1. Introduction
Delaunay mesh generation of non-smooth domains such as piecewise smooth surfaces and complexes is a difficult challenge. Aided by recent developments in sampling theory and computational topology, Chew’s furthest point strategy [
1,
2] (Delaunay refinement) has been applied to generate Delaunay meshes for smooth surfaces with provable guarantees [
3,
4]. The lack of global smoothness poses two main difficulties in extending these methods to non-smooth domains. First, the sampling theory developed for smooth surfaces breaks down for non-smooth surfaces. Secondly, small input angles possibly present at non-smooth regions pose problems for the termination of Delaunay refinement [
5].
Boissonnat and Oudot [
6] gave a provable algorithm for a class of non-smooth surfaces called Lipschitz-surfaces. They showed that their algorithm for smooth surface meshing [
3] extends to this class only if input angles are sufficiently large. Unfortunately, this approach failed to admit small input angles which limited the input class. Rineau and Yvinec [
7] implemented an algorithm for meshing volumes bounded by piecewise smooth surfaces; their approach also suffers from an angle constraint. Recently Cheng, Dey and Ramos [
8] proposed an approach that completely removed any constraint on input angles. As a result their algorithm could accommodate large class of input domains called piecewise smooth complexes (PSCs). This class includes polyhedral domains, smooth and piecewise smooth surfaces, and even non-manifolds.
The algorithm of [
8] uses the idea of protecting non-smooth curves and vertices in the input complex with balls. This idea already gave good results in the polyhedral case [
9,
10,
11]. A novelty introduced by Cheng
et al. is that they turn the balls into weighted points and then carry out the mesh refinement in the weighted Delaunay triangulation [
12,
13]. Notwithstanding its theoretical success, practical relevance of this algorithm remains questionable. It employs some expensive numerical computations that are hard to implement. Unless these computations are removed, one cannot expect a practical solution for Delaunay mesh generation of PSCs. The goal of this paper is to design a refinement strategy without expensive predicates so that it becomes implementation-friendly and practical.
Bottleneck. Consider a smooth surface given by an implicit equation. To generate a meaningful mesh for this surface, one needs to sample it at a scale that captures its smallest local variations. One approach would be to
guess a scale and sample the surface with it. If the guess is right, sampling with the furthest point strategy gives a mesh with provable guarantees as shown by Boissonnat and Oudot [
3]. A second approach would be to compute a version of the local length scales and mesh the surface with those scales. The algorithm of Cheng
et al. [
8] works on this latter principle. It computes how a curve or a surface varies normal-wise around a point. It also computes separation distances between different elements (vertices, curves, and surfaces) to capture separation feature size (gap size) in the sense of [
9,
14]. These assumed powerful numerical primitives allow Cheng
et al. to determine the size of the protecting balls with certain desirable properties and allow them to sample surface patches at appropriate length scales. Unfortunately, these computations are expensive and are hard to implement which makes the algorithm impractical.
Solution. To circumvent the problem we follow the guessing approach. We would like to guarantee that even if the guess is incorrect, the algorithm terminates and outputs a mesh which approximates the input complex at a coarse level. A main difficulty in this approach is to formulate a unified refinement strategy that captures the input topology correctly when the guessed scale is right and outputs a mesh with some reasonable properties all the time. To reach this goal we formulate a disk condition that says that the output mesh should have a topological disk formed by triangles around each vertex. This disk condition drives the refinement, that is, we go on refining protecting balls or surface meshes if this disk condition fails. If this refinement terminates, the disk condition necessarily holds for the output mesh. Then, by PL topology, the output Delaunay mesh restricted to each manifold surface patch is a manifold. Furthermore, the input incidence structure among different elements in the PSC is maintained. The output may not be homeomorphic to the input since a small feature such as a small handle may not be detected at the length scale the algorithm is asked to operate. However, a homeomorphic meshing is guaranteed when the supplied scale is sufficiently small. Actually, in practice, the disk condition usually suffices to provide a homeomorphism.
One of our main tasks is to prove that the refinement always terminates. To this end we use the following result. If the protecting balls are sufficiently small and satisfy some
separation properties (conditions C1-C3 in
Section 2.), then the disk condition holds if the restricted Delaunay triangles are sufficiently small. Therefore, the failure of the disk condition signals either balls do not satisfy separation properties, or are large, or triangles are large. The way we compute the protecting balls, failure of separation properties also implies that they are large. In essence, if the disk condition fails, either a ball or a triangle is too large. The algorithm refines the larger of the two and hence guarantees that neither a protecting ball nor a triangle gets arbitrarily small ensuring termination. One may observe that, this strategy does not allow adaptive mesh sizing. However, one may regulate the input scale to produce meshes at different levels of resolution.
Perhaps the most important ingredient in this approach is to maintain a set of protecting balls with the separation properties. It turns out that it is difficult to ensure one of these properties exactly (condition C3) when the balls are large. Instead we maintain a more relaxed condition which implies the desired property when the balls are sufficiently small.
We have implemented our algorithm in this paper. In an earlier attempt we tried to mesh with the disk condition but pre-computed the balls with a small radius chosen heuristically [
15]. The code failed in cases where the pre-selected size of the balls was wrong. The approach in this paper allows the refinement algorithm to determine the balls automatically instead of pre-computing them. We report experimental results for our protection algorithm and meshing in
Section 5. The code and a video explaining the experimental results have been released [
16].
1.1. Domain
Throughout this paper, we assume a generic intersection property that a k-manifold , , and a j-manifold , , intersect (if at all) in a -manifold if and . We will use both geometric and topological versions of closed balls. A geometric closed ball centered at point with radius , is denoted as . We use and to denote the interior and boundary of a topological space , respectively.
