Throughput Analysis on 3-Dimensional Underwater Acoustic Network with One-Hop Mobile Relay
Abstract
:1. Introduction
2. Related Work
3. Analysis of One-Hop Transmission
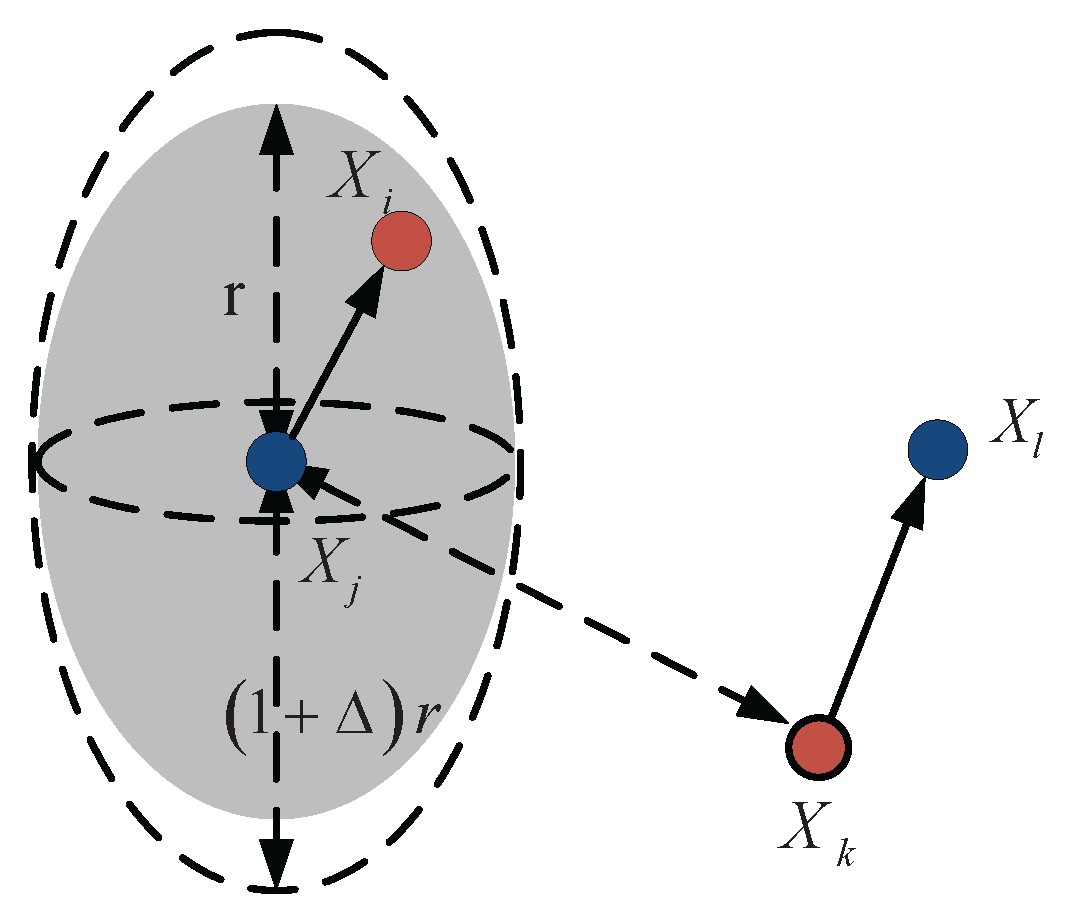
3.1. Delivery Rate of One-Hop Transmission
- (1)
- The distance between and is not larger than r:
- (2)
- For all other nodes simultaneously transmitting at the same time over the same channel,where is the subset of source nodes simultaneously transmitting over the same channel. The quantity models situations where a guard zone is specified by the protocol to prevent a neighboring node from transmitting on the same sub-channel at the same time.
3.2. Optimal Range of One-Hop Transmission
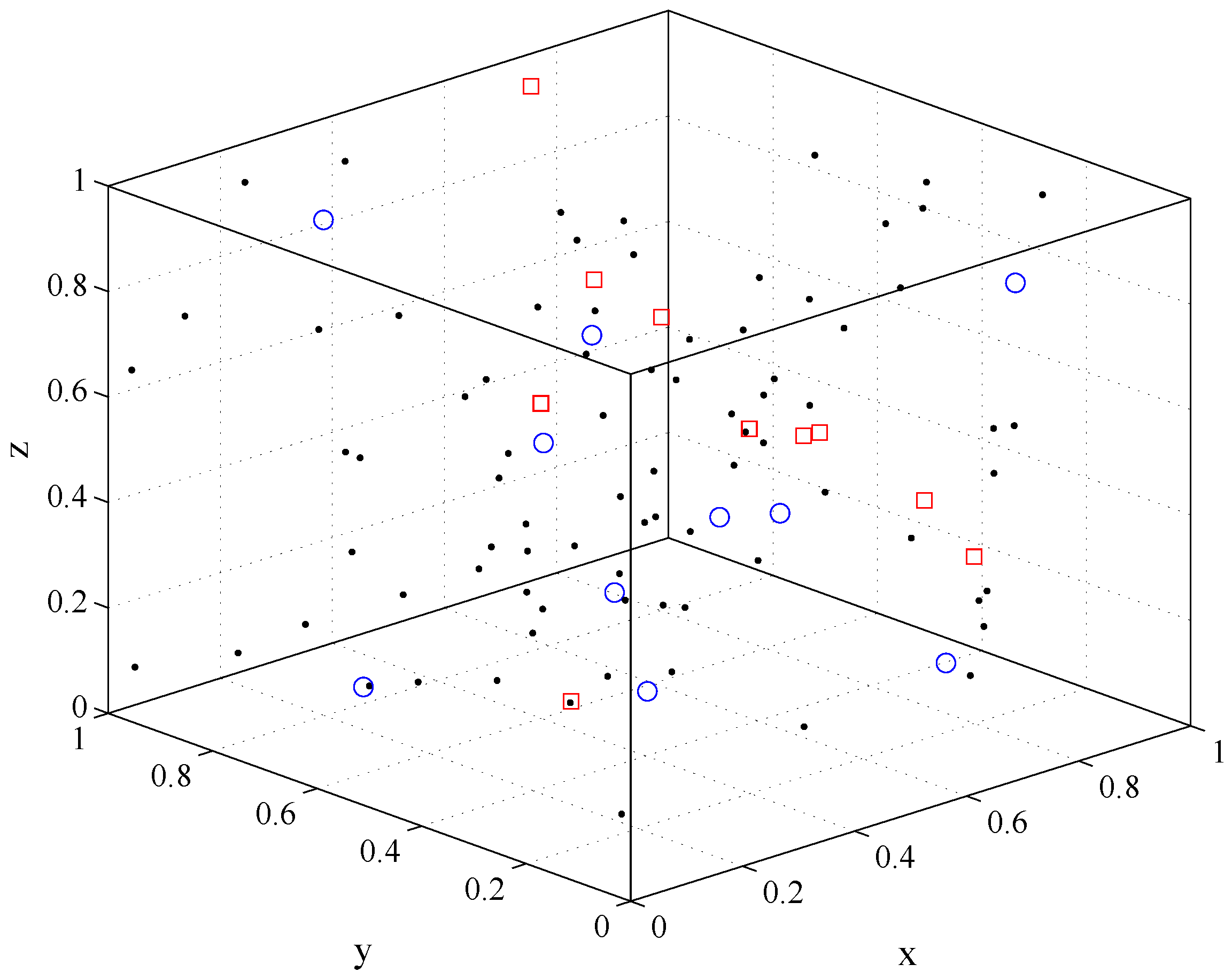
3.3. Simulation of One-Hop Transmission
4. Transmission Strategy Based on Mobile Relay
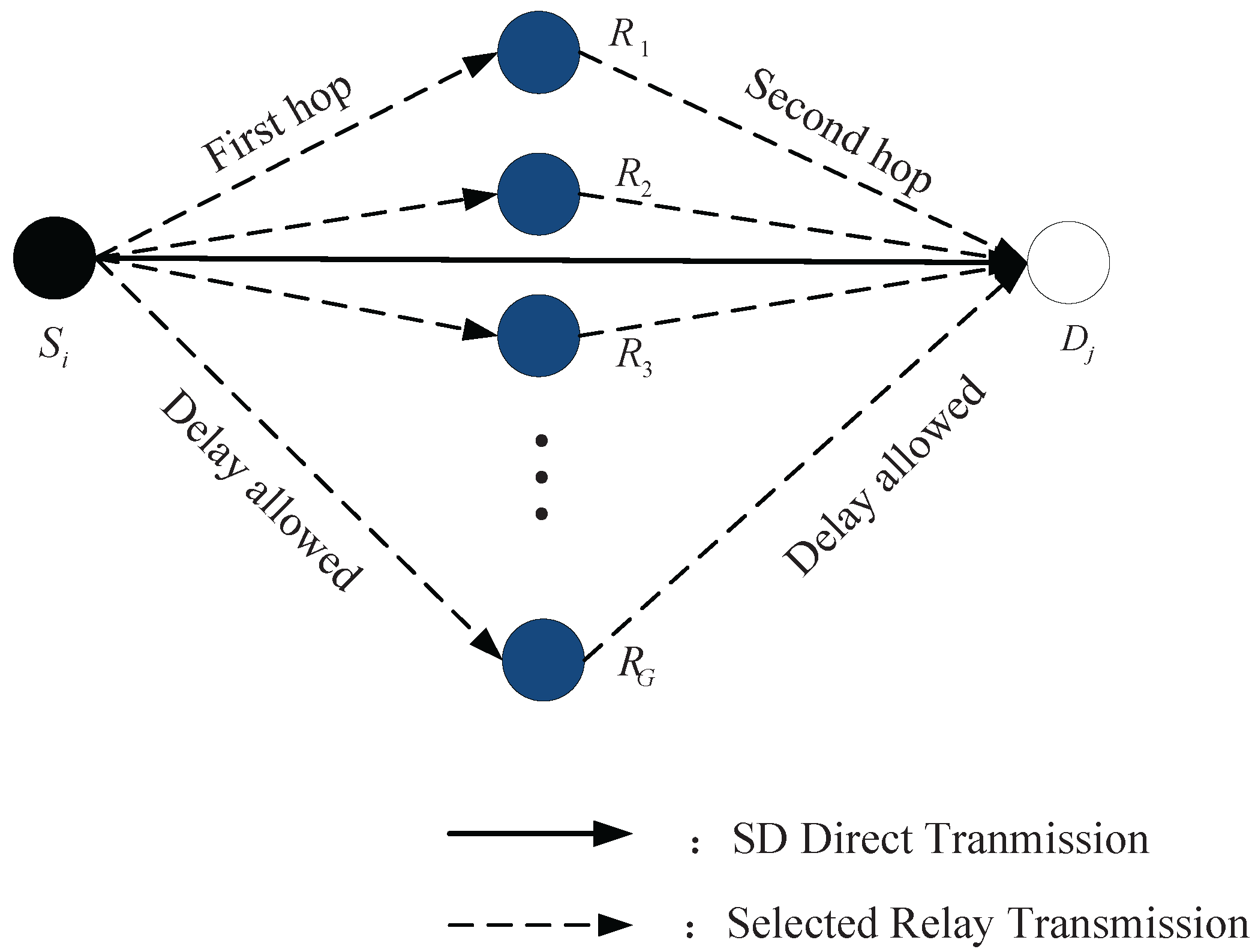
4.1. The One-Hop Mobile Relay Strategy
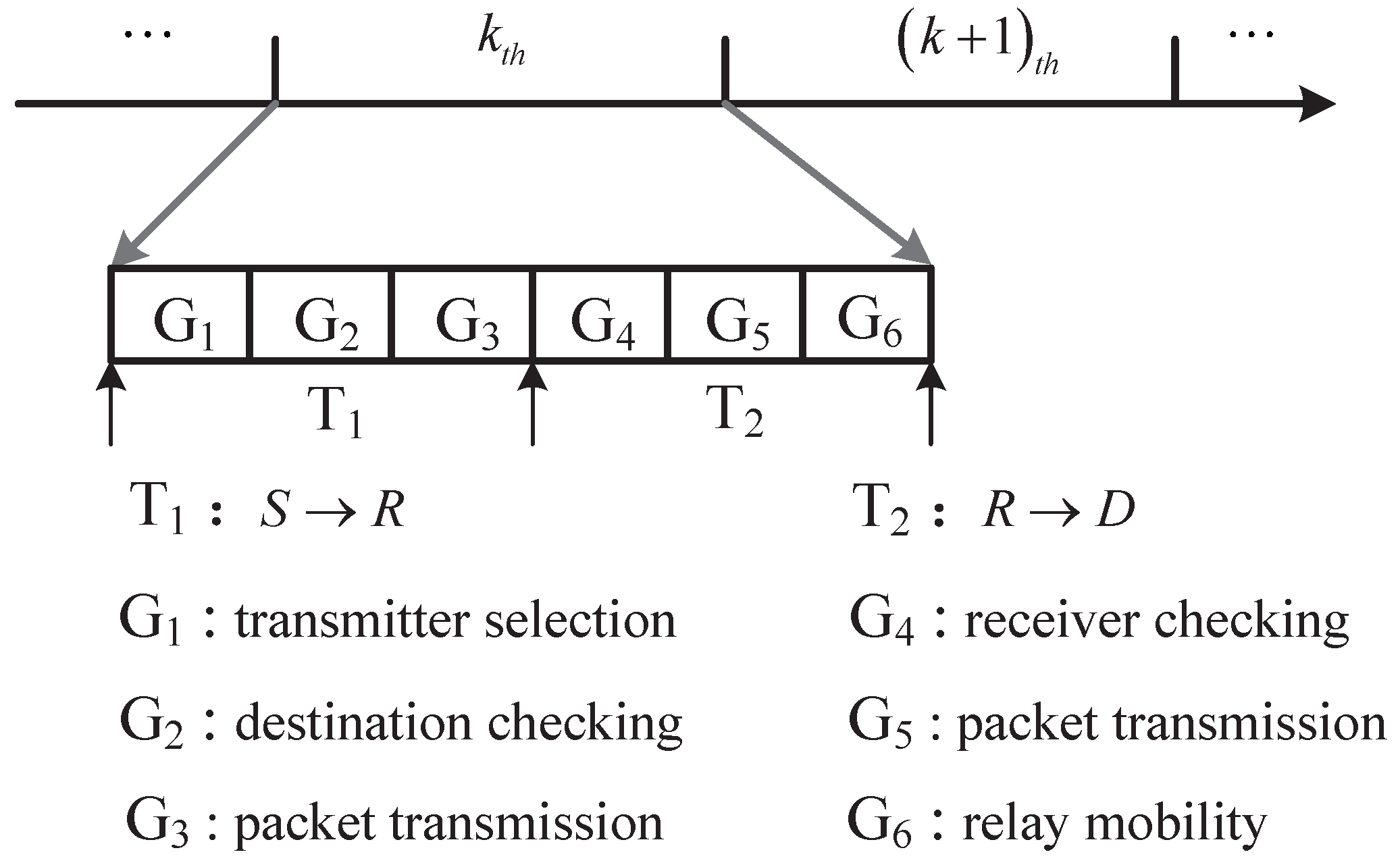
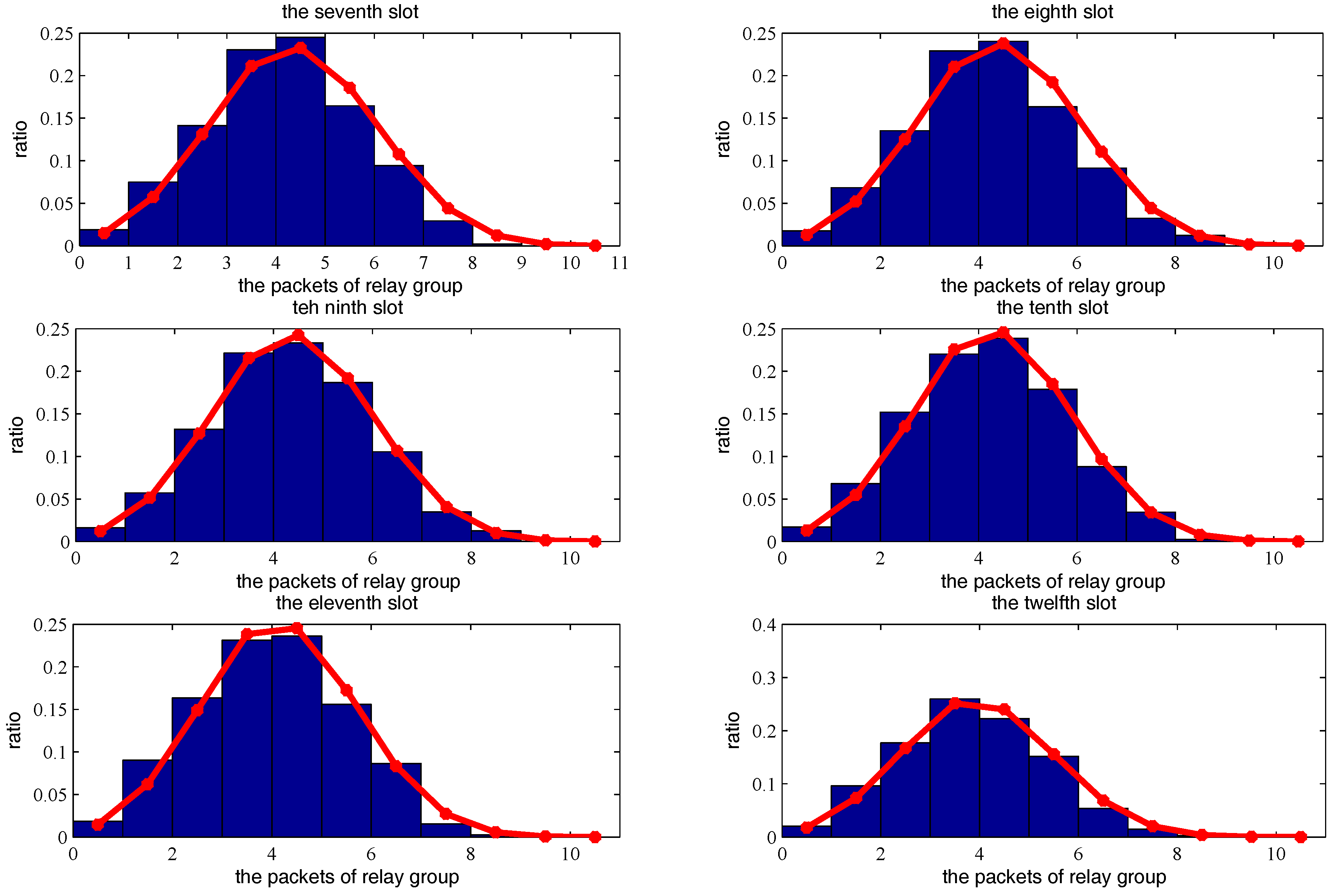
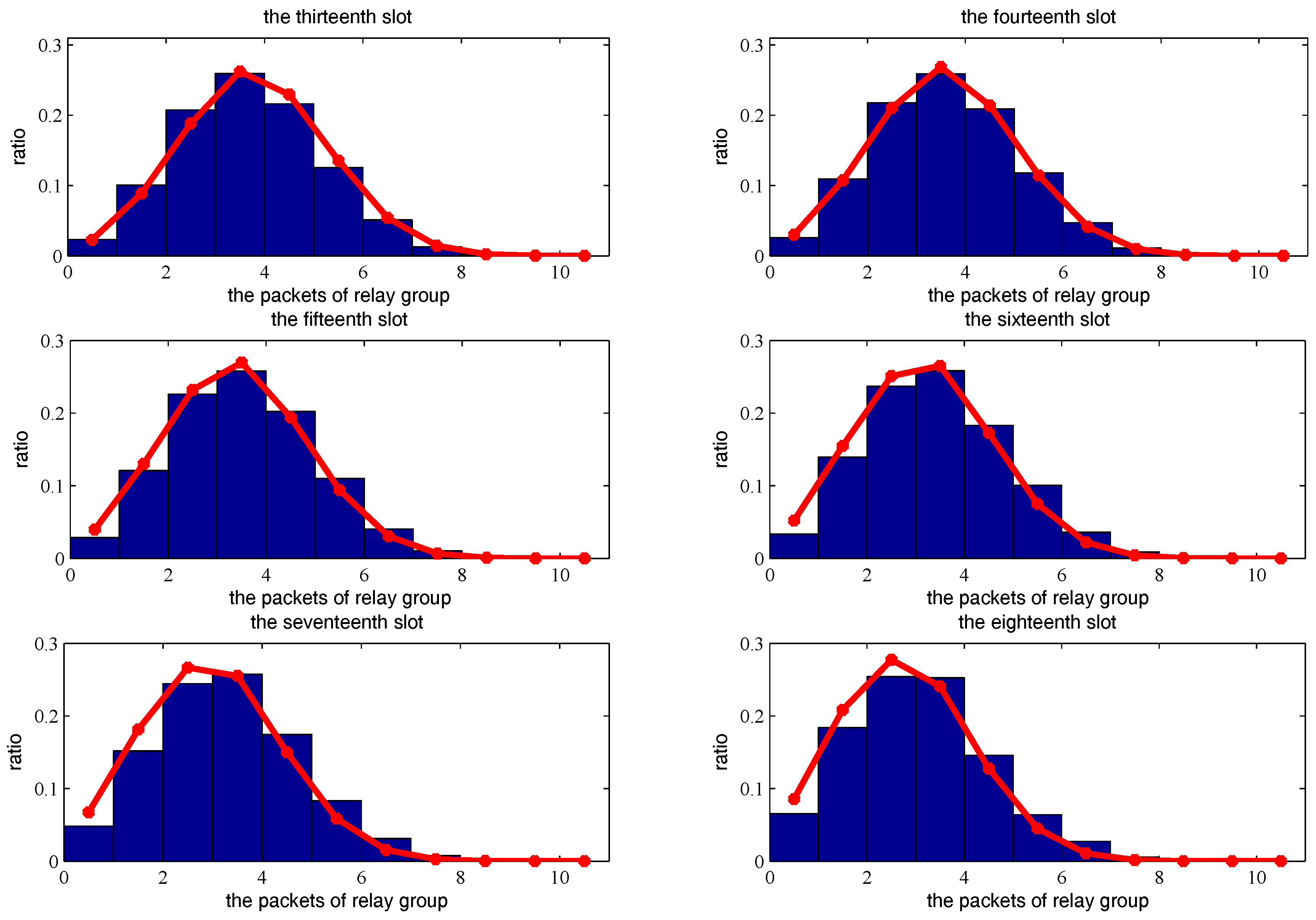
4.2. Partition of a Time Slot
5. Theoretical Analysis of Network Throughput Based on Two-Hop Transmission Strategy
