6.2. -Hardness on Four-Regular Graphs
We are now ready to show that vertex cover reconfiguration remains
-hard even if the input graph is restricted to be four-regular. We use the same ideas as we did in the previous section. Since vertex cover remains
-hard on four-regular graphs [
22] and any algorithm that solves the vertex cover compression problem can be used to solve the vertex cover problem, we get the desired result. The main difference here is that we need to construct a gadget,
, that is also four-regular. We describe
in terms of several component subgraphs, each playing a role in forcing the reconfiguration of vertex covers.
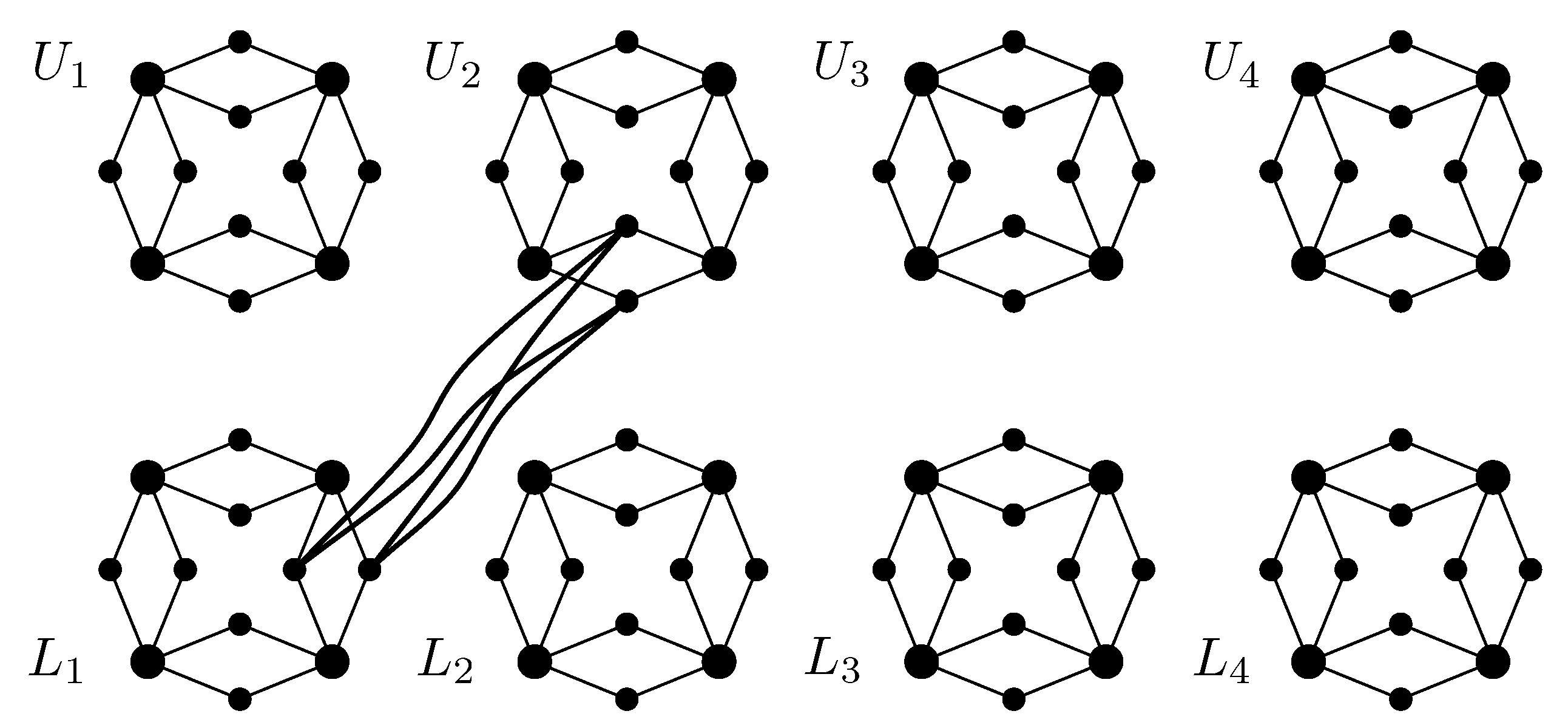
A k-necklace, , is a graph obtained by replacing every edge in a cycle on k vertices by two vertices and four edges. For convenience, we refer to every vertex on the original cycle as a bead and every new vertex in the resulting graph as a sequin. The resulting graph has k beads each of degree four and sequins each of degree two. Every two sequins that share the same neighbourhood in a k-necklace are called a sequin pair. We say two beads are adjacent whenever they share exactly two common neighbours. Similarly, we say two sequin pairs are adjacent whenever they share exactly one common neighbour. Every two adjacent beads (sequin pairs) are linked by a sequin pair (bead).
