FTUC: A Flooding Tree Uneven Clustering Protocol for a Wireless Sensor Network
Abstract
:1. Introduction
- A clustering algorithm enabling the CH election in large WSNs by building a tree network to convey the global minimum and maximum distance data to the BS.
- A way to balance the uneven distribution of CH by introducing referenced positions to elect CH, which balance the network load and prolong the network lifetime.
- The construction of unequal clusters to optimize the energy consumption of the overall network.
- A set of simulations to show the effectiveness of our approach, and to compare to state-of-art algorithms.
2. Related Work
3. Definitions and Models
3.1. Network Model
3.2. Node Energy Model
3.3. Network Life Cycle
3.4. Energy Consumption Balance
4. Problem Statements
4.1. Unevenly Distributed Cluster Problem
4.2. Global Minimum and Maximum Distances Problem
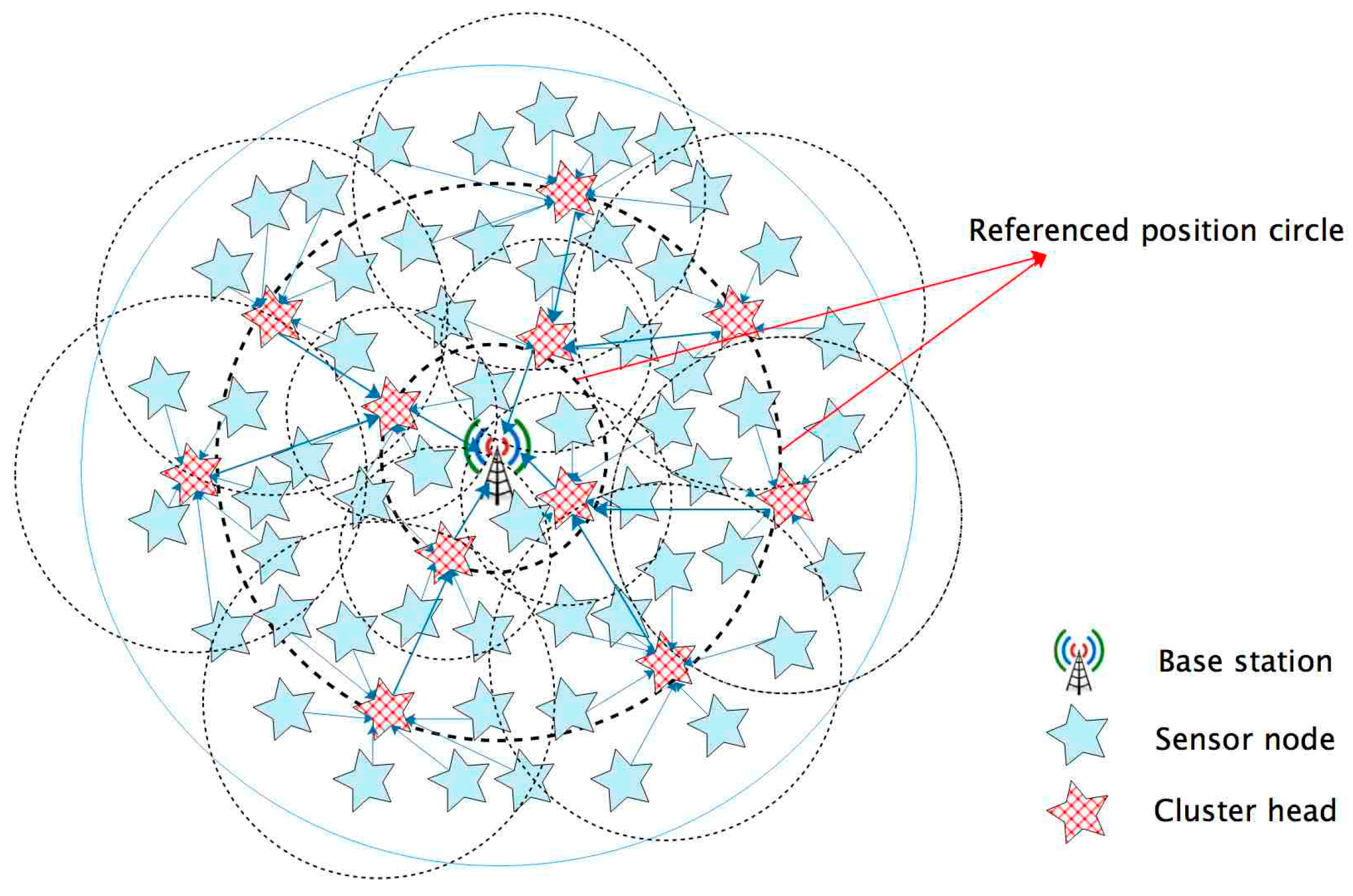
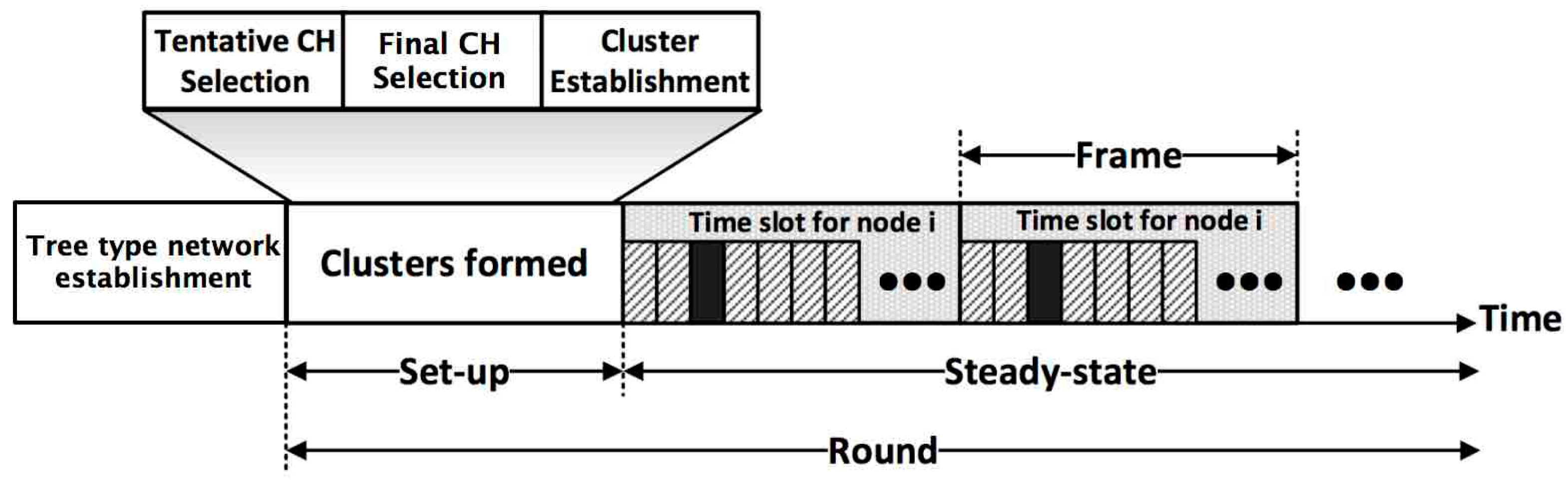
