A Novel Physical Layer Assisted Authentication Scheme for Mobile Wireless Sensor Networks
Abstract
:1. Introduction
1.1. Related Works and Issues
1.2. Our Motivations and Contributions
- (1)
- In our inter-burst authentication scheme, a new method is developed for the legitimate users to compare their RSS records while not requiring the sender to send his RSS values back to the receiver, which avoids the information disclose to the attacker. Hence, our proposed scheme is more secure than that in [5] and causes no loss of secrecy. Our scheme can be combined with other RSS-based physical-layer secret key generation schemes [22,23,24,25,26,27] to further enhance the security of wireless networks.
- (2)
- Our proposed inter-burst authentication scheme can detect the spoofing attack even in high dynamic environment.
- (3)
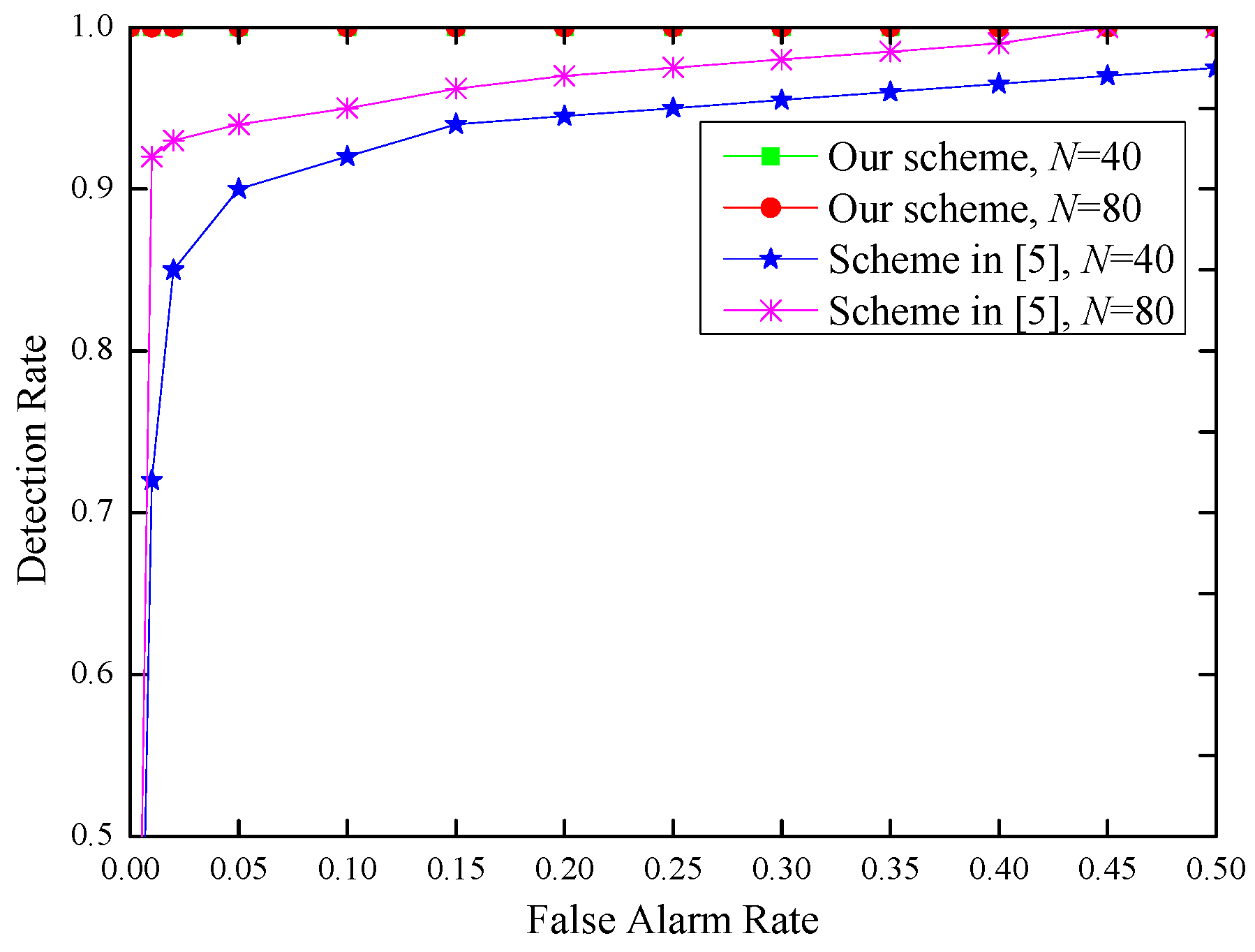
- Our proposed inter-burst authentication scheme is more efficient since it achieves higher detection rate while keeping lower false alarm rate. In our scheme, the detection rate can achieve 100% without false alarm both in indoor and outdoor environments. Moreover, our solution is lightweight in the sense that only one short message communication is needed. Our scheme can achieve fast and efficient message authentication with less communication and computation overheads.