The domain D is a piecewise smooth complex (PSC) where each element is a compact subset of a smooth () k-manifold, . Each element is closed and hence contains its boundaries. For simplicity we assume that each element has a non-empty boundary (used in Lemma 8, this restriction can be removed by some added complication in the initialization of the algorithm). We use to denote the subset of all k-dimensional elements, the kth stratum. is a set of vertices; is a set of curves called 1-faces; is a set of surface patches called 2-faces. For , we use to denote .
The domain D satisfies the usual proper requirements for being a complex: (i) interiors of the elements are pairwise disjoint and for any , ; (ii) for any , either or is a union of elements in D. We use to denote the underlying space of D. For , we also use to denote the underlying space of .
1.2. Complexes
We will be dealing with weighted points and their Delaunay and Voronoi diagrams. A weighted point p with weight is represented as a ball . The squared weighted distance of any two points p and q is where and are the weights of p and q respectively. With this definition, an unweighted point has a distance of from p. Under the distance metric , one can define weighted versions of Delaunay and Voronoi diagrams. For a weighted point set , let and denote the weighted Voronoi and Delaunay diagrams of S respectively. Each diagram is a cell complex where each k-face is a k-polytope in and is a k-simplex in . Each k-simplex ξ in is dual to a -face in and vice versa.
Let
S be a point set sampled from
. For any sub-collection
we define
to be the Delaunay subcomplex restricted to
, i.e., each simplex
, called a restricted simplex, is the dual of a Voronoi face
where
. By this definition, for any
,
denotes the Delaunay subcomplex restricted to
σ, and
An
i-face
should be meshed with
i-simplices. However,
may have lower dimensional simplices not incident to any restricted
i-simplex. Therefore, we compute special sub-complexes of restricted complexes. Define the following
i-dimensional subcomplexes (see
Figure 1):
is an
i-simplex or a sub-simplex of an
i-simplexand
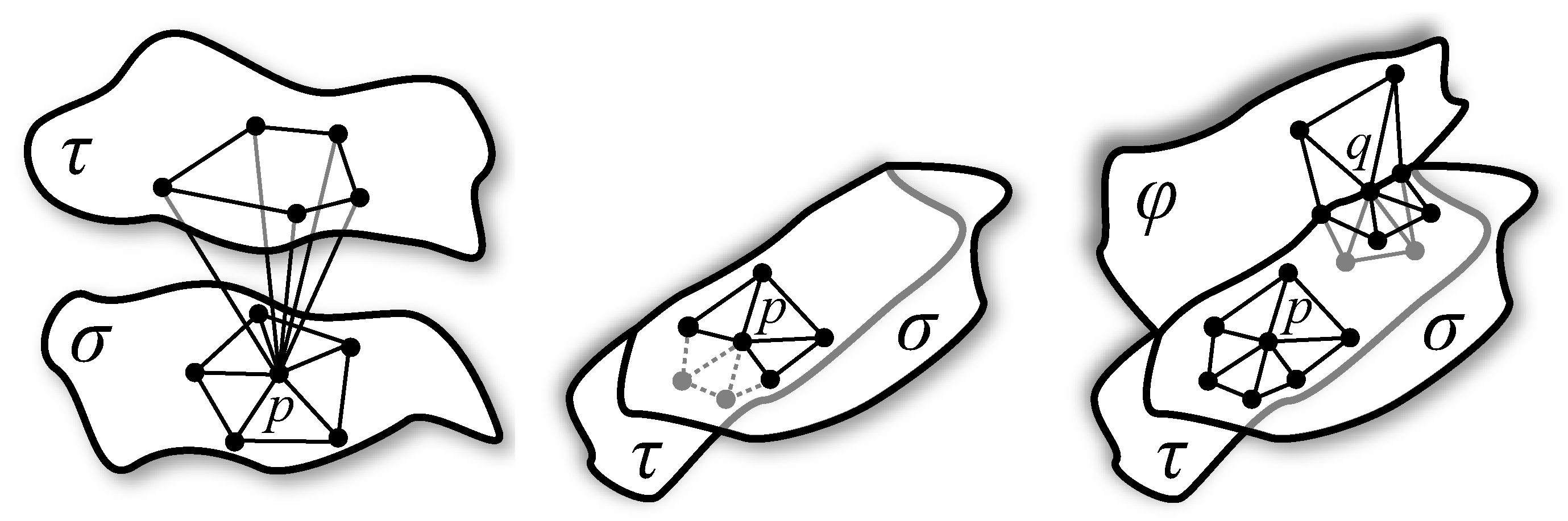
Figure 1.
(left) and (right) There is one extra edge in which is not in .
Figure 1.
(left) and (right) There is one extra edge in which is not in .
2. Protection and Refinement
The meshing algorithm computes a set of balls protecting 1-faces. Unlike [
8], the protecting balls are adjusted on the fly as refinement proceeds. It inserts points in 2-faces to refine the triangulation. The protecting balls and the triangulation are refined simultaneously either to satisfy a disk condition or to achieve a refinement level dictated by an input scale parameter. In what follows all skipped proofs appear in the appendix.
2.1. Covering 1-faces
Let
denote the curve segment oriented from
x to
y on any 1-face
σ. In this notation
where
σ is oriented from the end point
u to the other end point
v. Let
be a ball with
. The intersection
is a set of curve segments. Among them the curve segment containing
c is called the
segment of b in σ,
, see
Figure 2. Two balls
b and
with their centers
c and
respectively on a 1-face
σ are
adjacent if
does not contain any other ball center. In this case the corresponding weighted vertices of
b and
are also called
adjacent. Any two balls or weighted vertices that are not adjacent are called
non-adjacent. We use
to denote the Euclidean distance between two points
and use
to denote the length of a curve segment
. Let
be a set of balls that protect
σ where
with
. We require that the balls satisfy the following conditions:
- (C1)
and are centered at u and v respectively. These will be called the vertex balls.
