Efficient and Privacy-Preserving Data Aggregation and Dynamic Billing in Smart Grid Metering Networks
Abstract
:1. Introduction
1.1. Contribution
- First, we propose a new and efficient data generation and aggregation scheme to preserve the security and privacy of consumption usage data between the smart meter and data concentrator. The CGs are not able to derive the aggregated sum of the consumption data, but can only check the validity of the received reports. Moreover, to attain the efficiency at resource-constrained SM, we employed the elliptic curve cryptography, symmetric encryption, and one-way hashing operations.
- Second, we propose a price determining and dynamic billing mechanism that derives the dynamic price for different time-slots and computes the accurate bills for the customers. In addition, a customer can verify whether the energy bill received is accurate.
- Third, we successfully evaluate the security strength of the proposed scheme under the indistinguishability against adaptive chosen ciphertext attacks (IND-CGCCA) and unforgeability (also called existential forgeability against adaptive chosen message attacks—EUFCMA). Thus, the proposed scheme is also provably secure.
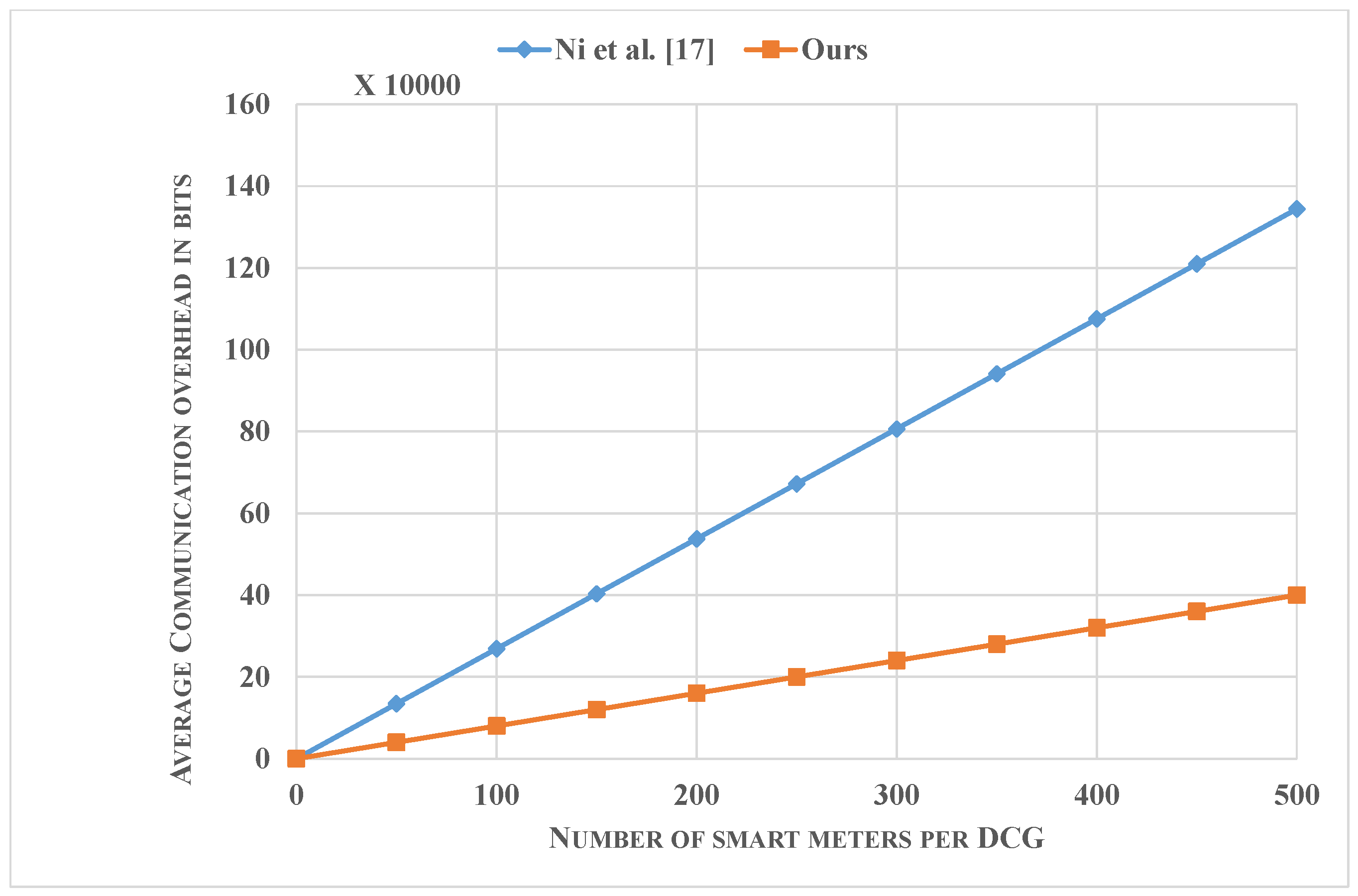
- Finally, we present performance comparisons of the proposed scheme, showing that our scheme requires lower computation and communication costs than the existing schemes. To be more specific, the total computational time for the report generation for until the computation of the bill by the customer would require 632 µs. With respect to communication costs, the security related information requires a payload of 1920 bits. We also show the scalability of our scheme regarding communication overhead from SM to CG and CG to OC for a varying number of SMs.
