1. Introduction
With wide deployment of wireless sensors in the real world, such as air quality monitoring and intrusion detection, wireless sensor networks (WSNs) have attracted tremendous research attention. Sensor coverage is one of the fundamental issues in WSNs. Sensors deployed under stochastic or manual deployment work cooperatively to accomplish a task such as sensing a certain field of interest. Based on the coverage subject, coverage issues can be classified into three categories: target coverage (e.g., [
1,
2,
3,
4,
5,
6]), area coverage (e.g., [
7,
8,
9,
10]) and barrier coverage (e.g., [
11,
12,
13,
14,
15]). The objective of target coverage aims to activate a subset of sensor nodes to monitor targets, which randomly appear in the 2D plane. In the context of the detection application, a target usually represents a static object that periodically generates some event signals, such as an acoustic signal.
In general, WSNs contain one or more sinks, which collect data from sensor nodes. Two sensor nodes can communicate with each other directly if they are within their communication range. As further studies of target coverage, connected target coverage (CTC) includes a more practical constraint, i.e., all active sensor nodes in CTC must be connected to the sink (probably via some relaying nodes). In order to transmit sensing data to the sink, each sensor node must find a route to the sink. Under this restriction, the nodes can communicate with each other and exchange information constructing an ad hoc network. Associated with this issue, existing work focuses mainly on two categories of optimization problems.
One of them is to find the least cost of potential sensor nodes satisfying both coverage and connectivity from a given set of sensor nodes, such as [
1,
16,
17,
18]. We name this problem the minimum cost CTC problem. The CTC problem under both the Boolean sensing model and the probabilistic model has been proven to be NP-hard [
1,
18]. This strategy minimizes the overall network cost as covering targets with the minimum number of sensor nodes. Consequently, if expensive sensors remain as a constraining resource that is economically infeasible for substantial over provision, we should take the minimum number of sensors as an optimization objective.
Most studies are concerned with maximizing network lifetime (e.g., [
19,
20,
21]) in the CTC problem as for sensors’ limited resources. The maximum lifetime CTC problem aims to schedule the activation of sensors to prolong network lifetime. To make a network last beyond the lifetime of an individual node, redundant nodes must be deployed. Hence, low-cost sensors with adequate energy may be the ideal basis for this issue.
In this paper, we study the CTC problem with omnidirectional probabilistic sensors working cooperatively. This is motivated by the observation that much work has been done to address the CTC problem; however, few of them take the probabilistic model (e.g., [
1,
16,
17,
21]) into consideration. Existing work makes a perfect assumption that a target will be covered when it lies in the sensing range of a sensor node (binary detection mode). This means that the event will be detected with probability
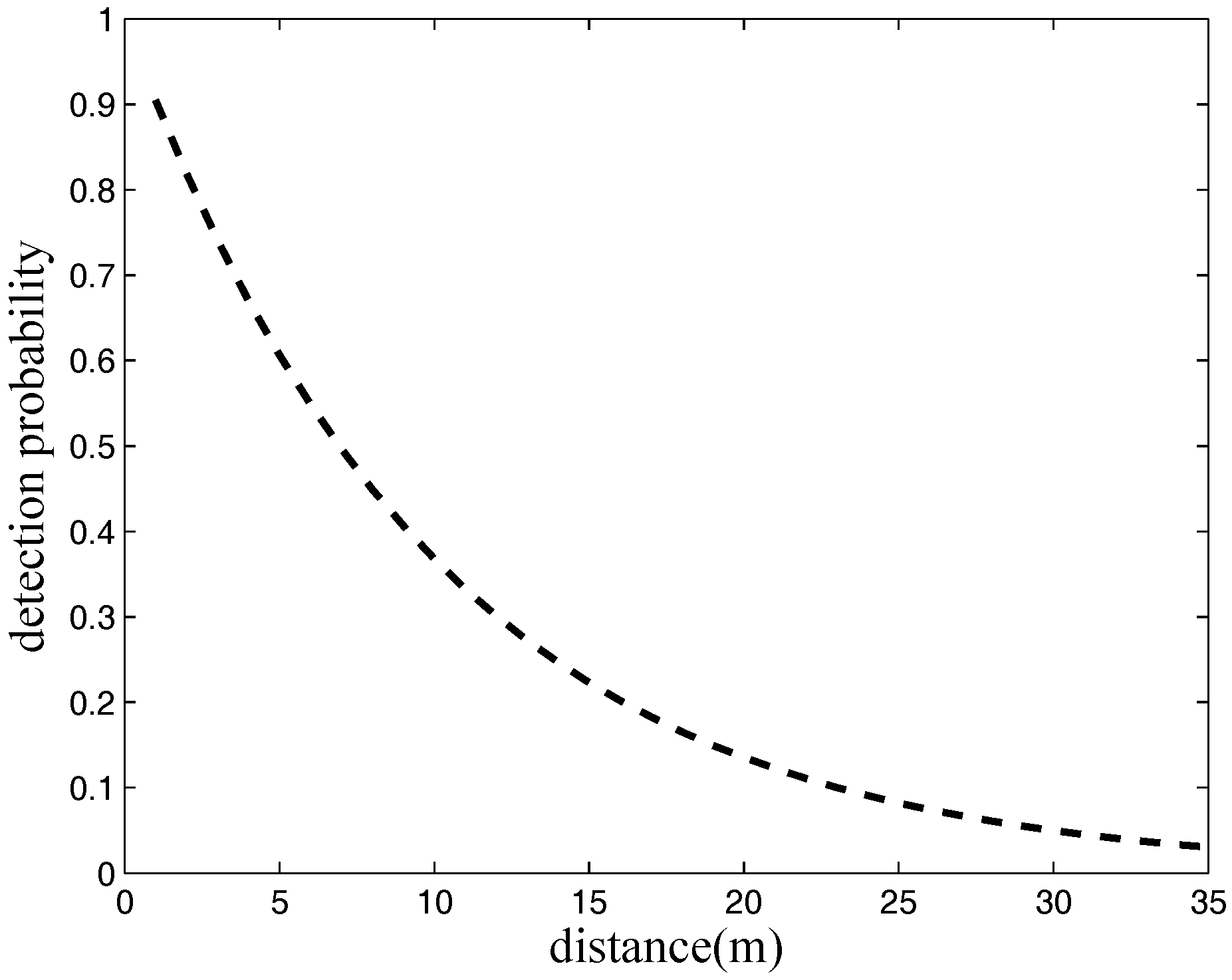
, either the target is located very close to the sensor, or it lies on the border of the sensing range. In practice, the sensing capability of a sensor is always affected by environmental factors, especially for acoustic sensors. Associated with the reasons mentioned above, the sensing quality of a sensor is represented by its detection probability, which follows a probabilistic distribution. Several empirical models have been proposed (e.g., [
22,
23]). Since the probabilistic sensing model utilizes a log-distance path loss model [
23], it means that the signal attenuates over distance, and it can be detected with high probability closer to the sensor. Leveraging the sensing model from probabilistic sensors, we can characterize the quality of sensor coverage more accurately.
