Smart Collaborative Caching for Information-Centric IoT in Fog Computing
Abstract
:1. Introduction
2. Related Work
2.1. IoT and ICN
2.2. IoT and Fog Computing
2.3. Comparison and Discussion
3. Smart Collaborative Caching for IoT
3.1. Preliminary Foundation
3.2. Model Establishment
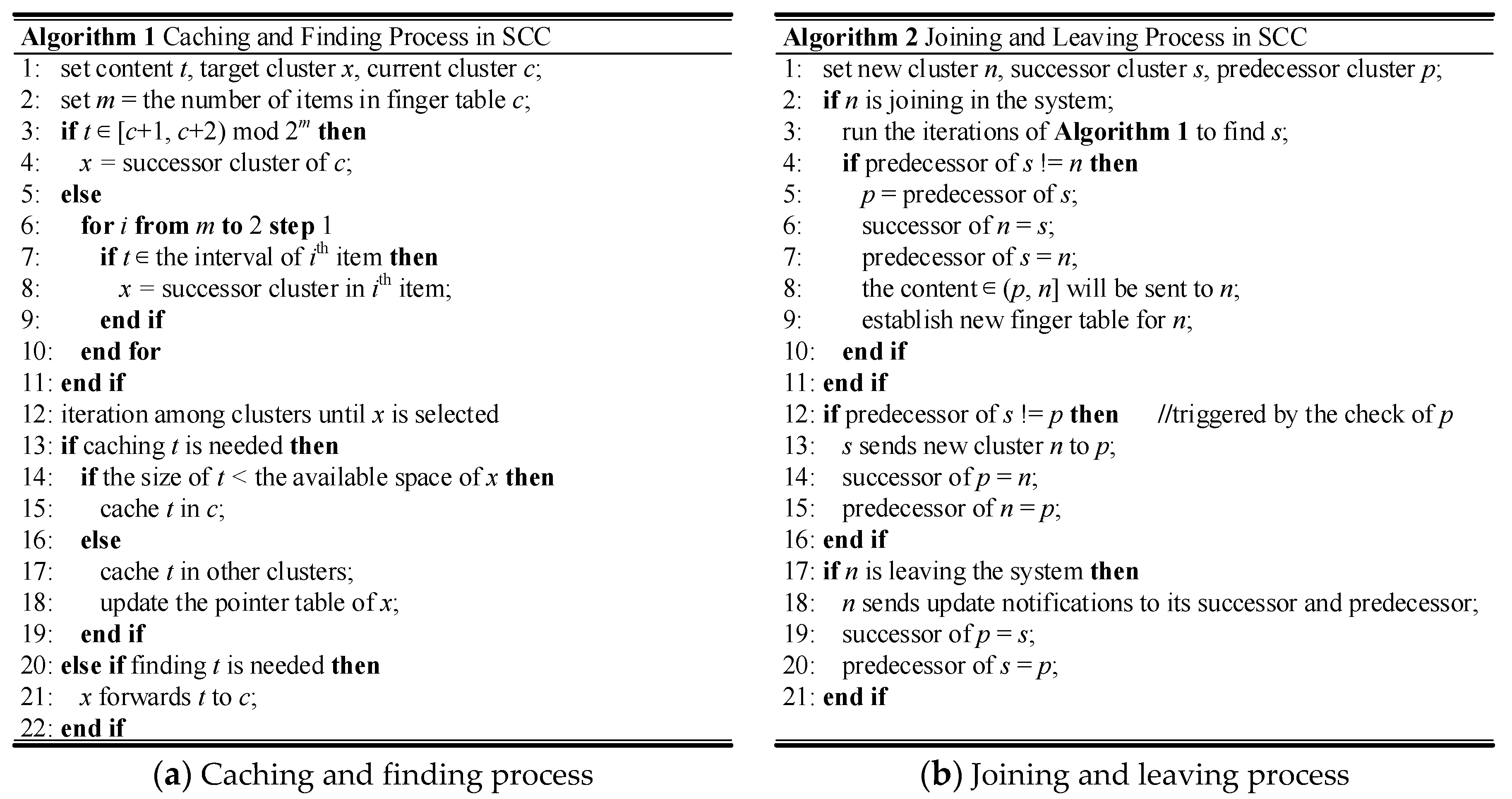
3.3. Primary Operations
3.3.1. Caching and Finding
3.3.2. Joining and Leaving
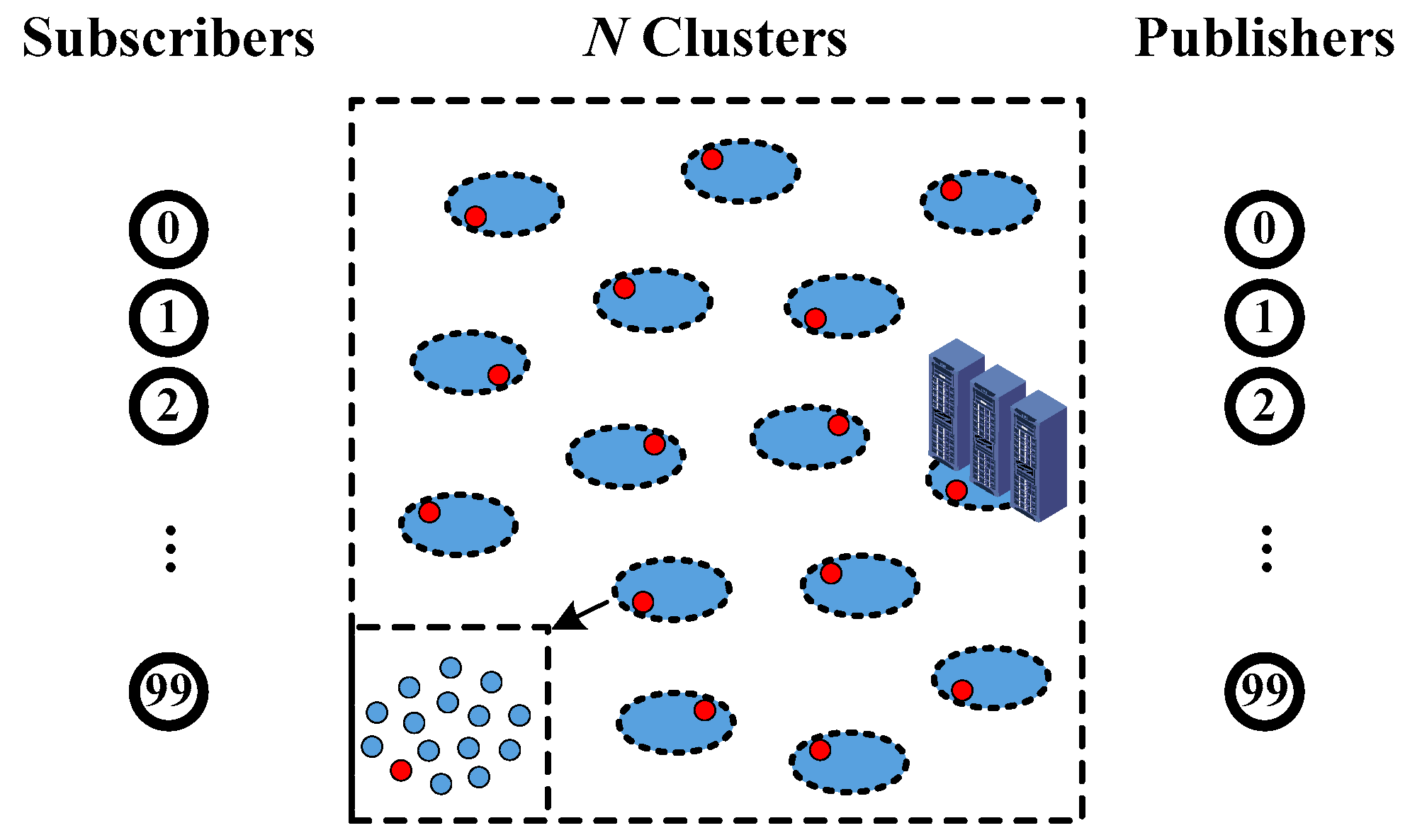
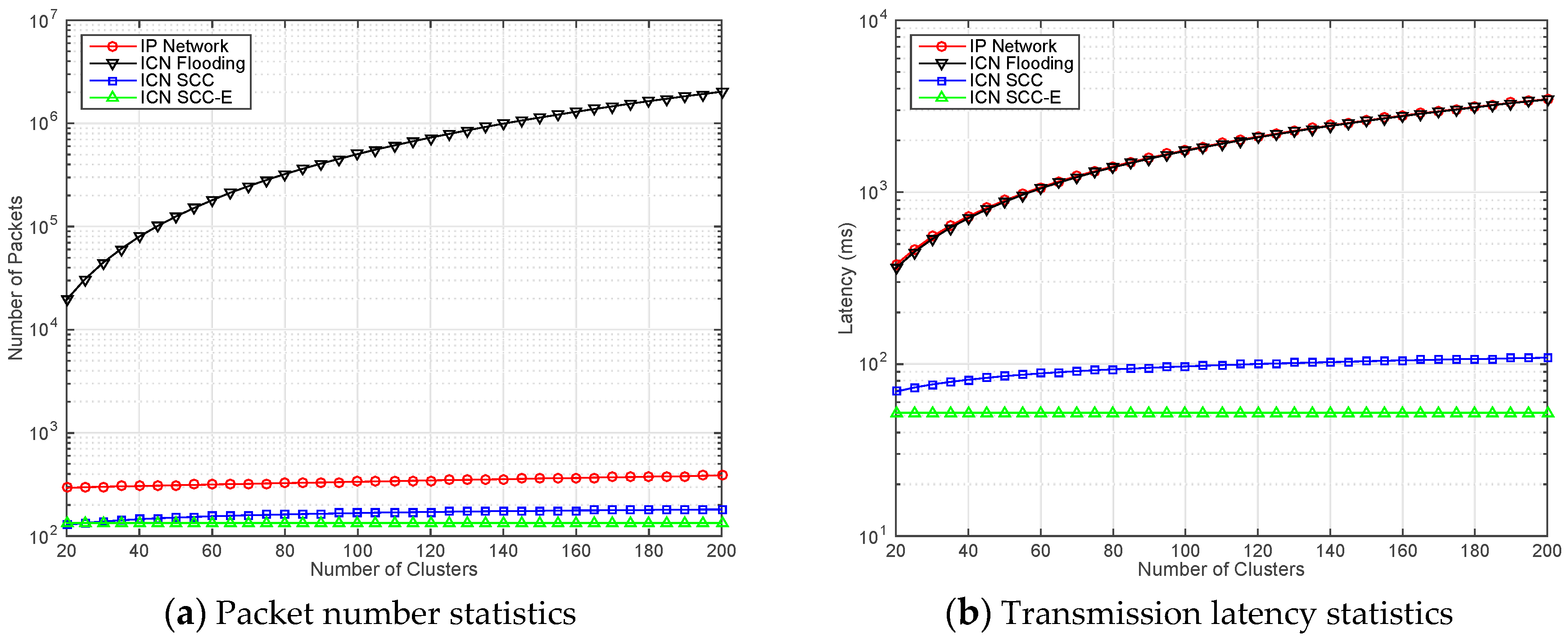
4. Validation and Discussion
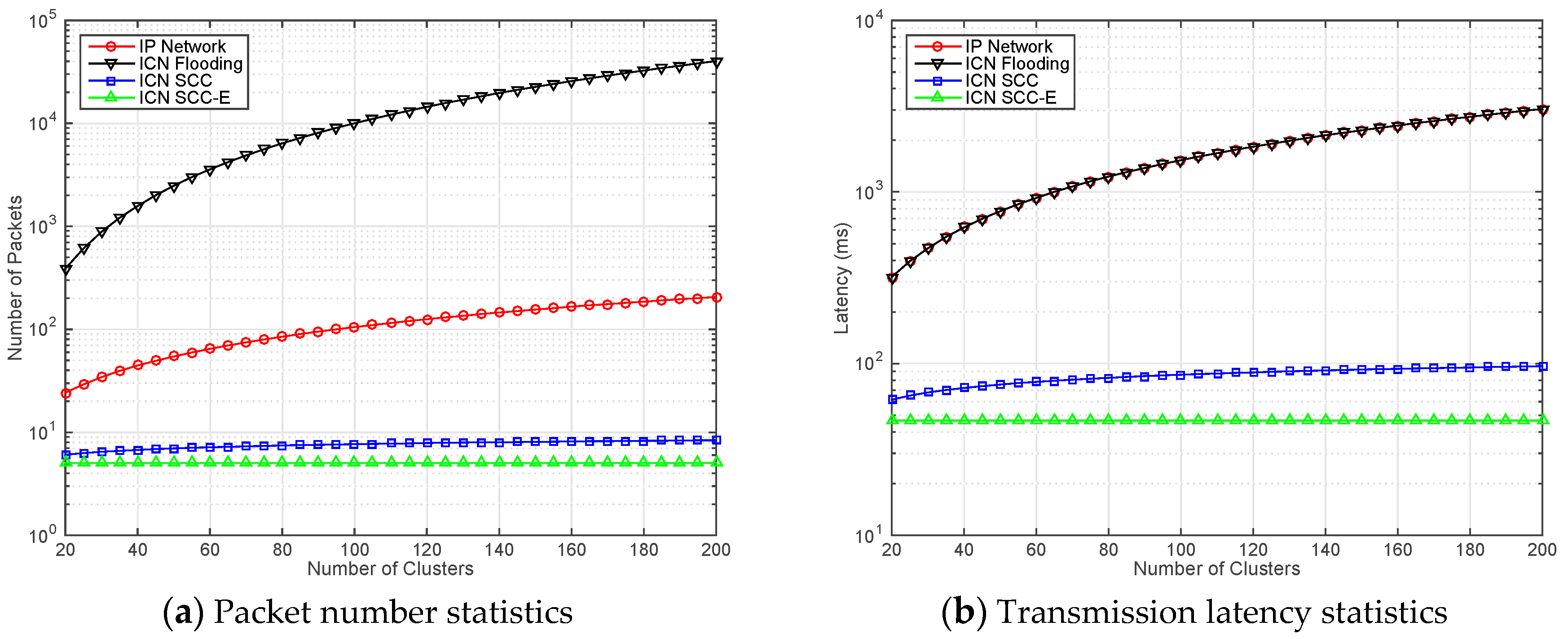
4.1. Scenario One: Simple Status Inquiry (One Request and One Response)
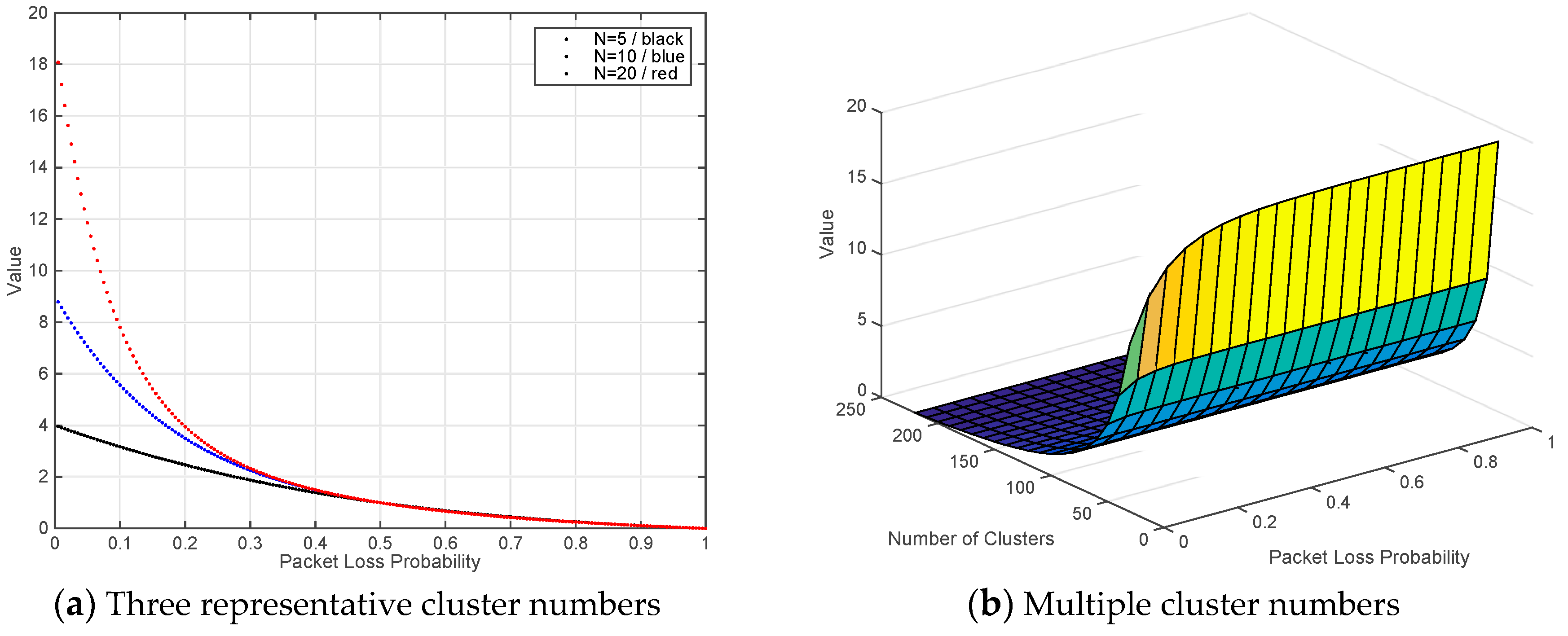
4.2. Scenario Two: Complex Content Sharing (One Request and Multiple Responses).
5. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Giridhar, P.; Amin, M.T.; Abdelzaher, T.; Wang, D.; Kaplan, L.; George, J.; Ganti, R. ClariSense+: An Enhanced Traffic Anomaly Explanation Service Using Social Network Feeds. Pervasive Mob. Comput. 2016, 33, 140–155. [Google Scholar] [CrossRef]
- Choo, K.-K.R.; Rokach, L.; Bettini, C. Mobile Security and Privacy: Advances, Challenges and Future Research Directions. Pervasive Mob. Comput. 2016, 32, 1–2. [Google Scholar] [CrossRef]
- Xu, C.; Jia, S.; Wang, M.; Zhong, L.; Zhang, H.; Muntean, G.-M. Performance-Aware Mobile Community-based VoD Streaming over Vehicular Ad Hoc Networks. IEEE Trans. Veh. Technol. 2015, 64, 1201–1217. [Google Scholar] [CrossRef]
- Guan, K.; Zhong, Z.; Alonso, J.I.; Briso-Rodriguez, C. Measurement of Distributed Antenna Systems at 2.4 GHz in a Realistic Subway Tunnel Environment. IEEE Trans. Veh. Technol. 2012, 61, 834–837. [Google Scholar] [CrossRef] [Green Version]
- Detweiler, C.A.; Hindriks, K.V. A Survey of Values, Technologies and Contexts in Pervasive Healthcare. Pervasive Mob. Comput. 2016, 27, 1–13. [Google Scholar] [CrossRef]
- Zhang, J.; Xue, N.; Huang, X. A Secure System for Pervasive Social Network-Based Healthcare. IEEE Access 2016, 4, 9239–9250. [Google Scholar] [CrossRef]