1.2. Outline of the Paper
2. Related Work
2.1. Privacy-Preserving Data Aggregation
2.2. Privacy-Preserving Data Aggregation and Billing
3. System and Adversary Models, and Design Goals
3.1. System Model
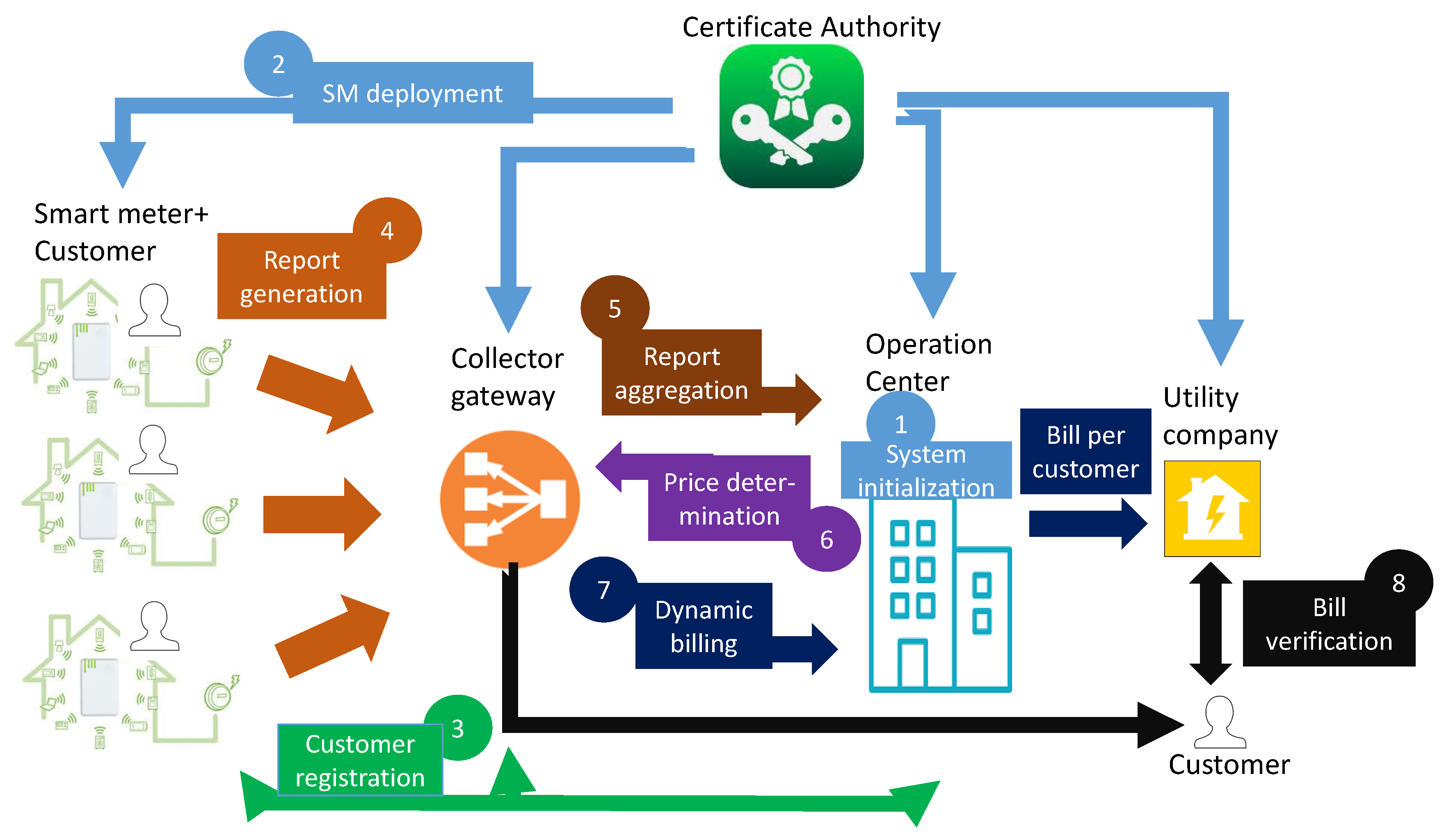
- Operation Center (OC): In general, this entity is responsible for the realtime maintenance, the analysis of the power quality, and the determination of dynamic prices for the electricity consumption in a certain region at different time slots per day. Please note that this paper will mainly concentrate further on the last aspect and show how the OC is able to compute the final price to be paid by each individual customer based on these variable prices. In our system model, the OC is considered to be a trusted entity, which generates and publishes the system parameters in the scheme. It also registers all entities participating. Although it is able to derive the final price to be paid by the customer, the OC should not have the possibility to derive the individual user consumption at each moment of the day. Instead, the OC must check the integrity of the received aggregated consumption data and be ensured that the dynamic prices are applied in a correct way.
- Data Collector Gateway (CG): This entity is responsible for the collection and aggregation of the information sent by the SMs in a certain region. Please note that from the information sent by the SMs, the CG is not able to derive the real user consumption usage data for a specific time period or even aggregated period. The CG can verify the integrity of the transmitted messages of the SMs. Later, based on the received dynamic prices, the CG can make computations on the encrypted data such that only the OC and customer are able to derive the real price. The CG is assumed to perform all the required actions. The CG is also considered to be a resource rich device and that to possess sufficient tamper proof storage for storing the secret shared keys with the SMs.
- Smart meter (SM): In a home area network even a building area network, the SM sends every fixed period (encrypted) information related to the realtime measured electricity consumption to the CG [19]. The SM is assumed to be a resource constrained device. The communication between the SM and CG can be established with the low power and/or long range technology, such as LoRa or by means of Power Line Communication (PLC) as studied in [20,21,22,23].
