Differential Characteristics Based Iterative Multiuser Detection for Wireless Sensor Networks
Abstract
:1. Introduction
2. Several Multiuser Detection Methods for DS-UWB Systems
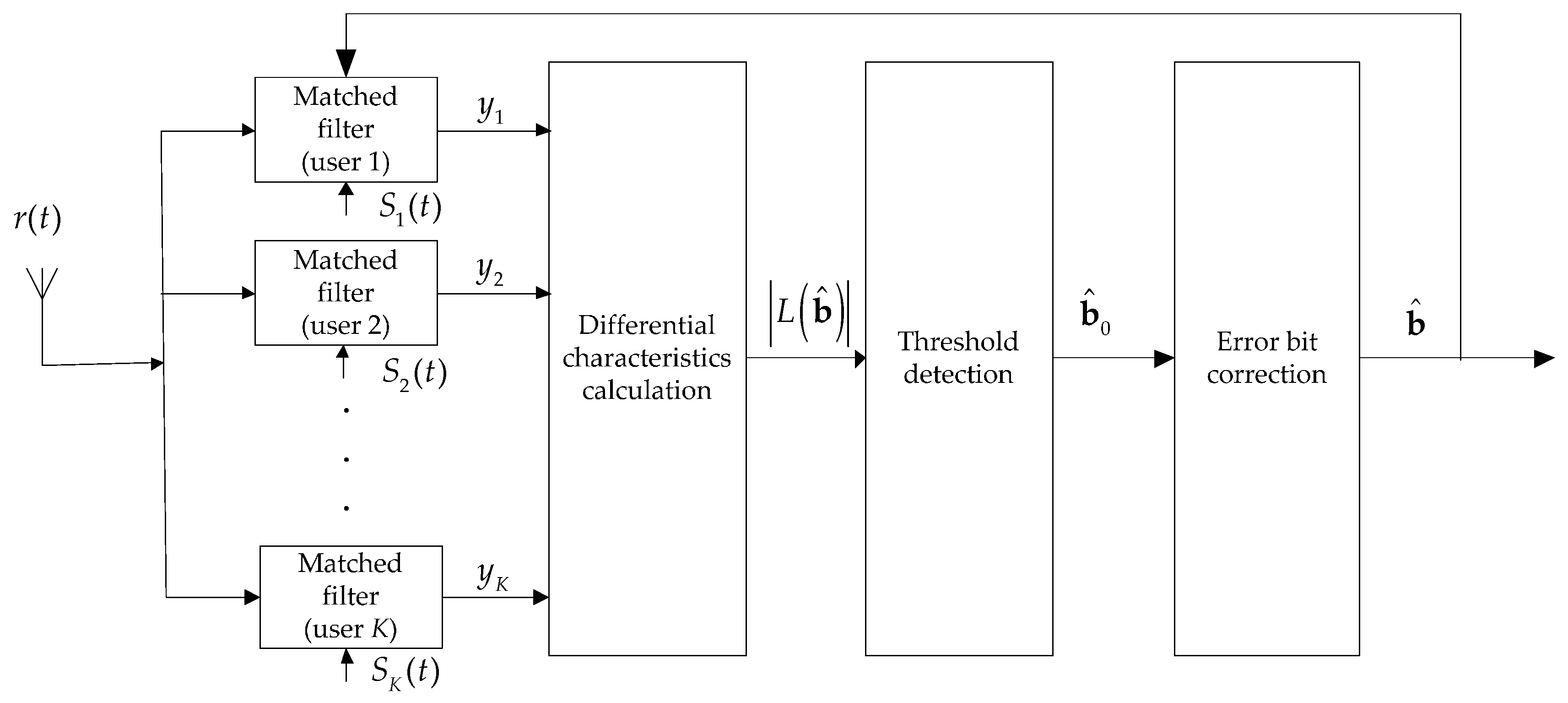
3. Multiuser Detection Based on Differential Characteristics
