In this section, we will firstly evaluate the performance of the proposed clustering strategy from the perspectives of stability, efficiency and computation cost. The existing schemes, such as MOBIC [
23], EnLOSC [
28] and our previous scheme CG-bCS [
33], are implemented as a comparison to analyze the performance of our strategy, CG-SECC. Besides, we also give a case study to illustrate the security of the reputation-based incentive and penalty mechanism.
7.1. Numerical Evaluation
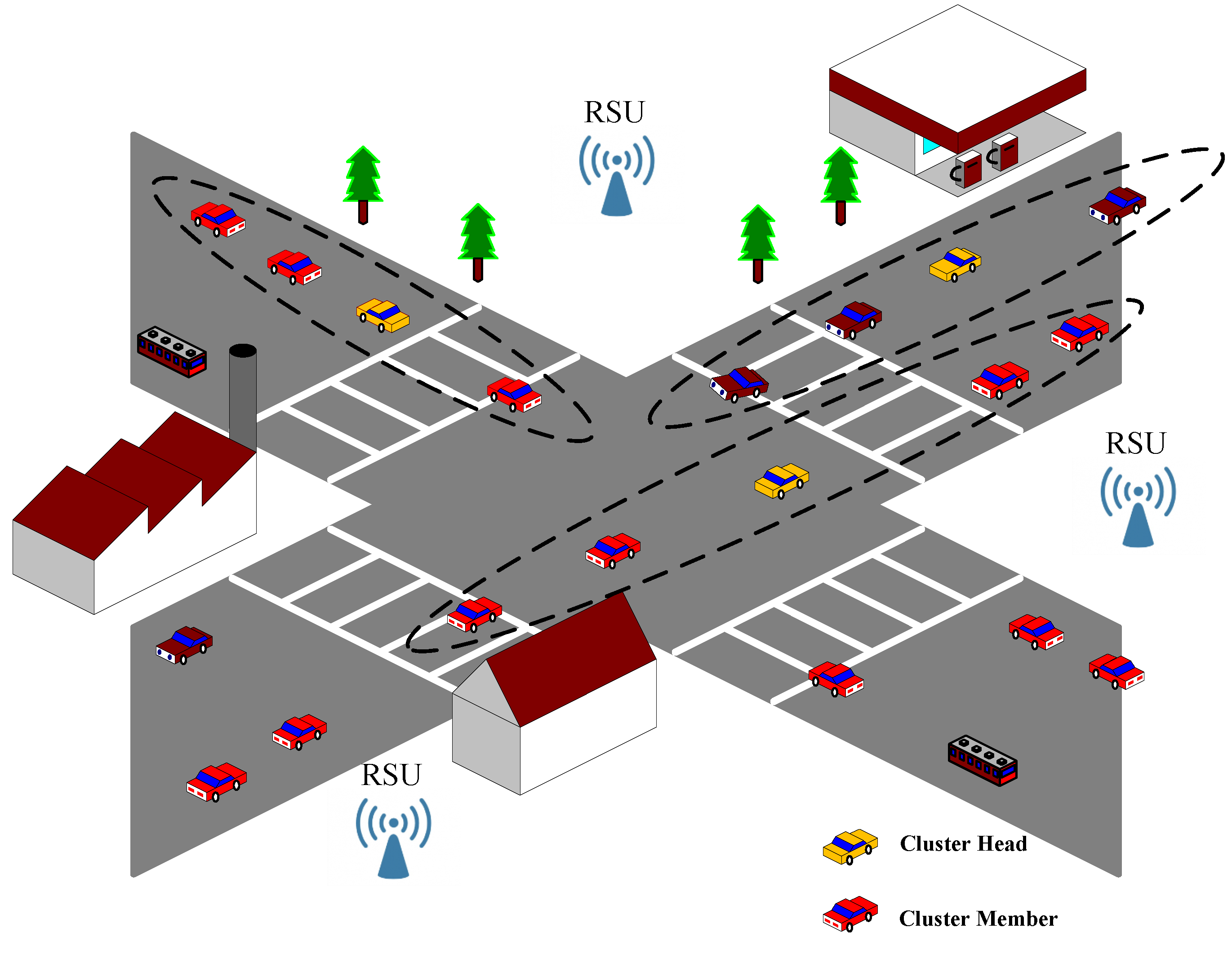
The simulation scenario is a two-lane crossroad, as shown in