5.1. Throughput Analysis of One Transmission Pair
- : The probability that the source packet is directly transmitted to the destination.
- : The probability that the data packet is successfully transmitted from the sender to the relay.
- : The probability that the data packet is successfully transmitted from the relay to the receiver.
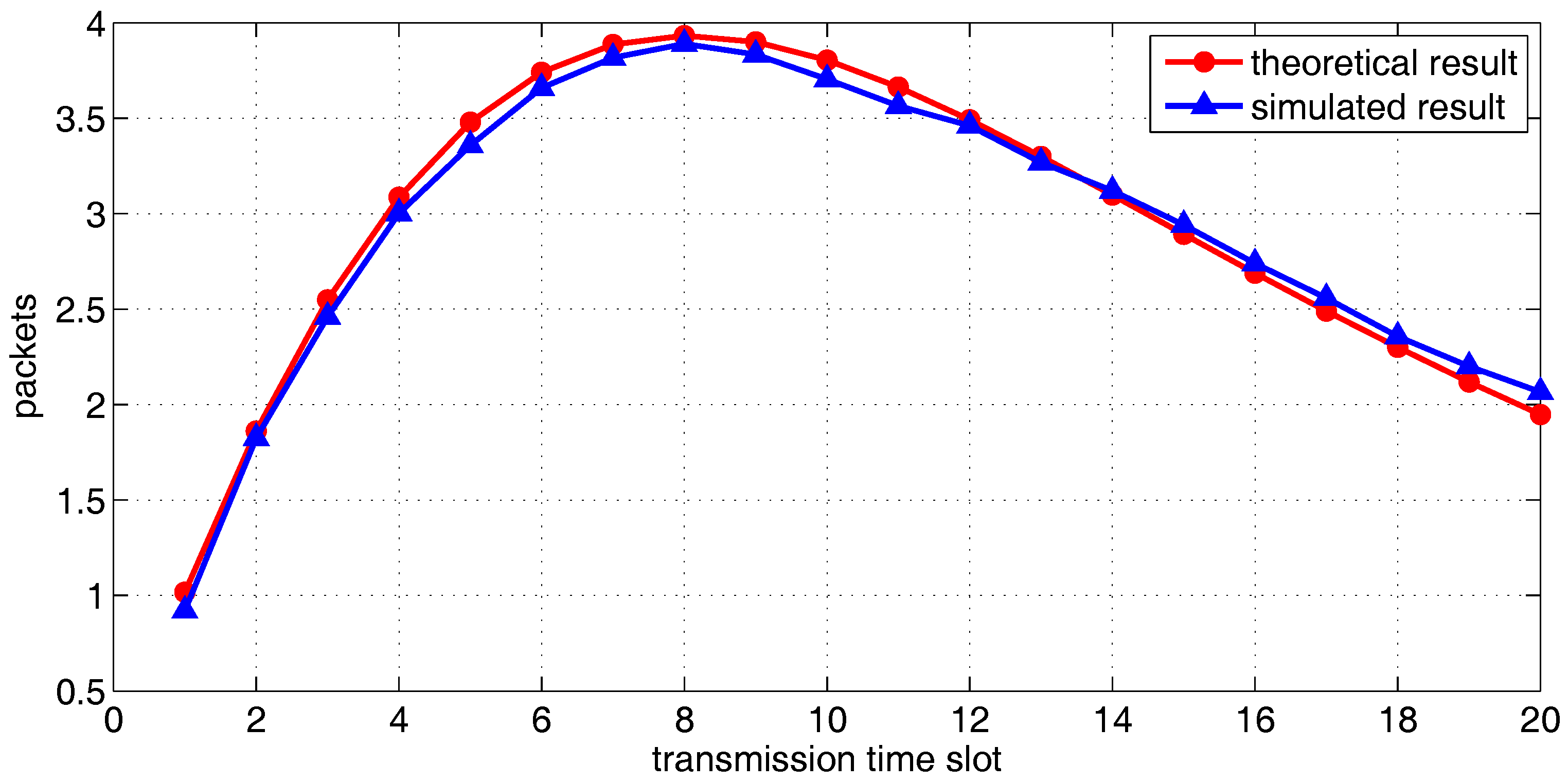
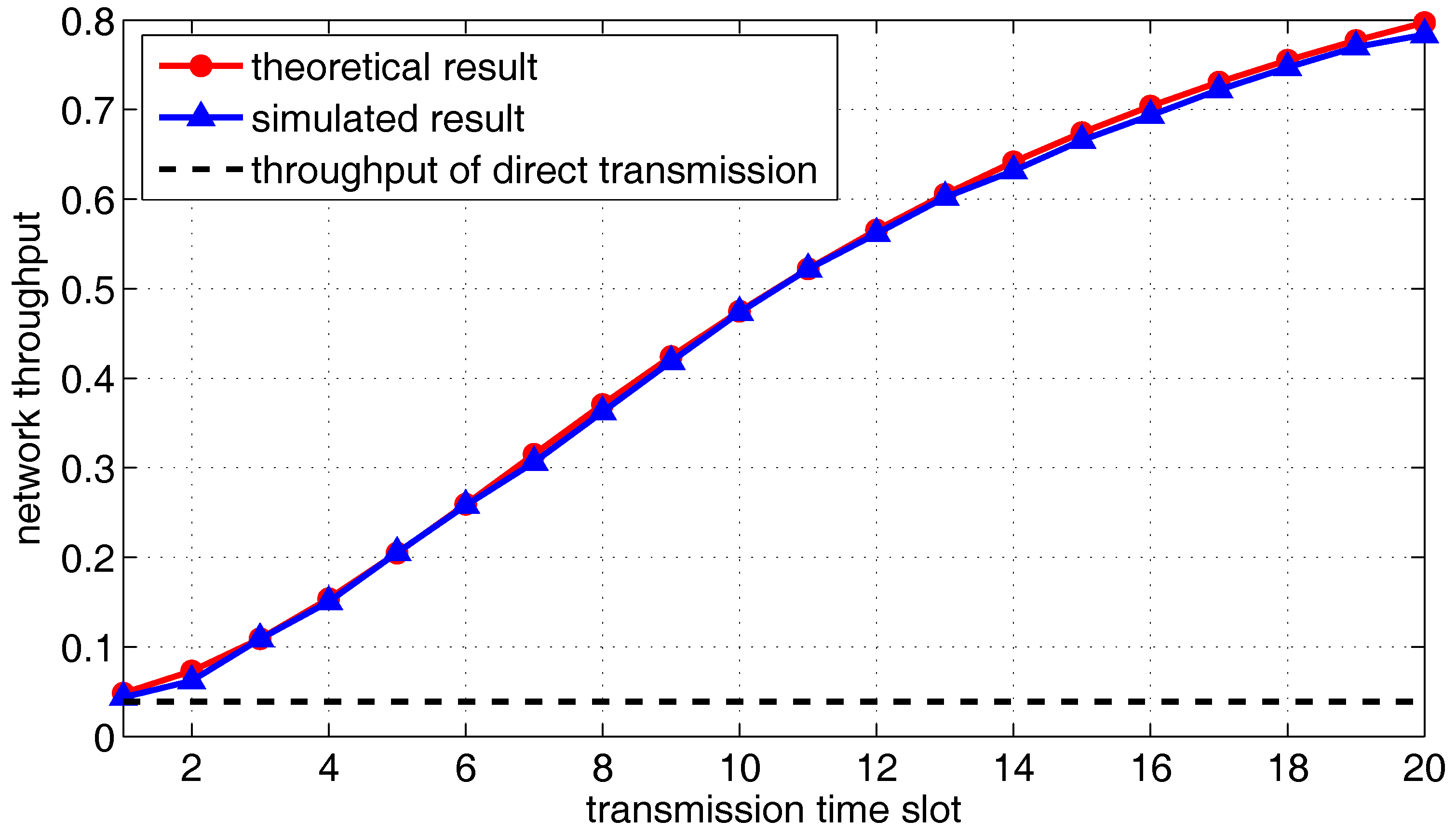
5.2. Throughput Analysis of Multiple Transmission Pairs
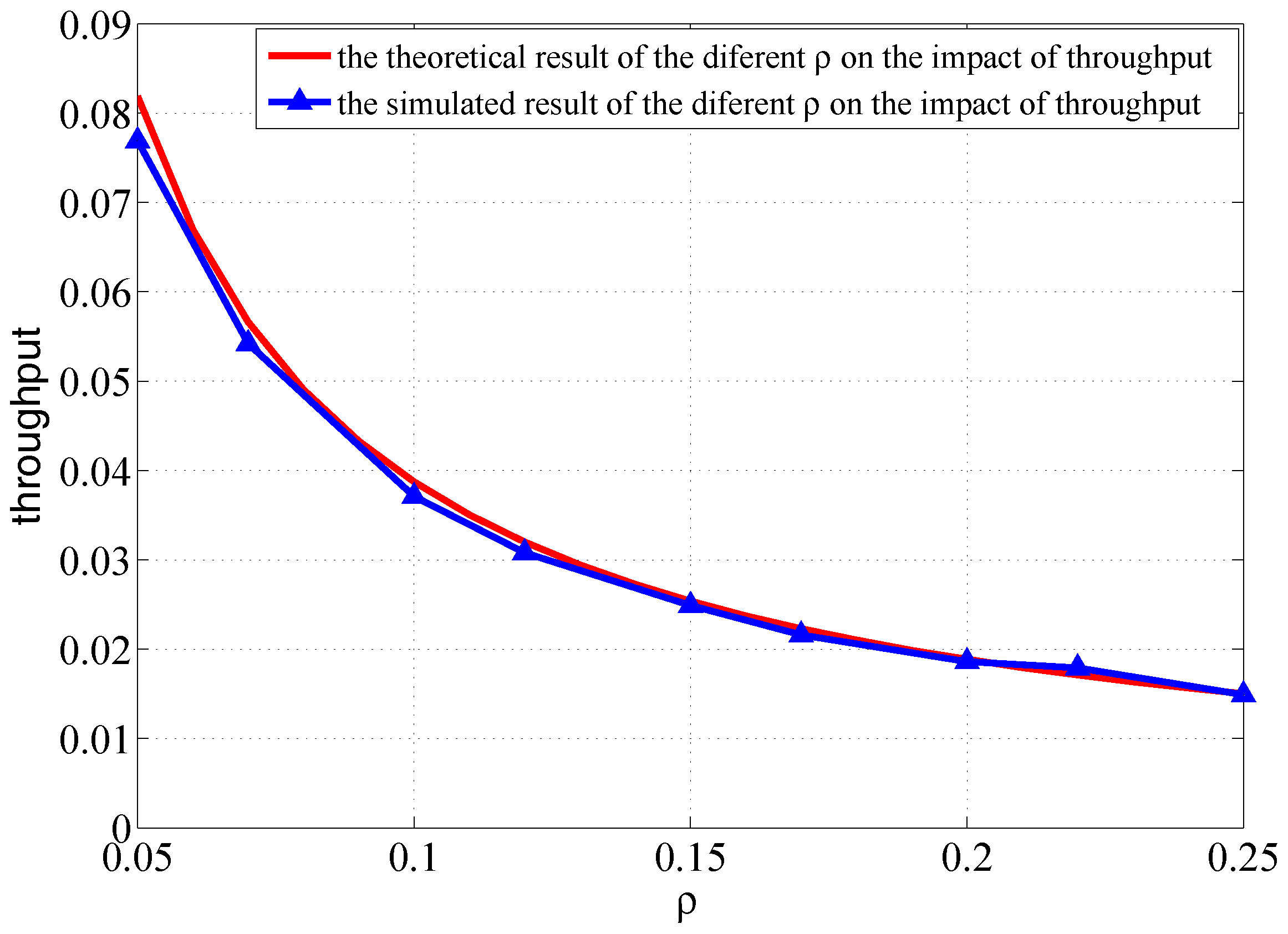
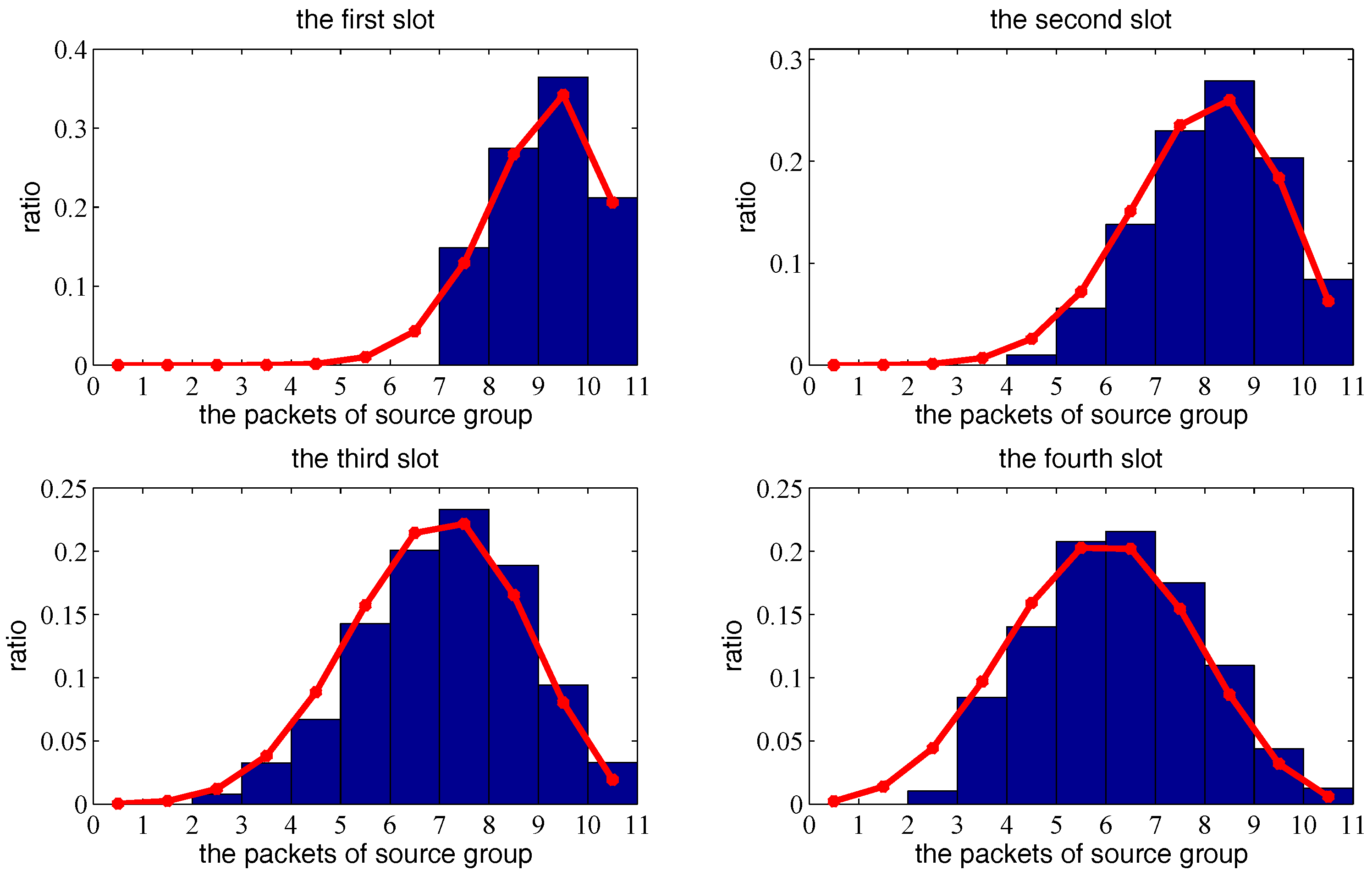
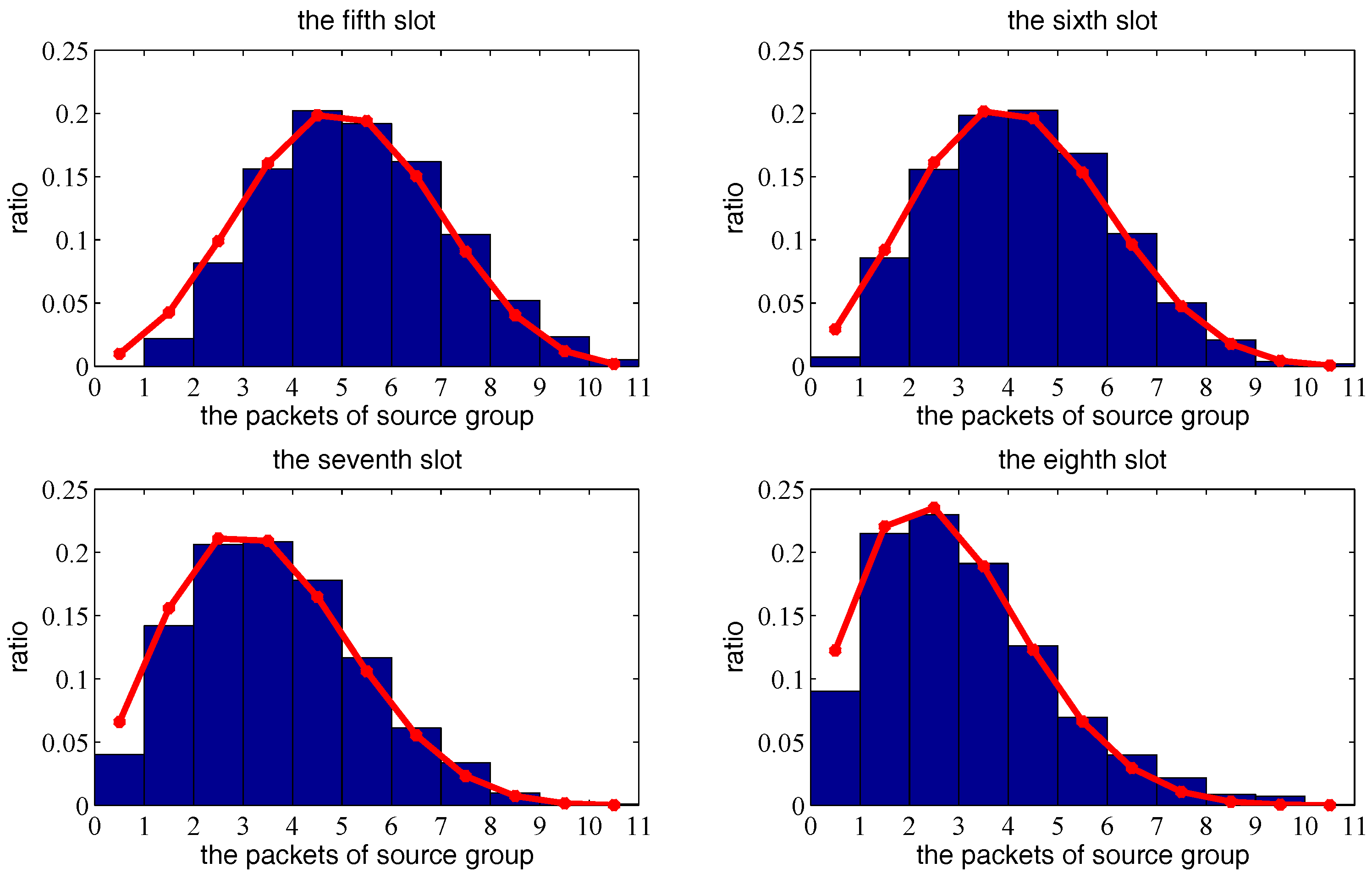
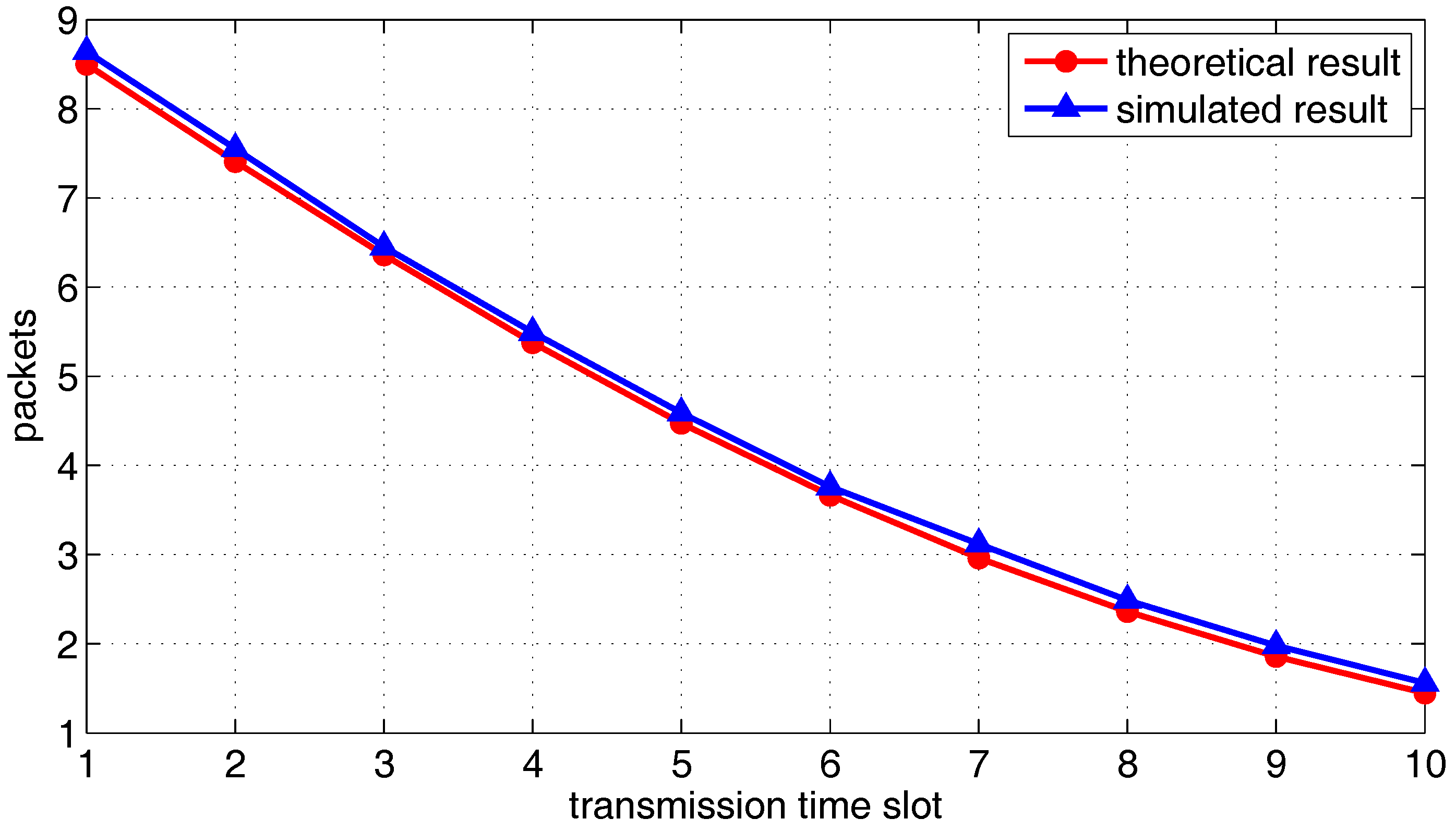
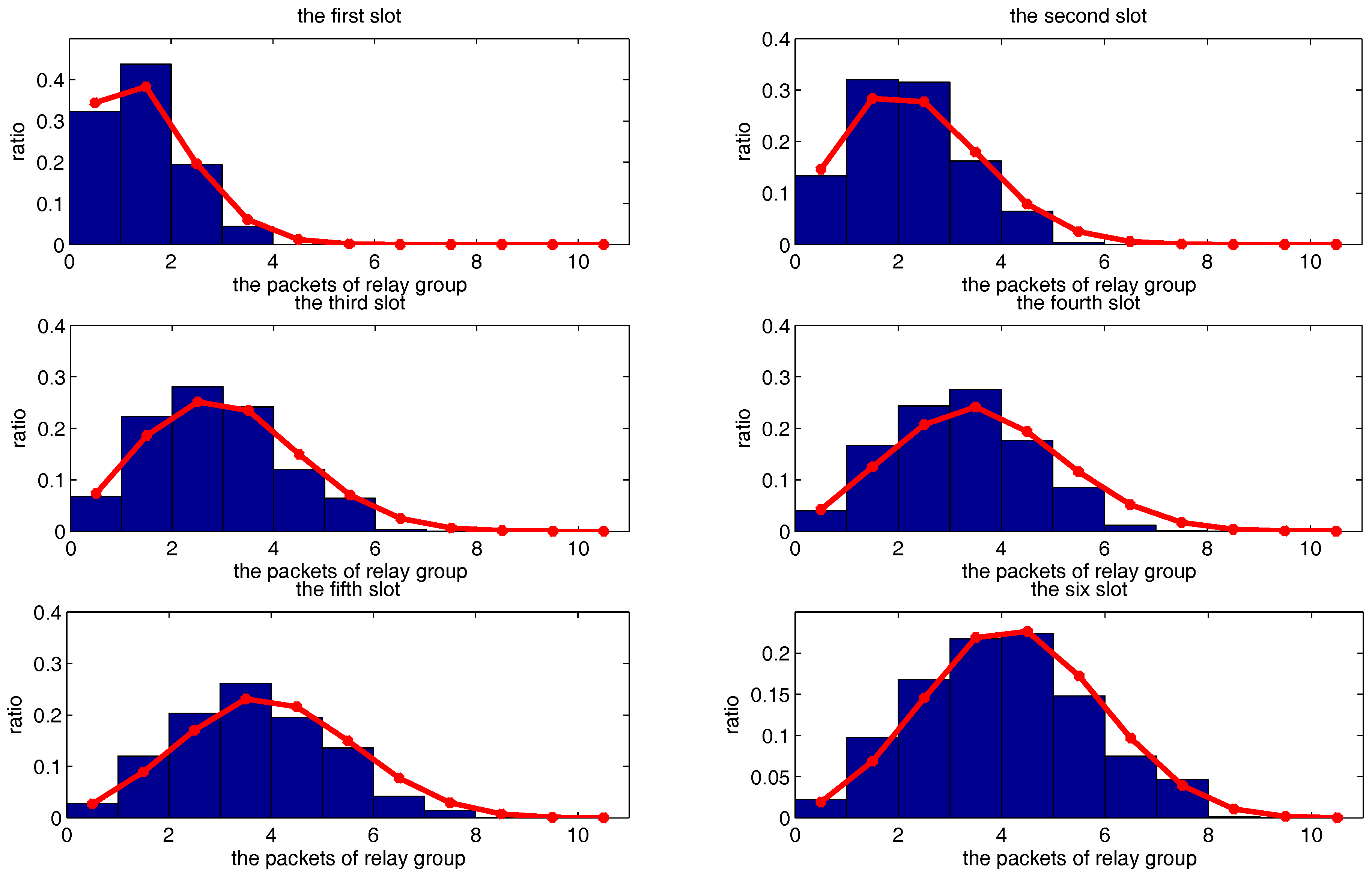
6. Simulation of Network Throughput Based on Two-Hop Transmission Strategy
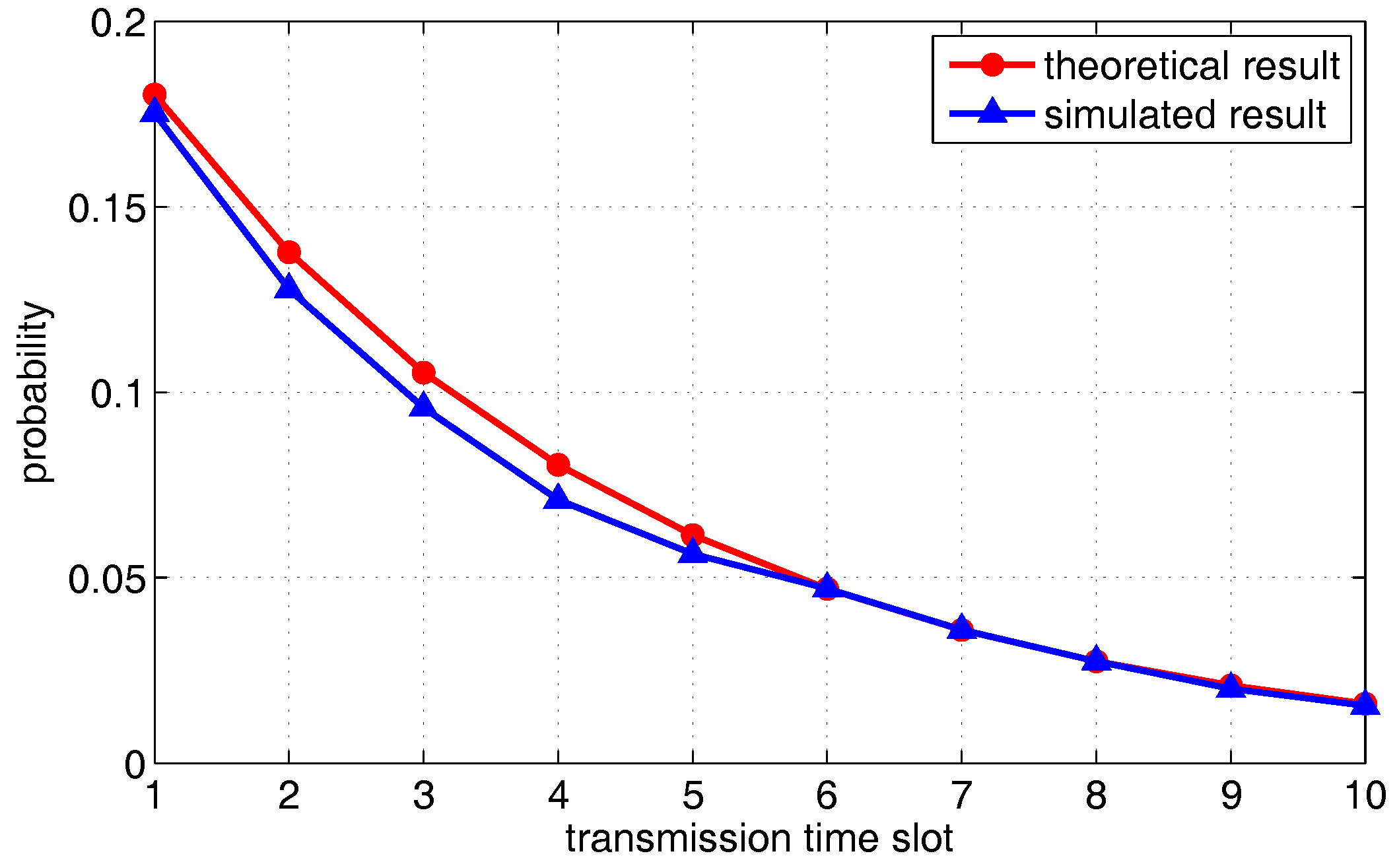
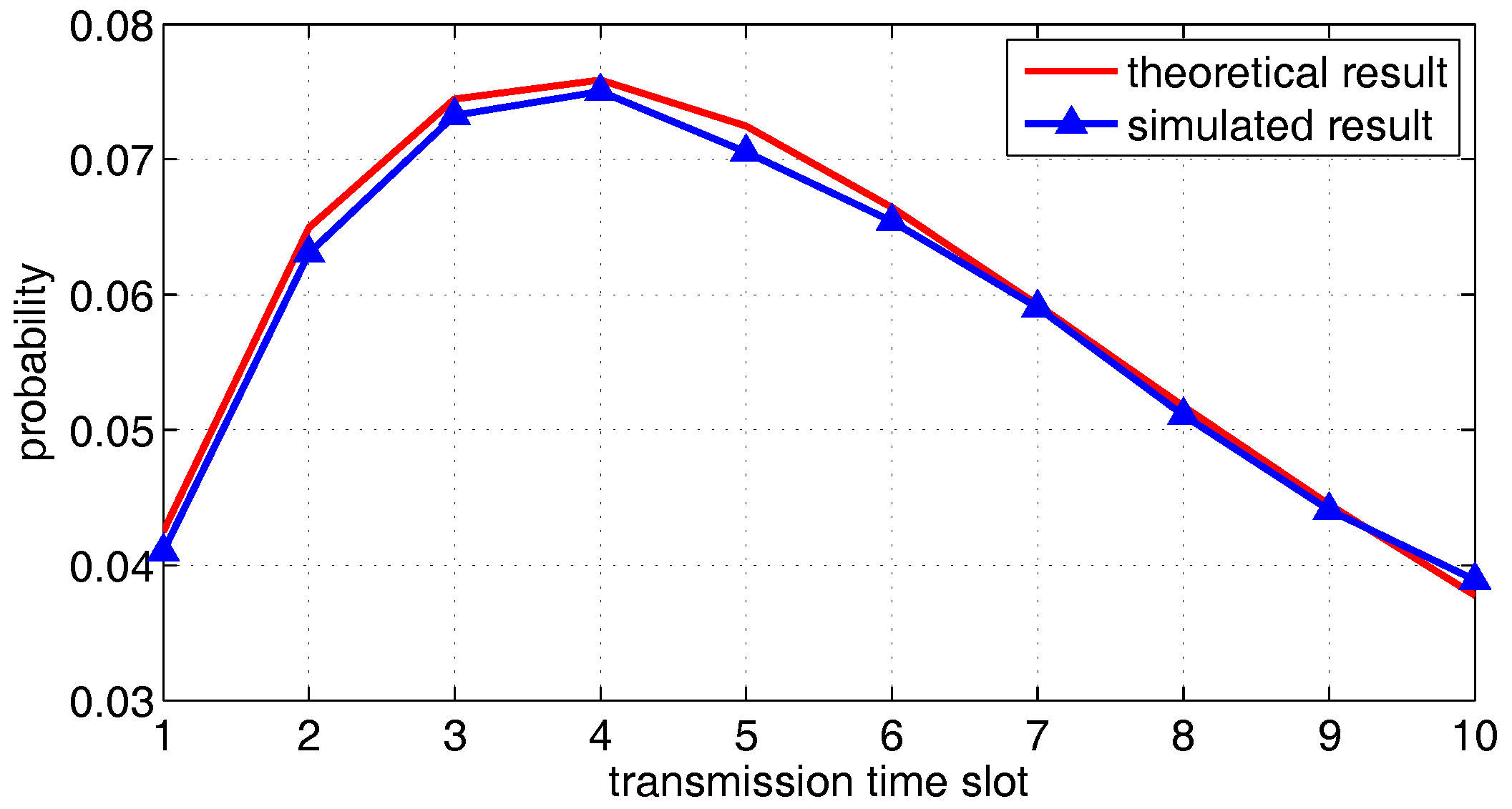
6.1. Simulation of One Transmission Pair
6.2. Simulation of Multiple Transmission Pairs
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Cayirci, E.; Tezcan, H.; Dogan, Y.; Coskun, V. Wireless sensor networks for underwater survelliance systems. Ad Hoc Netw. 2006, 4, 431–446. [Google Scholar] [CrossRef]
