Performance Analysis of a Novel Hybrid S-ALOHA/TDMA Protocol for Beta Distributed Massive MTC Access
Abstract
:1. Introduction
- The framework of the proposed HSTMAC protocol is detailed in this paper. The reserved uplink RBs are divided into TDMA part for H2H traffic with large size packets and S-ALOHA part for M2M traffic with small size packets. The foundation of HSTMAC protocol is proved through system capacity analysis.
- Considering the impact of ACB factor and backoff scheme, this paper derives the analytical performance of HSTMAC iteratively. Then the system equilibrium under arbitrary retransmission limit is analyzed rigorously, which can provide an insight on QoS provision.
- Based on the equilibrium analysis, a dynamic pre-backoff algorithm is designed for QoS guarantee by adaptively scattering new M2M arrivals over the transmission interval according to the highly synchronized traffic load.
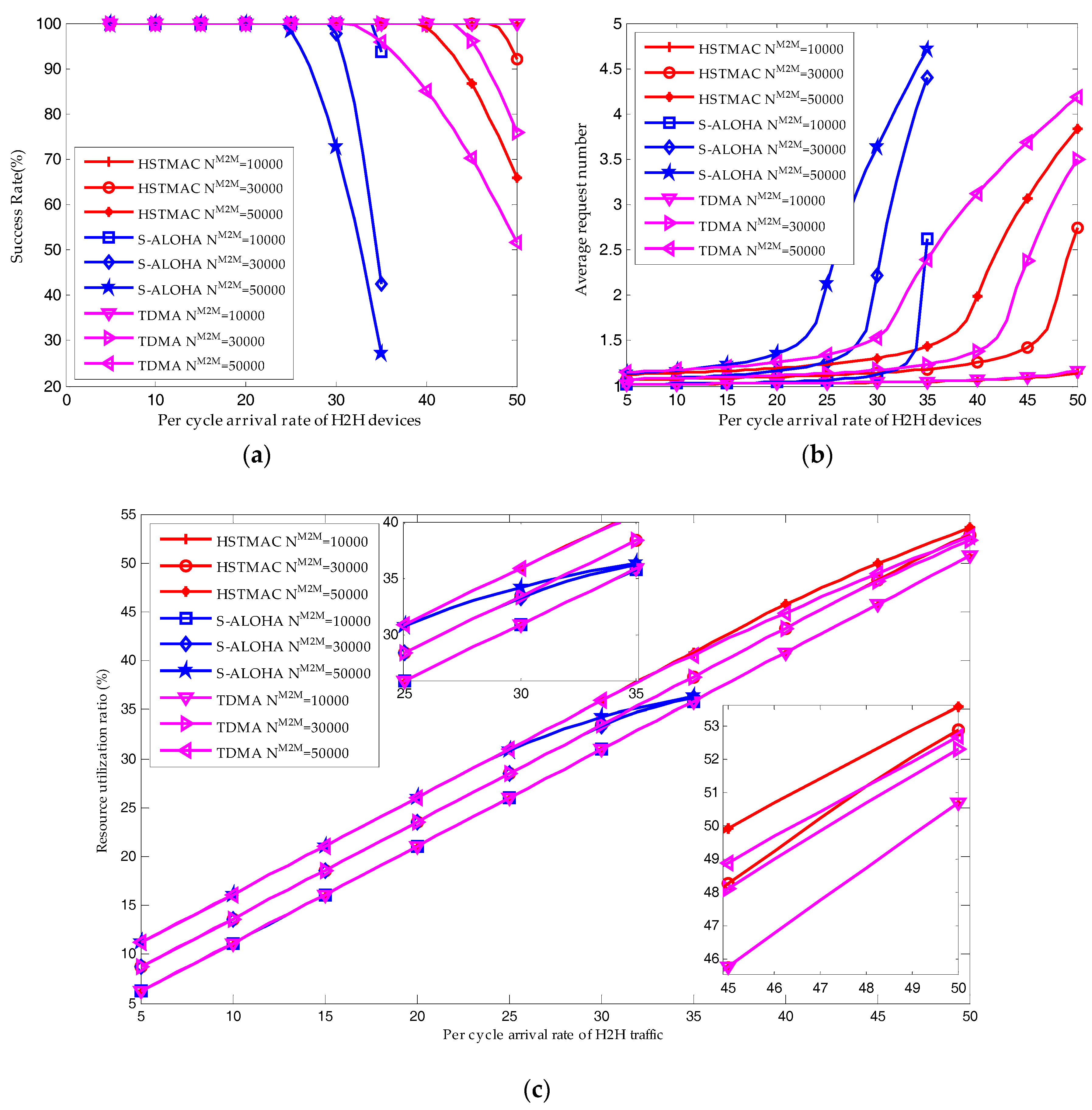
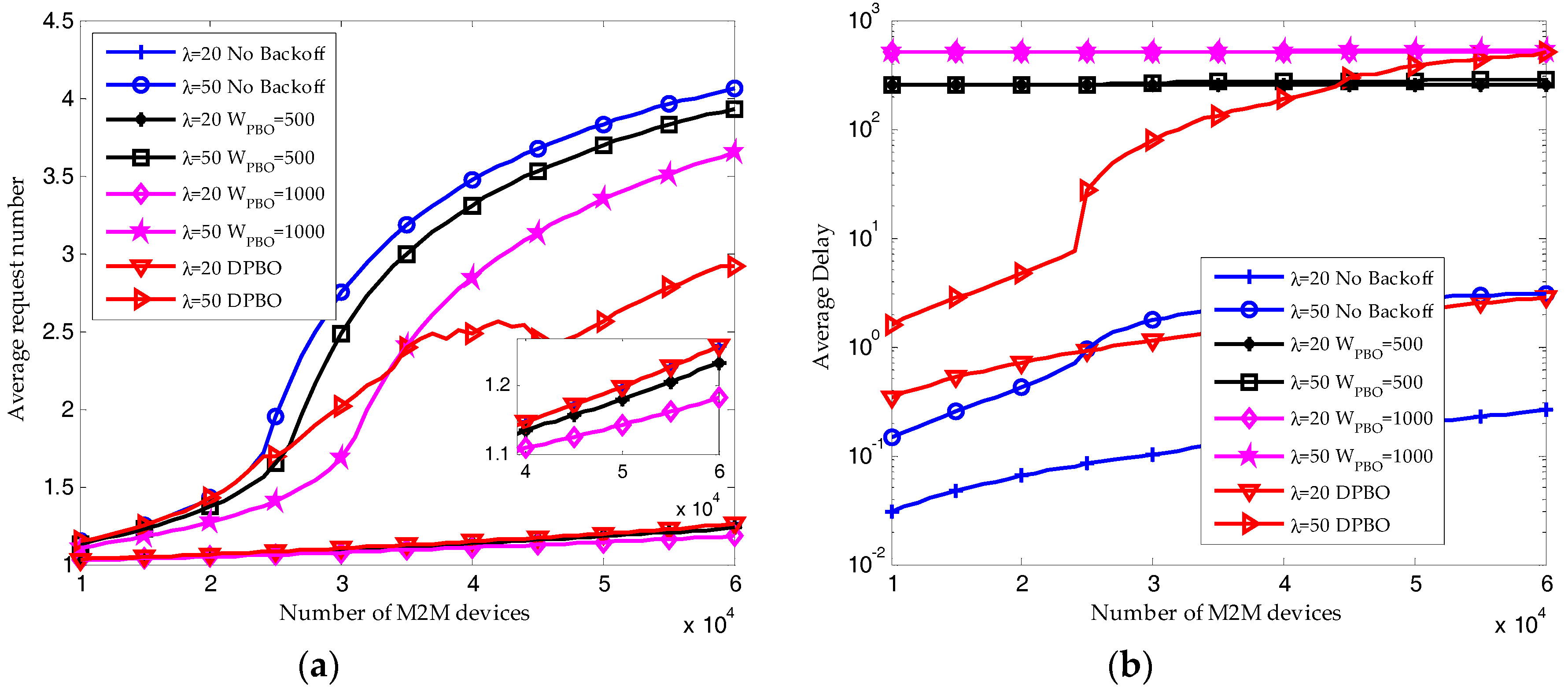
- The superiority of HSTMAC in terms of success possibility, resource utilization ratio, delay and average access request number, is validated through numerical and simulation results. Compared to uniform pre-backoff (UPBO) algorithm, the proposed DPBO algorithm can achieve a higher success probability with a much reduced delay.
