A Lightweight Anonymous Authentication Protocol with Perfect Forward Secrecy for Wireless Sensor Networks
Abstract
:1. Introduction
- The first and the simplest solution for the authenticated key establishment is a shared symmetric key between the user and the sensor node. In this case, if a WSN has n sensor nodes and m users, each sensor node needs to store m symmetric keys, each user needs to store n symmetric keys, and the WSN needs to establish nm symmetric keys.
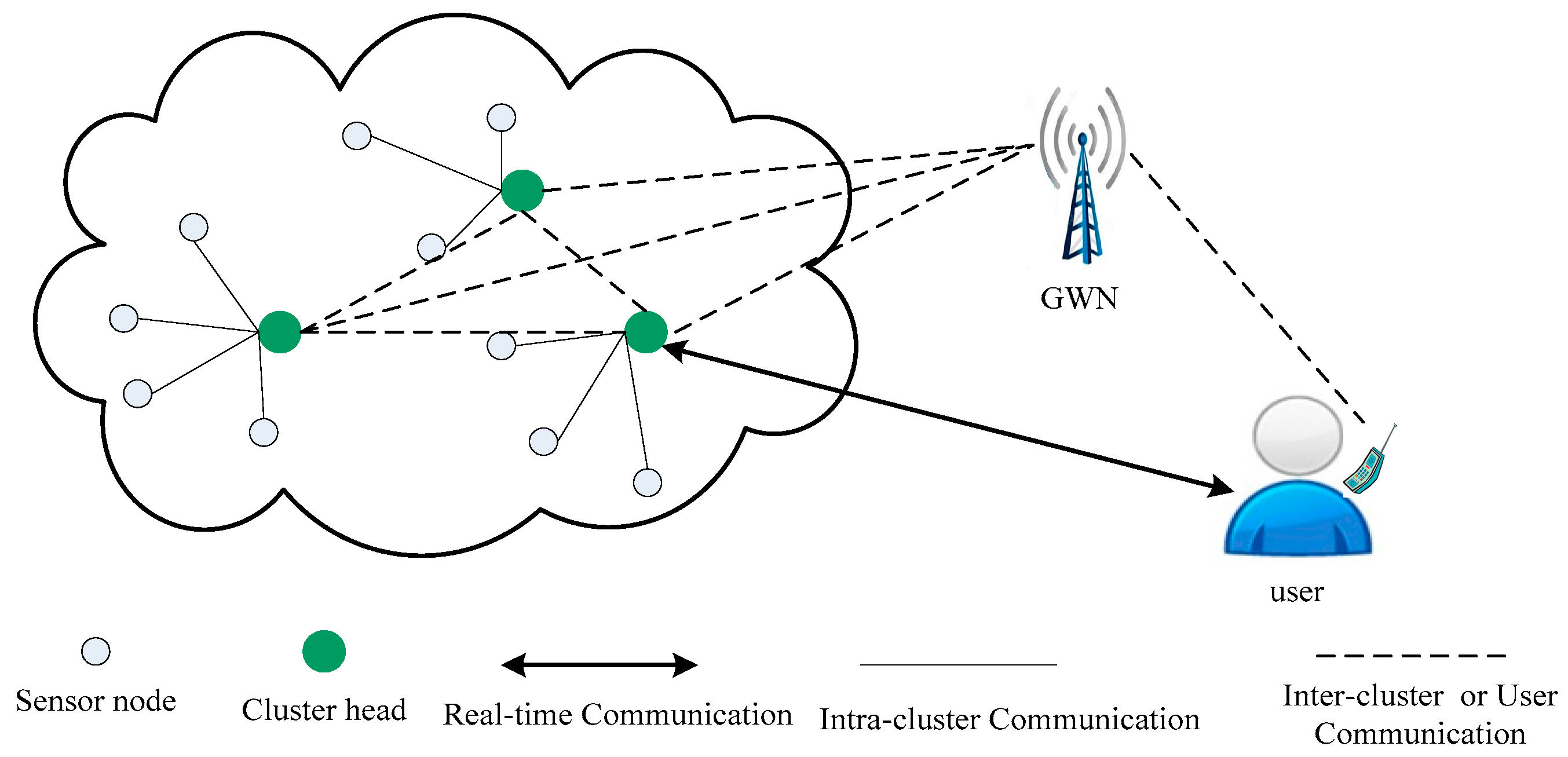
- Third, the user and the sensor node can achieve mutual authentication and establish a session key through a trust gateway node (GWN) [13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30]. In this case, both the user and the sensor node need to share only a single key with the GWN. The GWN can help the user and the sensor authenticate each other and distribute a shared secret session key at each session. After this phase, the user can use this session key to access the real-time data from the desired sensor node without involving the GWN.
1.1. Related Works
1.2. Motivation and Contributions
- (1)
- The proposed scheme is resilient to various kinds of known attacks, such as de-synchronization attack, known session-specific temporary information attack;
- (2)
- The proposed scheme can provide mutual authentication, user anonymity, and perfect forward secrecy, etc.
- (3)
- The proposed scheme uses lightweight cryptographic primitives, such as symmetric encryption/decryption and hash functions. It is very suitable for the resource constrained sensor nodes.
1.3. Adversary Model
- ➢
- A can control the channel among Ui, GWN and Snj. It means that A can eavesdrop, insert, block, and alter the transmitted messages through the public communication channel.
- ➢
- A can obtain one of the two authentication factors, smart card or password. If A has obtained the smart card, he can extract the secret value in the smart card and has the capability of enumerating identity and password space |DID*DPW|.
- ➢
- A may be another legitimate but malicious user in the system.
- ➢
- A may be a legitimate but malicious sensor node.