- Utility company: The utility company generates the customer’s bill based on the data received by the OC.
- Customer: The customer integrates own security material onto the SM via, e.g., USB. Moreover, based on the published dynamic prices of the OC and the data stored at the CG, the customer can check the validity of own bill that is generated by the Utility.
- Central Authority (CA): This trusted third party consists of two divisions. One division manages the distribution of the legitimate SMs. Each SM is installed with two pre-stored keys, one shared with the CG and another with the OC. The other division is responsible for the generation of a certificate for each legitimate entity (i.e., CG, OC and the customer related to a particular SM). This certificate allows to compute the corresponding public key.
3.2. Adversary Model
- The adversaries can eavesdrop on the communication messages sent between SM-to-CG, CG-to-OC, inject new messages, or replay and change messages following the Yao-Dolev security model [24]. This involves the real man-in-the-middle and replay attacks.
- For the sake of reality, consider an (insider) adversary, he/she can attack the CG’s database (e.g., aggregation reports, billings, feedback, etc.). The adversary can retrieve the information stored in the non tamper resistant part of the memory. These information may include encrypted consumption data and/or corresponding auxiliary data of the different SMs over the different periods of time. More precisely, the insider may aim the following attacks. First, an internal attacker, can inject the false data that provides wrong energy feedback to unbalance load management in a power grid. Second, the insider attacker (e.g., CG) might be interested to derive the individual consumption data in order to sell this information to other parties, e.g., social media, etc. Third, the CG might also be trying to deceive the OC by including other fake consumption data. Fourth, the CG might be trying to attack a particular SM in order to increase its electricity bill or contribute with a malicious SM to decrease the bill.