3.1. Differential Characteristics Calculation
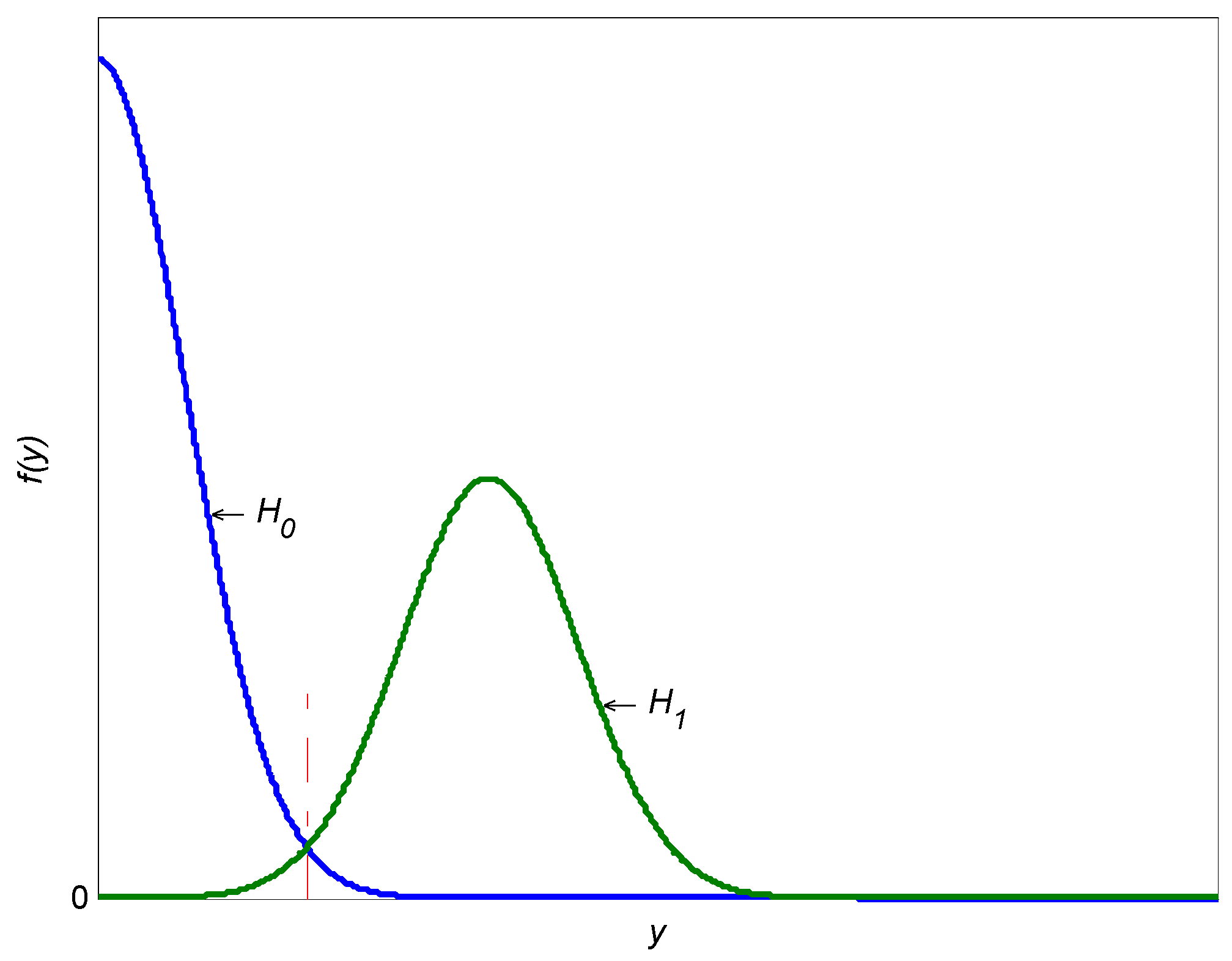
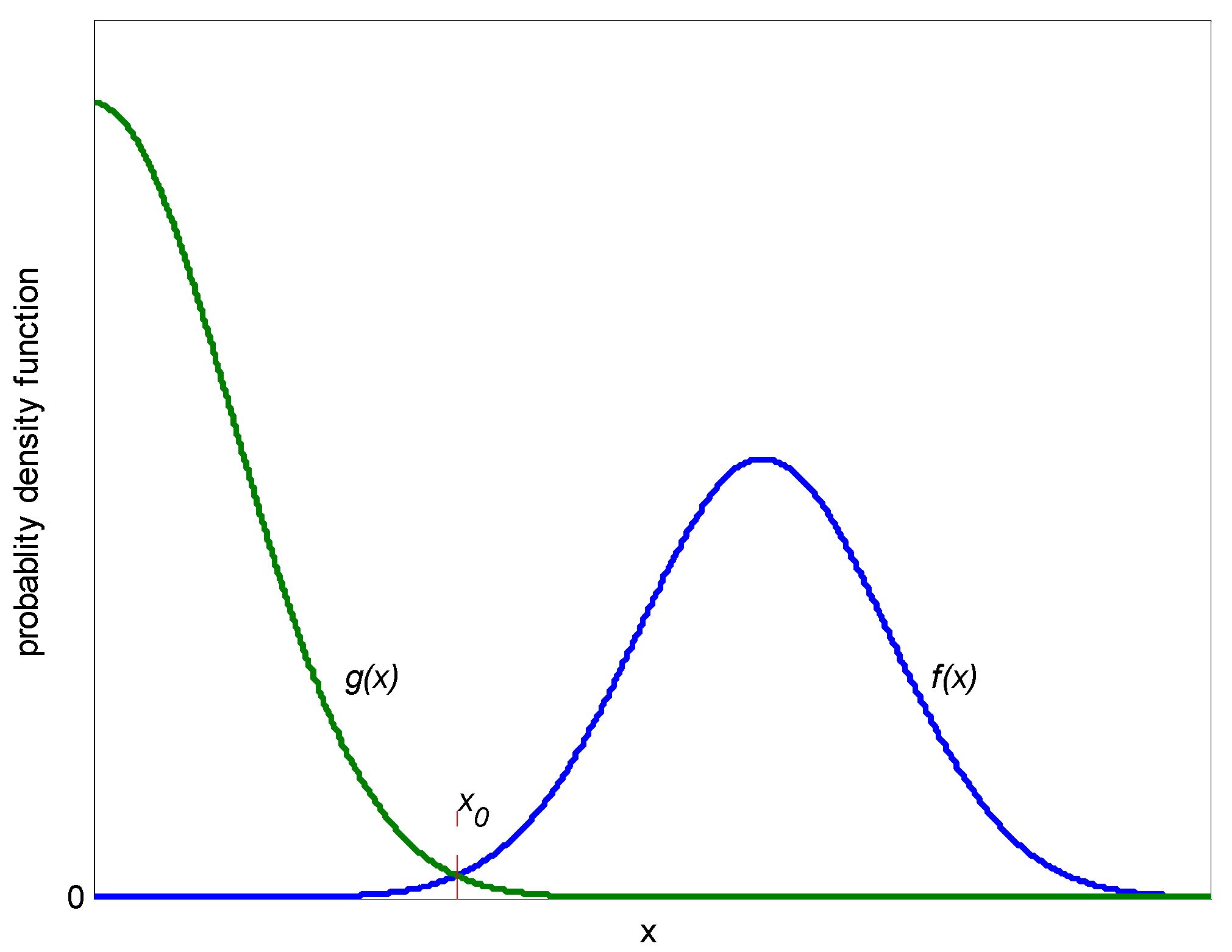
3.2. Preliminary Threshold Detection
3.3. Error Bit Correction
4. Simulation Results and Discussions