The graph consists of copies of a k-necklace. We let and denote the first and second k copies, respectively; for convenience, we use the terms “upper” and “lower” to mean “in U” and “in L”, respectively. We let and denote the j-th beads of necklace and , respectively, where and . Beads on each necklace in are numbered consecutively in “clockwise order” from one to k. For every two adjacent beads and , where , we let denote the sequin pair that links both beads.
For each sequin pair
, we add four edges to form a
(a joining biclique) with the pair
, for all
(
Figure 1); we say that sequin pairs
and
are joined. All
joining bicliques in
are vertex disjoint. The total number of vertices in
is
. Every vertex has degree exactly four; every bead is connected to four sequins from the same necklace, and every sequin is connected to two beads from the same necklace and two other sequins from a different necklace. We let
S be the set containing all upper beads and lower sequins, whereas
T contains all lower beads and upper sequins. Formally,
and
. Each set contains
vertices, that is half the vertices in
.
Proposition 8. S and T are minimum vertex covers of .
Proof. We need at least vertices to cover the edges in the vertex disjoint joining bicliques contained in . Moreover, any minimal vertex cover C of that includes a vertex v from a sequin pair , where , must also include w. Otherwise, the two beads linking to its adjacent sequin pairs must be in C to cover the edges incident on w, making v removable. Hence, any minimal vertex cover C of must include either one or both sequin pairs in a joining biclique. We let x denote the number of joining bicliques from which two sequin pairs are included in C. Similarly, we let y denote the number of joining bicliques from which only one sequin pair is included in C. Hence, and . When , and C cannot be a minimum vertex cover, as S and T are both vertex covers of of size . When , we are left with at least y uncovered edges incident to the sequin pairs not in C. Those edges must be covered using at least y beads and, hence, . If we assume , we get a contradiction since and . Therefore, S and T must be minimum vertex covers of . ☐
To prove the next two results, we consider the representation of reconfiguration sequences as edit sequences. Since S is a minimal vertex cover of , cannot start with a vertex removal. Since is a vertex cover of , and S and T are minimum vertex covers of , cannot end with a vertex addition. Moreover, if , then must touch every vertex in exactly once.
Proposition 9. Any (valid) edit sequence of length from S to T can be converted into a (valid) edit sequence α from S to T such that , , for all , and any two vertices u and v from the same sequin pair in are either added in the same maximal addition segment or removed in the same maximal removal segment of α. Consequently, .
Proof. Both vertices in a sequin pair share the same neighbourhood. Hence, when u is removed, all of its neighbours must have been added, making v also removable. Moreover, since every vertex is touched exactly once in , none of the neighbours of u and v will be touched in after the removal of u. Therefore, if v is not removed in the same maximal removal segment as u, then we obtain by shifting the removal of v, so that it happens immediately after the removal of u. It is not hard to see that and , for all .
For the case of additions, if only u is added in some maximal addition segment , then none of its neighbours can yet be removed. Let be the maximal addition segment in which v is added (which occurs after in ). We obtain by shifting the addition of u from to . ☐
Lemma 6. There exists a function of k, , such that is a yes-instance and is a no-instance of vertex cover reconfiguration for . Moreover, .
Proof. To show that such an exists, we first prove the lower bound by showing that any valid edit sequence of length from S to T must have some prefix where the number of vertex additions minus the number of vertex removals is at least , i.e., . In fact, we will show that the aforementioned property holds for any valid edit sequence of length in which two vertices from the same sequin pair are always added or removed in the same maximal addition or removal segment, respectively. Considering only such sequences is sufficient because, from Proposition 9, we know that any sequence of length can be transformed into such a sequence so that , for all . In other words, if has no prefix with (but does), then , a contradiction.