- Seah, W.K.; Tan, H.X. Multipath virtual sink architecture for underwater sensor networks. In Proceedings of the IEEE OCEANS 2006-Asia Pacific, Singapore, 16–19 May 2007; pp. 1–6. [Google Scholar]
- Agarwal, A.; Kumar, P. Capacity bounds for ad hoc and hybrid wireless networks. ACM SIGCOMM Comput. Commun. Rev. 2004, 34, 71–81. [Google Scholar] [CrossRef]
- Lucani, D.E.; Medard, M.; Stojanovic, M. Capacity scaling laws for underwater networks. In Proceedings of the IEEE 42nd Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 26–29 October 2008; pp. 2125–2129. [Google Scholar]
- Tan, D.D.; Le, T.T.; Kim, D.S. Distributed cooperative transmission for underwater acoustic sensor networks. In Proceedings of the IEEE Wireless Communications and Networking Conference Workshops (WCNCW), Shanghai, China, 7–10 April 2013; pp. 205–210. [Google Scholar]
- Hollinger, G.A.; Choudhary, S.; Qarabaqi, P.; Murphy, C.; Mitra, U.; Sukhatme, G.S.; Stojanovic, M.; Singh, H.; Hover, F. Underwater data collection using robotic sensor networks. IEEE J. Select. Areas Commun. 2012, 30, 899–911. [Google Scholar] [CrossRef]
- Gupta, P.; Kumar, P.R. The capacity of wireless networks. IEEE Trans. Inf. Theory 2000, 46, 388–404. [Google Scholar] [CrossRef]
