An N-k Analytic Method of Composite Generation and Transmission with Interval Load
Abstract
:1. Introduction
1.1. Motivation
- (1)
- Under certain load demands, which k transmission lines out produce the best N-k contingency, and which k transmission lines out produce the worst N-k contingency?
- (2)
- Under certain load demands, which k components that include transmission lines and generators out produce the best N-k contingency, and which k components out produce the worst N-k contingency?
- (3)
- Under uncertain load demands, which k components out and which load blocks produce the best system state, and which k components out and load blocks produce the worst-case system state (WSS). The WSS refers to the worst-case scenario under uncertain conditions of N-k contingency and load demand.
1.2. Literature Review and Contributions
- (1)
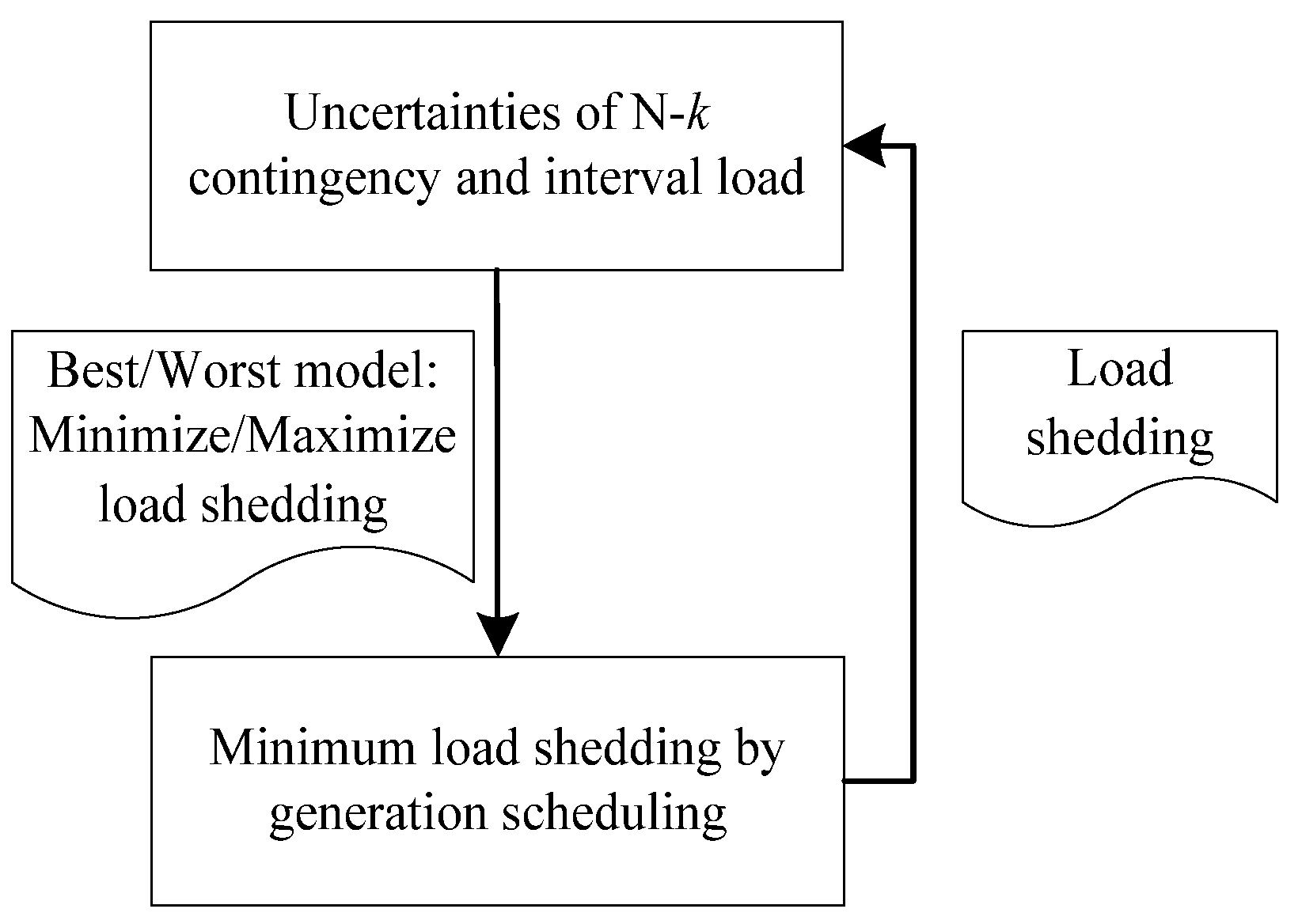
- From a stringently mathematical view, we establish two models for identifying the best and worst scenarios given the uncertainties of N-k contingency and load demand. These models are based on a minimum load shedding problem with linearized DC power flow. All N-k contingencies with generators and lines and interval loads were considered in this paper. The model used for identifying the best scenario is single mixed integer linear programming, but identifying the worst scenario is a bi-level optimization problem. Compared with the model for the best scenario, therefore, the model for the worst scenario is complex and applicable in real-world power systems. Therefore, we mainly focus on the model for identifying the worst scenario.