2. Related Works
3. The Proposed HSTMAC Framework and System Model
3.1. Foundation of the HSTMAC Protocol
3.1.1. System Capacity of S-ALOHA Protocol
3.1.2. System Capacity of TDMA Protocol
3.1.3. Packet Size Threshold
3.2. Optimal ACB Parameter
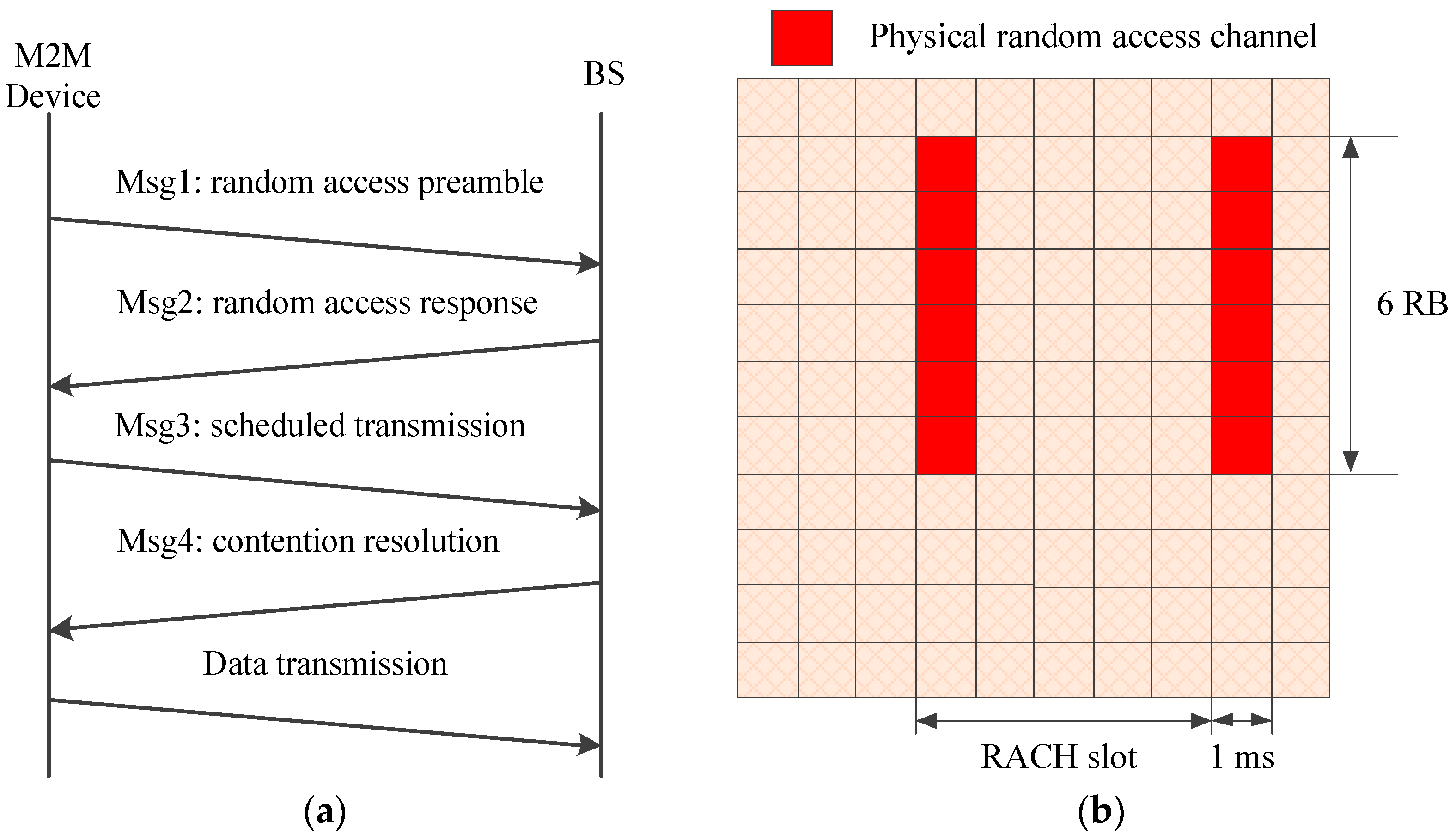
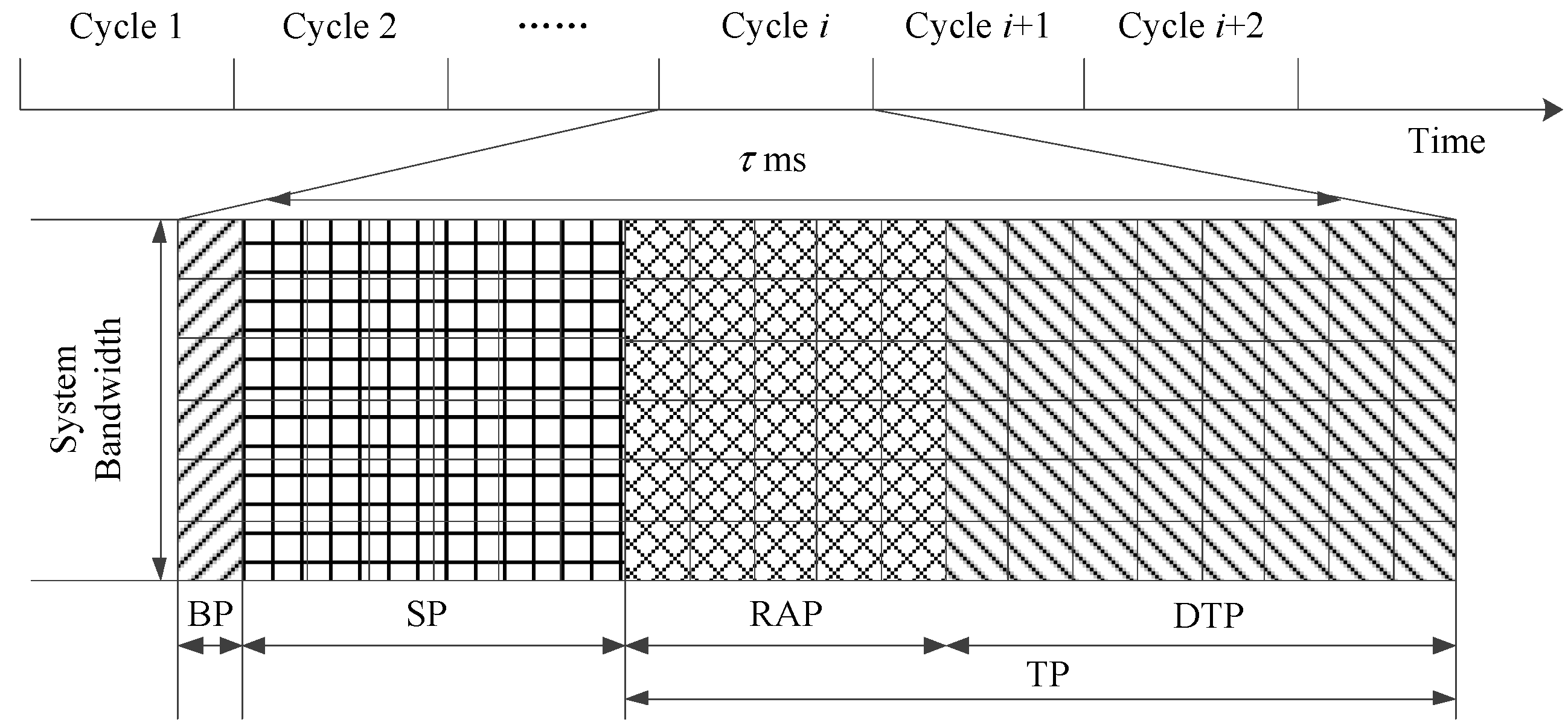
3.3. Frame Structure of the Proposed HSTMAC Protocol
4. A General Model for Analytical Performance Analysis
4.1. Analytical Performance Analysis
4.2. Performance Metrics
5. System Equilibrium Analysis under Arbitrary Transmission Limit