- Grossglauser, M.; Tse, D. Mobility increases the capacity of ad-hoc wireless networks. In Proceedings of the Twentieth Annual Joint Conference of the IEEE Computer and Communications Societies, Anchorage, AK, USA, 22–26 April 2001; Volume 3, pp. 1360–1369. [Google Scholar]
- Liu, J.; Jiang, X.; Nishiyama, H.; Kato, N. Delay and capacity in ad hoc mobile networks with f-cast relay algorithms. IEEE Trans. Wirel. Commun. 2011, 10, 2738–2751. [Google Scholar]
- Gamal, A.E.; Mammen, J.; Prabhakar, B.; Shah, D. Throughput-delay tradeoff in wireless networks. In Proceedings of the Twenty-third AnnualJoint Conference of the IEEE Computer and Communications Societies, Hong Kong, China, 7–11 March 2004; Volume 1. [Google Scholar]
- Al Hanbali, A.; Kherani, A.A.; Groenevelt, R.; Nain, P.; Altman, E. Impact of mobility on the performance of relaying in ad hoc networks. IEEE INFOCOM 2006. [Google Scholar] [CrossRef]
- Liu, W.; Lu, K.; Wang, J.; Xing, G.; Huang, L. Performance analysis of wireless sensor networks with mobile sinks. IEEE Trans. Veh. Technol. 2012, 61, 2777–2788. [Google Scholar] [CrossRef]