4.1. Number of Iterations
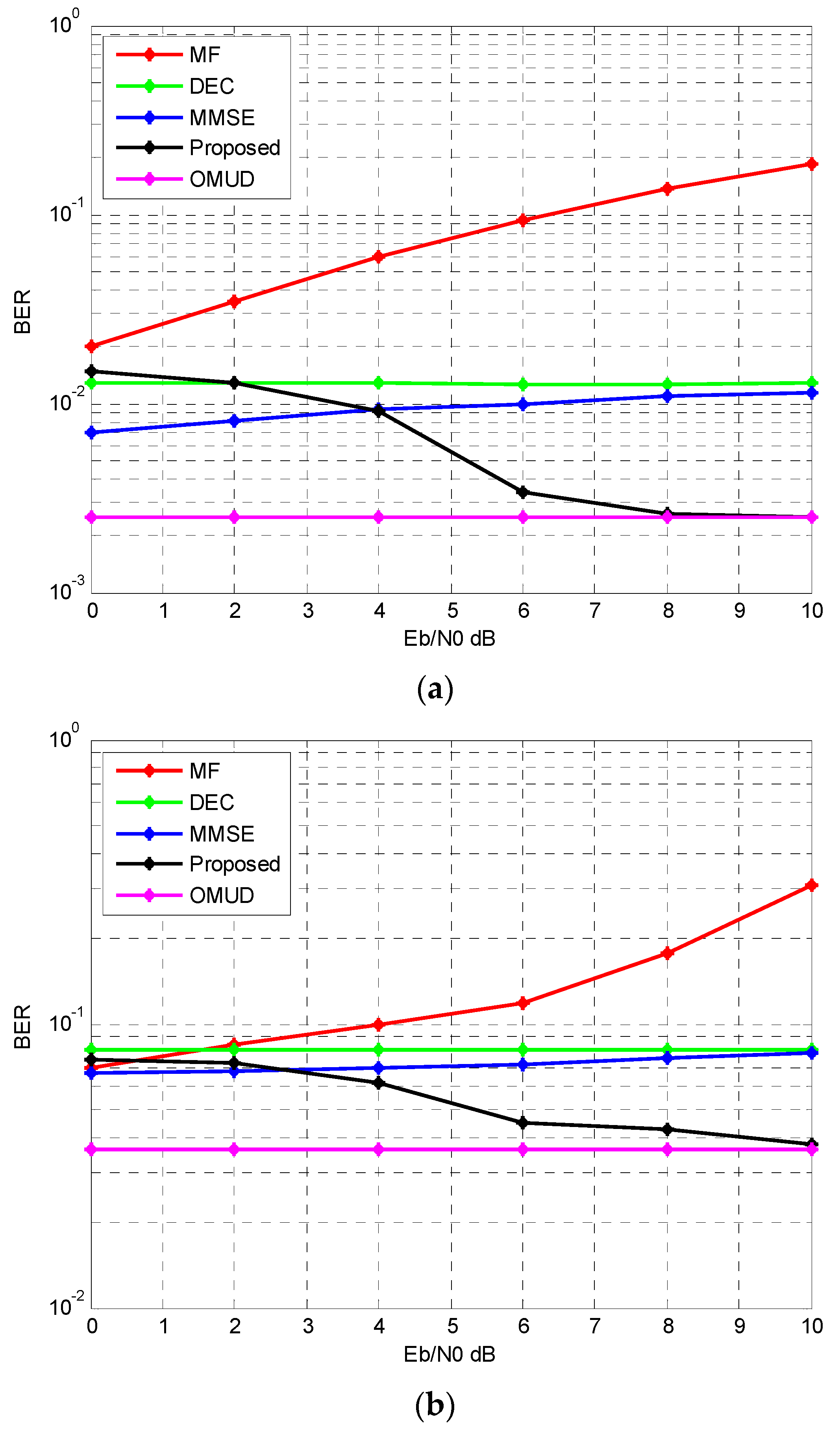
4.2. BER Performances of Different Eb/N0
4.3. Near-Far Effect Resistance Performance Comparison
4.4. User Capacity Performance Comparison
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Aseri, T.C. Comparison of routing protocols in wireless sensor network using mobile sink—A survey. In Proceedings of the 2014 Recent Advances in Engineering and Computational Sciences (RAECS), Chandigarh, India, 6–8 March 2014; pp. 1–4.