1.4. Notations
1.5. Organization of the Paper
2. Review of Two Related Schemes
2.1. Review of Lu et al.’s Scheme
2.1.1. User Registration
2.1.2. Sensor Node Registration
2.1.3. Login
2.1.4. Password Update Phase
2.2. Review of Jung et al.’s Scheme
2.2.1. User Registration
2.2.2. Login and Authentication
2.2.3. Password Update Phase
2.3. Security Analysis of Two Related Schemes
2.3.1. Smart Card Loss Attack
2.3.2. Impractical GWN Search Operation
2.3.3. No Provision for Perfect Forward Secrecy
3. The Proposed Scheme
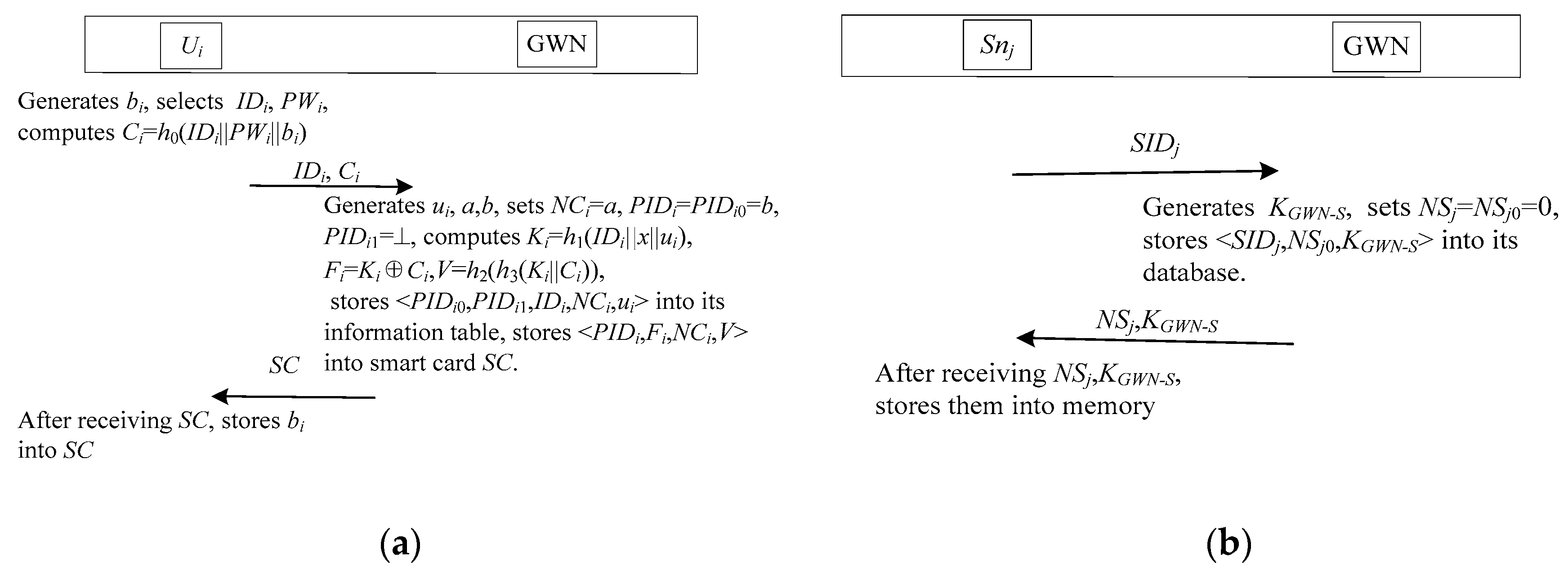
3.1. Registration Phase
3.1.1. User Registration
3.1.2. Sensor Node Registration
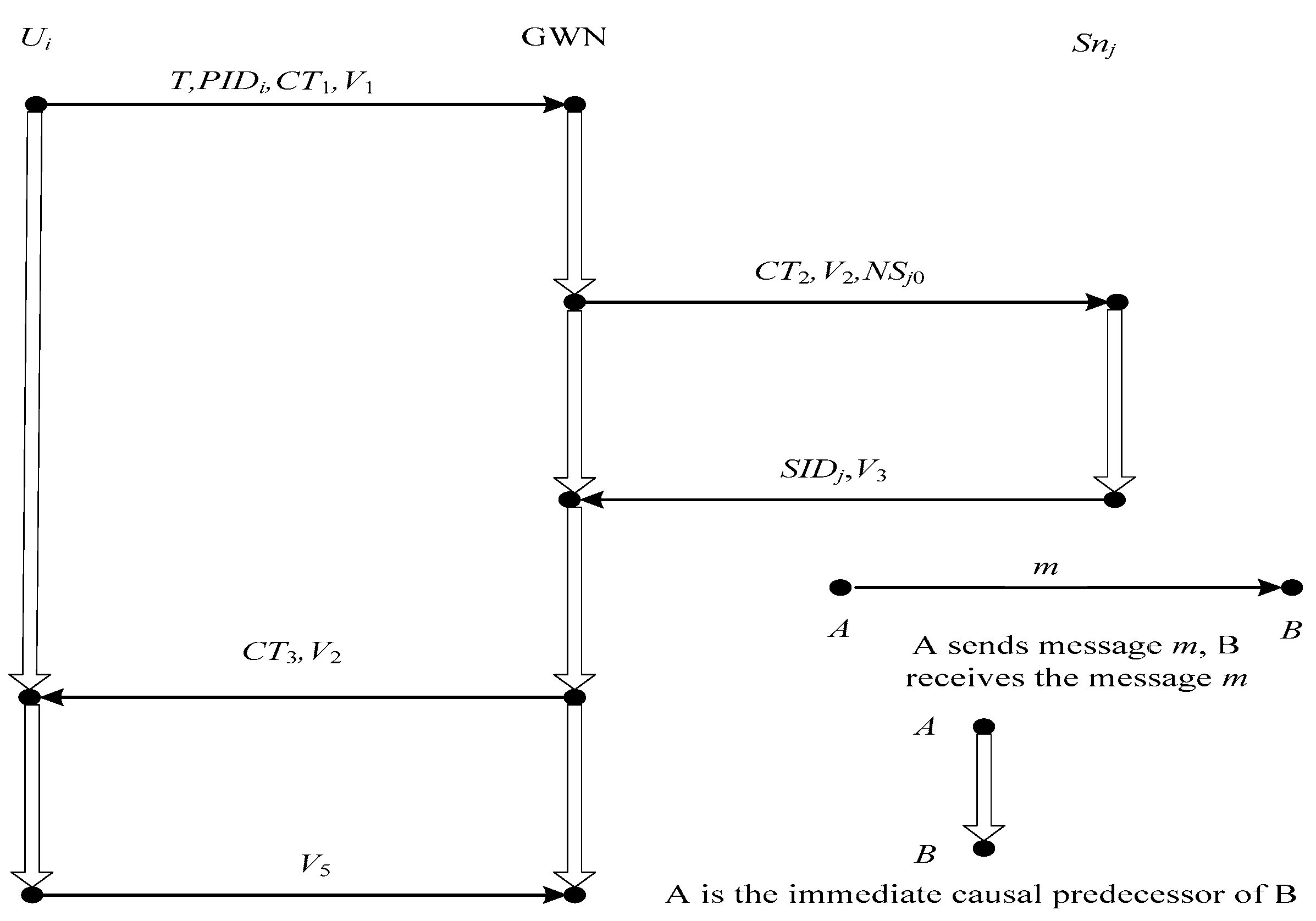
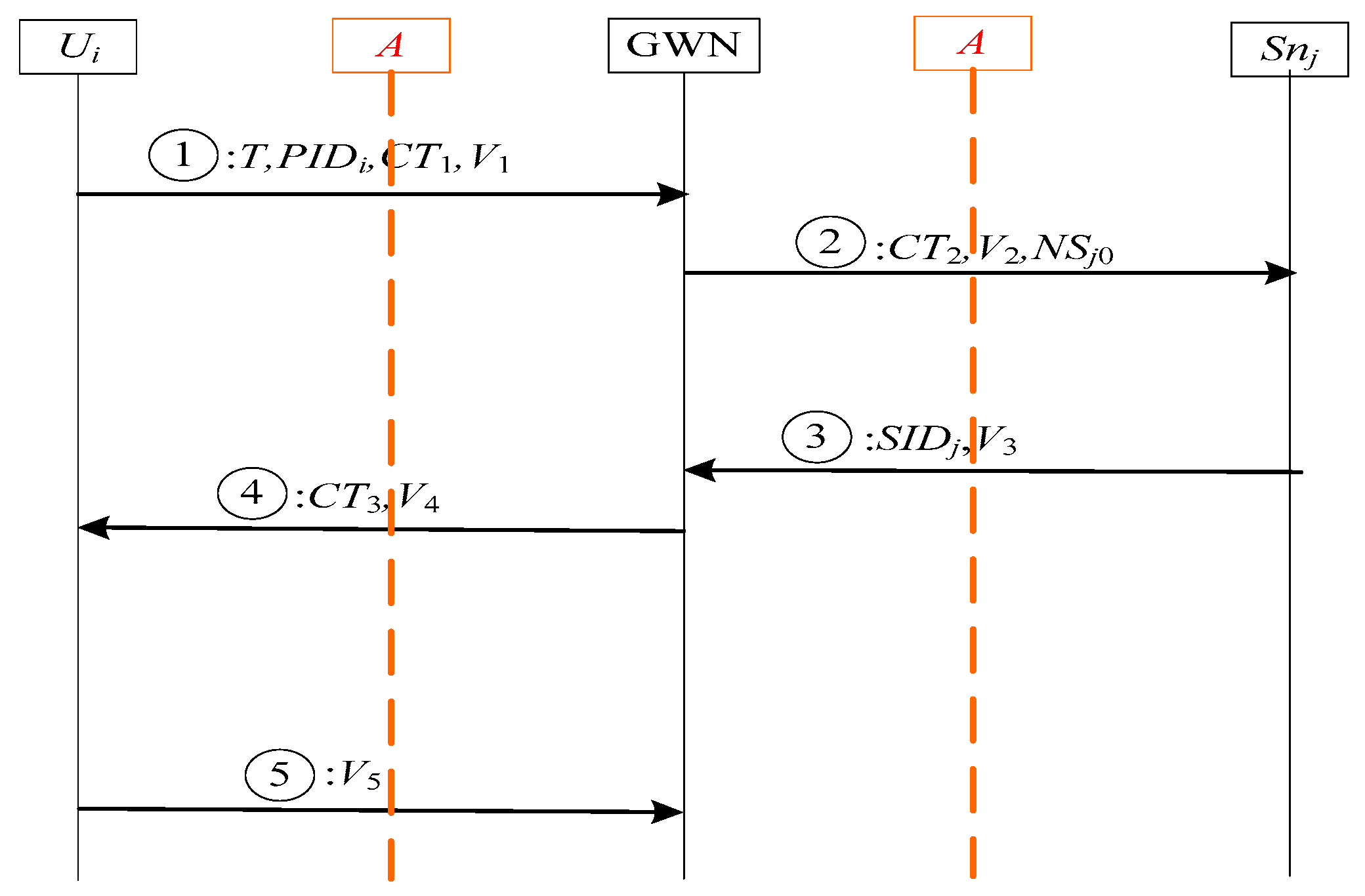
3.2. Authentication and Key Agreement Phase
- (1)
- GWN checks whether the pseudonym identity exists in the user information table.