5.1. System Balance Equation
5.2. Equilibrium Analysis for S-ALOHA System
5.2.1. Equilibrium Analysis in the Saturation State
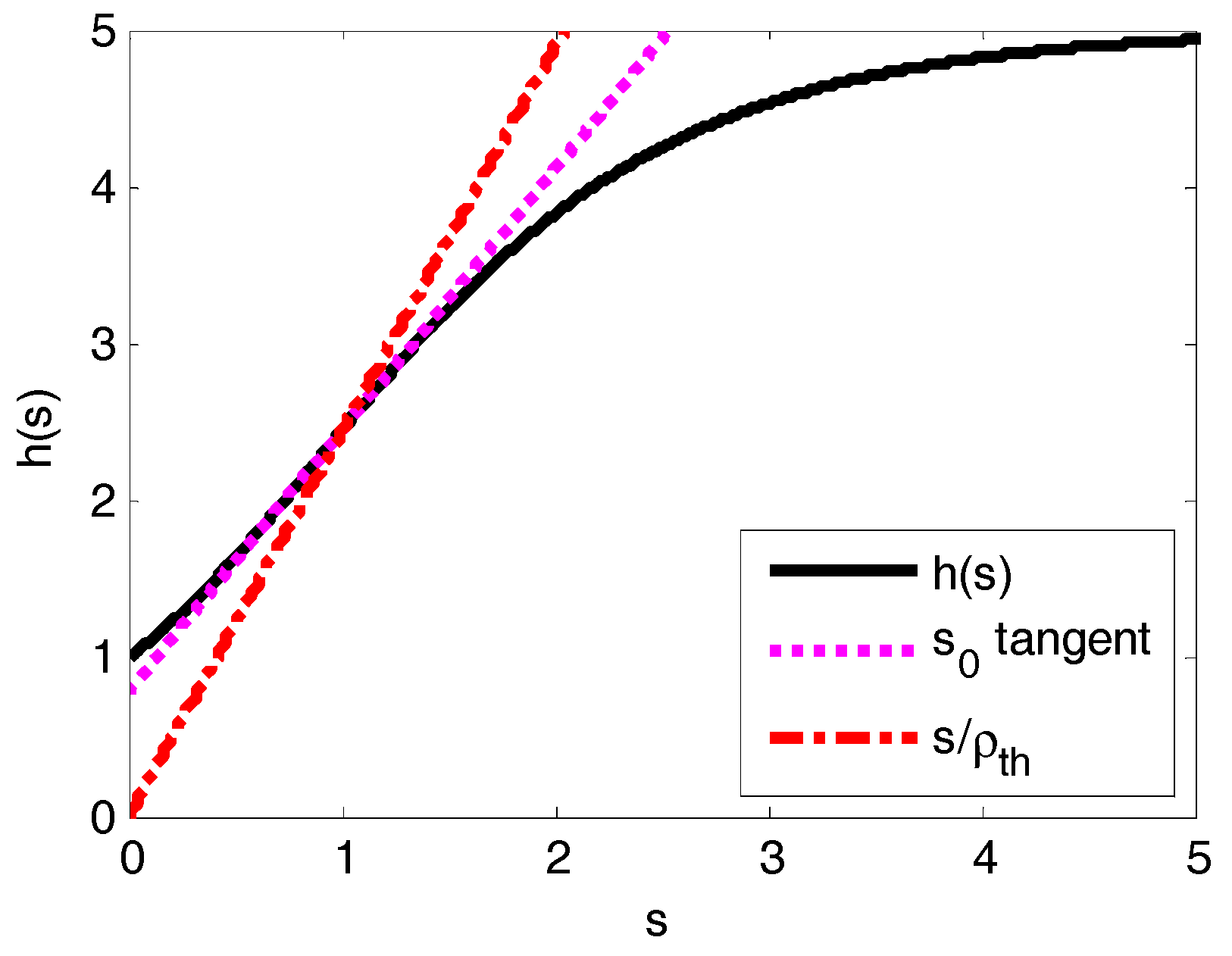
5.2.2. Equilibrium Analysis in the Non-Saturation State for Q ≤ 8
5.2.3. Equilibrium Analysis in the Non-Saturation State for Q ≥ 9
- (i)
- for ρ > ρ2, there is only a single equilibrium point on (s2,+∞);
- (ii)
- for ρ < ρ2, there is only a single equilibrium point on (0,s2) and there are two equilibrium points on (s2,+∞) for ρ1 > ρ > ρ2 and one equilibrium point on (s2,+∞) for ρ > ρ1.