We begin by highlighting the challenges we face with existing mechanisms. Considering the CTC problem under the probabilistic sensing model, we define the minimum
-connected target coverage (
-CTC) problem. The objective of the problem is to activate the minimum static sensors to achieve the detection probability threshold
for all of the targets. All sensors work in a cooperative fashion, which can improve the detection probability of all targets and reduce the number of active sensors impressively. Furthermore, all active sensors should retain connectivity with the sink (via the relaying node). The challenge of the minimum
-CTC problem we face is how to activate as few sensors as possible, to achieve high detection threshold
and provide connectivity for WSNs. Much different from sensors based on the 0/1 coverage model, probabilistic sensors have to cooperate with each other to achieve threshold
. This means that two or more sensors must be activated for one target, while only one is needed in the 0/1 disk model. This results in the sharp growth of candidate activation schemes, while taking all targets into consideration simultaneously. As a result, it is a non-trivial task to determine a better scheme from a tremendous amount of candidate schemes. Besides, different activation schemes will bring in different costs in connectivity. This induces further complexities in finding candidate activation schemes, as we must take account of the cost for connectivity at the same time. Although the probabilistic model was adopted in [
19,
20], is has been proven inadequate for a variety of reasons. In [
19], an unrealistic assumption is made that a target can be always detected with a probability over the detection threshold by at least one sensor, while the authors in [
20] take mobile sensors into consideration. Essentially, both of them fail to schedule probabilistic sensors to detect targets in a cooperative fashion. In [
18], an efficient algorithm probabilistic sensors coverage algorithm (PSCA) is presented based on set selection resulting in a better schedule scheme. However, PSCA is time consuming and unfeasible in large-scale WSNs.
To overcome the deficit of existing work where many redundant sensors are needed to achieve the unrealistic assumption in [
19] and expensive mobile sensors are required in [
20], we design an efficient algorithm with cost-effective static sensors to address the above challenges, inspired by the principle that sensors work in a collaborative way. The cost in [
19,
20] is high, since they fail to make sensors collaborate with each other. We firstly theoretically analyze the collaborative detection probability of a target by multiple sensors. Based on the theoretical analysis, we define the detection gain used to characterize a sensor’s influence on some targets. A target is deemed to achieve threshold
when its cumulative detection gain by sensors exceeds a certain threshold. On the basis of graph theory, we map the minimum
-CTC problem into a flow network. We show that the problem is NP-hard and propose a bounded approximation Algorithm 1, named the minimum vertices maximum flow algorithm (MVMFA). The key insight of MVMFA is that each augmenting path picked out by the pivotal Algorithm 2 FindPath has more flow and few inactive sensors. This means that a sensor with a high detection probability, but passing few relaying sensors by, will be activated firstly. Our main contributions are summarized as follows.
We formulate the minimum -CTC problem with omni-directional probabilistic sensors.
By reducing a minimum -detection coverage problem to the minimum -CTC problem, we prove it is NP-hard and transform it to the max-flow problem.
We propose the minimum vertices maximum flow algorithm to solve our problem and theoretically show its time complexity and approximation bound.
The rest of the paper is organized as follows. In
Section 2, a review of the relevant literature is given. In
Section 3, the problem statement and formulation are presented.
Section 4 discusses the theoretical analysis of the problem.
