1. Introduction
Recent years have witnessed a massive growth in the use of Wireless Sensor Networks (WSNs) in numerous applications, especially those operating in hostile environments such as space exploration, disaster management, search and rescue, and battlefield surveillance [
1]. In some of these applications that operate in such a hostile setup, a set of sensor nodes are deployed to an area of interest to collaboratively monitor certain events of interest. By deploying the sensor nodes to operate in harsh environments, it would be possible to avoid risk to human life and reduce the application cost [
2]. Sensors are small and battery operated devices, having limited processing and communication capabilities [
3].
Upon deployment, the sensor nodes are expected to stay reachable to each other and form a network. Network connectivity enables sensor nodes to share data and to coordinate their actions while performing a task, and to forward the collected data to a command center [
4]. Therefore, the inter-sensor nodes connectivity should be maintained all the time to enable such interactions.
However, the nodes of WSNs that serve in harsh environments are susceptible to failure. For example, in a battlefield, parts of the deployment area may be bombed, destroying the sensor nodes in the vicinity. The failed nodes may cause the WSN to be split into multiple disjoint partitions due to the loss of connectivity among the partitions. Losing the network connectivity in WSNs has a very negative effect on the applications since it prevents data exchange and hinders the coordination among some sensor nodes. Given the importance of data sharing in achieving WSN application goals, restoring the connectivity among these WSN partitions would be very necessary so that the WSN becomes operational again. The Euclidean Steiner Minimal Tree (ESMT) [
5] based approach for deploying relay nodes is one of the most efficient approaches [
6] for restoring the connectivity in such a case. Relay nodes are usually assumed to be more powerful and expensive than sensor nodes. Given hardware and deployment cost associated with relay nodes, it is usually desirable to minimize the number of required relay nodes. Thus, the goal of the recovery process in this paper is to re-establish the connectivity by forming an inter-partitions topology, while minimizing the number of required relay nodes. Such relay nodes placement optimization problem is proven to be an NP-hard problem by Lin and Xue [
7].
Several heuristic approaches have been proposed in the literature to solve this problem. Some of these heuristics focused on minimizing the count of the required relay nodes by forming a Minimum Spanning Tree (MST), in which every relay node has a node degree of two [
7,
8,
9]. Meanwhile, other works focused on the degree of connectivity of the formed topology with less priority on the number of relay nodes required [
4,
10,
11]. In this paper, we propose a novel relay nodes placement strategy based on space network coding that minimizes the number of required relay nodes to restore the connectivity of a partitioned WSN. In the context of this paper, each partition is represented by one sensor node that we call terminal.
Departing from
Network Information Flow (NIF) [
12] proposed in 2000, in which extra relay nodes can not be introduced,
Space Information Flow (SIF) [
13], also called Space Network Coding, is a concept proposed in 2011 that studies network coding in Euclidean space, in which an extra set of relay nodes can be inserted to connect a given set of terminal nodes. This paper uses the terms SIF and space network coding in an interchangeable way. The goal of SIF is to minimize the
cost of constructing a network, where the
cost is defined as the total length of information transmission required to achieve a one-bit end-to-end multicast throughput [
14]. A
Pentagram [
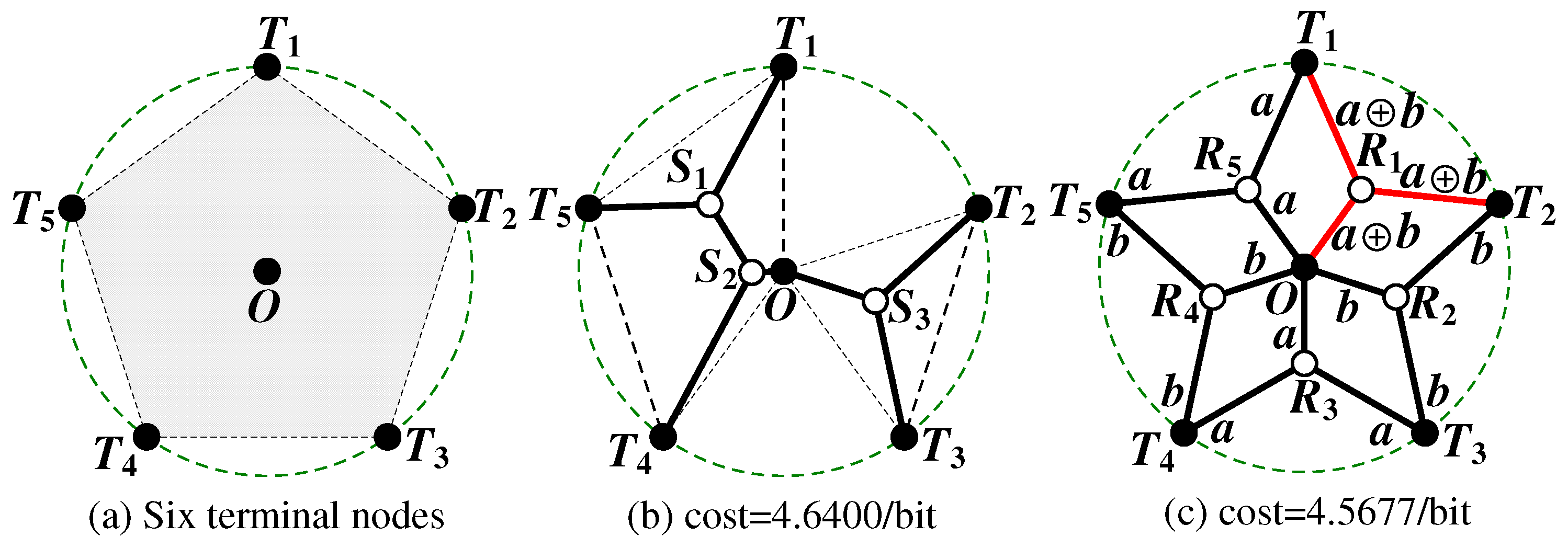
15] example illustrated in
Figure 1 demonstrates that the performance of SIF can be strictly better than that of ESMT, with the
Cost Advantage (CA) [
13] being strictly bigger than 1. CA is defined as the ratio of minimum cost necessary for achieving a target throughput by routing over that of network coding.
