2.1. Household Nanogrid
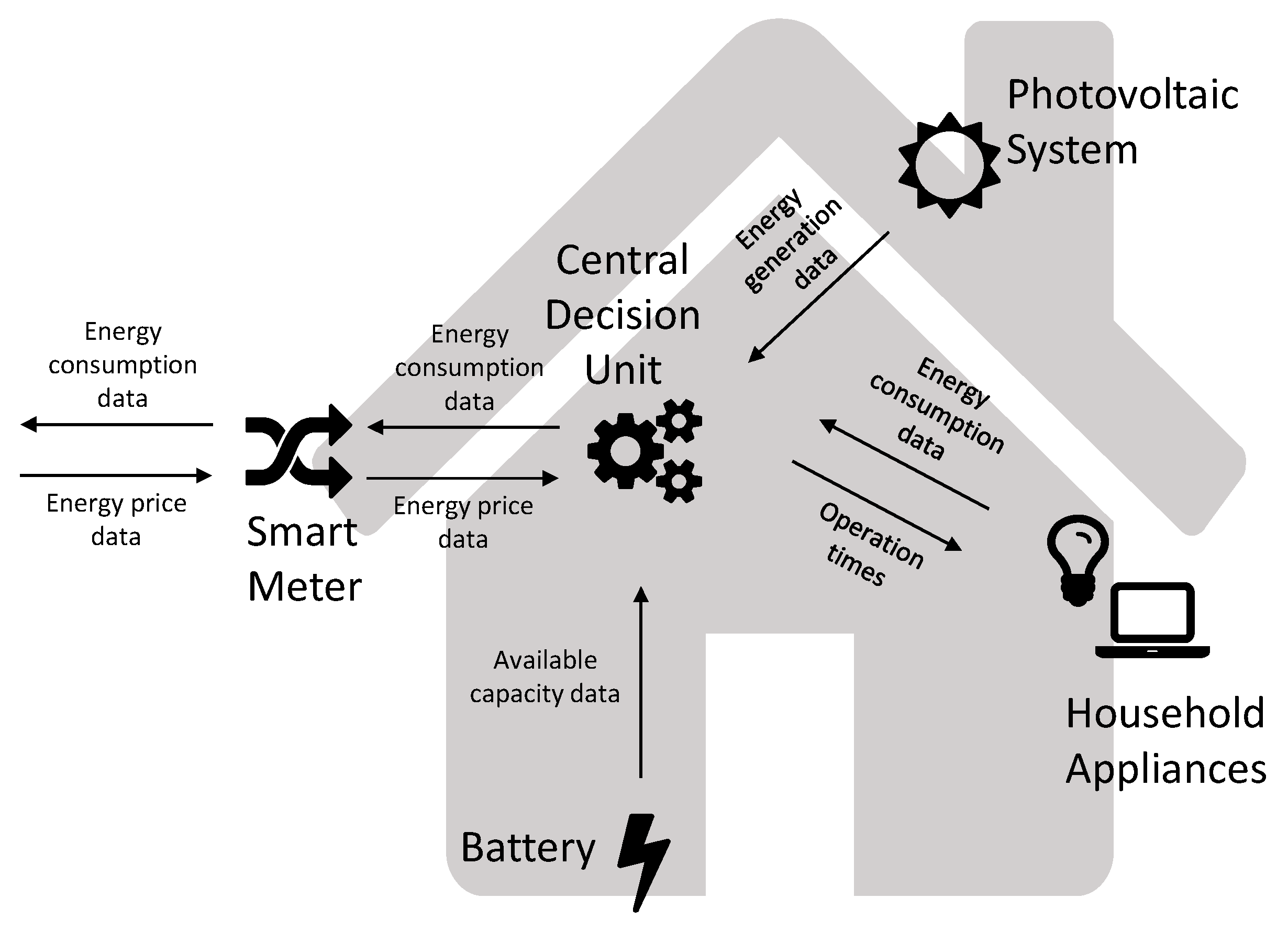
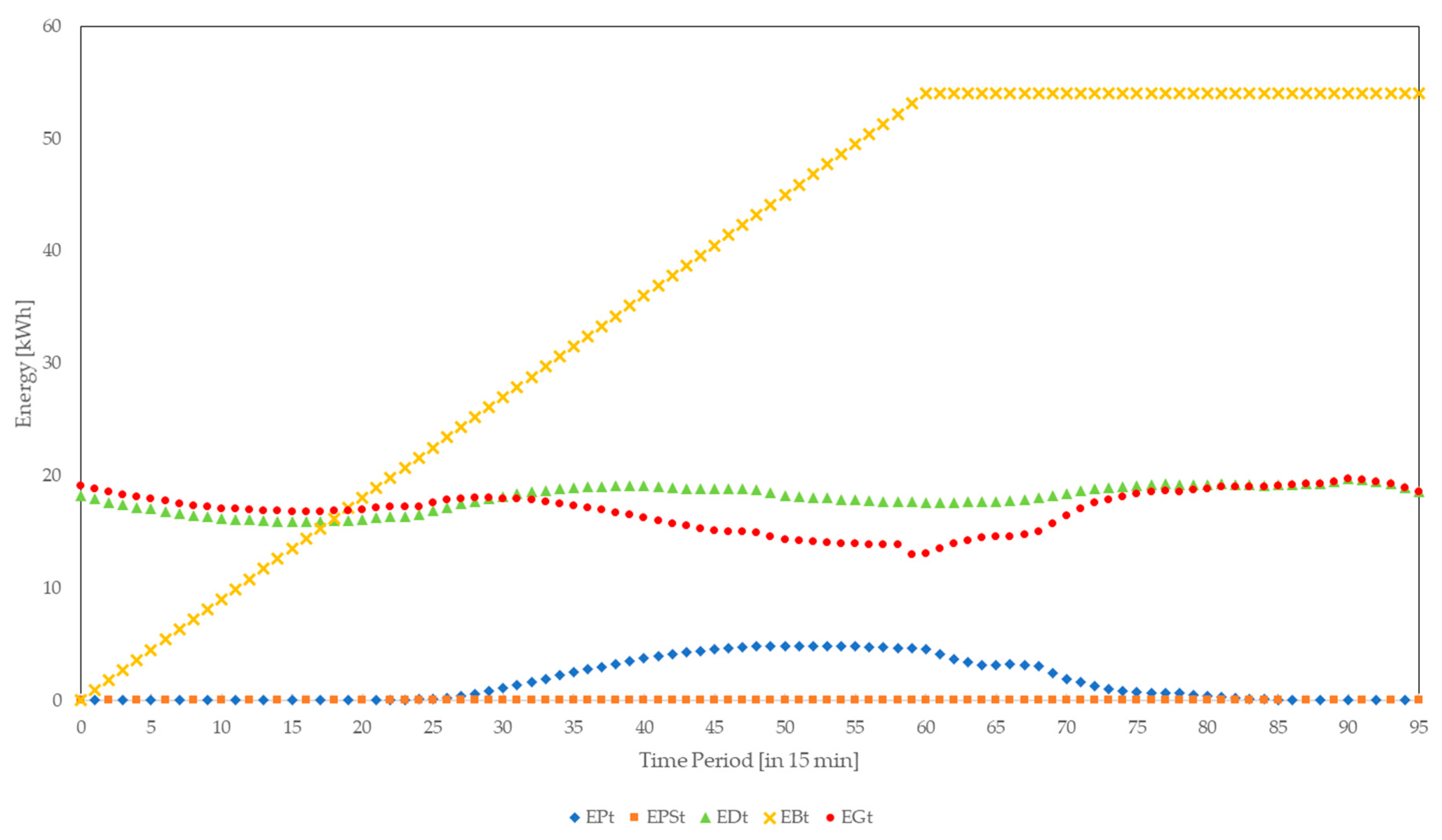
The model of household nanogrid consists of different components as can be seen in
Figure 2. Each component of the household nanogrid will be described and explained in detail in the following sections. The household nanogrid consists of household appliances, to model the energy demand of the household, a photovoltaic system, to model energy generation by the household itself, and a battery, to model energy storage. Furthermore, the household requires a central decision unit, which determines the usage of photovoltaic energy, the satisfaction of energy demand by household appliances, and the utilization of energy stored in the battery. Therefore, presents the “smart” feature of the household nanogrid. Between the central decision unit and the photovoltaic system, the battery, and the household appliances, communication of certain data is realized. Furthermore, the central decision unit transmits certain data to the SM, as well as receives other data from it. The SM represents the communication interface between the household nanogrid and the distribution grid, and provides the distribution grid with an opportunity to cut the energy supply to the household nanogrid. Finally, the functions of the distribution grid that are essential to the model need to be simulated as well. Therefore, grid energy price data, as well as the information, whether the energy supply to the household nanogrid is to be cut, need to be provided by the simulation of relevant distribution grid functionalities.
Following, the mathematical model describing the central decision unit’s decision making is explained. The objective function of the central decision unit ensures the minimization of cost to the household.
Furthermore, a constraint has to make sure that the household energy demand
and the energy used to charge the battery
equal the sum of grid energy demand
, photovoltaic generated energy
, and energy discharged from the battery
for every time period
t.
Moreover, it has to be ensured that the battery is only charged or discharged in one time period. With
and
being binary variables, which can only take the values of either 0 or 1.
Furthermore, it has to be ensured that the battery is not discharged further than the maximum capacity
of the battery.
Also, the different energy values cannot get lower than zero in each time period
t.
The cost to charge the battery
has to be lower than the defined cost limit to charge the battery
.