Section 5 presents our algorithm design and analysis. Simulation results are presented in
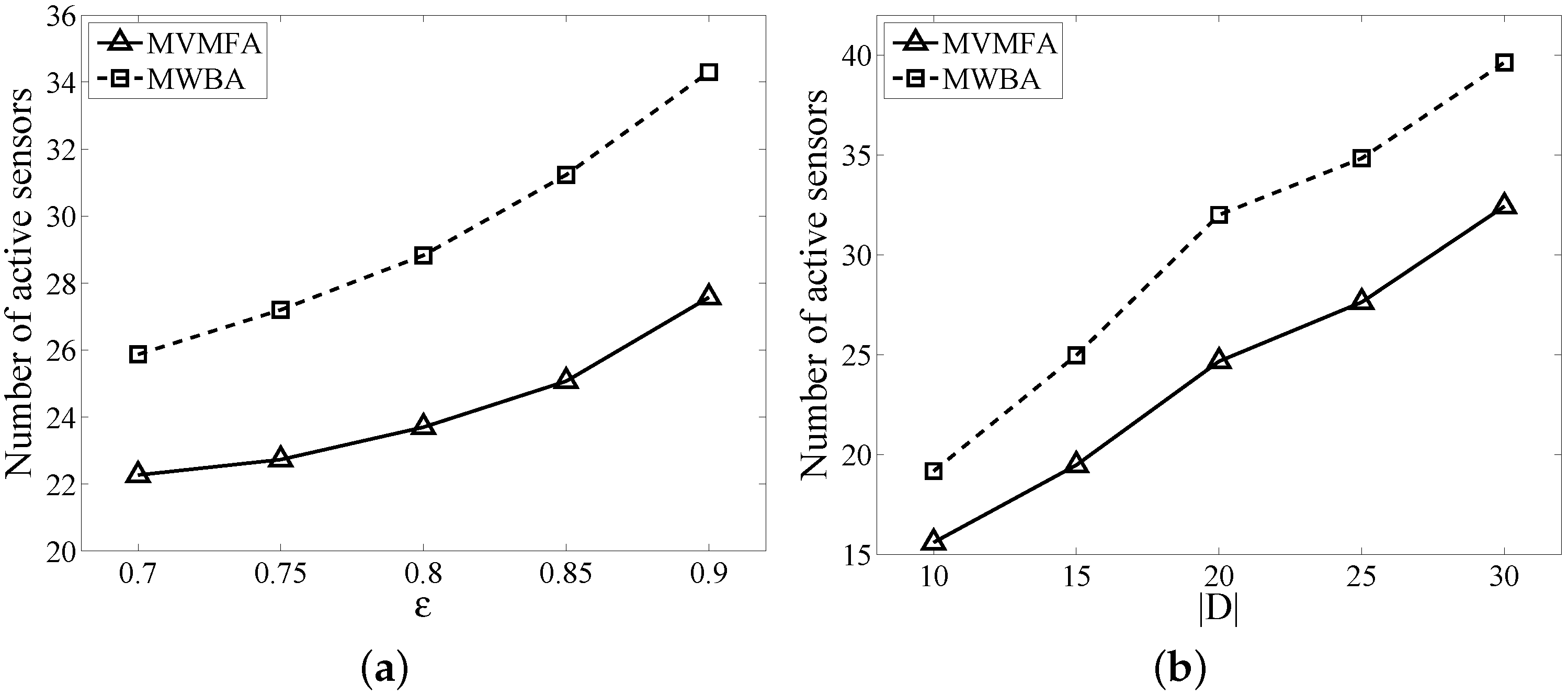
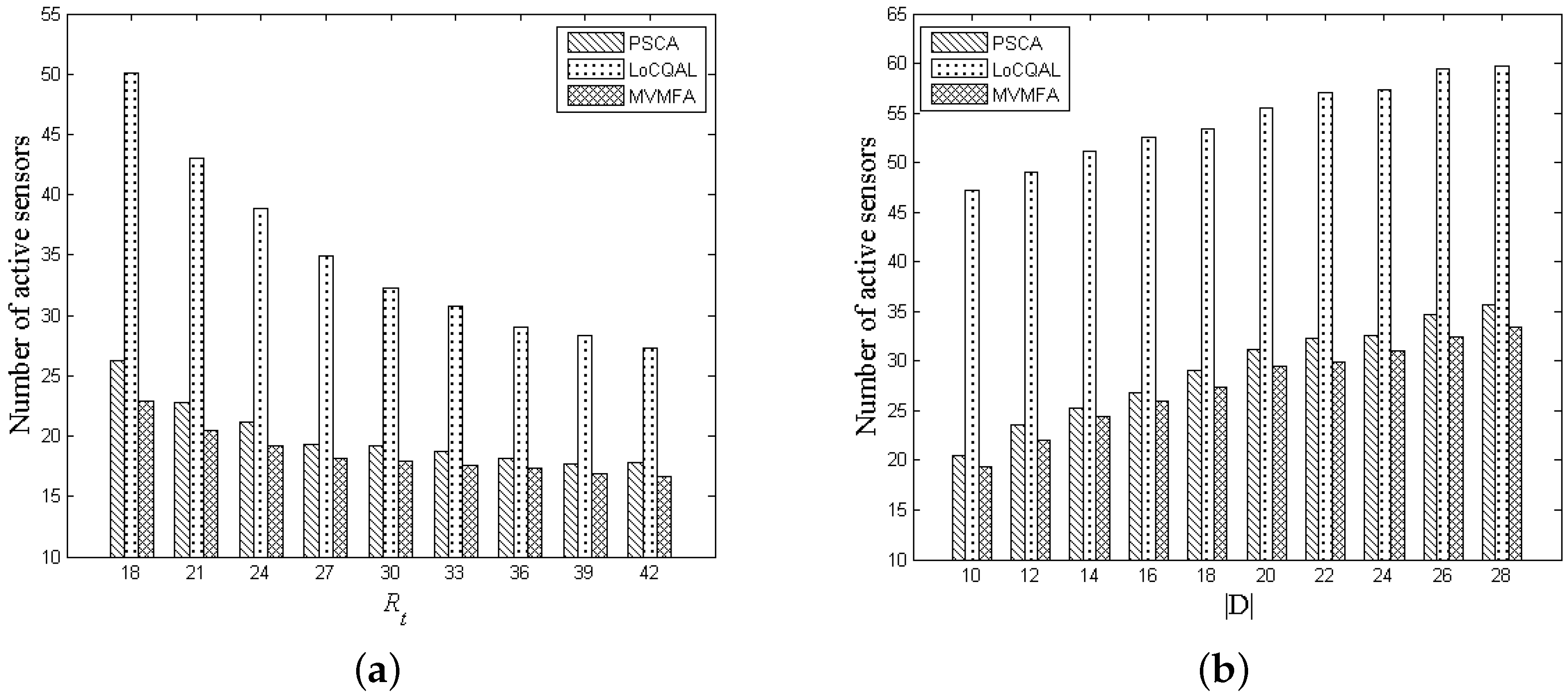
Section 6, and finally, we conclude the paper in
Section 7.
2. Related Work
WSNs have many applications in air quality, water pollution, intrusion detection, etc. [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15,
24]. Among the tremendous works in the research field of coverage, we survey the related CTC research proposals in the following section.
