1. Introduction
The smart grid is a new concept of the next-generation electric power system that has emerged to address challenges of the existing power grid. The smart grid is a modern electric power grid infrastructure for enhanced efficiency, reliability and safety, with smooth integration of renewable and alternative energy sources, through automated control and modern communications technologies [
1]. Communication architecture of smart grid including requirements, topologies, and protocol stack is required for smart grid environments [
2]. Smart grids provide more electricity to meet rising demand, increase reliability and quality of power supplies, increase energy efficiency, be able to integrate low carbon energy sources into power networks [
3]. To realize the smart grid technology, legacy substations are retrofitted by substation automation systems (SASs), allowing the robust control and communication tasks [
4]. The SAS system is used to control, supervise, and protect substations that are strategic nodes in power networks, which consist of large numbers of switchgears and measuring devices [
5]. Functions of an SAS are control and supervision, as well as protection and monitoring of the primary equipment and of the grid. The functions can be assigned to three levels: the station level, the bay level, and the process level. Devices of an SAS may be physically installed on different functional levels [
5]. The substation should continue to be operable if any SAS communications component fails [
6]. Communication networks in the SAS are defined by the International Electrotechnical Commission (IEC)’s IEC 61850 standard [
5,
6]. To ensure the operations of substations, seamless communication with fault-tolerance can be provided for SASs by using redundancy protocols. In most redundancy protocols, the communication is recovered from a fault in the network; this recovery takes some time, and even a short time period could be unacceptable for certain time-critical applications, including SAS [
7]. To help with this problem, the IEC developed and standardized two protocols that provide seamless communication with fault tolerant capability, including the parallel redundancy protocol (PRP) and high-availability seamless redundancy (HSR) [
8]. Both these protocols implement redundancy in the nodes and provide seamless communication based on the duplication of frames sent over redundant paths from a source to a destination. Unlike the PRP that uses two identical local area network (LAN) of similar topology, the HSR is applied to a single LAN to provide seamless redundancy for the network. With respect to PRP, HSR allows to roughly halve the network infrastructure [
8]. HSR is one of the redundancy protocols selected to provide seamless communication for SASs. HSR is mainly used ring topologies, including single-ring and connected-ring networks. In HSR, a node has two ports operated in parallel, called a doubly-attached node with HSR protocol (DANH). Singly-attached nodes (SANs), such as maintenance laptops or printers, cannot be inserted directly into HSR rings. SANs communicate with HSR ring devices through a redundancy box (RedBox) that acts as a proxy for the SANs attached to it. Quadruple port devices (QuadBoxes) are used to connect DANH rings in connected-ring networks. A single DANH ring consists of DANHs, each having two ring ports, interconnected by full-duplex links. When a source DANH sends a unicast frame to a destination DANH in a DANH ring, the source DANH prefixes the frame by an HSR tag and sends the tagged frame over each port. In the failure-free case, the destination DANH receives two identical frames from each port, removes the HSR tag of the first frame before passing it to its upper layers, and discards any duplicate. The standard HSR protocol works very effectively in single-ring networks. The HSR protocol, however, generates too much redundant unicast traffic in connected-ring networks. This drawback is caused by the following issues:
Issue 1: Duplicating and circulating frames in all the rings, except the destination DANH ring;
Issue 2: Forwarding unicast frames into all DANH rings;
Issue 3: Forwarding unicast frames into all QuadBox rings.
Several traffic filtering techniques have been proposed to solve the drawback and improve the network performance in HSR networks, including the quick removing (QR) technique [
9], the traffic control (TC) technique [
10], the port locking (PL) technique [
11], the hybrid QR and PL approach (QRPL) [
12], the enhanced port locking (EPL) technique [
13], and the filtering HSR traffic (FHT) technique [
14]. However, most of the techniques (QR, TC, PL, QRPL, and EPL) do not solve all the HSR issues, whereas the FHT solves all the issues but generates additional control overhead in HSR networks. Several dual paths-based techniques have been proposed to reduce redundant unicast traffic in HSR networks based on pre-established paths. These techniques discover and establish dual paths between a source and a destination in an HSR network before forwarding unicast traffic frames from the source to the destination through the dual paths. Dual paths-based techniques include the dual virtual paths (DVP) [
15] technique, which was then extended as extended dual virtual paths (EDVP) [
16], the ring-based dual paths (RDP) [
17] technique, and the dual separate paths (DSP) [
18] technique. These dual paths-based techniques significantly reduce redundant unicast traffic in HSR networks. The main drawback of the techniques, however, is to generate additional control overhead in the networks because they exchange control messages to discover and establish dual paths. In addition, there are other techniques for reducing redundant unicast traffic in HSR networks, including the HSR SwitchBox technique [
19] and the integration of HSR and OpenFlow (HSE + OF) [
20]. The HSR SwitchBox technique defines a new switching node in HSR networks that forwards HSR frames based on looking up of media access control (MAC) tables instead of flooding the frames. The HSE + OF approach aims to manage HSR networks by means of the software defined networking (SDN) paradigm. The approach defines new HSE + OF nodes whose control plane is managed by an OpenFlow controller [
20]. In other words, this approach is an implementation of HSR in SDN.
In this paper, we propose a very effectively filtering approach (EFA) to significantly reduce redundant unicast traffic in HSR networks by combining two existing filtering techniques with a newly-proposed filtering technique. We propose a new traffic filtering technique for QuadBox rings (FQR) to filter unicast traffic for unused QuadBox rings. The FQR technique is then combined with two existing techniques, including PL and QR to provide the combined approach EFA that effectively reduces redundant unicast traffic in HSR networks. The proposed EFA filters unicast traffic for both unused DANH rings by using the PL technique and unused QuadBox rings by using the newly-proposed FQR technique. The EFA also prevents the unicast traffic frames from being duplicated and circulated in rings by using the QR technique. The EFA, thus, significantly reduces redundant unicast traffic in HSR networks compared with the standard HSR protocol and other traffic-filtering techniques, such as QR, PL, QRPL, and EPL. In addition, although the EFA, FHT, and dual paths-based techniques exhibit similar network traffic performance, the EFA generates less control overhead than the FHT technique and existing dual paths-based techniques. In other words, the motivation of this paper is to propose a novel approach that reduces more redundant unicast traffic than the existing filtering techniques and generates less control overhead than the FHT and existing dual paths-based techniques. The proposed approach, therefore, saves network bandwidth and improves network performance.
The rest of this paper is organized as follows:
Section 2 describes several existing traffic filtering techniques, while
Section 3 introduces the proposed EFA for effectively reducing unicast traffic in HSR networks. In
Section 4, the performance of the proposed approach is analyzed, evaluated, and compared to that of the standard HSR protocol and existing techniques.
Section 5 describes several simulations and their results in order to evaluate and validate the performance analysis. Finally,
Section 6 provides several conclusions drawn from this work.