- (4)
- We conduct the performance analysis on the inter-burst authentication, and identify its applicability.
- (5)
- We validate our approach through real-world experiments under indoor and outdoor environments. Experiment results backs our proposed scheme well. Our scheme is a practical one.
1.3. Organization of the Paper
2. Theoretical Basis
2.1. Channel Reciprocity Principle
2.2. Spatial Uncorrelation Principle
2.3. Two Theorems
3. Our Proposed Authentication Scheme
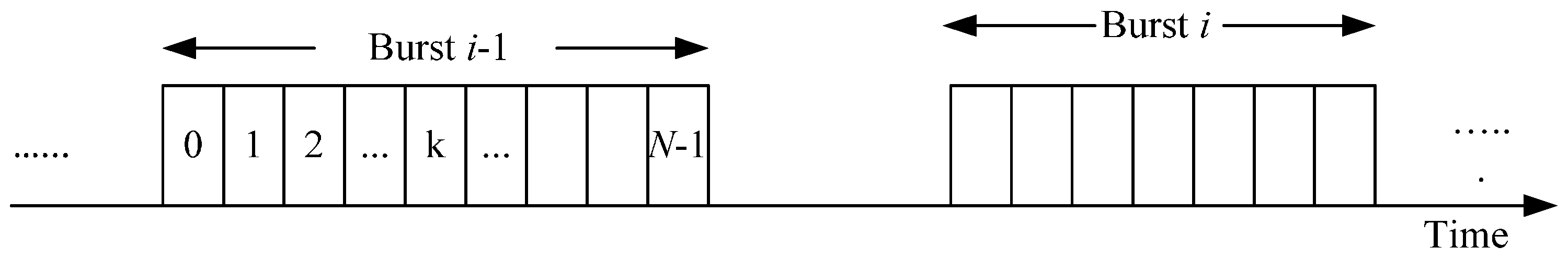
3.1. System and Communication Model
3.2. Authentication Scheme
4. Performance Evaluations
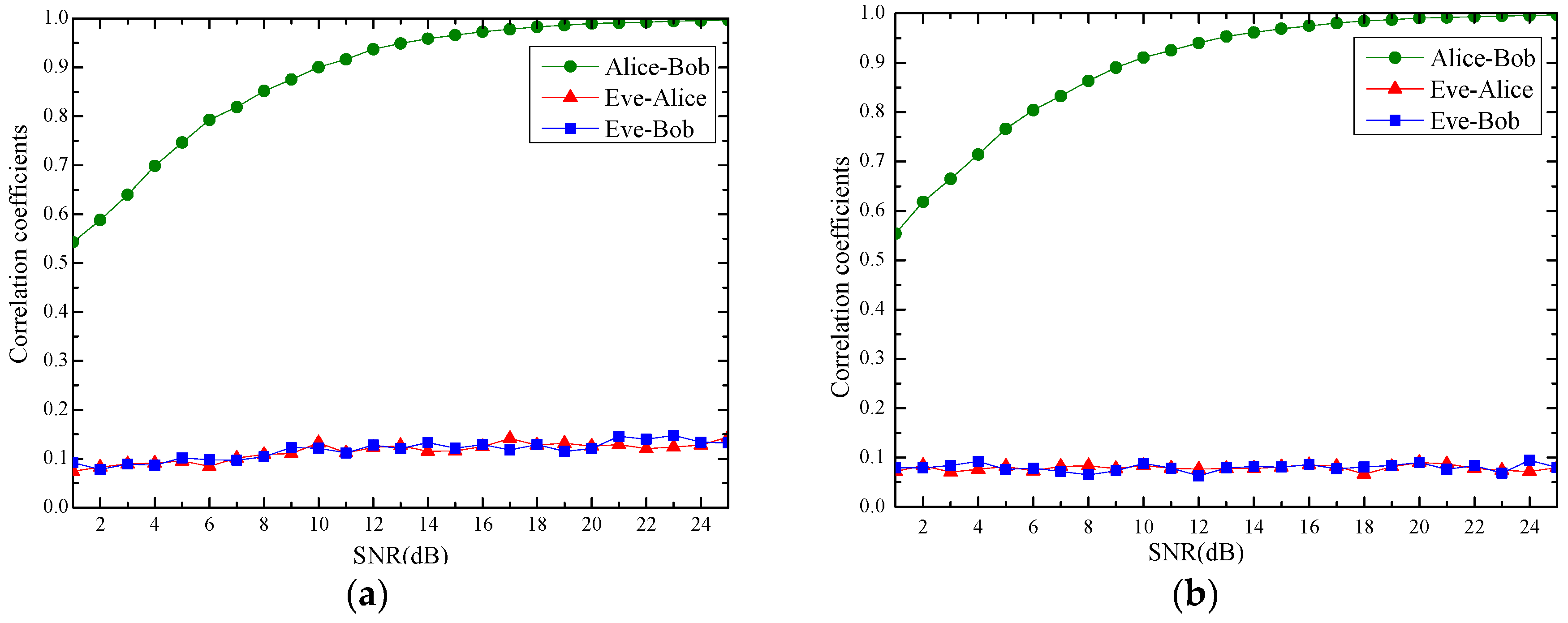