In earlier research related to CTC problem, the concept of connected coverage in target coverage in WSNs was proposed by Zhao in [
25]. The objective of connected coverage is to maximize the network lifetime. They defined a maximum cover tree (MCT) problem, scheduling sensors into multiple sets. Each set represents a cover tree, which is rooted at the sink node that can cover all of the target points. The MCT problem is also NP-complete, and they provide an approximation algorithm. In [
26], a round-based localized algorithm is proposed to coordinately determine sensor’ sensing range in order to prolong the WSN’s lifetime. However, in [
26], only the sensors routed to the sink are required to be active, instead of all sensors in the backbone. Both target coverage and connectivity are satisfied in [
25,
26].
There are two primary approaches to classify existing research on the CTC problem. One is the type of optimization objective: the minimum cost CTC problem [
1,
16,
17,
27] or the maximum lifetime CTC problem [
26,
28,
29,
30]. Early work on the minimum cost CTC problem [
1] assumed that the energy cost of WSNs included energy for both coverage and connectivity, called minimum-energy connected coverage (MeCoCo). By a reduction from the geometric set cover problem, the MeCoCo problem was proven to be NP-hard. The authors were the first to provide approximation algorithms with provable performance ratios for this problem. Similar to [
1] except for the definition of the cost, the minimum cost CTC problem is addressed in [
16,
17], where the goals of the problem are to schedule the minimum sensors with the constraints of coverage and connectivity. Two approximate methods based on the local search technique and genetic algorithm, respectively, were provided in [
16] with efficient results. In [
17], an oppositional gravitational search algorithm (OGSA)-based approach was proposed to solve the similar problem in [
16]. The simulation results show that the solution OGSA outperforms the approach of [
16]. The objective of minimum cost CTC in [
27,
28] was to design an efficient algorithm to place minimum relaying nodes to provide desired k-connectivity. A genetic algorithm-based approach, as well as a greedy-based approach are proposed in [
27] for minimum cost CTC, and a heuristic is designed for maximum lifetime in [
28]. In [
30], multiple sensing units are additionally taken into account. Two distributed heuristic schemes, REFS (remaining energy first scheme) and EEFS (energy efficiency first scheme), are proposed. Evaluations show that both of them can prolong the network lifetime effectively. However, EEFS outperforms REFS in network lifetime, but REFS is time saving.
Another way to classify existing work is by the type of sensing models. Some early works assumed that the sensing model was a 0/1 disk [
16,
28,
29,
30,
31], while more recent work began to take probabilistic models into consideration [
18,
19,
20,
23,
32,
33,
34]. An algorithm, CWGC-PM (communication weighted greedy cover probabilistic model), is specially designed to solve the CTC problem under the probabilistic coverage model in [
19]. However, they make an unrealistic assumption that each target is always detected with a probability over the detection threshold by at least one of the active source sensors. In [
20], mobile sensors are adopted to cover target beyond the detection threshold by moving closer to target. Probabilistic sensors were also employed to cover a series targets in [
32,
33]. A genetic algorithm based on a probabilistic coverage matrix is designed to select the minimum sensors to meet the probability of detection requirement in [
32]. However, they fail to take account of connectivity. Additionally, probabilistic sensors were used in [
33] to track moving targets. The probabilistic sensors coverage algorithm (PSCA) with provable approximation ratios [
18] for the minimum
-detection coverage problem aims to reduce the number of active sensors. They map the problem into a set select problem by constructing the candidate coverage set (CCS) and activate sensors for coverage requirement from the CCS. Moreover, a Steiner tree algorithm is used to picked out some sensors as relay nodes to maintain the network connectivity.
In summary, although probabilistic sensors have been adopted for the coverage problem [
18,
19,
20,
23,
32,
33,
35], there are still some differences. The subject detected in [
13,
33,
35] is different from us, since the work in [
13] focuses on barrier coverage. The paper [
33] is for moving targets tracking, and the paper [
35] solves the area coverage problem [
19]. Additionally, the authors in [
23,
32] fail to take connectivity into consideration. Despite that PSCA [
18] could obtain a better performance in the number of active sensors, it is infeasible for large-scale WSNs because of the high time complexity. In this study, an approximate algorithm, MVMFA, is proposed to schedule the sensors, such that a given set of targets can be detected beyond the detection threshold
, and the sensing information can be routed to the sink.
4. Theoretical Analysis
For mapping our problem into a network flow problem, we first linearize the collaborative detection probability formula similar to [
13,
18]. Next, we prove that the minimum
-CTC problem is NP-hard by a reduction from the minimum
-detection coverage problem. Lastly, we describe the transformation from our problem to a network flow problem in detail and present a method to set
.
4.1. Analysis of Detection Probability
Given a target
t detected by a sensor set
, the detection probability is Equation (
2). According the coverage requirement,
should be larger than
. Then, we can get:
We linearize the formula as follows.
The term is defined as the aggregate gain threshold.
Sensor detection gain
: A target can get detection gain from sensor
i according to the formula:
The detection gain reflects how much impact a sensor has on one target.
Cumulative detection gain : A target’s cumulative detection gain is to aggregate detection gains from the surrounding sensors.
Obviously, if the target t satisfies the coverage requirement, then its cumulative detection gain must be larger than , i.e.,
4.2. NP-Hardness
In this section, we prove the NP-hardness of the minimum
-CTC problem theoretically by a reduction from the minimum
-detection coverage problem [
18]. We have previously proven that the minimum
-detection coverage problem is NP-hard without taking connectivity into consideration. According to the proven NP-hardness, for any instance in the minimum
-detection coverage problem, it should be reduced to the minimum
-CTC problem in polynomial time.
Theorem 1. The minimum ϵ-CTC problem is NP-hard.