- (2)
- Applying strong duality theory and mathematical linearization methods, we transformed the bi-level optimization of identifying the worst scenario into a mixed integer linear program (MILP). The MILP can be mathematically solved by mature optimization software. The mathematical method of linear bi-level optimization has already been matured [15,17]; hence, the paper mainly uses strong duality and linearization method for the bi-level model solution.
- (3)
- Detailed analyses of N-k contingencies with IEEE-RTS-24 and IEEE-118 bus systems were performed. These numerical studies demonstrate the effectiveness of the MILP method for identifying the worst-case scenario and illustrate the impact of generator contingencies on N-k analysis.
1.3. Paper Organization
2. Problem Formulations
2.1. Model Assumptions
- (1)
- (2)
- Details of up, down and ramp constraints of generators are neglected. We assume generation units can be re-dispatched quickly under post contingency.
- (3)
- Only load shedding quantifies the quality of the state of the N-k contingency. The indicator for ranking all contingencies is only load shedding, which is useful to power system expansion planning [8].
- (4)
- Interval load demand describes the uncertain loads [8].
2.2. The Best-Case System State Model of N-k Contingency
2.3. Worst-Case System State Model of N-k Contingency
3. Model Solution
3.1. Single-Level Formulation
- (1)
- Under Karush–Kuhn–Tucker (KKT) conditions, the lower-level model can be substituted with its primal constraints, its dual constraints and its complementarity constraints.
- (2)
- Using primal and dual formulation (PD), the strong duality theorem (SDT) equality replaces its complementarity constraints.
3.2. Linearized Formulation
4. Numerical Studies
4.1. Results of Case 1 With Lines Contingecy and Peak Load
4.2. Results of Case 2 With Lines Contingency and Interval Load
4.3. Results of Case 3 With Lines and Generators Contingency and Peak Load
4.4. Results of Case 4 With Lines and Generators Contingency and Interval Load
4.5. Results of IEEE-118 Bus System With Lines and Generators Contingency and Interval Load
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
List of Symbols
| Sets and Indices | |