- If , i.e., ρ ≥ ρth, the system would surely converge to a saturated equilibrium state. Therefore, the equilibrium point cannot be computed by Equation (35) directly and the ACB scheme would ensure that s = 1. Then the average success probability and resource utilization ratio can be computed as:
- If , i.e., ρ < ρth, the ACB scheme would ensure the system converges to an equilibrium state which is non-saturate. The single unique equilibrium point s ∈ (0,1) can be computed by Equation (35). In the non-saturation state we can have:
5.3. Equilibrium Analysis for TDMA System
- If , the system would surely converge to a saturated equilibrium state. Therefore, the ACB scheme would ensure that s = 1. Then the average success probability and resource utilization ratio can be computed as:
- If , the ACB scheme would ensure the system converges to an equilibrium state which is non-saturate. The single unique equilibrium point s ∈ (0,1) and the corresponding θ can be computed by Equations (35) and (46). In the non-saturation state we can have:
5.4. QoS Guaranteed Resource Allocation and Dynamic Pre-Backoff Algorithm
| Algorithm 1: Dynamic pre-backoff algorithm (DPBO) |
|
6. Numerical and Simulation Results
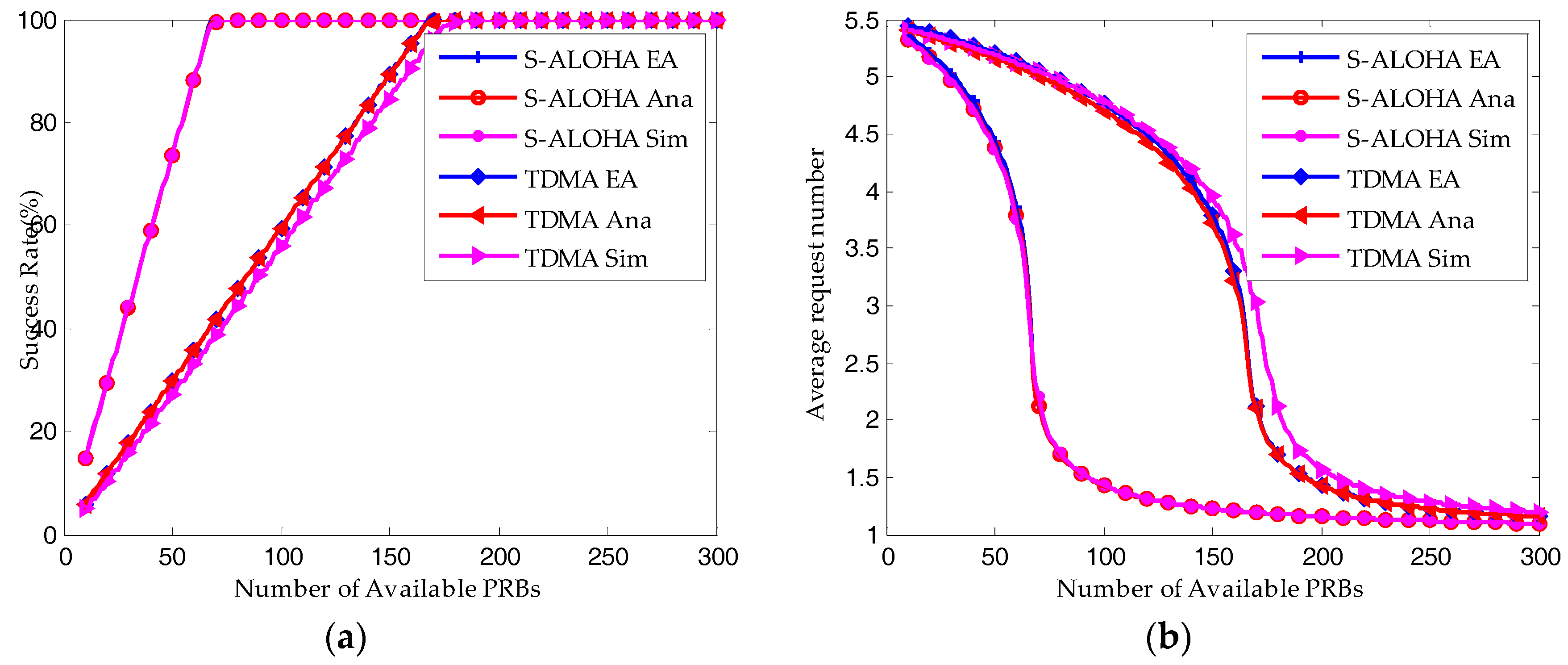
6.1. System Performance versus Packet Size
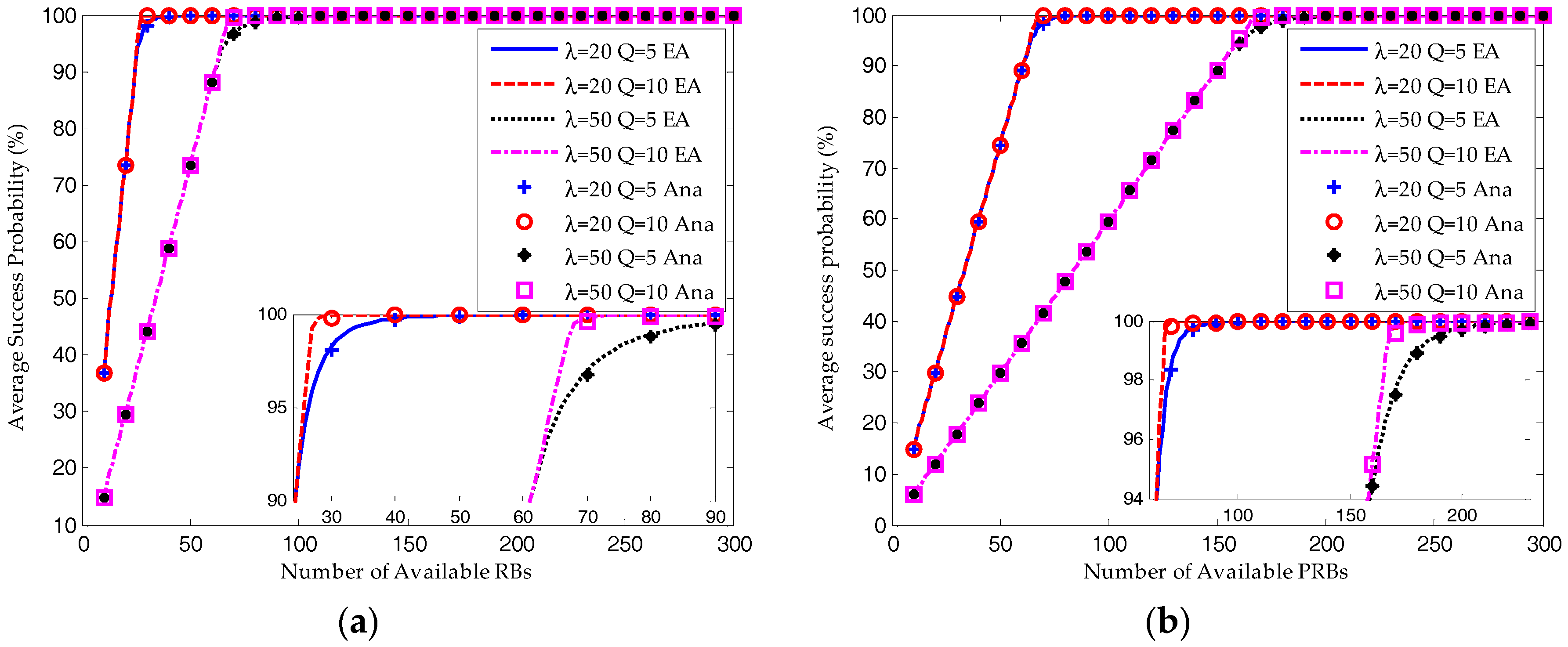