- Premarathne, U.S.; Khalil, I.; Atiquzzaman, M. Secure and Reliable Surveillance over Cognitive Radio Sensor Networks in Smart Grid. Pervasive Mob. Comput. 2015, 22, 3–15. [Google Scholar] [CrossRef]
- Mukherjee, J.C.; Shukla, S.; Gupta, A. High-quality Aware Scheduling for Imbalance Reduction through Charging Coordination of Electric Vehicles in Smart Grid. Pervasive Mob. Comput. 2015, 21, 104–118. [Google Scholar] [CrossRef]
- Xu, C.; Jia, S.; Zhong, L.; Muntean, G.-M. Socially Aware Mobile Peer-to-Peer Communications for Community Multimedia Streaming Services. IEEE Commun. Mag. 2015, 53, 150–156. [Google Scholar] [CrossRef]
- Guan, K.; Li, G.; Kuerner, T.; Molisch, A.F.; Peng, B.; He, R.; Hui, B.; Kim, J.; Zhong, Z. On Millimeter Wave and THz Mobile Radio Channel for Smart Rail Mobility. IEEE Trans. Veh. Technol. 2016, 66, 5658–5674. [Google Scholar] [CrossRef]
- Lindgren, A.; Abdesslem, F.B.; Ahlgren, B.; Schelén, O.; Malik, A.M. Design Choices for the IoT in Information-Centric Networks. In Proceedings of the 2016 13th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016; pp. 882–888. [Google Scholar]
- Li, S.; Zhang, Y.; Raychaudhuri, D.; Ravindran, R.; Zheng, Q.; Dong, L.; Wang, G. IoT Middleware Architecture over Information-Centric Network. In Proceedings of the 2015 IEEE Globecom Workshops (GC Wkshps), San Diego, CA, USA, 6–10 December 2015; pp. 1–7. [Google Scholar]
- Baccellil, E.; Mehlis, C.; Hahm, O.; Schmidt, T.C.; Wählisch, M. Information centric networking in the IoT: Experiments with NDN in the wild. In Proceedings of the ACM-ICN ’14: 1st ACM Conference on Information-Centric Networking, Paris, France, 24–26 September 2014; pp. 77–86. [Google Scholar]
- Amadeo, M.; Campolo, C.; Quevedo, J.; Corujo, D.; Molinaro, A.; Iera, A.; Aguiar, R.L. Information-centric networking for the internet of things: Challenges and opportunities. IEEE Netw. 2016, 30, 92–100. [Google Scholar] [CrossRef]