- Li, P.; Fang, Y.; Li, J. Throughput, delay, and mobility in wireless ad hoc networks. In Proceedings of the IEEE INFOCOM, San Diego, CA, USA, 14–19 March 2010; pp. 1–9. [Google Scholar]
- Li, X.; Fang, S. Deployment analysis of underwater acoustic wireless sensor networks. J. Acoust. Soc. Am. 2012, 131, 3486. [Google Scholar] [CrossRef]
- Pompili, D.; Melodia, T.; Akyildiz, I.F. Three-dimensional and twodimensional deployment analysis for underwater acoustic sensor networks. Ad Hoc Netw. 2009, 7, 778–790. [Google Scholar] [CrossRef]
- Stojanovic, M. On the relationship between capacity and distance in an underwater acoustic communication channel. ACM SIGMOBILE Mob. Comput. Commun. Rev. 2007, 11, 34–43. [Google Scholar] [CrossRef]
- Stefanov, A.; Stojanovic, M. Clustered underwater ad-hoc networks in the presence of interference. In Proceedings of the IEEE Forty Fourth Asilomar Conference on Signals, Systems and Computers (ASILOMAR), Pacific Grove, CA, USA, 7–10 November 2010; pp. 1908–1912. [Google Scholar]
- Cao, R.; Yang, L.; Qu, F. On the capacity and system design of relay-aided underwater acoustic communications. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC), Sydney, Australia, 18–21 April 2010; pp. 1–6. [Google Scholar]
- Stojanovic, M. Design and capacity analysis of cellular-type underwater acoustic networks. IEEE J. Ocean. Eng. 2008, 33, 171–181. [Google Scholar] [CrossRef]
- Stefanov, A.; Stojanovic, M. Design and performance analysis of underwater acoustic networks. IEEE J. Select. Areas Commun. 2011, 29, 2012–2021. [Google Scholar] [CrossRef]
- Stamatiou, K.; Casari, P.; Zorzi, M. The throughput of underwater networks: Analysis and validation using a ray tracing simulator. IEEE Trans. Wirel. Commun. 2013, 12, 1108–1117. [Google Scholar] [CrossRef]
- Gupta, P.; Kumar, P.R. Internets in the sky: The capacity of three dimensional wireless networks. Commun. Inf. Syst. 2001, 1, 33–49. [Google Scholar] [CrossRef]
- Koliada, S. Distribution of link distances in a wireless network. J. Res. Natl. Inst. Stand. Technol. 2001, 106, 401–412. [Google Scholar]
- Fan, J.; Chen, F.; Guan, Q.; Ji, F.; Yu, H. On the probability of finding a receiver in an ellipsoid neighborhood of a sender in 3d random uans. In Proceedings of the 11th ACM International Conference on Underwater Networks & Systems, Shanghai, China, 24–26 October 2016; pp. 51–52. [Google Scholar]