- (C2)
σ is covered by the balls, that is, and any two adjacent balls and intersect deeply, that is, where .
- (C3)
No point in is contained in a ball non-adjacent to .
Notice that the choice of the constant in C2 is a little arbitrary. We need only a factor of in the expression and a follow-up analysis with other constants are also possible.
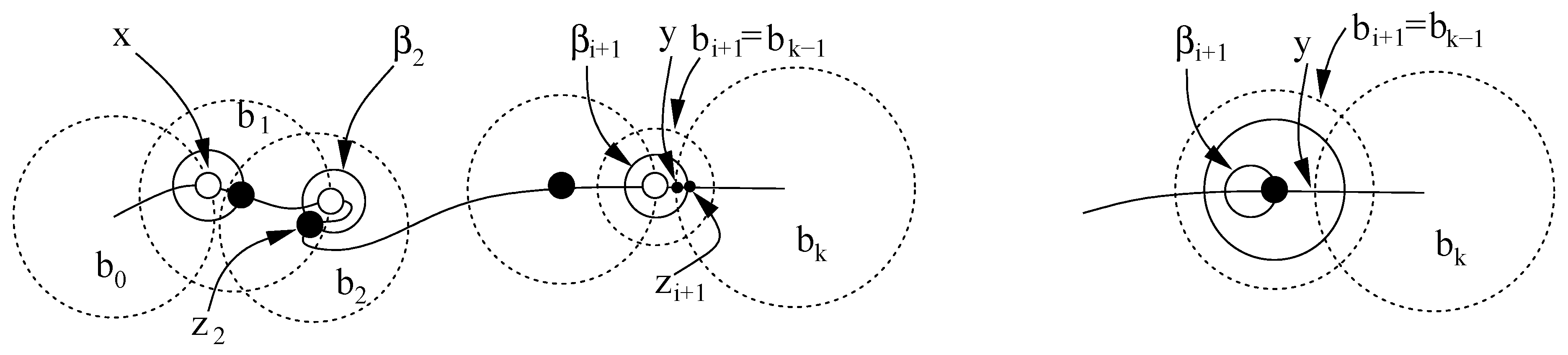
Figure 2.
Covering 1-faces : (left) A 1-face σ between u and v is being protected. The ball b shown with solid boundary has as the curve segment between and . The balls satisfy C1 and C2 but intersect arbitrarily. (right) Balls are refined and they start satisfying separation properties C1-C3.
Figure 2.
Covering 1-faces : (left) A 1-face σ between u and v is being protected. The ball b shown with solid boundary has as the curve segment between and . The balls satisfy C1 and C2 but intersect arbitrarily. (right) Balls are refined and they start satisfying separation properties C1-C3.
We will maintain a point set with the following properties throughout the algorithm: all points in S except those in are unweighted and no unweighted point has a negative weighted distance to any other point. This means each unweighted point has non-empty. We call such a point set admissible.
It is worthwhile to note that one of the consequences of conditions C1-C3 would be the following result which would imply R2 in Lemma 2.
Lemma 1 Let S be an admissible point set satisfying conditions C1-C3. Let p and q be adjacent weighted vertices on a 1-face σ. is the only Voronoi facet in that intersects .
Let z be any point in . Let and be the balls centered at p and q respectively. The point z is contained in . Due to property C3, z being a point in cannot lie inside any ball other than and . We remark that and may have a common intersection with another ball, but z cannot be contained in that ball. Therefore, z cannot lie on any Voronoi facet partly defined by a point other than p and q. However, has to intersect at least one Voronoi facet since p and q lie in two different Voronoi cells. Therefore, the only Voronoi facet which intersects is .
For any and any triangle , define to be the maximum weighted distance between the vertices of t and points in . This is the maximum weighted distance between vertices of t and the points where the dual Voronoi edge of t intersects σ.
λ-property: We say S has the λ-weight property if each point in S has a weight at most . We say S has the λ-size property if for each triangle and S has the λ-weight property.
The following observation is at the heart of our refinement algorithm (see
Section 7. in appendix for a proof sketch).
Lemma 2 Let be an admissible point set and be a point on a 2-face σ. Let be the set of all connected components in that intersect a Voronoi edge. There exists a constant so that hypotheses H1
and H2
imply results R1
and R2
where- (H1)
S satisfies λ-size property.
- (H2)
Weighted points in S satisfy C1-C3.
- (R1)
is a 2-disk where any edge of intersects at most once and any facet of intersects in an empty set or an open curve.
- (R2)
If , at least two Voronoi facets of intersect , each intersecting one of the curve segments between p and its adjacent weighted points (possibly two) in .
Interpreted in terms of the Delaunay triangulation, the conclusion of the above lemma implies that the triangles incident to p and restricted with respect to σ form a topological disk around p. This disk has p at the boundary if and only if p is in . Furthermore, if p is in , it is connected to its two adjacent weighted points in on this disk. We will formulate a disk condition with these properties. Our refinement algorithm is primarily driven by this disk condition. The conclusion of Lemma 2 fails only if either there is a protecting ball with radius more than λ, or there is a triangle for which for some . However, since we do not know which of the above two cases has happened, we take a conservative approach. We compute the maximum radius of all protecting balls and also compute the maximum over all t and σ. Let x be the point of intersection of a Voronoi edge with D which realizes . If we refine the largest protecting ball. Otherwise, we insert x. In the first case we are ensured that we are refining balls of size larger than a fixed positive constant. In the second case, we are inserting a point in a compact domain with a positive lower bound on its distances to every other points. Termination by packing argument follows.