- Waltari, O.; Kangasharju, J. Content-Centric Networking in the Internet of Things. In Proceedings of the 2016 13th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016; pp. 73–78. [Google Scholar]
- Melvix, J.S.M.L.; Lokesh, V.; Polyzos, G.C. Energy Efficient Context based Forwarding Strategy in Named Data Networking of Things. In Proceedings of the ACM Conference on Information-Centric Networking, Kyoto, Japan, 26–28 September 2016; pp. 249–254. [Google Scholar]
- Datta, S.K.; Bonnet, C. Interworking of NDN with IoT architecture elements: Challenges and solutions. In Proceedings of the 2016 IEEE 5th Global Conference on Consumer Electronics, Kyoto, Japan, 11–14 October 2016; pp. 1–2. [Google Scholar]
- Siris, V.A.; Thomas, Y.; Polyzos, G.C. Supporting the IoT over Integrated Satellite-Terrestrial Networks Using Information-Centric Networking. In Proceedings of the 2016 8th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Larnaca, Cyprus, 21–23 November 2016; pp. 1–5. [Google Scholar]
- Borgia, E.; Bruno, R.; Conti, M.; Mascitti, D.; Passarella, A. Mobile edge clouds for Information-Centric IoT services. In Proceedings of the 2016 IEEE Symposium on Computers and Communication (ISCC), Messina, Italy, 27–30 June 2016; pp. 422–428. [Google Scholar]
- Amadeo, M.; Campolo, C.; Iera, A.; Molinaro, A. Information Centric Networking in IoT scenarios: The case of a smart home. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 648–653. [Google Scholar]
- Ahlgren, B.; Lindgren, A.; Wu, Y. Demo: Experimental Feasibility Study of CCN-lite on Contiki Motes for IoT Data Streams. In Proceedings of the ACM-ICN ‘16: Proceedings of the 3rd ACM Conference on Information-Centric Networking, Kyoto, Japan, 26–28 September 2016; pp. 221–222. [Google Scholar]
- Quevedo, J.; Corujo, D.; Aguiar, R. A case for ICN usage in IoT environments. In Proceedings of the 2014 IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; pp. 2770–2775. [Google Scholar]