- If PIDi = PIDi0, it means that both the user’s and GWN’s pseudonym identity are updated in the previous session. Then GWN needs to verify whether the one-time hash chain value updates or not. GWN checks whether PIDi1 = ⊥ holds.
- ✧
- If the equation does not hold, it means that the GWN’s hash chain value does not update in the previous session. So, GWN computes NC’i = h1(NCi), Ki = h1(IDi||x||ui), EK = h1(PIDi0||Ki||NC’i), rA||T = DEK(CT1), V’1 = h3(IDi||rA||Ki||PIDi0||NC’i||T). The GWN checks whether V’1 matches with the received V1. If it holds, GWN generates a random PID’i0, and sets PIDi1 = PIDi0, PIDi0 = PID’i0, NCi = NC’i. Otherwise, GWN terminates the session.
- ✧
- Otherwise, GWN computes Ki = h1(IDi||x||ui), EK = h1(PIDi0||Ki||NCi), rA||T = DEK(CT1), V’1 = h3(IDi||rA||Ki||PIDi0||NCi||T). The GWN checks whether V’1 matches with the received V1. If it holds, GWN generates a random PID’i0, and sets PIDi1 = PIDi0, PIDi0 = PID’i0. Otherwise, GWN terminates the session.
- If PIDi = PIDi1, it means that the user’s pseudonym identity and hash chain are not updated in the previous session. GWN computes Ki = h1(IDi||x||ui), EK = h1(PIDi1||Ki||NCi), rA||T = DEK(CT1), V’1 = h3(IDi||rA||Ki||PIDi1||NCi||T). GWN checks whether V’1 matches with the received V1. If it holds, GWN generates a random PID’i0, and sets PIDi0 = PID’i0. Otherwise, GWN terminates the session.
- If PIDi ≠ PIDi0, PIDi ≠ PIDi1, GWN terminates the session.
- (2)
- GWN randomly generates a session key sk and chooses a specified sensor node SIDj, and computes CT2 = (sk||IDi)⊕h0(KGWN-S||SIDj||NSj0), V2 = h3(IDi||SIDj||sk||KGWN-S||NSj0). Subsequently, GWN updates KGWN-S = h1(KGWN-S||SIDj), NSj0 = NSj0 + 1.
- (3)
- GWN sends {CT2,V2,NSj0} to the sensor node Snj that Ui wants to interact with via the public channel.
3.3. Password Update Phase
3.4. Dynamically Deploy Sensor Nodes Phase
4. Security Analysis of Our Scheme
4.1. Authentication Proof Based on Strand Space Model
4.1.1. The Basic Notion of Strand Space Model
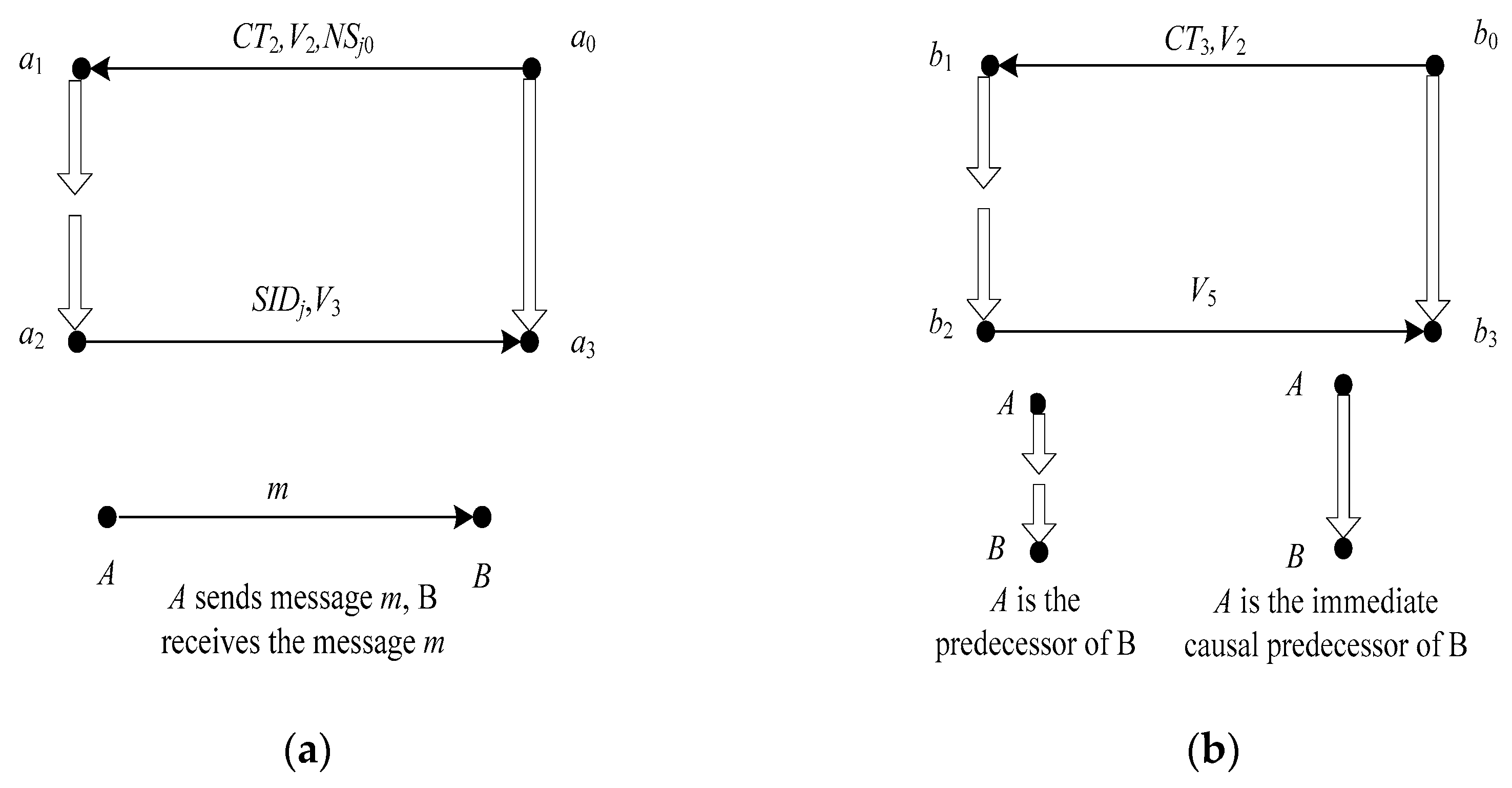
- +t/-t: send/receive a term t.