2. Related Work
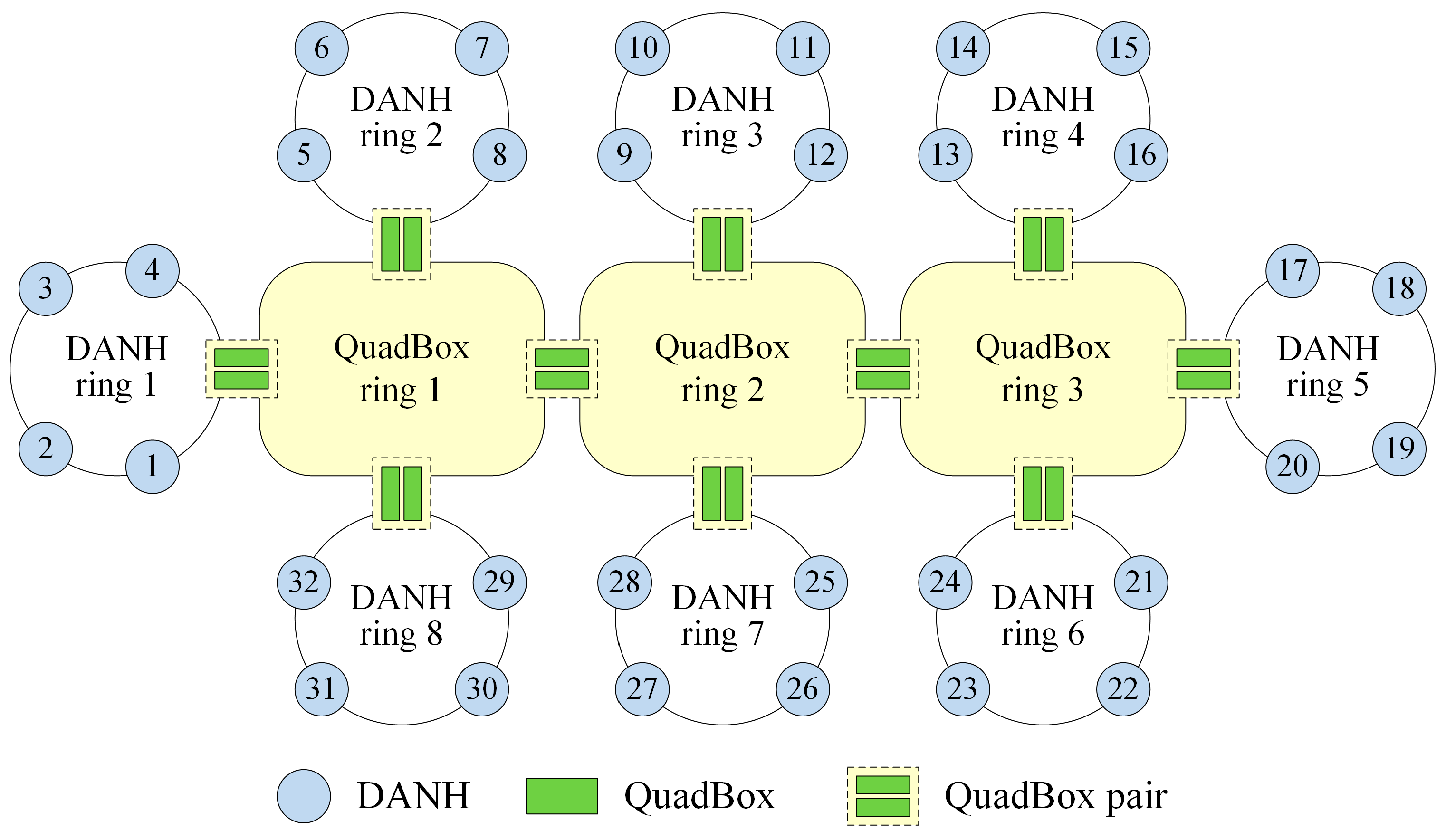
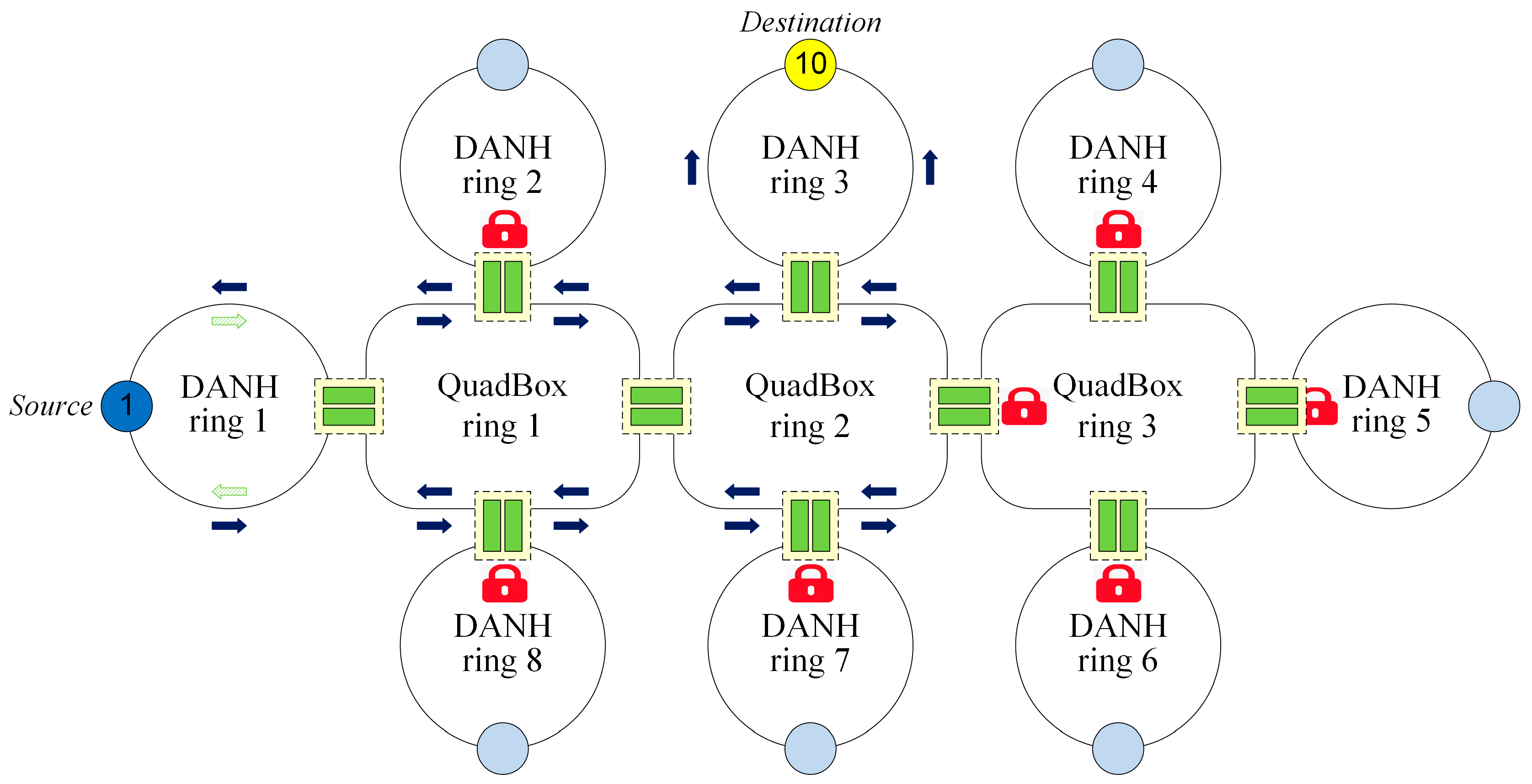
This section introduces several existing traffic filtering techniques including QR, PL, QRPL, EPL, and FHT that were proposed to reduce redundant unicast traffic in HSR networks. To demonstrate the operations of these existing filtering techniques, we consider an HSR network with eight DANH rings and three QuadBox rings as shown in
Figure 1.
