Novel Sparse-Coded Ambient Backscatter Communication for Massive IoT Connectivity
Abstract
:1. Introduction
1.1. Backgrounds
1.2. Related Works
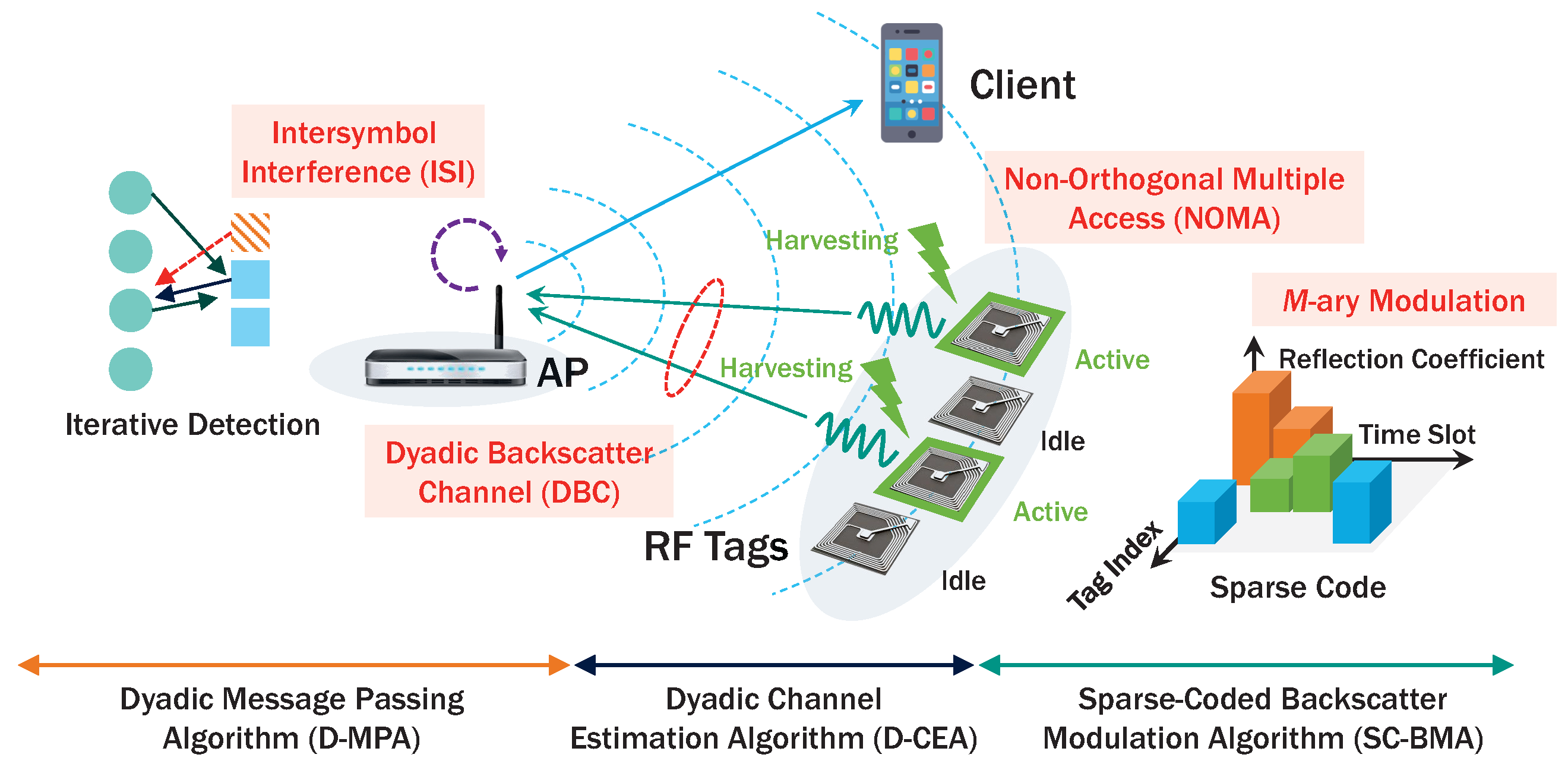
- Modulation and Coding Scheme (MCS): In AmBC, MCS is implemented by only passive RF components with limited circuit power. Advanced MCS such as an adapting power ratio in conventional power-domain NOMA, or infinite-length channel coding may not be available in low-complexity AmBC hardware. Hence, code-domain NOMA based on sparse coding is preferred to power-domain NOMA especially for AmBC applications [28,29].
- Channel and Detector Modeling: Generally, AmBC modulation is operated in time domain typically using OOK [5,6] and M-PSK [2]. NOMA modulation, on the other hand, is operated in frequency domain such as filtered OFDM [31] for mitigating multipath fading. Consequently, AmBC signal is severely distorted by ISI as a tag’s information is conveyed in a high-rate ambient RF signal and experiences a two-way fading channel in time domain. Thus, proper channel and detector modeling are necessary in AmBC to prevent performance degradation, which may be induced by application of NOMA.
1.3. Proposed Sparse-Coded AmBC (SC-AmBC)
- Grant-Free Uplink Transmission: With sparse coding, RF tags can transmit data in the uplink based on a predefined sparse codebook. The codebook structure can accommodate massive and bursty uplink traffic without a request-grant procedure [34]. The property can lead to low-latency without scheduling and resource allocation in contrast to the cognitive radio based AmBC [27].