- Neely, M.J.; Modiano, E. Capacity and delay tradeoffs for ad hoc mobile networks. IEEE Trans. Inf. Theory 2005, 51, 1917–1937. [Google Scholar] [CrossRef]
- Toumpis, S.; Goldsmith, A.J. Large wireless networks under fading, mobility, and delay constraints. In Proceedings of the INFOCOM 2004 Twenty-Third Annual Joint Conference of the IEEE Computer and Communications Societies, Hong Kong, China, 7–11 March 2004; Volume 1. [Google Scholar]
- Lin, X.; Shroff, N.B. The fundamental capacity-delay tradeoff in large mobile ad hoc networks. In Proceedings of the Third Annual Mediterranean Ad Hoc Networking Workshop, Bodrum, Turkey, 27–30 June 2004. [Google Scholar]
- Sharma, G.; Mazumdar, R.R. Delay and Capacity Trade-off in Wireless ad hoc Networks with Random Waypoint Mobility. 2005. Available online: https://ece.uwaterloo.ca/~mazum/MONET2004.pdf (accessed on 16 January 2018).
- El Gamal, A.; Mammen, J.; Prabhakar, B.; Shah, D. Optimal throughput-delay scaling in wireless networks: Part i: The fluid model. IEEE/ACM Trans. Netw. (TON) 2006, 14, 2568–2592. [Google Scholar] [CrossRef]