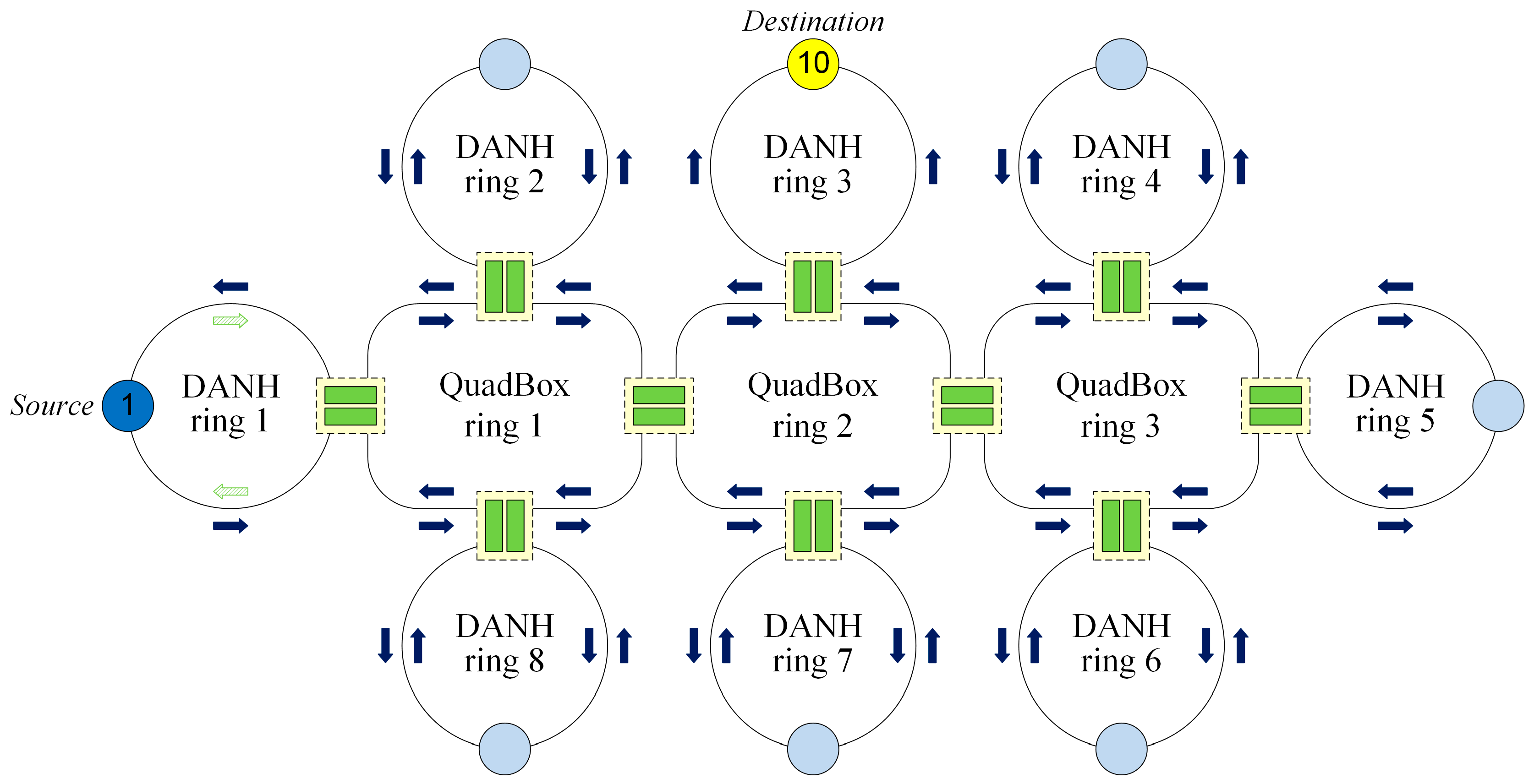
Under the standard HSR protocol, when source node 1 sends a unicast frame to destination node 10, the frame is duplicated and circulated in all rings, except the destination DANH ring as shown in
Figure 2. This flooding process generates excessively redundant unicast traffic in the HSR network.
2.1. QR
QR reduces redundant traffic in HSR networks by solving the HSR issue 1. In other words, the QR technique prevents traffic frames from being duplicated and circulated in rings, as shown in
Figure 3. When a node receives an HSR frame for the first time, the node floods the frame over all its ports except the received port from which the frame has been received. Later, if the node continues to receive other copies of the frame, the node will discard the duplicate copies.
QR is the simplest traffic filtering technique. The technique can filter any traffic. The main disadvantage of QR, however, is that it does not filter unicast traffic for unused rings.