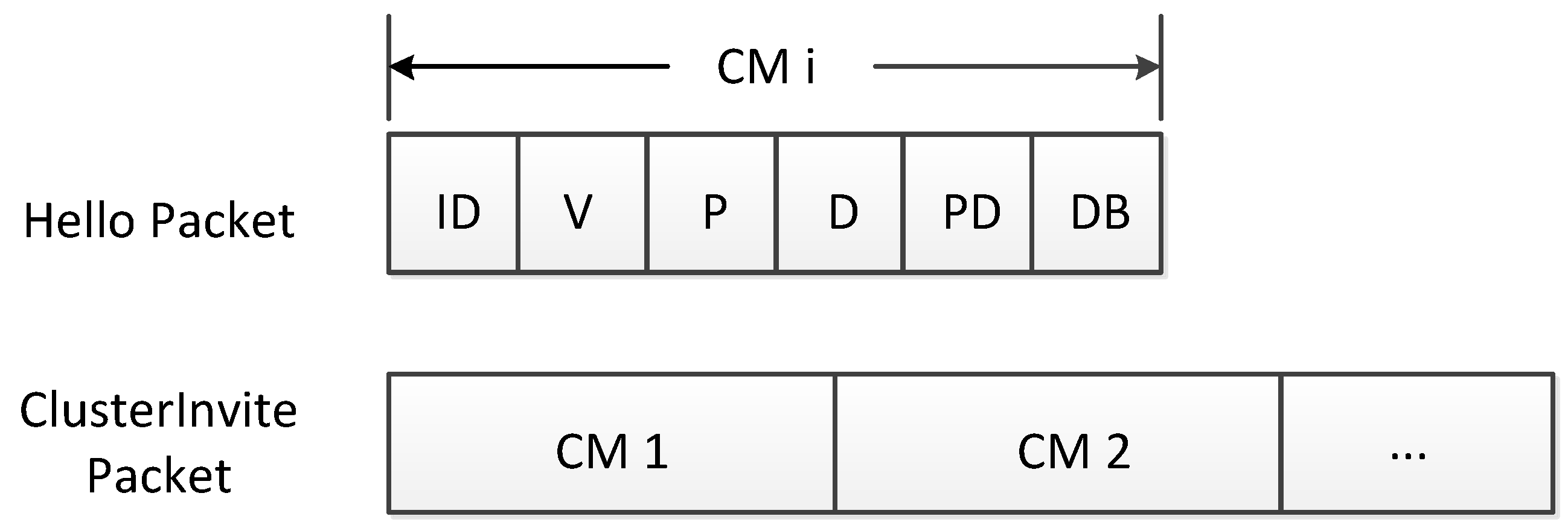
Figure 1. A variety of packets shown in
Figure 2, containing self information of every node in VCPS, can be broadcast, forwarded and shared among vehicles. For more practical considerations, the number of vehicles is set up from 20 to 250, and the vehicle speed range is selected randomly between 0 km/h and 36 km/h; the provided available bandwidth and the demand bandwidth are defined as 10∼50 Mbit/s and 1∼10 Mbit/s, respectively. Besides, the communication radius
D is 100 m, and the threshold
to identify whether a node can be considered as a cluster head is 10.