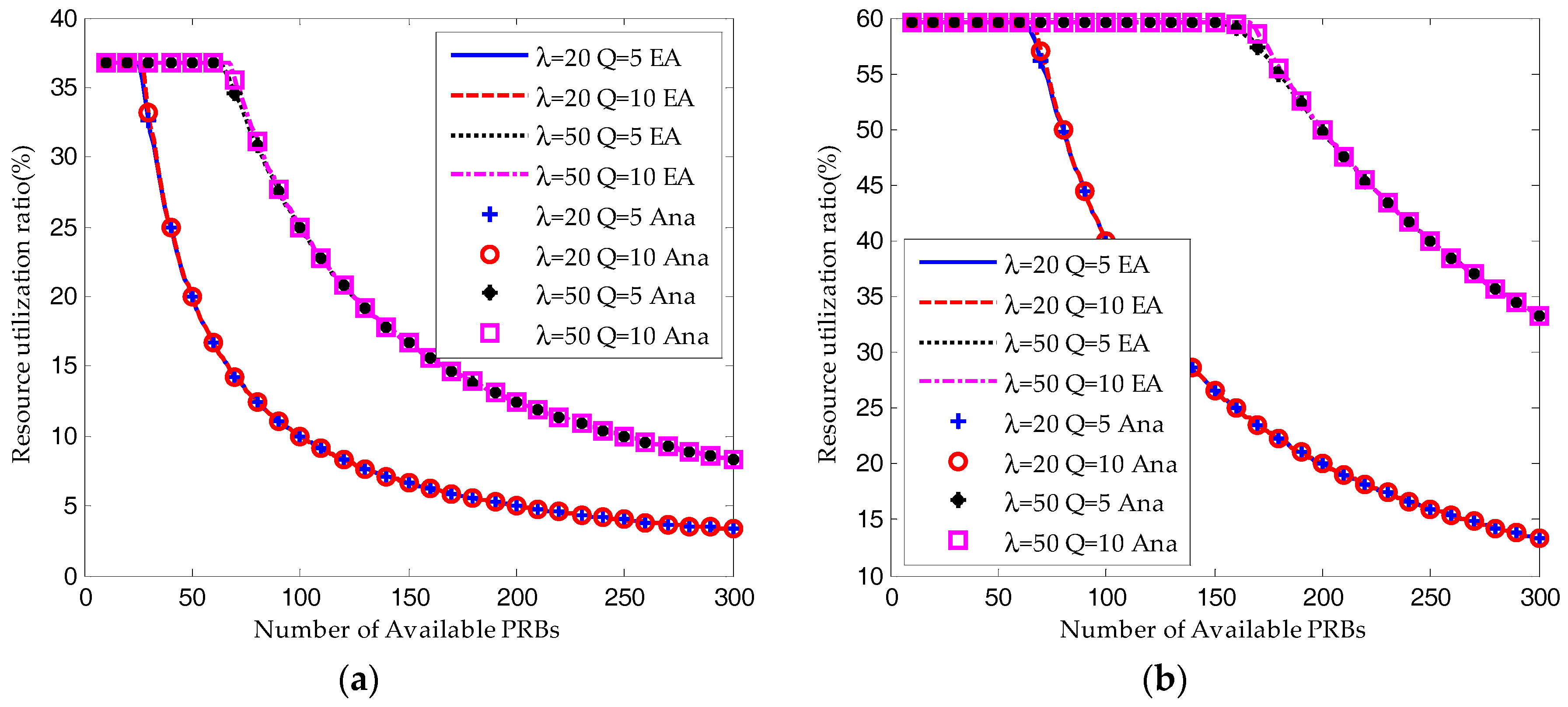
6.2. Equlibrium Analysis
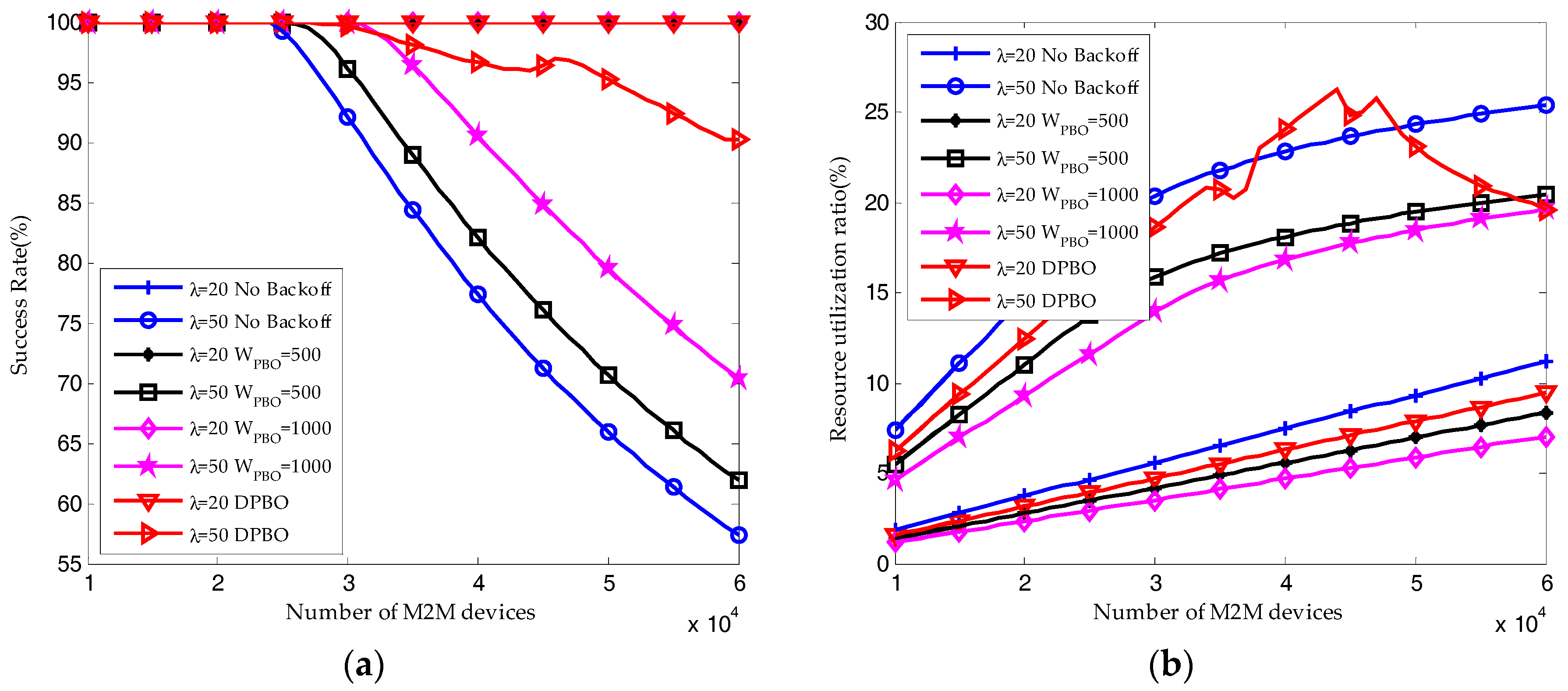
6.3. Performance of the HSTMAC Protocol without Backoff Scheme
6.4. Performance of the HSTMAC Protocol with Dynamic Pre-Backoff Scheme
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Andreev, S.; Galinina, O.; Pyattaev, A. Understanding the IoT connectivity landscape: A contemporary M2M radio technology roadmap. IEEE Commun. Mag. 2015, 53, 32–40. [Google Scholar] [CrossRef]
- Palattella, M.R.; Dohler, M.; Grieco, A. Internet of things in the 5G era: Enablers, architecture, and business models. IEEE J. Sel. Areas Commun. 2016, 34, 510–527. [Google Scholar] [CrossRef]
- Kartsakli, E.; Lalos, A.; Antonopoulos, A. A survey on M2M systems for mHealth: A wireless communications perspective. Sensors 2014, 14, 18009–18052. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Chen, M.; Wan, J.; Gonzalez, S.; Liao, X.; Leung, V.C.M. A survey of recent developments in home M2M networks. IEEE Commun. Surv. Tutor. 2014, 16, 98–114. [Google Scholar] [CrossRef]
- OECD Report. Machine-to-Machine Communications: Connecting Billions of Devices; OECD Digital Economy Papers; OECD: Paris, France, 2012; Available online: http://dx.doi.org/10.1787/5k9gsh2gp043-en (accessed on 26 August 2017).