- Hail, M.A.; Amadeo, M.; Molinaro, A.; Fischer, S. Caching in Named Data Networking for the wireless Internet of Things. In Proceedings of the 2015 International Conference on Recent Advances in Internet of Things (RIoT), Singapore, 7–9 April 2015; pp. 1–6. [Google Scholar]
- Ye, Y.; Qiao, Y.; Lee, B.; Murray, N. PIoT: Programmable IoT using Information Centric Networking. In Proceedings of the NOMS 2016—2016 IEEE/IFIP Network Operations and Management Symposium, Istanbul, Turkey, 25–29 April 2016; pp. 825–829. [Google Scholar]
- Chen, J.; Li, S.; Yu, H.; Zhang, Y.; Raychaudhuri, D.; Ravindran, R.; Gao, H.; Dong, L.; Wang, G.; Liu, H. Exploiting ICN for Realizing Service-Oriented Communication in IoT. IEEE Commun. Mag. 2016, 54, 24–30. [Google Scholar] [CrossRef]
- Dong, L.; Ravindran, R.; Wang, G. ICN based distributed IoT resource discovery and routing. In Proceedings of the 2016 23rd International Conference on Telecommunications (ICT), Thessaloniki, Greece, 16–18 May 2016; pp. 1–7. [Google Scholar]
- Hahm, O.; Adjih, C.; Baccelli, E.; Schmidt, T.C.; Wahlisch, M. Designing Time Slotted Channel Hopping and Information—Centric Networking for IoT. In Proceedings of the 2016 8th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Larnaca, Cyprus, 21–23 November 2016; pp. 1–5. [Google Scholar]
- Dong, L.; Wang, G. Support context-aware IoT content request in Information Centric networks. In Proceedings of the 2016 25th Wireless and Optical Communication Conference (WOCC), Chengdu, China, 21–23 May 2016; pp. 1–4. [Google Scholar]
- Hail, M.A.; Fischer, S. IoT for AAL: An Architecture via Information-Centric Networking. In Proceedings of the 2015 IEEE Globecom Workshops (GC Wkshps), San Diego, CA, USA, 6–10 December 2015; pp. 1–6. [Google Scholar]
- Hail, M.A.; Fischer, S. Flexible API for IoT services with Named Data Networking. In Proceedings of the 2016 IEEE International Conference on Emerging Technologies and Innovative Business Practices for the Transformation of Societies (EmergiTech), Balaclava, Mauritius, 3–6 August 2016; pp. 176–181. [Google Scholar]