- El-Nasr, M.A.; Shaban, H. Low-power and reliable communications for UWB-based wireless monitoring sensor networks in underground mine tunnels. Int. J. Distrib. Sens. Netw. 2015, 2015, 48. [Google Scholar] [CrossRef]
- Botteron, C.; Briand, D.; Mishra, B.; Tasselli, G.; Janphuang, P.; Haug, F.-J.; Skrivervik, A.; Lockhart, R.; Robert, C.; de Rooij, N.F.; et al. A low-cost UWB sensor node powered by a piezoelectric harvester or solar cells. Sens. Actuators 2016, A239, 127–136. [Google Scholar] [CrossRef]
- Slottke, E.; Kuhn, M.; Wittneben, A.; Luecken, H.; Cartalemi, C. UWB marine engine telemetry sensor networks enabling reliable low-complexity communication. In Proceedings of the 2015 IEEE 82nd Vehicular Technology Conference, Boston, MA, USA, 6–9 September 2015.
- Neuhold, D.; Schmidt, J.F.; Bettstetter, C.; Klaue, J.; Schupke, D. Experiments with UWB aircraft sensor networks. In Proceedings of the 2016 IEEE Conference on Computer Communications Workshops, San Francisco, CA, USA, 10–15 April 2016.
- Wang, L.; Heng, C.H.; Lian, Y. A sub-GHz mostly digital impulse radio UWB transceiver for wireless body sensor networks. IEEE J. Emerg. Sel. Top. Circuits Syst. 2014, 3, 344–353. [Google Scholar] [CrossRef]
- Verdu, S. Minimum probability of error for asynchronous Gaussian multiple-access channels. IEEE Trans. Inf. Theory 1986, 32, 85–96. [Google Scholar] [CrossRef]
- Li, J.Y.; Gang, W.; Chen, F.J. On minimum-BER linear multiuser detection for DS-CDMA channels. IEEE Trans. Signal Process. 2007, 55, 1053–1103. [Google Scholar] [CrossRef]
- Steiner, A.; Lupu, V.; Katz, U.; Shamai, S. The spectral efficiency of successive cancellation with linear multiuser detection for randomly spread CDMA. IEEE Trans. Signal Process. 2012, 58, 2850–2873. [Google Scholar] [CrossRef]
- Hu, L.; Zhou, X.Y.; Zhang, L.W. Blind multiuser detection based on Tikhonov regularization. IEEE Commun. Lett. 2011, 15, 482–484. [Google Scholar]
- Muhammad, Z.; Ding, Z. Blind multiuser detection for synchronous high rate space-time block coded transmission. IEEE Trans. Wirel. Commun. 2011, 10, 2171–2185. [Google Scholar] [CrossRef]
- Saberali, S.M.; Amindavar, H. Low-complexity ad-hoc non-linearities for blind multiuser detection of long-code code-division multiple access signals and asymptotic performance evaluation. IET Commun. 2014, 8, 1527–1533. [Google Scholar] [CrossRef]
- Ali, I.; Kim, D.N.; Song, Y.J.; Azeemi, N.Z. A novel subspace tracking algorithm and its application to blind multiuser detection in cellular CDMA systems. J. Commun. Netw. 2010, 12, 216–221. [Google Scholar] [CrossRef]
- He, F.; Gunawan, E.; Guan, Y.L.; Zheng, L.H. Improved two-stage CMA-based blind receivers for joint equalisation and multiuser detection. IET Commun. 2012, 6, 1131–1136. [Google Scholar] [CrossRef]
- Stuwart, S.L.; Selvi, S.T. Precoder based collaborative blind multiuser detection of CDMA signals. Wirel. Pers. Commun. 2015, 83, 135–148. [Google Scholar] [CrossRef]
- Albataineh, Z.; Salem, F. Robust blind multiuser detection algorithm using fourth-order cumulant matrices. Circ. Syst. Signal Process. 2015, 34, 2577–2595. [Google Scholar] [CrossRef]