- 3GPP TS 22.368 V13.1.0. Service Requirements for Machine-Type Communications (MTC). December 2014. Available online: http://www.3gpp.org/ftp/Specs/2014-12/Rel-13/22_series/ (accessed on 8 December 2017).
- Shariatmadari, H.; Ratasuk, R.; Iraji, S.; Laya, A.; Taleb, T.; Jäntti, R.; Ghosh, A. Machine-type communications: Current status and future perspectives toward 5G systems. IEEE Commun. Mag. 2015, 53, 10–17. [Google Scholar] [CrossRef]
- Ghavimi, F.; Chen, H.-H. M2M communications in 3GPP LTE/LTE-A networks: Architectures, service requirements, challenges, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 525–549. [Google Scholar] [CrossRef]
- Rico-Alvarino, A.; Vajapeyam, M.; Xu, H.; Wang, X.; Blankenship, Y.; Bergman, J.; Tirronen, T.; Yavuz, E. An overview of 3GPP enhancements on machine to machine communications. IEEE Commun. Mag. 2016, 54, 14–21. [Google Scholar] [CrossRef]
- 3GPP TS 36.211 V12.8.0. Evolved Universal Terrestrial Radio Access (E-UTRA): Physical Channels and Modulation. December 2015. Available online: http://www.3gpp.org/ftp/Specs/2015-12/Rel-12/36_series/ (accessed on 8 December 2017).
- 3GPP TR 37.868 V11.0.0. Study on RAN Improvements for Machine-Type Communications. September 2011. Available online: http://www.3gpp.org/ftp/Specs/2011-09/Rel-11/37_series/ (accessed on 8 December 2017).