Unlike the fast-changing highway scenario, we can adopt the classification method instead of machine learning to reduce the computation delay for obtaining appropriate
,
and
a due to the stable traffic flow in our system model (i.e., the steady and low-speed moving in the crossroad [
43]). In that case, we can ignore the delay caused by the the parameters selection in (
8). Here, the initial
and
are setup as one and
, while the initial
a is denoted as
, to conduct a similar simulation scenario as in [
33] in terms of the velocity and the vehicles’ position. When the clustering performance degrades dramatically, the coefficients values of the utility must be adjusted based on the classification method in
Section 4 to satisfy the changeable environment.
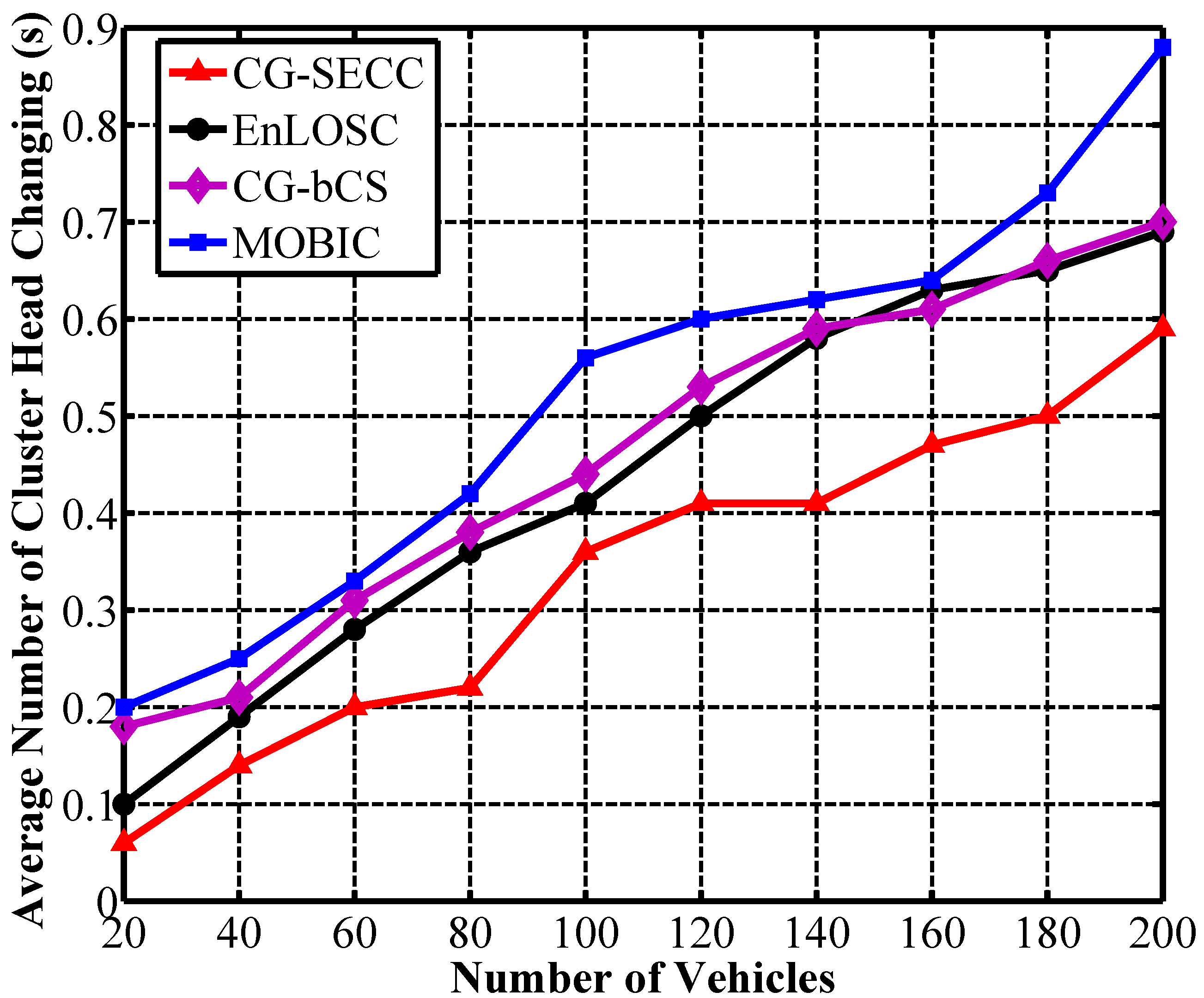
Figure 5 shows the performance of clustering stability represented by the average number of cluster heads changing per second. Obviously, the cluster-based communication network will not be stable if the value is large. Among the four algorithms, CG-bCS, EnLOSC and our proposed strategy can obtain more stable clusters than the MOBIC scheme due to the election of proper clustering heads. Besides, in comparison with CG-bCS and EnLOSC from
Figure 5, the number of CH handoffs in CG-SECC is fewer, which represents higher clustering stability. The reason for the improvement of clustering stability is the application of the nodes’ mobility criterion. Moreover, the better stability also indicates that the proposed strategy in this paper can solve the frequently changeable network topology challenges causing by the nodes’ high mobility. In other words, the proposed strategy demonstrates the high stability so as to be more suitable for the crossroad scenario in VCPS.