5. FTUC Algorithm
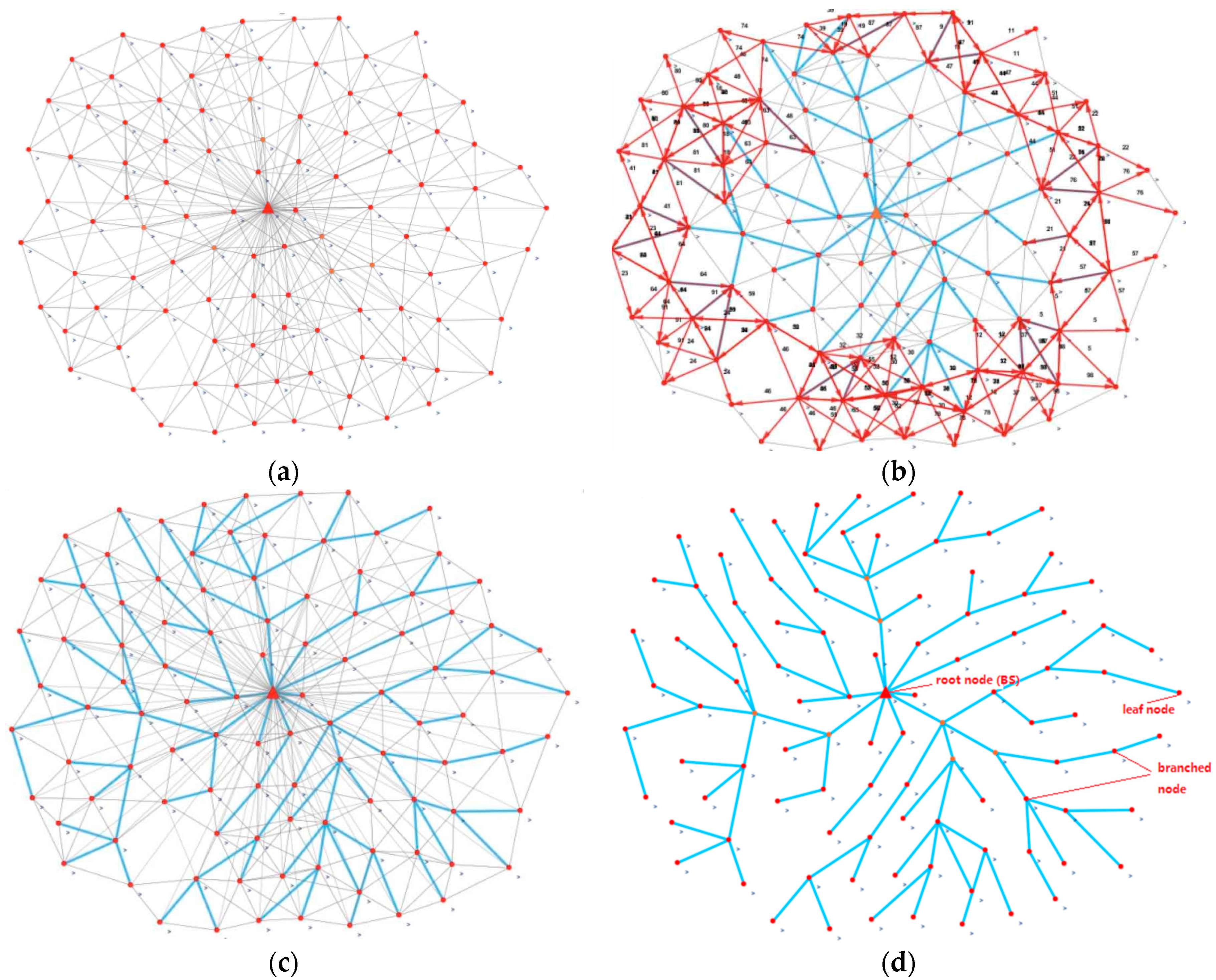
5.1. Flooding Tree Subnetwork
| Algorithm 1 Building the tree sub-network | |
| Input: id root Output: leaf | |
| 1: id = getId() | 13: if (type == T1) and (once == false) then |
| 2: if (id == id root) then | 14: once = true |
| 3: leaf = false | 15: message = (T2, id) |
| 4: once = true | 16: send(message, rid) |
| 5: message = (T1, id) | 17: message = (T1, id) |
| 6: send(message, *) | 18: send(message, *) |
| 7: else | 19: end if |
| 8: leaf = true | 20: if (type == T2) then |
| 9: once = false | 21: leaf = false |
| 10: end if | 22: end if |
| 11: while (true) do | 23: end while |
| 12: (type, rid) = read() | |
5.2. Building Cluster Phase
5.3. Inter-Cluster Communication
5.4. Stable Communication Phase
6. Simulation and Analysis
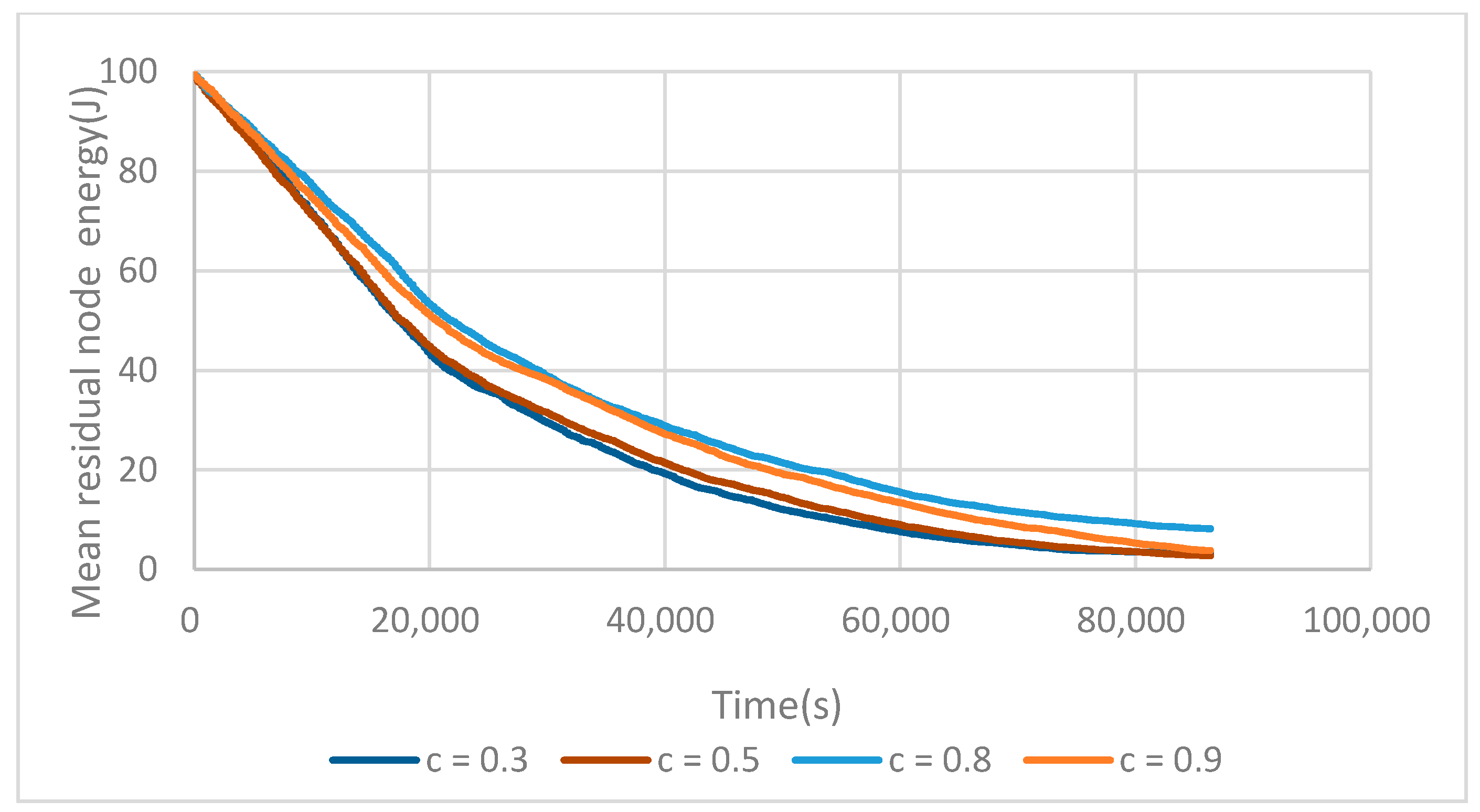
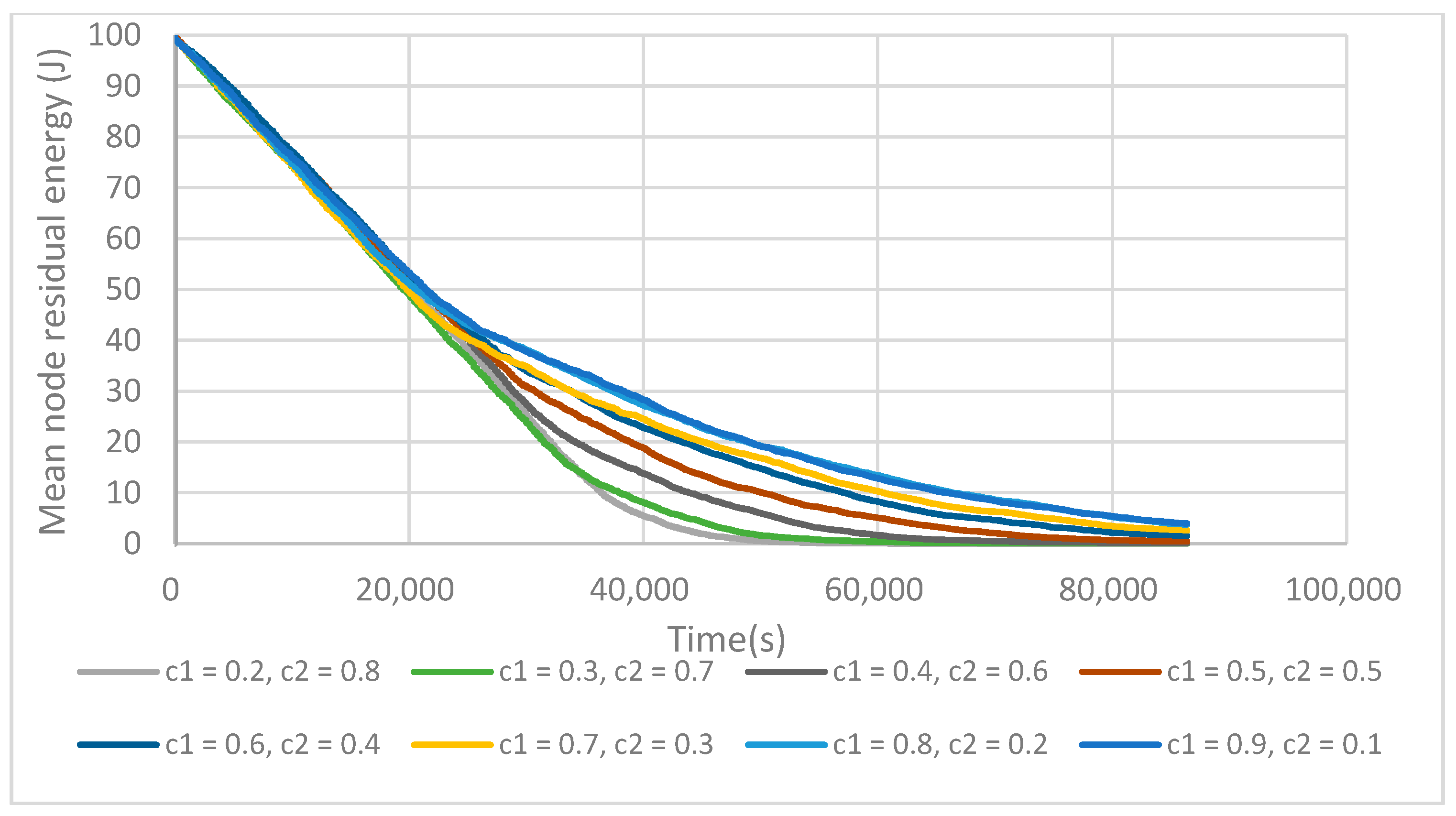
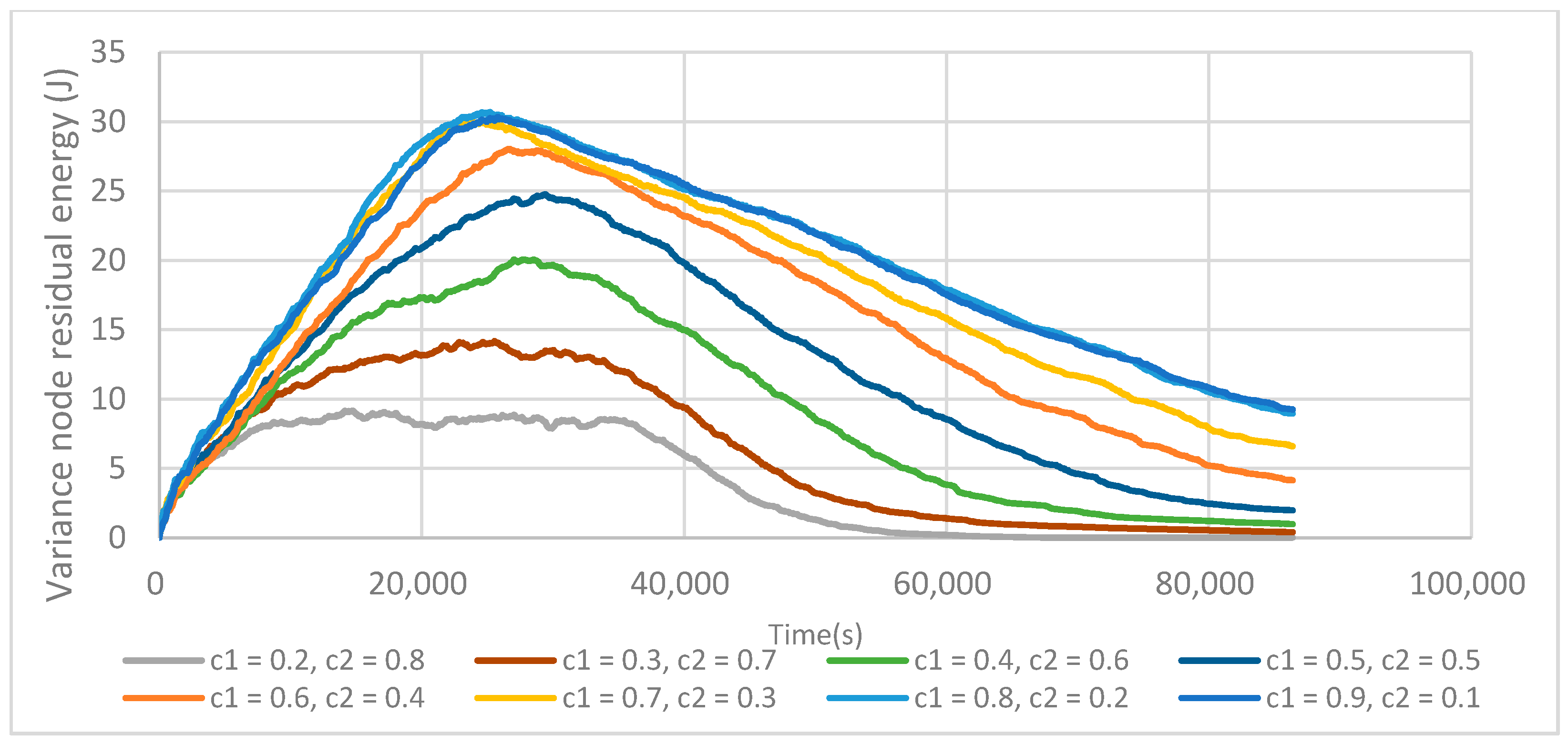
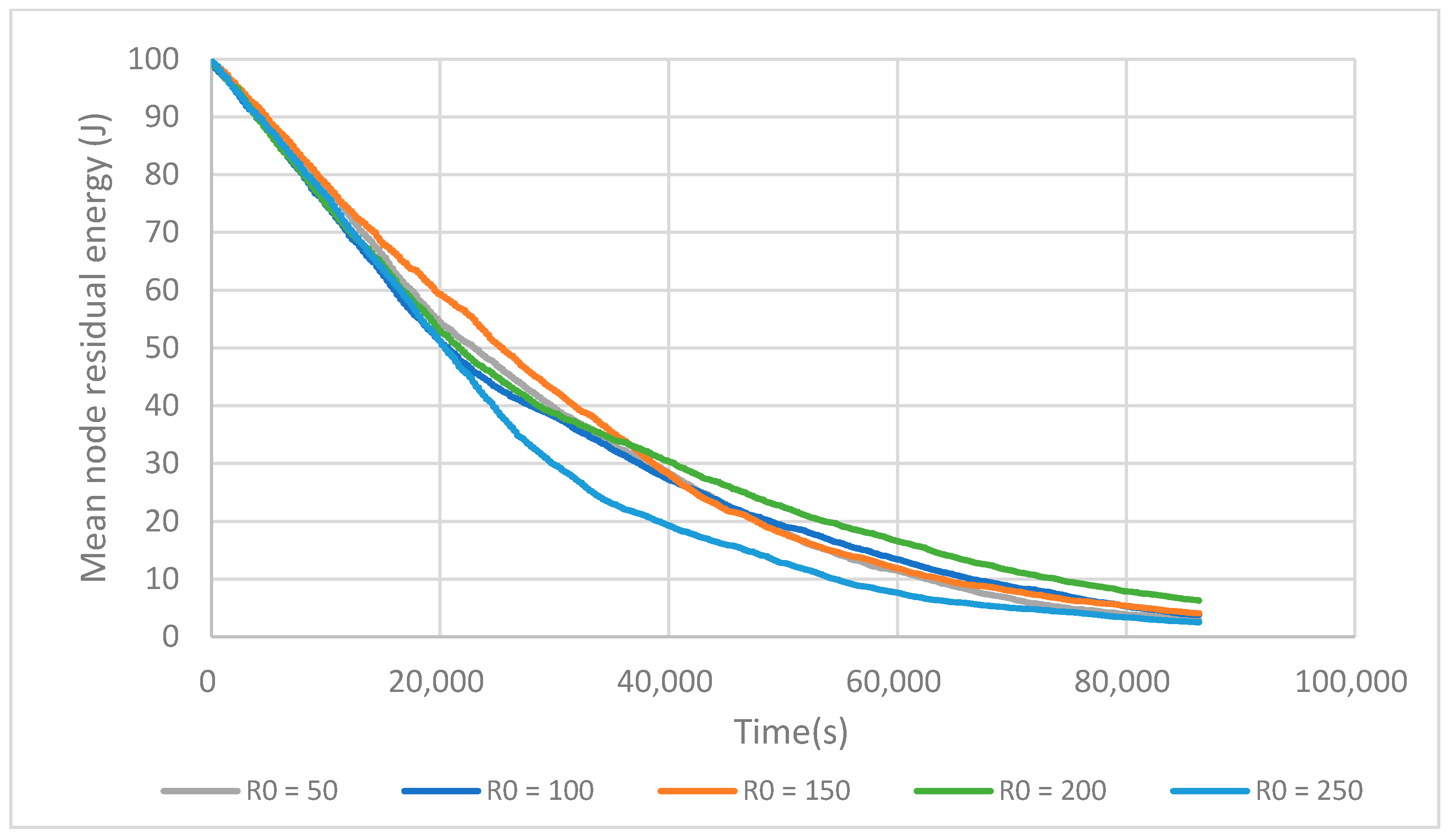