We let position x, , be the smallest position such that contains exactly vertex removals. Those vertices correspond to a set , as touches every vertex exactly once. The claim is that must contain at least vertex additions. We let denote the set of added vertices in . Since , we complete the proof of the lower bound by showing that . To do so, we show that for any of size , contains at least vertices.
In what follows, we restrict our attention to the bipartite graph , and we let and denote the two partitions of Z. We subdivide into two sets: contains upper beads, and contains lower sequins. Since every vertex in has four neighbours in and adjacent beads share exactly two neighbours, we have , and equality occurs whenever contains beads from the same two upper necklaces. Whenever contains fewer than beads and consists of connected components, at least one bead from each component (except possibly the first) will be adjacent to at most one other bead in the same component. Therefore, .
Proposition 9 implies that will always contain both vertices of any sequin pair. Since we are only considering vertices in , some sequins in might be missing the other sequin in the corresponding pair. However, all the neighbours of the sequin pair have to be in , so we assume without loss of generality that vertices in can be grouped into sequin pairs. Every sequin pair in has four neighbours in . Adjacent sequin pairs share exactly one neighbour. Hence, , and equality occurs whenever contains k sequin pairs of a single lower necklace. Whenever contains fewer than k sequin pairs and consists of connected components, at least one sequin pair from each component will be adjacent to at most one other sequin pair in the same component. Therefore, .
Combining the previous observations, we know that when either
or
is empty,
, as needed. When both are not empty, we let
. Hence,
, and we rewrite it as:
We now bound the size of
I. Note that
I can only contain upper sequin pairs joined with sequin pairs in
. As every sequin pair in
has either zero or two neighbours in
I,
. Moreover, for every two sequin pairs in
having two neighbours in
I, there must exist at least one vertex in
, which implies
. Finally, whenever a sequin pair
has two neighbours in
I, then
, as at least one bead neighbouring the sequin pair joined with
p must be in
. Every other sequin pair
,
, with two neighbours in
I will force at least one additional connected component in either
or
since
contains a single joining biclique between any two necklaces. Therefore, the total number of connected components is
. Putting it all together, we get:
Combining Equations (
8) and (
9), we get:
Therefore, is a vertex cover of of size at least , as needed.
To show the upper bound, we show that is a yes-instance by providing an actual reconfiguration sequence:
- (1)
Add all k beads in . Since S is a vertex cover of , we know that the additional k beads will result in a vertex cover of size .
- (2)
Add both vertices in , and remove both vertices in . The removal of both vertices in is possible since we added all their neighbours in (Step (1)) and . The size of a vertex cover reaches after the additions and then drops back to .
- (3)
Repeat Step (2) for all sequin pairs and for . The size of a vertex cover is again once Step (3) is completed. Step (2) is repeated a total of k times. After every repetition, we have a vertex cover of since all beads in were added in Step (1), and the remaining neighbours of each sequin pair in are added prior to the removals.
- (4)
Add both vertices in , and remove vertex .
- (5)
Add and . At this point, the size of a vertex cover is .
- (6)
Remove both vertices in .
- (7)
Repeat Steps (4), (5) and (6) until all beads in have been added and the sequin pairs removed. When we reach the last sequin pair in , was already added, and hence, we gain a surplus of one, which brings the vertex cover size back to .
- (8)
Repeat Steps (4) to (7) for every remaining necklace in L.
Since every vertex in is touched exactly once, we know that . In the course of the described reconfiguration sequence, the maximum size of any vertex cover is . Hence, . This completes the proof. ☐
It would be interesting to close the gap on , but the existence of such a value is enough to prove the main theorem of this section.
Theorem 5. Vertex cover reconfiguration is -hard on four-regular graphs.
Proof. We prove the result by a reduction from vertex cover compression to vertex cover reconfiguration where the input graph is restricted to be four-regular in both cases. For , an instance of vertex cover compression, we form . We let be an instance of vertex cover reconfiguration, where and , and is the value whose existence was shown in Lemma 6.
Clearly, and both S and T are vertex covers of . We claim that G has a vertex cover of size if and only if there is a reconfiguration sequence of length or less from S to T.
