Feedback Power Control Strategies inWireless Sensor Networks with Joint Channel Decoding
Abstract
:1. Introduction
2. System Model in the Absence of Non-Idealities
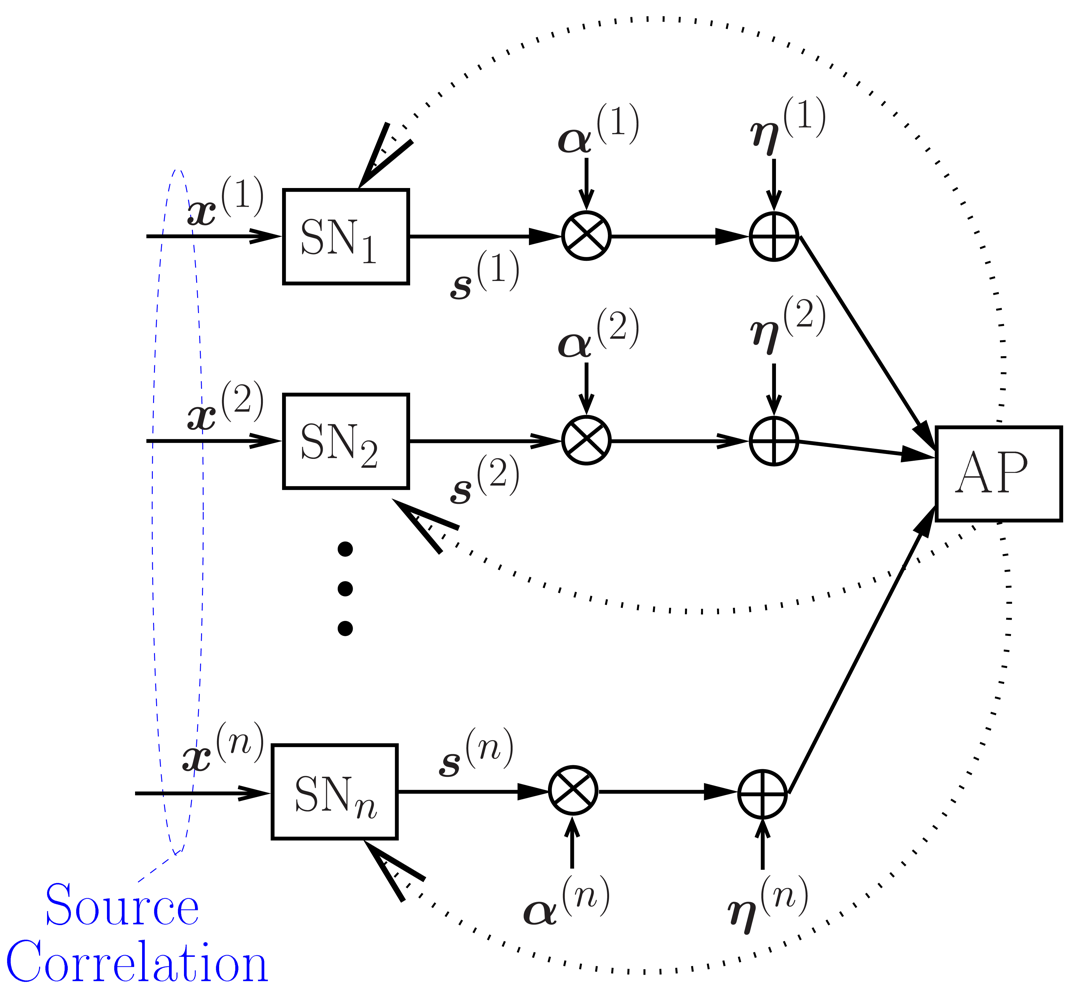
2.1. Communication Scheme and Feedback Power Control
 [|α(k)|2] = 1. We denote as
the binary (not modulated) codeword
generated at the k-th node. For simplicity, we assume that binary phase shift keying (BPSK) is the modulation format, i.e.,
, where
and
is the energy per coded bit transmitted by the k-th node. Indicating by
the transmit power at the k-th node, the transmitted bit energy in the k-th link can be written as
, where Tbit is the bit duration. Since we are considering a block fading model, we assume that the link gains can be perfectly estimated at the AP (e.g., using a short preamble with pilot symbols).