- Amadeo, M.; Campolo, C.; Molinaro, A. Internet of Things via Named Data Networking: The support of push traffic. In Proceedings of the 2014 International Conference and Workshop on the Network of the Future (NOF), Paris, France, 3–5 December 2014; pp. 1–5. [Google Scholar]
- Sarkar, S.; Misra, S. Theoretical modelling of fog computing: A green computing paradigm to support IoT applications. IET Netw. 2016, 5, 23–29. [Google Scholar] [CrossRef]
- Yannuzzi, M.; Milito, R.; Serral-Gracià, R.; Montero, D.; Nemirovsky, M. Key ingredients in an IoT recipe: Fog Computing, Cloud computing, and more Fog Computing. In Proceedings of the 2014 IEEE 19th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Athens, Greece, 1–3 December 2014; pp. 325–329. [Google Scholar]
- Giang, N.K.; Blackstock, M.; Lea, R.; Leung, V.C.M. Developing IoT applications in the Fog: A Distributed Dataflow approach. In Proceedings of the 2015 5th International Conference on the Internet of Things (IOT), Seoul, Korea, 26–28 October 2015; pp. 155–162. [Google Scholar]
- Lee, K.; Kim, D.; Ha, D.; Rajput, U.; Oh, H. On security and privacy issues of fog computing supported Internet of Things environment. In Proceedings of the 2015 6th International Conference on the Network of the Future (NOF), Montreal, QC, Canada, 30 September–2 October 2015; pp. 1–3. [Google Scholar]
- Sarkar, S.; Chatterjee, S.; Misra, S. Assessment of the Suitability of Fog Computing in the Context of Internet of Things. IEEE Trans. Cloud Comput. 2015, PP. [Google Scholar] [CrossRef]
- Bibani, O.; Yangui, S.; Glitho, R.H.; Gaaloul, W.; Hadj-Alouane, N.B.; Morrow, M.J.; Polakos, P.A. A demo of a PaaS for IoT applications provisioning in hybrid cloud/fog environment. In Proceedings of the 2016 IEEE International Symposium on Local and Metropolitan Area Networks (LANMAN), Rome, Italy, 13–15 June 2016; pp. 1–2. [Google Scholar]