- NOMA: Sparse code encodes data in multi-dimensional complex codewords providing higher degrees of freedom than conventional two-dimensional AmBC modulators [2,5,6,26]. As a result, sparse code can support concurrent RF transmissions and multiple-access interference (MAI) can be efficiently resolved by an iterative message passing algorithm (MPA) [32].
- Projected M-ary Modulation: In conventional AmBC modulators, M-ary modulation is only implemented by M distinct load impedances increasing form factors of RF devices for higher-order modulations [2,8,9]. On the other hand, with sparse coding, M-ary data can be represented by few constellation symbols using codeword projection/expansion method [35,36]. Thus, M-ary modulation can be realized in AmBC without increasing form factors of RF devices.
- Sparse-coded backscatter modulation algorithm (SC-BMA) supporting M-ary modulation for AmBC with small-form factors. The modulation can constitute multi-dimensional signal space, which can be easily implemented for passive RF tags without increasing form-factor and exempted from complex signal processing burdening low-cost RF tags.
- Dyadic channel estimation algorithm (D-CEA) fully capturing characteristics of DBC. The channel modeling includes both the effect of cascaded channel in AmBC and the effect of NOMA signaling and is distinguished from one-way Rayleigh and single-path fading channel without ISI.
- Dyadic MPA (D-MPA) based on dyadic factor graph exploiting the weighted-sum of ISI caused by DBC in information exchange process. The proposed MPA exploiting ISI instead of filtering it provides superior detection performance to traditional MPA designed for one-way channels.
2. System Model
2.1. Notation
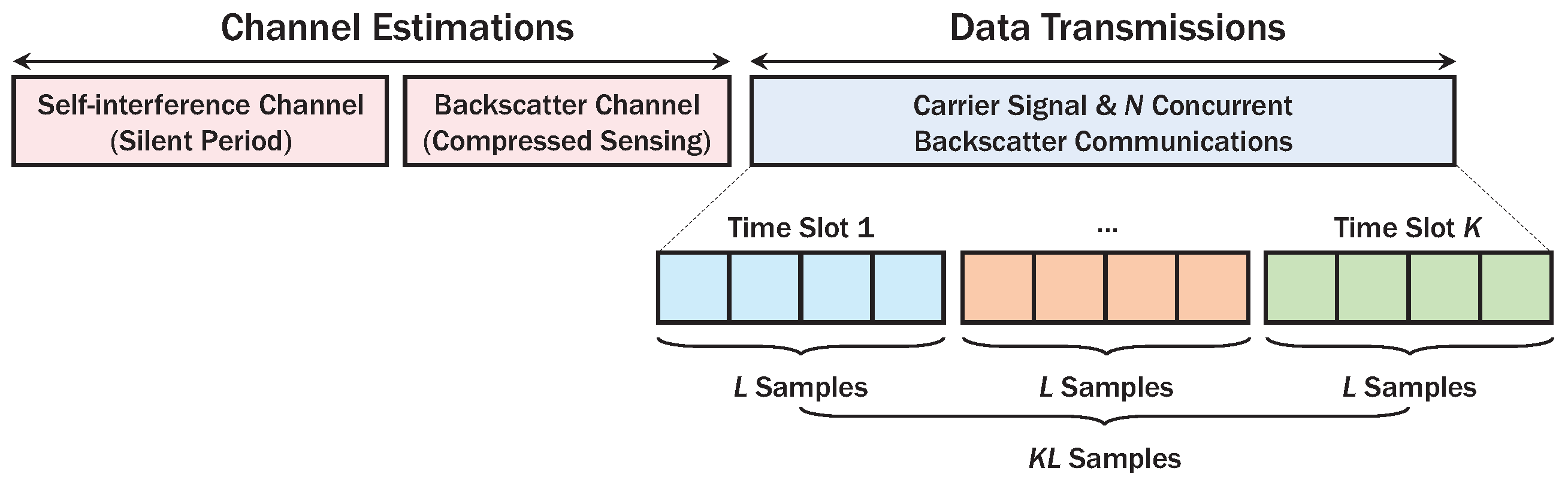
2.2. System Model
3. Sparse-Coded Load Modulation
- Small-form Factor: The size of the RF tags is very limited for IoT applications such as implanted biosensors and wearables, so they should have a small number of load impedances to reduce their size. The proposed SC-BMA can enable M-ary modulation [35,36] for these small-form factor IoT devices, which is in sharp contrast to traditional M-ary backscatter modulators with massive number of load impedances (e.g., M-PSK [2], M-QAM [8,52,53]).
- Interference Exploitation: Detection performance of AmBC is severely degraded by the interferences (i.e., MAI and ISI). To rather exploit these interferences for massive connectivity, we design the codeword structure capturing sparsity [39] of ambient EH and characteristics of DBC [18,23] where two-way fading and severe ISI occur.
- In each dimension, there are three constellation points (i.e., .
- A parameter set satisfies the inequality .