[|α(k)|2] = 1. We denote as
the binary (not modulated) codeword
generated at the k-th node. For simplicity, we assume that binary phase shift keying (BPSK) is the modulation format, i.e.,
, where
and
is the energy per coded bit transmitted by the k-th node. Indicating by
the transmit power at the k-th node, the transmitted bit energy in the k-th link can be written as
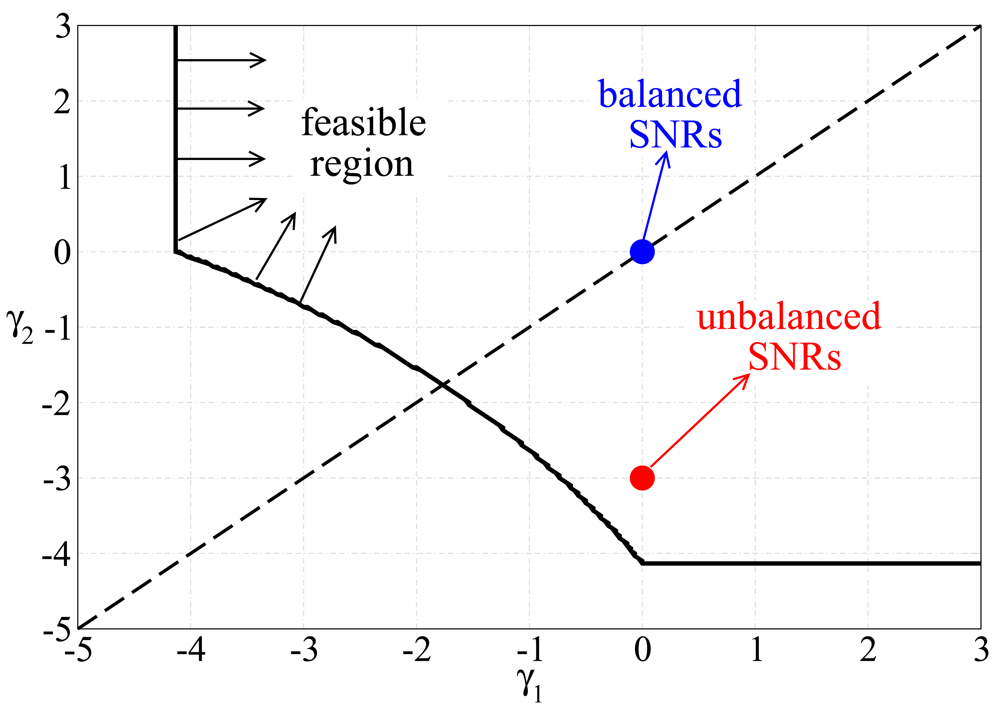
, where Tbit is the bit duration. Since we are considering a block fading model, we assume that the link gains can be perfectly estimated at the AP (e.g., using a short preamble with pilot symbols).2.2. Feasible SNR Region of a Multiple Access Scheme
3. Feedback Power Control
3.1. Feedback Power Control Strategies with Unlimited Transmit Power