4.1. Reciprocity and Spatial Uncorrelation Validation
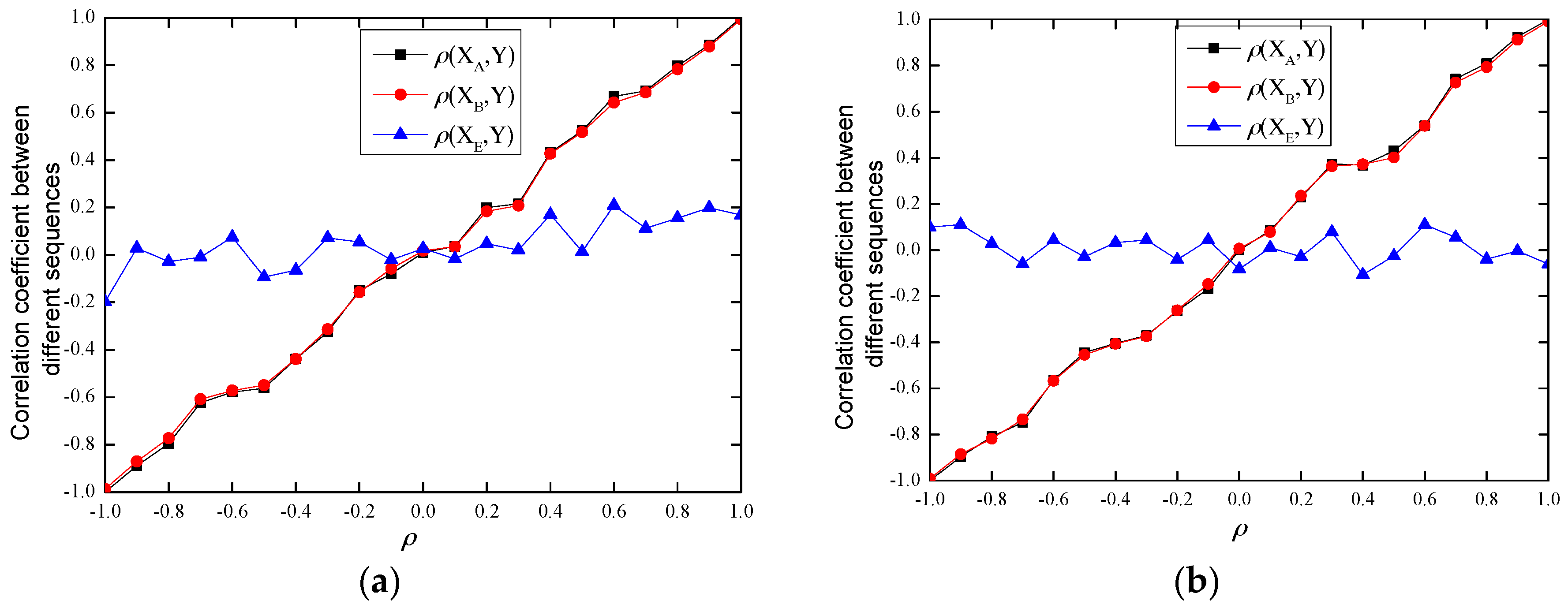
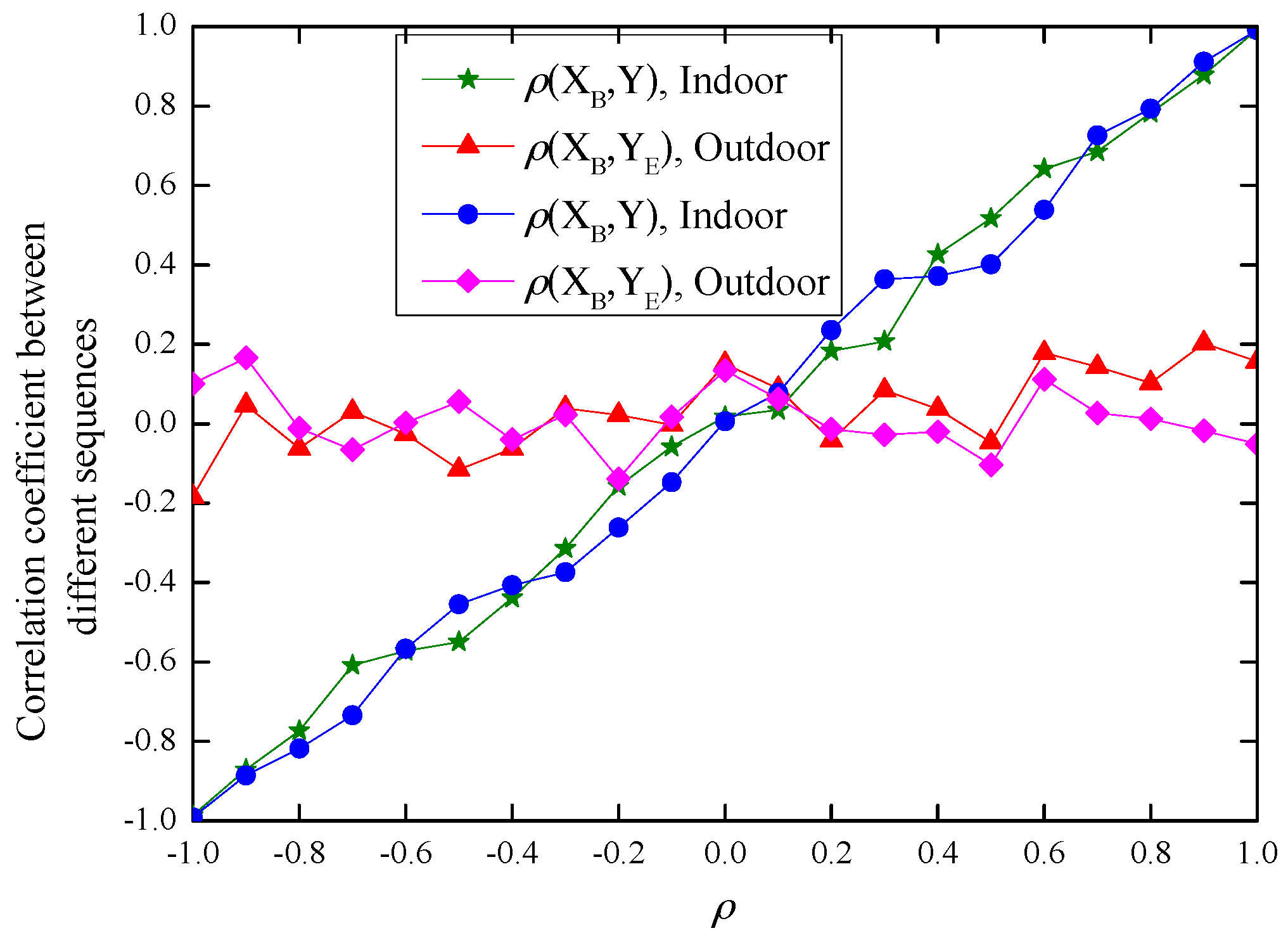
4.2. Theorem 2 Validation
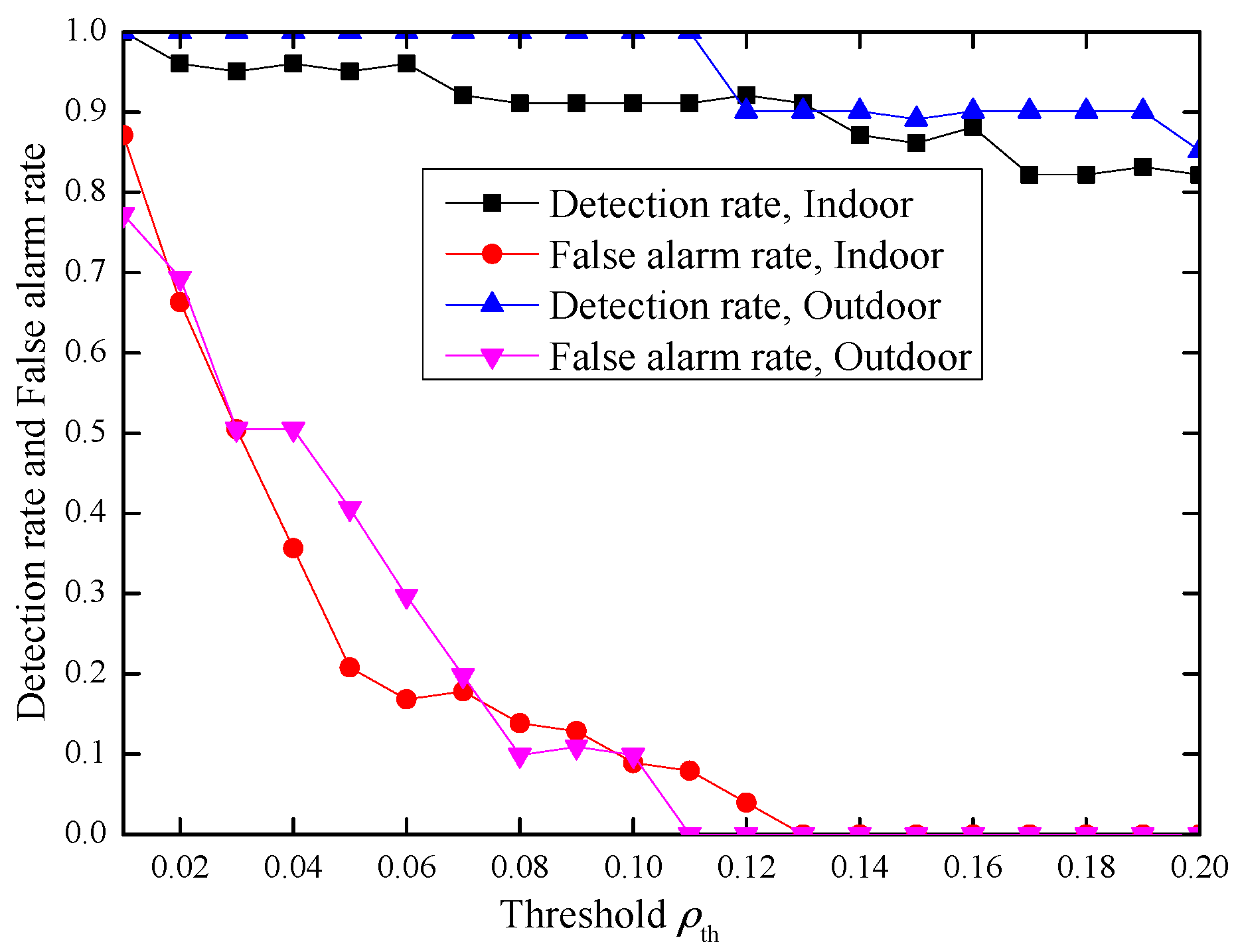
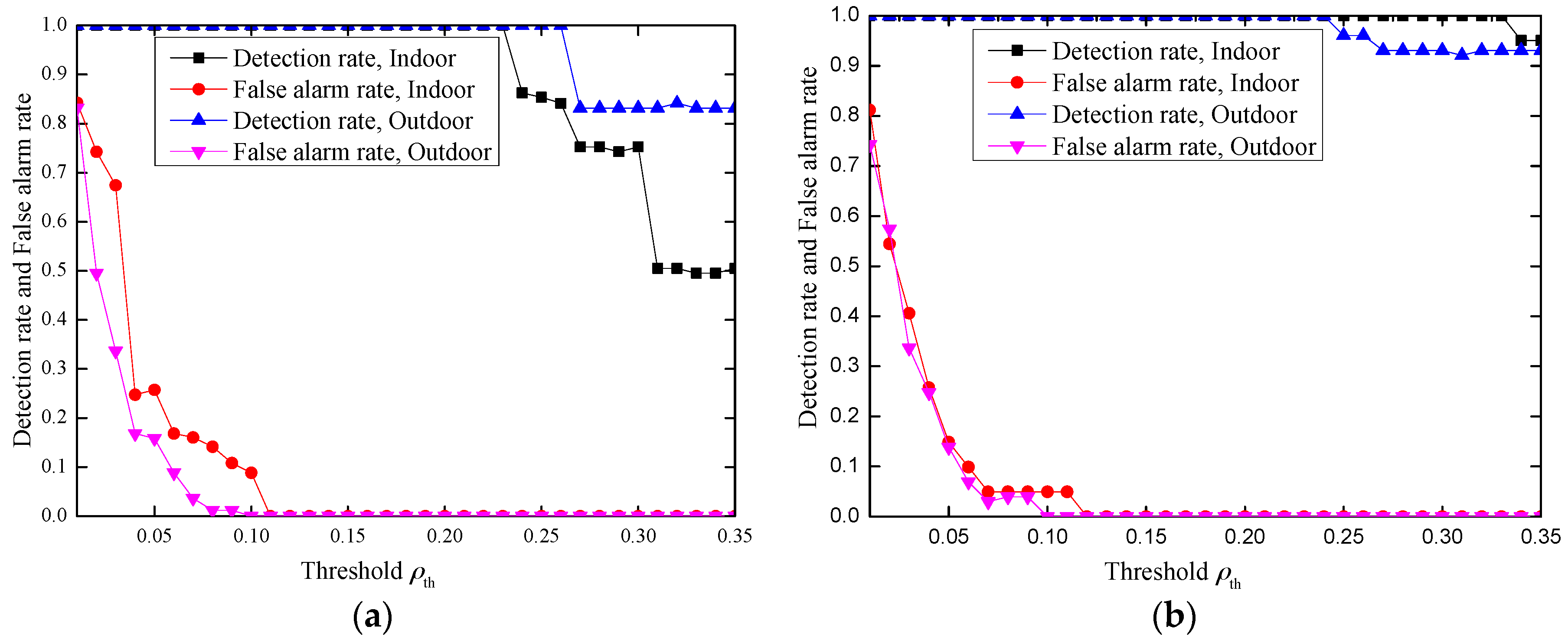
4.3. Performance Evaluation of Our Proposed Scheme
4.3.1. The Choosing of Parameters and
4.3.2. Performance Evaluation
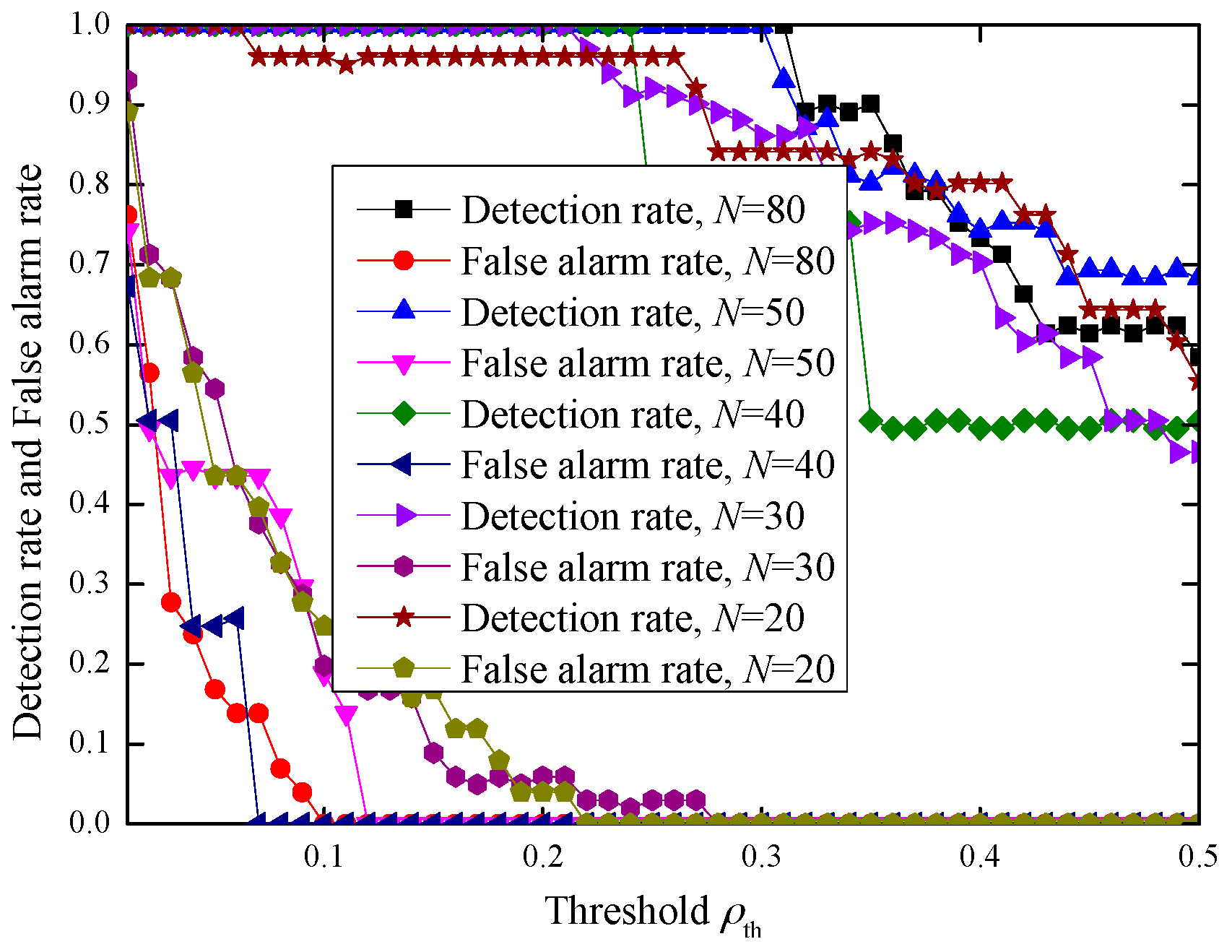
4.3.3. Impact of the Frame Number in Each Burst
4.3.4. Security
4.3.5. Overheads
4.3.6. Applicability
5. Conclusions
Acknowledgments
Conflicts of Interest
Appendix A
Appendix B
References