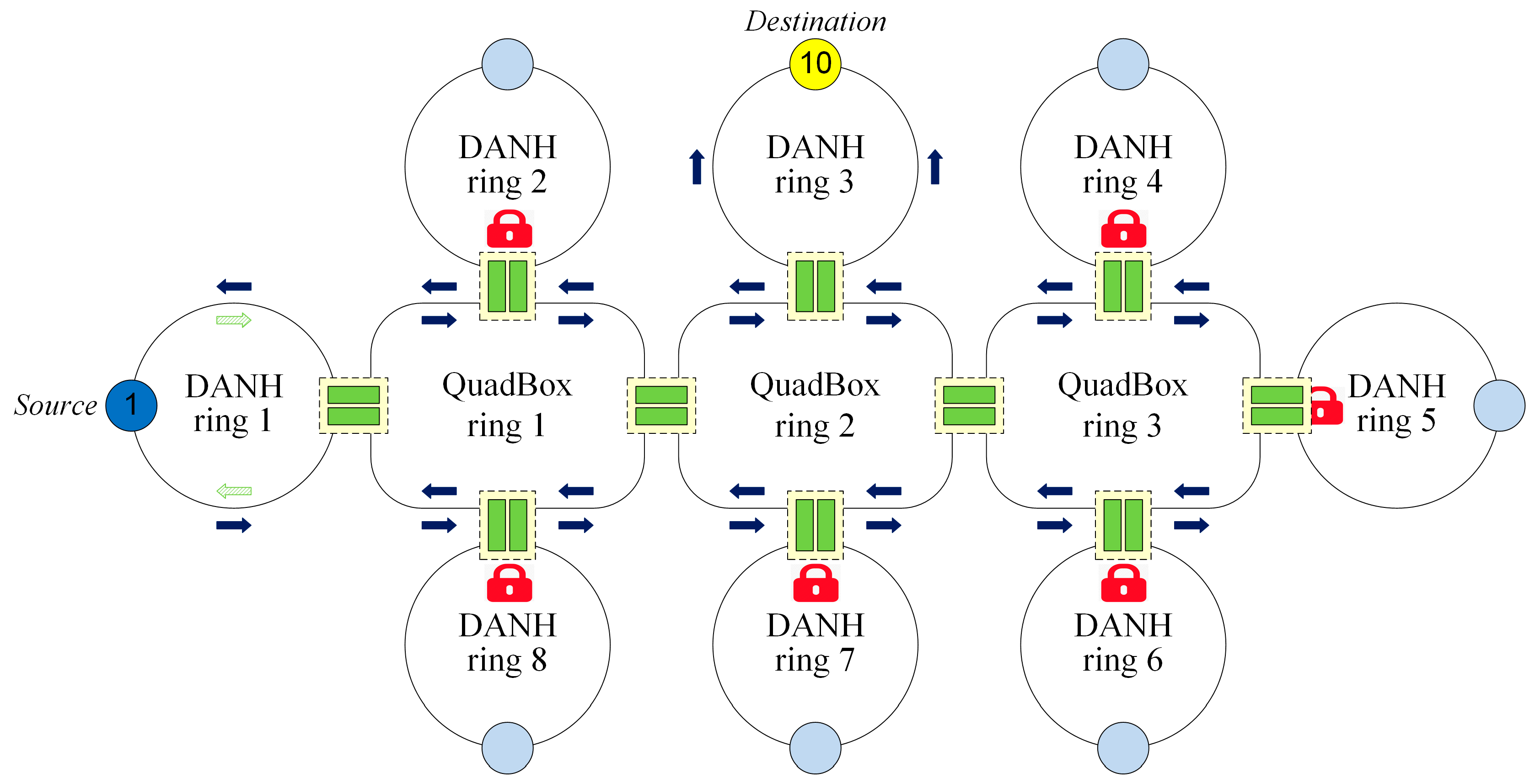
2.2. PL
PL reduces redundant unicast traffic in HSR networks by filtering unicast traffic for unused DANH rings. PL divides each access QuadBox into two sides: a DANH side that is connected to a DANH ring and a QuadBox side that is connected to a QuadBox ring. The technique does not forward a unicast frame to DANH rings that do not contain the destination DANH by locking DANH sides connecting the DANH rings. When the source DANH sends unicast frames to the destination DANH, the PL technique uses the first sent frame to check if DANH rings contain the destination DANH and then lock DANH rings that do not contain the destination DANH. After the phase, the PL does not forward unicast frames into the locked DANH rings, as shown in
Figure 4.
The drawbacks of PL, however, are that it does not solve the HSR issues 1 and 3.
2.3. QRPL
QRPL is a hybrid approach that combines the QR technique with the PL technique. The QRPL approach uses the PL technique to filter unicast traffic frames for DANH rings and the QR technique to remove duplicated and circulated frames from rings, as shown in
Figure 5.
The main drawback of the QRPL approach, however, is that it does not filter unicast traffic for QuadBox rings, which results in redundant unicast traffic traveling in these rings.
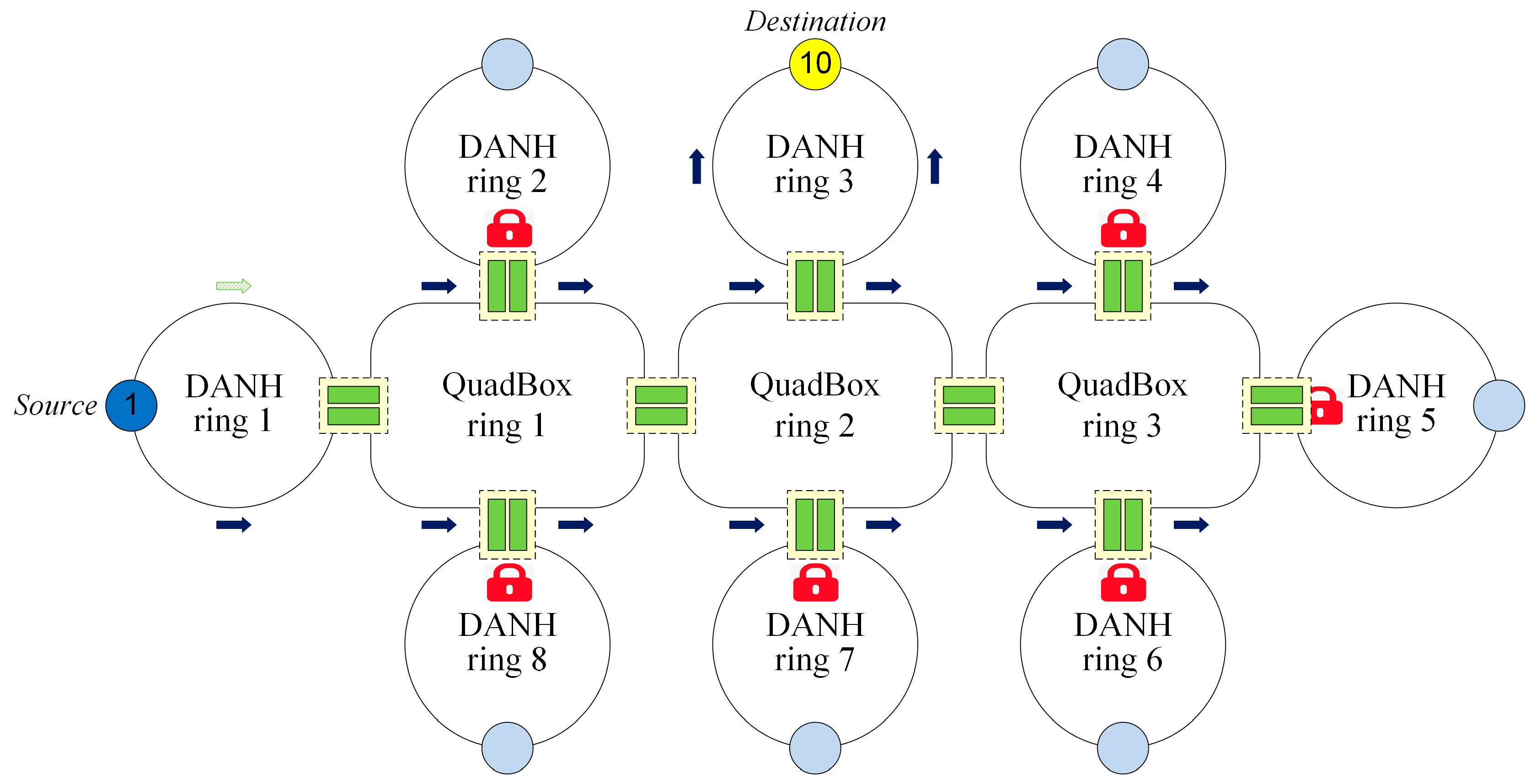
2.4. EPL
EPL is the improved version of the PL technique that filters unicast traffic for both unused DANH and QuadBox rings, as shown in
Figure 6. The EPL technique works with the same locking concept as the PL technique.