- Seo, B. SINR lower bound based multiuser detector for uplink MC-CDMA systems with residual frequency offset. IEEE Commun. Lett. 2012, 16, 1612–1615. [Google Scholar] [CrossRef]
- Quan, Z.; Liu, J. Efficient multiuser detector based on box-constrained deregularization and its FPGA design. J. Syst. Eng. Electron. 2012, 23, 179–187. [Google Scholar] [CrossRef]
- Shim, B.; Song, B. Multiuser detection via compressing sensing. IEEE Commun. Lett. 2012, 16, 972–974. [Google Scholar] [CrossRef]
- Zahedi, A.; Rajamand, S.; Jafari, S.; Rajati, M.R. A novel multiuser detector based on restricted search space and depth-first search method in DS/CDMA communication system. Wirel. Pers. Commun. 2015, 82, 1531–1545. [Google Scholar] [CrossRef]
- Gu, Y.B.; Yang, M.L.; Shi, Z.G.; Wu, Z.L. The applications of decision-level data fusion technologies in the field of multiuser detection for DS-UWB systems. Sensors 2015, 15, 24771–24790. [Google Scholar] [CrossRef] [PubMed]
- Zhang, R.; Cioffi, J.M. Iterative spectrum shaping with opportunistic multiuser detection. IEEE Trans. Commun. 2012, 60, 1680–1691. [Google Scholar] [CrossRef]
- Zhang, R.; Cioffi, J.M. Exploiting opportunistic multiuser detection decentralized multiuser MIMO systems. IEEE Trans. Wirel. Commun. 2011, 10, 2474–2485. [Google Scholar] [CrossRef]
- Mimura, K.; Okada, M. Generating functional analysis for iterative CDMA multiuser detectors. IEEE Trans. Inf. Theory 2014, 60, 3645–3670. [Google Scholar] [CrossRef]
- Takeuchi, K.; Tanaka, T.; Kawabata, T. Performance improvement of iterative multiuser detection for large sparsely spread CDMA systems by spatial coupling. IIEEE Trans. Inf. Theory 2015, 61, 1768–1794. [Google Scholar] [CrossRef]
- Azmi, P.; Zand, T.S. An iterative multiuser detector for overloaded LDPC coded CDMA systems. Wirel. Pers. Commun. 2012, 66, 41–56. [Google Scholar] [CrossRef]
- Lu, H.Y. Iterative multiuser detectors for spatial-frequency-time-domain spread multi-carrier DS-CDMA systems. IEEE. Trans. Veh. Technol. 2011, 60, 1640–1650. [Google Scholar] [CrossRef]
- Varanasi, M.K.; Aazhang, B. Near-optimum detection in synchronous code-division multiple access systems. IEEE Trans. Commun. 1991, 39, 725–736. [Google Scholar] [CrossRef]
- Wang, X.D.; Poor, H.V. Iterative (Turbo) soft interference cancellation and decoding for coded CDMA. IEEE Trans. Commun. 1999, 47, 1046–1061. [Google Scholar] [CrossRef]




| System | DS-UWB |
|---|---|
| Modulation mode | BPSK |
| Pseudo random sequences (PRS) | Balanced Gold sequences |
| Length of PRS | 127 |
| Number of tested bits | 50,000,000 |
| Communication channel | AWGN |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, X.; Jiang, X.; Wu, Z.; Zhuang, S. Differential Characteristics Based Iterative Multiuser Detection for Wireless Sensor Networks. Sensors 2017, 17, 388. https://doi.org/10.3390/s17020388
Chen X, Jiang X, Wu Z, Zhuang S. Differential Characteristics Based Iterative Multiuser Detection for Wireless Sensor Networks. Sensors. 2017; 17(2):388. https://doi.org/10.3390/s17020388
Chicago/Turabian StyleChen, Xiaoguang, Xu Jiang, Zhilu Wu, and Shufeng Zhuang. 2017. "Differential Characteristics Based Iterative Multiuser Detection for Wireless Sensor Networks" Sensors 17, no. 2: 388. https://doi.org/10.3390/s17020388