- Bellardo, J.; Savage, S. 802.11 Denial-of-Service Attacks: Real Vulnerabilities and Practical Solutions. In Proceedings of the 12th Conference on USENIX Security Symposium, Washington, DC, USA, 4–8 August 2003; pp. 15–28.
- Wen, H.; Ho, P.H.; Qi, C.; Gong, G. Physical layer assisted authentication for distributed ad hoc wireless sensor networks. IET Inf. Secur. 2010, 4, 390–396. [Google Scholar] [CrossRef]
- Hou, W.; Wang, X.; Chouinard, J.Y.; Refaey, A. Physical layer authentication for mobile systems with time-varying carrier frequency offsets. IEEE Trans. Commun. 2014, 62, 1658–1667. [Google Scholar] [CrossRef]
- Xiao, L.; Greenstein, L.J.; Mandayam, N.B.; Trappe, W. Using the physical layer for wireless authentication in time-variant channels. IEEE Trans. Wirel. Commun. 2008, 7, 2571–2579. [Google Scholar] [CrossRef]
- Zeng, K.; Govindan, K.; Mohapatra, P. Non-cryptographic authentication and identification in wireless networks. IEEE Wirel. Commun. 2010, 17, 56–62. [Google Scholar] [CrossRef]
- Hao, P.; Wang, X.; Refaey, A. An enhanced cross-layer authentication mechanism for wireless communications based on PER and RSSI. In Proceedings of the 13th IEEE Canadian Workshop on Information Theory (CWIT), Toronto, ON, Canada, 18–21 June 2013; pp. 44–48.
- Liu, J.; Wang, X. Physical Layer Authentication Enhancement Using Two-Dimensional Channel Quantization. IEEE Trans. Wirel. Commun. 2016, 15, 4171–4182. [Google Scholar] [CrossRef]