The EPL technique, however, does not prevent unicast frames from being duplicated and circulated in active rings.
2.5. FHT
FHT is the only technique that solves all the HSR issues abovementioned in
Section 1. The FHT technique filters unicast frames for both unused DANH and QuadBox rings by using MAC tables. The technique learns MAC addresses of DANHs and builds MAC tables by exchanging control messages. In addition, the FHT prevents unicast frames from being duplicated in rings. The process of forwarding unicast frames under the FHT technique is shown in
Figure 7.
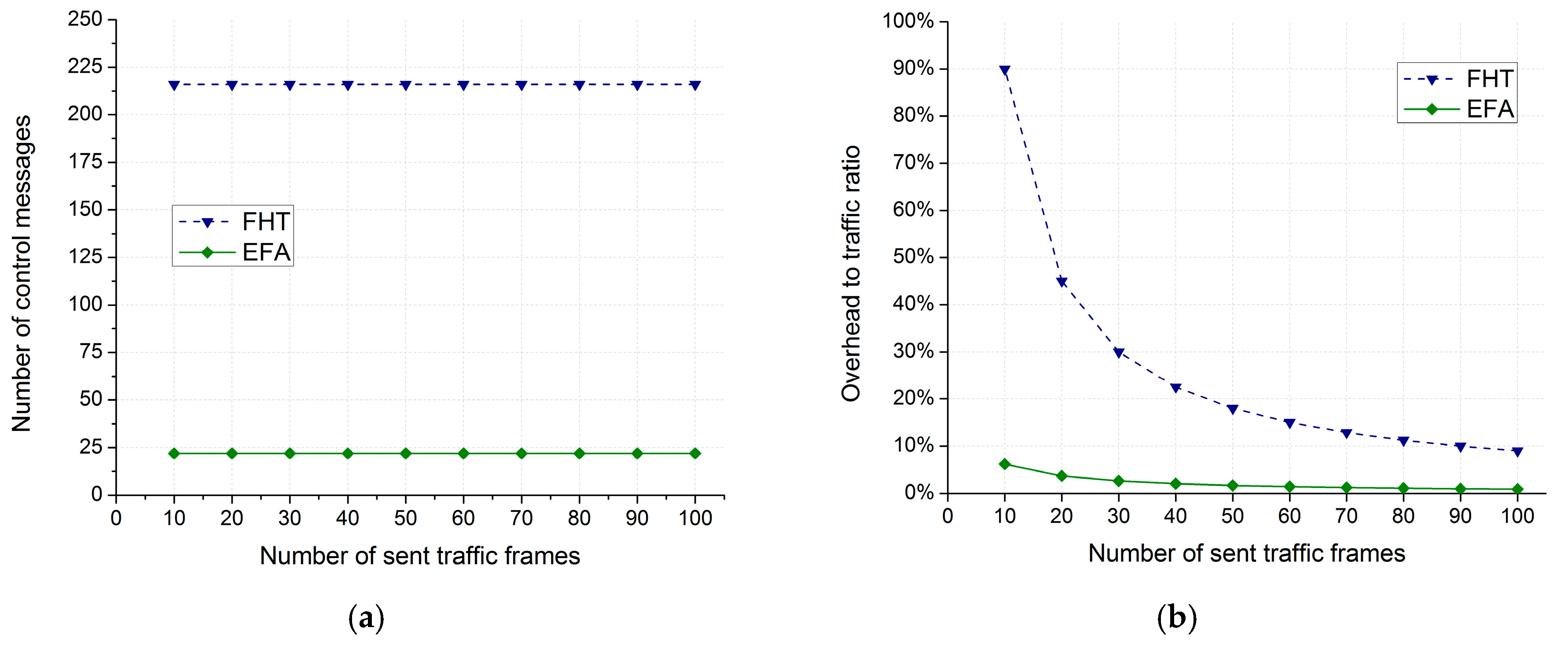
The main drawback of the FHT technique is that it generates additional control overhead in HSR networks due to the use of control messages.
2.6. Comparisons
As described above, several existing traffic filtering techniques have advantages and disadvantages. While QR prevents unicast frames from being duplicated and circulated in rings, it does not filter unicast traffic for unused rings. The PL and EPL filter unicast traffic for unused rings. They, however, do not remove duplicated unicast traffic from rings. The QRPL is a hybrid approach that combines the QR with the PL in order to filter unicast traffic for unused DANH rings and to prevent the traffic from being duplicated and circulated in rings. The QRPL, however, does not filter the unicast traffic for unused QuadBox rings. The FHT filters unicast traffic for both unused DANH and QuadBox rings, as well as removing duplicated traffic from rings. FHT does generate a certain degree of control overhead for learning and building MAC tables, however. The characteristics of these filtering techniques are summarized in
Table 1.
3. The Proposed EFA
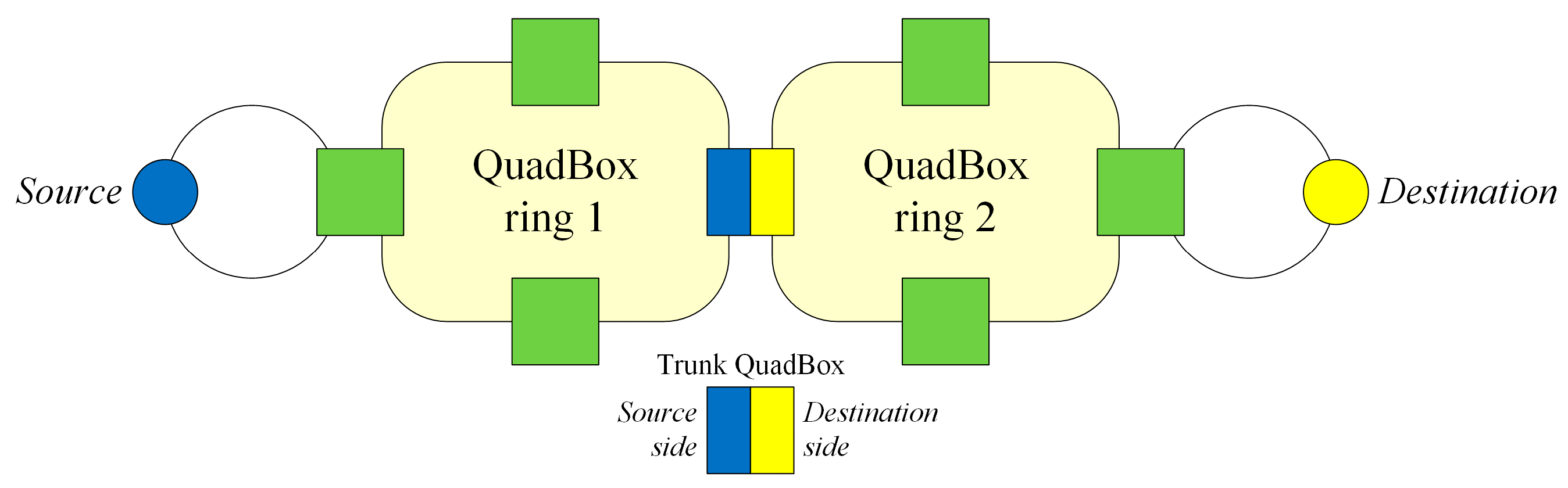
Three types of QuadBoxes are defined in this paper: access QuadBoxes, trunk QuadBoxes, and QuadBox pairs:
The access QuadBox is a QuadBox that connects to at least one DANH ring;
The trunk QuadBox is a QuadBox that does not connect to any DANH ring; in other words, trunk QuadBoxes are used to connect QuadBox rings;
A QuadBox pair refers to two QuadBoxes that are used as a pair to connect two rings to prevent a single point of failure.