| , , | Set of decision variables of all, upper level and lower level model |
| Set of the dual variables | |
| Set of the auxiliary variables | |
| Set of indices of buses | |
| Set of indices of transmission lines | |
| Set of indices of generation units | |
| , | Bus index |
| The th lines or units | |
| Line index | |
| Variables | |
| Load shedding at bus | |
| Binary contingency variable of line , 0 denotes contingency, 1 otherwise | |
| Binary contingency variable of unit , 0 denotes contingency, 1 otherwise | |
| Load demand at bus | |
| Voltage angle at bus | |
| Real power flow through line | |
| Real power produced by unit | |
| Dual variable of node power balance | |
| Dual variable of branch DC power flow equation | |
| Dual variable of lower and upper bound of limit of power flow of line | |
| Dual variable of lower and upper bound of limit of output power of unit | |
| Dual variable of lower and upper bound of limit of load shedding at bus | |
| Auxiliary variable associated with line for linearization | |
| Auxiliary variable associated with unit for linearization | |
| Binary auxiliary variable for load demand discretization at bus | |
| Auxiliary variable associated with load at bus for linearization | |
| Constants | |
| , | Lower bound and upper bound of load demand at bus |
| Susceptance of transmission line | |
| Capacity of transmission line | |
| Incident element of bus and transmission line | |
| Capacity of generation unit | |
| The number of contingency | |
| Big number associated with transmission line for linearization | |
| One third of load demand at bus | |
Appendix A
References
- Li, W. Risk Assessment of Power Systems: Models, Methods, and Applications; Wiley-IEEE: Hoboken, NJ, USA, 2005. [Google Scholar]
- Karimi, E.; Ebrahimi, A. Probabilistic transmission expansion planning considering risk of cascading transmission line failures. Int. Trans. Electr. Energy Syst. 2015, 25, 2547–2561. [Google Scholar] [CrossRef]
- Lee, S.T. Probabilistic online risk assessment of non-cascading and cascading transmission outage contingencies. Eur. Trans. Electr. Power 2008, 18, 835–853. [Google Scholar] [CrossRef]