- <s,i>: a node of s, where s ∈ Σ, 1 ≤ i ≤ length(tr(r)). If n = <s,i>, then, index(n) = i, strand(n) = s, term(n) is the ith signed term in the trace of s, and uns_term(n) is the unsigned part of the ith signed term in the strand of s.
- n1 → n2: it means that the node n1 sends a message and n2 receives the message.
- n1 n2: it means that n1 is an immediate causal predecessor of n2, n1 = <s,i> and n2 = <s,i + 1>.
- n1 + n2: it means that n1 is a precedence of n2, n1 = <s,i> and n2 = <s,j>, i < j.
- S: a set of edges with respect to the causal relations →, and +.
- n n’: it means that there are one or more edges in S leading from n to n’.
- n n’: it means that there are zero or more edges in S leading from n to n’.
- T: a set of atomic messages.
- K: a set of cryptographic keys, which disjoints from T.
- {m}K: it means that the message m is encrypted by the key K.
4.1.2. Penetrator Strands
4.1.3. Authentication Proof Based on the Stand Space Model
- (1)
- Ui → GWN: PIDi, CT1, V1
- (2)
- GWN → Snj: CT2, V2, NSj0
- (3)
- Snj → GWN: SIDj, V3
- (4)
- GWN → Ui: CT3, V4
- (5)
- Ui → GWN: V5
- (1)
- Penetrator strands s ∈ P.
- (2)
- ‘User strands’ with trace U[IDi,SIDj,T, rA,PIDi,PIDi0,Ki,NCi,sk], defined to be < + {PIDi, CT1, V1}, -{CT3, V4}, + {V5}>, where IDi, SIDj ∈ Tname, rA, sk,PIDi ∈ T, Ki,NCi ∈ K, rA Tname, rA K.
- (3)
- ‘GWN strands’ with trace G[IDi,SIDj,T, rA,PIDi0, PIDi1,Ki,NCi,sk,KGWN-S, NSj0],defined to be < −{PIDi, CT1, V1}, + { CT2,V2,NSj }, −{SIDj, V3}, + { CT3,V4}, −{V5} >, where IDi, SIDj ∈ Tname, rA, sk,PIDi,PIDi0,PIDi1 ∈ T, Ki,NCi,KGWN-S ∈ K, sk Tname, sk K.
- (4)
- ‘Sensor node’ strands with trace Sn[IDi,SIDj,sk,KGWN-S,NSj0],defined to be <−{CT2,V2,NSj0}, + {SIDj, V3} >
4.2. Formal Security Validation Using ProVerif
- event beginUGparam(host), event endUGparam(host),
- event beginGUparam(host), event endGUparam(host),
- event beginGSparam(host), event endGSparam(host),
- event beginSGparam(host), event endSGparam(host).
- ➢
- Query not attacker(secretA[]), not attacker(secretB[]),not attacker(secretC[]), not attacker(secretD[])
- ✧
- RESULT not attacker(secretA[]), not attacker(secretB[]), not attacker(secretC[]), not attacker(secretD[]) are true.
- ✧
- The result means that the adversary has not trace to reconstruct secretA, secretB, secretC, secretD. Hence, the session key sk is secure to resist cracking.
- ➢
- Query inj-event(endGUparam(GWN)) ═> inj-event(beginGUparam(GWN))
- ✧
- RESULT inj-event(endGUparam(GWN)) = = > inj-event(beginGUparam(GWN)) is true.
- ✧
- This result means that the execution of the event beginGUparam(GWN) is preceded by the execution of the event endGUparam(GWN). Hence, the authentication of the user to the GWN holds.
- ➢
- Query inj-event(endUGparam(user)) ═> inj-event(beginUGparam(user))
- ✧
- RESULT inj-event(endUGparam(user)) ═> inj-event(beginUGparam(user)) is true.
- ✧
- This result means that the execution of the event beginUGparam(user) is preceded by the execution of the event endUGparam(user). Hence, the authentication of the GWN to the user holds.
- ➢
- Query inj-event(endGSparam(GWN)) ═> inj-event(beginGSparam(GWN))
- ✧
- RESULT inj-event(endGSparam(GWN)) ═> inj-event(beginGSparam(GWN)) is true.
- ✧
- This result means that the execution of the event beginGSparam(GWN) is preceded by the execution of the event endGSparam(GWN). Hence, the authentication of the sensor node to the GWN holds.
- ➢
- Query inj-event(endSGparam(SN)) ═> inj-event(beginSGparam(SN))
- ✧
- RESULT inj-event(endSGparam(SN)) ═> inj-event(beginSGparam(SN)) is true.
- ✧
- This result means that the execution of the event beginSGparam(GWN) is preceded by the execution of the event endSGparam(GWN). Hence, the authentication of the GWN to the sensor node holds.