We know from Lemma 6 that the reconfiguration of requires at least available capacity. However, , which violates the maximum allowed capacity. Therefore, if there is a reconfiguration sequence from S to T, then one of the vertex covers in the sequence must contain at most vertices. By Proposition 8, we know that of those vertices are needed to cover the edges in . Thus, the remaining vertices must be in and should cover all edges in . By construction of , these vertices correspond to a vertex cover of G.
Similarly, if G has a vertex cover such that , then the following reconfiguration sequence transforms S to T: add all vertices of , remove all vertices of C, apply the reconfiguration sequence whose existence was shown in Lemma 6 to and finally add back all vertices of C and remove those of . The length of this sequence is equal to whenever and is shorter otherwise. ☐
6.3. Algorithm for Graphs of Bounded Degree
In this section, we prove that vertex cover reconfiguration parameterized by
ℓ is fixed-parameter tractable for graphs of degree at most
d. Our algorithm is randomized and based on a variant of the colour-coding technique [
23] that is particularly useful in designing parameterized algorithms on graphs of bounded degree. The technique, known in the literature as random separation [
24], boils down to a simple, but fruitful observation that in some cases, if we randomly colour the vertex set of a graph using two colours, the solution or vertices we are looking for are appropriately coloured with high probability. In our case, we want to make sure that the set of touched vertices gets highlighted. We note that our algorithm can easily be derandomized using standard techniques [
25].
We start with an instance of VCR, with G having degree at most d. Recall that we partition into the sets , , , and the independent set . We colour independently every vertex of G using one of two colours, say red and blue (denoted by and ), with probability . We let denote the resulting random colouring. Suppose that is a yes-instance, and let denote a reconfiguration sequence from S to T of length at most ℓ. We say that the colouring is successful if both of the following conditions hold:
Observe that
and
are disjoint. Therefore, the two aforementioned conditions are independent. Moreover, since the maximum degree of
G is
d, we have
. Consequently, the probability that
is successful is at least:
Let denote the set of vertices coloured red and denote the set of vertices coloured blue. Moreover, we let , …, denote the set of connected components of . The main observation now is the following:
Proposition 10. If χ is successful, then , has a non-empty intersection with at most ℓ connected components of , and each one of those components consists of at most ℓ vertices.
Proof. The fact that follows from the observation that every vertex in must be added or removed at least once and no vertex in is ever added or removed. In other words, if is removed, then all of its untouched neighbours must be in . Similarly, if is added, then prior to being added, all of its untouched neighbours must be in .
Since , we know that consists of at most ℓ connected components (each of size at most ) and consists of at most ℓ components (each of size at most ℓ). Let C be a connected component of such that . We claim that we can safely ignore (and hence delete) this component when is successful. Suppose to the contrary that . Since is successful, it must be the case that every vertex in is coloured blue. However, we know that there exists at least one vertex in that is coloured red (since C is a connected component of and all vertices in C are coloured red). As we have obtained a contradiction, we can conclude that when is successful, can intersect at most ℓ connected components of , and none of those components can be of a size greater than ℓ, as claimed. ☐
Given Proposition 10, we can safely assume that every connected component of consists of at most ℓ vertices (as the remaining components can be ignored when is successful). For simplicity, let us first assume that is connected. Thus, if is successful, then there exists a single component in , say , such that , and . Therefore, we can simply enumerate all possible sequences of length at most ℓ and make sure that at least one of them is the required reconfiguration sequence from S to T. This brute-force testing can be accomplished in time .
Let us now consider the general case when
is not necessarily connected. We say a component
C of
is important if
. There are at most
ℓ important components. Hence, we only need to bound the number of unimportant components. To that end, we partition the unimportant components of
into equivalence classes with respect to the following relation ≃:
Proposition 11. The total number of graphs with at most ℓ vertices is at most , and therefore, the equivalence relation ≃ has at most equivalence classes.
Assume that some equivalence class contains more than ℓ unimportant components. We claim that retaining only ℓ of them is enough. To see why, it is enough to note that intersects with at most ℓ of those components; they are all isomorphic; and the neighbours of any such component are contained in . Putting it all together, we know that we have at most equivalence classes, each with at most ℓ components, and each component is of size at most ℓ. Hence, we can guess the sequence from S to T in time (testing whether two graphs with ℓ vertices are isomorphic can be accomplished naively in time ).