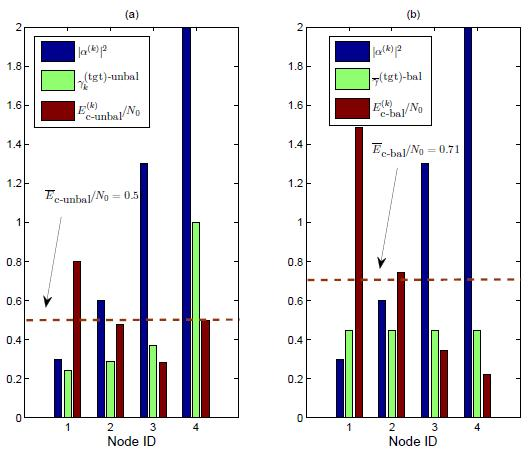
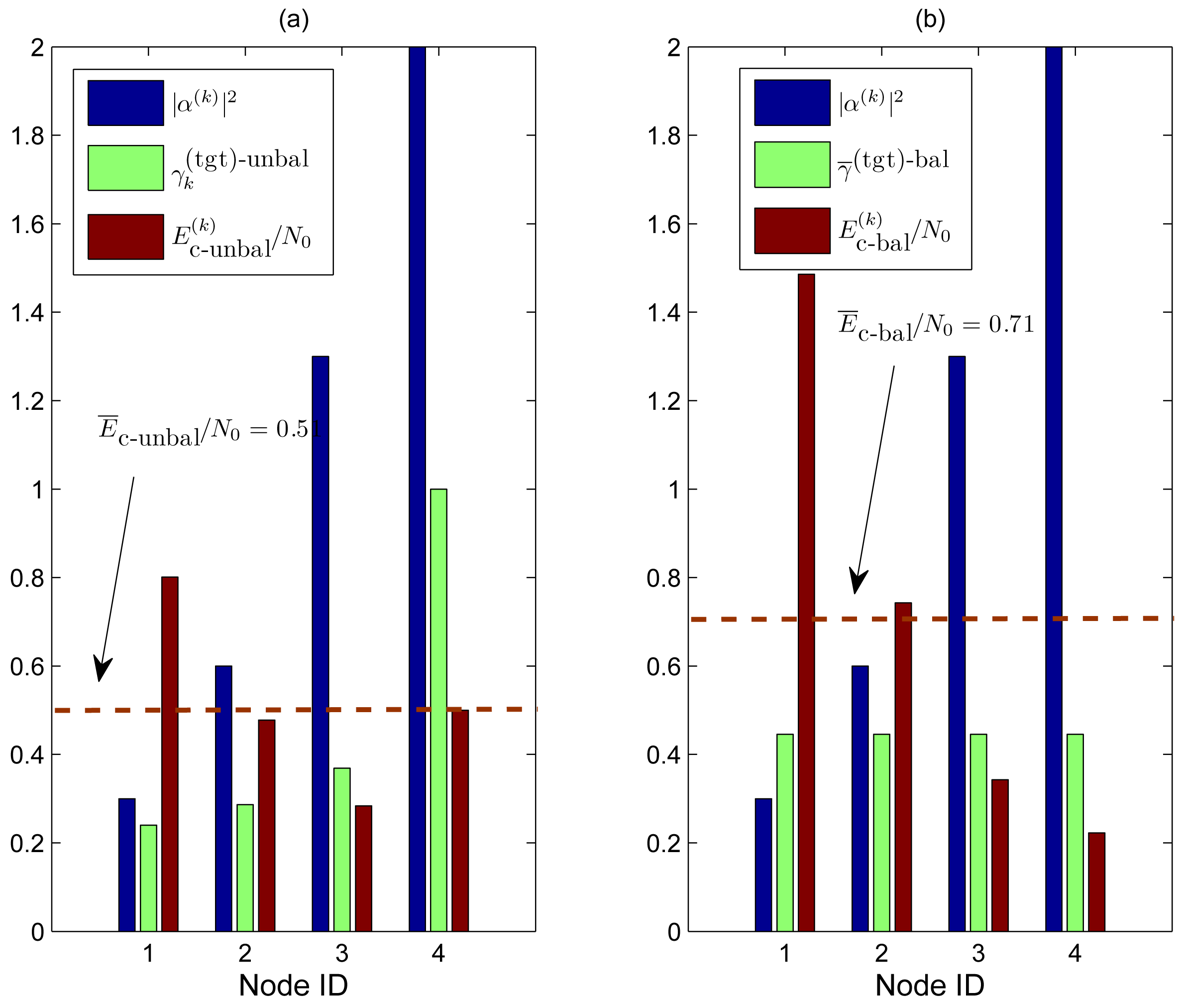
- In subfigure (a), we show the results obtained by applying the optimized (unbalanced) power control strategy. The target SNRs at the AP (shown as green bars) are the following: , , , and . At this point, the target SNRs at the transmitters (depicted in red) becomeThe average target SNR Ēc−unbal/N0 at the transmitter is thus equal to 0.51 (dashed horizontal line).
- In subfigure (b), we show the results obtained by applying the balanced SNR power control strategy. The minimum common target SNR at the AP, given by (15), is 0.45. Therefore, the target SNRs at the transmitters (depicted in red) are the following:The average SNR Ēc−bal/N0 at the transmitter becomes 0.71 (dashed horizontal line).