4.3. Further Security Analysis of Our Scheme
4.3.1. Resistance to De-synchronization Attack
4.3.2. Mutual Authentication
4.3.3. User Anonymity
4.3.4. Perfect Forward Secrecy
4.3.5. Resistance to Smart Card Loss Attack
4.3.6. Resistance Known Session-Specific Temporary Information Attack
4.3.7. Resistance to Stolen Verifier Table Attack
4.3.8. Resistance to User Impersonation Attack
4.3.9. Resistance to Sensor Node Spoofing Attack
4.3.10. Resistance to Replay Attack
4.3.11. Resistance to Man-in-the-middle Attack
4.3.12. Resistance to Wrong Password Login/Update Attack
4.4. Security Comparisons
5. Performance Analysis
5.1. Computation Analysis
- Th: the time complexity of the general hash function.
- TE/D: the time complexity of general symmetric-key encryption/decryption algorithm.
5.2. Communication Analysis
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Appendix A. The Details in the Proof of Our Proposed Scheme Using Strand Space Model
- (1)
- Σ is a LAAP space and C is a bundle containing a GWN’s strand s with trace G[IDi,SIDj,T, rA,PIDi0, PIDi1,Ki,NCi,sk,KGWN-S, NSj0];
- (2)
- EK KP, KGWN-S KP, where EK = h1(PIDi||Ki||NCi); and
- (3)
- rA ≠ PIDi0 ≠ sk ≠ PIDi ≠ PIDi1, PIDi0 and sk are uniquely originating in Σ.
- (1)
- Σ is a LAAP space and C is a bundle containing a user’s strand s with trace U[IDi,SIDj,rA,PIDi,PIDi0,Ki,NCi,sk] and a sensor node’s strand t with Sn[IDi,SIDj,sk,KGWN-S,NSj0];
- (2)
- GEK KP, KGWN-S KP, where GEK = h1(rA||PIDi1||Ki||NCi); and
- (3)
- rA ≠ PIDi0 ≠ sk ≠ PIDi ≠ PIDi1, PIDi0 and sk are uniquely originating in Σ.
References
- Yick, J.; Mukherjee, B.; Ghosal, D. Wireless sensor network survey. Comput. Netw. 2008, 52, 2292–2330. [Google Scholar] [CrossRef]
- O’Donovan, T.; O’Donoghue, J.; Sreenan, C.; Sammon, D.; O’Reilly, P.; O’Connor, K.A. A Context Aware Wireless Body Area Network (BAN). In Proceedings of the 3rd International Conference on Pervasive Computing Technologies for Healthcare (PervasiveHealth 2009), London, UK, 1–3 April 2009. [Google Scholar]
- Hart, J.K.; Martinez, K. Environmental Sensor Networks: A revolution in the earth system science? Earth Sci. Rev. 2006, 78, 177–191. [Google Scholar] [CrossRef]
- Tiwari, A.; Ballal, P.; Lewis, F.L. Energy-efficient wireless sensor network design and implementation for condition-based maintenance. ACM Trans. Sens. Netw. 2007, 3, 1. [Google Scholar] [CrossRef]
- Gnawali, O.; Jang, K.Y.; Paek, J.; Vieira, M.; Govindan, R.; Greenstein, B.; Joki, A.; Estrin, D.; Kohler, E. The tenet architecture for tiered sensor networks. In Proceedings of the 4th International Conference on Embedded Networked Sensor Systems, 31 October–3 November 2006; ACM: New York, NY, USA, 2006; pp. 153–166. [Google Scholar] [CrossRef]
- Yang, D.; Misra, S.; Fang, X.; Xue, G.; Zhang, J. Two-tiered constrained relay node placement in wireless sensor networks: Computational complexity and efficient approximations. IEEE Trans. Mob. Comput. 2012, 11, 1399–1411. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Chilamkurti, N. A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Inf. Sci. 2015, 321, 263–277. [Google Scholar] [CrossRef]
- He, D.; Chen, C.; Chan, S.; Bu, J.; Yang, L.L. Security Analysis and Improvement of a Secure and Distributed Reprogramming Protocol for Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2013, 60, 5348–5354. [Google Scholar] [CrossRef]
- Perrig, A.; Stankovic, J.; Wagner, D. Security in wireless sensor networks. Commun. ACM 2004, 47, 53–57. [Google Scholar] [CrossRef]
- Koyama, K.; Maurer, U.M.; Okamoto, T.; Vanstone, S.A. New public-key schemes based on elliptic curves over the ring Zn. In Advances in Cryptology-CRYPTO’91; Springer: Berlin/Heidelberg, Germany, 1992; pp. 252–266. [Google Scholar]
- Watro, R.; Kong, D.; Cuti, S.F.; Gardiner, C.; Lynn, C.; Kruus, P. TinyPK: Securing sensor networks with public key technology. In Proceedings of the 2nd ACM Workshop on Security of Ad Hoc and Sensor Networks, Washington, DC, USA, 25 October 2004; pp. 59–64. [Google Scholar]
- Hwang, M.S.; Li, L.H. A new remote user authentication scheme using smart cards. IEEE Trans. Consum. Electron. 2000, 46, 28–30. [Google Scholar] [CrossRef]
- Wong, K.H.; Zheng, Y.; Cao, J.; Wang, S. A dynamic user authentication scheme for wireless sensor networks. In Proceedings of the IEEE International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, Taichung, Taiwan, 5–7 June 2006; pp. 1–9. [Google Scholar]
- Das, M.L. Two-Factor user authentication in wireless sensor networks. IEEE Trans. Wirel. Commun. 2009, 8, 1086–1090. [Google Scholar] [CrossRef]
- Huang, H.F.; Chang, Y.F.; Liu, C.H. Enhancement of two-factor user authentication in wireless sensor networks. In Proceedings of the 2010 Sixth International Conference on Intelligent Information Hiding and Multimedia Signal Processing, Darmstadt, Germany, 15–17 October 2010; pp. 27–30. [Google Scholar]
- Chen, T.H.; Shih, W.K. A robust mutual authentication protocol for wireless sensor networks. ETRI J. 2010, 32, 704–712. [Google Scholar] [CrossRef]
- Khan, M.K.; Alghathbar, K. Cryptanalysis and security improvements of two-factor user authentication in wireless sensor networks. Sensors 2010, 10, 2450–2459. [Google Scholar] [CrossRef] [PubMed]