- Multidimensional symbols are mapped with Gray code labeling.
| Algorithm 1 Sparse-coded backscatter modulation algorithm (SC-BMA) | |
| 1: | input the number of time slots K and the modulation order M |
| 2: | obtain the symbol mapping from (11) |
| 3: | fordo |
| 4: | initialize |
| 5: | for do |
| 6: | for do |
| 7: | for do |
| 8: | if then |
| 9: | ▹ first non-zero element |
| 10: | else if then |
| 11: | ▹ second non-zero element |
| 12: | else |
| 13: | ▹ zero element |
| 14: | end if |
| 15: | end for |
| 16: | |
| 17: | end for |
| 18: | end for |
| 19: | end for |
| 20: | obtain , ▹ one-way factor graph, codebook |
| 21: | generate , |
| 22: | generate , |
| 23: | output the codebooks and the factor graphs |
| Algorithm 2 Dyadic channel estimation algorithm (D-CEA) | |
| 1: | input the composite forward-backward channels and the ambient source signals |
| 2: | fordo |
| 3: | initialize |
| 4: | for do |
| 5: | solve (20) for the variable |
| 6: | end for |
| 7: | estimate the channel vector |
| 8: | estimate the Toeplitz matrices and from the Equation (3) |
| 9: | for do |
| 10: | estimate the dyadic forward and backward channels and from (26) and (27) |
| 11: | end for |
| 12: | end for |
| 13: | output the dyadic foward channel and the dyadic backward channel |
4. Iterative Detection on Dyadic Channel
- Interference Exploitation: To achieve massive connectivity in AmBC, the interferences (i.e., MAI and ISI) should be exploited in non-orthogonal manners [31,32], instead of excluding them by using orthogonal signaling as in conventional detectors [2,23]. In addition, iterative MPA should be modified for DBC to achieve additional gain without loss of backscatter signal power.
- Low Complexity: The received signals in AP are superposition of multiple backscatter signals with M-ary modulation. In addition, ISI introduces another superposition of backscatter signals with delay spreads in the dyadic channels, further increasing complexity of iterative detector. Hence, the complexity of detector should be as low as possible for practical applications of SC-AmBC.
- There are FNs with degree and FNs with degree .
- There are K VNs with degree and VNs with degree .
5. Simulation Results
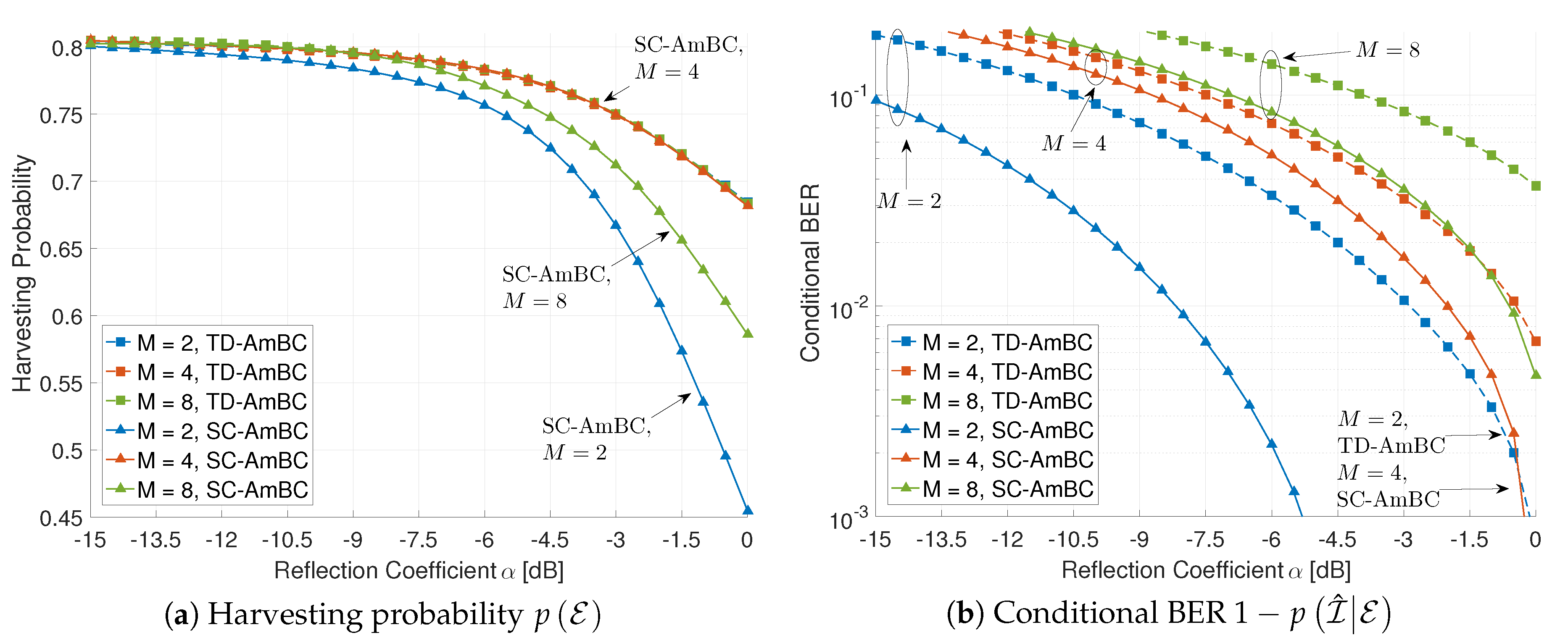
5.1. Applicability to M-Ary Modulation
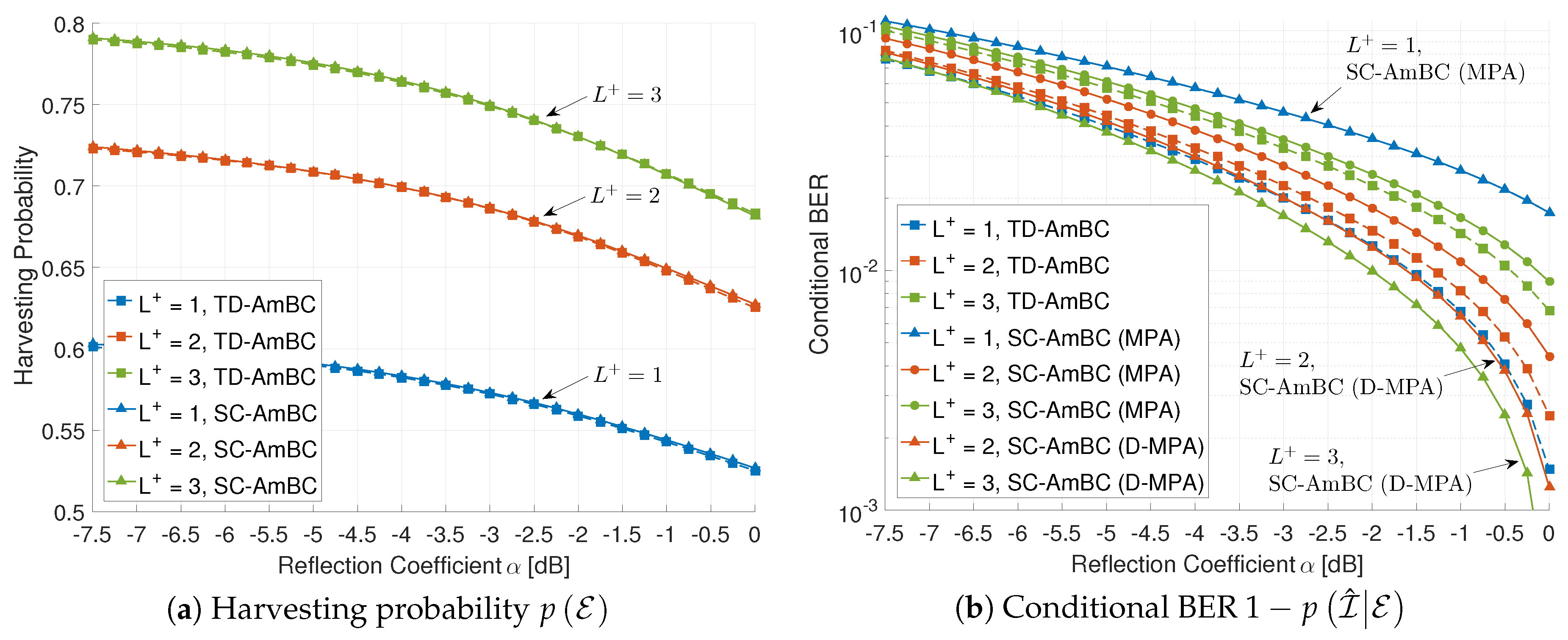
5.2. Applicability to DBC
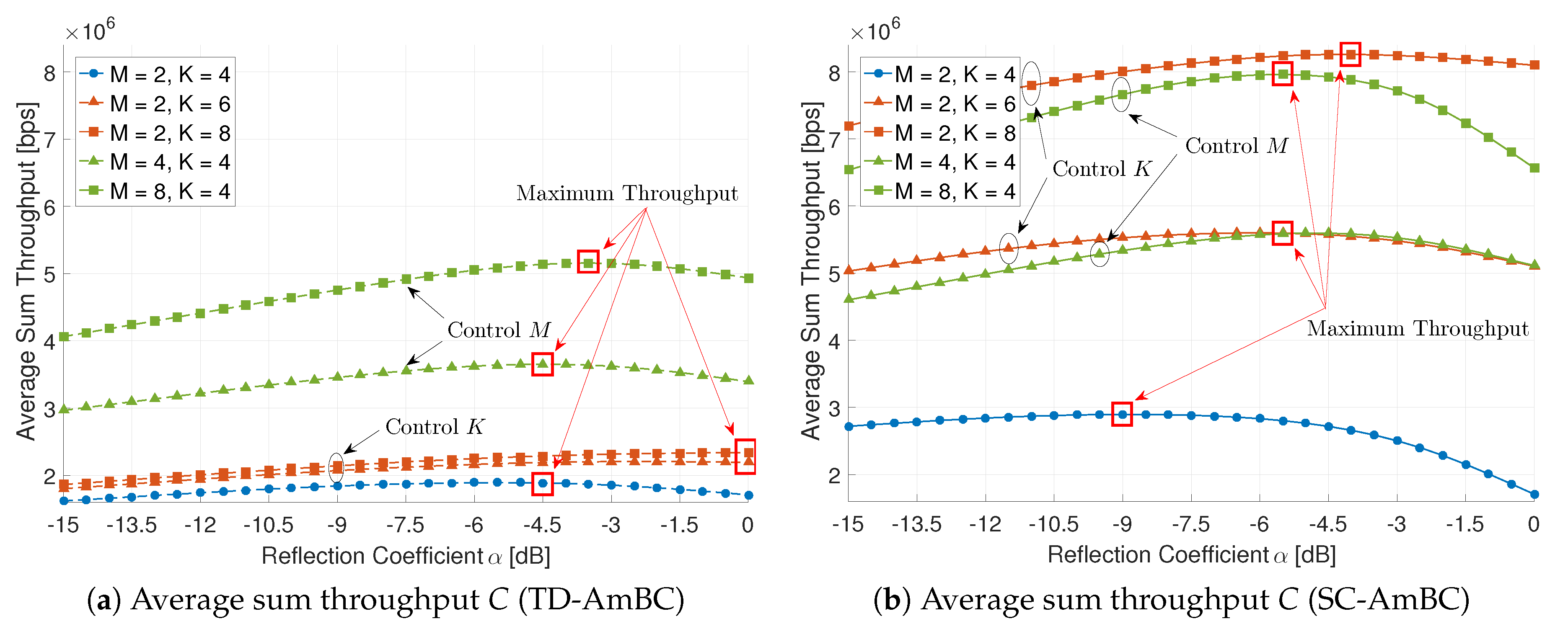
5.3. Applicability to NOMA
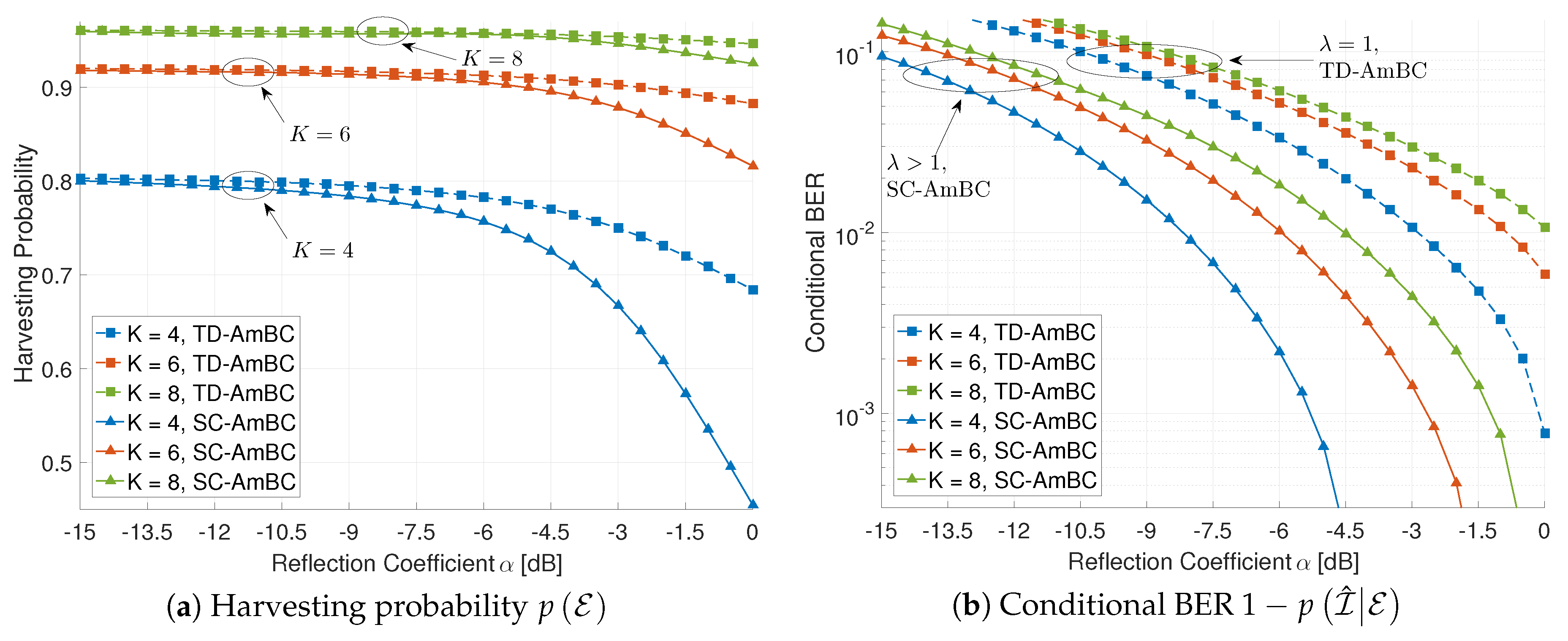
5.4. Applicability to Energy Harvesting