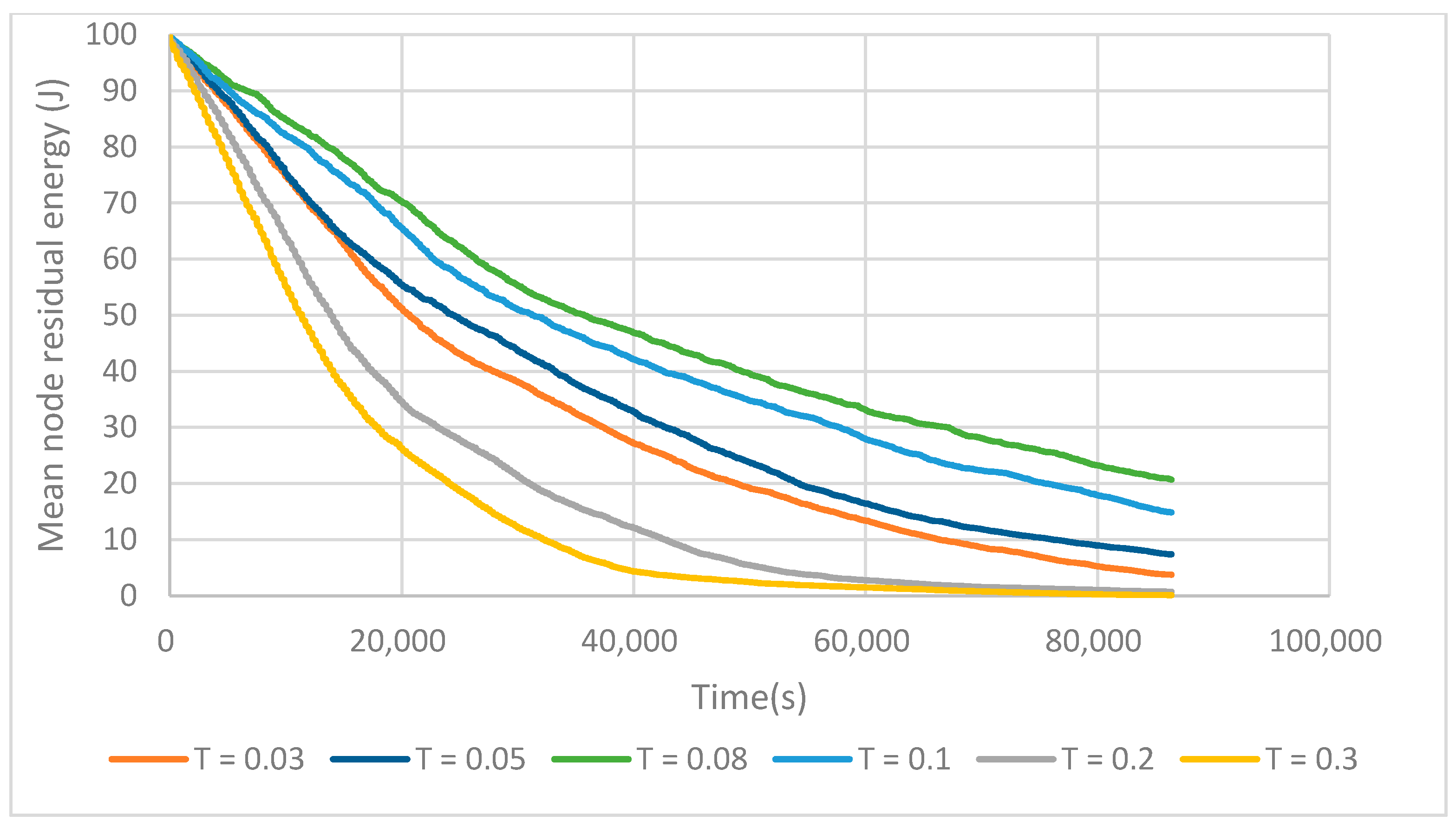
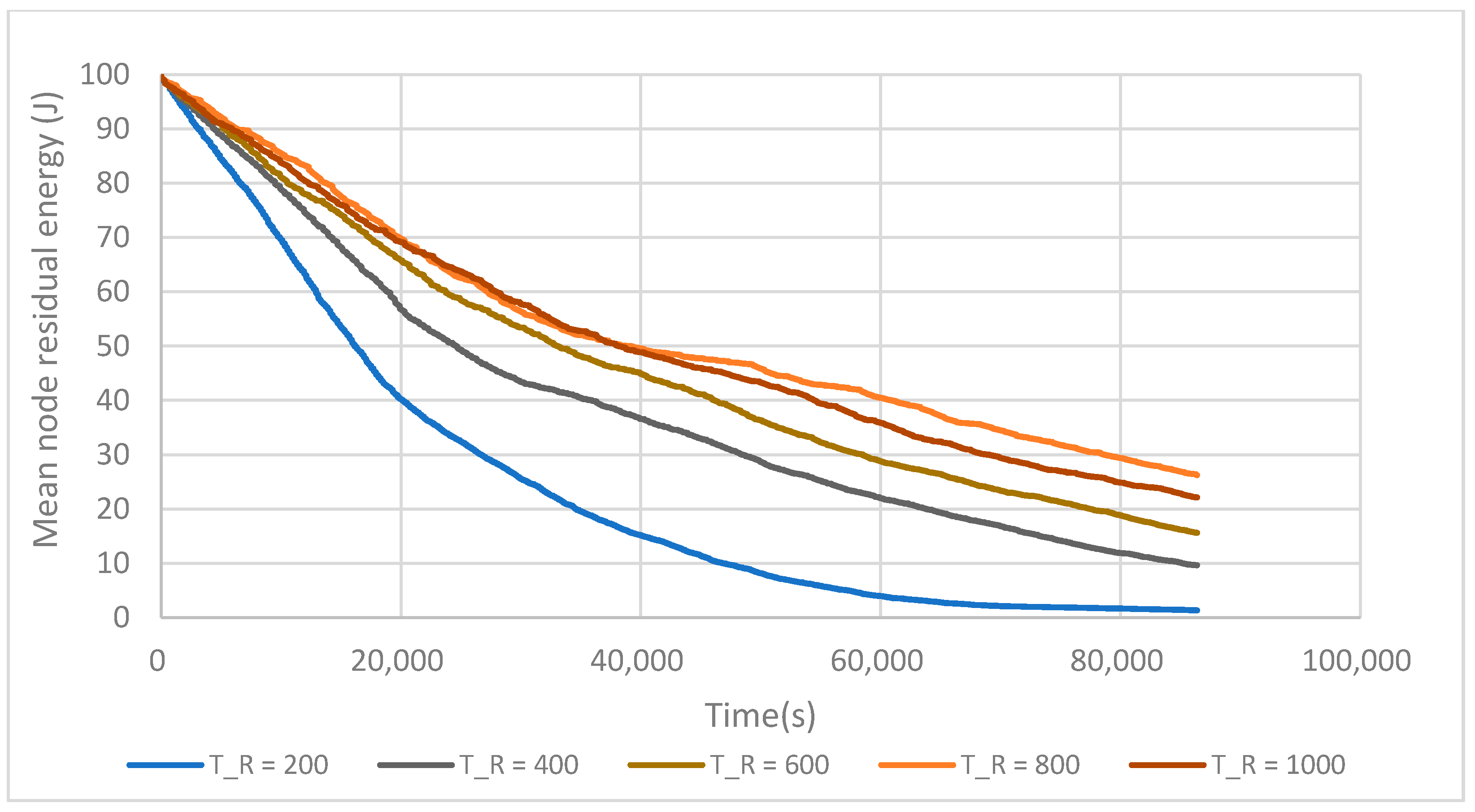
6.1. FTUC Parameterization
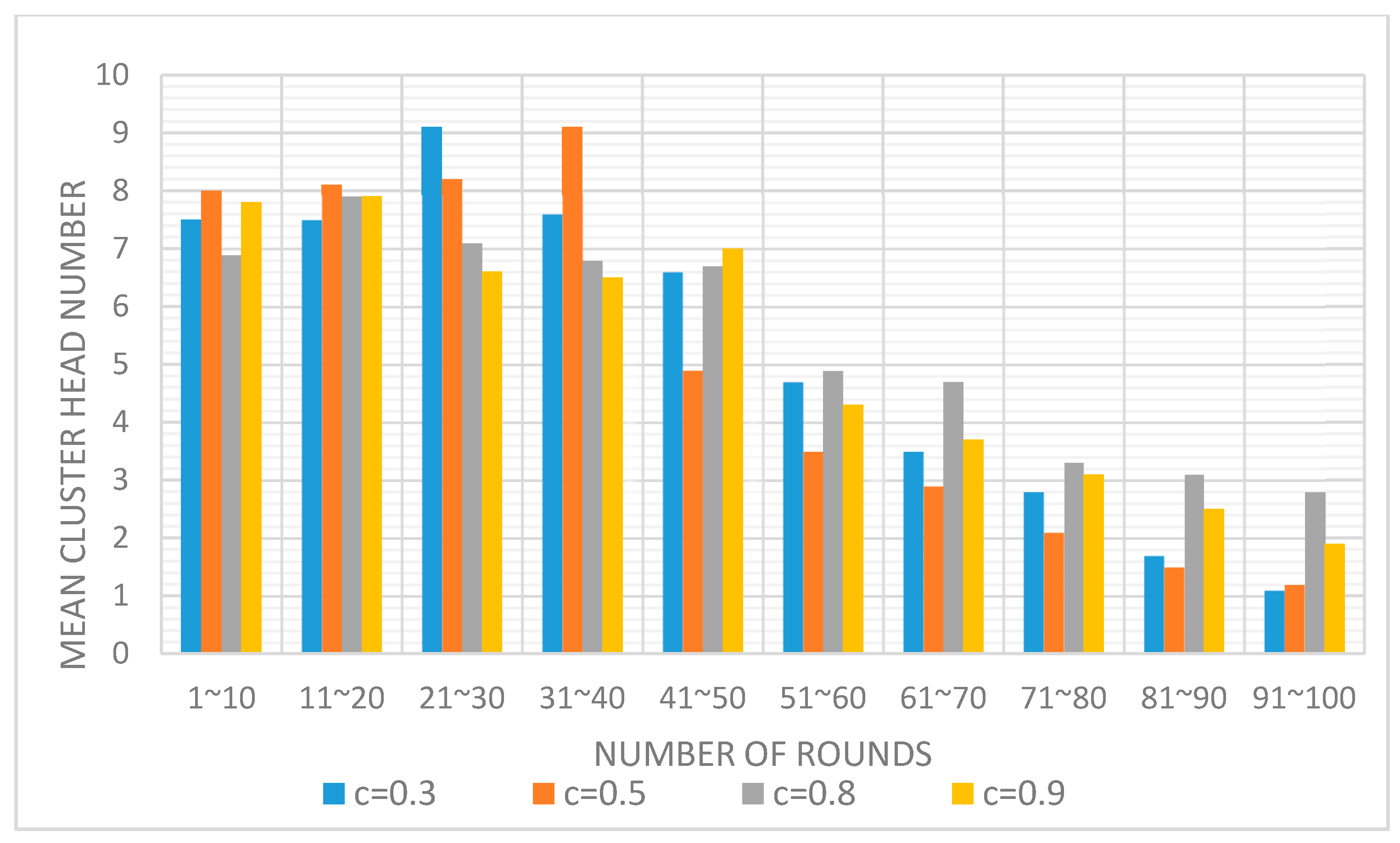
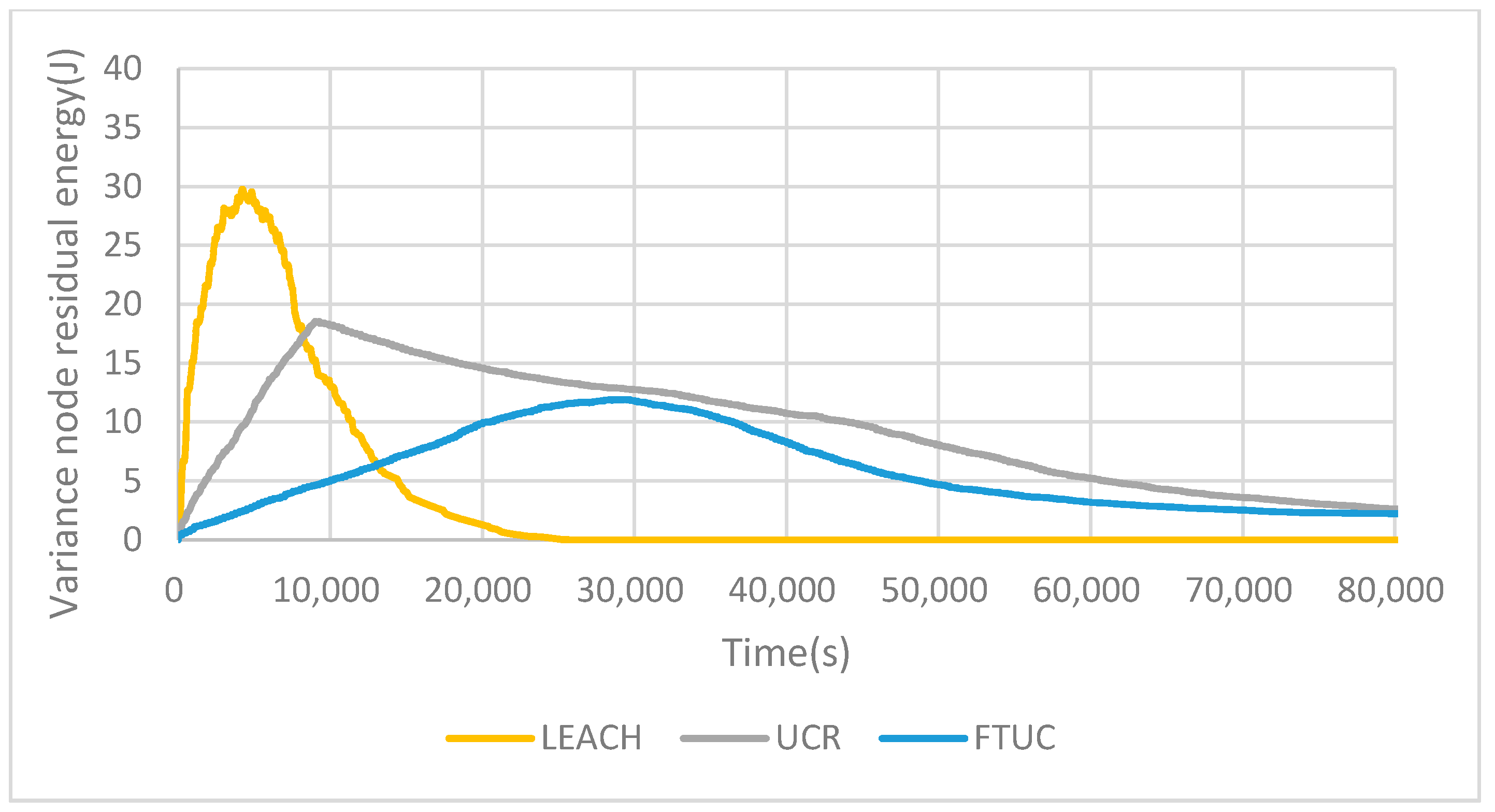
6.2. Analysis of Cluster Creation
6.3. Energy Efficiency
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Akyildiz, L.F.; Welilian, S.; Sankarasubramaniam, Y.; Cayirci, E. A survey on sensor networks. IEEE Commun. 2002, 4, 102–114. [Google Scholar] [CrossRef]
- Akkaya, K.; Younis, M. A survey on routing protocols for wireless sensor networks. Ad Hoc Netw. 2005, 3, 325–349. [Google Scholar] [CrossRef]
- Trasviña-Moreno, C.A.; Blasco, R.; Marco, Á.M.; Casas, R.; Trasvina-Castro, A. Unmanned aerial vehicle based wireless sensor network for marine-coastal environment monitoring. Sensors 2017, 17, 460. [Google Scholar]
- Mittal, A.; Aggarwal, R.; Kaur, S. A survey on Industrial Wireless Sensor Network Routing Algorithms. Int. Res. J. Eng. Technol. 2016, 3, 1983–1989. [Google Scholar]
