1. Introduction
The Internet of Things (IoT) assimilates a huge number of pervasive and heterogeneous objects which continuously produce information on the physical world. Most of this information is accessible over standard Web browsers, and many application-programming-interfaces (APIs) are available to access the sensors and actuators. In 1999, a British technology pioneer Kevin Ashton used a new term for the first time, the “Internet of Things (IoT)”, to describe a mechanism in which the objects in the physical world could connect to the internet by using different sensors [
1]. He defined terminology to connect Radio-frequency Identification (RFID) tags with the internet for trail and count the goods in the industry without human involvement. The Internet of Things connects several technologies within the prevailing Internet infrastructure to offer advanced connectivity of systems, devices, and services [
1,
2,
3,
4,
5]. IoT goes beyond machine-to-machine communications and covers a variety of protocols, domains, and applications [
6,
7]. More precisely, the Internet of Things encloses acuity in the internet-connected devices or objects to communicate, swap information, take decisions, invoke actions and provide appealing services. Currently, the IoT is becoming impressive and gaining popularity in every field of life and providing significant benefits globally. The fundamental objective of the Internet of Things is to grant secure and autonomous connections among real-world objects and applications to exchange data and information on the environment.
Recently, various researchers have used social networking concepts in the field of Internet of Things (IoT). Therefore, the resulting paradigm is known as the Social Internet of Things (SIoT), which has the capability to back the innovative applications and networking facilities for the internet of things with efficient and effective manners [
8]. In the SIoT paradigm, devices mimic the social networking behavior and interact with heterogeneous devices globally and communicate autonomously under some specific rules. The scientific research has proved that the huge number of individuals knotted in a social circle can provide far more precise information than a lone individual even if that individual is knowledgeable [
9]. Such principles have been used widely in Internet-related research areas. Consequently, numerous methods have been introduced that use social networks for the exploration of Internet resources, Traffic optimization, Physical-aware Coalition Formation, and Resource Allocation in smart IoT Application or to select effective strategies for content distribution [
10,
11,
12,
13,
14]. The emergence of the ‘‘Internet of Things’’ and ‘‘Social Networking concepts’’ has gained popularity and momentum instantaneously. SIoT allows smart heterogeneous devices to interact with each other autonomously through various applications, mechanisms, and techniques [
8,
15,
16,
17,
18]. The idea of SIoT is rapidly growing because it has the potential to carry numerous desirable implications in the near future when the world is highly populated with heterogeneous smart objects [
8]. This idea mimics humans behavior in friend selection, interaction, and communication in finding the desired services [
19,
20]. In the process of friend selection, the Biphase authentication scheme can build trust between friends or devices [
21].
M.E.J. Newman and Juyoung Park in Reference [
22] has argued that social networks are different from many other networks, including biological networks (e.g., neural networks) and technological networks (e.g., the Internet, computer networks, etc.) in two essential ways. The first is that they have nontrivial clustering and the other is the positive correlations between the degrees of adjacent vertices. Social networks are usually divided into groups, and it has currently been advised that these divisions could account for the observed clustering. Newman and Park have demonstrated that the group structuring in networks can also account for degree correlations. Watts and Strogatz in Reference [
23] have mentioned that most of the networks have high transitivity or high clustering, i.e., assume that X and Y have a connection between them and Y and Z also have a connection, then there will most probably be a connection between X and Z. This is also called the triadic behavior of social networks. Non-social networks do not mostly have a high clustering coefficient but, on the other hand, social networks have always had a high clustering coefficient. In general, non-social networks usually have more randomness (i.e., large characteristics path length) and small clustering coefficient while social networks are always approximately regular networks but they also have a small characteristic path length. A large clustering coefficient shows that how densely the nodes are connected with each other in a network.
Essentially, we are living in a world of networks in both ways, where any complex system in nature can be exhibited as a network in which nodes are considered the elements of the structure and the edges represent the connections among them. Neural networks, biological and chemical structures, computer networks, social networks, and the Internet are the most common networking illustrations [
24]. The Characterization of the physical properties of the networks is necessary to understand the complex dynamics of these structures. The Watts and Strogatz model [
23] shows the topology of some social and biological networks which are neither completely random nor completely regular. The intermediate form of these networks is called a “small world”; the term small-world was used for the first time around 50 years ago in the field of social psychology by S. Milgram [
25]. The small world network has a comparatively small clustering coefficient than social network (i.e., regular network) but also has small characteristic path lengths like random networks. The properties of the small world and their respective models are explicitly explained in References [
26]. Many researchers have worked on different aspects like the spreading of diseases in small worlds [
27], social network applications [
28], and the Internet [
29].