- Jiang, Q.; Ma, Z.; Ma, J.; Li, G. Security enhancement of robust user authentication framework for wireless sensor networks. China Commun. 2012, 9, 103–111. [Google Scholar]
- He, D.J.; Gao, Y.; Chan, S.; Chen, C.; Bu, J.J. An enhanced two-factor user authentication scheme in wireless sensor networks. Ad Hoc Sens. Wirel. Netw. 2010, 10, 361–371. [Google Scholar]
- Das, A.K.; Sharma, P.; Chatterjee, S.; Sing, J.K. A dynamic password-based user authentication scheme for hierarchical wireless sensor networks. J. Netw. Comput. Appl. 2012, 35, 1646–1656. [Google Scholar] [CrossRef]
- Turkanovic, M.; Hölbl, M. An improved dynamic password-based user authentication scheme for hierarchical wireless sensor networks. Elektron. Elektrotech. 2013, 19, 109–116. [Google Scholar] [CrossRef]
- Turkanović, M.; Brumen, B.; Hölbl, M. A novel user authentication and key agreement scheme for heterogeneous ad hoc wireless sensor networks, based on the Internet of Things notion. Ad Hoc Netw. 2014, 20, 96–112. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. Understanding security failures of two-factor authentication schemes for real-time applications in hierarchical wireless sensor networks. Ad Hoc Netw. 2014, 20, 1–15. [Google Scholar] [CrossRef]
- Xue, K.P.; Ma, C.S.; Hong, P.L.; Ding, R. A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J. Netw. Comput. Appl. 2013, 36, 316–323. [Google Scholar] [CrossRef]
- Jiang, Q.; Ma, J.; Lu, X.; Tian, Y. An Efficient Two-Factor User Authentication Scheme with Unlinkability for Wireless Sensor Networks. Peer-to-Peer Netw. Appl. 2014, 8, 1070–1081. [Google Scholar] [CrossRef]
- Das, A.K. A Secure and Robust Temporal Credential-based Three-Factor User Authentication Scheme for Wireless Sensor Networks. Peer-to-Peer Netw. Appl. 2016, 9, 223–244. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. A Realistic Lightweight Anonymous Authentication Protocol for Securing Real-Time Application Data Access in Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2016, 63, 7124–7132. [Google Scholar] [CrossRef]
- Lu, Y.; Li, L.; Peng, H.; Yang, Y. An Energy Efficient Mutual Authentication and Key Agreement Scheme Preserving Anonymity for Wireless Sensor Networks. Sensors 2016, 16, 837. [Google Scholar] [CrossRef] [PubMed]
- Jung, J.; Kim, J.; Choi, Y.; Won, D. An Anonymous User Authentication and Key Agreement Scheme Based on a Symmetric Cryptosystem in Wireless Sensor Networks. Sensors 2016, 16, 1299. [Google Scholar] [CrossRef] [PubMed]
- Mir, O.; Munilla, J.; Kumari, S. Efficient anonymous authentication with key agreement protocol for wireless medical sensor networks. Peer-to-Peer Netw. Appl. 2017, 10, 79–91. [Google Scholar] [CrossRef]
- Wang, D.; Wang, N.; Wang, P.; Qing, S. Preserving privacy for free: Efficient and provably secure two-factor authentication scheme with user anonymity. Inf. Sci. 2015, 321, 162–178. [Google Scholar] [CrossRef]
- Wang, D.; He, D.; Wang, P.; Chu, C.H. Anonymous two-factor authentication in distributed systems: Certain goals are beyond attainment. IEEE Trans. Dependable Secur. Comput. 2015, 12, 428–442. [Google Scholar] [CrossRef]
- Park, D.; Boyd, C.; Moon, S.J. Forward Secrecy and Its Application to Future Mobile Communications Security. In Proceedings of the Public Key Cryptography, Melbourne, Australia, 18–20 January 2000; pp. 433–445. [Google Scholar]
- Ma, C.; Wang, D.; Zhao, S. Security Flaws in Two Improved Remote User Authentication Schemes Using Smart Cards. Int. J. Commun. Syst. 2012, 27, 2215–2227. [Google Scholar] [CrossRef]
- Jiang, Q.; Zeadally, S.; Ma, J.; He, D. Lightweight Three-Factor Authentication and Key Agreement Protocol for Internet-Integrated Wireless Sensor Networks. IEEE Access 2017, 5, 3376–3392. [Google Scholar] [CrossRef]
- Wang, D.; Wang, P. On the anonymity of two-factor authentication schemes for wireless sensor networks: Attacks, principle and solutions. Comput. Netw. 2014, 73, 41–57. [Google Scholar] [CrossRef]
- Fabrega, F.; Herzog, J.C.; Guttman, J.D. Strand spaces: Why is a security protocol correct? In Proceedings of the IEEE Symposium on Security and Privacy, Oakland, CA, USA, 6 May 1998; pp. 160–171. [Google Scholar]
- Fabrega, F.; Herzog, J.C. Strand spaces: Proving Security Protocol Protocols Correct. J. Comput. Secur. 1999, 7, 191–230. [Google Scholar] [CrossRef]
- Abadi, M.; Blanchet, B. Computer-assisted verification of a protocol for certified email. Sci. Comput. Program. 2005, 58, 3–27. [Google Scholar] [CrossRef]
- Abadi, M.; Glew, N.; Horne, B.; Pinkas, B. Certified email with a light on-line trusted third party: Design and implementation. In Proceedings of the 11th International World Wide Web Conference, Honolulu, HI, USA, 7–11 May 2002; ACM: Honolulu, HI, USA, 2002; pp. 387–395. [Google Scholar]
- Abadi, M.; Blanchet, B.; Cedric, F. Just Fast Keying in the pi calculus. ACM Trans. Inf. Syst. Secur. 2007, 10, 9. [Google Scholar] [CrossRef]
- Blanchet, B.; Smyth, B.; Cheval, V.; Sylvestre, M. ProVerif 1.96: Automatic Cryptographic Protocol Verifier, User Manual and Tutorial. Available online: http://prosecco.gforge.inria.fr/personal/bblanche/proverif/ (accessed on 21 September 2016).