3.2. Practical Feedback Power Control Strategies
4. Performance Analysis in the Absence of Non-Idealities
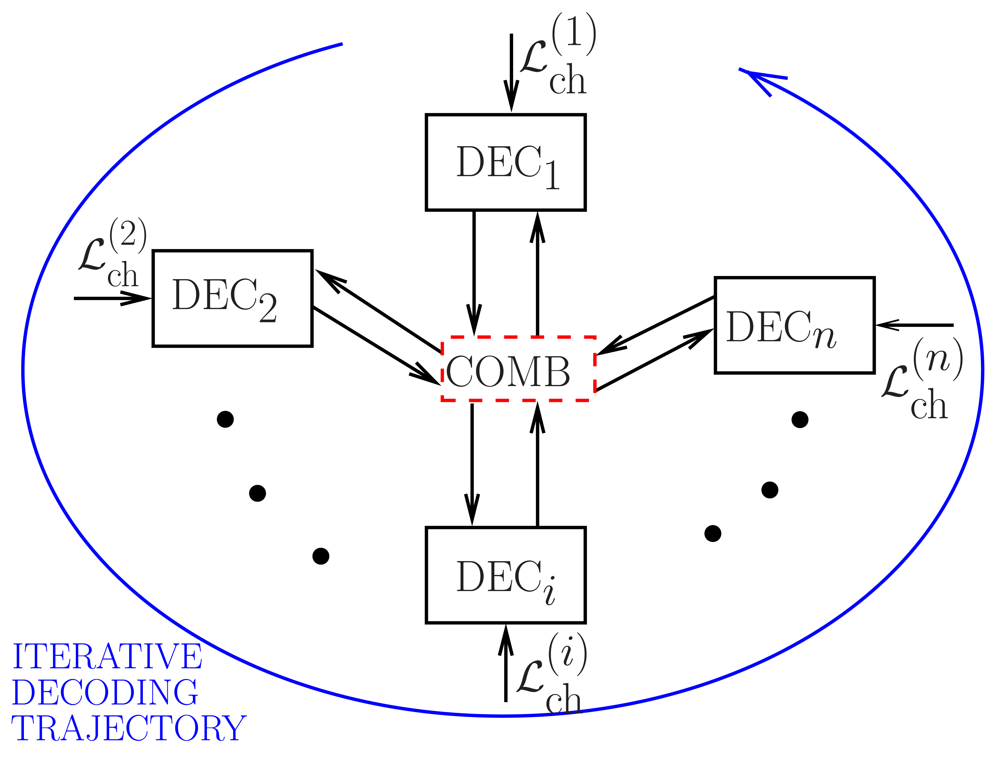
4.1. Iterative Joint Channel Decoding at the AP
 dec, depends on the specific decoding algorithm under use, namely the SP algorithm in the presence of LDPC coding or the BCJR algorithm in the presence of the SCCC. In both cases, the decoding complexity is linearly dependent on the number N of coded bits, i.e., one can write
dec, depends on the specific decoding algorithm under use, namely the SP algorithm in the presence of LDPC coding or the BCJR algorithm in the presence of the SCCC. In both cases, the decoding complexity is linearly dependent on the number N of coded bits, i.e., one can write
 dec = N
dec = N  dec−bit, where
dec−bit, where
 dec−bit is the decoding complexity “per coded bit.” Finally, at the input of each decoder one needs to consider a proper combination of the LLRs on the information bits output by the other n − 1 decoders. This combination has a complexity which depends linearly on the number L of information bits per sequence. Indicating as