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kellogg, B.; Talla, V.; Smith, J.R.; Gollakota, S. Passive Wi-Fi: Bringing low power to Wi-Fi transmissions. In Proceedings of the 13th Usenix Symposium on Networked Systems Design and Implementation (NSDI’16), Santa Clara, CA, USA, 16–18 March 2016; pp. 151–164. [Google Scholar]
- Bharadia, D.; Joshi, K.R.; Kotaru, M.; Katti, S. BackFi: High throughput WiFi backscatter. In Proceedings of the ACM SIGCOMM’15, London, UK, 17–21 August 2015; pp. 283–296. [Google Scholar]
- Ensworth, J.F.; Reynolds, M.S. Every smart phone is a backscatter reader: Modulated backscatter compatibility with Bluetooth 4.0 low energy (BLE) devices. In Proceedings of the 2015 IEEE International Conference on RFID (IEEE RFID 2015), San Diego, CA, USA, 15–17 April 2015; pp. 78–85. [Google Scholar]
- Ma, Y.; Selby, N.; Adib, F. Drone relays for battery-free networks. In Proceedings of the ACM SIGCOMM’17, Los Angeles, CA, USA, 21–25 August 2017; pp. 335–347. [Google Scholar]
- Liu, V.; Parks, A.; Talla, V.; Gollakota, S.; Wetherall, D.; Smith, J.R. Ambient backscatter: Wireless communication out of thin air. In Proceedings of the ACM SIGCOMM’13, Hong Kong, China, 12–16 August 2013; pp. 39–50. [Google Scholar]
- Kellogg, B.; Parks, A.; Gollakota, S.; Smith, J.R.; Wetherall, D. Wi-Fi backscatter: Internet connectivity for RF-powered devices. In Proceedings of the ACM SIGCOMM’14, Chicago, IL, USA, 17–22 August 2014; pp. 607–618. [Google Scholar]
- Parks, A.N.; Liu, A.; Gollakota, S.; Smith, J.R. Turbocharging ambient backscatter communication. In Proceedings of the ACM SIGCOMM’14, Chicago, IL, USA, 17–22 August 2014; pp. 619–630. [Google Scholar]
- Thomas, S.J.; Reynolds, M.S. A 96 Mbit/sec, 15.5 pJ/bit 16-QAM modulator for UHF backscatter communication. In Proceedings of the 2012 IEEE International Conference on RFID (IEEE RFID 2012), Orlando, FL, USA, 3–5 April 2012; pp. 185–190. [Google Scholar]
- Thomas, S.J.; Wheeler, E.; Teizer, J.; Reynolds, M.S. Quadrature amplitude modulated backscatter in passive and semipassive UHF RFID systems. IEEE Trans. Microw. Theory Technol. 2012, 60, 1175–1182. [Google Scholar] [CrossRef]
- Krikidis, I. Retrodirective large antenna energy beamforming in backscatter multi-user networks. IEEE Wirel. Commun. Lett. 2018, 1–4. [Google Scholar] [CrossRef]
- Gong, S.; Huang, X.; Xu, J.; Liu, W.; Wang, P.; Niyato, D. Backscatter relay communications powered by wireless energy beamforming. IEEE Trans. Commun. 2018. [Google Scholar] [CrossRef]
- Boyer, C.; Roy, S. Space time coding for backscatter RFID. IEEE Trans. Wirel. Commun. 2013, 12, 2272–2280. [Google Scholar] [CrossRef]