- An adversary may perform an impersonation attack on one or a group of SMs to send fake data on behalf of non-compromised SMs to the CG. Moreover, an attacker can also be a malicious customer, being aware of the private key of the SM, that tries to modify the real consumption data.
3.3. Design Goals
- Confidentiality: The individual user consumption for each specific fine grained period should not be leaked to any entity, including the CG and the OC, at any circumstance. This information is very sensitive as it could be used to derive user’s behaviour. In addition, no information on the aggregated consumption at SM or regional level should be leaked to both the CG and any other outsider. Finally, the total price to be paid, should only be derivable by the OC and the customer.
- Integrity: The integrity of the messages should be checked at several places into the scheme in order to be sure that the correct electricity bills are derived. First, the CG should check that the consumption reports sent by the SMs at the different periods are unaltered by outsiders, and hence coming from legitimate registered SMs. Second, the OC should be ensured that the derived aggregated consumption data is based on the received consumption data of legitimate SMs and thus, does not include data coming from outsiders or a corrupted CG. Finally, the OC should also be able to verify that the derived final price for a certain SM is based on the sum of correct combinations between the received consumption data of that particular SM and the defined price in that region for each period.
- Authentication: This feature ensures that the transmitted data is coming from a registered SM and legitimate CG. Correct establishment of the authenticity feature avoids impersonation and man-in-the-middle attacks.
- Efficiency: Typically the SM is a resource constrained device, therefore, a security scheme should take communication and computation efficiency into consideration.
4. Preliminaries
4.1. Brief Background of Elliptic Curve Cryptography
- The Elliptic Curve Discrete Logarithm Problem (ECDLP): This problem states that given two EC points R and Q of , it is computationally hard for any polynomial-time bounded algorithm to determine a parameter , such that .
- The Elliptic Curve Diffie Hellman Problem (ECDHP): Given two EC points with two unknown parameters , it is computationally hard for any polynomial-time bounded algorithm to determine the EC point .
4.2. Private-Public Key Generation
5. Proposed Scheme
- System initialization: The OC fixes the cryptographic mechanisms to be used (EC, generator P, Hash function H), retrieves a certificate with the CA, generates its corresponding private and public key and publishes . Also the CGs retrieve a certificate with the CA, generate their corresponding private and public key and publish .
- Smart meter deployment: In this phase, the CA installs two secret keys, and , in the tamper resistant module (e.g., low cost TPM [29]) of the SM. The group key is shared with the CG to which the SM will report, and is shared with the OC. Please note that these keys can be renewed by the CG and OC respectively through dedicated unicast communications to all active registered SMs. In addition, the public key of the CA, , together with the EC parameters and required security functions are also installed on the device.
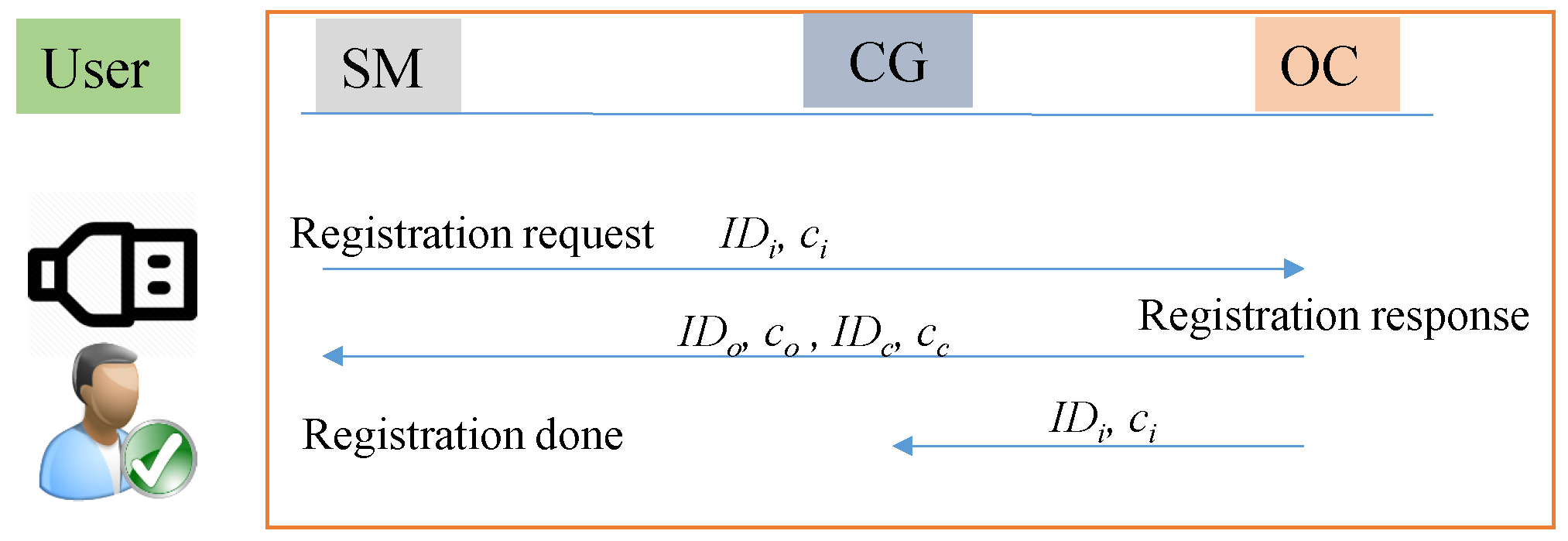