dec−bit is the decoding complexity “per coded bit.” Finally, at the input of each decoder one needs to consider a proper combination of the LLRs on the information bits output by the other n − 1 decoders. This combination has a complexity which depends linearly on the number L of information bits per sequence. Indicating as
 LLR the complexity required to combine 2 LLRs, one can assume that the complexity required to combine n − 1 LLRs, relative to corresponding n − 1 bits at the same epoch, is on the order of n
LLR the complexity required to combine 2 LLRs, one can assume that the complexity required to combine n − 1 LLRs, relative to corresponding n − 1 bits at the same epoch, is on the order of n  LLR. Therefore, recalling that the number of external iterations is
, the overall complexity, denoted as
LLR. Therefore, recalling that the number of external iterations is
, the overall complexity, denoted as
 , can be written as
, can be written as
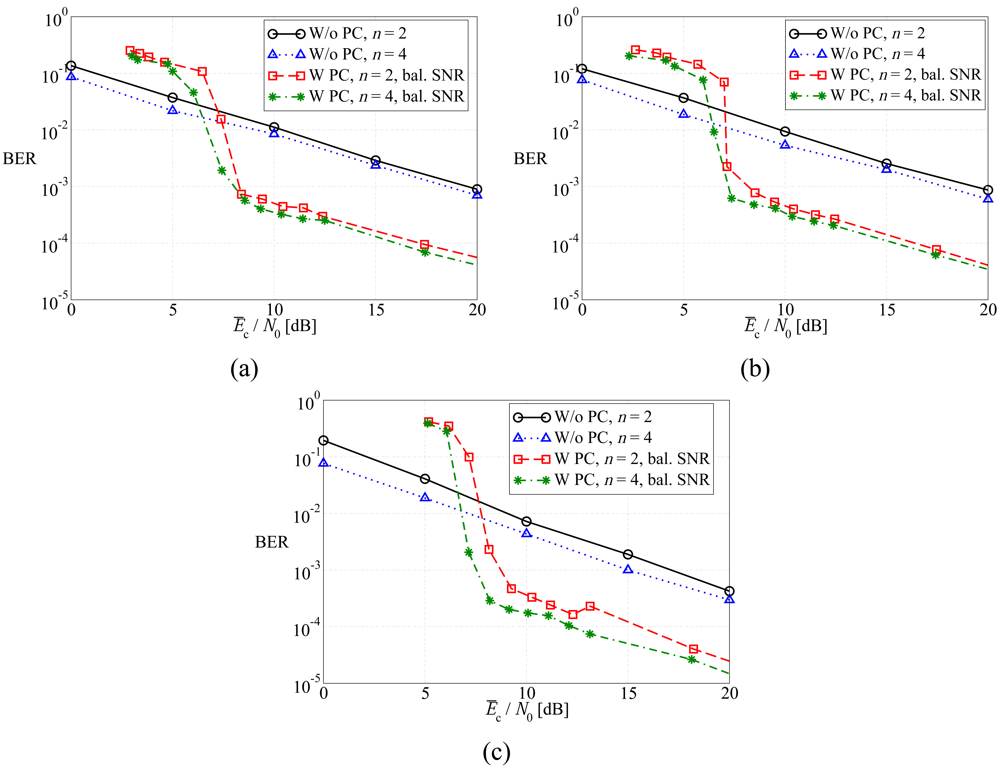
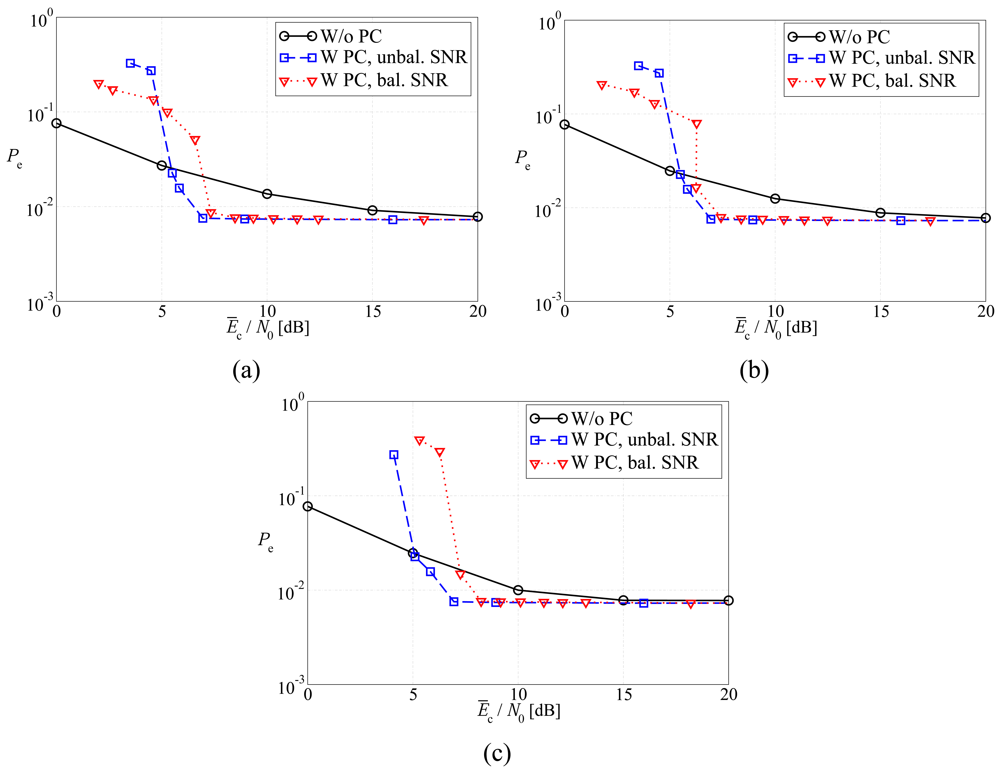
4.2. Numerical Results
5. On the Robustness of the Proposed Feedback Power Control Strategies
5.1. Non-Orthogonal Links: Multiple Access Interference
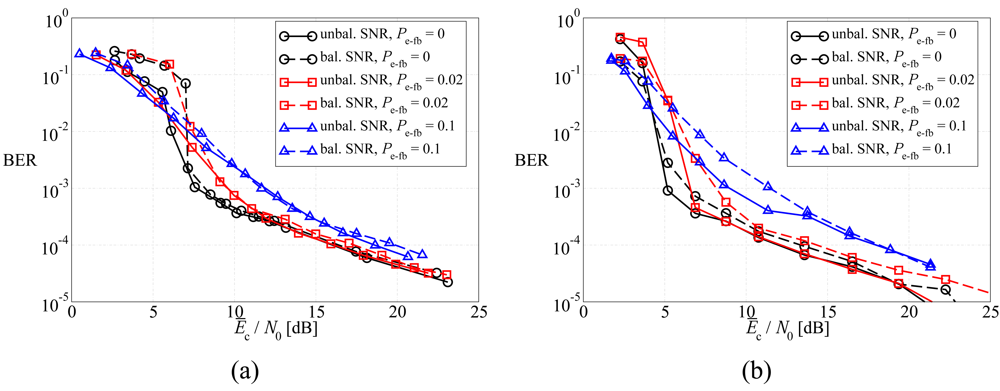
5.2. Noisy Feedback Channels