For the last two decades, the Internet of Things (i.e., devices, services, and technologies) have been growing exponentially. According to References [
30,
31], the estimated count of these IoT devices is projected to reach 50 billion by 2020. IoT devices generate massive amounts of real-time data and information on the physical world, therefore, dealing with that real-time data in smart cities (i.e., public health care, transportation, fire sensors, etc.) [
32,
33,
34] and dealing with high-speed big data are still very big challenges [
35,
36]. The SIoT system empowers the IoT devices to connect globally with each other to share information and services. Consequently, it develops a problematic scenario in which it must find an appropriate object, information, or service from highly populated complex networks. In this paper, we proposed an innovative idea in which we emerged the small world network concept in a SIoT field. The ultimate goal of this technique is to reduce the complexity of the network and to enhance the searching capabilities of the smart social agent. In
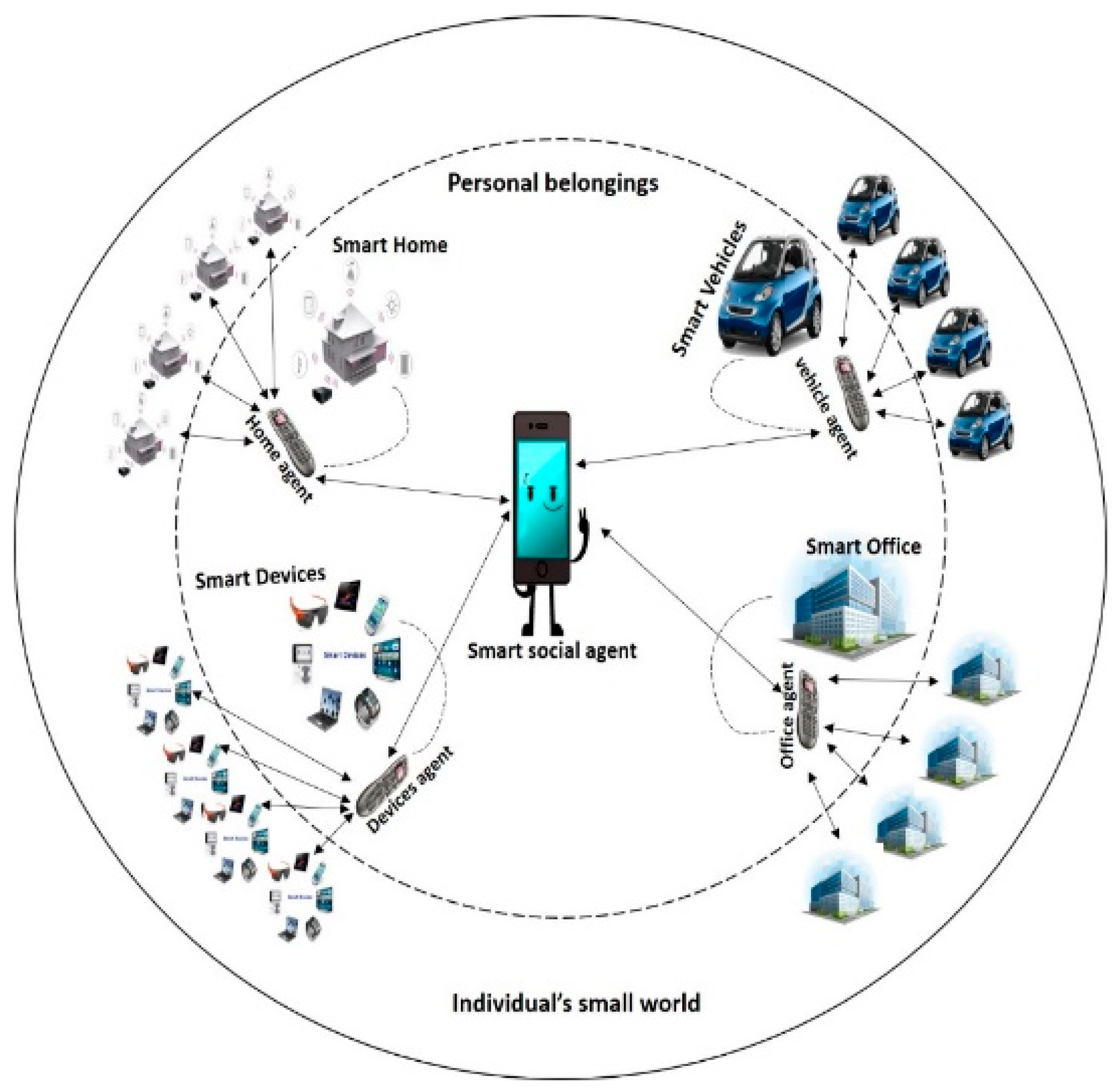
Figure 1, we introduce the new term “individual’s small world”, in which heterogeneous objects are connected with each other on the basis of a logical configuration and they talk with each other without human intervention to find the desired service efficiently in a decentralized way. The balanced tree representation of this individual’s small world justifies the efficient behavior of our proposed work.
The small world SIoT paradigm uses the properties of small world networks and the characteristics of SIoT devices. The authors proposed this idea to create a network of IoT devices in such a way as to make the network scalable and navigable. The motivation behind this idea is to reduce the complexity of the network, as well as the internet load. For instance, if we send a query to the internet, in response, we get millions of replies (i.e., the information gathered by numerous devices all over the world). However, finding the right information from among the search results is, again, a big problem. This action puts more load on the internet and consumes more time in searching for information. Our purpose is to introduce a smart search mechanism which minimizes the search results while retaining a high accuracy within the network. Due to the sequential behavior of a small world, we visualized our network as a balanced tree. While adding nodes in the network, every parent node (Smart Social Agent) saves the complete information of its child nodes (personal friends). The Smart Social Agent directly approaches the best possible node (a friend that possibly has the information) that contains information instead of traversing all the network nodes (asking all the friends). If the agent fails to find the information, it requests that the child node find the information in its child nodes (i.e., in its personal friends). The organization of the paper is as follows.
Section 2 comprises the literature, the proposed scheme is explained in
Section 3. Additionally,
Section 4 contains the results and future work.
Section 5 concludes the work.