- Salman, O.; Elhajj, I.; Kayssi, A.; Chehab, A. Edge computing enabling the Internet of Things. In Proceedings of the 2015 IEEE 2nd World Forum on Internet of Things (WF-IoT), Milan, Italy, 14–16 December 2015; pp. 603–608. [Google Scholar]
- Aazam, M.; Huh, E.N. Fog Computing Micro Datacenter Based Dynamic Resource Estimation and Pricing Model for IoT. In Proceedings of the 2015 IEEE 29th International Conference on Advanced Information Networking and Applications, Gwangiu, Korea, 24–27 March 2015; pp. 687–694. [Google Scholar]
- Skarlat, O.; Schulte, S.; Borkowski, M.; Leitner, P. Resource Provisioning for IoT Services in the Fog. In Proceedings of the 2016 IEEE 9th International Conference on Service-Oriented Computing and Applications (SOCA), Macau, China, 4–6 November 2016; pp. 32–39. [Google Scholar]
- Aazam, M.; St-Hilaire, M.; Lung, C.H.; Lambadaris, I. MeFoRE: QoE based resource estimation at Fog to enhance QoS in IoT. In Proceedings of the 2016 23rd International Conference on Telecommunications (ICT), Thessaloniki, Greece, 16–18 May 2016; pp. 1–5. [Google Scholar]
- Aazam, M.; St-Hilaire, M.; Lung, C.H.; Lambadaris, I. PRE-Fog: IoT trace based probabilistic resource estimation at Fog. In Proceedings of the 2016 13th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2016; pp. 12–17. [Google Scholar]
- Abedin, S.F.; Alam, M.G.R.; Tran, N.H.; Hong, C.S. A Fog based system model for cooperative IoT node pairing using matching theory. In Proceedings of the 2015 17th Asia-Pacific Network Operations and Management Symposium (APNOMS), Busan, Korea, 19–21 August 2015; pp. 309–314. [Google Scholar]
- Aazam, M.; Huh, E.N. Fog Computing and Smart Gateway Based Communication for Cloud of Things. In Proceedings of the 2014 International Conference on Future Internet of Things and Cloud, Barcelona, Spain, 27–29 August 2014; pp. 464–470. [Google Scholar]
- Taneja, M.; Davy, A. Poster Abstract: Resource Aware Placement of Data Stream Analytics Operators on Fog Infrastructure for Internet of Things Applications. In Proceedings of the 2016 IEEE/ACM Symposium on Edge Computing (SEC), Washington, DC, USA, 27–28 October 2016; pp. 113–114. [Google Scholar]
