An Interactive Real-Time Locating System Based on Bluetooth Low-Energy Beacon Network †
Abstract
:1. Introduction
- We combine the broadcast and mesh topology options of Bluetooth to extend the applicability of beacon solutions. Smartphone users are able to interact with the backend system with a single and pervasive network technology—Bluetooth.
- The user experience of Bluetooth beacon-based applications is enhanced because our system can work without smartphone users’ Internet connections. In other words, smartphone users only need to turn on the Bluetooth interface to enjoy the interactive locating services without paying a dime on their phone bills.
- We implemented a real-time locating system solely based on Bluetooth. The feasibility and usefulness of our work have been verified through extensive experiments.
- We identify some potential problems of deploying the Bluetooth locating system, and propose possible solutions to solve/mitigate the problems.
2. Related Work
2.1. Locating Systems and Applications Based on Bluetooth Low Energy (BLE)
2.2. Implementations of Bluetooth Mesh Networking
2.3. Bluetooth Beacon Technology
3. System Design
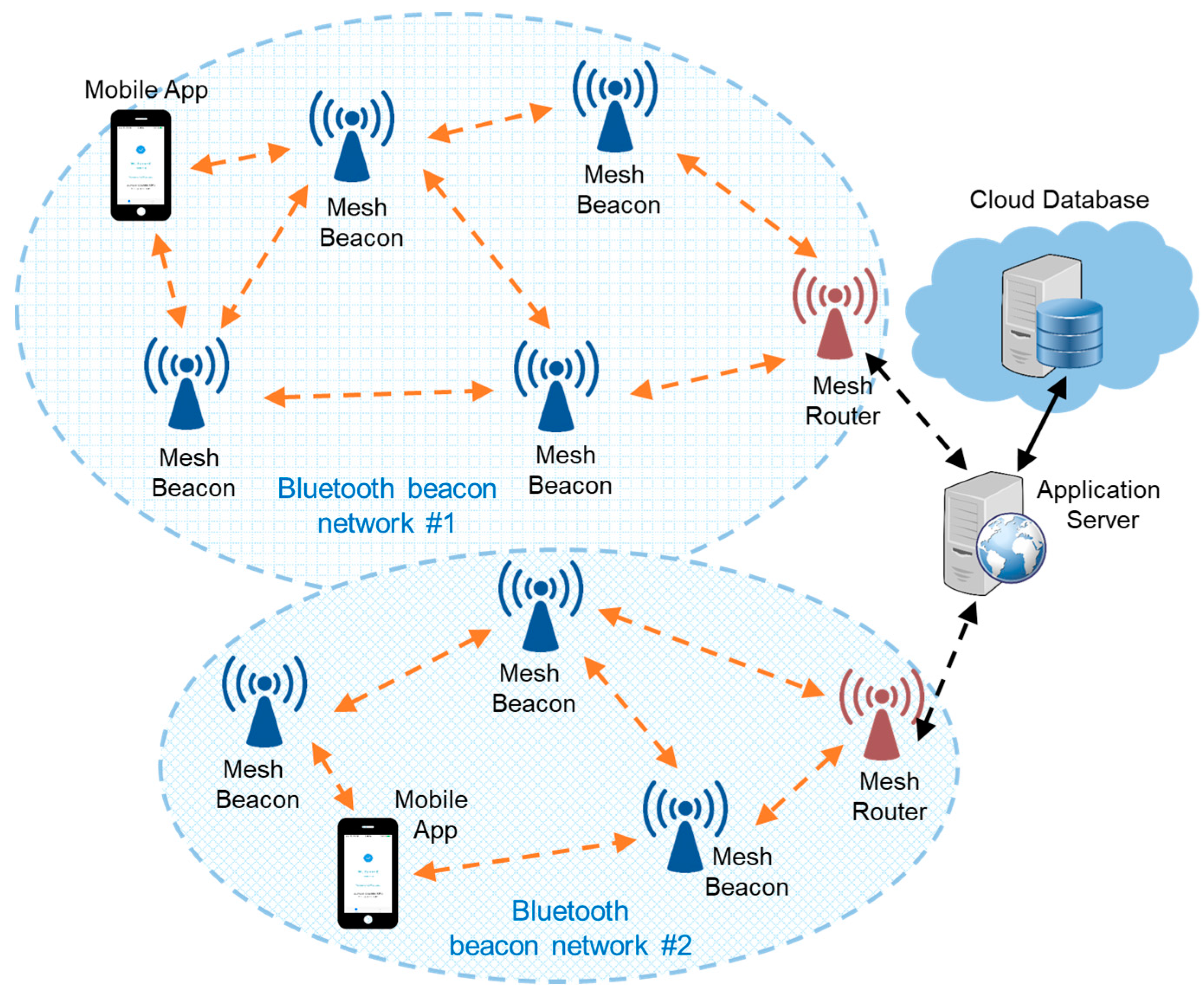
3.1. System Architecture
- Mobile App: a locating application running on mobile users’ smartphones. It listens to the beacon messages sent by the Mesh Beacons to figure out the current location of the mobile user. It responds to the received beacon message by broadcasting the mobile user’s encrypted presence message.