For the purpose of illustrating the efficiency of clusters, we explore average throughput per vehicle in
Figure 6. Obviously, the cluster is efficient if this average value is large. The average throughput of every vehicle is merely equal when the vehicle density is low, because the provided available bandwidth from cluster heads is enough for the requirements of all members. Once the density is high, however, the overload issue for cluster heads may frequently occur. Depicted in
Figure 6, apparently, the average throughput is the lowest in MOBIC. The result represents that we may lose efficiency due to the overload of the cluster head if we consider only the stability of the cluster. In other words, the algorithm considering the overhead of the cluster head is especially necessary. In addition, we can also learn that the cluster efficiency of both CG-bCS and the proposed strategy is higher than that of EnLOSC, which illustrates that clustering strategies can precisely decrease the cluster heads’ overhead through the bandwidth on demand method. Moreover, comparing with CG-bCS, CG-SECC has a slightly lower clustering efficiency. This is due to the cost of the clustering stability and the reduced calculation. In other words, when we use the two criteria in
Section 5.3 for finding potential heads to decrease the calculation for nodes, we may not obtain the optimal clustering structure, which finally results in the slightly lower efficiency of clusters.
Due to the frequently changing topology structure of VCPS, the computation complexity for clustering formation should be adaptive to reduce the end-to-end delay.
Figure 7 provides the computation delay for clustering formation and maintenance using CG-SECC and EnLOSC. Note that we omit the computational analysis of MOBIC because of its weak performance in the aspect of cluster stability and the average throughput. In
Figure 7, we learn that the computational delay in CG-SECC is adaptive, but larger than that in EnLOSC, which is clearer along with the increasing number of vehicles. However, this increased delay is the cost of the improvement of stability and efficiency for the clustering structure. In other words, in order to prolong the lifetime of a cluster, we surely need a more stable and efficient clustering structure.
Moreover, we also demonstrate the computational complexity between CG-bCS and the proposed strategy.
Table 1 shows the analysis of the iteration times when the number of vehicles,
N, increases. Obviously, the number of iterations for these two algorithm is small when there are only a few vehicles in the crossroads (i.e.,
N is small), because of the limited cooperation possibility. Furthermore, we can conclude that the number of iterations that CG-SECC needs to converge is much smaller than that of CG-bCS. This is owing to the use of two criteria for finding potential heads, which sharply decreases the cluster heads with which nodes want to cooperate.