2. Related Work
The Internet of Things, which is also known as IoT, is a novel paradigm in the field of information technology. The IoT is gaining a significant consideration day by day and becoming more popular and effective. The term IoT is the coalition of two words, “Internet” and “Things”, where the Internet is the existing worldwide system of interconnected computer networks used to assist billions of users all over the world, whereas the Things can be any object in the real world. The fundamental purpose and ultimate target of IoT is to connect every real-world object with the internet. At the early stage, the Radio Frequency Identification tag has been connected with the internet to track and count real-world objects without human interference. In the IoT, any worldly thing or object could be a virtual object by integrating a small chip, sensor, or embedded system [
37]. These virtual things can utilize the available resources and produce the desired data or information and collaborate toward a common goal. For instance, a user’s cell phone knows about the user’s mental and physical state or condition through a network of sensors, chips, or devices that are monitoring the user’s body. Therefore, the user does not need to monitor anything while all the embedded or surrounded devices can act on his behalf.
The Internet of Things enables billions of objects to connect with each other and the environment to collect information in real time scenarios, which is not possible with simple objects around us. For instance, the currently used Internet of Things, which works as a local network of objects such as Machine-to-Machine (M2M), Wireless Sensor Networks (WSNs), smart homes, etc., can only obtain information from a specific region [
34,
38,
39,
40]. The IoT provides more comprehensive, large-scale, and antique information of the surrounding by collaborating a diverse intranet of things, even though the devices have heterogeneity, local communication protocols, device mobility in the clustering, and different deployment technologies [
39,
41,
42]. The explicit objective of the Internet of Things notion in the real-world is actually conceivable through the integration of numerous permitting technologies. The Internet of Things (IoT) integrates several technologies and envisages a diversity of objects or things around us, which are able to communicate with each other through standard communication protocols and unique addressing systems to grasp common goals [
2,
43]. An architecture has been proposed for connecting Fog Nodes (FNs) and the Internet of Everything (IoE) [
44], which will help accomplish the technologies in future smart cities in a distributed manners. The Fog Data Center (FDC) [
45] offers a promising platform for analyzing and filtering the data generated by different sensors utilizing the resources of the Fog Nodes. The fog environment demands the deployment of a huge number of fog nodes and the correlation of this network with the fog data center.
Recently, the idea of merging the ‘‘Internet of Things’’ and ‘‘Social Networks’’ has been executed, gaining popularity overnight. The well-known ‘‘Social Internet of Things’’ (SIoT) paradigm has the potential to carry many required implications into a future smart world, which is highly populated by smart devices spread throughout the daily life of human beings. The idea of socialization among smart heterogenous objects for the first time has been introduced by Lars. E Holmquist et al., in Reference [
46]. They focused on a system which could enable intelligent wireless objects/devices—mostly wireless sensors—to develop temporary relations. A substantial step towards the SIoT paradigm was accomplished in Reference [
47]. In this paper, the insinuations of the emergence between the social networks and IoT have been examined, moreover, a few interesting exemplary applications are described as well. This paper, however, does not describe how social relationships should be established by objects and does not propose any solution regarding the required architecture and protocols. Regardless, for the better understanding of the social networks, social relationships, and social behavior, we always seek help from the concepts in sociology and anthropology [
46,
48]. The motivation behind SIoT is to socialize the Internet of things in such a way that the communication and searching of the right devices and services could be performed efficiently. Therefore, social devices can build their networks according to the rules set by the owners [
19]. There could be many reasons for introducing the SIoT infrastructure, but above all is the reason is to establish and exploit the social relationships among real-world objects instead of their owners. The owners’ intervention can be foreseen, but all “things or objects” have to play their key roles.
The implication of the Social networking concept in IoT is proven to be a breakthrough in the Information Technology (IT) arena. Smart IoT objects use the properties of social networks for constructing network or relationships among objects where objects play the role of social actors (such as individuals or organizations) and the links among them are considered relationships between social entities. Smart IoT objects mimic human behavior for friendship selection, communication, and sharing environmental information. IoT devices follow the instructions or rules set by their owners for selecting, replacing, or removing a friend device [
19]. In short, the SIoT paradigm works like a real-world social network. Social networks are an interdisciplinary field of sociology, social psychology, graph theory, and statistics. Emile Durkheim and Ferdinand Tönnies prefigured the idea of social networks in their research in the late 1980s. Ferdinand Tönnies claimed that “social groups can exist as personal and direct social ties that either link individuals who share values and beliefs or impersonal, formal, and instrumental social links”, while Emile Durkheim gave a non-individualistic explanation of social facts. We are living in the world of networks where any intricate structure in nature can be shown as a network; in which nodes are considered elements of the structure and edges represent the connections among them. Social networks, neural networks, biological and chemical structures, computer networks, and the Internet are the most common networking demonstrations [
24]. The Watts and Strogatz model exhibits the topology of some social networks in three different states. The first one is a regular graph or network where the probability of the randomness is 0 (i.e., the minimum random connections among the nodes), the second state is a random network with a probability of 1 (i.e., the maximum random connections among the nodes). The third state is the intermediate form of the regular and random network, known as a small world network, which is also known as the small world problem or the small world phenomena.