- He, C.; Wang, Z.J.; Miao, C.; Leung, V.C.M. Block-level unitary query: Enabling orthogonal-link space-time code with query diversity for MIMO backscatter RFID. IEEE Trans. Wirel. Commun. 2016, 15, 1937–1949. [Google Scholar] [CrossRef]
- Talla, V.; Hessar, M.; Kellogg, B.; Najafi, A.; Smith, J.R.; Gollakota, S. LoRa backscatter: Enabling the vision of ubiquitous connectivity. Proc. ACM Interact. Mob. Wearable Ubiquitous Technol. 2017, 1, 105. [Google Scholar] [CrossRef]
- Wang, J.; Hassanieh, H.; Katabi, D.; Indyk, P. Efficient and reliable low-power backscatter networks. In Proceedings of the ACM SIGCOMM’12, Helsinki, Finland, 13–17 August 2012; pp. 61–72. [Google Scholar]
- Zhu, G.; Ko, S.-W.; Huang, K. Inference from randomized transmissions by many backscatter sensors. IEEE Trans. Wirel. Commun. 2018, 17, 3111–3127. [Google Scholar] [CrossRef]
- Liu, W.; Huang, K.; Zhou, X.; Durrani, S. Full-duplex backscatter interference networks based on time-hopping spread spectrum. IEEE Trans. Wirel. Commun. 2017, 16, 4361–4377. [Google Scholar] [CrossRef]
- Griffin, J.D.; Durgin, G.D. Link envelope correlation in the backscatter channel. IEEE Commun. Lett. 2007, 11, 735–737. [Google Scholar] [CrossRef]
- Griffin, J.D.; Durgin, G.D. Gains for RF tags using multiple antennas. IEEE Trans. Antennas Propag. 2008, 56, 563–570. [Google Scholar] [CrossRef]
- Liu, H.-C.; Lin, W.-C.; Lin, M.-Y.; Hsu, M.-H. Passive UHF RFID tag with backscatter diversity. IEEE Antennas Wirel. Propag. Lett. 2011, 10, 415–418. [Google Scholar]
- He, C.; Chen, X.; Wang, Z.J.; Su, W. On the performance of MIMO RFID backscattering channels. EURASIP J. Wirel. Commun. Netw. 2012, 11, 1–15. [Google Scholar] [CrossRef]
- Goldsmith, A. Wireless Communications; Cambridge University Press: New York, NY, USA, 2005. [Google Scholar]
- Darsena, D.; Gelli, G.; Verde, F. Modeling and performance analysis of wireless networks with ambient backscatter devices. IEEE Trans. Commun. 2017, 65, 1797–1814. [Google Scholar] [CrossRef]
- Yang, G.; Zhang, Q.; Liang, Y.-C. Cooperative ambient backscatter communications for green internet-of-things. IEEE IoT J. 2018, 5, 1116–1130. [Google Scholar] [CrossRef]
- Yang, G.; Liang, Y.-C.; Zhang, R.; Pei, Y. Modulation in the air: Backscatter communication over ambient OFDM carrier. IEEE Trans. Commun. 2018, 66, 1219–1233. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, G.; Dou, Z.; Zhong, Z. Coding and detection schemes for ambient backscatter communication systems. IEEE Access 2017, 5, 4947–4953. [Google Scholar] [CrossRef]