6. Extension to Scenarios with Fusion: CEO Problem
6.1. Fusion Rule
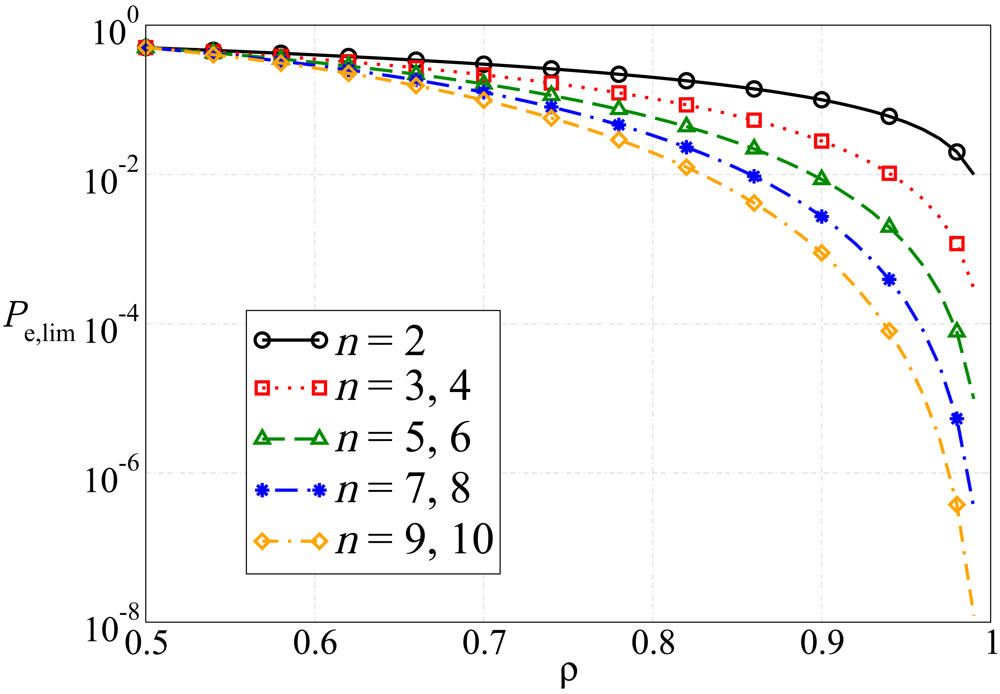
6.2. Numerical Results
7. Concluding Remarks
References
- Akyildiz, I.; Su, W.; Sankarasubramaniam, Y.; Cayirci, E. A survey on sensor networks. IEEE Commun. Mag. 2002, 40, 102–114. [Google Scholar]
- Gupta, P.; Kumar, P. The capacity of wireless networks. IEEE Trans. Inform. Theory 2000, 46, 388–404. [Google Scholar]
- Gamal, H.E. On the scaling laws of dense wireless sensor networks: the data gathering channel. IEEE Trans. Inform. Theory 2005, 51, 1229–1234. [Google Scholar]
- Barros, J.; Servetto, S.D. Network information flow with correlated sources. IEEE Trans. Inform. Theory 2006, 52, 155–170. [Google Scholar]
- Shamai, S.; Verdù, S. Capacity of channels with uncoded side information. European Trans. Telecommun. 1995, 6, 587–600. [Google Scholar]
- Slepian, D.; Wolf, J.K. Noiseless coding of correlated information sources. IEEE Trans. Inform. Theory 1973, 19, 471–480. [Google Scholar]
- Aaron, A.; Girod, B. Compression with Side Information Using Turbo Codes. Proceedings of IEEE Data Compression Conference, Snowbird, UT, USA, April 2002; pp. 252–261.