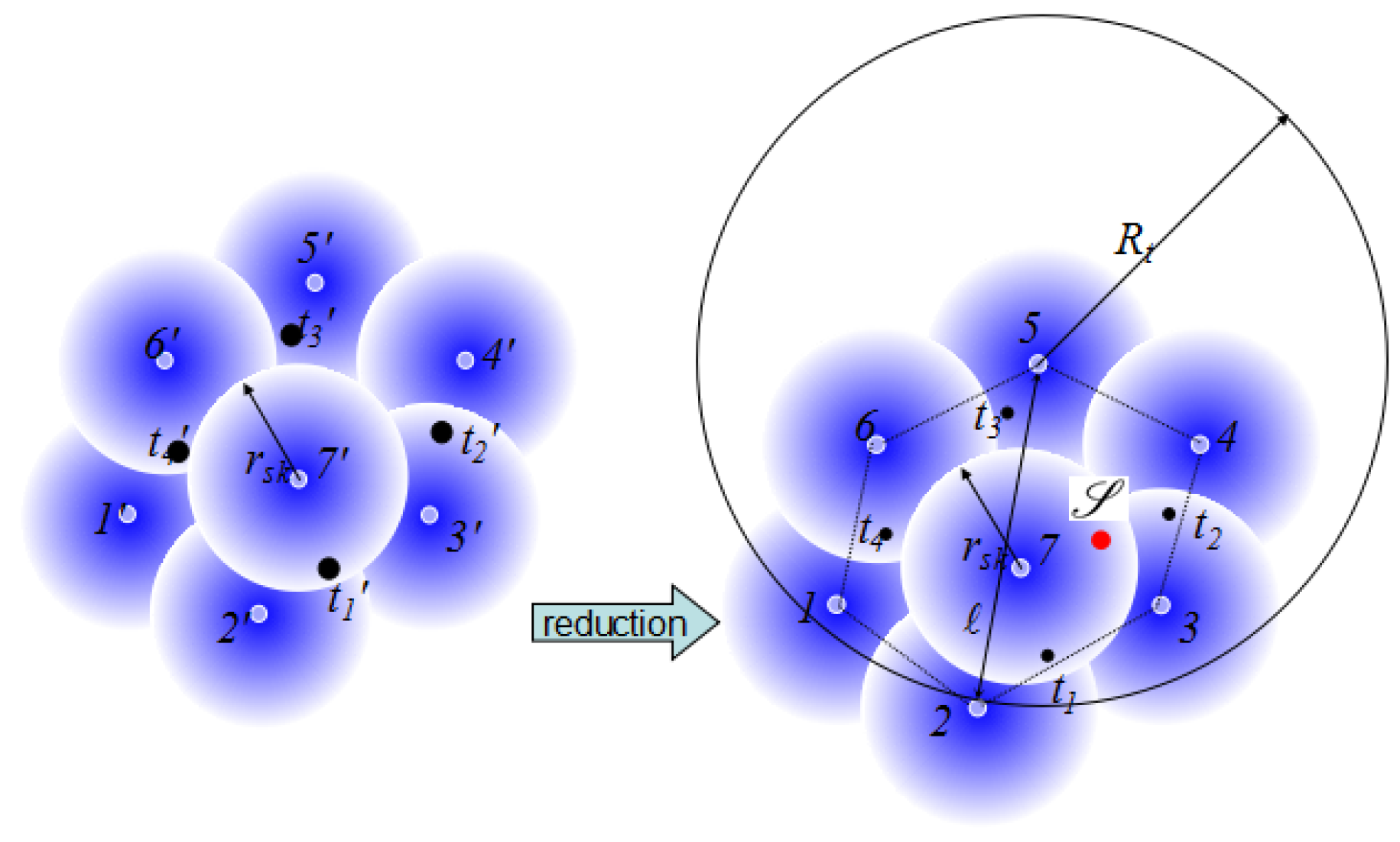
Proof of Theorem 1. Assume an instance of the minimum -detection coverage problem, and , where denotes the sensor set and denotes the target set. It aims to activate the least sensors from that all targets in must be detected beyond the detection probability threshold . Note that all sensors in the minimum -detection coverage problem share the same parameters. The reducing procedure will be presented in detail.
As shown in
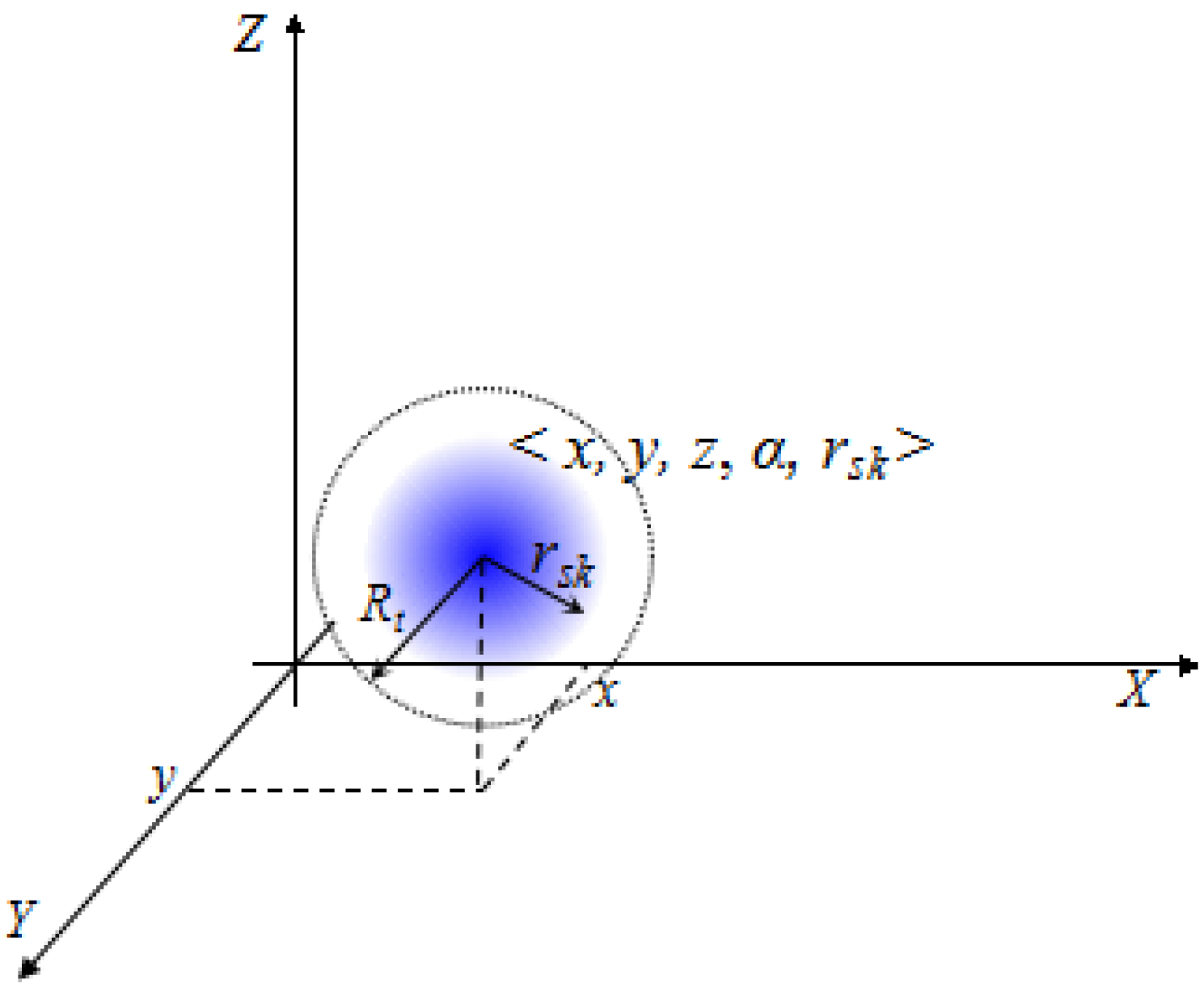
Figure 4, we calculate the diameter (denoted by
ℓ) of the sensor set
based on the rotating calipers [
37] in
time, followed by computing the convex hull of
. For each sensor
in
, a corresponding probabilistic sensor
i is created at the same location with the same
and
. Additionally, for each target
in
, a corresponding target
is put at the same location. Lastly, we put the sink
anywhere in the convex hull. As a result, any active sensor can communication with the sink directly with one hop. Under these settings, the minimum
-CTC problem is to find the least probabilistic sensors with
and
, centered in sensors
to detect all targets, which is exactly the same as the minimum
-detection coverage problem.
In other words, the minimum
-detection coverage problem is a special case of the minimum