For the above algorithm to work, it is important that the balls satisfy C1-C3 when balls are sufficiently small. It turns out that it is difficult to maintain the condition C3 at early phases when the balls are relatively large. We replace C3 by the following two conditions that are maintained by the ball refinement algorithm. These conditions imply C3 when the balls are small enough. For a 1-face
covered by balls
these conditions are:
- (C3.a)
Let be any ball in . For an adjacent ball , if is contained in , then .
- (C3.b)
Any two balls centered in different 1-faces do not intersect and any two non-adjacent balls centered on a common 1-face have a weighted distance larger than the radius of the smaller ball.
Lemma 3 There exists a so that, if all protecting balls are smaller than λ, C3.a and C3.b imply C3.
Consider any two non-adjacent balls and . If c and are on different 1-faces, b and do not intersect by C3.b. Then C3 is satisfied trivially. So, assume that c and belong to a common 1-face σ.
We show that and do not intersect for sufficiently small λ. It follows from the differentiability of σ that there exists a so that any ball of size smaller than λ intersects σ in a single segment. Assuming that b and have radii smaller than λ, we have and . We claim that no point in can lie in when λ is sufficiently small. If there were such a point, there would exists a ball with one of the following properties: (i) either is adjacent to b and its center lies in , or (ii) is adjacent to and lies in . Without loss of generality, assume that (i) holds since the other case can be argued exactly the same way.
We know that the length is at least by property C3.a. Making λ sufficiently small, can be set arbitrarily close to which would imply that can be made arbitrarily close to r. This would contradict that is at least . Therefore, we can claim that the curve segments of two non-adjacent balls cannot intersect if they are centered on a same 1-face σ.
2.2. Ball refinement
The ball refinement routine simply removes a ball and covers the curve segment between the centers of its adjacent balls with balls of smaller radii. Therefore, we encounter the generic situation where a curve segment
needs to be covered by protecting balls whose radii are determined by a given parameter
. The points
x and
y are the right and left end points of some segments, say
and
respectively, see
Figure 3. We call this routine C
over(
).
We proceed from x toward y along the curve while computing the balls that satisfy conditions C1, C2, and C3.a. Condition C3.b is taken care of by another routine called Separate. As we walk from x to y, each step places a new ball of radius α that intersects deeply with the previous ball while covering a new piece of the curve. When we reach y, we place a ball that intersects deeply with both the endpoint ball and the previous one in the walk.
More specifically, suppose that
is already computed. Let
. We compute a small ball
that
aids the computation of
, see
Figure 3. The aiding ball helps compute the next ball so that its center is not contained in the segment of the previous ball. Among the two end points of segment
, we use the one which is further from
x. Let this end point be
. The center of the next ball
is placed at
.
Figure 3.
Curve segment between x and y is being covered. Aiding balls are shown with solid boundaries. Notice how the centers of and are placed with the aiding balls. The end game with enlarged aiding ball is shown on left, the other case is shown on right.
Figure 3.
Curve segment between x and y is being covered. Aiding balls are shown with solid boundaries. Notice how the centers of and are placed with the aiding balls. The end game with enlarged aiding ball is shown on left, the other case is shown on right.
We will eventually encounter one of two situations near the end: either
extends past
or
contains
y. These situations are shown in the left and right images of
Figure 3, respectively. In the first case
may violate C3.a and in the second case
may not intersect
deeply violating C2. In these cases we conduct an
end game. If
, we throw away
and take
as
enlarged concentrically to a radius
. In the other case when
contains
y, we enlarge
to a radius of
. C
over terminates after the end game. Lemma 4 is proved in the appendix.
Lemma 4 Let b be a ball adjacent to and in a set of balls that satisfy C1, C2, and C3.a. Suppose we replace b with Cover where is the segment between and . Then, for α less than the radii of the balls , and , C1, C2, and C3.a remain satisfied after Cover terminates.
Cover does not necessarily satisfy C3.b. We use the routine Separate to enforce C3.b on a set of balls . This routine calls RefineBall(b) which removes the ball b and replaces it with smaller balls.
| Separate() |
|
| RefineBall (b) |
| endwhile. |
- 2
return .
|
Lemma 5 If Separate issues a call to refine a ball b, its radius must be more than a fixed positive constant .
First assume that the two balls and considered by Separate belong to the same 1-face σ. By assumption . Let x be any point where the boundary spheres of b and meet. If θ is the angle between the normals to b and at x, the squared weighted distance between b and is given by . For , this weighted distance is more than when which is satisfied for . The curve can be assumed to lie within cones having apexes at c and and arbitrarily small aperture angles if r and hence is sufficiently small. Since and do not intersect if r is small enough (Proof of Lemma 3), the curve needs to avoid the common intersection of b and . These two constraints force the angle θ to be close to π as r approaches zero. In other words, there is a fixed positive constant so that if , the weighted distance between b and becomes larger than .
Next, assume that b and have centers on different 1-faces. We need to consider the special case of vertex balls before we argue about this case. A vertex ball b can intersect a ball whose center lies on a different 1-face only if b’s radius is more than a fixed positive constant. This is true because we always refine the larger of the two such intersecting balls and there is a positive distance between a vertex and any 1-faces that do not contain it. This observation with the argument in the previous paragraph imply that a vertex ball is refined by Separate only if its size is more than a fixed positive constant. Since no vertex balls can be smaller than a fixed positive constant, two balls centered on two different 1-faces intersect only if the larger ball has a radius more than a fixed positive constant .