- Customer registration phase: In this phase, the customer belonging to region R receives a SM with pre-stored keys and . Please note that the device possesses a USB connection, which is used by the customer to install its own secret keys. To activate the device installed in its house, the customer needs to undergo three processes. Therefore, the OC provides as a service to the customer a secure web portal for the communication with the CA and with itself. Moreover, a secure offline program is also provided, which needs to be downloaded by the customer and will prepare the required script, used to install the secret keys into the SM. As a first step, the customer contacts the CA and receives a certificate , which is bounded to its identity , consisting of its personal identity and the serial number of the SM. Second, the customer registers with the OC by sending the message containing the parameters . Following the ECQV scheme, the OC is able to compute the public key of the using . The OC responds with sending the certificates and identities and of itself and the CG to which it should communicate. The customer now enters and the secret random value used to initiate the certificate process of into the offline program. Based on this input, the program is able to derive the private and public key pair and the public keys and of the OC and CG respectively. Also the secret shared keys and with the OC and CG respectively are computed. Through the USB connection, the customer is now able to install in the tamper resistant part of the hardware of the .The OC also sends to the CG the identity and certificate of the , joining its region. The CG computes the corresponding public key of the and securely stores in its memory. The flow of customer registration phase is summarised in Figure 3.
- Report generation: At the beginning of the day d, the generates . Please note that this value is similar for all legitimate and registered SMs.After a fixed period T, at timestamp , with , the reads the consumption measurement and computes the following operations:Next, the message is sent to CG.
- Report aggregation: For each received message, the CG first checks the integrity and authenticity of the message by verifying the correctness of using . If negative, a correction message is requested. If the SM fails to send a correct message, it will be excluded and reported to the OC. If positive, the CG stores all the received messages with during day d by the N different with and identity from its region. Please note that the customer has access to the database where this information is stored.There are in general 6 (each 4 h) or 24 (each hour) periods per day in which the data is aggregated. At the end of a particular period , for instance a period consisting of s different time slots (e.g., ), the following operations to aggregate the different consumption messages of all with in its region are made.The message is sent to the OC.
- Price determination: In this phase, the received report first needs to be read by the OC. Upon arrival of the message , the OC first computes for all N SMs at the time period with in its regionThen, the OC checks the following equality:If the equality is correct, then the actual consumption data M for that period of the N SMs in its region equals toBased on these aggregated consumption data in a specific region, the OC defines the fluctuant electricity prices for that region, corresponding to the different time slots with . These prices are sent to the CG and officially published.
- Dynamic billing: Based on the received prices, the CG now performs the following operations for computing the bill of the :The message is sent to the OC. The OC can then verify the computation of the CG, and after a positive validation compute the effective price. Thus, in order to verify the operation of the CG, the following equality should hold:If so, the effective price p equals toThe message is securely sent to the utility company.