Actually, the main complexity of the clustering maintenance scheme is caused by both the amount of computation in one iteration and the number of iterations. To compare the complexity between CG-bCS and the scheme in this paper, we consider the following two aspects. On the one hand, we suppose the common pseudocode from Line 8 to Line 13 in Algorithm 4 for electing the cluster head and utility calculation as a unit of calculation, called the Inner Loop Part (ILP). Accordingly, in each iteration of CG-bCS, the complexity of cluster maintenance can be represented as
. Similarly in CG-SECC, the main complexity of the clustering maintenance is represented as
. Obviously, the number of nodes in
is definitely more than
. Thus, the complexity of the strategy in this paper is lower than CG-bCS. On the other hand, due to the lesser number of iterations of CG-SECC shown in
Table 1, the amount of computation in CG-SECC is reduced greatly. All in all, although the proposed strategy may not create the coalition structure with optimal efficiency, it can implement fast clustering with the average throughput similar to CG-bCS.
Through these three numerical evaluations and analysis, we can conclude that the proposed strategy with the lower number of iterations is more adaptive to obtain the clustering structure in the crossroads.
7.2. Case Study
The security problem in VCPS has already been studied in the past. In [
42], a Bayesian coalition game-based reliable data transmission was proposed for the vehicular cloud, which focused on the packet delivery ratio, end-to-end delay and reliable data transmission. Then, they also exploited a new approach, named VDDZ, to protect the CA in the cluster from direct communications and attacks from unknown vehicles in [
40]. Although these studies could ensure the data consistency and legitimacy enforcement of messages, both of them cannot keep the malicious nodes from falsely declaring their transmission capacity. In fact, the reputation-based incentive and penalty mechanism proposed in
Section 6 is not only aware of and deals with such malicious nodes, but also enhances the effectiveness of the clustering structure. To evaluate the proposed incentive and penalty mechanism, this section exploits a case study to analyze the related secure performance.
Figure 8 provides two existing clusters (C1 and C2) with the determined CHs (V1 and V5). Here, we suppose that the provided bandwidth of V1 is 12 Mbps, and the demands of the nodes in C1 (i.e., V1, V2, V3 and V4) are 1, 2, 3 and 4 Mbps. Such a bandwidth will be used for knowing the road traffic condition, accident prevention, payment services or entertainment applications. Furthermore, V7 in C2 is assumed as a malicious one. In other words, V7 can only provide an 8-Mbps bandwidth, but it will report the fake bandwidth capability for the purpose of becoming the CH and obtaining better reputation.
We first analyze the security in the existing cluster (e.g., C1). Supposing that V2 acts as a malicious node, it will send an accusation packet to the RSU to replace V1 as the new cluster head. Obviously, such selfish behavior will heavily decrease the current cluster’s efficiency. Thus, we can exploit the reputation-based incentive and penalty mechanism to effectively prevent this from happening. In that case, the final reputation table of all of these nodes is depicted in
Table 2.
Next, once the PHL of the malicious vehicle (V7) includes V1, it will broadcast its fraud bandwidth capability (e.g., 13 Mbps) in its Hello packet to contend to be selected as a cluster head so as to obtain higher reputation. As mentioned previously in
Section 5, V7 will have the opportunity to replace V1 as the next cluster head. Obviously, the bandwidth V7 provides must not satisfy the total demand of the nodes in C1, which will cause the degradation of the clustering communication. Particularly, some CMs (e.g., V2) in the cluster cannot complete their information transmission. Thus, we start the incentive and penalty mechanism. Namely, V2 will send an Accusation packet to the adjacent RSU to report the fraud capability of V7. After detecting the real provided bandwidth of V7 by the adjacent RSU, the final reputations of every node in C1 are listed in
Table 3.
Without using the reputation-based incentive and penalty mechanism, in fact, the real average throughput of every vehicle in C1 is only 1.6 Mbps, while that value after adopting the mechanism will be up to 2.4 Mbps. Note that different cases can be handled in the same way.
In other words, this case study aims at verifying whether our mechanism could (1) detect and isolates malicious nodes and (2) improve the clusters performance. According to the above analysis, we learn that the reputation of malicious nodes is set as −1 and that the value of cluster heads is rewarded as +1. Besides, we can conclude that the reputation-based incentive and penalty mechanism will improve the average throughput of the cluster.