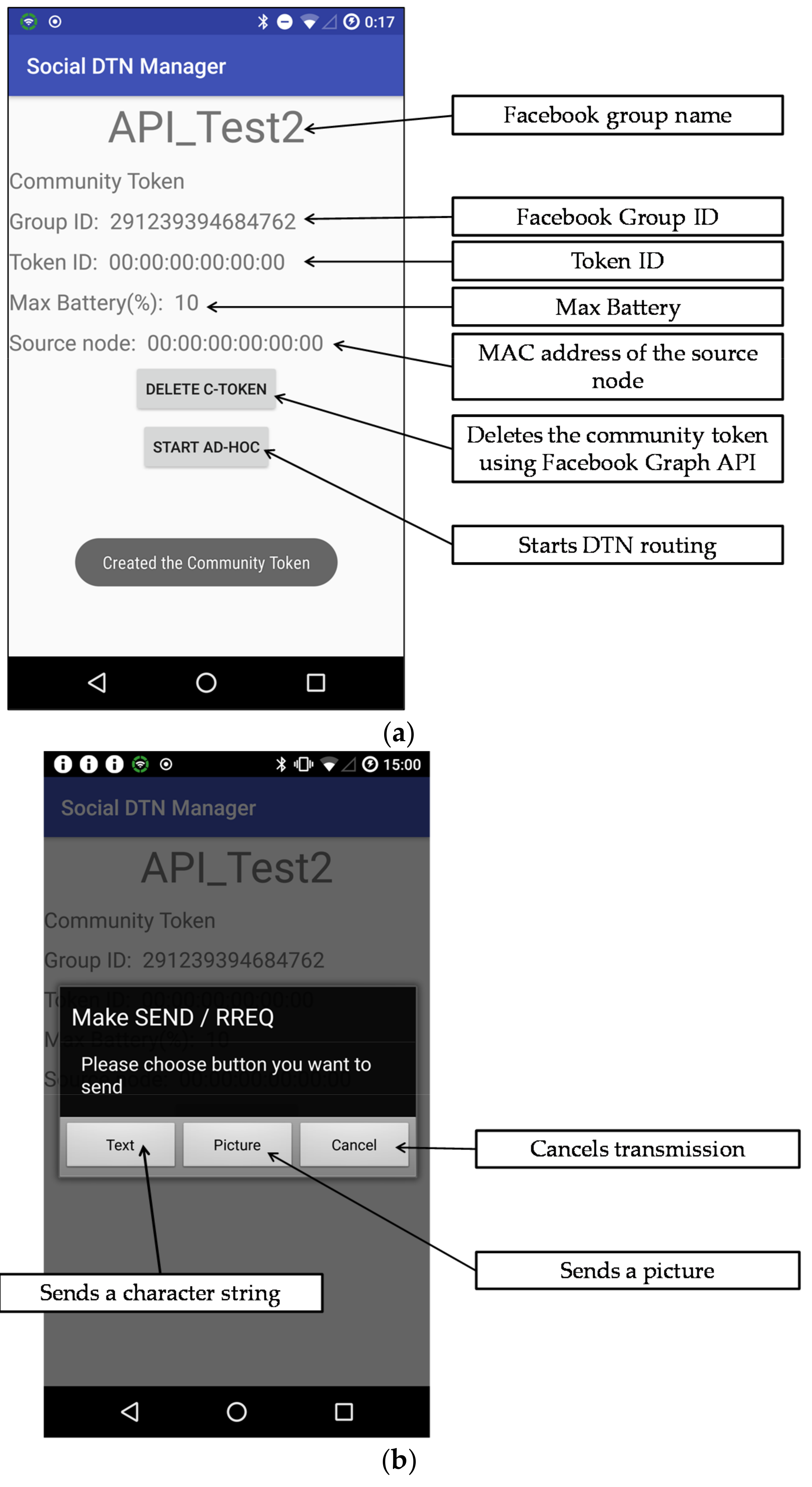
4.1. Functions Implemented in the System
4.2. GUI of the Social DTN Manager
5. Evaluation
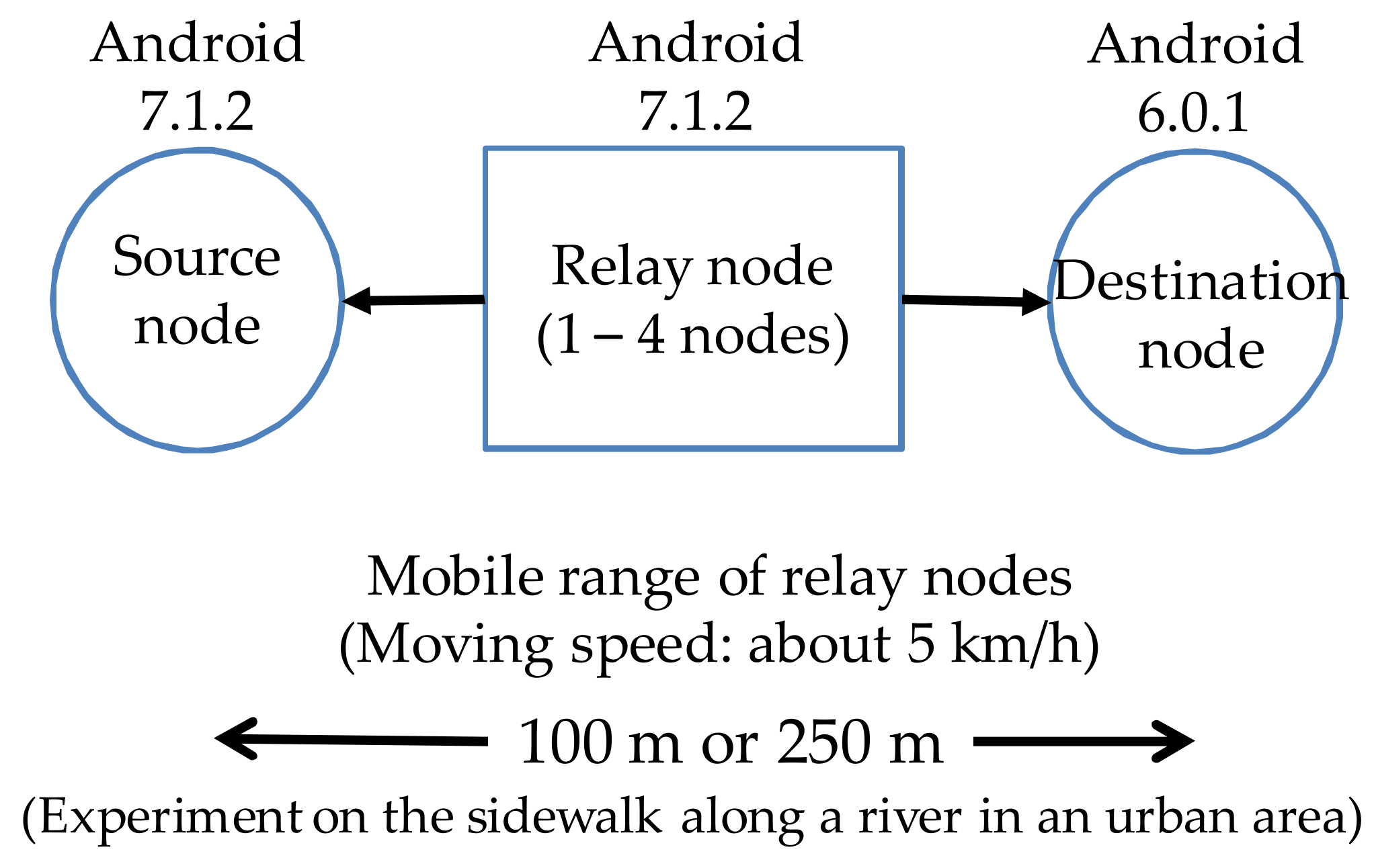
5.1. Operation Test of the Social DTN Manager
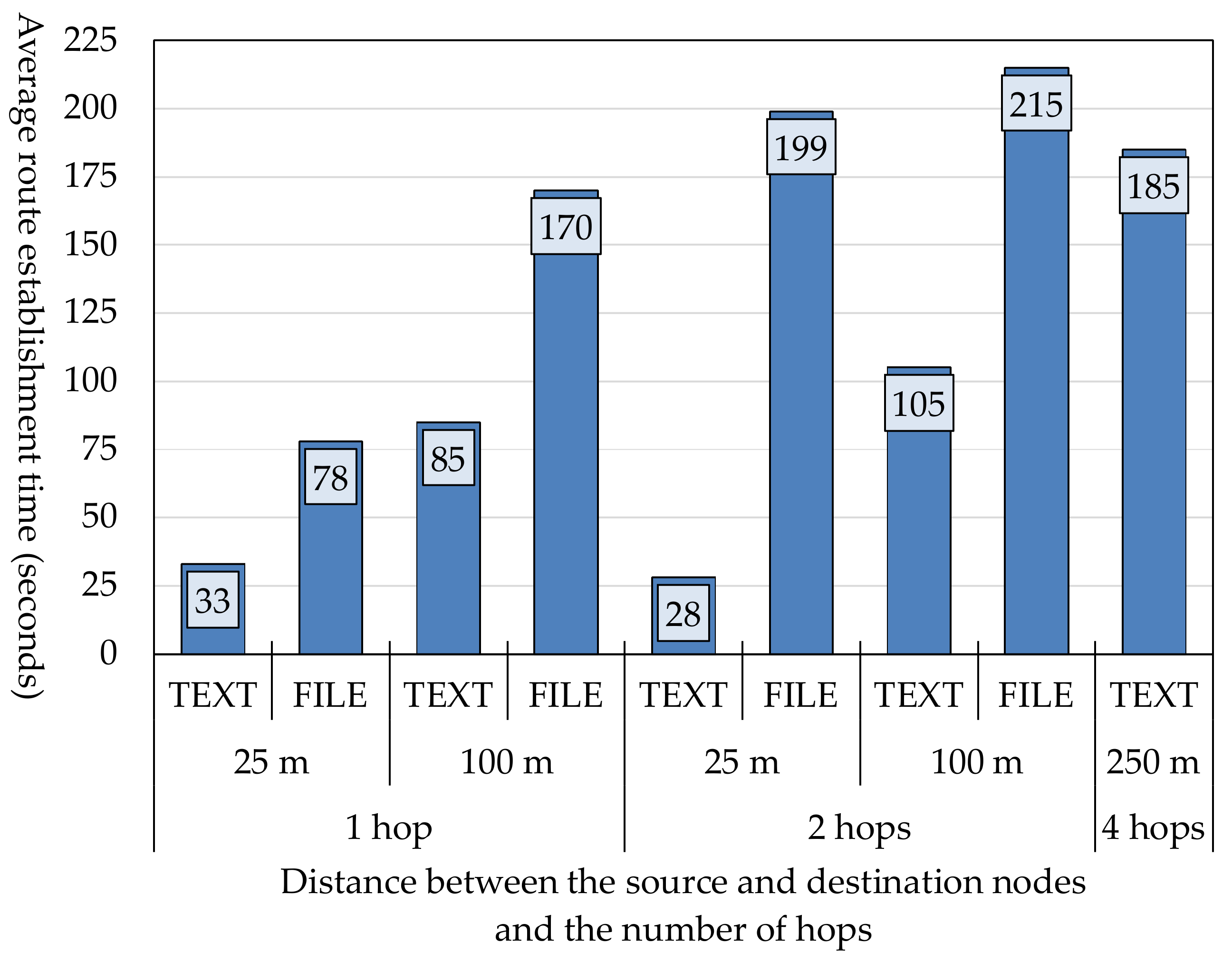
5.2. Route Establishment Time
5.3. Route Establishment Time When There Are Terminals Belonging to Different Groups
5.4. Data Exchange Time
6. Conclusions
Author Contributions
Conflicts of Interest
References
- Papadopoulou, E.; Gallacher, S.; Taylor, N.K.; Williams, M.H.; Blackmun, F.L.; Ibrahim, I.S.; Lim, M.I.; Mimtsoudis, I.; Skillen, P.; Whyte, S. Combining Pervasive Computing with Social Networking for a Student Environment. In Proceedings of the Twelfth Australasian Symposium on Parallel and Distributed Computing, Auckland, New Zealand, 20–23 January 2014; pp. 11–19. [Google Scholar]