- Da Xu, L.; He, W.; Li, S. Internet of things in industries: A survey. IEEE Trans. Ind. Inform. 2014, 10, 2233–2243. [Google Scholar]
- Arseni, S.C.; Halunga, S.; Fratu, O.; Vulpe, A.; Suciu, G. Analysis of the security solutions implemented in current Internet of Things platforms. In Proceedings of the Grid, Cloud & High Performance Computing in Science, Cluj-Napoca, Romania, 28–30 October 2015; pp. 1–4. [Google Scholar]
- Golsorkhtabar, M.; Nia, F.K.; Hosseinzadeh, M.; Vejdanparast, Y. The novel energy adaptive protocol for heterogeneous wireless sensor networks. In Proceedings of the 2010 3rd IEEE International Conference on Computer Science and Information Technology, Chengdu, China, 9–11 July 2010; pp. 178–182. [Google Scholar]
- Xu, L.; Collier, R.; O’Hare, G.M.P. A Survey of Clustering Techniques in WSNs and Consideration of the Challenges of Applying Such to 5G IoT Scenarios. IEEE Int. Things J. 2017, 4, 1229–1249. [Google Scholar] [CrossRef]
- Li, X.; Li, D.; Wan, J.; Vasilakos, A.V.; Lai, C.F.; Wang, S. A review of industrial wireless networks in the context of industry 4.0. Wirel. Netw. 2017, 23, 23–41. [Google Scholar] [CrossRef]
- Liu, X. A survey on clustering routing protocols in wireless sensor networks sensors. Sensors 2012, 12, 11113–11153. [Google Scholar] [CrossRef] [PubMed]
- Chang, Y.; Tang, H.; Cheng, Y.; Zhao, Q. Dynamic Hierarchical Energy-Efficient Method Based on Combinatorial Optimization for Wireless Sensor Networks Sensors. Sensors 2017, 17, 1665–1680. [Google Scholar] [CrossRef] [PubMed]
- Chen, G.; Li, C.; Ye, M.; Jie, W. An unequal cluster-based routing protocol in wireless sensor networks. Wirel. Netw. 2009, 15, 193–207. [Google Scholar] [CrossRef]
- Abbasi, A.A.; Younis, M. A survey on clustering algorithms for wireless sensor networks. Comput. Commun. 2007, 30, 2826–2841. [Google Scholar] [CrossRef]