- Islam, M.; Taha, A.-E.; Akl, S. A survey of access management techniques in machine type communications. IEEE Commun. Mag. 2014, 52, 74–81. [Google Scholar] [CrossRef]
- Laya, A.; Alonso, L.; Alonso-Zarate, J. Is the random access channel of LTE and LTE-A suitable for M2M communications? A survey of alternatives. IEEE Commun. Surv. Tutor. 2014, 16, 4–16. [Google Scholar] [CrossRef]
- Rajandekar, A.; Sikdar, B. A survey of MAC layer issues and protocols for machine-to-machine communications. IEEE Internet Things J. 2015, 2, 175–186. [Google Scholar] [CrossRef]
- Soltanmohammadi, E.; Ghavami, K.; Naraghi-Pour, M. A survey of traffic issues in machine-to-machine communications over LTE. IEEE Internet Things J. 2016, 6, 865–884. [Google Scholar] [CrossRef]
- Shih, M.-J.; Wei, H.-Y.; Lin, G.-Y. Two paradigms in cellular internet-of-things access for energy-harvesting machine-to-machine devices: Push-based versus pull-based. IET Wirel. Sens. Syst. 2016, 6, 121–129. [Google Scholar] [CrossRef]
- Shafiq, M.Z.; Ji, L.; Liu, A.X.; Pang, J.; Wang, J. Large-scale measurement and characterization of cellular machine-to-machine traffic. IEEE/ACM Trans. Netw. 2013, 21, 1960–1973. [Google Scholar] [CrossRef]
- Durisi, G.; Koch, T.; Popovski, P. Toward massive, ultrareliable, and low-latency wireless communication with short packets. Proc. IEEE 2016, 104, 1711–1726. [Google Scholar] [CrossRef]
- Dhillon, H.S.; Huang, H.; Viswanathan, H.; Valenzuela, R.A. Fundamentals of throughput maximization with random arrivals for M2M communications. IEEE Trans. Commun. 2014, 62, 4094–4109. [Google Scholar] [CrossRef]
- Wiriaatmadja, D.T.; Choi, K.W. Hybrid random access and data transmission protocol for machine-to-machine communications in cellular networks. IEEE Trans. Wirel. Commun. 2015, 14, 33–46. [Google Scholar] [CrossRef]
- Sui, N.; Wang, C.; Xie, W.; Xu, Y. Hybrid S-ALOHA/TDMA protocol for LTE/LTE-A networks with coexistence of H2H and M2M traffic. KSII Trans. Internet Inf. Syst. 2017, 11, 687–708. [Google Scholar] [CrossRef]
- Duan, S.; Shah-Mansouri, V.; Wang, Z.; Wong, V.W.S. D-ACB: Adaptive congestion control algorithm for bursty M2M traffic in LTE networks. IEEE Trans. Veh. Technol. 2016, 65, 9847–9861. [Google Scholar] [CrossRef]
- Oh, C.-Y.; Hwang, D.; Lee, T.-J. Joint access control and resource allocation for concurrent and massive access of M2M devices. IEEE Trans. Wirel. Commun. 2015, 14, 4182–4192. [Google Scholar] [CrossRef]
- Vilgelm, M.; Guersu, M.; Kellerer, W.; Reisslein, M. LATMAPA: Load-adaptive throughput-maximizing preamble allocation for prioritization in 5G random access. IEEE Access 2017, 5, 1103–1116. [Google Scholar] [CrossRef]
- Kim, J.S.; Munir, D.; Hasan, S.F.; Chung, M.Y. Enhancement of LTE RACH through extended random access process. Electron. Lett. 2014, 50, 1399–1400. [Google Scholar] [CrossRef]
- Jang, H.S.; Kim, S.M.; Ko, K.S.; Cha, J.; Sung, D.K. Spatial group based random access for M2M communications. IEEE Commun. Lett. 2014, 18, 961–964. [Google Scholar] [CrossRef]
- Jang, H.S.; Park, H.; Sung, D.K. A non-orthogonal resource allocation scheme in spatial group based random access for cellular M2M communications. IEEE Trans. Veh. Technol. 2017, 66, 4496–4500. [Google Scholar] [CrossRef]
- Wei, C.-H.; Cheng, R.-G.; Tsao, S.-L. Performance analysis of group paging for machine-type communications in LTE networks. IEEE Trans. Veh. Technol. 2013, 62, 3371–3382. [Google Scholar] [CrossRef]
- Arouk, O.; Ksentini, A. General model for RACH procedure performance analysis. IEEE Commun. Lett. 2016, 20, 372–375. [Google Scholar] [CrossRef]
- Koseoglu, M. Lower bounds on the LTE-A average random access delay under massive M2M arrivals. IEEE Trans. Commun. 2016, 64, 2104–2115. [Google Scholar] [CrossRef]
- Chen, J.; Lin, Y.-T.; Cheng, R.-G. A delayed random access speed-up scheme for group paging in machine-type communications. In Proceedings of the 2015 IEEE International Conference on Communications (ICC 2015), Taipei, Taiwan, 23–25 April 2015; pp. 623–627. [Google Scholar]
- Jiang, W.; Wang, X.; Deng, T. Performance analysis of a pre-backoff based random access scheme for machine-type communications. In Proceedings of the 2014 International Conference on Intelligent Green Building and Smart Grid (IGBSG 2014), Taipei, Taiwan, 23–25 April 2014; pp. 1–4. [Google Scholar]