- Vaiman, M.; Keith, B.; Chen, Y.; Chowdhury, B.; Dobson, I.; Hines, P.; Papic, M.; Miller, S.; Zhang, P. Risk assessment of cascading outages: Methodologies and challenges. IEEE Trans. Power Syst. 2012, 27, 631–641. [Google Scholar] [CrossRef]
- Youwei, J.; Ke, M.; Zhao, X. N-k Induced Cascading Contingency Screening. IEEE Trans. Power Syst. 2015, 30, 2824–2825. [Google Scholar]
- Sing-Po, W.; Chen, A.; Chih-Wen, L.; Chun-Hung, C.; Shortle, J.; Jin-Yi, W. Efficient splitting simulation for blackout analysis. IEEE Trans. Power Syst. 2015, 30, 1775–1783. [Google Scholar]
- Correa, C.A.; Bolanos, R.; Garces, A. Enhanced multiobjective algorithm for transmission expansion planning considering N-1 security criterion. Int. Trans. Electr. Energy Syst. 2015, 25, 2225–2246. [Google Scholar] [CrossRef]
- Peng, W.; Haozhong, C.; Jie, X. The interval minimum load cutting problem in the process of transmission network expansion planning considering uncertainty in demand. IEEE Trans. Power Syst. 2008, 23, 1497–1506. [Google Scholar] [CrossRef]
- Habibi, M.R.; Rashidinejad, M.; Zeinaddini-Meymand, M.; Fadainejad, R. An efficient scatter search algorithm to solve transmission expansion planning problem using a new load shedding index. Int. Trans. Electr. Energy Syst. 2014, 24, 153–165. [Google Scholar] [CrossRef]
- Nam, H.K.; Kim, Y.H.; Shim, K.S.; Choi, J.H.; Kwak, N.H. A new ultra-fast contingency screening algorithm without time-domain simulation for online transient security assessment. Eur. Trans. Electr. Power 2008, 18, 725–741. [Google Scholar] [CrossRef]
- Salam, M.A.; Ahmed, S.S. A new method for screening the contingencies before dynamic security assessment of a multimachine power system. Eur. Trans. Electr. Power 2006, 16, 393–408. [Google Scholar] [CrossRef]
- Kaplunovich, P.; Turitsyn, K. Fast and Reliable Screening of N-2 Contingencies. IEEE Trans. Power Syst. 2016, 31, 4243–4252. [Google Scholar] [CrossRef]
- Arroyo, J.M. Bilevel programming applied to power system vulnerability analysis under multiple contingencies. IET Gener. Trans. Distrib. 2010, 4, 178–190. [Google Scholar] [CrossRef]
- Fliscounakis, S.; Panciatici, P.; Capitanescu, F.; Wehenkel, L. Contingency ranking with respect to overloads in very large power systems taking into account uncertainty, preventive, and corrective actions. IEEE Trans. Power Syst. 2013, 28, 4909–4917. [Google Scholar] [CrossRef]