- Bajcsy, J.; Mitran, P. Coding for the Slepian-Wolf Problem with Turbo Codes. Proceedings of IEEE Global Telecommun Conference, San Antonio, TX, USA, November 2001; 2, pp. 1400–1404.
- Deslauriers, I.; Bajcsy, J. Serial Turbo Coding for Data Compression and the Slepian-Wolf Problem. Proceedings of IEEE Information Theory Workshop, Paris, France, March 2003; pp. 296–299.
- Xiong, Z.; Liveris, A.D.; Cheng, S. Distributed source coding for sensor networks. IEEE Signal Processing Mag. 2004, 21, 80–94. [Google Scholar]
- Garcia-Frias, J.; Zhao, Y. Compression of correlated binary sources using turbo codes. IEEE Commun. Lett. 2001, 5, 417–419. [Google Scholar]
- Daneshgaran, F.; Laddomada, M.; Mondin, M. Iterative joint channel decoding of correlated sources employing serially concatenated convolutional codes. IEEE Trans. Inform. Theory 2005, 51, 2721–2731. [Google Scholar]
- Muramatsu, J.; Uyematsu, T.; Wadayama, T. Low-density parity-check matrices for coding of correlated sources. IEEE Trans. Inform. Theory 2005, 51, 3645–3654. [Google Scholar]
- Daneshgaran, F.; Laddomada, M.; Mondin, M. LDPC-based channel coding of correlated sources with iterative joint decoding. IEEE Trans. Commun. 2006, 54, 577–582. [Google Scholar]
- Garcia-Frias, J.; Zhao, Y.; Zhong, W. Turbo-like codes for transmission of correlated sources over noisy channels. IEEE Signal Processing Mag. 2007, 24, 58–66. [Google Scholar]
- Shannon, C.E. The zero-error capacity of a noisy channel. IRE Trans. Inform. Theory 1956, 2, 8–19. [Google Scholar]
- Gaarder, T.; Wolf, J.K. The capacity region of a multiple-access channel can increase with feedback. IEEE Trans. Inform. Theory 1975, 21, 100–102. [Google Scholar]
- Cover, T.M.; Leung, C.S.K. A rate region for the multiple access channel with feedback. IEEE Trans. Inform. Theory 1981, 27, 292–298. [Google Scholar]
- Murugan, A.D.; Gopala, P.K.; El-Gamal, H. Correlated sources over wireless channels: Cooperative source-channel coding. IEEE J. Select. Areas Commun. 2004, 22, 988–998. [Google Scholar]
- Ong, L.; Motani, M. Coding strategies for multiple-access channels with feedback and correlated sources. IEEE Trans. Inform. Theory 2007, 53, 3476–3497. [Google Scholar]
- Berger, T.; Zhen, Z.; Viswanathan, H. The CEO problem. IEEE Trans. Inform. Theory 1996, 42, 887–902. [Google Scholar]
- Zhao, Y.; Garcia-Frias, J. Joint estimation and compression of correlated nonbinary sources using punctured turbo codes. IEEE Trans. Commun. 2005, 53, 385–390. [Google Scholar]
- Papoulis, A. Probability, Random Variables and Stochastic Processes; McGraw-Hill: New York, NY, USA, 1991. [Google Scholar]
- Cover, T.M.; Thomas, J.A. Elements of Information Theory; John Wiley & Sons: New York, NY, USA, 1991. [Google Scholar]
- Abrardo, A.; Ferrari, G.; Martalò, M.; Franceschini, M.; Raheli, R. Optimizing Channel Coding for Orthogonal Multiple Access Schemes with Correlated Sources. Proceedings of Information Theory and Applications Workshop (ITA 2009), San Diego, CA, USA, February 2009.