- Customer verification: The customer can now verify the computed price p, by consulting both the stored values with the CG and the published prices for that particular day d, using its private key . This key allows reconstruction of and for all , and thus the determination of the equation:
6. Security Analysis
6.1. Formal Proof
- : In this query, randomly selects a value , sends r as response to and stores in table the tuple with .
- CreateSM(): In this query, generates a private key and certificate for the SM, and stores it in the table .
- CreateReportSM(): First, checks if exists in . If not, does a CreateSM() query. Else, for a given , it generates a tuple and stores it in the table .
- CreateAggregatedReport(): In this query, first checks if the reports of the SMs are available. If not, CreateReportSM queries are executed. Else, a random value z and private key for the CG are chosen and used to compute the aggregated report . This value is stored in the table .
- Retrieve(): Here, checks the validity of the report and decrypts it to get the aggregated consumption data m.
6.1.1. Game 1
6.1.2. Game 2
6.2. Informal Proof
- Confidentiality: The individual user consumption of a SM with identity for each time slot cannot be retrieved by an outsider, other SM, CG or OC. This follows from the fact that the only two parameters containing this information, , include knowledge which is either uniquely known by the CG or the OC, taking into account the hardness of the ECDHP. The aggregated consumption data of the SMs can also not be leaked to an outsider or another SM, as the parameter m containing information on the aggregated sum depends either on knowledge uniquely known by the OC or by the CG. Similar reasoning holds for the price to be payed.
- Integrity: The integrity is checked at three places. First, the CG checks that the reports sent by the SMs are unaltered and are coming from legitimate registered SMs. This follows from the fact that is included in the hash value to be checked by the CG. This parameter can only be computed by registered SMs, which is verified through the usage of its public key that is stored in the CG’s database.In the second place, the OC checks that the aggregated consumption data does not include data coming from outsiders, a corrupted CG, or a corrupted SM. To validate this fact, Equation (1) plays a major role. If a SM is sending corrupt info on the consumption data, then two different values of are included during the computation of the variables . Also if the CG has the intention to corrupt the sum of aggregated data, it would change the value by simply adding or subtracting a certain amount. However, this operation will always be noticed by the OC, as in that case Equation (1) will not be satisfied.Similarly, the OC can also verify that the derived final price for a certain SM is based on the sum of correct combinations between the received consumption data of that particular SM and the defined price in that region for each period, thanks to verification of Equation (2). This follows from the fact that in the calculation of , the parameters and are involved.
- Authentication: Identities and certificates are shared among the legitimate entities during initialization and registration, such that the corresponding public key can be unambiguously derived of it thanks to the ECQV mechanism. Authentication of the sender and receiver is obtained as the transmitted messages heavily rely on the usage of the private key of the sender and public key of the receiver. As a consequence, the message is only meaningful for the receiver and sender with the corresponding private and public key respectively.
7. Performance Analysis
8. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Zhou, X.; Brown, M.A. Smart meter deployment in Europe: A comparative case study on the impacts of national policy schemes. J. Clean. Prod. 2017, 144, 22–32. [Google Scholar] [CrossRef]