- Xiao, L.; Greenstein, L.; Mandayam, N.; Trappe, W. A physical-layer technique to enhance authentication for mobile terminals. In Proceedings of the 2008 IEEE International Conference on Communications, Beijing, China, 19–23 May 2008; pp. 1520–1524.
- Xiao, L.; Greenstein, L.; Mandayam, N.; Trappe, W. MIMO-assisted channel-based authentication in wireless networks. In Proceedings of the 42nd IEEE Annual Conference on Information Sciences and Systems, Princeton, NJ, USA, 19–21 March 2008; pp. 642–646.
- Chen, Y.; Xu, W.; Trappe, W.; Martin, R.P. Detecting and localizing wireless spoofing attacks. In Securing Emerging Wireless Systems; Springer: New York, NY, USA, 2009; pp. 1–18. [Google Scholar]
- Liu, F.J.; Wang, X.; Tang, H. Robust physical layer authentication using inherent properties of channel impulse response. In Proceedings of the IEEE Military Communications Conference, Baltimore, MD, USA, 7–11 November 2011; pp. 538–542.
- Tugnait, J.K.; Kim, H. A channel-based hypothesis testing approach to enhance user authentication in wireless networks. In Proceedings of the 2010 Second International Conference on Communication Systems and Networks (COMSNETS 2010), Bangalore, India, 5–9 January 2010; pp. 1–9.