It follows that the lemma holds with .
| RefineBall(b) |
| If b covers , let be the minimum of the radii of balls adjacent to b on σ and b itself. |
If is a vertex ball, shrink b to . For each σ covered by b let be the adjacent ball to b on σ. Compute := RefineBall . Return Separate(). If b is not a vertex ball, let be the segment between and where and are adjacent to b. Remove b and return Cover where .
|
Lemma 6 (i) RefineBall terminates and (ii) maintains C1, C2, C3.a, and C3.b.
(i) : Observe that RefineBall makes recursive calls to itself and through Separate. Consider the trees of ball refinements made by these recursive calls. An internal node b in the trees represents a ball b that is refined into smaller balls (children).
We observe that every internal node except the roots is refined by Separate. The only way RefineBall can call itself is when a ball is to be refined in step 1. But, then becomes a root. All other calls to RefineBall are generated by Separate.
By Lemma 5, Separate calls RefineBall on a ball b only if the size of b is larger than a fixed positive constant . The children of a node b are created by Cover which, by construction, creates only finitely many balls with radius at most th the radius of b. The height of any refinement tree is finite since any path from the root to a leaf has internal nodes with radius larger than and each level decreases the radius by a factor or less. Also, each node has finitely many children. Therefore, each refinement tree is finite. Now we argue that the number of roots and hence the entire set of refinement trees is finite implying that RefineBall terminates.
Except for the first ball b, RefineBall(b) creates a root for each in step 1. If such a root is created, the ball b must be a vertex ball. Later in recursion, a call to RefineBall on a vertex ball can only be given by Separate. Therefore, each root except b can be associated with a call to RefineBall by Separate on a vertex ball. Observe the following: only a fixed number of roots are created per vertex ball; a vertex ball is shrunk by a factor of two between two successive calls to refine it; Separate calls for refining a vertex ball only if its size is larger than a fixed positive constant (Lemma 5). These observations mean that only finitely many roots are created.
(ii): Almost immediate: assume that C1, C2, and C3.a hold before calling RefineBall. It creates new balls by calling Cover which satisfies C1, C2, and C3.a (Lemma 4). If a ball does not satisfy C3.b (may happen only after a vertex ball is refined), it refines it by calling Separate. The claim follows.
3. Meshing Algorithm
The algorithm for meshing D first protects the 1-faces with Protect(D,λ) where λ is a user defined parameter. It acts as an input scale parameter which becomes an upper limit for the radii of the protecting balls.
| Protect(D,λ) |
Protect each vertex with a ball where is rd the distance of v to any other vertex in . Let be the set of vertex balls. For each do the following. Let u and v be the end points of σ where and . Let . Cover (x, y, α). Find a ball with radius larger than λ. If found, compute RefineBall (b) and repeat step 3. return Separate().
|
Lemma 7 Protect terminates with balls satisfying C1, C2, C3.a, and C3.b.
Observe that at the end of step 2, Protect creates a set of finitely many balls (most likely quite large). Each call to RefineBall on a ball b creates only finitely many balls as output (Lemma 6). Since a ball is refined only if its radius is more than , and since each refine shrinks the radii by at least a factor of 2, there are only finitely many balls created in step 3.
Termination of step 4 follows from Lemma 5. Hence Protect terminates. At termination it must satisfy C1, C2, C3.a, and C3.b since it refines balls with Cover and calls Separate to enforce C3.b.
After the initial protection of
, refinement of
begins. In this phase Delaunay refinement is run with a
disk condition which can be seen as a generalization of a similar condition used in [
3,
4]. See
Figure 4 for more explanations. Let
p be a point on a 2-face
σ and let
be the set of triangles in
that are incident to
p.
DiskCondition(p) : (D1) For each containing p, the underlying space of is a 2-disk, (D2) point p is in the interior of this 2-disk if and only if , (D3) in , p is not connected to any other point on which is not adjacent to it, (D4) all vertices of are in σ.
Once the restricted Delaunay triangles are collected, the above checks are only combinatorial. One may notice that D1 and D2 are dual to R1 and R2 of Lemma 2. We assume that as we insert points, weighted or unweighted, and get updated appropriately.
Figure 4.
Disk condition: (left) Triangles incident to point are assumed to be restricted to σ; they do not form a disk since they form two disks pinched at p violating condition D1. (middle) The point has a topological disk but some of its vertices (lightly shaded) belong to τ violating condition D4. (right) Points p and q satisfy the disk condition. Point p, an interior point in σ, lies in the interior of its disk in σ. The point q, a boundary point, has three disks for each of the three 2-faces.
Figure 4.
Disk condition: (left) Triangles incident to point are assumed to be restricted to σ; they do not form a disk since they form two disks pinched at p violating condition D1. (middle) The point has a topological disk but some of its vertices (lightly shaded) belong to τ violating condition D4. (right) Points p and q satisfy the disk condition. Point p, an interior point in σ, lies in the interior of its disk in σ. The point q, a boundary point, has three disks for each of the three 2-faces.
| DelPSC |
Protection. Let := Protect(). Let S be the current weighted point set. Mesh2Complex. Let be any tuple where . Let be the triangle that maximizes over all t and σ. Let realize this maximum, say . Let be the maximum radius of all vertices realized by ball, say b.