- Lu, X.; Niyato, D.; Jiang, H.; Kim, D.I.; Xiao, Y.; Han, Z. Ambient backscatter assisted wireless powered communications. IEEE Wirel. Commun. 2018, 35, 170–177. [Google Scholar] [CrossRef]
- Dai, L.; Wang, B.; Yuan, Y.; Han, S.; Chih-Lin, I.; Wang, Z. Non-orthogonal multiple access for 5G: Solutions, challenges, opportunities, and future research trends. IEEE Commun. Mag. 2015, 53, 74–81. [Google Scholar] [CrossRef]
- Cai, Y.; Qin, Z.; Cui, F.; Li, G.Y.; McCann, J.A. Modulation and multiple access for 5G networks. IEEE Commun. Surv. Tutor. 2018, 20, 629–646. [Google Scholar] [CrossRef]
- Liu, Y.; Ding, Z.; Elkashlan, M.; Poor, H.V. Cooperative non-orthogonal multiple access with simultaneous wireless information and power transfer. IEEE J. Sel. Areas Commun. 2016, 34, 938–953. [Google Scholar] [CrossRef]
- Nissel, R.; Schwarz, S.; Rupp, M. Filter bank multicarrier modulation schemes for future mobile communications. IEEE J. Sel. Areas Commun. 2017, 35, 1768–1782. [Google Scholar] [CrossRef]
- Nikopour, H.; Baligh, H. Sparse code multiple access. In Proceedings of the 2013 IEEE 24th International Symposium on Personal Indoor and Mobile Radio Communications (PIMRC Workshops), London, UK, 8–9 September 2013; pp. 332–336. [Google Scholar]
- Taherzadeh, M.; Nikopour, H.; Bayesteh, A.; Baligh, H. SCMA codebook design. In Proceedings of the 2014 IEEE 80th Vehicular Technology Conference (VTC Fall), Vancouver, BC, Canada, 14–17 September 2014. [Google Scholar]
- Au, K.; Zhang, L.; Nikopour, H.; Yi, E.; Bayesteh, A.; Vilaipornsawai, U.; Ma, J.; Zhu, P. Uplink contention based SCMA for 5G radio access. In Proceedings of the 2014 Globecom Workshops (GC Wkshps), Austin, TX, USA, 8–12 December 2014; pp. 900–905. [Google Scholar]
- Wu, Y.; Zhang, S.; Chen, Y. Iterative multiuser receiver in sparse code multiple access systems. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 2918–2923. [Google Scholar]
- Bayesteh, A.; Nikopour, H.; Taherzadeh, M.; Baligh, H.; Ma, J. Low complexity techniques for SCMA detection. In Proceedings of the 2015 Globecom Workshops (GC Wkshps), San Diego, CA, USA, 6–10 December 2015. [Google Scholar]
- Han, K.; Huang, K. Wirelessly powered backscatter communication networks: Modeling, coverage and capacity. IEEE Trans. Wirel. Commun. 2017, 16, 2548–2561. [Google Scholar] [CrossRef]
- Boyer, C.; Roy, S. Coded QAM backscatter modulation for RFID. IEEE Trans. Commun. 2012, 60, 1925–1934. [Google Scholar] [CrossRef]
- Zhou, Y.; Yu, Q.; Meng, W.; Li, C. SCMA codebook design based on constellation rotation. In Proceedings of the 2017 IEEE International Conference on Communications (ICC), Paris, France, 21–25 May 2017. [Google Scholar]