- Hirai, K.; Takami, K. Building a Social MANET based on an SNS Community Token. In Proceedings of the 13th International Symposium on Frontiers of Information Systems and Network Applications (FINA-2017), Taipei, Taiwan, 27–29 March 2017. [Google Scholar]
- Tsuru, M.; Uchida, M.; Takine, T.; Nagata, A.; Matsuda, T.; Miwa, H.; Yamamura, S. Delay tolerant networking technology: The latest trends and prospects. IEICE Commun. Soc. Mag. 2011, 2011, 57–68. [Google Scholar] [CrossRef]
- Vahdat, A.; Becker, D. Epidemic Routing for Partially-Connected Ad Hoc Networks; Technical Report CS-2000-06; Duke University: Durham, NC, USA, 2000. [Google Scholar]
- Spyropoulos, T.; Psounis, K.; Raghavendra, C.S. Spray and Wait: An Efficient Routing Scheme for Intermittently Connected Mobile Networks. In Proceedings of the ACM SIGCOMM’05 Workshops, Philadelphia, PA, USA, 22–26 August 2005. [Google Scholar]
- LeBrun, J.; Chuah, C.; Ghosal, D.; Zhang, M. Knowledge-Based Opportunistic Forwarding in Vehicular Wireless Ad Hoc Networks. In Proceedings of the IEEE Vehicular Technology Conference (VTC 2005-Spring), Stockholm, Sweden, 30 May–1 June 2005. [Google Scholar]
- Zhao, W.; Ammar, M.; Zegura, E. A Message Ferrying Approach. In Proceedings of the 5th ACM International Symposium on Mobile Ad Hoc Networking and Computing (MobiHoc’04), Tokyo, Japan, 24–26 May 2004; pp. 187–198. [Google Scholar]
- Okamoto, K.; Takami, K. Routing Based on Information about the Routes of Fixed-Route Traveling Nodes and on Destination Areas Aimed at Reducing the Load on the DTN. Future Internet 2016, 8, 15. [Google Scholar] [CrossRef]
- Ippisch, A.; Graffi, K. Infrastructure Mode Based Opportunistic Networks on Android Devices. In Proceedings of the IEEE 31st International Conference on Advanced Information Networking and Applications (AINA 2017), Taipei, Taiwan, 27–29 March 2017. [Google Scholar]
- Ippisch, A.; Sati, S.; Graffi, K. Device to device communication in mobile Delay Tolerant networks. In Proceedings of the 21st International Symposium on Distributed Simulation and Real Time Applications (DS-RT), Rome, Italy, 18–20 October 2017; pp. 91–98. [Google Scholar]
- Lindgren, A.; Doria, A.; Schel’en, O. Probabilistic Routing in Intermittently Connected Networks. ACM SIGMOBILE Mobile Comput. Commun. Rev. 2003, 7, 19–20. [Google Scholar] [CrossRef]
- Facebook for Developers. Available online: https://developers.facebook.com/docs/graph-api/overview/ (accessed on 6 January 2018).