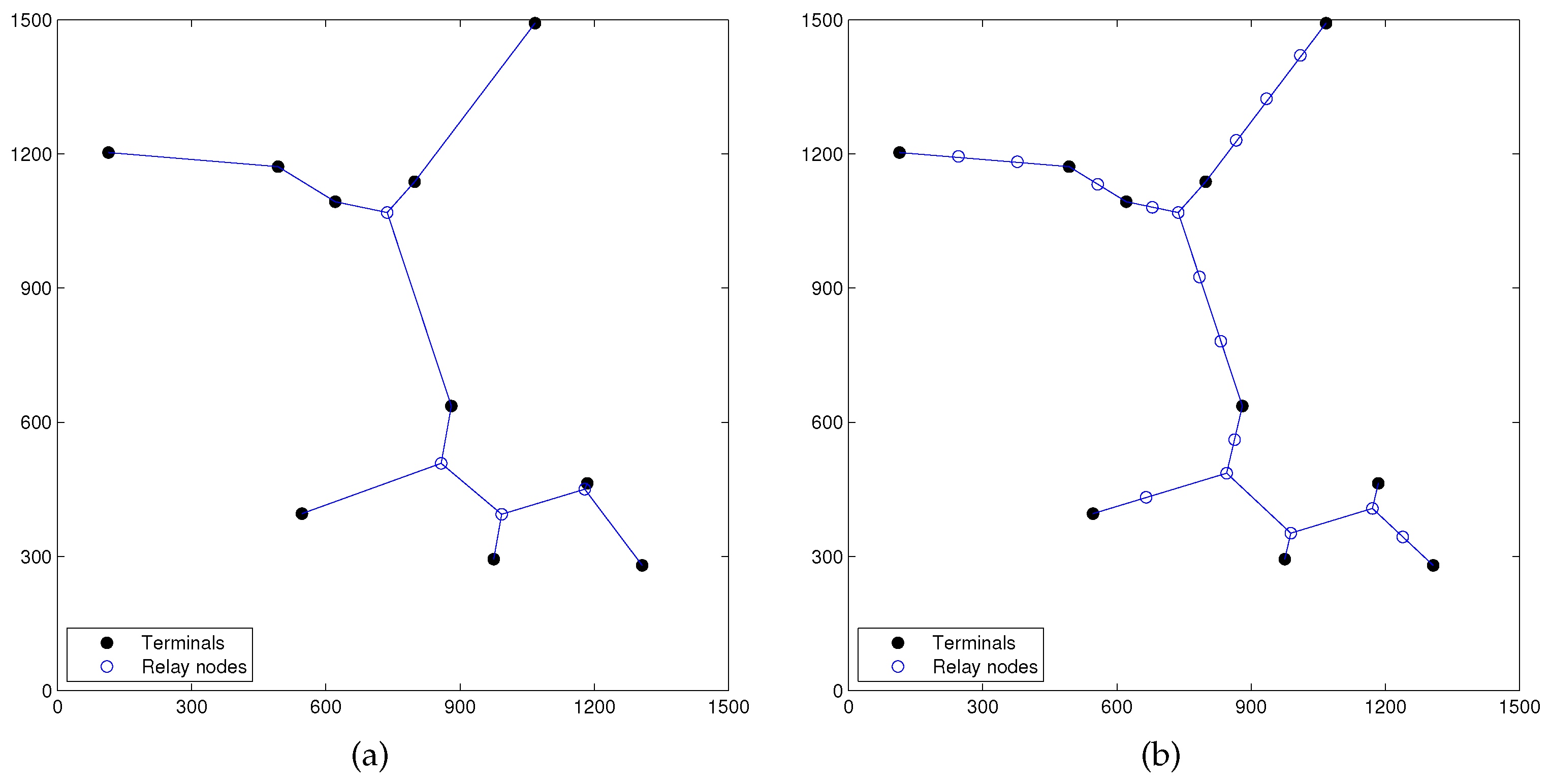
Figure 1a depicts a multicast version of SIF problem with six terminal nodes in a 2D Euclidean space, where five nodes (
to
) are evenly distributed along a circle and form a regular pentagon centered at node
O. The radius of the circumscribed circle is 1. Node
O is chosen as the multicast source, with the other five being receivers. We compare network coding and routing, using cost as our comparison metric. Routing in space with additional relay nodes allowed to be introduced, in order to connect the terminal nodes, is equivalent to the ESMT problem. With ESMT, the optimal solution is computed by ESMT exact algorithm [
16], which has a cost of 4.6400/bit, as illustrated in
Figure 1b. Three Steiner nodes (
to
) are inserted to connect the terminal nodes, each adjacent to three links that form three angles of
.
Figure 1c shows the optimal solution based on space network coding, where five relay nodes (
to
) are inserted to connect the terminal nodes, each adjacent to three links that form three angles of
. The total distance is 9.1354 and each sink receives two bits. The normalized per bit cost is 9.1354/2 = 4.5677/bit, and it is strictly smaller than the optimal cost based on ESMT. CA = 4.6400/4.5677 ≈ 1.0158 > 1. Despite its small value, we emphasize that the gap between the two optimal costs reveals that space network coding is fundamentally a different problem from routing in space, with a different problem structure, and probably a different computational complexity.