We can define the “small world problem” as follows: “What are the probabilities that two randomly selected people from a population could have a mutual friend?” [
49,
50]. The small world problem has been appealing to researchers from many fields, such as mathematics, history, computer science, sociology, psychology, communication studies, and political science [
25,
51]. Numerous mathematical models have been proposed by mathematicians to reveal the rational work of small the world problem paradigm [
23]. Computer scientists perform experiments on big data to provide empirical evidence [
52]. Small world networks are present everywhere, such as in the form of emails, scientists and actors, the World Wide Web, collaboration networks, power transmission grids, and online social networks. The vast study of small world problems helps us understand why the social network is organized in the way it is, and how it spreads information, such as how a contagious disease spreads in a network [
27].
3. Proposed Work
The social network paradigm is gaining popularity due to its vast and flexible nature. The social networking notions allow IoT objects to establish their social relationships autonomously. The motivation behind this paradigm is to maximize or to boost the capability of IoT devices to select, discover, and comprise of different services and information gathered by the heterogeneous devices connected to the physical world. In the SIoT paradigm, the smart object (i.e., the IoT devices) mimic human nature and build their relationships like social actors. IoT devices follow the rules set by their owner for constructing a network and searching for objects, information, and services. As a social network is a network of social entities and because these entities are strongly tied with each other, the network complexity is increased and a triadic closure is produced. Triadic closure is a concept in social networking which indicates the existence of strong or weak connections among three nodes. Assume that A, B, and C are three nodes in a network; if a strong link exists between A and B as well as A and C, then there is probably also a link between A and C. This triadic closure has a significant existence in social networks, which helps in carrying and spreading information among network nodes. However, due to triadic behavior, there is always duplicate information in the network. The duplicate information and triples might not be a big issue in small networks but it creates a problematic scenario when the network is very big and complex.
In the near future, when more than 50 billion devices will be connected with each other [
31], all the devices will generate and share their data with each other, which results in the scalability and navigability being the biggest issues. To prevent these issues, in this research, we suggested a well-known small world network for the SIoT infrastructure in order to enhance the network navigability and scalability. The proposed work uses the characteristics of both SIoT and small world paradigms. Small world phenomena reveal that by utilizing acquaintances (i.e., those who we know by a first name) within six steps, we can connect to anyone in the world. In the same way, SIoT system devices can connect to the devices that they know by their first name (i.e., only friends’ devices) and share their information and get the desired services. In this paper, we follow the rules defined by Stanley Milgram during an experiment on small world phenomena. The small world network has a restrictive property which does not allow contact with a node if it is not known by its first name. Moreover, to get rid of the duplicate information, we applied a constraint, that is, while selecting friend nodes, the parent node does not add a node that is a mutual friend with an already existing friend. Our smart social agent adds the friend nodes based on logical configurations (i.e., common interests, information, and services), thus, the smart social agent saves the information of all friend nodes (i.e., the personal fiends that lie in the first layer of the network nodes). The ultimate achievement is that the smart social agent is more efficient in navigating the network, it reduces the network complexity, it avoids unnecessary queries and their replies, and it reduces the temporal complexity in searching for required services.
Due to the SIoT characteristics, the smart social agent communicates with heterogeneous devices while building social networks of devices and thus the smart social agent mimics small world behavior. The smart social agent only connects with devices that it knows by a first name and that have the same logical configurations. To avoid triadic behavior, we restrict the smart social agent to keep the friends count within a range that has minimum mutual friends. Although, in a real-world scenario, it is highly unlikely for two friends to live in the same place or work at the same place and have friend circles that do not have any mutual friends. For this situation, we set a rule that the smart social agent cannot add two nodes if they are friends with each other. In this case, the smart social agent will choose the node with more common interests. Let us assume that both friends have their own friend circles (i.e.,
). Here,
. Here,
is the total number of people that have an equally likely chance to be friend with
. Suppose that each group has
friends from
, therefore,
. However, suppose that there is a probability that
, Equation (1) gives us the probability of the mutual friend.
The Equation (1.1) is the expanded form of the Equation (1). For a small population and a small friend group size, this equation may be easy to solve, but for a large population, the computational time and complexity will be very high. However, to avoid complexity and to perform the computation in a reasonable time, we use the Stirling approximation Equation (1.2).
3.1. Friend Selection
The smart social agent inherits the qualities and the capabilities of humans and mimics human behavior while searching for friends or services for establishing a social network of heterogeneous smart objects.