The main purpose of the proposed EFA is to filter unicast traffic frames for both unused DANH rings and unused QuadBox rings, as well as preventing the unicast traffic frames from being duplicated and circulated in rings of HSR networks.
3.1. Removing Duplicated Unicast Traffic
To solve issue 1 of HSR, the EFA uses the QR technique to prevent unicast traffic frames from being duplicated and circulated in all rings of HSR networks. By using the QR technique, each HSR node, such as a DANH node or a QuadBox node, forwards a unicast frame over all its ports (except the received port) when the node has received the frame for the first time. Later, if the node receives copies of the frame, the node will discard the duplicated copies.
3.2. Filtering Unicast Traffic for DANH Rings
The EFA filters unicast traffic for any DANH rings that do not contain the destination by applying the PL technique. For a communication session between source node 1 and destination node 10, when the source sends the first unicast frame, each access QuadBox forwards the frame into its DANH ring to check if its DANH ring contains the destination node. If not, then the access QuadBox locks its DANH side to prevent the frame from being forwarded into the DANH ring.
3.3. Filtering Unicast Traffic for QuadBox Rings
To solve issue 3 of HSR (as noted above), we propose in this paper a novel filtering technique called “filtering for QuadBox rings” (FQR) to filter unicast traffic for unused QuadBox rings. FQR divides each trunk QuadBox into two sides, both of which consist of two ports connected to a QuadBox ring. For a communication session between a source and a destination in an HSR network, FQR sets each side of each trunk QuadBox to either the source side or the destination side. The source side is closer to the source than the destination side, as shown in
Figure 8. The source and destination sides of each trunk QuadBox are only locally significant in each communication session.
FQR filters unicast traffic for any QuadBox rings that are not used to deliver unicast frames in a communication session between a source and a destination in an HSR network by locking the destination sides of the QuadBoxes. The FQR operation consists of (1) the setting step and (2) the locking step, as described below.
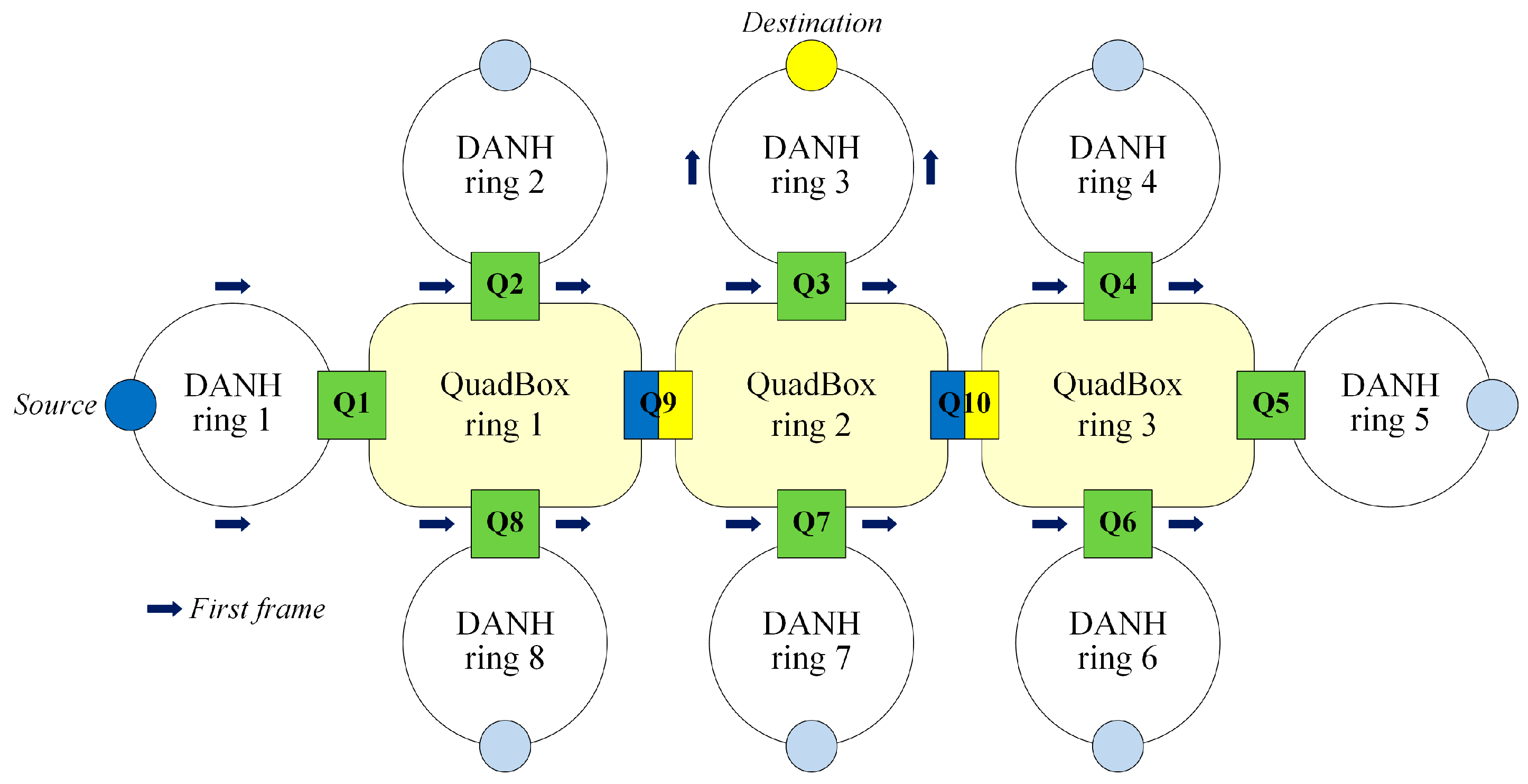
3.3.1. Setting Step
In this step, each side of each trunk QuadBox is set to either the source side or the destination side. This step is initiated once a communication session between a source and a destination is started. In other words, the step is performed while the first traffic frame is delivered from the source to the destination of the communication session. When the source sends the first HSR frame to the destination, the frame is flooded into all the rings in the network (as occurs in the standard HSR protocol). When a trunk QuadBox receives the first frame of the communication session, the trunk QuadBox sets the side from which the frame is received to the source side and sets the other side to the destination side, as shown in
Figure 9.