- Heinzelman, W.B.; Chandrakasan, A.P.; Balakrishnan, H. An application-specific protocol architecture for wireless microsensor networks. IEEE Trans. Wirel. Commun. 2002, 1, 660–670. [Google Scholar] [CrossRef]
- Manjeshwar, A.; Agrawal, D.P. TEEN: A Routing Protocol for Enhanced Efficiency in Wireless Sensor Networks. In Proceedings of the 15th International Parallel and Distributed Processing Symposium, San Francisco, CA, USA, 23–27 April 2000; Volume 1, p. 189. [Google Scholar]
- Younis, O.; Fahmy, S. HEED: A Hybrid, Energy-Efficient, Distributed Clustering Approach for Ad hoc Sensor Networks. IEEE Trans. Mob. Comput. 2004, 3, 366–379. [Google Scholar] [CrossRef]
- Han, R.; Yang, W.; Wang, Y.; Kaiming, Y. DCE: A Distributed Energy-Efficient Clustering Protocol for Wireless Sensor Network Based on Double-Phase Cluster-Head Election. Sensors 2017, 17, 998. [Google Scholar] [CrossRef] [PubMed]
- Jin, Y.; Wang, L.; Kim, Y.; Yang, X. EEMC: An energy-efficient multi-level clustering algorithm for large-scale wireless sensor networks. Comput. Netw. 2008, 52, 542–562. [Google Scholar] [CrossRef]