- Google Developers. Available online: https://developers.google.com/nearby/connections/overview (accessed on 6 January 2018).
- Boldrini, C.; Conti, M.; Jacopini, J.; Passarella, A. HiBOp: A History Based Routing Protocol for Opportunistic Networks. In Proceedings of the IEEE International Symposium on World of Wireless, Mobile and Multimedia Networks (WoWMoM’07), Helsinki, Finland, 18–21 June 2007; pp. 1–12. [Google Scholar]
- Cyanogenmod. Available online: http://web.archive.org/web/20160410142436 (accessed on 26 February 2018).
- Thinktube Inc. Available online: http://www.thinktube.com/android-tech/46-android-wifi-ibss (accessed on 26 February 2018).
- Debian Kit for Android. Available online: http://sven-ola.commando.de/repo/debian-kit-en.html (accessed on 26 February 2018).
- RFC 3651—Ad Hoc On-Demand Distance Vector (AODV) Routing. Available online: https://www.ietf.org/rfc/rfc3561.txt (accessed on 21 March 2018).
- Android Studio, SDK Platform Tools Release Notes. Available online: https://developer.android.com/studio/releases/platform-tools.html (accessed on 4 March 2018).
- Facebook Android SDK. Available online: https://developers.facebook.com/docs/android?locale=en_US (accessed on 4 March 2018).
- Google Play Service API (Nearby). Available online: https://developers.google.com/android/guides/setup (accessed on 4 March 2018).
- Github Google-Gson. Available online: https://github.com/google/gson (accessed on 4 March 2018).








| Community Identification | Routing Table | Routing Table Creation | Criteria Used to Determine Flooding | Routing Method | |
|---|---|---|---|---|---|
| None | None | None: flooding of messages to all adjacent nodes | Epidemic [4] | ||
| Flooding of messages to nodes up to a certain number of hops (a certain number of copies) | Spray and Wait [5] | ||||
| Distance to the destination node | Location-based [6] | ||||
| Motion vector to the destination node | motion vector scheme (MoVe) [6] | ||||
| Used | Proactive | Fixed | Routing table (includes encounter probability calculation type, social-context-awareness type) | Message ferry [7], Routing based on traveling route information [8] | |
| Encounter information sharing | Meta information exchange [9,10], PRoPHET [11], HiBOp [14] | ||||
| Present | Reactive | Proposed method | |||
| Implementation | Detailed Method | Usage Conditions | Position |
|---|---|---|---|
| OS modification | Custom operating system (OS) + patches [15,16] |
| Existing methods |
| Building a virtual environment called “Debian” [17] | |||
| Application | Google Nearby Connections API [13], which is independent of OS |
| Proposed method |
| Name | Overview | Usage |
|---|---|---|
| Group ID | The ID used in the social networking service (SNS) is used. | This is used to identify a group. |
| Token ID | The initial value is the MAC (Media Access Control) address of the source node. The value is incremented by one each time the community token is updated. | This is used to determine which community token is new. |
| Max-Battery of Device (MBoD) | This is the maximum level of battery power consumption in communication. This is reduced by the level of battery power consumed during the DTN communication. | If the value of a node becomes “0”, the node is eliminated from routing in order to avoid excessive use of resources. |
| Source node address | This is the MAC address of the source node that has created the community token. | This is used for routing. (See Section 3.4 for detail). |
| Type | rreQ_m | rreP_m | dsnD_m | |
|---|---|---|---|---|
| Element | ||||
| Message type m_type (1 byte) | Yes | Yes | Yes | |
| Route establishment request ID (8 bytes) | Yes | Yes | Yes | |