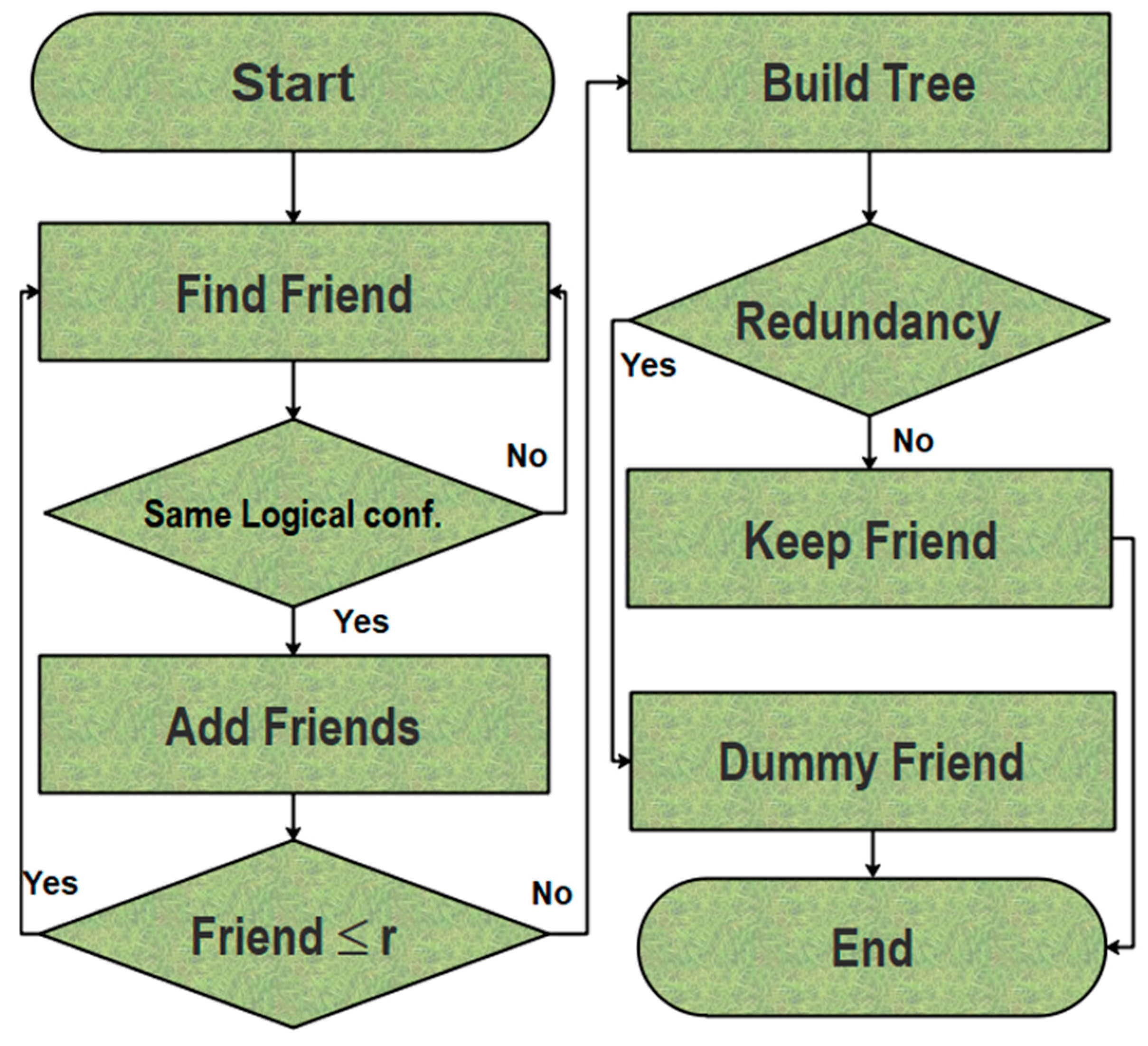
Figure 2 shows the flow chart which reflects the procedure of friendship selection in the proposed work. Algorithm 1 explains the steps of friend selection for an individual’s small world phenomenon.
| Algorithm 1. The friendship selection algorithm. |
| Input: File of List of logical configurations “”. |
| Output: Friends circle “” | |
| Step 1: Find a friend |
| If () = = friend’s () |
| {add friend ();} |
| Else {Find friend “” } |
| Step 2: Check threshold () |
| If ( < ) |
| {Execute step 1;} |
| Else {Build Balance tree;} |
| Step 3: Check redundancy |
| If (Redundant) |
| {add dummy friend node “”} |
| Else {keep friend “” } |
| End ( ); |
3.2. Explanation
In Algorithm 1, to train the Smart Social Agent, the owner sets some rules according to his wish and the Smart Social Agent follows these rules to assist its owner. In step 1, Smart Social Agent finds friends inside the owner’s friend list and checks the logical configuration. The process continues until the friend count reaches the threshold. Here, the threshold is required to avoid triadic closure. After obtaining all friends and friends of friends, all nodes will be presented as a balance tree. As the tree is the restricted form of a graph, it can represent friends that are original stack holders. The time and computational complexity of a graph are very high, but a tree, on the other hand, is quite a different scenario. Especially if we make a small world with a certain threshold. Then, searching for a friend, information, or desired service needs less time and computational complexity, i.e., Θ (log (n)). We choose Balanced Tree because its complexity is lower than the graph.
Logical configuration is defined as the information required by a Smart Social Agent. This information is asked by devices and lies under the Smart Social Agent. The logical configuration could be explained as the actual requirement of a human. There could be certain scenarios where the device can act for the betterment of humans according to certain configurations, such as room temperature in a specific season or during illnesses. These Smart Social Agents will be sorted and saved as an array. If the logical configuration matches, the Smart Social Agent will save it in the array, otherwise, it will discard it. Lastly, if the friends are above the threshold, the Smart Social Agent will terminate them accordingly. If the configuration matches with the friend, the agent will add it to the small world tree unless the friend count is less than the threshold. There could be possibilities like mutual friends that can violate the rules defined in the balance tree. To accommodate such scenarios and to keep the balanced tree properties intact, we add dummy nodes. The dummy nodes have flags to help the traversal of the tree. If a dummy flag is found, then the algorithm will not traverse the node and search for other options.