Also, the amount of photovoltaic energy sold to the grid
cannot exceed the amount of photovoltaic energy that is generated in each time period
t .
In order to solve the problem that is presented by covering the household’s energy demand , an algorithm is developed, which assigns the different energy sources to the energy demand under the aforementioned restrictions. The different variables, like battery capacity , maximum charging rate of the battery , and cost limit to charge the battery , are set beforehand, and are provided to the central decision unit by the different objects that are created to represent the different parts of the household nanogrid. The central decision unit utilizes these variables, as well as input data, to solve the linear program to minimize the household’s energy cost by following the different restrictions.
The central decision unit is the center piece of the household nanogrid model, it has the purpose of controlling the behavior of all household components, as well as obtaining information from, and communicate data to, the smart meter and the different household components. To fulfill these tasks, the central decision unit utilizes an algorithm to determine the different variables.
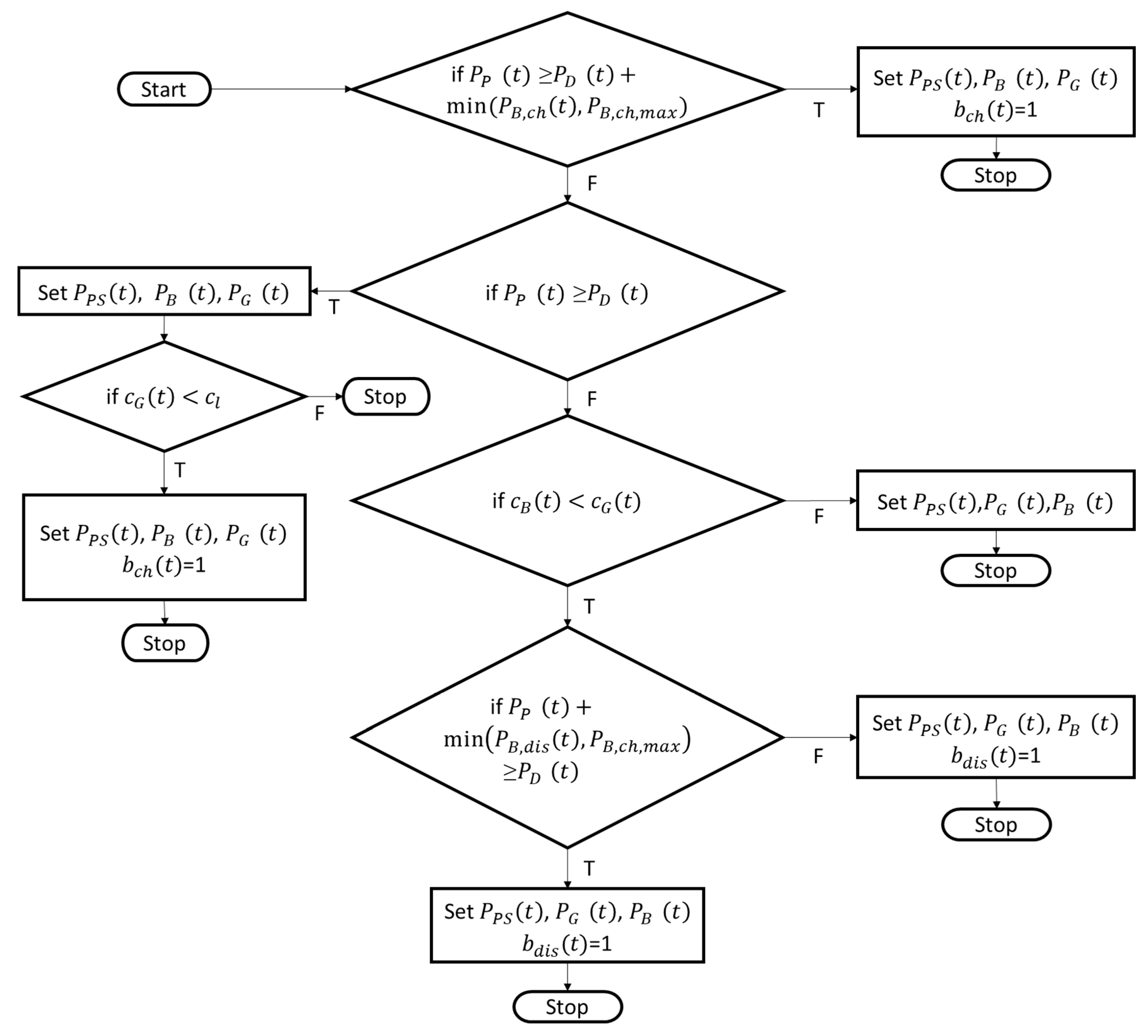
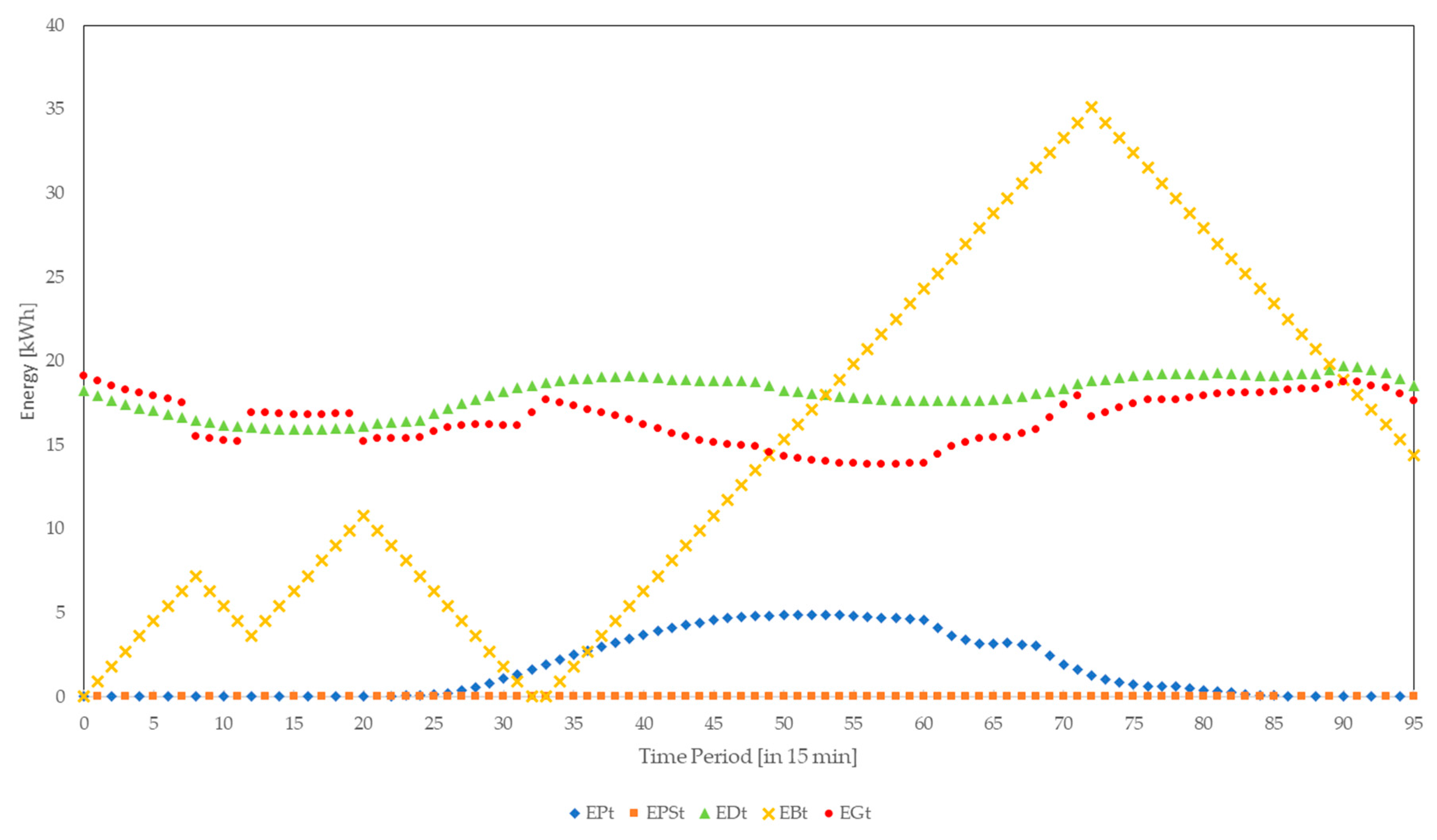
The first part of the algorithm is shown in
Figure 3. The algorithm will assign the energy sources associated with least cost for the household nanogrid to be utilized to meet the household nanogrid’s energy demand first. If there is a surplus of free photovoltaic generated energy
, then the battery will be charged accordingly. The algorithm determines how much photovoltaic generated energy
will be sold back to the distribution grid, to what extent the battery is charged
, and how much energy needs to be bought from the distribution grid
in each time period.