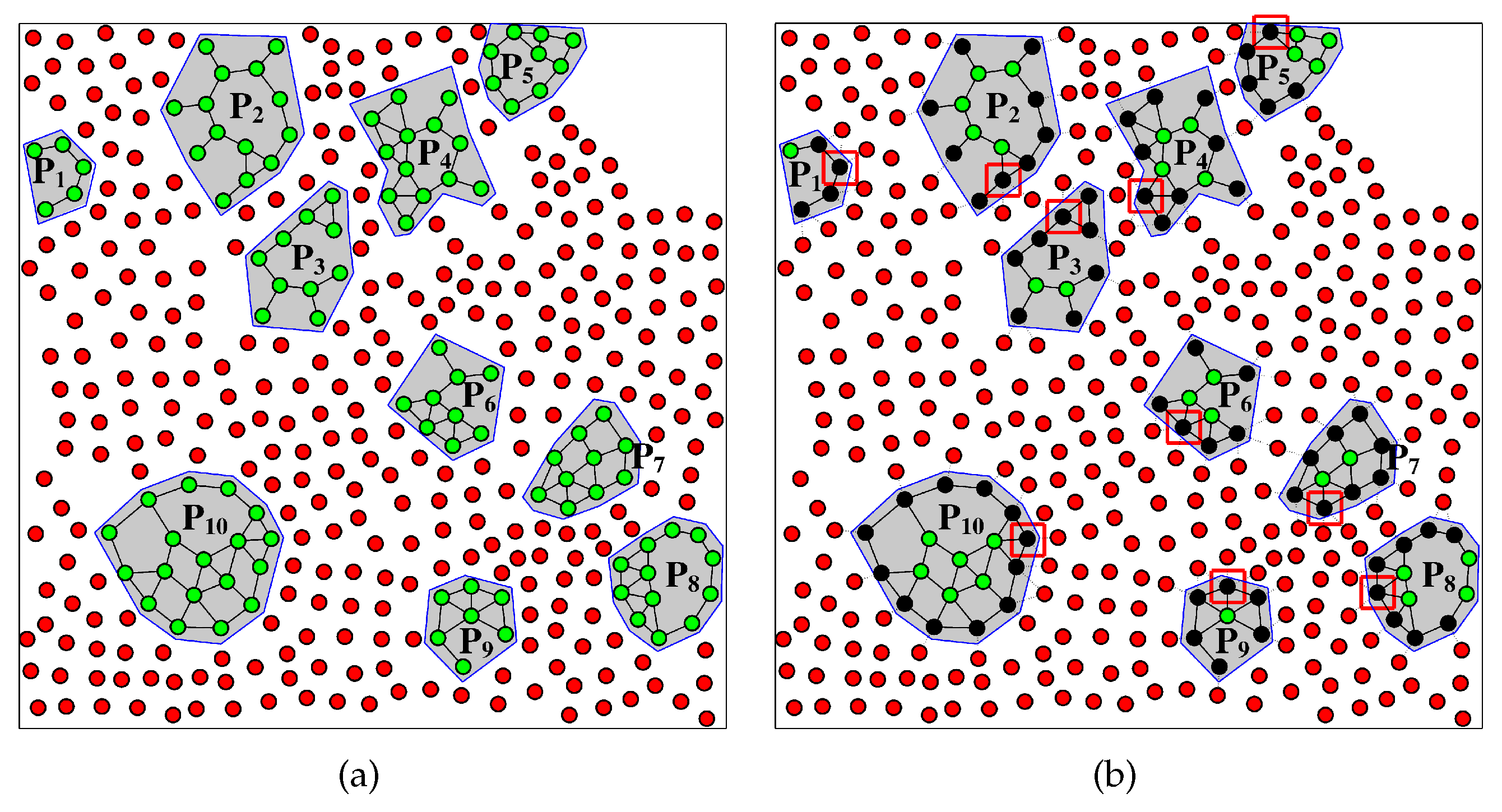
The main contributions of this work are as follows. Unlike most existing works that are based on MST or ESMT, we propose a new polynomial time min-cost multicast Relay Placement algorithm based on Space Network Coding (RPSNC) that optimally solves the problem of restoring the network connectivity for the special case of three terminals and strives to minimize the number of relay nodes required for restoring the connectivity for larger networks using Delaunay triangulation, non-uniform partitioning and linear programming techniques. Delaunay triangulation is able to adapt RPSNC to any density distribution of relay nodes and terminals, non-uniform partitioning aims to adapt RPSNC to any density distribution of terminals, while linear programming aims to optimize the required number of relay nodes by computing the min-cost of the inter-partitions topology. Linear programming also determines the connection links between the relay nodes and terminals. It is worth noting that the proposed RPSNC computes not only the minimal number of relay nodes, but also the geometric location of each required relay node in Euclidean space. To the best of our knowledge, this is the first work to propose a min-cost multicast space network coding based algorithm for connectivity restoration in WSNs.
RPSNC first selects one representative sensor node in each partition and sets it as a terminal. It then combines non-uniform partitioning and Delaunay triangulation techniques for generating the candidate relay nodes; afterwards, RPSNC applies linear programming for choosing the optimal relay nodes and computing their connection links with terminals. Basically, the distance between the optimal relay nodes and terminals may exceed the communication range of the optimal relay nodes. Hence, RPSNC opts to populate additional relay nodes along the connection links to achieve a strong connectivity and a better relay nodes coverage. The simulation results demonstrate the effectiveness of RPSNC.
The rest of this paper is organized as follows. Related work is covered in
Section 2. The problem definition and considered system model are described in
Section 3. The details of RPSNC are provided in
Section 4. The simulation results are presented in
Section 5. The paper is finally concluded in
Section 6.
2. Related Work
Relay nodes placement in WSNs has been used not only for restoring the connectivity, but also for improving the WSNs performance, such as WSN longevity [
17]. Given the scope of contributions of this paper, this section focuses on works which target the connectivity restoration in partitioned WSNs. Some of the published works in this category employ centralized algorithms [
18,
19], where one of the sensor nodes is in charge of generating the recovery plan and coordinating the relocation process. These approaches rely on the availability of an alternate communication path to inform other nodes on what to do. On the other hand, distributed algorithms [
20,
21] have been the preferred choice for restoring the connectivity of large networks and for repairing partitioned networks. In such a case, the sensor nodes are assumed to have some pre-failure state (e.g., k-hop) information and utilize that information to detect and recover from network partitioning. However, these algorithms may not be well suited for restoring the connectivity when the network is significantly damaged due to the fact that sensor nodes have resource and capability constraints and may not be able for a long distance move if the affected area is large. Most of the published studies on connectivity restoration in partitioned WSNs strive to restore the connectivity by carefully placing a minimum number of relay nodes in such a way that data routes are formed between each pair of terminals. As mentioned earlier, this problem is proven to be NP-Hard by Lin and Xue [
7]. They proposed a polynomial time approximation algorithm which populates relay nodes on the edges of MST of the terminals. First, the algorithm constructs a complete graph
of terminals, where
V is the set of terminals and
E is the set of all edges
, where
. Subsequently, using Kruskal’s MST algorithm, the tree edges are computed. Relay nodes are then deployed along each edge in the tree at a distance of at most
R apart, where
R is the communication range of a relay node.
Wang et al. [
22] proposed a Collaborative Connectivity Restoration Algorithm (CCRA) based on cooperative communication and node maneuverability to restore the network connectivity after multiple nodes failure. CCRA opts to simplify the recovery process by gridding. Moreover, the distance that an individual node needs to travel during the recovery process is reduced by choosing the nearest suitable candidates. Cheng et al. [
8] proposed a three-step heuristic algorithm to form ESMT with minimum Steiner points. In the first step, it connects the sensor nodes where the distance between the sensor nodes is less than or equal to
R. In the second step, it forms three-stars in that, for each subset of three sensor nodes
, there exists a point
s such that
s is at most
R units away from
u,
v and
w. In the last step, the algorithm populates relay nodes along the MST edges connecting two different connected components.