3.3. Network Depth: (Degree of Separation)
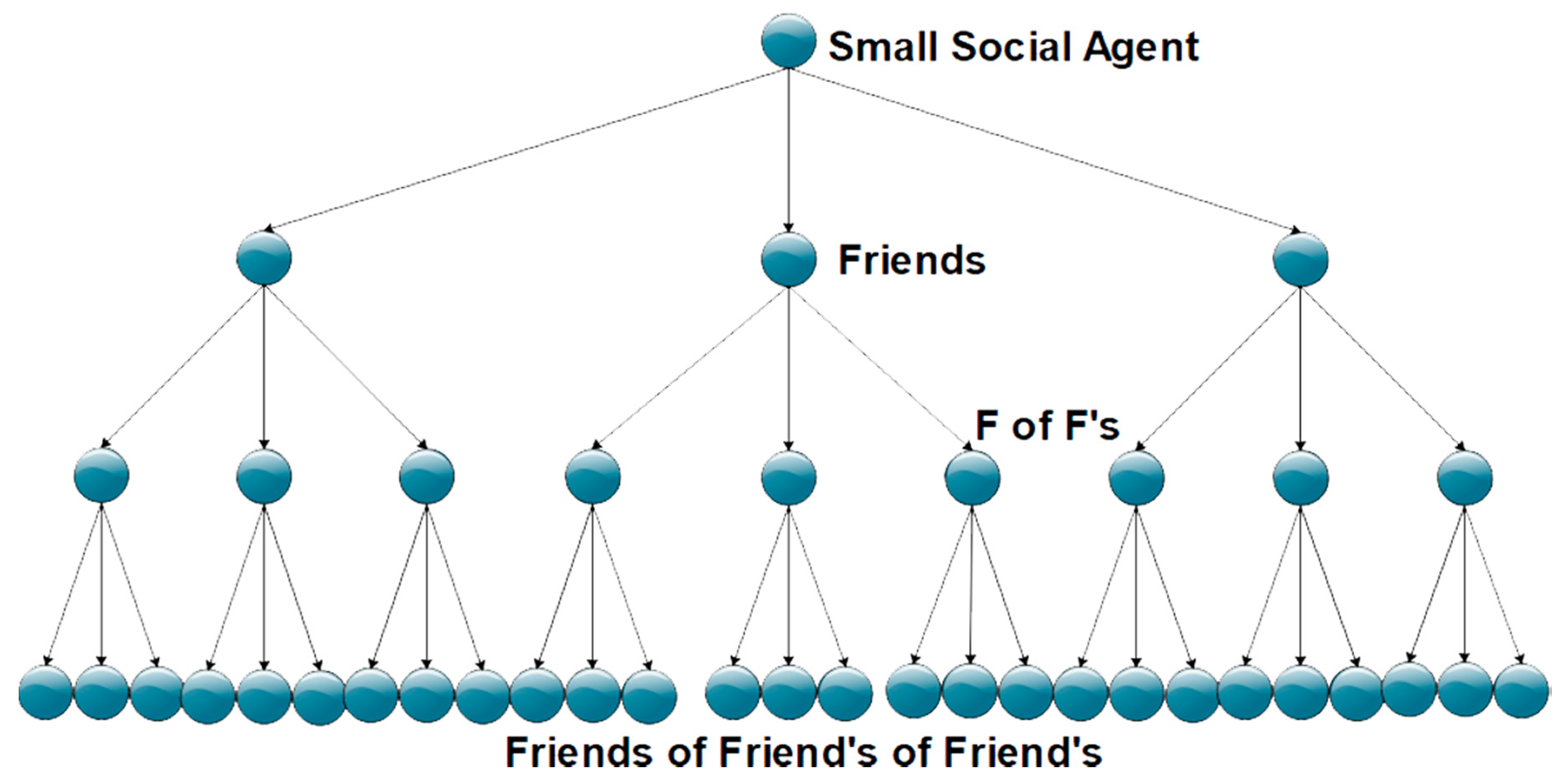
There are several ways to visualize the network architecture or the connections between the nodes. Therefore, the balance tree is the most useful representation of such structures; see
Figure 3. So, we used a balanced tree in our proposed work to highlight the sequentially increasing behavior of the network up to a fixed number of depth levels. Some may ask the question, why did we choose the balanced tree? We have a brief answer to this question. The balanced tree graphical representation is quite easy to understand, it is clear and efficient during searching, it increases sequentially with the same pattern, and it avoids redundancy.
Moreover, because of its consistent behavior, finding a total number of nodes, the degree of the nodes, and tracking the nodes is quite easy.
In
Figure 3, suppose we have a finite set of devices (i.e., friends) denoted by
Assume that each of the nodes in “
” has an “
” number of connections associated with them or the degree of the node. Similarly, in the next step, let us consider that all of these “
” connections further have an “
” set of connections and so on, up to a finite number of levels (i.e., the network depth). By seeing the sequentially increasing mechanism of these links, we can calculate the total number of nodes as
. If we keep continuing to make connections, then, at the next level, the number of nodes will be
,
, … and at
nth level, the total nodes will be
. The total number of nodes in the network can be calculated using Equation (2)
The total number of nodes can also be calculated using Equation (2.1)
Here,
is the total number of nodes in the network connected in a pattern. This pattern represents the geometric series, which can also be written in the form of Equation (2.2)
Here, “” is the first term, which is always in our balance tree representation, while “” is the common ratio or a constant number of connections of each node. “” is the finite number of steps or the network depth, which represents the degree of separation in the small world concept.
Figure 4 contains the pictorial representation of our proposed scheme. To elaborate our idea, let us go through with this example. Assume that
and that we have
connections for each node in
,
total layers in the network including the first term, and
= total devices in the network.
We replace the values of “”, “”, and “” in Equation (3). By putting these values into Equation (3), we obtain the total number of devices in a network, which really helps to scale the network.