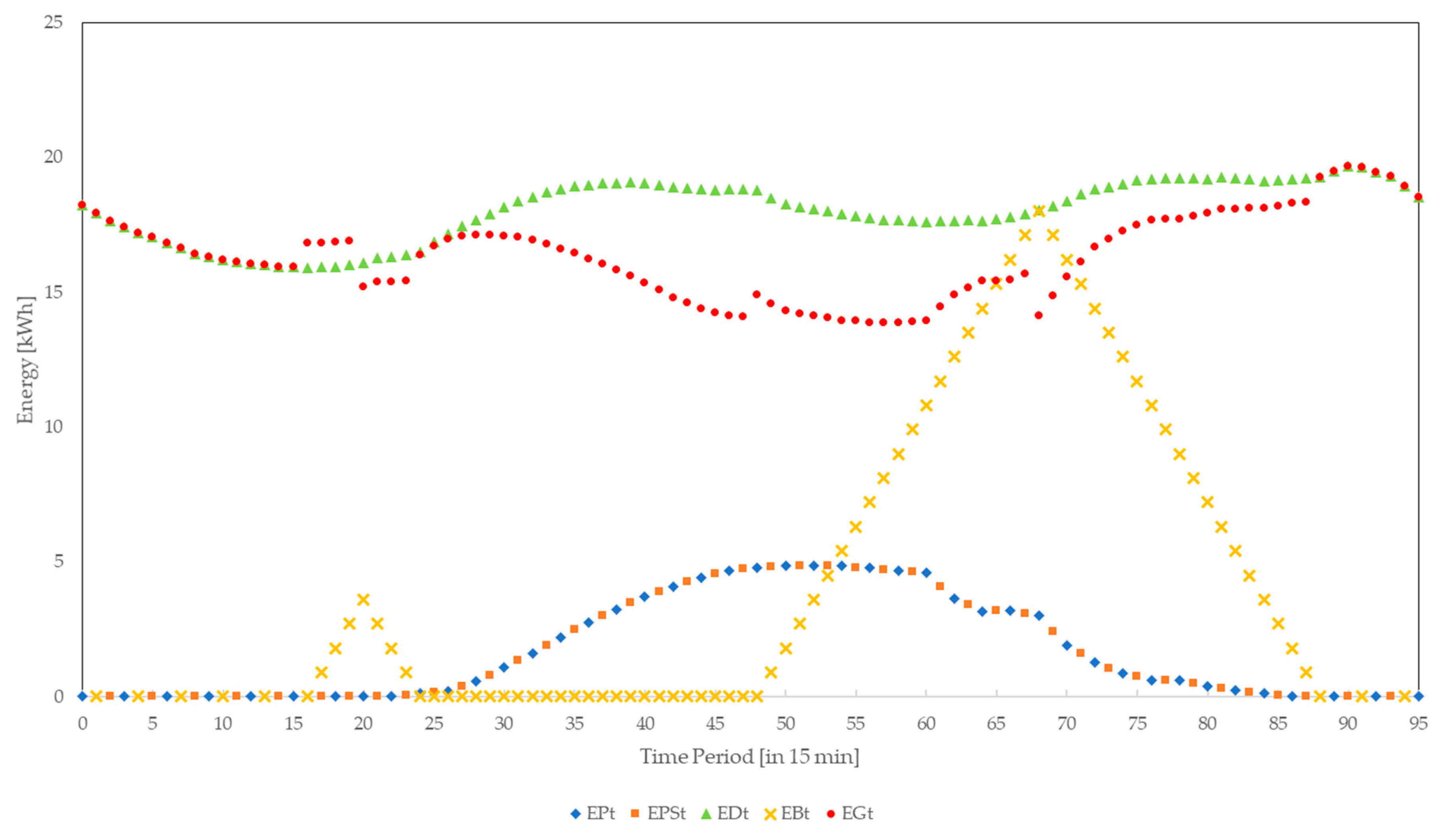
Figure 4 shows the algorithms step of making sure the battery is charged when possible independently of ensuring the coverage of household nanogrid energy demand. Apart from charging the battery when there is a surplus of free photovoltaic generated energy
, it is also charged when grid energy’s price
is lower than the set price limit for battery charging
.
Apart from the central decision unit, there are other household nanogrid components, which will be described in the following paragraphs.