- Jalali, F.; Vishwanath, A.; de Hoog, J.; Suits, F. Interconnecting Fog computing and microgrids for greening IoT. In Proceedings of the 2016 IEEE Innovative Smart Grid Technologies—Asia (ISGT-Asia), Melbourne, Australia, 28 November–1 December 2016; pp. 693–698. [Google Scholar]
- Rauniyar, A.; Engelstad, P.; Feng, B.; Thanh, D.V. Crowdsourcing-Based Disaster Management Using Fog Computing in Internet of Things Paradigm. In Proceedings of the 2016 IEEE 2nd International Conference on Collaboration and Internet Computing (CIC), Pittsburgh, PA, USA, 1–3 November 2016; pp. 490–494. [Google Scholar]
- Chiang, M.; Zhang, T. Fog and IoT: An Overview of Research Opportunities. IEEE Internet Things J. 2016, 3, 854–864. [Google Scholar] [CrossRef]
- Hu, P.; Ning, H.; Qiu, T.; Zhang, Y.; Luo, X. Fog Computing-Based Face Identification and Resolution Scheme in Internet of Things. IEEE Trans. Ind. Inf. 2017, 13, 1910–1920. [Google Scholar] [CrossRef]
- Dastjerdi, A.V.; Buyya, R. Fog Computing: Helping the Internet of Things Realize Its Potential. Computer 2016, 49, 112–116. [Google Scholar] [CrossRef]
- Prazeres, C.; Serrano, M. SOFT-IoT: Self-Organizing FOG of Things. In Proceedings of the 2016 30th International Conference on Advanced Information Networking and Applications Workshops (WAINA), Crans-Montana, Switzerland, 23–25 March 2016; pp. 803–808. [Google Scholar]
- Gia, T.N.; Jiang, M.; Rahmani, A.M.; Westerlund, T.; Liljeberg, P.; Tenhunen, H. Fog Computing in Healthcare Internet of Things: A Case Study on ECG Feature Extraction. In Proceedings of the 2015 IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, Liverpool, UK, 26–28 October 2015; pp. 356–363. [Google Scholar]
- Abdullahi, I.; Arif, S.; Hassan, S. Ubiquitous Shift with Information Centric Network Caching Using Fog Computing. Computational Intelligence in Information Systems; Springer: Cham, Switzerland, 2015; pp. 327–335. [Google Scholar]