3.4. Searching for Information
Finding information in a large and complex network like a social network is still a big challenge. The internet is the most suitable example of social networking, with billions of devices connected to the internet to share information. When attempting to find some information in response to a query, we always get millions of replies based on the best-matched responses, closely related responses, or responses with the same keywords. However, finding the exact information among the search results is still a quite difficult task. Our proposed “Small World SIoT” paradigm really consider this issue and we suggested an idea to tackle it efficiently. Adding only friend nodes in a network ensures security and privacy, which eliminates the DDoS possibilities in the network [
53]. Techniques like key authentication can be utilized while selecting friend devices [
54]. Additionally, neglecting mutual friendships decreased the network complexity and duplicate information.
Figure 5 shows an exemplary scenario of a small world network which illustrates the searching mechanism.
The red node is a smart social agent and here it has four friend nodes (i.e., nodes that it knows by their first name). The smart social agent added them based on logical configurations (i.e., common interests) or because they can provide services in the mentioned arena. Because our proposed system is a sequentially increasing network, all four of these nodes further have four nodes each. The network depth can vary but the claim of “six degrees of separation” ensure us that the information can be found within six steps. However, in our case, we visualized the network depth up to three degrees of separation. The bold colorful lines represent the best possible path to find the information. For further explanation, suppose the smart social agent is always interested in finding information or seeking help to get served in the mentioned fields, where purple nodes contain educational information, yellow nodes belong to the medical field, green nodes have industrial information, and sea green nodes are good in the entertainment industry or they can provide any service to the smart social agent related to their fields. Let us take an example of medical information or a medical service; there are many nodes containing medical information. However, instead of traversing all the nodes or getting information from all the nodes, our smart social agent knows which node could have the information (as the SSA saves brief information of its personal friends while adding nodes). Therefore, the smart social agent will directly contact the yellow node instead of asking the other three nodes. If the information is available with that node, it will provide it, otherwise, the same step will be taken by the yellow node and instead of asking the other three nodes, it will ask its yellow child node. For instance, if the information is available with the yellow node at the third layer, the black line will be the path to obtain the information. If the smart social agent fails to get the information using the best possible path, it will then ask for information from the other nodes.
4. Results and Future Work
Figure 6 shows the percentage of mutual friends with respect to the increasing count of friends per smart social agent (i.e., person). In this paper, we considered the population of Anchorage, Alaska, and examined the probability of the existence of mutual friends between two different friend groups among the population. Anchorage is a city with a population of 298,700. Although, in a real-world scenario, due to the frequent use of social networking apps these days, most humans are connected with an average of 500 people that they know on a first name basis. However, because of mutual friends, family, and locality-based friends or, in short, because of triadic behavior, information always circulates within the circle. Moreover, sometimes information that is fetched is not very helpful.
Consequently, our proposed work is efficient enough to tackle the ongoing problems. For instance, the smart social agent does not send or accept the friend request if the object is a mutual friend of its first friendship layer or if the agent does not know the object by its first name. Our algorithm avoids triadic behavior, helping us to grow the network sequentially in an exponential manner and gain accurate information swiftly. On the other hand, the algorithm does not allow for the agent to talk with unknown entities, which is helpful in avoiding security and privacy issues. Thus, each friend (Node) shares only its first friendship layer, as shown in
Figure 3. Therefore, every node has its own small world according to its desired services. For future work, we are designing an algorithm which can find the required service or an object in a minimum amount of time, compare to the SIoT paradigm. So far, numerous researchers are dealing with small world problem with hypothetical figures, which gives an estimated value of the total number of friends, mutual friends, and the degree of separation. Consequently, we are working on a formulation that will provide an accurate friend count and degree of separation in real-world scenarios as well.
Our proposed individual small world, ideally, needs a network with 0 mutual degrees. This is not possible in a real-world social network scenario.