- Jiang, R.; Zhang, M.; Li, G.; Guan, Y. Two-stage network constrained robust unit commitment problem. Eur. J. Oper. Res. 2014, 234, 751–762. [Google Scholar] [CrossRef]
- Arroyo, J.M.; Galiana, F.D. On the Solution of the Bilevel Programming Formulation of the Terrorist Threat Problem. IEEE Trans. Power Syst. 2005, 20, 789–797. [Google Scholar] [CrossRef]
- Bard, J.F. Practical Bilevel Optimization: Algorithms and Applications, 1st ed.; Kluwer Academic Publishers: Dordrecht, The Netherlands, 1998. [Google Scholar]
- Romero, N.R.; Nozick, L.K.; Dobson, I.D.; Xu, N.; Jones, D.A. Transmission and generation expansion to mitigate seismic risk. IEEE Trans. Power Syst. 2013, 28, 3692–3701. [Google Scholar] [CrossRef]
- Zheng, Q.P.; Jianhui, W.; Liu, A.L. Stochastic optimization for unit commitment—A review. IEEE Trans. Power Syst. 2015, 30, 1913–1924. [Google Scholar] [CrossRef]
- Majidi-Qadikolai, M.; Baldick, R. Stochastic Transmission Capacity Expansion Planning With Special Scenario Selection for Integrating N-1 Contingency Analysis. IEEE Trans. Power Syst. 2016, 31, 4901–4912. [Google Scholar] [CrossRef]
- Pozo, D.; Sauma, E.E.; Contreras, J. A Three-Level Static MILP Model for Generation and Transmission Expansion Planning. IEEE Trans. Power Syst. 2013, 28, 202–210. [Google Scholar] [CrossRef]
- Baringo, L.; Conejo, A.J. Transmission and wind power investment. IEEE Trans. Power Syst. 2012, 27, 885–893. [Google Scholar] [CrossRef]
- Jin, S.; Ryan, S.M. A Tri-Level Model of Centralized Transmission and Decentralized Generation Expansion Planning for an Electricity Market—Part I. IEEE Trans. Power Syst. 2014, 29, 132–141. [Google Scholar] [CrossRef]
- Subcommittee, P.M. Ieee reliability test system. IEEE Trans. Power Appl. Syst. 1979, PAS-98, 2047–2054. [Google Scholar] [CrossRef]
- IEEE 118-Bus System. Available online: http//motor.ece.iit.edu/data/ (accessed on 20 October 2015).
- Lofberg, J. Yamip. Available online: http://users.isy.liu.se/johanl/yalmip/ (accessed on 20 October 2015).
- Gurobi Reference Manual. Available online: http://www.gurobi.com/documentation/ (accessed on 20 October 2015).
- Matpower. Available online: http://www.pserc.cornell.edu/matpower/ (accessed on 20 October 2015).