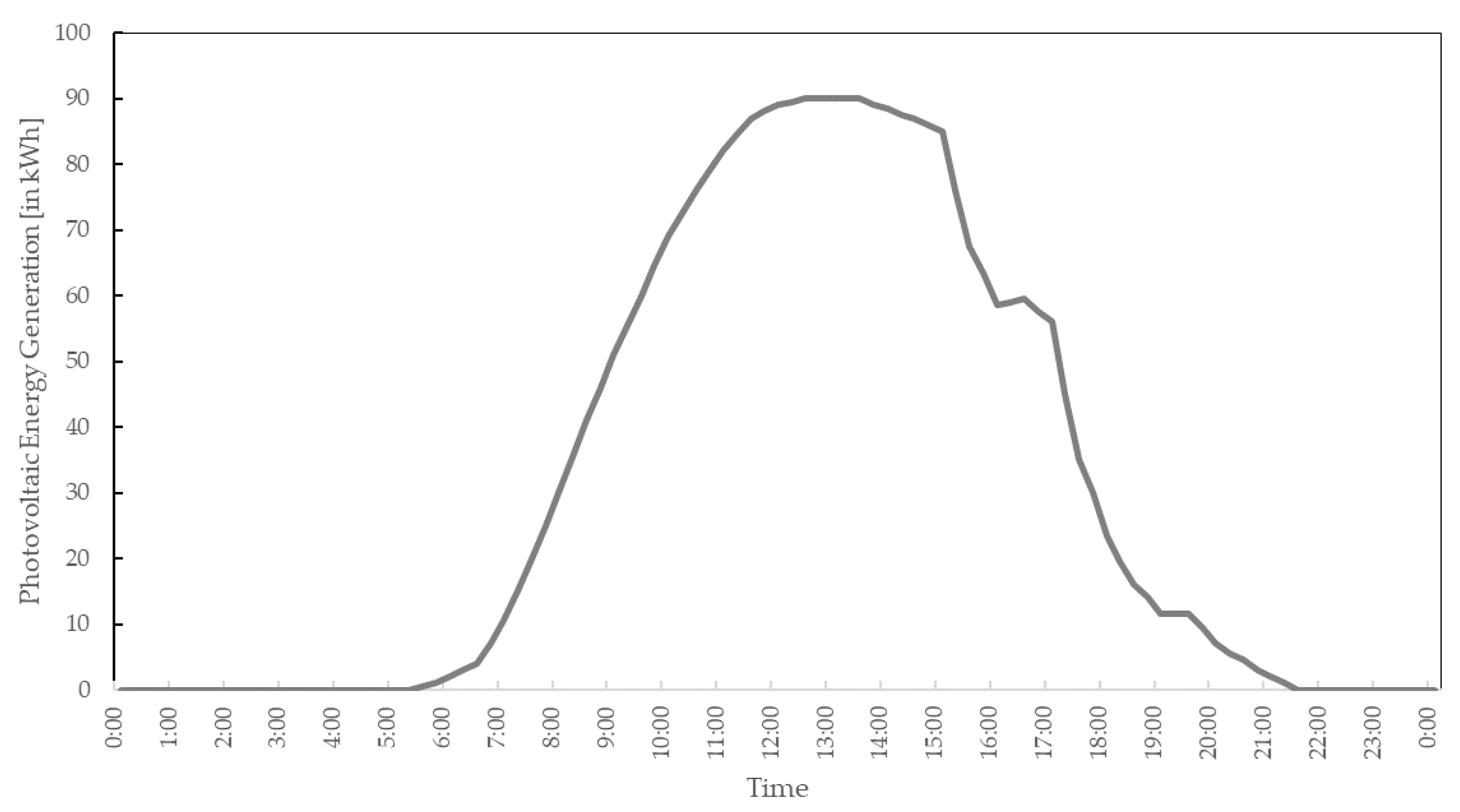
The photovoltaic energy generation was modeled by utilizing the empirically obtained energy generation data from a photovoltaic systems producer. The curve concerning photovoltaic energy generation
, as shown in
Figure 5, was utilizing the data obtained by 200 kW solar panels on a particularly sunny summer day in Sheffield, UK, in an experiment by the company Powerstar [
18].
The battery has different attributes, with which it is possible to control the utilization of the battery, mainly the charging and discharging processes. To have full control of the battery, setting the maximum storage capacity of the battery , setting the currently stored amount of energy , as well as setting the maximum charging rate , is essential. Also, the battery can be set to a busy state, so it cannot be employed for other actions, while it is being used.
The battery provides functions for all of the parameters to be set and read. The currently stored energy in the battery is a crucial measure to control important decisions that the central decision unit has to make.
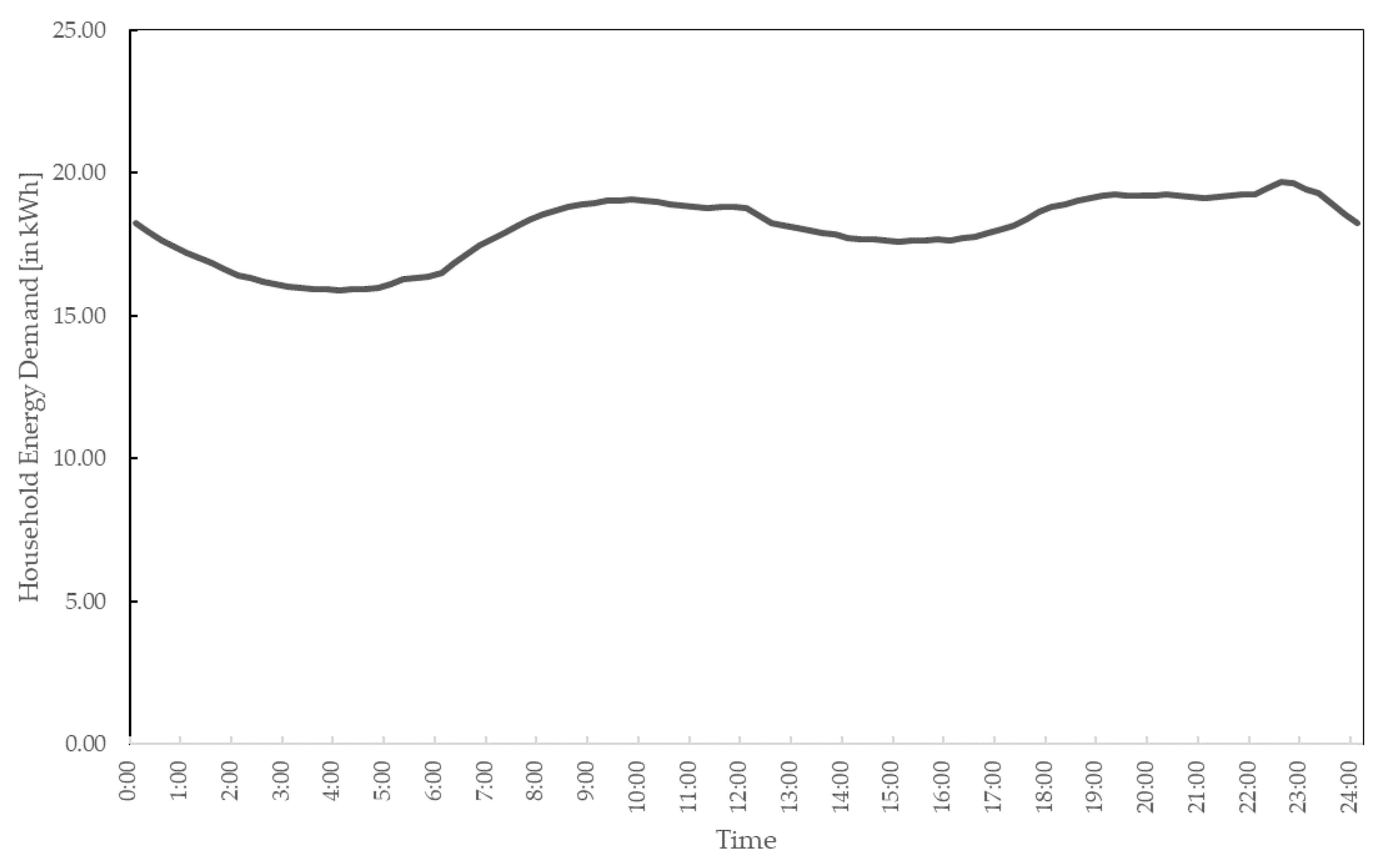
The curve for the energy demand, as shown in
Figure 6, was taken from the data provided by the ELIA grid for Belgian consumers [
19]. The household’s energy demand
is provided to the central decision unit as a set of data, including a function in the object of energy demand
, which allows the central decision unit to receive the value of household energy demand
for one specific time period.
The smart meter is designed as the connection between the grid and the household. It has two main functions, namely, the transmission of different data between grid and the household, and secondly, to provide the grid with the possibility of cutting off the energy supply to the household. Also, it is the task of the smart meter to transmit the grid energy price from the grid to the household. While the grid energy demand and the amount of photovoltaic energy to be sold back to the grid have to be transmitted from the household to the grid.
In our model, the only information from the grid that is essential for the household nanogrid simulation is the grid energy price, as well as the information, whether grid energy is provided. Therefore, the distribution grid energy price is transmitted by the SM to the household nanogrid along with the information, whether the distribution grid will supply the household nanogrid with energy.