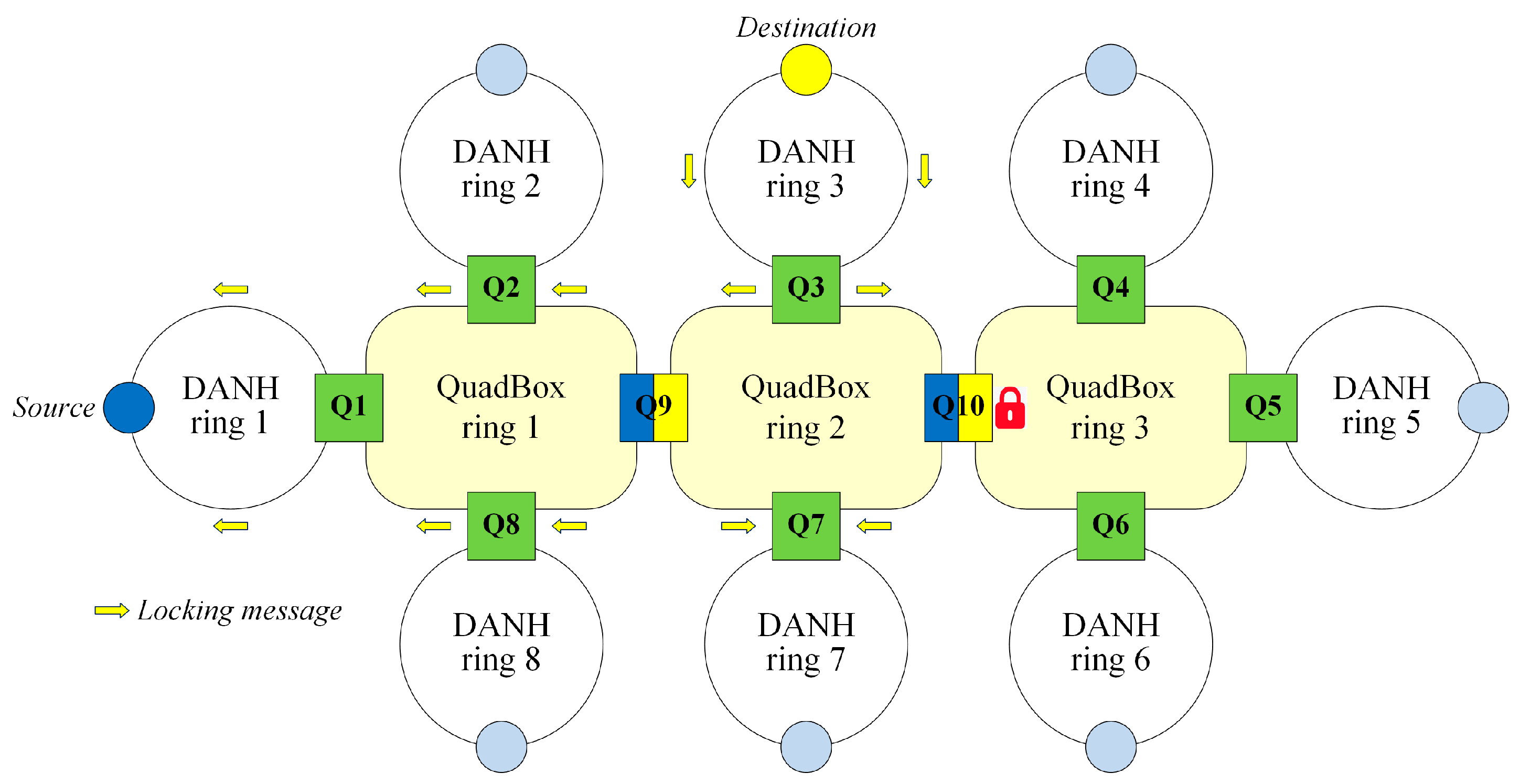
3.3.2. Locking Step
This step locks the destination sides of any QuadBoxes that are not used to deliver unicast traffic frames from the source to the destination. Once the destination receives the first HSR frame sent by the source, the destination initiates the locking step by sending a “locking” message back to the source. Only trunk QuadBoxes process and forward the locking message, whereas access QuadBoxes discard the message. When a trunk QuadBox receives a locking message, it checks if the side from that the locking message has been received is the source side or the destination side:
If the received side is the destination side, then the QuadBox does not lock its destination side.
If the received side is the source side, then the QuadBox locks its destination side.
The trunk QuadBox then forwards the received locking message over its ports, except for the received port and the locked ports, which belong to the locked destination side.
Figure 10 shows the process of checking and locking destination sides based on receiving the locking message at trunk QuadBoxes.
3.4. Operations of the Proposed EFA
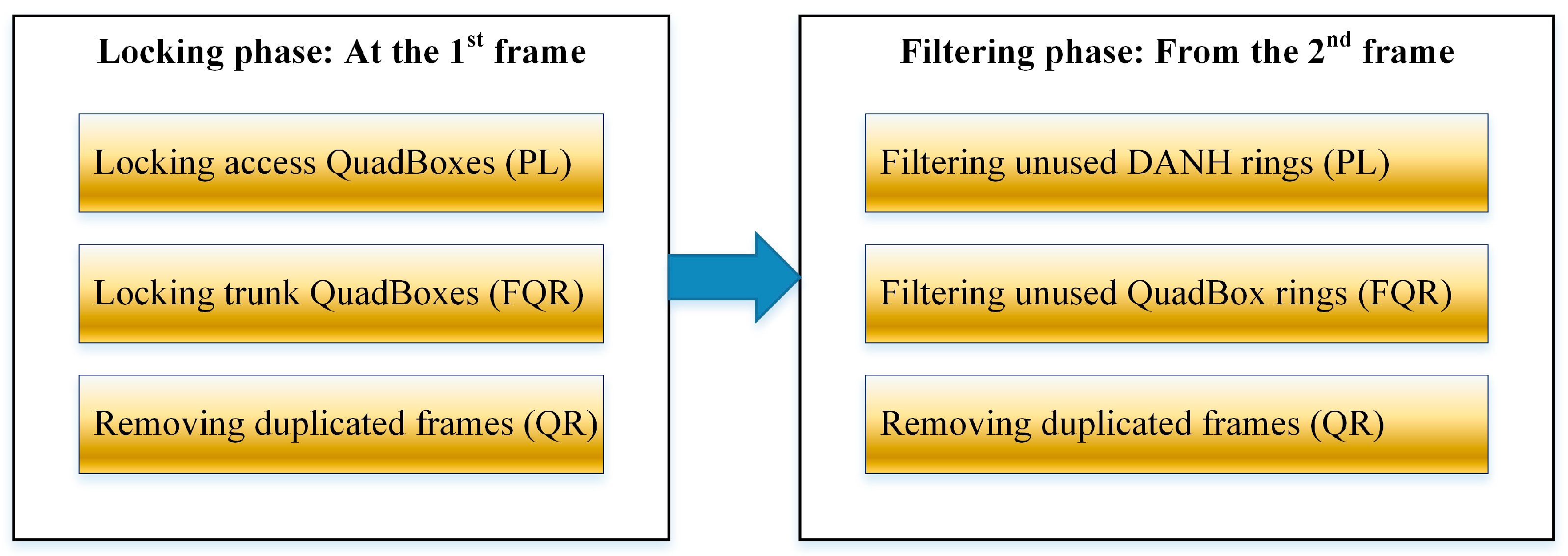
The EFA consists of two phases as shown in
Figure 11, including locking phase and filtering phase. The locking phase occurs during the forwarding process of the first frame. In this phase, the EFA checks and locks access and trunk QuadBoxes that connect to unused DANH and QuadBox rings, respectively. The locking phase is followed by the filtering phase that starts when the second frame is sent. In the filtering phase, the EFA does not forward unicast frames into unused DANH and QuadBox rings.