- Govind Singh, J.; Guha Thakurta, P.; Soder, L. Load curtailment minimization by optimal placements of SVC/STATCOM. Int. Trans. Electr. Energ. Syst. 2014. [Google Scholar] [CrossRef]

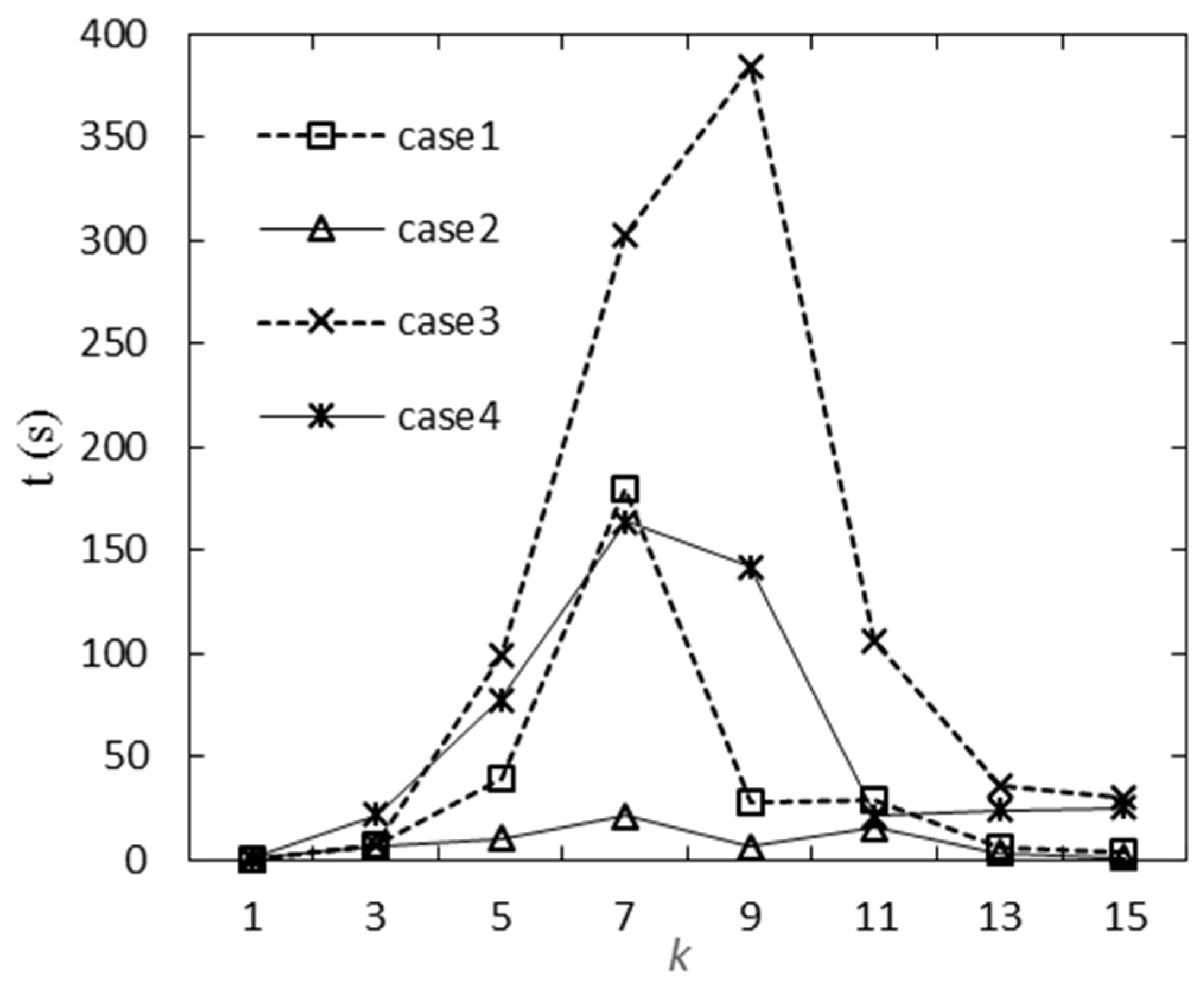
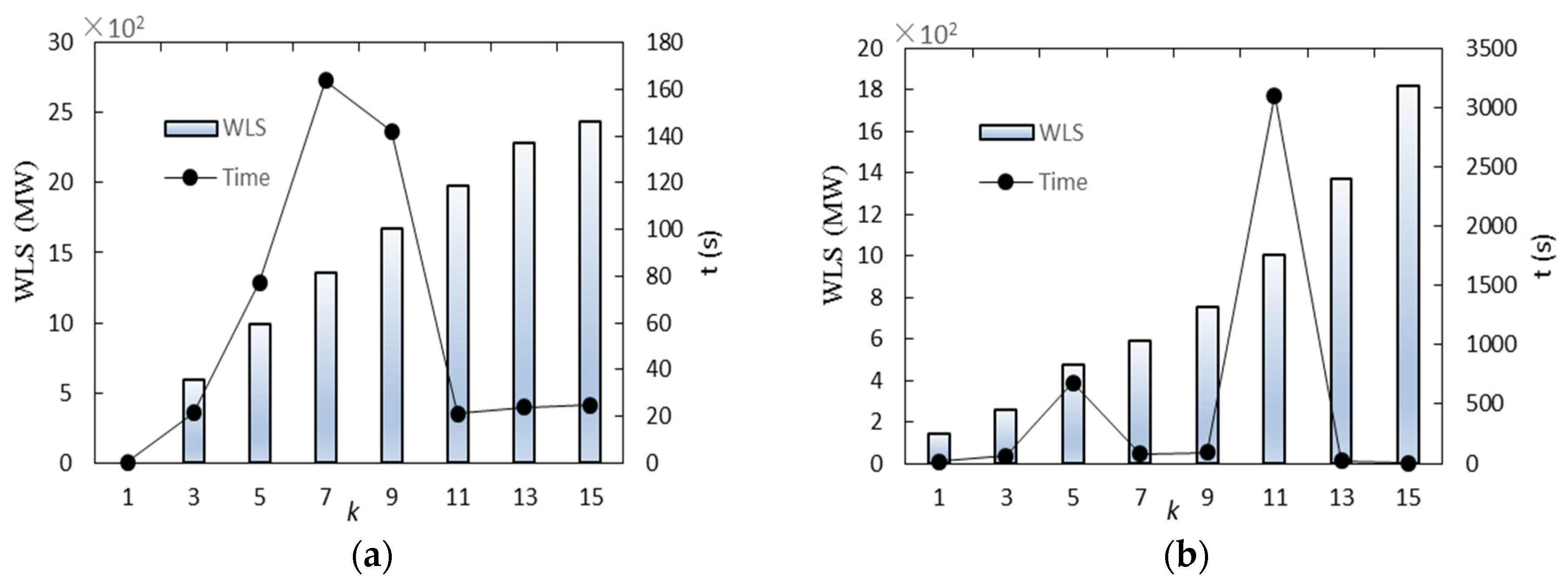
| k | WLS/MW | Contingency Lines | t (s) |
|---|---|---|---|
| 1 | 0 | -- | 0.2 |
| 3 | 309 | 16–19, 20–23, 20–23 | 7.4 |
| 5 | 842 | 11–13, 12–13, 12–23, 14–16, 15–24 | 38.8 |
| 7 | 1017 | 1–3, 3–24, 7–8, 11–13, 12–13,12–23, 14–16 | 179.7 |
| 9 | 1373 | 7–8, 9–12, 10–12, 11–13, 15–21, 15–21, 16–17, 20–23, 20–23 | 27.9 |
| 11 | 1428 | 7–8, 9–12, 10–12, 11–13, 14–16, 15–16, 15–21, 15–21, 16–19, 20–23, 20–23 | 28.7 |
| 13 | 1552 | 1–3, 1–5, 2–4, 2–6, 7–8, 9–12, 10–12, 11–13, 15–21, 15–21, 16–17, 20–23, 20–23 | 5.8 |
| 15 | 1607 | 1–3, 1–5, 2–4, 2–6, 7–8,11–13, 12–13, 12–23, 14–16, 15–16, 15–21, 15–21, 16–19, 20–23, 20–23 | 3.1 |
| k | WLS/MW | Contingency Lines | Non-Peak Buses | t (s) |
|---|---|---|---|---|
| 1 | 0 | -- | -- | 0.2 |
| 3 | 309 | 16–19, 20–23, 20–23 | 7, 13 | 6.5 |
| 5 | 842 | 3–24, 11–13, 12–13, 12–23, 14–16 | 13, 19(1), 20 | 10.4 |
| 7 | 1017 | 2–4, 7–8, 11–13, 12–13, 12–23, 14–16, 15-24 | 7, 13(2), 18 | 21.1 |
| 9 | 1373 | 7–8, 11–13, 12–13, 12–23, 15–21, 15–21, 16–17, 20–23, 20–23 | 7, 13, 18 | 6.1 |
| 11 | 1428 | 7–8, 11–13, 12–13, 12–23, 14–16, 15–16, 15–21, 15–21, 16–19, 20–23, 20–23 | 7(2) | 15.6 |
| 13 | 1552 | 1–3, 1–5, 2–4, 2–6, 7–8, 11–13, 12–13, 12–23, 15–21, 15–21, 16–17, 20–23, 20–23 | 1(1), 2 | 3.4 |
| 15 | 1607 | 1–3, 1–5, 2–4, 2–6, 7–8, 9–12, 10–12, 11–13, 14–16, 15–16, 15–21, 15–21, 16–19, 20–23, 20–23 | 1, 7, 18 | 1.1 |
| k | WLS/MW | Contingency Lines | Contingency Units/MW | t (s) |
|---|---|---|---|---|
| 1 | 0 | -- | -- | 0.3 |
| 3 | 595 | -- | 400(18), 400(21), 350(23) | 7.3 |
| 5 | 989 | -- | 2*197(13), 400(18), 400(21), 350(23) | 98.9 |
| 7 | 1361 | 7–8 | 3*197(13), 400(18), 400(21), 350(23) | 302.4 |
| 9 | 1671 | 7–8 | 3*197(13), 155(15), 155(16), 400(18), 400(21), 350(23) | 384.4 |
| 11 | 1981 | 7–8 | 3*197(13), 155(15), 155(16), 400(18), 400(21), 2*155(23), 350(23) | 105.7 |
| 13 | 2281 | 7–8, 17–22, 21–22 | 3*197(13), 155(15), 155(16), 400(18), 400(21), 2*155(23), 350(23) | 35.2 |