- Talla, V.; Smith, J.R. Hybrid analog-digital backscatter: A new approach for battery-free sensing. In Proceedings of the 2013 IEEE International Conference on RFID (IEEE RFID 2013), Penang, Malaysia, 30 April–2 May 2013; pp. 74–81. [Google Scholar]
- Bharadia, D.; McMilin, E.; Katti, S. Full duplex radios. In Proceedings of the ACM SIGCOMM’13, Hong Kong, China, 12–16 August 2013; pp. 375–386. [Google Scholar]
- Peng, J.; Chen, W.; Bai, B.; Guo, X.; Sun, C. Joint optimization of constellation with mapping matrix for SCMA codebook design. IEEE Signal Process. Lett. 2017, 24, 264–268. [Google Scholar] [CrossRef]
- Robertson, P.; Villebrun, E.; Hoeher, P. A comparison of optimal and sub-optimal MAP decoding algorithms operating in the log domain. In Proceedings of the 1995 IEEE International Conference on Communications (ICC), Seattle, WA, USA, 18–22 June 1995; pp. 1009–1013. [Google Scholar]
- Hoshyar, R.; Wathan, F.P.; Tafazolli, R. Novel low-density signature for synchronous CDMA systems over AWGN channel. IEEE Trans. Signal Process. 2008, 56, 1616–1626. [Google Scholar] [CrossRef] [Green Version]
- Sabharwal, A.; Schniter, P.; Guo, D.; Bliss, D.W.; Rangarajan, S.; Wichman, R. In-band full-duplex wireless: Challenges and opportunities. IEEE J. Sel. Areas Commun. 2014, 32, 1637–1652. [Google Scholar] [CrossRef]
- Zhang, Z.; Chai, X.; Long, K.; Vasilakos, A.V.; Hanzo, L. Full duplex techniques for 5G networks: Self-interference cancellation, protocol design, and relay selection. IEEE Commun. Mag. 2015, 53, 128–137. [Google Scholar] [CrossRef]
- Donoho, D.L. Compressed sensing. IEEE Trans. Inf. Theory 2006, 52, 1289–1306. [Google Scholar] [CrossRef]
- Wang, G.; Gao, F.; Fan, R.; Tellambura, C. Ambient backscatter communication systems: Detection and performance analysis. IEEE Trans. Commun. 2016, 64, 4836–4846. [Google Scholar] [CrossRef]
- Qian, J.; Gao, F.; Wang, G.; Jin, S.; Zhu, H. Noncoherent detections for ambient backscatter system. IEEE Trans. Wirel. Commun. 2017, 16, 1412–1422. [Google Scholar] [CrossRef]
- Wang, Z.; Giannakis, G.B. Wireless multicarrier communications—Where Fourier meets Shannon. IEEE Signal Process. Mag. 2000, 17, 29–48. [Google Scholar] [CrossRef]
- Kim, Y.-H.; Ahn, H.-S.; Yoon, C.; Lim, Y.; Lim, S.-O. An ambient RF energy harvesting and backscatter modulating tag system enabling zero-power wireless data communication. In Proceedings of the Seventh International Conference on the Internet of Things (IoT ’17), Linz, Austria, 22–25 October 2017. [Google Scholar]