- Mai, V.; Khalil, I. Design and implementation of a secure cloud-based billing model for smart meters as an Internet of things using homomorphic cryptography. Future Gener. Comput. Syst. 2017, 72, 327–338. [Google Scholar] [CrossRef]
- Gaoqi, L.; Junhua, Z.; Fengji, L.; Steven, R.W.; Yang, Z.Y. A review of false data injection attacks against modern power systems. IEEE Trans. Smart Grid 2017, 8, 1630–1638. [Google Scholar]
- Asghar, M.R.; Dan, G.; Daniele, M.; Imrich, C. Smart Meter Data Privacy: A Survey. IEEE Commun. Surv. Tutor. 2017, 19, 2820–2835. [Google Scholar] [CrossRef]
- Song, T.; Debraj, D.; Zhan, S.W.; Junjie, Y.; Das, S.K. Survey of Security Advances in Smart Grid: A Data Driven Approach. IEEE Commun. Surv. Tutor. 2017, 19, 397–422. [Google Scholar]
- Chen, L.; Lu, R.; Cao, Z. PDAFT: A privacy-preserving data aggregation scheme with fault tolerance for smart grid communications. Peer-to-Peer Netw. Appl. 2015, 6, 1122–1132. [Google Scholar] [CrossRef]
- Wang, Z. An Identity-Based Data Aggregation Protocol for the Smart Grid. IEEE Trans. Ind. Inform. 2017, 13, 2428–2435. [Google Scholar] [CrossRef]
- Badra, M.; Zeadally, S. Lightweight and efficient privacy-preserving data aggregation approach for the Smart Grid. Ad Hoc Netw. 2017, 64, 32–40. [Google Scholar] [CrossRef]
- Asmaa, A.; Xuemin, S. Lightweight security and privacy preserving scheme for smart grid customer-side networks. IEEE Trans. Smart Grid 2017, 8, 1064–1074. [Google Scholar]
- Agarkar, A.; Agrawal, H. R-LWE based lightweight privacy preserving scheme for Smart Grid. In Proceedings of the International Conference on Computing, Analytics and Security Trends (CAST), Pune, India, 19–21 December 2016; pp. 410–415. [Google Scholar]
- Debiao, H.; Sherali, Z.; Huaqun, W.; Qin, L. Lightweight Data Aggregation Scheme against Internal Attackers in Smart Grid Using Elliptic Curve Cryptography. Wirel. Commun. Mob. Comput. 2017, 2017, 194845. [Google Scholar] [CrossRef]
- Vahedi, E.; Bayat, M.; Pakravan, M.R.; Aref, M.R. A secure ECC-based privacy preserving data aggregation scheme for smart grids. Comput. Netw. 2017, 129, 28–36. [Google Scholar] [CrossRef]
- Shaohua, L.; Kaiping, X.; Qingyou, Y.; Peilin, H. PPMA: Privacy-Preserving Multi-Subset Aggregation in Smart Grid. IEEE Trans. Ind. Inform. 2018, 14, 462–471. [Google Scholar]
- Fábio, B.; Denise, D.; Leon, B.; Johannes, B.; Max, M. A privacy-enhancing protocol that provides in-network data aggregation and verifiable smart meter billing. In Proceedings of the IEEE Symposium on Computers and Communication (ISCC), Funchal, Portugal, 23–26 June 2014; pp. 1–6. [Google Scholar]
- Tom, E.; Basel, H. Performance Analysis of Secure and Private Billing Protocols for Smart Metering. Cryptography 2017, 1, 20. [Google Scholar] [Green Version]
- Jianbing, N.; Kuan, Z.; Xiaodong, L.; Xuemin, S. Balancing security and efficiency for smart metering against misbehaving collectors. IEEE Trans. Smart Grid 2017. [Google Scholar] [CrossRef]
- Kazuma, O.; Yusuke, S.; Fumiaki, Y.; Mitsugu, I.; Kazuo, O. Privacy-preserving smart metering with verifiability for both billing and energy management. In Proceedings of the 2nd ACM Workshop on ASIA Public-Key Cryptography, Kyoto, Japan, 3 June 2014; pp. 23–32. [Google Scholar]
- Gope, P.; Sikdar, B. An Efficient Data Aggregation Scheme for Privacy-Friendly Dynamic Pricing-based Billing and Demand-Response Management in Smart Grids. IEEE Internet Things J. 2018. [Google Scholar] [CrossRef]
- Tung, H.Y.; Tsang, K.F.; Chui, K.T.; Tung, H.C.; Chi, H.R.; Hancke, G.P.; Man, K.F. The generic design of a high-traffic advanced metering infrastructure using ZigBee. IEEE Trans. Ind. Inform. 2014, 10, 836–844. [Google Scholar] [CrossRef]
- Noelia, U.P.; Itziar, A.; Luis, H.C.; Txetxu, A.; David, D.L.V.; Amaia, A. Study of unwanted emissions in the CENELEC-A band generated by distributed energy resources and their influence over narrow band power line communications. Energies 2016, 9, 1007. [Google Scholar]