- Mesh Beacon: a beacon device that can send, receive, and relay messages in the Bluetooth beacon network. Specifically, it not only broadcasts beacon messages, but also receives presence message from Mobile Apps, and relays the presence message to the Application Server.
- Mesh Router: a gateway device between the Bluetooth beacon network and the rest of the network. It is responsible for collecting the presence messages from the Mobile Apps within the range of the Bluetooth beacon network. Once the Mesh Router receives a presence message, it will upload the presence state to the Application Server through hypertext transfer protocol (HTTP), and send an acknowledgement message back to the Mobile App in response to receiving the presence message from a specific user.
- Application Server: a shared HTTP server for the Mesh Routers from several Bluetooth beacon networks. It buffers the presence states of the mobile users, and forwards the presence states to the Cloud Database.
- Cloud Database: a real-time database in the cloud environment. It is responsible for keeping the history records of all the mobile users’ presence states.
3.2. Flow of Operations
- When the Mobile App discovers a beacon message from a certain Mesh Beacon, it locates itself based on the Major/Minor values embedded in the message. In our design, the Mobile App directly looks up a built-in location table to resolve the Major/Minor values, so the name of the detected location can be shown on the user interface immediately.
- Once the locating process has completed, the Mobile App composes the presence message containing the encrypted user ID and the detected Major/Minor values, and then broadcasts the presence message. The objective of broadcasting the presence message is to inform the backend system that this specific user has shown up at a particular location.
- As soon as any Mesh Beacon hears the presence message, it uses the managed-flood-based approach to rebroadcast the presence message. The purpose of rebroadcasting the presence message is to relay it to the Mesh Router. The managed-flood-based approach can make sure that once a specific presence message has been broadcasted by a Mesh Beacon, the Mesh Beacon will not rebroadcast it again.
- When the Mesh Router hears the presence message originated from a certain Mobile App, it uploads the content in the presence message to the Application Server. Meanwhile, it sends an acknowledgement message back to the Mobile App by broadcast.
- When any Mesh Beacon hears the acknowledgement message, it rebroadcasts the message by using the managed-flood-based approach again. The purpose of rebroadcasting the acknowledgement message is to relay it to the Mobile App.
- (Continue from item 4) When the Application Server receives the presence state from the Mesh Router, it forwards the presence state to the Cloud Database. In the Cloud Database we are able to see the locating history for all the mobile users.
- When the acknowledgement message from the Mesh Router has been received at the Mobile App, the Mobile App displays a welcome message indicating that the backend system is aware of the user’s presence.
3.3. Messages in the Beacon Network
- Type 1: beacon messages sent by the Mesh Beacons
- Type 2: presence messages sent by the Mobile Apps
- Type 3: presence messages forwarded by the Mesh Beacons
- Type 4: acknowledgement messages sent by the Mesh Router.
4. Implementation and Experiments
4.1. Implementation and Deployment of Our Prototype System
4.2. Experiment 1
4.3. Experiment 2
4.4. Experiment 3
4.5. Discussions
4.5.1. The Communication Range of Bluetooth Beacons
4.5.2. Contention on Advertising Channels and Interference from Wi-Fi
4.5.3. Problems Related to a Large Deployment Area
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Middleton, P.; Tsai, T.; Yamaji, M.; Gupta, A.; Rueb, D. Forecast: Internet of Things–Endpoints and Associated Services, Worldwide. 2017. Available online: https://www.gartner.com/doc/3840665/forecast-internet-things--endpoints (accessed on 5 May 2018).
- Zigbee Alliance. Available online: http://www.zigbee.org/ (accessed on 5 May 2018).
- Bluetooth Low Energy. Available online: https://www.bluetooth.com/what-is-bluetooth-technology/how-it-works/low-energy (accessed on 5 May 2018).
- Wi-Fi HaLow. Available online: http://www.wi-fi.org/discover-wi-fi/wi-fi-halow (accessed on 5 May 2018).
- LoRa Alliance. Available online: https://www.lora-alliance.org/ (accessed on 5 May 2018).