- Besnoff, J.; Abbasi, M.; Ricketts, D.S. High data-rate communication in near-field RFID and wireless power using higher order modulation. IEEE Trans. Microw. Theory Technol. 2016, 64, 401–413. [Google Scholar] [CrossRef]
- Jordao, M.; Correia, R.; Carvalho, N.B. High order modulation backscatter systems characterization. In Proceedings of the 2018 IEEE Topical Conference on Wireless Sensors and Sensor Networks (WiSNet), Anaheim, CA, USA, 14–17 January 2018; pp. 44–46. [Google Scholar]
- Boutros, J.; Viterbo, E. Signal space diversity: A power- and bandwidth-efficient diversity technique for the Rayleigh fading channel. IEEE Trans. Inf. Theory 1998, 44, 1453–1467. [Google Scholar] [CrossRef]
- Choi, J.W.; Shim, B.; Ding, Y.; Rao, B.; Kim, D.I. Compressed sensing for wireless communiciations: Useful tips and tricks. IEEE Surv. Tutor. 2017, 19, 1527–1550. [Google Scholar] [CrossRef]
- Yang, G.; Ho, C.K.; Zhang, R.; Guan, Y.L. Throughput optimization for massive MIMO systems powered by wireless energy transfer. IEEE J. Sel. Areas Commun. 2015, 33, 1640–1650. [Google Scholar] [CrossRef]
- ISO/IEC Standard for Information Technology—Telecommunications and Information Exchange between Systems—Local and Metropolitan Area Networks—Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications; ISO/IEC 8802-11 IEEE Std 802.11 Second edition 2005-08-01 ISO/IEC 8802 11:2005(E) IEEE Std 802.11i-2003 Edition; IEEE: Piscataway, NJ, USA, 2005; pp. 1–721.





| M | Projected Information from VN n to FN | |
|---|---|---|
| 4 | 1 | |
| 2 | ||
| 8 | 1 | |
| 2 | ||
| Expanded Information from FN to VN | ||
| 4 | 1 | |
| 2 | ||
| 8 | 1 | |
| 2 | ||
| TD-AmBC [2,23] | SC-AmBC | ||
|---|---|---|---|
| Modulation | Load impedances | M | 2 |
| Constellation dimension | 2 | ||
| Constellation symbols | M | ||
| Detection | ISI exploitation | no | yes |
| MAI exploitation | no | yes | |
| Complexity | low | medium | |
| BER | high | low | |
| Networking | Max. sum throughput | ||
| Max. connectivity | K | ||
| Duty cycle | |||
| Latency | high | low | |
| Multiple access | orthogonal | non-orthogonal |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kim, T.Y.; Kim, D.I. Novel Sparse-Coded Ambient Backscatter Communication for Massive IoT Connectivity. Energies 2018, 11, 1780. https://doi.org/10.3390/en11071780
Kim TY, Kim DI. Novel Sparse-Coded Ambient Backscatter Communication for Massive IoT Connectivity. Energies. 2018; 11(7):1780. https://doi.org/10.3390/en11071780
Chicago/Turabian StyleKim, Tae Yeong, and Dong In Kim. 2018. "Novel Sparse-Coded Ambient Backscatter Communication for Massive IoT Connectivity" Energies 11, no. 7: 1780. https://doi.org/10.3390/en11071780