| 15 | 2433 | 7–8, 17-22, 21–22 | 76(1), 76(2), 3*197(13), 155(15), 155(16), 400(18), 400(21), 2*155(23), 350(23) | 30.5 |
| K | WLS/MW | Contingency Lines | Contingency Units/MW | Non-Peak Buses | t (s) |
|---|---|---|---|---|---|
| 1 | 0 | -- | -- | -- | 0.3 |
| 3 | 595 | -- | 400(18), 400(21), 350(23) | 7 | 21.4 |
| 5 | 989 | -- | 2*197(13), 400(18), 400(21), 350(23) | -- | 77.3 |
| 7 | 1361 | 7–8 | 3*197(13), 400(18), 400(21), 350(23) | -- | 163.7 |
| 9 | 1671 | 7–8 | 3*197(13), 400(18), 400(21), 2*155(23), 350(23) | -- | 141.9 |
| 11 | 1981 | 7–8 | 3*197(13), 155(15), 155(16), 400(18), 400(21), 2*155(23), 350(23) | -- | 21.2 |
| 13 | 2281 | 7–8, 17–22, 21–22 | 3*197(13), 155(15), 155(16), 400(18), 400(21), 2*155(23), 350(23) | -- | 23.9 |
| 15 | 2433 | 7–8, 17–22, 21–22 | 2*76(2), 3*197(13), 155(15), 155(16), 400(18), 400(21), 2*155(23), 350(23) | -- | 24.9 |
| k | WLS/MW | Contingency Lines | Contingency Units/MW | t (s) |
|---|---|---|---|---|
| 1 | 143.20 | 68–116 | -- | 16 |
| 3 | 258.70 | 68–116, 77–78, 79–80 | -- | 64 |
| 5 | 474.70 | 8–5, 13–15, 14–15, 16–17, 68–116 | -- | 678 |
| 7 | 593.35 | 8–5, 15–17, 16–17, 15–19, 33–37, 68–116 | 100(15) | 82 |
| 9 | 750.65 | 8–9, 23–24, 44–45, 42–49(2), 38–65, 68–116 | 500(8), 350(25) | 92 |
| 11 | 1001.20 | 9–10, 81–80 | 500(8), 350(25), 250(46), 250(49), 200(56), 200(59), 420(62), 420(65), 300(66) | 3101 |
| 13 | 1369.70 | 8–5, 86–87 | 300(24), 350(25), 250(46), 420(62), 420(65), 300(66), 500(77), 500(89), 300(92), 300(99), 300(100) | 22 |
| 15 | 1819.70 | 8–5, 86–87 | 300(24), 350(25), 250(46), 250(49), 200(56), 420(62), 420(65), 300(66), 500(77), 500(89), 300(92), 300(99), 300(100) | 4 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hong, S.; Cheng, H.; Zeng, P. An N-k Analytic Method of Composite Generation and Transmission with Interval Load. Energies 2017, 10, 168. https://doi.org/10.3390/en10020168
Hong S, Cheng H, Zeng P. An N-k Analytic Method of Composite Generation and Transmission with Interval Load. Energies. 2017; 10(2):168. https://doi.org/10.3390/en10020168
Chicago/Turabian StyleHong, Shaoyun, Haozhong Cheng, and Pingliang Zeng. 2017. "An N-k Analytic Method of Composite Generation and Transmission with Interval Load" Energies 10, no. 2: 168. https://doi.org/10.3390/en10020168