-CTC problem, under the constraints of homogeneous sensors with the same
and
. In [
18], the minimum
-detection coverage problem has been proven NP-hard. Therefore, the minimum
-CTC problem must also be NP-hard. ☐
4.3. Problem Transformation
Both the detection probability and detection gain will be very small when the distance between sensor and target is large. Furthermore, it will be more cost-effective to obtain the probability with short distance.
Minimum detection probability : is a pre-defined threshold set by applications. If the detection probability of a target t is detected by one sensor i to be less than , we take it as zero, otherwise .
We have previously presented a method in [
18] to determine the
for different detection probability threshold
. Here, we give a suggestion to design the
for each probabilistic according to:
Due to requirements of both coverage and connectivity, the minimum -CTC problem is complex. We introduce a network flow model to solve it.
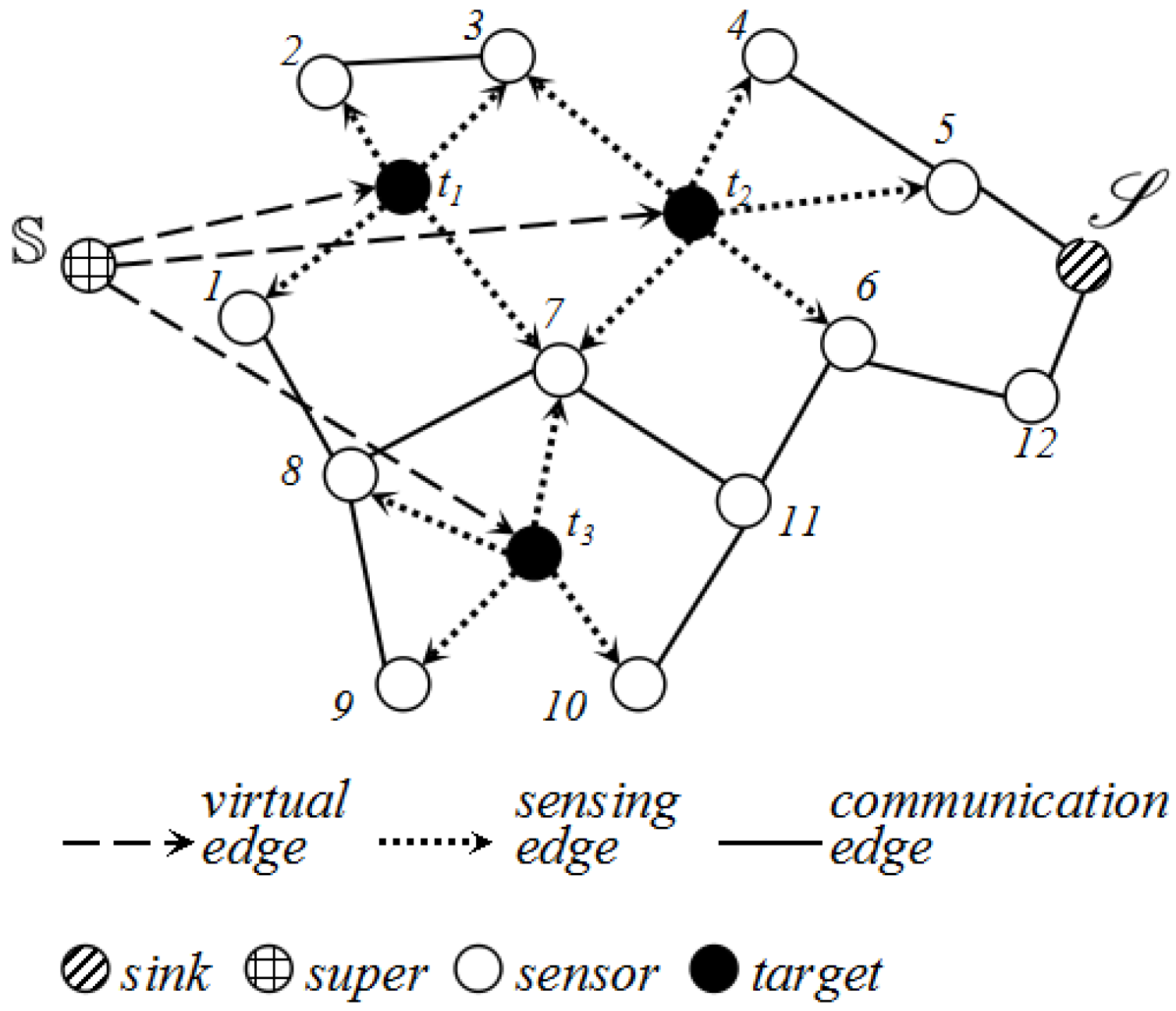
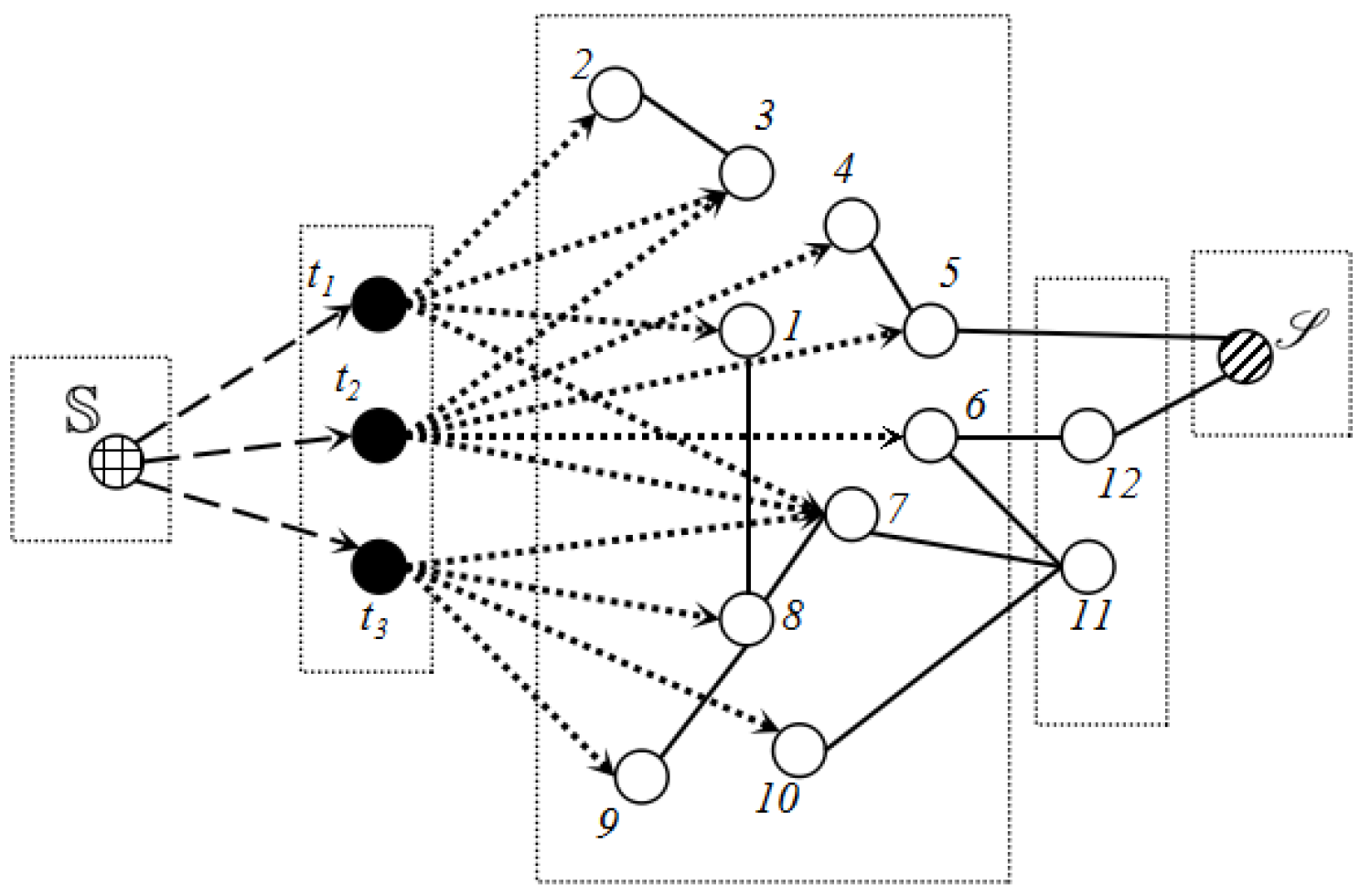
Based on the analysis of detection probability, we further build a flow graph to characterize the feature of the network where S denotes the sensor set, where D is the target set; denotes the sink; represents the super source we created; and E is the edge set. In order to transform our problem to a max-flow problem, we create a super source as the source of the flow graph G.
The construction of G is as follows:
- (1)
For , we add directed edge , into E with capacity . We name it the virtual edge.
- (2)
For
,
, if
, it will be linked with an directed edge
with capacity
according to Equation (
3). We denote it the sensing edge.
- (3)
For , if , an undirected edge will be added into E and its capacity is . We denote it the communication edge.
- (4)
For , if , then with capacity .
Theorem 2. When G’s maximum flow equals , the sensors delivering the maximum flow satisfy both the coverage and connectivity requirements for the minimum ϵ-CTC problem.
Proof of Theorem 2. When the maximum flow reaches
, it means that each virtual edge is saturated. As a result, the flow from each target is
, and it will be transferred to the sink
by communication edges. Assuming for each,
denotes the sensor set that transfers flow from
t, we can get
(
is the flow value through node
i). As a result, the detection probability of
t is at least
based on Equation (
4). Since
flows from
t will eventually arrive at the sink
, each sensor in
can communicate with the sink (probably via some relaying nodes). ☐
According to Theorem 2, we can reduce the minimum -CTC problem to the minimum vertices maximum flow problem.