The literature works [
3,
6,
9] have studied the same problem that we tackle in this paper. In [
3], Senel and Younis presented a three-step algorithm called Federating network Segments via Triangular Steiner tree Approximation (FeSTA), which is based on the triangle Steiner method. In the first step, FeSTA finds the best triangles and forms islands of segments by establishing intra-triangle connectivity. Then, in the second step, disjoint islands of segment are federated. In the final step, the Steiner nodes of the best triangles are applied for optimization. In [
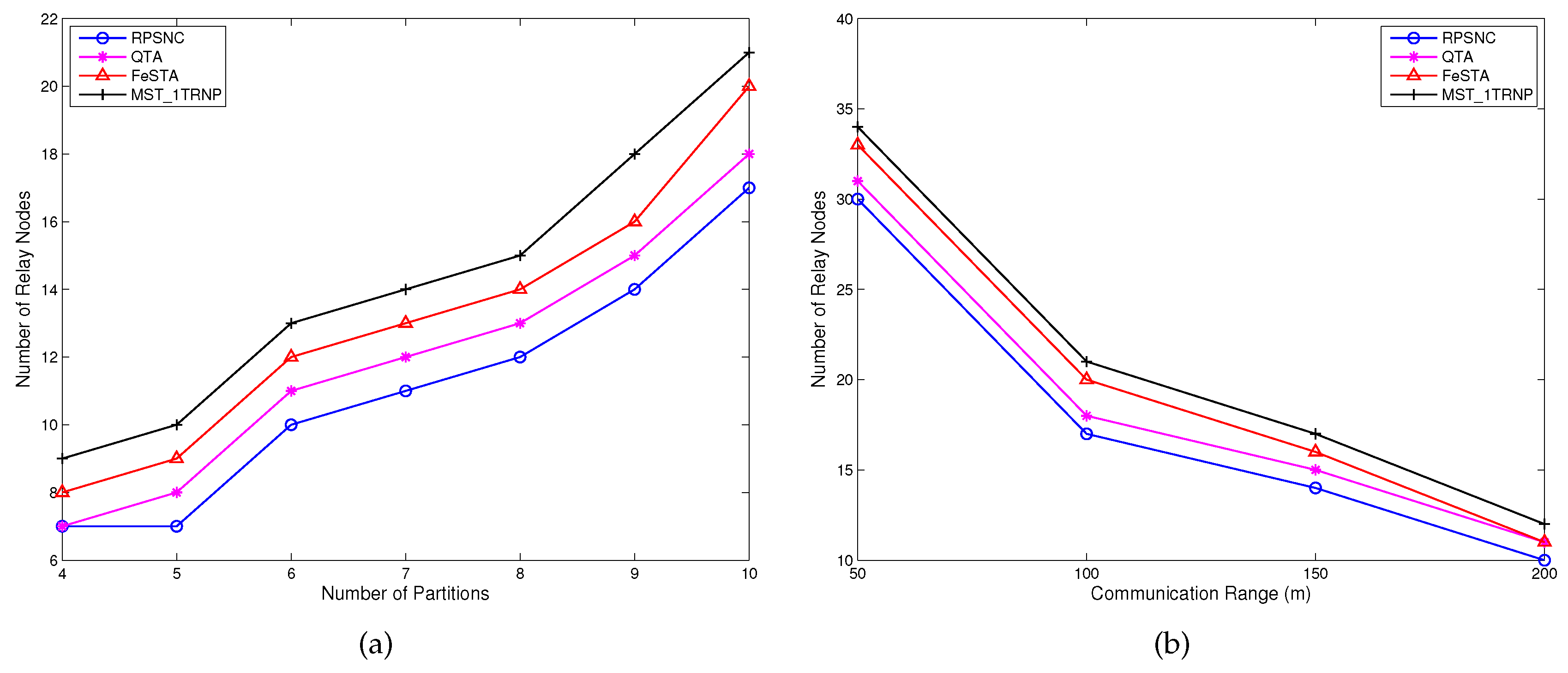
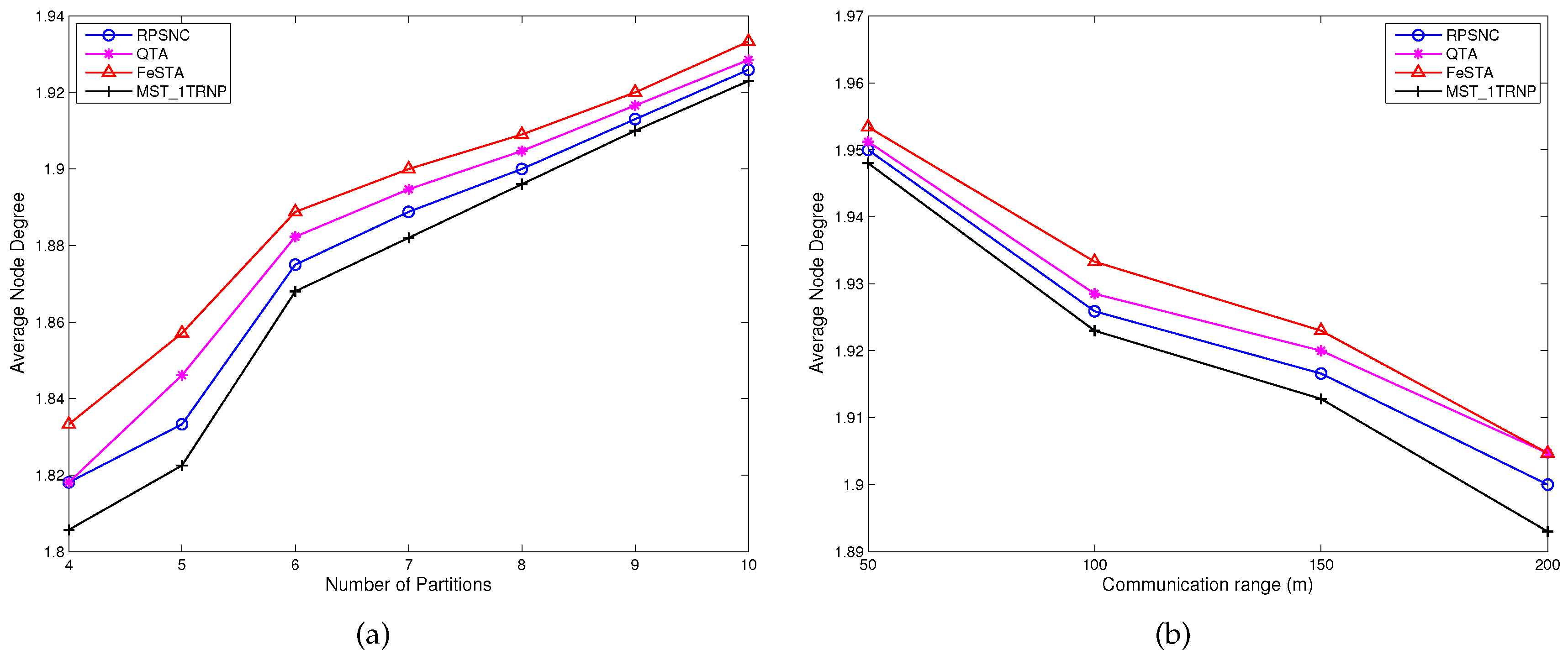
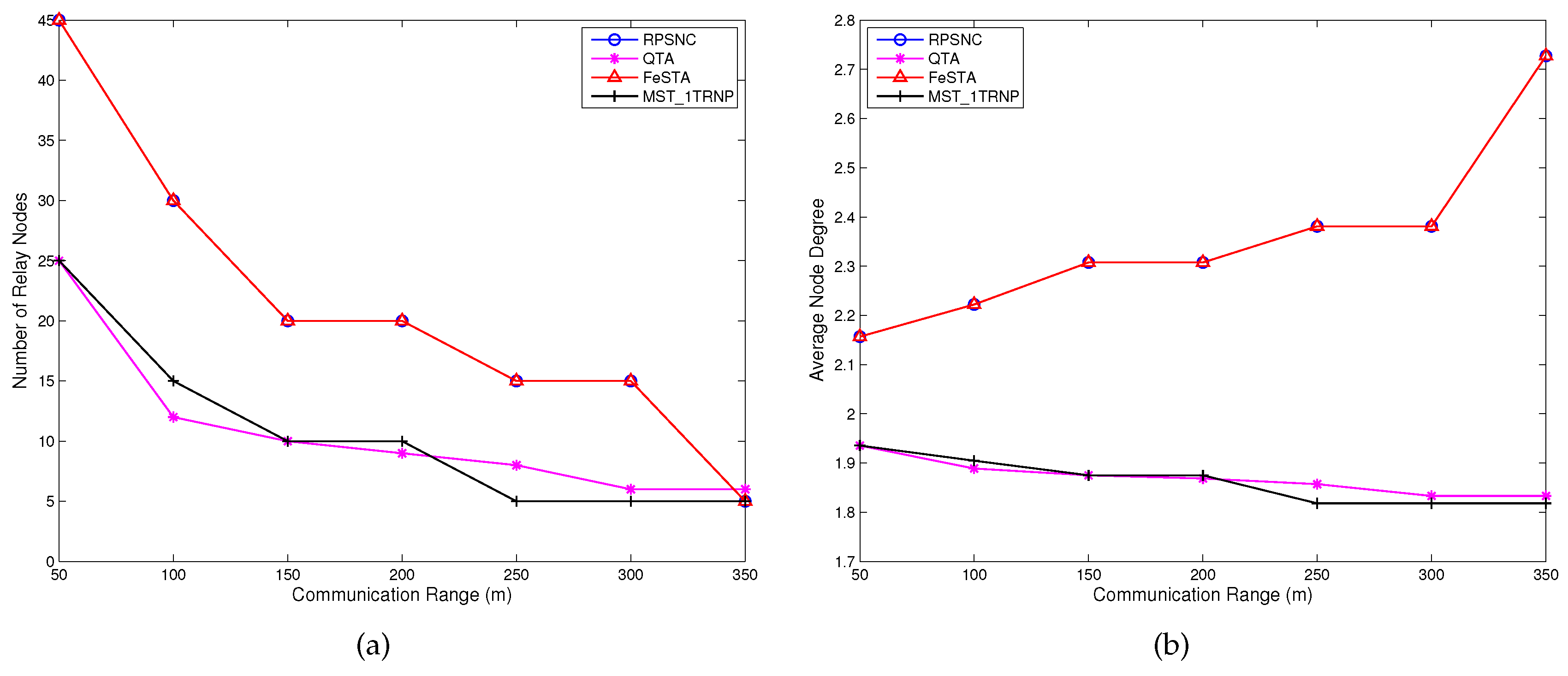
6], Chen and Shi proposed a step by step heuristic algorithm called Quadrilateral Steiner Tree Algorithm (QTA), which is based on the quadrilateral Steiner method. First, the disjointed partitions are detected and their locations are determined. Then, the appropriate quadrilaterals are selected to connect the partitions and the Steiner nodes of these quadrilaterals are found. The partitions that are not connected by the Steiner nodes of the selected quadrilaterals are connected with the MST method. Unlike FeSTA and QTA, which are based on triangle and quadrilateral Steiner methods, respectively, RPSNC is based on space network coding and takes full advantage of considering Delaunay triangles and quadrilaterals Steiner nodes. In contrast to FeSTA and QTA that connect the partitions (terminals) of WSN step by step, RPSNC connects all the partitions at once, which may enable us to reduce the number of required relay nodes. Furthermore, RPSNC significantly performs better than FeSTA and QTA, as it will be proven and confirmed later by RPSNC analysis and the simulation experiments. In [
9], Chen et al. proposed an algorithm called a Minimum Spanning Tree based on a single-Tiered Relay Node Placement (MST_1TRNP), which deploys relay nodes along MST edges of the terminals, where terminals can be considered as sensor nodes. Unlike MST_1TRNP, RPSNC finds the Delaunay triangles and concatenates two neighboring Delaunay triangles to obtain quadrilaterals. Then, RPSNC places the relay nodes at the Steiner points inside the Delaunay triangles and quadrilaterals.