- Xiong, L. Lightweight-Anonymous-Authentication-WSNs. Available online: https://github.com/idle010/Lightweight-Anonymous-Authentication-WSNs (accessed on 26 October 2017).
- Wang, D.; Wang, P. On the usability of two-factor authentication. In Proceedings of the 10th International Conference on Security and Privacy in Communication Systems, Beijing, China, 24–26 September 2014; pp. 141–150. [Google Scholar]
- Wang, D.; Wang, P. Two Birds with One Stone: Two-Factor Authentication with Security beyond Conventional Bound. IEEE Trans. Dependable Secur. Comput. 2016, 1–23. [Google Scholar] [CrossRef]
- He, D.; Kumar, N.; Lee, J.H.; Sherratt, R. Enhanced three-factor security protocol for consumer USB mass storage devices. IEEE Trans. Consum. Electron. 2014, 60, 30–37. [Google Scholar] [CrossRef]
- Lee, C.C.; Chen, C.T.; Wu, P.H.; Chen, T.Y. Three-factor control protocol based on elliptic curve cryptosystem for universal serial bus mass storage devices. IET Comput. Digit. Tech. 2013, 7, 48–55. [Google Scholar] [CrossRef]



| Notation | Descriptions |
|---|---|
| Ui | The user |
| Snj | The sensor node |
| GWN | The gateway node |
| SC | The smart card |
| IDi,PWi | Unique identity and password of Ui |
| SIDj | Unique identity of Snj |
| IDGWN | Unique identity of GWN |
| PID | Pseudonym identity |
| PIDi | Pseudonym identity of Ui in the user side |
| TIDi | A random number of Ui generated in the GWN |
| x | The secret key of GWN |
| xi | The shared secret key between GWN and Ui |
| KGWN_S | The shared secret key between GWN and Snj |
| bi | A random number generate by Ui |
| SK | The session key |
| EK,DK | Encryption/Decryption using the symmetric key K |
| h,h0,h1,h3 | One-way hash function |
| h2 | One-way hash function, h2:{0,1}*→{0,1,...,1023} |
| T,T1,T2,T3,T4 | Current timestamp |
| || | String concatenation operation |
| ⊕ | XOR operation |
| Features | Lu et al. [28] | Jung et al. [29] | Ours |
|---|---|---|---|
| Resistance to de-synchronization attack | √ | √ | √ |
| Mutual authentication | √ | √ | √ |
| User anonymity | √ | √ | √ |
| Perfect forward security | × | × | √ |
| Smart card loss attack | × | × | √ |
| Resistance to known session-specific temporary information attack | √ | √ | √ |
| Resistance to stolen verifier table attack | √ | √ | √ |
| Resistance to user impersonation attack | √ | √ | √ |
| Resistance to sensor node spoofing attack | √ | √ | √ |
| Resistance to replay attack | √ | √ | √ |
| Resistance to man-in-the-middle attack | √ | √ | √ |
| Resistance to wrong password login/update attack | √ | √ | √ |
| Schemes | Users | GWN | Sensor Node | Total |
|---|---|---|---|---|
| Lu et al. [28] | 7Th + 2TE/D ≈ 0.01344s | 8Th + 4TE/D ≈ 0.02496s | 4Th + 2TE/D ≈ 0.01248s | 19Th + 8TE/D ≈ 0.05088s |
| Jung et al. [29] | 5Th + 2TE/D ≈ 0.0128s | 5Th + 2TE/D ≈ 0.0128s | 4Th ≈ 0.00128s | 13Th + 4TE/D ≈ 0.02688s |
| Ours | 9Th + 2TE/D ≈ 0.01408s | 11Th + 2TE/D ≈ 0.01472s | 4Th ≈ 0.00128s | 25Th + 4TE/D ≈ 0.03008s |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xiong, L.; Peng, D.; Peng, T.; Liang, H.; Liu, Z. A Lightweight Anonymous Authentication Protocol with Perfect Forward Secrecy for Wireless Sensor Networks. Sensors 2017, 17, 2681. https://doi.org/10.3390/s17112681
Xiong L, Peng D, Peng T, Liang H, Liu Z. A Lightweight Anonymous Authentication Protocol with Perfect Forward Secrecy for Wireless Sensor Networks. Sensors. 2017; 17(11):2681. https://doi.org/10.3390/s17112681
Chicago/Turabian StyleXiong, Ling, Daiyuan Peng, Tu Peng, Hongbin Liang, and Zhicai Liu. 2017. "A Lightweight Anonymous Authentication Protocol with Perfect Forward Secrecy for Wireless Sensor Networks" Sensors 17, no. 11: 2681. https://doi.org/10.3390/s17112681