- (a)
If condition D1 or D2 in DiskCondition(p) is violated if insert x into S else compute RefineBall (b). - (b)
Else if D3 or D4 in DiskCondition(p) is violated insert x into S - (c)
Else if for some tuple where insert that realizes into S.
If S has grown in the last execution of step 2, repeat step 2. Return .
|
Notice that in step 2(a) we refine either a ball or a triangle if either D1 or D2 is violated. However, for D3 or D4 violations in step 2(b), we only refine a triangle. This is important because D3 and D4 are not covered by Lemma 2 and may be violated no matter how small the balls are. We argue separately for D3 and D4 in the termination proof. In step 2(c) we refine triangles to reach the refinement level of the input scale.
We observe that DelPSC never inserts unweighted points inside any protecting ball. If the inserted point x in step 2(a) lies in a protecting ball , its weighted distance to q would be non-positive. Its weighted distance to its nearest Voronoi neighbor in S would even be smaller. Since the largest ball has a positive radius, x would not be inserted (we would call RefineBall(b) instead). If x is inserted in step 2(b), the point p is connected to a point q where either or p and q are non-adjacent weighted points on a 1-face. In both cases p and q have a positive weighted distance ensured by C3.b. Therefore, a restricted triangle t incident to has positive. It follows that the point x which realizes the maximum of over all t and σ has a positive weighted distance to its nearest Voronoi neighbor in S. Hence x cannot lie in a protecting ball. Finally, since , any point x inserted in step 2(c) has a positive distance to its Voronoi neighbors, and thus outside of every protecting ball. Therefore, point x has a positive weighted distance from p and hence cannot be inside a ball.
Guarantees: The analysis of the algorithm establishes two main facts: (i) the algorithm terminates, and (ii) at termination the output mesh has guarantees G1 and G2:
- (G1)
For each , is a 2-manifold with vertices only in σ. Further, is homeomorphic to with vertices only in .
- (G2)
There exists a so that if , the output mesh of DelPSC(D,λ) is homeomorphic to . Further, this homeomorphism respects stratification with vertex restrictions, that is, for , is homeomorphic to where and vertices of lie in σ.
Theorem 1 DelPSC terminates.
First, we argue that if the algorithm refines a ball, its radius is larger than a fixed positive constant. Assume that and have been defined as in the algorithm.
Consider a vertex p on a 2-face σ. The conclusion of Lemma 2 implies disk conditions D1 and D2. Therefore, if it does not hold for p, at least one of the premises of Lemma 2 does not hold. (H1) S does not satisfy the -property for some . (H2) Protecting balls do not satisfy C1-C3. But, when the disk condition is checked, the protecting balls satisfy condition C1, C2, C3.a, and C3.b due to Lemma 6(ii). Therefore, if H2 has failed, at least one ball has a radius more than where satisfies Lemma 3. The argument implies . Therefore, if a ball is refined its radius is more than δ.
The entire ball refinement can be represented with trees as in the proof of Lemma 7 where a ball is refined only if its radius is at least a fixed positive constant. The argument for Lemma 7 still holds to claim that only finitely many balls are refined altogether. Therefore, the algorithm cannot refine balls forever. This also implies that the minimum size of the balls remains larger than a fixed positive constant, say .
Now we argue that each point inserted by the algorithm maintains a lower bound on its distance to all other points. Then, a standard packing argument implies termination. In step 2(a), each inserted point x maintains a weighted distance at least if it is inserted because of violation of either D1 or D2. If D3 or D4 is violated in step 2(b), the weighted distance of x from p is at least half the weighted distance between p and a point q where either p and q are non-adjacent points in or q lies on a different 2-face. Since protecting balls have a minimum size and any two intersecting non-adjacent balls maintain a weighted distance larger than the of the radius of the smaller ball, the weighted distance between p and q is larger than a fixed positive constant. Hence, x has a distance more than a fixed positive constant from all other points. The only remaining case is step 2(c) where a point is inserted only if its weighted distance is at least from all other points.
4. Proof of Guarantees
Let M denote the output mesh of DelPSC.
Theorem 2 M has guarantee G1.
At the end of Mesh2Complex the disk condition ensures that is a simplicial complex where each vertex v belongs to σ and has a 2-disk as its star. It follows from a result in PL topology that is a 2-manifold when DelPSC terminates.
The boundary of has all weighted vertices in . Each such point p is connected to its adjacent vertices in by the disk condition. Therefore, the boundary of consists of edges that connect adjacent vertices in and hence this boundary is homeomorphic to .
To prove G2 we use a result of Edelsbrunner and Shah [
17] about the extended topological ball property (TBP). It can be shown that the following two properties P1 and P2 imply the extended TBP [
8]. Therefore, according to the Edelsbrunner-Shah [
17] result, the underlying space of
is homeomorphic to the
if P1 and P2 hold. Let
F be a
k-face of
where
S is the output vertex set.
- (P1)
If F intersects an element , the intersection is a closed -ball.
- (P2)
There is a unique lowest dimensional element so that F intersects and only elements that are incident to .
Lemma 2 almost provides condition P1 except for the case that
may intersect a patch
τ where
(
Figure 7 (middle, right)). Lemma 8 establishes that this is not possible. Lemma 9 gives P2. Proofs of both of them appear in the appendix.
Lemma 8 There exists a constant so that following holds. Let S be the point set output by DelPSC for some . Then for each point , .
Lemma 9 Let S be the point set as defined in Lemma 8. Let F be a k-face in . There is an element so that F intersects and only elements in D that have on their boundary.
Theorem 3 M satisfies G2.