Minimum vertices maximum flow problem: Based on the flow graph we constructed, our ultimate aim is to find a minimum set , and the subgraph of the max flow of (the construction method is the same as G) is equal to .
Without a doubt, the minimum vertices maximum flow problem is also NP-hard.
5. Algorithm Design
Based on the above analysis, we have proven the minimum vertices maximum flow problem to be NP-hard. It is hard to find the optimal solution in polynomial time. In this section, we first design an approximation solution, named the minimum vertices maximum flow algorithm (MVMFA). Next, the time complexity and approximation ratios are proven in theory.
5.1. Approximation Algorithm
The minimum vertices maximum flow problem aims to find a minimum set to meet upper flow value . We design the MVMFA (Algorithm 1) based on the FindPath, which aims to find the augmenting path.
Firstly, we create flow graph
G as mentioned in
Section 4. As we know, the key to solve the problem using the network flow is to map the problem into the network flow graph. MVMFA is based on the classical network flow method of Ford–Fulkerson. The basic idea of MVMFA is to find the augmenting path iteratively with a bigger
:
and the flow will be sent to the sink
along the path. The distinction between MVMFA and other maximum flow algorithms, such as Edmonds-Karp [
38] and Dinic [
39], is the method to find the augmenting path. Probabilistic sensors will be activated along the augmenting path.
| Algorithm 1 MVMFA. |
- 1:
- 2:
- 3:
- 4:
- 5:
if then - 6:
return C - 7:
else - 8:
- 9:
- 10:
goto 4 - 11:
end if
|
5.2. Algorithm Analysis
We analyze the performance of our proposed algorithm MVMFA theoretically in this section.
In this paper, we present the FindPath algorithm (Algorithm 2) to find an augmenting path . FindPath is based on the priority queue and breadth-first-search method. We define the structure NodeInfo to record the information of the search nodes.
struct NodeInfo{
;
;
;
;
};
As mentioned above, represents the flow value, while is the number of inactive sensor nodes when achieving some search node. is the sensor identifier corresponding to the search node. In the priority queue we defined, the search node with bigger will be in front of the queue (if the count is zero, the with bigger flow is larger than the others).
| Algorithm 2 FindPath. |
- 1:
- 2:
- 3:
- 4:
- 5:
while do - 6:
pop the first search node pnode of Q; - 7:
if then - 8:
- 9:
- 10:
- 11:
end if - 12:
- 13:
if then - 14:
- 15:
else - 16:
- 17:
end if - 18:
for do - 19:
if then - 20:
- 21:
if then - 22:
; - 23:
else - 24:
; - 25:
end if - 26:
; - 27:
; - 28:
; - 29:
; - 30:
end if - 31:
end for - 32:
end while - 33:
if then - 34:
- 35:
end if
|
Lemma 1. After each invocation of FindPath, some sensing edge or virtual edge will be saturated.
Proof of Lemma 1. All vertices in
G can be divided into five parts as
Figure 6 shows, super source, target nodes, sensor nodes, relaying nodes and the sink
. The characteristic of our flow graph
G determines that the flow in
starts from the virtual edge, passes the sensing edge and arrives at the sink through the communication edge. The flow value of each augmenting path relies on the capacity of the virtual edge and sensing edge due to the limited capacity.
Before we first call FindPath, all sensor nodes have not been activated. Assuming is the first augmenting path by FindPath, denotes virtual edge, while represents the sensing edge. It is obvious that the flow in is ( is the capacity of ). Thus, or will be saturated. In either case, will not appear in the augmenting path any more.
After that, the augmenting path that FindPath explores later has two scenarios:
(1) does not contain activating sensor nodes. This scenario is the same as , and will not be selected by FindPath anymore.
(2) contains activating sensors. Without loss of generality, we assume is the first active sensor node, which is in . There is no doubt that flow in equals . Due to the active sensor node , there must be a path in which all sensor nodes have to be activated previously. Along , flow will not decrease while the count of the search node will not increase. Whether the flow is or , FindPath will not pass anymore. In summary, after each invocation of FindPath, some sensing edges or virtual edges must be saturated. Meanwhile, FindPath passes every sensing edge at most once. ☐
Theorem 3. The time complexity of MVMFA is , where κ is the maximum out-degree of targets.
Proof of Theorem 3. Lemma 1 shows that each sensing edge is selected at most once. Hence, FindPath is invoked at most times ( denotes the out-degree of target t). In FindPath, the while loop executes at most times because each edge is pushed into the priority queue at most once (each search node represents an edge). In the while loop, it costs time to push adjacent search nodes into the priority queue. Therefore, the time complexity of MVMFA is . ☐
We assume N is the size of C computed by MVMFA, while is the optimum.
Theorem 4. , where ( is the minimum hops from a to b minus one) and β is the maximum indegree of sensor nodes.
Proof of Theorem 4. Assuming MVMFA invokes k times FindPath, each flow value is denoted by , and each count is , respectively.
According to FindPath based on the priority queue and the breadth-first-search, we can find the augmenting path with a bigger
. We can get:
where in the
i-th invocation of the FindPath,
denotes the minimum flow of all search nodes and
represents the maximum count. In the worst case scenario, the augmenting path may arrive at the sink with the flow value
and
inactive sensors. Furthermore,
is not larger than
, i.e.,
with Equations (
5) and (
6),
According to Equations (
5) and (
7), we can get:
The minimum
-CTC problem concentrates on finding the minimum
C. When we just take account of coverage without connectivity, we assume
is the minimum number sensors ensuring coverage needs. Obviously,
. Let
denote the maximum indegree of sensor nodes. It means one sensor can detect at most
targets. Therefore, the least number of sensors we need satisfies:
With Equations (
8) and (
9),
☐