We have proven that the probability that is successful is at least . Hence, to obtain a Monte Carlo algorithm with false negatives, we repeat the above procedure times and obtain the following result:
Theorem 6. There exists a one-sided error Monte Carlo algorithm with false negatives that solves the vertex cover reconfiguration problem on graphs of degree at most d in time .
6.4. Algorithm for Nowhere Dense Graphs
In this section, we present a more general result, showing that the reconfiguration variant of every first-order definable optimization problem parameterized by ℓ is fixed-parameter tractable on every fixed nowhere dense class of graphs.
Let us quickly recall the necessary definitions from logic. For our purpose, it suffices to consider first-order logic over the vocabulary of coloured graphs. We refer to the textbook [
26] for extensive background on logic.
Let be two unary relation symbols and E a binary relation symbol. We call the vocabulary of graphs with two colours A and B. First-order formulas over the vocabulary of coloured graphs are formed from atomic formulas , , and , where are variables (we assume that we have an infinite supply of variables), by the usual Boolean connectives ¬ (negation), ∧ (conjunction) and ∨ (disjunction) and existential and universal quantification , respectively. The free variables of a formula are those not in the scope of a quantifier, and we write to indicate that the free variables of the formula are among . To define the semantics, we inductively define a satisfaction relation ⊨. Let G be a graph and . For simplicity, we do not distinguish between A as a symbol and A as a set. For a formula , and , means that G satisfies if the free variables are interpreted by . If is atomic, then if . Similarly, if , then if . The meanings of the equality symbol, the Boolean connectives and the quantifiers are the usual ones.
Let
be a first-order formula that has a free set variable
X. For example, the vertex cover problem is defined by the formula:
As another example, we can define dominating sets by the formula:
and independent sets by the formula:
Naturally, we can define a reconfiguration variant for each such formula . Given two sets , we ask for a sequence , and such that for all intermediate configurations . We call the corresponding decision problem -reconfiguration, and we refer to a solution of a problem instance as a -reconfiguration sequence.
Nowhere dense graph classes were introduced by Nešetřil and Ossona de Mendez [
27] as a very general model of uniform sparseness in graphs. We refer to the textbook [
28] for the formal definition of the notion of nowhere denseness and for more background on its theory. For our purpose, it is sufficient to note that most familiar classes of sparse graphs are nowhere dense, e.g., every proper minor closed class and every class of bounded degree is nowhere dense. We will prove the following theorem.
Theorem 7. Let be a first-order formula over the vocabulary of graphs with a free set variable; let be a nowhere dense class of graphs; let be a real; and let be an integer. Then, there exists a constant and an algorithm that, given an n-vertex graph and two sets with , , decides whether there exists a φ-reconfiguration sequence of length at most ℓ in time .
Proof. Our proof is based on a result of Grohe, Kreutzer and Siebertz [
29], which states that for every first-order formula
(without free variables), every nowhere dense class
of graphs and every real
, there exists a constant
, such that given an
n-vertex graph
, one can decide in time
whether
holds in
G.
In order to approach the
-reconfiguration problem, we want to write a formula
over the vocabulary of graphs with two colours
S and
T without free variables, which expresses the existence of a
-reconfiguration sequence of length at most
ℓ. We will guarantee that the length of
is bounded by a function depending only on
ℓ (and on
, though only as a fixed constant). Then, by fixing any
and using the result of [
29], we conclude that
-Reconfiguration is fixed-parameter tractable parameterized by
ℓ on every nowhere dense class
.
The formula
simply states the existence of a sequence of
ℓ elements that will be added or removed in the course of the reconfiguration. For each initial sequence of length
of these
ℓ guesses, we state in
that the formula
is satisfied for the set
S modified according to the first
i operations. Finally, we state that the reconfiguration leads to the set
T. The precise formula is cumbersome to write; however, we expect that the reader is convinced that we can express the desired statement in first-order logic once we have stated how to handle a single addition and removal of a vertex. To state that a vertex is added to the set
S, we write the formula:
where
is obtained from
by replacing every atom
for a variable
x by the formula
. If we now want to remove a vertex, we extend the formula to the formula:
where
is the formula obtained from
by replacing every atom
by the formula
, and
is obtained from
by replacing
by
. Similarly, we can handle any sequence of additions and removals of vertices of length at most
ℓ and form a big disjunction over all such sequences to obtain the final formula
. ☐