- Khan, J.A.; Westphal, C.; Ghamri-Doudane, Y. A Content-based Centrality Metric for Collaborative Caching in Information-Centric Fogs. IFIP Networking-ICFC. arXiv, 2017; arXiv:1705.01343. [Google Scholar]
- Khan, J.A.; Westphal, C.; Ghamri-Doudane, Y. Offloading Content with Self-organizing Mobile Fogs. ITC 29. arXiv, 2017; arXiv:1707.06285. [Google Scholar]
- Stoica, I.; Morris, R.; Liben-Nowell, D.; Karger, D.R.; Kaashoek, M.F.; Dabek, F.; Balakrishnan, H. Chord: A scalable peer-to-peer lookup protocol for Internet applications. IEEE/ACM Trans. Netw. 2003, 11, 17–32. [Google Scholar] [CrossRef]
- Woungang, I.; Tseng, F.H.; Lin, Y.H.; Chou, L.D.; Chao, H.C.; Obaidat, M.S. MR-Chord: Improved Chord Lookup Performance in Structured Mobile P2P Networks. IEEE Syst. J. 2015, 9, 743–751. [Google Scholar] [CrossRef]
- Zave, P. Reasoning about Identifier Spaces: How to Make Chord Correct. IEEE Trans. Softw. Eng 2016, arXiv:1610.01140. [Google Scholar]
- Gupta, A.; Liskov, B.; Rodrigues, R. Efficient routing for peer-to-peer overlays. In Proceedings of the 1st conference on Symposium on Networked Systems Design and Implementation, San Francisco, CA, USA, 29–31 March 2004; pp. 113–126. [Google Scholar]

© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, F.; Ai, Z.-Y.; Li, J.-J.; Pau, G.; Collotta, M.; You, I.; Zhang, H.-K. Smart Collaborative Caching for Information-Centric IoT in Fog Computing. Sensors 2017, 17, 2512. https://doi.org/10.3390/s17112512
Song F, Ai Z-Y, Li J-J, Pau G, Collotta M, You I, Zhang H-K. Smart Collaborative Caching for Information-Centric IoT in Fog Computing. Sensors. 2017; 17(11):2512. https://doi.org/10.3390/s17112512
Chicago/Turabian StyleSong, Fei, Zheng-Yang Ai, Jun-Jie Li, Giovanni Pau, Mario Collotta, Ilsun You, and Hong-Ke Zhang. 2017. "Smart Collaborative Caching for Information-Centric IoT in Fog Computing" Sensors 17, no. 11: 2512. https://doi.org/10.3390/s17112512