- Uribe-Perez, N.; Hernandez, L.; Gomez, R.; Soria, S.; de la Vega, D.; Angulo, I.; Arzuaga, T.; Gutierrez, L. Smart management of a distributed generation microgrid through PLC PRIME technology. In Proceedings of the 2015 International Symposium on Smart Electric Distribution Systems and Technologies (EDST), Vienna, Austria, 8–11 September 2015; pp. 374–379. [Google Scholar]
- Huh, J.H.; Otgonchimeg, S.; Seo, K. Advanced metering infrastructure design and test bed experiment using intelligent agents: focusing on the PLC network base technology for Smart Grid system. J. Supercomput. 2016, 72, 1862–1877. [Google Scholar] [CrossRef]
- Huh, J.H.; Seo, K. Smart Grid Test Bed Using OPNET and Power Line Communication, Advances in Computer and Electrical Engineering; IGI Global: Hershey, PA, USA, 2017. [Google Scholar]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef] [Green Version]
- He, D.; Kumar, N.; Zeadally, S.; Vinel, A.; Yang, L.T. Efficient and Privacy-Preserving Data Aggregation Scheme for Smart Grid Against Internal Adversaries. IEEE Trans. Smart Grid 2017, 8, 2411–2450. [Google Scholar] [CrossRef]
- Darrel, H.; Alfred, J.M.; Scott, V. Guide to Elliptic Curve Cryptography; Springer Science & Business Media: New York, NY, USA, 2006. [Google Scholar]
- Standards for Efficient Cryptography (SEC). SEC 2: Recommended Elliptic Curve Domain Parameters; Standards for Efficient Cryptography Group; Certicom Corp: Mississauga, ON, Canada, 2006. [Google Scholar]
- Standards for Efficient Cryptography (SEC). SEC 4: Elliptic Curve Qu-Vanstone Implicit Certificate Scheme; Standards for Efficient Cryptography Group; Certicom Corp: Mississauga, ON, Canada, 2013. [Google Scholar]
- Moreno, A.; Hossein, H.; Kalikinkar, M.; Mauro, C.; Radha, P. Despicable me (ter): Anonymous and fine-grained metering data reporting with dishonest meters. In Proceedings of the 2016 IEEE Conference on Communications and Network Security (CNS), Philadelphia, PA, USA, 17–19 October 2016; pp. 163–171. [Google Scholar]
- Manuel, B.; Pooya, F. Certificateless signcryption. In Proceedings of the 2008 ACM Symposium on Information, Computer and Communications Security, Tokyo, Japan, 19–20 March 2008; pp. 369–372. [Google Scholar]
- David, P.; Jacques, S. Security arguments for digital signatures and blind signatures. J. Cryptol. 2000, 13, 361–396. [Google Scholar]



| Registration Phase (SM) | Report Generation (SM) | Report Aggregation (CG) | Report Reading Phase (OC) | Billing phase | |||
|---|---|---|---|---|---|---|---|
| OC | CG | Customer | |||||
| [16] | |||||||
| [17] | – | – | – | ||||
| [11] | – | – | – | – | – | ||
| Ours | |||||||
| Phase | [16] | [17] | [11] | Our |
|---|---|---|---|---|
| Report generation (SM) | 24.7 | 96.2 | 1.97 | 0.7 |
| Report aggregation (CG) | 2355.4 | 1657.23 | - | 565.06 |
| Report reading (OC) | 328.1 | 174.3 | Null | 16.56 |
| Dynamic billing (CG) | 2254.7 | Null | Null | 16.51 |
| Dynamic billing (OC) | 3564.1 | 26.5 | Null | 16.48 |
| Dynamic billing (Customer) | 54.9 | 183.4 | Null | 0.05 |
| Message | SM Report | Aggregated Report | Bill |
|---|---|---|---|
| [16] | 2688 | 2388 | 2880 |
| Proposed scheme | 800 | 640 | 480 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Braeken, A.; Kumar, P.; Martin, A. Efficient and Privacy-Preserving Data Aggregation and Dynamic Billing in Smart Grid Metering Networks. Energies 2018, 11, 2085. https://doi.org/10.3390/en11082085
Braeken A, Kumar P, Martin A. Efficient and Privacy-Preserving Data Aggregation and Dynamic Billing in Smart Grid Metering Networks. Energies. 2018; 11(8):2085. https://doi.org/10.3390/en11082085
Chicago/Turabian StyleBraeken, An, Pardeep Kumar, and Andrew Martin. 2018. "Efficient and Privacy-Preserving Data Aggregation and Dynamic Billing in Smart Grid Metering Networks" Energies 11, no. 8: 2085. https://doi.org/10.3390/en11082085