2.2. Cyber-Attacks
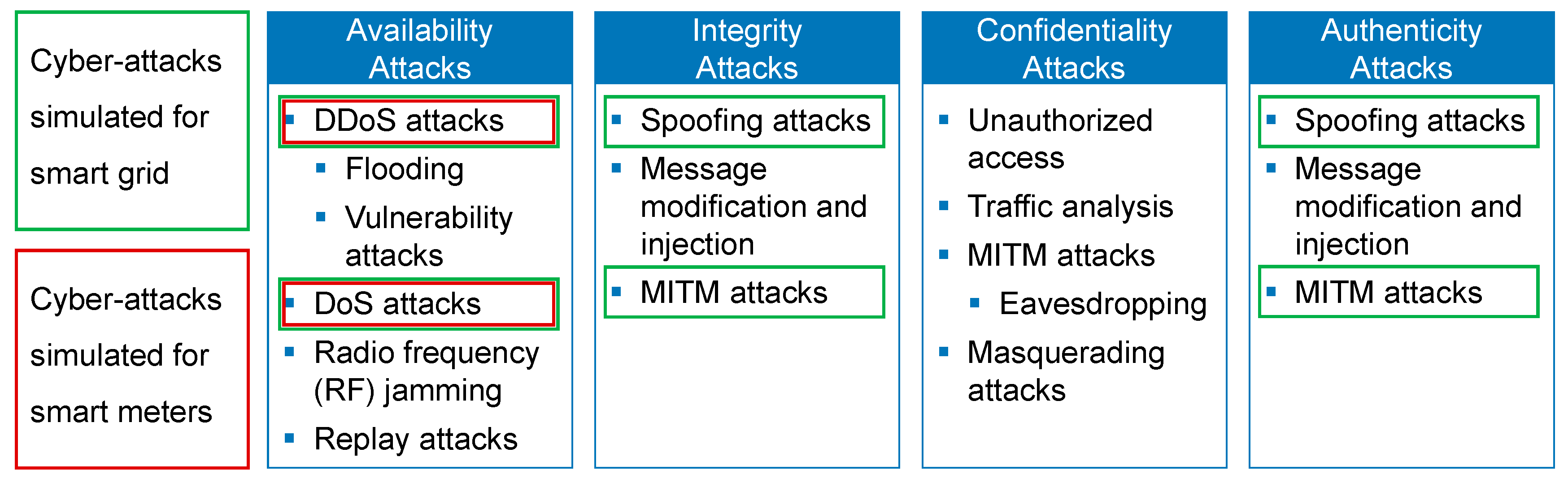
Cyber-attacks were injected into the household nanogrid model in order to simulate and evaluate the impact of different attacks. The first category of cyber-attacks that were injected is availability attacks. Availability attacks aim at compromising, or even blocking, the network’s communication [
9]. In order to simulate availability attacks on the household nanogrid model, an individual approach for each kind of availability attack was defined in a way, in which it could be applied to the household nanogrid model. The different simulation approaches for availability attacks are shown in
Table 3, and are described in the following paragraphs.
Different types of DoS/DDoS attacks, which have different effects on a network, exist [
3,
5]. Since DoS/DDoS attacks seek to compromise the network’s availability by attacking the network with requests, three different scenarios are simulated. The first scenario simulates a DoS attack, and therefore shows no measurable delay ∆
t = 0 because a single DoS attack, as found during literature survey, does not delay the system. To simulate the impact of DDoS attacks, small ∆
t > 0 and big ∆
t >> 0 time delays were modelled.
The second type of availability attacks, RF jamming is an availability attack, which is characterized by interruption of the network’s communication by interference utilizing radio signals for an undefined period of time [
8]. Therefore, the simulation of RF jamming aims at the interruption of data transmission for different lengths of time. First, no grid energy price data will be provided to the central decision unit for one time period
. Second, no grid energy price data will be provided for multiple periods
.
Thirdly, replay attacks can either aim at delaying or repeating data transmission within the network [
3]. For this reason, two simulations are conducted to assess replay attacks. One simulation aims at delaying grid price energy data transmission
. While the other simulation aims at repeating it
.
The second category of cyber-attacks are integrity attacks. Because Integrity describes the network’s protection against unauthorized changes to communication [
9], integrity attacks aim at interfering with the network’s communication by different access points. Since different types of integrity attacks only vary in the means that are used to alter data transmitted via the network, but the modification of data is likely to be the same, one simulation approach is sufficient to assess the effects of all integrity attacks.