The focus of [
4,
10,
11] is also on a variant of the problem of re-establishing the connectivity of a partitioned WSN, where additional metrics of relay node degree must be optimized. In [
4], Lee and Younis opt to federate the disjoint partitions in a such way that the inter-partition topology has a high node degree. They modeled the deployment area as a grid of equal-sized cells, and each network partition is assumed to be located in the middle of the cell. A Cell-based Optimized Relay node Placement (CORP) algorithm is proposed. CORP is a two-phase polynomial time algorithm. The first phase aims to iteratively identify the border terminals and the best cell to deploy a relay node. The second phase aims to connect all terminals by populating relay nodes inwards until all relay nodes become reachable to one another, after which redundant relay nodes are pruned. In [
10], Zheng et al. proposed a Partial 3-Connectivity Restoration Algorithm (P3CRA) that constructs the dual-ring topology structure to improve the quality of the formed topology. P3CRA ensures that, after the connectivity restoration, all the partitions have at least three-connectivity, and the deployed relay nodes have at least two-connectivity. In [
11], Senel et al. proposed a SpiderWeb approach that opts to re-establish the connectivity using the least number of relay nodes, while achieving a high node degree in the formed topology. As opposed to these approaches, minimizing the number of required relay nodes is the main goal for RPSNC. A comparative summary of some approaches for relay nodes placement is provided in
Table 1.
Ahmadi et al. [
24] focused on the problem of simultaneously reducing energy consumption and increasing WSN lifetime. They proposed an effective algorithm that provides greater efficiency energy consumption as it preserves the network with its low energy consumption. In a subsequent work, Naranjo et al. [
25] proposed a modified Stable Election Protocol (SEP), named Prolong-SEP (P-SEP) to prolong the stable period of Fog-supported WSNs by maintaining the balanced energy consumption. Unlike these works that are based on routing, we propose a min-cost multicast relay placement approach based on space network coding for restoring the connectivity in partitioned WSNs.
In line with space network coding, Xiahou et al. [
26] applied space network coding as a tool to design a framework for analyzing the network coding conjecture in undirected graphs.
Regarding the applications of network coding in WSNs, Wang et al. [
27] applied partial network coding for data collection in WSNs operating in harsh environments. Rout and Ghosh [
28] proposed a network coding based communication algorithm to improve the WSN lifetime. Eritmen and Keskinoz [
29] proposed a signature selection and relay power allocation method based on network coding that significantly improves the throughput of WSNs that operate over non-orthogonal channels. Ayday et al. [
30] proposed a network coding based protocol called Location-Aware Network-Coding Security (LANCS) that provides security services such as data confidentiality, authenticity, and availability in WSNs.
However, to the best of our knowledge, space network coding has not been applied for connectivity restoration in WSNs. Our work is different from the above works in a significant aspect: we introduce a new min-cost multicast space network coding approach that aims to solve the problem of restoring the network connectivity in partitioned WSNs.
3. Problem Statement and Fundamental Definitions