Figure 6 (the evaluation of an individual small world on the population of Alaska) shows that the number of mutual relationships is (roughly) linearly proportional to the number of friends. After crossing a threshold of 57 friends, the mutuality starts to appear. However, for the best results, we chose an optimum number of friends which has approximately 0 mutual degrees, around 10 friends. For further evaluation, the dataset of a social networking website named Slashdot [
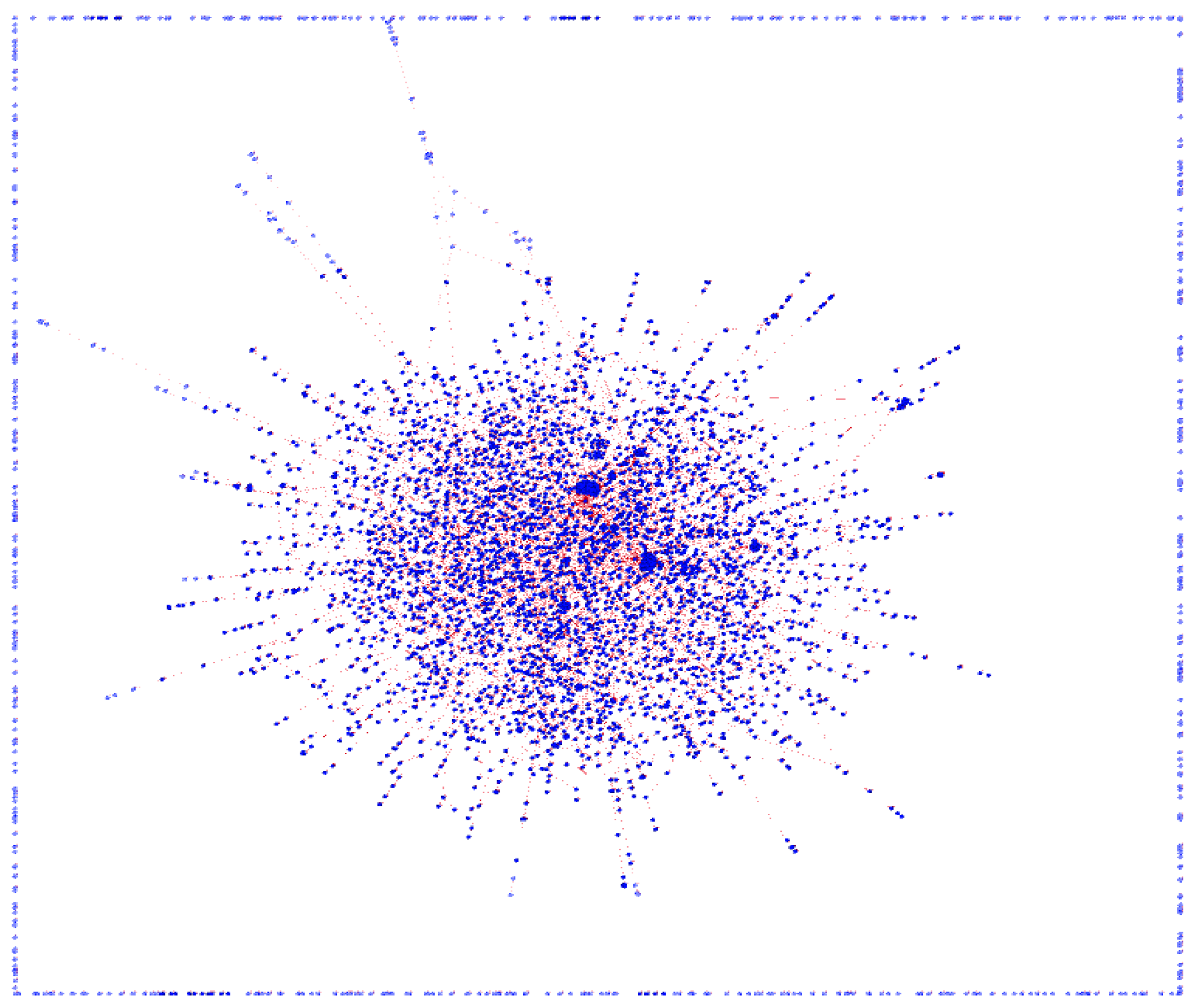
41] was used. Slashdot is a technology-oriented news-sharing website that features user-submitted and editor evaluated content. The website also contains a tag feature with which users can label people as friends or foes. The resulting network contains directed links between friends/foes. It consists of 82,168 nodes and 948,464 edges. The number of nodes was narrowed down to 10,000. The generated network, ‘A’ (i.e., the Slashdot social network), is shown in
Figure 7. The blue color indicates the nodes and the red texture underneath indicates the edges. On the fringes of this network, nodes with an in-degree value of 1 and an out-degree value of 0 can be seen. In order to evaluate our proposition, a filter was applied. The filter contains the union of three conditional parameters, i.e., (a) a mutual-degree = [0, 1], (b) an in-degree = 1, and (c) an out-degree = 24. The resulting network, ‘B’ (i.e., the small world network of Slashdot social network), is shown in
Figure 8.
Here, it can be seen that the mutuality has been diminished to a great extent. On the borders of Network B, many nodes are present in isolation. In the center of the top border, a connection between nodes in the central part of the network and the nodes residing on the border of the network is visible. Here, the phenomenon of individual small worlds is noticeable. It can be said that two small worlds, say sub-network C (central) and sub-network P (peripheral), are connected with at least one link in a network with minimum mutuality. Furthermore, in C, the separation among the individual small worlds in the form of loosely coupled layers can also be seen. This further consolidates the idea of optimizing a social network with respect to small worlds. This discovery is encouraging because it has been evaluated with a real-world directed social network dataset. The comparison between Network A and Network B is presented in
Table 1.
Network B has a lower clustering coefficient value because of the reduced degree of connectivity caused by the smaller values of filtration parameters. Network B also shows an increase in the network diameter and the path length. Since the degree of the filtered network was reduced, many existing links were dismissed. These links contained hubs (nodes with a high degree of connectivity). After the dismissal of the hubs, the path is bound to be greater because the nodes with lower connectivity require additional searching and a higher number of hops. The average degree has been reduced greatly. Though it is a parameter that is well suited to undirected networks, we have included it here because the value for the out-degree in our network is comparatively greater than the in-degree and the mutual-degree. This guarantees a non-zero mutuality.
The distribution shows a significant number of nodes with a degree distribution of 0. The small world phenomenon is satisfied here because the mutuality is lesser to a great extent. There is an uneven growth in the degree due to the pruning of data in the original dataset and the application of the filter over the pruned data Clustering Coefficient Distribution is shown in
Figure 9 to a great extent. The distribution shows a majority of nodes with an approximately zero clustering coefficient value. This indicates a lack of shortest paths in the network. The findings presented in
Table 1 also indicates an increase in the path length value for Network B, which is validated with this graph. .
Figure 10 presents a normalized graph for the Closeness Centrality Distribution.