But, in the simulation model, there are different types of data transmitted. Therefore, the effects of integrity attacks can be analyzed depending on the data type that is targeted by the attack. Simulations were defined for altered grid energy price, household energy demand, and photovoltaic energy that is being sold back to the grid, as is shown in
Table 4. For the definition of the attack simulation a consumer was assumed as the attacker. Therefore, all of the alterations made by cyber-attacks benefit a consumer. A first simulation approach concerns the grid energy price data, that is set to half
. Second, the grid energy demand transmitted to the distribution grid is set to half
. Third, the data of photovoltaic energy sold back to the grid is set to the amount of photovoltaic generated energy
.
The third category of cyber-attacks compromises the confidentiality of a network. This implies that confidentiality attacks aim at obtaining unauthorized access to sensitive information [
9]. Unauthorized access can enable the attacker to alter some data transmitted via the network. Alteration of data depends on the identity and objective of the attacker. Assuming that a consumer as the attacker three different options to gain benefits by altering data exist. First, the consumer could decrease the grid energy price transmitted to the SM
. In order to obtain more information about the effects of grid energy price manipulation, a grid price of
was investigated. Second, the amount of photovoltaic generated energy sold back to the grid could be increased
. Third, the household’s energy demand could be decreased
. These different mathematical modelling approaches are shown in
Table 5.
Apart from unauthorized access, there are other confidentiality attacks, which are traffic analysis, man-in-the-middle (MITM) attacks, and masquerading attacks. However, they solely aim at obtaining data from the grid, not altering it. Therefore, these attacks do not have an impact on the results of the simulation model.
The fourth category of cyber-attacks are authenticity attacks. Authenticity defines the network’s ability to verify the genuineness of messages [
9]. Even though authenticity is defined differently to integrity, the cyber-attacks in both categories are the same. Simulating the cyber-attacks for the authenticity category would not add additional value to the study.