In the context of this paper, a WSN is a set of sensors scattered in an area of interest to detect and track some events. We consider a WSN that has been split into multiple disjoint partitions due to a major scale damage in a part of the network, e.g., inflicted by explosives in a battlefield. We strive to restore the partitioned network by linking the disconnected partitions. A sensor is battery-operated and has limited communication and processing capabilities. We assume that sensors are stationary, which is typical for WSNs. All communication is over a single shared wireless channel. A wireless link can be established between a pair of sensor nodes if they are within the communication range R of each other.
A relay node is a more powerful node with significantly more energy reserve, longer transmission range and richer processing capabilities than sensors. Although relay nodes can be equipped with sensing circuitry, they mainly perform data aggregation and forwarding. Unlike sensors, relay nodes can be mobile and have some navigation capabilities. Relay nodes are favored in the recovery process since it is easier to accurately place them relative to sensors and their communication range is larger, which facilitate and expedite the connectivity restoration among the disjoint partitions. Intuitively, relay nodes are more expensive and consequently the main objective of this paper is to minimize the required number of relay nodes. In this paper, it is assumed that all deployed relay nodes have the same communication range “R”.
The problem that we study in this paper can be formally defined as follows: “Given disjoint partitions of a WSN, find the minimum number and optimal positions of required relay nodes for restoring inter-partitions connectivity”. This problem is challenging in that we need to compute not only the number of optimal relay nodes and the geometric location of each optimal relay node, but also the best way of connecting them with terminals to achieve the optimal solutions. As mentioned earlier, we assume that each partition is represented by a sensor node, which we call terminal. Each terminal connects a partition to the resulting topology and plays a role of gateway after restoration. In the context of this paper, a partition is a connected set of sensor nodes, denoted as .
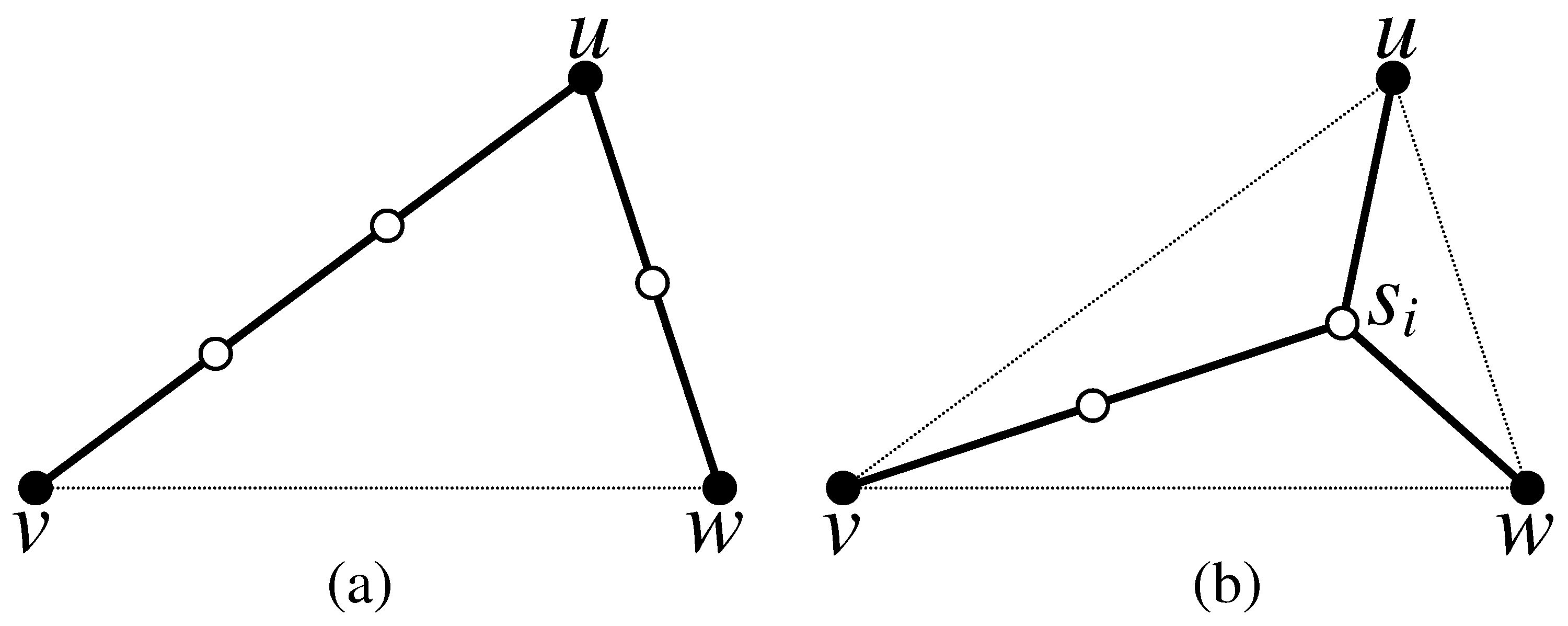
Definition 1. Let N denotes the planar points. The Voronoi diagram of N partitions the plane into regions, called Voronoi regions, such that each point lies in exactly one region. The Voronoi polygon of a point , denoted as , consists of all points in the plane for which is the closest point among all other points. The collection of Voronoi polygons for each is called Voronoi diagram . The Delaunay triangulation is the planar straight line dual graph of Voronoi diagram [31]. Definition 2. The number of relay nodes required for connecting two terminals u and v is called the of the edge and denoted aswhere is the Euclidean distance between u and v, and R is the communication range of relay nodes. Definition 3. Let be a triangle and p be an arbitrary point inside . The number of relay nodes required to connect the vertices of at p is called the of at p and it is denoted as . Basically, a relay node will be placed at p and then connected to the vertices and w by placing the relay nodes on the edges , and , respectively. Thus, Definition 4. The point that minimizes the of the triangle is called the Steiner point and the weight at the Steiner point is called the of and denoted as , or simply . The Steiner point can be formally defined as follows: If we multiply Equation (
2) by “R” after removing the ceiling brackets, it follows that the minimization becomes linear in terms of distance. There are only two possible ways to achieve the optimal solution for connecting the three terminals
u,
v, and
w of the triangle
: (1) via Steinerizing the two smallest edges of
as depicted in
Figure 2a, which is equivalent to constructing the Steinerized MST for the three terminals; (2) via finding the Steiner point
of
and Steinerizing the edges
,
and
, as depicted in