For a sufficiently small , DelPSC satisfies the conditions of Lemma 8 and Lemma 9. This means that properties P1 and P2 are satisfied when λ is sufficiently small. Also when P1 and P2 are satisfied . It follows that the Edelsbrunner-Shah conditions are satisfied for the output M of DelPSC. Thus, M has an underlying space homeomorphic to . The homeomorphism constructed by Edelsbrunner and Shah actually respects the stratification, that is, for each , is homeomorphic to σ. Also, consists of only edges that connect adjacent vertices on σ. Furthermore, property G1 holds for any output of DelPSC. This means, . Because of the vertex balls, we also have trivially. Therefore, for , and has vertices only in σ.
7. Proofs of lemmas in Section 2
For proving Lemma 2 we need some standard results from sampling theory [
20,
21]. Recall that we have assumed each 2-face in the domain to be a compact subset of a smooth (
) 2-manifold without boundary. This helps us to carry forward a result on normal variation from smooth surfaces straightforwardly to the surface patches with boundaries. If surface elements are not assumed to be a subset of smooth surfaces without boundary, normal variation proof becomes more complicated with a worse error bound.
Let
σ be any 2-face which by assumption is a subset of a smooth 2-manifold
without boundary. The surface normal
to
σ at
x is the surface normal of
at
x. Let
M denote the medial axis of
, that is,
M is the closure of all points in
which have two or more closest points in
. Borrowing from [
20], we define the local feature size
. In the analysis, we use a global lower bound on the
function. We define:
Recall that denotes the weighted distance between two weighted points x and y, that is, where and are the weights of x and y respectively. For a triangle t, consider the disk whose weighted distance to all of t’s vertices (possibly weighted) is zero. The radius of this disk is called the orthoradius of t.
Lemma 10 Let be some constant.
- (i)
For any two points x and y in σ such that ,
- (a)
the angle between the surface normals at x and at y is at most ;
- (b)
the angle between and the surface normal at x is at least .
- (ii)
Let be a triangle with vertices on σ which are possibly weighted with a weight for . Furthermore, let the orthoradius of be no more than . Then, .
(i.a) Follows from the normal variation result in [
22].
(i.b) Follows from the Edge Normal Lemma in [
21].
(ii) Let
R and
be the circumradius and orthoradius of
respectively. For a sufficiently small
ω, the circumcenter
x lies inside the orthocircle of
. Then, minimum weighted distance of
x to any of three vertices of
, is a lower bound on
, that is,
Without loss of generality, assume that
p subtends the largest angle in
. Plugging
and using
in the Triangle Normal Lemma (Lemma 3.5 in [
21]), we get that
Consider a weighted vertex
on a 2-face
σ. For any facet
F of
, we use
to denote the plane of
F. Let
. Let
. By the Feature Ball Lemma in [
21]
is a 2-disk.
Lemma 11 For any facet F of , if intersects , then and both and contain no closed curve.
Let
be the dual Delaunay edge of
F where
intersects
at
x. We have
from which we can derive that
. It follows that
which is less than
. By Lemma 10(ib),
. There is no closed curve in
because such a closed curve would bound a 2-disk in
, which would contain a point
x such that
. This is a contradiction because
by Lemma 10(i.a). Since
contains no closed curve, neither does
. This proves the claim.
Lemma 12 For any facet F of , if and conditions C1-C3 hold, then is either empty or a single open curve.
We assume that
intersects
since otherwise
is empty and there is nothing to prove. First, we show that if
is within a distance of
λ from
p,
is a single open curve. Consider the disk
. Let
be the projection of
onto
. Let
be the line through the center of
orthogonal to
. Let
x be any point in
. The angle between
and the tangent plane at
p is at most
by Lemma 10(i.b). We already proved that
. We are interested in an upper bound on the distance
. Let
be the orthogonal projection of
x onto
L. Consider the triangle
. Observe that
is the angle between
and the tangent plane at
p and
is at least
. We obtain
Let
be the strip of points at distance
or less from
L. Since the radius of
B is
and
is at most
λ distance from
p, the radius of
is at least
. It follows that the boundary of
intersects
in two disjoint circular arcs, say
A and
.
We already proved that there is no closed curve in
(Lemma 11). Now we show that
cannot contain two open curves. First, we eliminate the case where
are two open curves each having an end point on
. For this to happen,
F has to intersect
in more than one point, which is impossible by Lemma 1 if the protecting balls satisfy condition C1-C3. Therefore, we can assume that if
has two open curves, at least one, say
C, has both end points on the circular arcs
A and/or
. Consider the case where
C has end points both in
A and
. The other curve, say
, in
must have an end point in at least one of
A and
. It follows that either
A or
should have an end point of both
C and
. Without loss of generality, assume that
A has end points of both
C and
and let
s and
t be these end points. We observe that the line segment
cannot make an angle with
L less than the least angle made between
L and a tangent to
A. This least angle is made by the tangent to
A at any of its end points. Since the width of
is
and the radius of
is at least
, this least angle is more than
. Therefore,
makes an angle of at least
with
L, or equivalently of at most
with
. Since
,
makes an angle of at most
radians with
. The line of
intersects
σ at two points, namely at
s and
t, where
. Here we can use the Long Distance Lemma in [
21] to obtain
which contradicts
.
Next, consider the case where C has both endpoints on a single arc, say A. Taking these end points as s and t we can argue as in the previous paragraph to reach a contradiction.