- Olteanu, A.C.; Oprina, G.D.; Tapus, N.; Zeisberg, S. Enabling mobile devices for home automation using Zigbee. In Proceedings of the 19th International Conference on Control Systems and Computer Science, Bucharest, Romania, 29–31 May 2013; pp. 189–195. [Google Scholar]
- Vivek, G.V.; Sunil, M.P. Enabling IoT services using WiFi-Zigbee gateway for a home automation system. In Proceedings of the 2015 IEEE International Conference on Research in Computational Intelligence and Communication Networks (ICRCICN), Kolkata, India, 20–22 November 2015; pp. 77–80. [Google Scholar]
- Shim, J.-S.; Kim, H.-J.; Lee, N.-U.; Park, S.-C. Design of Zigbee-BLE gateway direct communication system for smart home environment. In Advances in Computer Science and Ubiquitous Computing (CSA-CUTE 17); Park, J.J., Loia, V., Yi, G., Sung, Y., Eds.; Springer: Singapore, 2018; pp. 1428–1433. [Google Scholar]
- DeCuir, J. Introducing Bluetooth smart: Part 1: A look at both classic and new technologies. IEEE Consum. Electron. Mag. 2014, 3, 12–18. [Google Scholar] [CrossRef]
- Dementyev, A.; Hodges, S.; Taylor, S.; Smith, J. Power consumption analysis of Bluetooth low energy, Zigbee and ANT sensor nodes in a cyclic sleep scenario. In Proceedings of the 2013 IEEE International Wireless Symposium (IWS), Beijing, China, 14–18 April 2013; pp. 1–4. [Google Scholar]
- Siekkinen, M.; Hiienkari, M.; Nurminen, J.K.; Nieminen, J. How low energy is Bluetooth low energy? Comparative measurements with Zigbee/802.15.4. In Proceedings of the 2012 IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Paris, France, 1 April 2012; pp. 232–237. [Google Scholar]
- Apple iBeacon. Available online: https://developer.apple.com/ibeacon/ (accessed on 5 May 2018).
- Filippoupolitis, A.; Oliff, W.; Loukas, G. Occupancy detection for building emergency management using BLE beacons. In 31st International Symposium on Computer and Information Sciences (ISCIS 2016), Kraków, Poland, 27–28 October 2016; Czachórski, T., Gelenbe, E., Grochla, K., Lent, R., Eds.; Springer: Cham, Switzerland, 2016; pp. 233–240. [Google Scholar]
- Lin, X.Y.; Ho, T.W.; Fang, C.C.; Yen, Z.S.; Yang, B.J.; Lai, F. A mobile indoor positioning system based on iBeacon technology. In Proceedings of the 2015 37th Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC), Milan, Italy, 25–29 August 2015; pp. 4970–4973. [Google Scholar]
- Zhao, Z.; Fang, J.; Huang, G.Q.; Zhang, M. iBeacon enabled indoor positioning for warehouse management. In Proceedings of the 2016 4th International Symposium on Computational and Business Intelligence (ISCBI), Olten, Switzerland, 5–7 September 2016; pp. 21–26. [Google Scholar]
- Faragher, R.; Harle, R. Location fingerprinting with Bluetooth low energy beacons. IEEE J. Sel. Areas Commun. 2015, 33, 2418–2428. [Google Scholar] [CrossRef]
- Onofre, S.; Caseiro, B.; Pimentão, J.P.; Sousa, P. Using fuzzy logic to improve BLE indoor positioning system. In 7th IFIP WG 5.5/SOCOLNET Advanced Doctoral Conference on Computing, Electrical and Industrial Systems (DoCEIS); Springer: Costa de Caparica, Portugal, 2016; pp. 169–177. [Google Scholar]
- Fard, H.K.; Chen, Y.; Son, K.K. Indoor positioning of mobile devices with agile iBeacon deployment. In Proceedings of the 2015 IEEE 28th Canadian Conference on Electrical and Computer Engineering (CCECE), Halifax, NS, Canada, 3–6 May 2015; pp. 275–279. [Google Scholar]
- Wu, X.; Shen, R.; Fu, L.; Tian, X.; Liu, P.; Wang, X. iBILL: Using iBeacon and Inertial Sensors for Accurate Indoor Localization in Large Open Areas. IEEE Access 2017, 5, 14589–14599. [Google Scholar] [CrossRef]
- Martin, P.; Ho, B.J.; Grupen, N.; Muñoz, S.; Srivastasa, M. Demo Abstract: An iBeacon Primer for Indoor Localization. In Proceedings of the 1st ACM Conference on Embedded Systems for Energy-Efficient Buildings (BuildSys’14), Memphis, TN, USA, 3–6 November 2014; pp. 190–191. [Google Scholar]
- He, S.; Hu, T.; Chan, S.-H.G. Contour-based Trilateration for Indoor Fingerprinting Localization. In Proceedings of the 13th ACM Conference on Embedded Networked Sensor Systems (SenSys’15), Seoul, Korea, 1–4 November 2015; pp. 225–238. [Google Scholar]
- Mesh Networking Specifications. Available online: https://www.bluetooth.com/specifications/mesh-specifications (accessed on 5 May 2018).