Figure 2b, where
.
Theorem 1. The optimal solution for connecting three terminals and w of a triangle can be achieved either via Steinerizing the two smallest edges of or Steinerizing the edges from its vertices to the Steiner point .
Proof. The proof of this theorem involves two cases:
Case 1: All relay nodes in the optimal solution lie on the edges joining the pairs of terminals. This case is straightforward and applicable only if there is no such point inside the triangle that provides a better solution.
Case 2: There is a relay node inside the triangle
that connects all pairs of terminals in the optimal solution. From Definition 4, it is known that such a relay node is located at the Steiner point
of
. As a result of finding the Steiner point
of the triangle
, three sub-triangles namely
,
and
are formed. In order to obtain a solution for connecting the terminals
and
w of the triangle
via
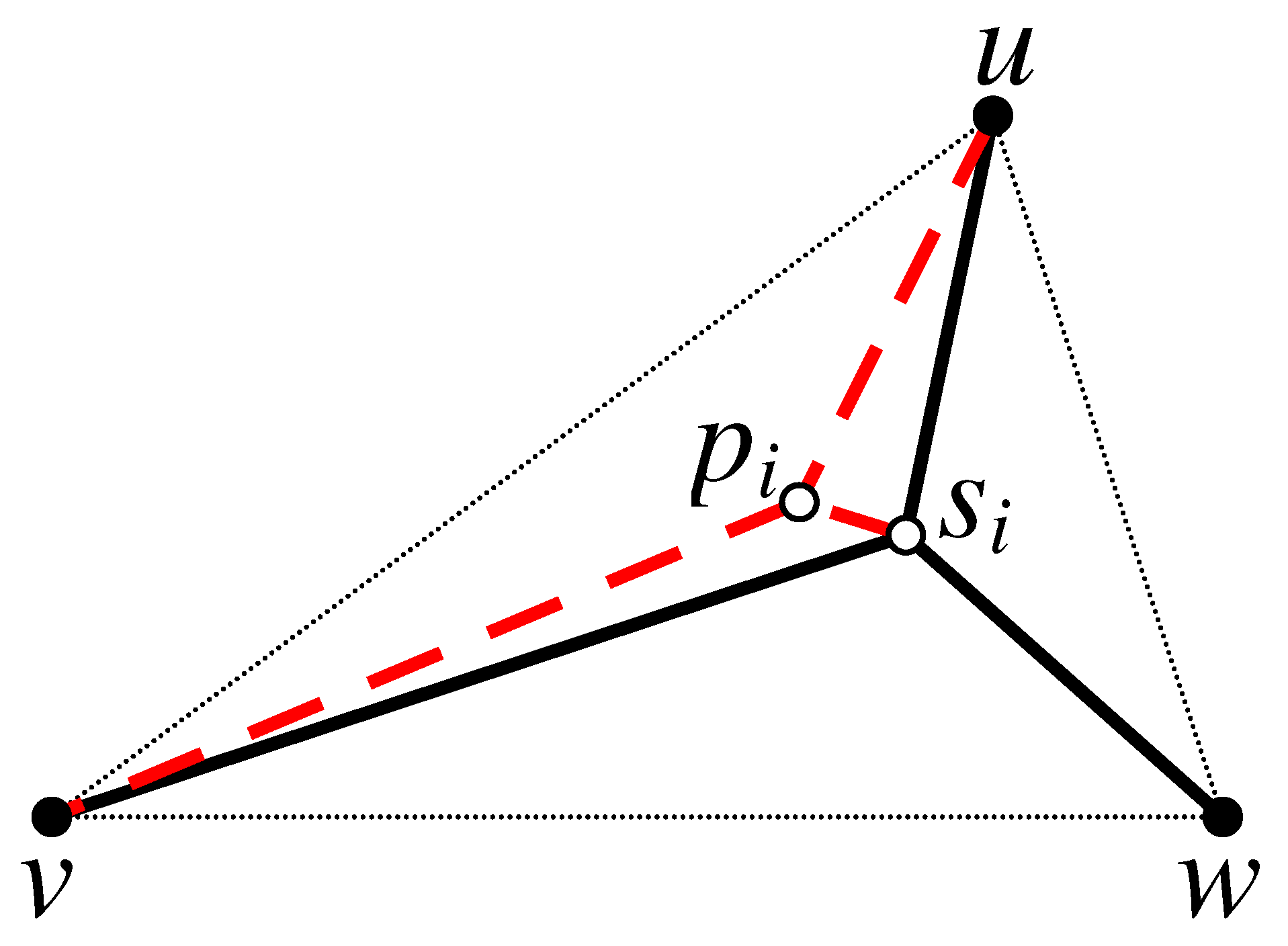
, we first need to find the Steinerized MST for each of these sub-triangles. In order to prove the optimality, we need to show that the Steinerized MST is the optimal solution for the sub-triangles. We pursue our proof by way of contradiction. Assume that connecting the terminals of a sub-triangle, let say for instance
, via an internal point
yields a better solution than Steinerizing the two smallest edges of
, as illustrated in
Figure 3. Based on this assumption, we can write the following expressions:
Applying the triangular inequality on
we get
Then,
and, hence,
After connecting the terminals
u,
and
v of the sub-triangle
via an internal point
, the total number of relay nodes required for connecting the terminals
u,
v and
w of the triangle
is the sum of
of the edges
,
,
,
plus 2 (due to the two points
and
). Therefore,
Using Equation (
4), we get
Based on Definition 3,
is the
of the triangle
at point
, and it is denoted as
. Consequently, Equation (
5) becomes
Using Equation (
3), we can write
From Equations (6) and (7), we have
. However, this is a contradiction since the definition of a Steiner point
implies that
is minimal and cannot be greater than
. Therefore,
of
must be equal to
, which is equivalent to constructing the Steinerized MST for the sub-triangle
. The same proof can be applied to
and
. To complete our proof, it is worth noting that if we simultaneously consider Steinerizing two of the three sub-triangles via the Steiner point
, the resulting topology will not be cycle-free. Thus, we can conclude that considering two (or three) sub-triangles simultaneously will increase the required number of relay nodes and hence provide no benefit to the solution. ☐
Theorem 1 suggests that RPSNC optimally solves the problem of re-establishing the network connectivity for the case of three terminals. It is challenging to design an optimal algorithm for re-establishing the network connectivity for larger networks because, as we mentioned earlier, the problem is NP-hard.
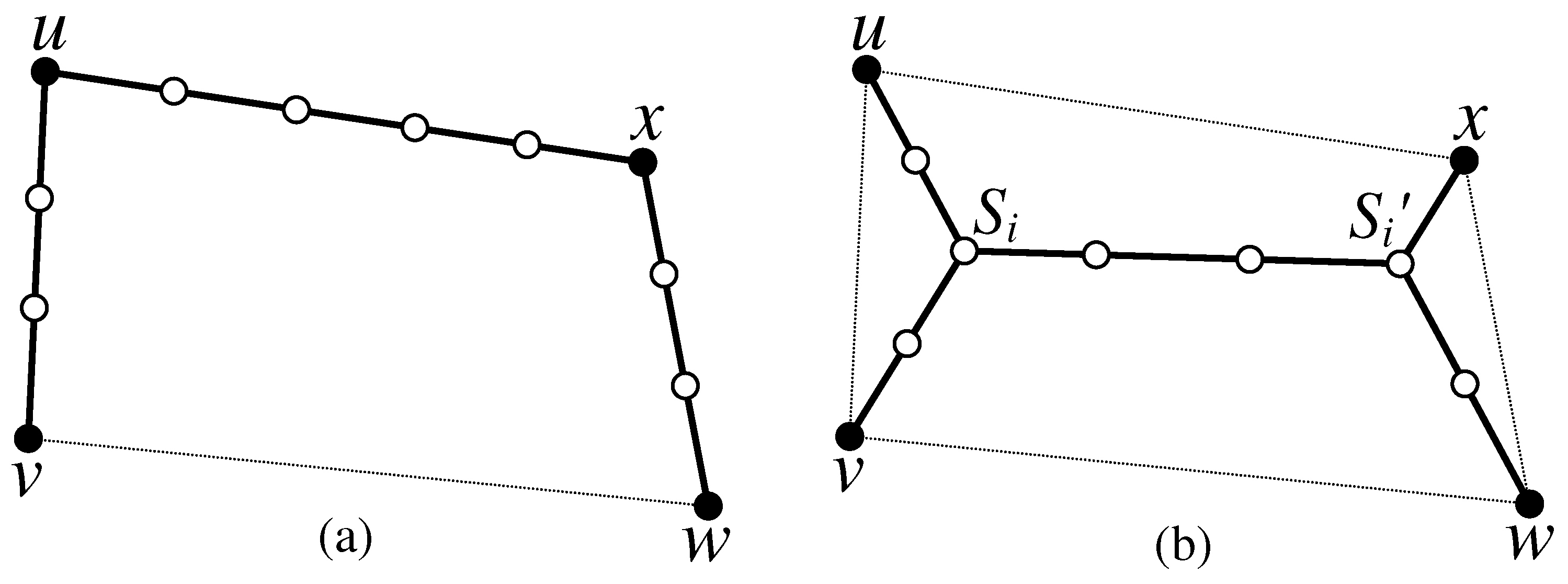
Definition 5. Let be a quadrilateral. There are two possible solutions for connecting the four terminals u, v, w and x of : (1) via Steinerizing the three smallest edges of as depicted in Figure 4a, which is equivalent to constructing the Steinerized MST for the four terminals; (2) via finding the Steiner points and of and Steinerizing the edges , , , and , as depicted in Figure 4b, where . Definition 6. The number of relay nodes required for connecting the terminals of a quadrilateral by forming MST of these terminals, as depicted in Figure 4a, is called the MST-Weight of , denoted as , and computed aswhere R is the communication range of a relay node. Definition 7. The number of relay nodes required for connecting the terminals of a quadrilateral via the Steiner points and , as illustrated in Figure 4b is called the C-weight of , denoted as and computed as