Third, we claim that for any facet F of , if F intersects , is a single open curve with endpoints in or in . We already proved that there is no closed curve in . Since F does not have any tangential contact with σ, is a set of open curves and the endpoints of any open curve in thus lie in or in . Assume to the contrary that contains two open curves, say ξ and . By our assumption, is within a distance of λ from p. We have shown before that is a single open curve. Follow from ξ to . When we leave ξ, we must leave F at a Voronoi edge . Afterwards, we stay in the plane and we must cross the support line of e again in order to reach . Therefore, some tangent to is parallel to e. However, the angle between the surface normal at some point on and would then be at least by Lemma 10(ii) since . This contradicts Lemma 10(i.a) proving the claim.
Recall that denote the components of that intersect a Voronoi edge of . We show that intersect and its faces in topological balls if S has the λ-size property for a sufficiently small λ. We need the following result which says that when λ is sufficiently small, each Voronoi cell contains at least one Voronoi edge intersecting σ if .
Lemma 13 There exists a so that if S satisfies the λ-size property, then is non-empty for any
Suppose that is empty, that is, no Voronoi edge of intersects σ. By our assumption is non-empty and let be a weighted point in . Because of Lemma 1, an edge of has to intersect σ. Consider walking on a path in σ from p to q. Let be sequence of vertices whose Voronoi cells are encountered along this walk. Since no edge of intersects σ and some edge of intersects σ, there exists two consecutive vertices and in this sequence so that no edge of intersects σ whereas some edge of does intersect σ. By Lemma 2 we can claim that is a disk. A boundary cycle of overlaps with the boundary of . This is impossible as the curves on the boundary of intersect Voronoi edges whereas those on the boundary of do not.
Now we are ready to prove the main claim of Lemma 2.
Figure 7 explains more about its implications.
Figure 7.
(left) A 2-face σ has intersected where is not topological disk, this is not possible by R1. (middle) is a disk but another face τ where intersects some edge of . It does not violate R1 but violates Lemma 8. (right) Within B, σ intersects in a topological disk. There is a different component (τ) which does not intersect any Voronoi edge and hence does not contribute any dual restricted triangle incident to p. R1 does not prevent it though Lemma 8 does.
Figure 7.
(left) A 2-face σ has intersected where is not topological disk, this is not possible by R1. (middle) is a disk but another face τ where intersects some edge of . It does not violate R1 but violates Lemma 8. (right) Within B, σ intersects in a topological disk. There is a different component (τ) which does not intersect any Voronoi edge and hence does not contribute any dual restricted triangle incident to p. R1 does not prevent it though Lemma 8 does.
Lemma 14 There is a so that if H1 and H2 of Lemma 2 are satisfied, then is a topological disk. Furthermore, each Voronoi edge and facet that intersects does so in a single point and single open curve respectively.
Recall . Consider an edge of that intersects . By Lemma 10(ii), . Then, by Lemma 10(i.a), is monotonic in the direction of e when λ is sufficiently small. Therefore, e intersects and hence at most once. Each facet of that intersects intersects it in a single open curve by Lemma 12. This completes the proof of the second part of the lemma.
We show that the argument of Lemma 4.12 in [
4] can be used here to establish that
is a topological disk. Following the notation in the proof of this lemma, let us call a cycle in
that intersects a Voronoi edge a type 1 cycle. Let
X denote the set of type 1 cycles. Each Voronoi facet containing a point in
X has a Voronoi edge intersecting
. By H1, this intersection point is within
λ distance of
p. Therefore,
B intersects all Voronoi facets that contain a point in
X. These Voronoi facets intersect
in a single open curve which is in
B. Also, if
intersects
, the entire curve segment
is contained in the protecting ball of
p. This means each point of
X is within
λ distance of
p. Since each cycle in
X is a piecewise smooth closed curve where each piece is either an open curve contained in a Voronoi facet or a segment of
, it is contained completely in
B. Therefore, each boundary of
which intersects a Voronoi edge lies in
B.
Consider the arrangement of closed curves in
X on
which is a topological disk according to the Feature Ball Lemma [
21]. Let
be a closed curve which does not contain any other curve of
X inside. At least one such curve exists since
X is not empty by Lemma 13. The closed curve
C must bound a disk, say
D in
σ. At this point we can invoke the proof of Lemma 4.12 in [
4] to prove that
establishing our first claim. The boundary
lies in
X which has at most a single interval in any Voronoi facet as we argued above. This establishes our second claim.
[Proof of Lemma 2.]
Proof of R1: Follows from Lemma 14.
Proof of R2: Since conditions C1-C3 hold, Lemma 1 can be applied. The conclusion of this lemma implies R2.
[Proof of Lemma 4.] Cover affects only the sequence of balls as referred in its description. By construction the new balls cover entire curve segment and vertex balls are not changed. So, C1 and the first part of C2 are satisfied. To prove the second part consider a ball . We have following cases:
Case 1 (): We need to examine the effect of the new ball onto . First notice that cannot contain by construction. Therefore, C3.a holds trivially. If is not created with the end game, the radius of is α and where by construction. This satisfies C2. If is created with the end game, then two cases occur. If is the enlarged aiding ball , its radius is . Then, . This satisfies C2. In the case where is not the enlarged aiding ball, its radius is . We can similarly argue that . So, satisfies C2.
Case 2 (): In this case the center of cannot lie in by construction. So, C3.a holds trivially. The ball is necessarily created with the end game. If is enlarged , satisfying C2. In the case where is not the enlarged aiding ball, its radius is . Then, satisfying C2.
Case 3 (): If is adjacent to and , it satisfies C2 by arguments in previous two cases. Also, is not large enough to contain or . Hence C3.a also holds. Now consider the case where is adjacent to another ball b where and . If neither nor b is created by end game, we have satisfying C2. Also, in this case which satisfies C3.a. We are left with the case when either of b and is created with the end game. With similar arguments, one can check that C2 and C3.a hold in these cases too.