- Qualcomm. CSRmesh(r) Development Kit. Available online: http://www.csr.com/tw/node/4684 (accessed on 5 May 2018).
- Zenker, P.; Krug, S.; Binhack, M.; Seitz, J. Evaluation of BLE Mesh Capabilities: A Case Study Based on CSRmesh. In Proceedings of the 2016 Eighth International Conference on Ubiquitous and Future Networks (ICUFN), Vienna, Austria, 5–8 July 2016; pp. 790–795. [Google Scholar]
- nRF OpenMesh. Available online: https://github.com/NordicPlayground/nRF51-ble-bcast-mesh (accessed on 5 May 2018).
- Levis, P.; Clausen, T.; Hui, J.; Gnawali, O.; Ko, J. RFC 6206: The Trickle Algorithm. Available online: https://tools.ietf.org/html/rfc6206 (accessed on 5 May 2018).
- Kim, H.-S.; Lee, J.; Jang, J.W. BLEmesh: A wireless mesh network protocol for Bluetooth low energy devices. In Proceedings of the 2015 3rd International Conference on Future Internet of Things and Cloud (FiCloud), Rome, Italy, 24–26 August 2015; pp. 558–563. [Google Scholar]
- Eddystone. Available online: https://developers.google.com/beacons/eddystone (accessed on 11 May 2018).
- AltBeacon. Available online: http://altbeacon.org/ (accessed on 11 May 2018).
- The Physical Web. Available online: https://google.github.io/physical-web/ (accessed on 12 May 2018).
- Bluetooth Topology Options. Available online: https://www.bluetooth.com/bluetooth-technology/topology-options (accessed on 5 May 2018).
- Bluetooth Core Specification Version 4.1. Available online: https://www.bluetooth.com/specifications/bluetooth-core-specification/legacy-specifications (accessed on 11 May 2018).
- Redbear Duo. Available online: https://redbear.cc/duo/ (accessed on 5 May 2018).
- Google Firebase. Available online: https://firebase.google.com/ (accessed on 5 May 2018).
- Sponås, J.G. Things You Should Know about Bluetooth Range. Available online: https://blog.nordicsemi.com/getconnected/things-you-should-know-about-bluetooth-range (accessed on 5 May 2018).
- Bluetooth Core Specification Version 5.0. Available online: https://www.bluetooth.com/specifications/bluetooth-core-specification (accessed on 11 May 2018).
- Darroudi, S.M.; Gomez, C. Bluetooth low energy mesh networks: A survey. Sensors 2017, 17, 1467. [Google Scholar] [CrossRef] [PubMed]











| Item | Technology |
|---|---|
| Mobile App | Apple iOS version 10.2 |
| Mesh Beacon and Mesh Router | RedBear Duo development board (with Bluetooth V4.1 and IEEE 802.11n Wi-Fi) |
| Application Server | Node.js web server on Linux Ubuntu 14.04 |
| Cloud Database | Google Firebase |
| Locations | Timestamp of the Locating Record | |
|---|---|---|
| User 1 | User 2 | |
| B | 17:14:18 | 17:14:18 |
| C | 17:14:37 | 17:14:36 |
| D | 17:14:56 | 17:14:58 |
| C | 17:15:24 | 17:15:27 |
| B | 17:15:39 | 17:15:40 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lin, Y.-W.; Lin, C.-Y. An Interactive Real-Time Locating System Based on Bluetooth Low-Energy Beacon Network †. Sensors 2018, 18, 1637. https://doi.org/10.3390/s18051637
Lin Y-W, Lin C-Y. An Interactive Real-Time Locating System Based on Bluetooth Low-Energy Beacon Network †. Sensors. 2018; 18(5):1637. https://doi.org/10.3390/s18051637
Chicago/Turabian StyleLin, You-Wei, and Chi-Yi Lin. 2018. "An Interactive Real-Time Locating System Based on Bluetooth Low-Energy Beacon Network †" Sensors 18, no. 5: 1637. https://doi.org/10.3390/s18051637