- Wang, X.; Hao, P.; Hanzo, L. Physical-Layer Authentication for Wireless Security Enhancement: Current Challenges and Future Developments. IEEE Commun. Mag. 2016, 54, 152–158. [Google Scholar] [CrossRef]
- Van Vaerenbergh, S.; González, O.; Via, J.; Santamaría, I. Physical layer authentication based on channel response tracking using Gaussian processes. In Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Florence, Italy, 4–9 May 2014; pp. 2410–2414.
- Hou, W.; Wang, X.; Chouinard, J.Y. Physical layer authentication in OFDM systems based on hypothesis testing of CFO estimates. In Proceedings of the IEEE International Conference on Communications (ICC), Ottawa, ON, Canada, 10–15 June 2012; pp. 3559–3563.
- Durgin, G.D. Space-Time Wireless Channels; Prentice Hall Professional: Upper Saddle River, NJ, USA, 2003. [Google Scholar]
- Rappaport, T.S. Wireless Communications: Principles and Practic; Prentice Hall PTR: Upper Saddle River, NJ, USA, 1996. [Google Scholar]
- Jakes, W.C.; Cox, D.C. Microwave Mobile Communications; Wiley-IEEE Press: New York, NY, USA, 1994. [Google Scholar]
- Demirbas, M.; Song, Y. An RSSI-based scheme for sybil attack detection in wireless sensor networks. In Proceedings of the 2006 International Symposium on World of Wireless, Mobile and Multimedia Networks, Washington, DC, USA, 26–29 June 2006; pp. 564–570.
- Sheng, Y.; Tan, K.; Chen, G.; Kotz, D.; Campbell, A. Detecting 802.11 MAC layer spoofing using received signal strength. In Proceedings of the 27th IEEE Conference on Computer Communications, Piscataway, NJ, USA, 13–18 April 2008.
- Patwari, N.; Kasera, S.K. Robust location distinction using temporal link signatures. In Proceedings of the 13th Annual ACM International Conference on Mobile Computing and Networking, Montreal, QC, Canada, 9–14 September 2007; pp. 111–122.
- Mathur, S.; Trappe, W.; Mandayam, N.; Ye, C.; Reznik, A. Radio-telepathy: extracting a secret key from an unauthenticated wireless channel. In Proceedings of the 14th ACM International Conference on Mobile Computing and Networking, San Francisco, CA, USA, 14–19 September 2008; pp. 128–139.
- Jana, S.; Premnath, S.N.; Clark, M.; Kasera, S.K.; Patwari, N.; Krishnamurthy, S.V. On the effectiveness of secret key extraction from wireless signal strength in real environments. In Proceedings of the 15th ACM Annual International Conference on Mobile Computing and Networking, Beijing, China, 20–25 September 2009; pp. 321–332.
- Luo, Y.; Pu, L.; Peng, Z.; Shi, Z. RSS-based secret key generation in underwater acoustic networks: advantages, challenges, and performance improvements. IEEE Commun. Mag. 2016, 54, 32–38. [Google Scholar] [CrossRef]
- Liu, H.; Yang, J.; Wang, Y.; Chen, Y. Collaborative secret key extraction leveraging received signal strength in mobile wireless networks. In Proceedings of the IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 927–935.
- Premnath, S.N.; Jana, S.; Croft, J.; Gowda, P.L.; Clark, M.; Kasera, S.K.; Patwari, N.; Krishnamurthy, S.V. Secret key extraction from wireless signal strength in real environments. IEEE Trans. Mob. Comput. 2013, 12, 917–930. [Google Scholar] [CrossRef]
- Guillaume, R.; Winzer, F.; Czylwik, A.; Zenger, C.T.; Paar, C. Bringing PHY-based key generation into the field: An evaluation for practical scenarios. In Proceedings of the IEEE 82nd Vehicular Technology Conference (VTC Fall), Boston, MA, USA, 6–9 September 2015; pp. 1–5.

© 2017 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license ( http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, Q. A Novel Physical Layer Assisted Authentication Scheme for Mobile Wireless Sensor Networks. Sensors 2017, 17, 289. https://doi.org/10.3390/s17020289
Wang Q. A Novel Physical Layer Assisted Authentication Scheme for Mobile Wireless Sensor Networks. Sensors. 2017; 17(2):289. https://doi.org/10.3390/s17020289
Chicago/Turabian StyleWang, Qiuhua. 2017. "A Novel Physical Layer Assisted Authentication Scheme for Mobile Wireless Sensor Networks" Sensors 17, no. 2: 289. https://doi.org/10.3390/s17020289