At the first frame, the network will work in the same way as the standard HSR protocol. From the second frame, unicast frames will be forwarded and filtered under the EFA effect. In the locking phase, when the source sends the first frame of a communication session to the destination, the frame is flooded in the whole network. During delivery of the first frame, access QuadBoxes use the PL technique to check their DANH rings and lock their DANH sides if their DANH rings do not contain the destination. Once the destination receives the first unicast frame, the destination sends a locking message back to the source. Upon receiving the locking message, trunk QuadBoxes use the FQR technique to check and lock their destination sides, if needed. Access QuadBoxes discard the locking message they have received. At that time, QuadBoxes have locked sides that are not used to forward unicast frames from the source to the destination. In the filtering phase, the next frames will not be forwarded into any DANH and QuadBox rings that are connected to locked DANH sides and locked destination sides. In addition, the EFA uses the QR technique to remove any duplicated unicast frames from rings.
Figure 12 illustrates the process of forwarding unicast frames from source 1 to destination 10 in the sample HSR network.
6. Conclusions
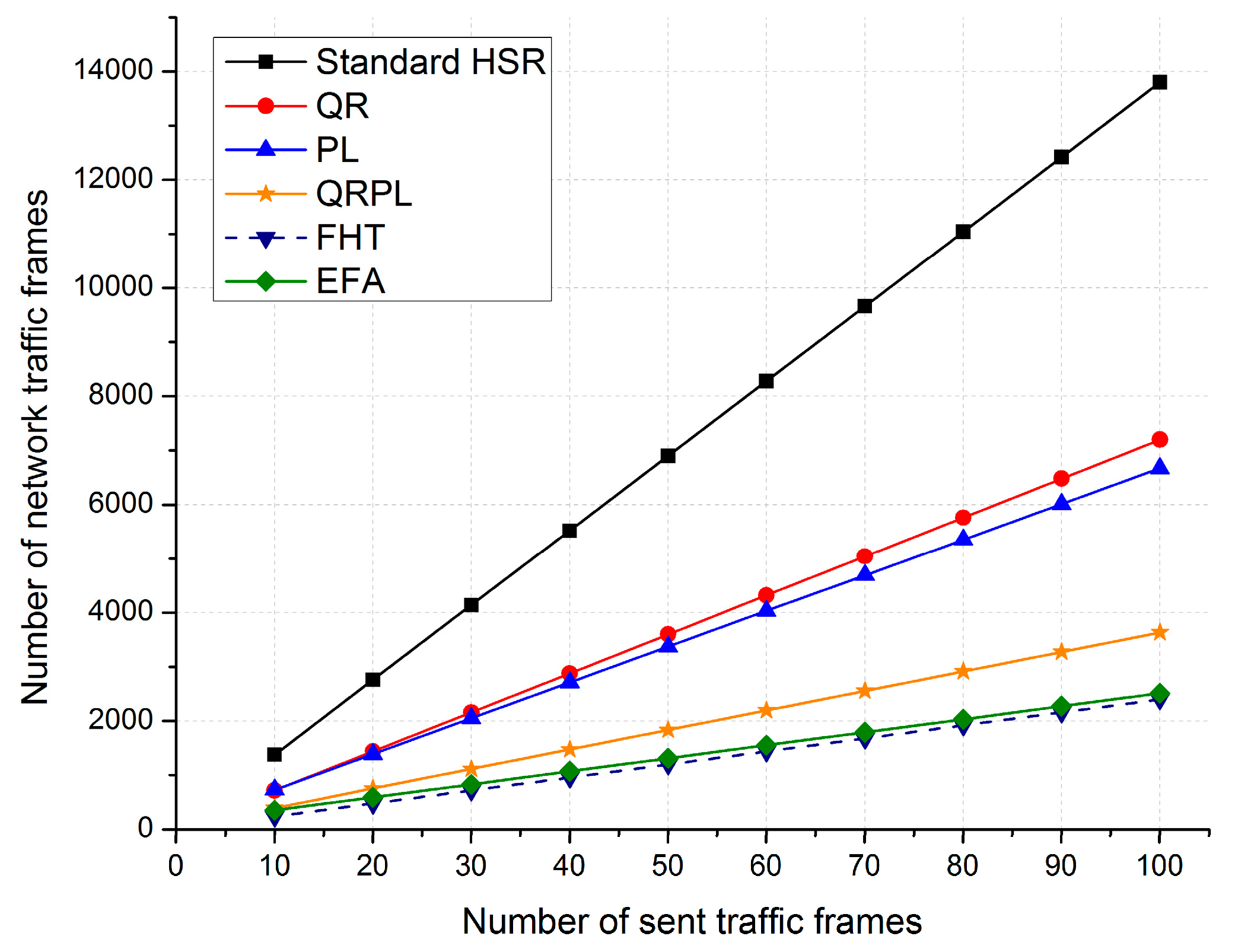
In this paper we proposed a novel approach called EFA for effectively reducing redundant unicast traffic in HSR networks. The EFA integrates a novel filtering technique for QuadBox rings in HSR networks called the FQR technique with two existing filtering techniques, QR and PL, in order to filter redundant unicast traffic for both DANH and QuadBox rings, as well as to prevent unicast frames from being duplicated and circulated in rings. The EFA thus demonstrates the best network traffic performance among the various available filtering techniques. The analytical and simulation results showed that, for the sample network, EFA reduced network unicast traffic by 80% compared with the standard HSR protocol, by ~62% compared with the QR technique, by ~60% compared with the PL technique, and by ~26% compared with the hybrid approach of QRPL. In addition, among the best traffic performance techniques, the EFA demonstrates the best overhead performance. For the sample network, the number of control messages generated by the EFA is one tenth that of the FHT. In conclusion, the EFA is a very efficient approach that reduces more redundant unicast traffic in HSR networks than existing filtering techniques and generates less control overhead in the networks than the FHT. The EFA, thus, saves network bandwidth and improves network traffic performance in HSR networks.
Our future work will develop and implement the EFA in hardware devices.