- Boyd, S.; Vandenberghe, L. Convex Optimization; Cambridge University Press: Cambridge, UK, 2004. [Google Scholar]
- Abrardo, A.; Giambene, G.; Sennati, D. Optimization of power control parameters for DS-CDMA cellular systems. IEEE Trans. Commun. 2001, 49, 1415–1424. [Google Scholar]
- Kschischang, F.R.; Frey, B.J.; Loeliger, H.A. Factor graphs and the sum-product algorithm. IEEE Trans. Inform. Theory 2001, 47, 498–519. [Google Scholar]
- Bahl, L.R.; Cocke, J.; Jelinek, F.; Raviv, J. Optimal decoding of linear codes for minimizing symbol error rate. IEEE Trans. Inform. Theory 1974, 20, 284–287. [Google Scholar]
- Berrou, C.; Glavieux, A. Near optimum error correcting coding and decoding: turbo-codes. IEEE Trans. Commun. 1996, 44, 1261–1271. [Google Scholar]
- Barros, J.; Tuechler, M. Scalable decoding on factor trees: A practical solution for sensor networks. IEEE Trans. Commun. 2006, 54, 284–294. [Google Scholar]
- Abrardo, A. Performance bounds and codes design criteria for channel decoding with a-priori information. IEEE Trans. Wireless Commun. 2009, 8, 608–612. [Google Scholar]
- Hu, X.; Eleftheriou, E.; Arnold, D. Regular and irregular progressive edge-growth tanner graphs. IEEE Trans. Inform. Theory 2005, 51, 386–398. [Google Scholar]
- Benedetto, S.; Divsalar, D.; Montorsi, G.; Pollara, F. Serial concatenation of interleaved codes: performance analysis, design, and iterative decoding. IEEE Trans. Inform. Theory 1998, 44, 909–926. [Google Scholar]
- Viterbi, A.J. Principles of Spread Spectrum Communications; Addison-Wesley: Boston, MA, USA, 1995. [Google Scholar]
- Varshney, P.K. Distributed Detection and Data Fusion; Springer-Verlag: New York, NY, USA, 1997. [Google Scholar]







| γk [dB] | ΔEc,k [dB] | Binary Feedback Command |
|---|---|---|
| −ΔEmax | ||
| … | … | … |
| −2ΔEstep | -1-1 | |
| −ΔEstep | -1 | |
| ΔEstep | +1 | |
| +2ΔEstep | +1+1 | |
| … | … | … |
| +ΔEmax | ||
Notes
- 1.For the sake of notational simplicity, the derivation is carried out considering a single packet transmission act, i.e., we do not use any index to indicate the specific packet.
- 2.Note that, for a fixed symbol duration (i.e., transmitting rate), a power variation is in a one-to-one correspondence with an energy variation.
- 3.Note that the internal iterations in each component subdecoder refer to (i) the iterations between the variable nodes and the check nodes in the presence of LDPC coding and the SP algorithm or (ii) the turbo iterations between convolutional decoders in the presence of turbo coding and the BCJR algorithm (at each convolutional decoder).
- 4.Since the a priori probabilities need to be evaluated for the systematic bits, in this case and, therefore, . The joint PMF of can then be obtained directly from (1). Note that equation (24) is an approximation since, heuristically, the first probability in the summation at the right-hand side is obtained from the reliability values generated by the other decoder, whereas the second probability is a priori.
- 5.Note that the number of internal iterations is fixed with SCCCing, whereas it can vary in the LDPC coded case. Note also that the number of external iterations between the component decoders differs between the cases with LDPC codes and SCCC. This is due to the different convergence characteristics of the iterative decoders associated with these channels codes.
- 6.Note that the exact statistics of the residual multiple access interference should be better investigated. This goes beyond the scope of this paper. However, the Gaussian approximation allows to have useful insights on the impact of the multiple access interference on the proposed feedback power control strategies.
© 2009 by the authors; licensee Molecular Diversity Preservation International, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/3.0/).
Share and Cite
Abrardo, A.; Ferrari, G.; Martalò, M.; Perna, F. Feedback Power Control Strategies inWireless Sensor Networks with Joint Channel Decoding. Sensors 2009, 9, 8776-8809. https://doi.org/10.3390/s91108776
Abrardo A, Ferrari G, Martalò M, Perna F. Feedback Power Control Strategies inWireless Sensor Networks with Joint Channel Decoding. Sensors. 2009; 9(11):8776-8809. https://doi.org/10.3390/s91108776
Chicago/Turabian StyleAbrardo, Andrea, Gianluigi Ferrari, Marco Martalò, and Fabio Perna. 2009. "Feedback Power Control Strategies inWireless Sensor Networks with Joint Channel Decoding" Sensors 9, no. 11: 8776-8809. https://doi.org/10.3390/s91108776