- Harwahyu, R.; Wang, X.; Sari, R.F.; Cheng, R.-G. Analysis of group paging with pre-backoff. EURASIP J. Wirel. Commun. Netw. 2015, 2015, 1–9. [Google Scholar] [CrossRef]
- Arouk, O.; Ksentini, A.; Taleb, T. Group paging-based energy saving for massive MTC accesses in LTE and beyond networks. IEEE J. Sel. Areas Commun. 2016, 34, 1086–1102. [Google Scholar] [CrossRef]
- Jian, X.; Liu, Y.; Wei, Y.; Zeng, X.; Tan, X. Random access delay distribution of multichannel Slotted ALOHA with its applications for machine type communications. IEEE Internet Things J. 2017, 4, 21–28. [Google Scholar] [CrossRef]
- De Andrade, T.P.C.; Astudillo, C.A.; da Fonseca, N.L.S. The impact of massive machine type communication devices on the access probability of human-to-human users in LTE networks. In Proceedings of the 2014 IEEE Latin-America Conference on Communications (LATINCOM), Cartagena de Indias, Colombia, 5–7 November 2014; pp. 1–6. [Google Scholar]
- Foddis, G.; Garroppo, R.G.; Giordano, S.; Procissi, G.; Roma, S.; Topazzi, S. On RACH preambles separation between human and machine type communication. In Proceedings of the 2016 IEEE International Conference on Communications (ICC 2016), Kuala Lumpur, Malaysia, 22–27 May 2016; pp. 1–6. [Google Scholar]
- Pang, Y.C.; Chao, S.L.; Lin, G.Y.; Wei, H.Y. Network access for M2M/H2H hybrid systems: A game theoretic approach. IEEE Commun. Lett. 2014, 18, 845–848. [Google Scholar] [CrossRef]
- Sidhu, P.; Woungang, I.; Carvalho, G.H.S.; Anpalagan, A.; Dhurandher, S.K. An analysis of machine-type-communication on human-type-communication over wireless communication networks. In Proceedings of the 2015 IEEE 29th International Conference on Advanced Information Networking and Applications Workshops, Gwangiu, Korea, 24–27 March 2015; pp. 332–337. [Google Scholar]
- Kim, T.; Ko, K.S.; Sung, D.K. Prioritized random access for accommodating M2M and H2H communications in cellular networks. In Proceedings of the 2015 IEEE Globecom Workshops (GC Workshops), San Diego, CA, USA, 6–10 December 2015; pp. 1–6. [Google Scholar]
- Liu, Y.; Yuen, C.; Cao, X.; Hassan, N.U.; Chen, J. Design of a scalable hybrid MAC protocol for heterogeneous M2M networks. IEEE Internet Things J. 2014, 1, 99–111. [Google Scholar] [CrossRef]
- Misic, J.; Misic, V.; Khan, N. Sharing it my way: Efficient M2M access in LTE/LTE-A networks. IEEE Trans. Veh. Technol. 2017, 66, 696–709. [Google Scholar] [CrossRef]
- Wei, C.-H.; Cheng, R.-G.; Tsao, S.-L. Modeling and estimation of one-shot random access for finite-user multichannel Slotted ALOHA systems. IEEE Commun. Lett. 2012, 16, 1196–1199. [Google Scholar] [CrossRef]
- Tyagi, R.R.; Aurzada, F.; Lee, K.-D.; Kim, S.G.; Reisslein, M. Impact of retransmission limit on preamble contention in LTE-Advanced network. IEEE Syst. J. 2015, 9, 752–765. [Google Scholar] [CrossRef]
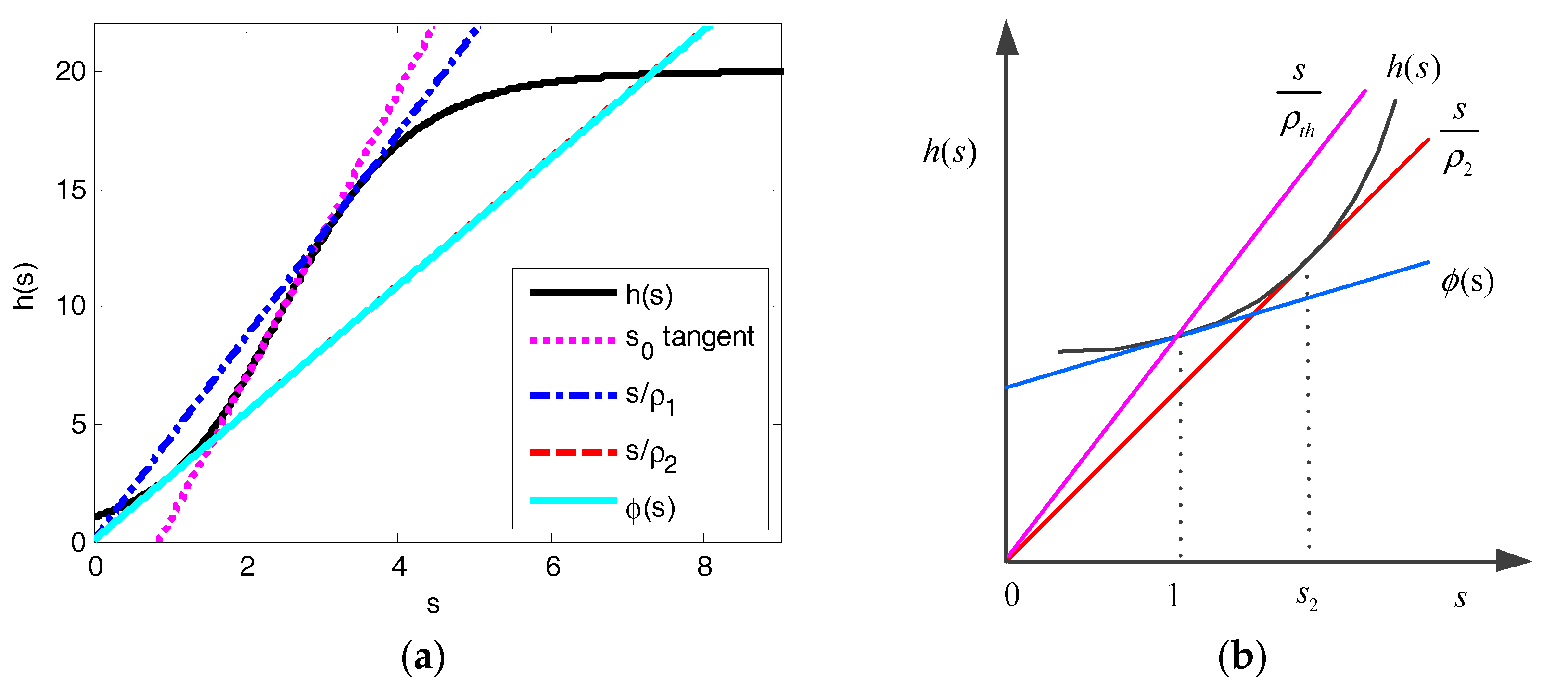



| Parameter | Settings |
|---|---|
| Cell bandwidth | 10 MHz (50 RBs in frequency domain) |
| Cycle interval | 5 ms |
| Reserved RBs for uplink transmission | 200 |
| Transmission limit | 5, 10 |
| H2H traffic model | Poisson distribution |
| M2M traffic model | Beta distribution |
| Signaling overhead parameter for H2H traffic | 2 |
| Packet size of H2H traffic | 2 |
| Packet size of M2M traffic | 0.5 |
| Number of M2M devices | 10,000–60,000 |
| Activation time of M2M devices | 10 s |
| Beta function parameters | 3, 4 |
| Backoff window size for M2M traffic | 20 |
| DPBO time control parameter for M2M traffic | 10 |
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | |
|---|---|---|---|---|---|---|---|---|---|---|
| 0.3679 | 0.6004 | 0.7474 | 0.8403 | 0.8991 | 0.9362 | 0.9597 | 0.9745 | 0.9839 | 0.9898 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sui, N.; Xu, Y.; Wang, C.; Xie, W. Performance Analysis of a Novel Hybrid S-ALOHA/TDMA Protocol for Beta Distributed Massive MTC Access. Sensors 2017, 17, 2875. https://doi.org/10.3390/s17122875
Sui N, Xu Y, Wang C, Xie W. Performance Analysis of a Novel Hybrid S-ALOHA/TDMA Protocol for Beta Distributed Massive MTC Access. Sensors. 2017; 17(12):2875. https://doi.org/10.3390/s17122875
Chicago/Turabian StyleSui, Nannan, Youyun Xu, Cong Wang, and Wei Xie. 2017. "Performance Analysis of a Novel Hybrid S-ALOHA/TDMA Protocol for Beta Distributed Massive MTC Access" Sensors 17, no. 12: 2875. https://doi.org/10.3390/s17122875