| Destination node address DA (17 bytes) | Yes | Yes | Yes | |
| Source node address SA (17 bytes) | Yes | Yes | Yes | |
| Transmitted data (n bytes) | No | No | Yes | |
| Element | Remarks |
|---|---|
| Terminal node address (TNA) | DA and SA, which are elements in each message |
| Relay node address (RNA) | The address of the adjacent node that has received rreQ_m or rreP_m that contains TNA. The SA of that message is set in TNA. The address of the adjacent node is set in RNA. |
| Function Name | Program Size | Functional Overview |
|---|---|---|
| Linkage with Facebook | 853 lines | Enables the user to use his/her own Facebook account to browse, post or delete messages in the group he/she belongs to as the administrator. |
| Terminal information acquisition | 191 lines | Obtains the terminal’s MAC address and MBoD. |
| Community token management | 639 lines | Uploads or downloads a community token created using terminal information to or from the Facebook group. |
| DTN routing | 2087 lines | Establishes an ad hoc communication link and performs routing. |
| Text and file exchange | 244 lines | Exchanges text and files with terminals to which a communication link has been established. |
| Classification | Item | Contents |
|---|---|---|
| Development environment | Machine | DELL OptiPlex 3040 |
| OS | Windows10 Pro | |
| Application development software | Android Studio 3.0 (Gradle version 4.1) | |
| Build tool | API 26.0.2: Android8.0 (Oreo) [19] | |
| Application execution conditions | Application name | Social DTN Manager |
| Operating environment | Android sdk 15 (Android 4.3) or higher | |
| Application type | Android SDK, Java | |
| Third-party plug-ins | Facebook Android SDK [20] Google Play Service API (nearby) [21] Google gson [22] |
| Terminal Model | OS Version | Usage |
|---|---|---|
| Nexus5 | Android 7.1.2 | Source node |
| HUAWEI Y6 SCL-L02 IMEI:861105030008770 | Android 7.1.2 | Relay node |
| HUAWEI Y6 SCL-L02 IMEI: 861105030097666 | Android 7.1.2 | Relay node |
| BLUEDOT BNP-500 Serial: ZLY5CUNNQS6HUWK7 | Android 4.4.2 | Relay node |
| BLUEDOT BNP-500 Serial: OVTSEY79QO4HZT8D | Android 4.4.2 | Relay node |
| NEC PC-TE507FAW | Android 6.0.1 | Destination node |
| Item | Value |
|---|---|
| Number of terminals | 3, 4 or 6 |
| Number of hops (i.e., number of relay nodes) | 1, 2 or 4 |
| Number of experiments | 3 experiments per pattern |
| Use of different community tokens | None |
| Item | Value |
|---|---|
| Number of terminals | 5 or 6 |
| Number of hops | 1 or 2 |
| Number of experiments | 2 per pattern |
| Number of terminals belonging to a different group | 1 advertising terminal and 1 discovering terminal |
| Number of different types of community token | 3 |
| Item | Value |
|---|---|
| Number of terminals | 3, 4 or 6 |
| Number of hops | 1, 2 or 4 |
| Number of experiments | 3 per pattern |
| Distance between the source node and the destination node | 25 or 100 m (250 m only in the case of 4 hops) |
| Exchanged data | Character string (TEXT = 55 bytes), Image file (FILE = 1 Mbytes) |
| Presence of different community tokens | None |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Takasuka, H.; Hirai, K.; Takami, K. Development of a Social DTN for Message Communication between SNS Group Members. Future Internet 2018, 10, 32. https://doi.org/10.3390/fi10040032
Takasuka H, Hirai K, Takami K. Development of a Social DTN for Message Communication between SNS Group Members. Future Internet. 2018; 10(4):32. https://doi.org/10.3390/fi10040032
Chicago/Turabian StyleTakasuka, Hidenori, Koichi Hirai, and Kazumasa Takami. 2018. "Development of a Social DTN for Message Communication between SNS Group Members" Future Internet 10, no. 4: 32. https://doi.org/10.3390/fi10040032