- Neely, M.J. Dynamic power allocation and routing for time-varying wireless networks. IEEE J. Select. Areas Commun. 2005, 23, 89–103. [Google Scholar] [CrossRef]
- Chen, K.; Ma, M.; Cheng, E.; Yuan, F.; Su, W. A Survey on MAC Protocols for Underwater Wireless Sensor Networks. IEEE Commun. Surv. Tutor. 2014, 16, 1433–1447. [Google Scholar] [CrossRef]



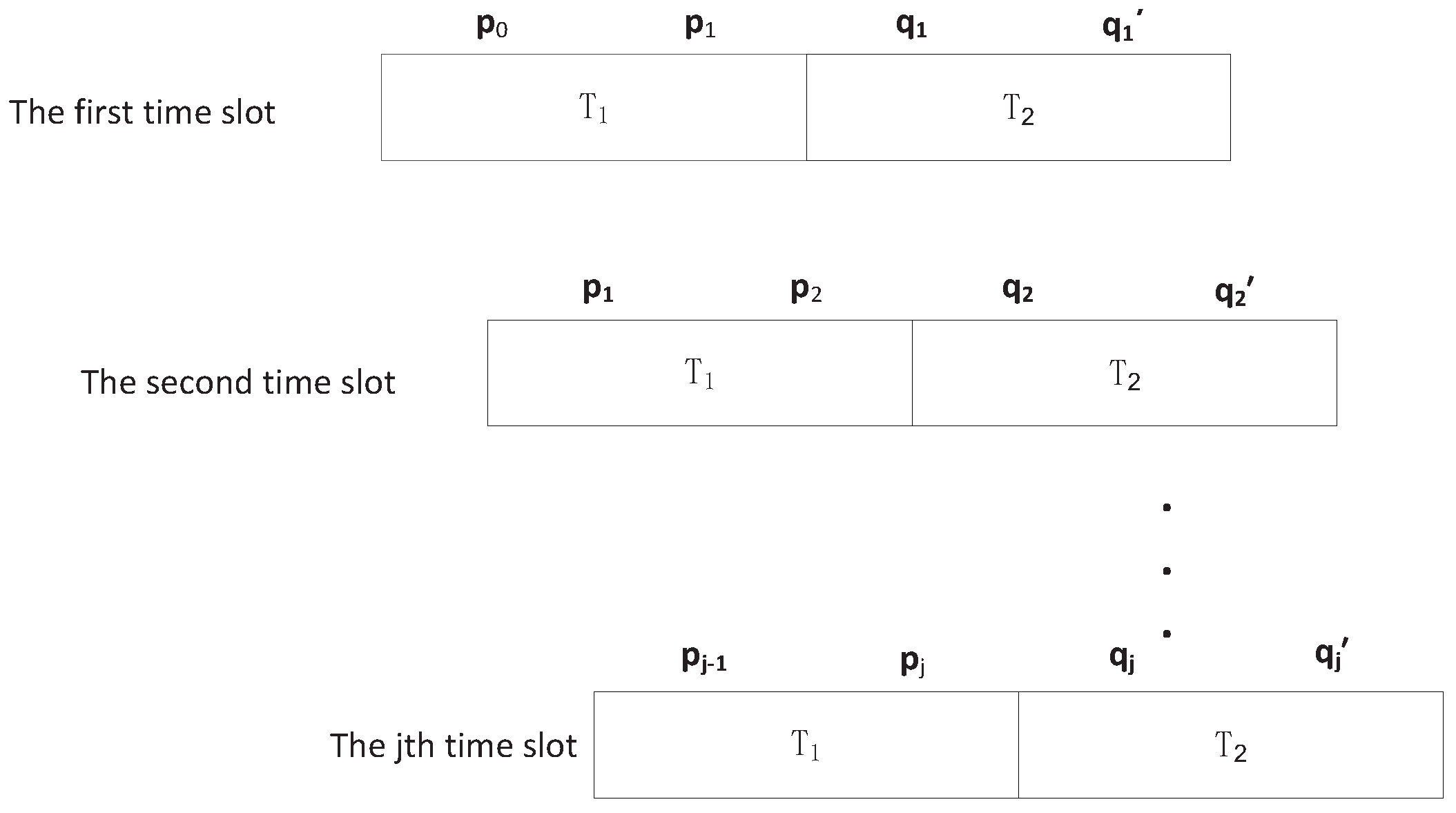
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhong, X.; Chen, F.; Fan, J.; Guan, Q.; Ji, F.; Yu, H. Throughput Analysis on 3-Dimensional Underwater Acoustic Network with One-Hop Mobile Relay. Sensors 2018, 18, 252. https://doi.org/10.3390/s18010252
Zhong X, Chen F, Fan J, Guan Q, Ji F, Yu H. Throughput Analysis on 3-Dimensional Underwater Acoustic Network with One-Hop Mobile Relay. Sensors. 2018; 18(1):252. https://doi.org/10.3390/s18010252
Chicago/Turabian StyleZhong, Xuefeng, Fangjiong Chen, Jiasheng Fan, Quansheng Guan, Fei Ji, and Hua Yu. 2018. "Throughput Analysis on 3-Dimensional Underwater Acoustic Network with One-Hop Mobile Relay" Sensors 18, no. 1: 252. https://doi.org/10.3390/s18010252