- Soro, S.; Heinzelman, W.B. Prolonging the lifetime of wireless sensor networks via unequal clustering. In Proceedings of the 19th IEEE International Parallel and Distributed Processing Symposium, Denver, CO, USA, 4–8 April 2005. [Google Scholar]
- Jiang, C.J.; Shi, W.R.; Tang, X.L.; Wang, P.; Xiang, M.; Xiang, M. Energy-Balanced Unequal Routing Protocol for Wireless Sensor networks. J. Softw. 2012, 23, 1222–1232. [Google Scholar] [CrossRef]
- Santoro, N. Design and Analysis of Distributed Algorithms; John Wiley & Sons: Hoboken, NJ, USA, 2007; Volume 56. [Google Scholar]
- Cupcarbon. Available online: www.cupcarbon.com (accessed on 19 November 2017).
- Cheng, L.; Niu, J.; Gu, Y.; Luo, C.; He, T. Achieving efficient reliable flooding in low-duty-cycle wireless sensor networks. IEEE/ACM Trans. Netw. 2016, 24, 3676–3689. [Google Scholar] [CrossRef]


| Parameter | Value |
|---|---|
| 50 | |
| 6 | |
| 0.0011 | |
| 87 | |
| 0.001 | |
| 0.001 |
| Parameter | Value |
|---|---|
| C, C1, C2 | 0.8, 0.8, 0.2 |
| T, R0 | 0.08, 200 |
| TR (s) | 800 |
| 0.4, 0.3, 0.3 |
| LT-1 (s) | LT-2 (s) | Improved of LT-1 (%) | Improved of LT-2(%) | |
|---|---|---|---|---|
| LEACH | 5420 | 34,510 | 186.3 | 130.6 |
| UCR | 13,380 | 63,810 | 16.0 | 24.7 |
| FTUC | 15,520 | 79,510 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
He, W.; Pillement, S.; Xu, D. FTUC: A Flooding Tree Uneven Clustering Protocol for a Wireless Sensor Network. Sensors 2017, 17, 2706. https://doi.org/10.3390/s17122706
He W, Pillement S, Xu D. FTUC: A Flooding Tree Uneven Clustering Protocol for a Wireless Sensor Network. Sensors. 2017; 17(12):2706. https://doi.org/10.3390/s17122706
Chicago/Turabian StyleHe, Wei, Sebastien Pillement, and Du Xu. 2017. "FTUC: A Flooding Tree Uneven Clustering Protocol for a Wireless Sensor Network" Sensors 17, no. 12: 2706. https://doi.org/10.3390/s17122706





