1. Introduction
Cyber-physical systems (CPSs) have emerged as a promising research paradigm [
1] which integrates computing, communication and control, that has become a new generation intelligent system. With the extensive development of network applications, CPS has been further integrated, which facilitates the seamless integration between networks and human society. In this context, people, machines, and information systems need to be urgently integrated [
2,
3,
4], which leads to the creation of cyber-physical-social systems [
5,
6]. On the other hand, with the extensive penetration and integration of personalized mobile devices (e.g., wearable devices, smartphones) in people’s daily lives, people have become the most sensitive social sensors. Therefore, sensing people’s social information has become a new paradigm of cyber physical social system-related applications, called cyber physical social sensing (CPSS) [
7,
8].
CPSS is designed to operate in conjunction with and in service of people. It leverages the sensed information collected by sensing nodes and aggregates it for recognizing people’s behaviors (e.g., mobility pattern), and in turn provides people with a higher level of combined information or services, which simplifies people’s lives. The rapid development of mobile devices with various sensors is the catalyst to promote CPSS to form a context-aware or social-aware mobile wireless sensor network. Many open issues have been studied, such as energy efficiency optimization [
9], security attacks [
10,
11], etc. Among them, the technology utilized to sense or track people’s behavior attracts more attention. CPSS allows people to collect and share information using cyber devices intuitively [
12]. In contrast to it, in this article, we explore how to track people’s behaviors without people actively participating in the activity, namely, passive tracking.
Comparisons between different people tracking technologies are summarized in
Table 1. Due to many attractive features, such as non-intrusive (third-party) and high positioning precision, camera networks are widely used for tracking people’s behaviors [
13,
14]. However, camera-based methods require line of sight (LOS), and cannot be deployed flexibly. Radio frequency identification (RFID) [
15] and IEEE 802.15.4/ZigBee sensor networks [
16] can also be utilized as tracking methods. The tracking systems based on them use electronic tags carried by people, and tag readers deployed in the area of interest. They can perform in non-line of sight (NLOS) manner and can be deployed flexibly. However, all these technologies are intrusive.
Given the popularity of mobile devices today, there has been a growing interest in tracking people’s behaviors through all kinds of sensors built into mobile devices [
17], such as global positioning system (GPS), Wireless Fidelity (Wi-Fi), and Bluetooth, etc. GPS has been used in people tracking [
17] in a participatory manner, however, it rarely works indoors. Bluetooth-based tracking methods [
18] are available indoors, and the tracking mechanism is similar to that of RFID or ZigBee, therefore, the method is also considered intrusive. In addition, cellular signals can be also used to track people’s behaviors [
19,
20], and the tracking is performed on the network side. However, there exist many limits in this method, such as intrusiveness, poor positioning precision, and inflexible deployment. Wi-Fi has been ubiquitously deployed, especially in public areas such as airports, shopping centers, etc. In addition, almost all of the mobile devices integrate Wi-Fi functionality. In this context, Wi-Fi-based sensing networks have become the world’s largest wireless sensor networks. Researchers have also utilized Wi-Fi to do participatory CPSS [
21]. However, in our work, we focus on passive CPSS using Wi-Fi.
Wi-Fi-enabled mobile devices, carried by people, discontinuously send out Wi-Fi messages, even when not connecting with any access point (AP). The presence of people can be identified by sensing these messages. Furthermore, each Wi-Fi-enabled mobile device is equipped with a wireless network adapter, which contains a universal unique device identifier, a media access control (MAC) address. Almost all of the Wi-Fi messages encapsulate the MAC address, with which different people can be distinguished [
22]. By placing a dedicated set of hardware devices called monitors dispersed in areas of interest to sense Wi-Fi messages, people’s behaviors can be tracked. One typical application is Wi-Fi-based indoor localization [
23], in which Wi-Fi received signal strength (RSS) is utilized by Wi-Fi monitors to identify the locations of people with Wi-Fi devices.
To show the feasibility of the Wi-Fi-based passive CPSS approach, we performed a case study that tracked people’s access behaviors in Wi-Fi networks. Analyzing people’s access behaviors has attracted significant attention recently [
24,
25,
26,
27,
28,
29,
30,
31,
32,
33,
34,
35]. This can be beneficial in many aspects, such as assessment of wireless network utilization, site planning, and design for intelligent and robust wireless network protocols. Therefore, there is a pressing need to characterize and understand people’s access behaviors, including access or exit time, session duration, and other access details, etc.
Previous studies have focused on mobility and association pattern analysis based on the traces collected from Wi-Fi networks through different methods. These methods can be mainly classified into four categories: wired monitoring, polling based on simple network-management protocol (SNMP), specialized applications on the Wi-Fi device, and AP syslog. Wired monitoring collects Wi-Fi traffic at the wired portion adjacent to APs. Schwab et al. [
24] presented a method to capture and analyze traffic patterns on a campus Wi-Fi network, based on the traces collected via wired monitoring. Wired monitoring can provide accurate and detailed traces. However, the monitor has to build physical connections with the networks, making this approach inconvenient to deploy. In addition, wired monitoring provides very limited visibility into MAC-level transmission dynamics. The approach we propose adopts passive monitoring, which means the monitors can be deployed flexibly without having to build any connection with the network. SNMP polling is another popular method. Based on the SNMP traces, user mobility patterns in a large corporate Wi-Fi networks were explored in [
27]. The study in [
30] examined the utilization of Wi-Fi hotspot networks based on the SNMP traces. However, SNMP polls data typically at intervals of minutes. Therefore, some instantaneous transmission dynamics might be lost. Wi-Fi devices with specialized applications can also participate in the trace collection [
32]. However, this method suffers from some limitations. First, the assumption that people are willing to install these applications is not always true. Second, these applications may involve modifying drivers, which is complex and costly. Furthermore, the applications run in the Wi-Fi device may need sufficient storage capacity, and incur high energy consumption. Researchers have also used AP syslog [
33,
35] to characterize and analyze access patterns. However, it is insufficient to expose the MAC-level transmission dynamics of Wi-Fi networks, such as the retransmission and some other details of transmission events.
Some works utilized these methods simultaneously. Researchers in [
25] analyzed user behavior and network performance in a public-area wireless network based on traces from SNMP and wired monitoring. In [
26] researchers analyzed the usage of a mature campus Wi-Fi network based on traces from syslog, SNMP polling, and tcpdump sniffers. Furthermore, some researchers [
28,
29,
31] have modeled user mobility and association patterns in university campus Wi-Fi networks, based on the traces from SNMP and AP syslog. However, none of them can sense the transmissions from Wi-Fi devices which do not build connection with any AP.
In this article, we develop a passive CPSS system operating in a non-intrusive, flexible, and simplified manner to tracking people’s access behaviors in Wi-Fi networks. Through this system we ease the way to collect detailed access traces with low cost and high flexibility such that brings us closer to understanding people’s access patterns and behaviors in Wi-Fi networks. The contributions are summarized as follows:
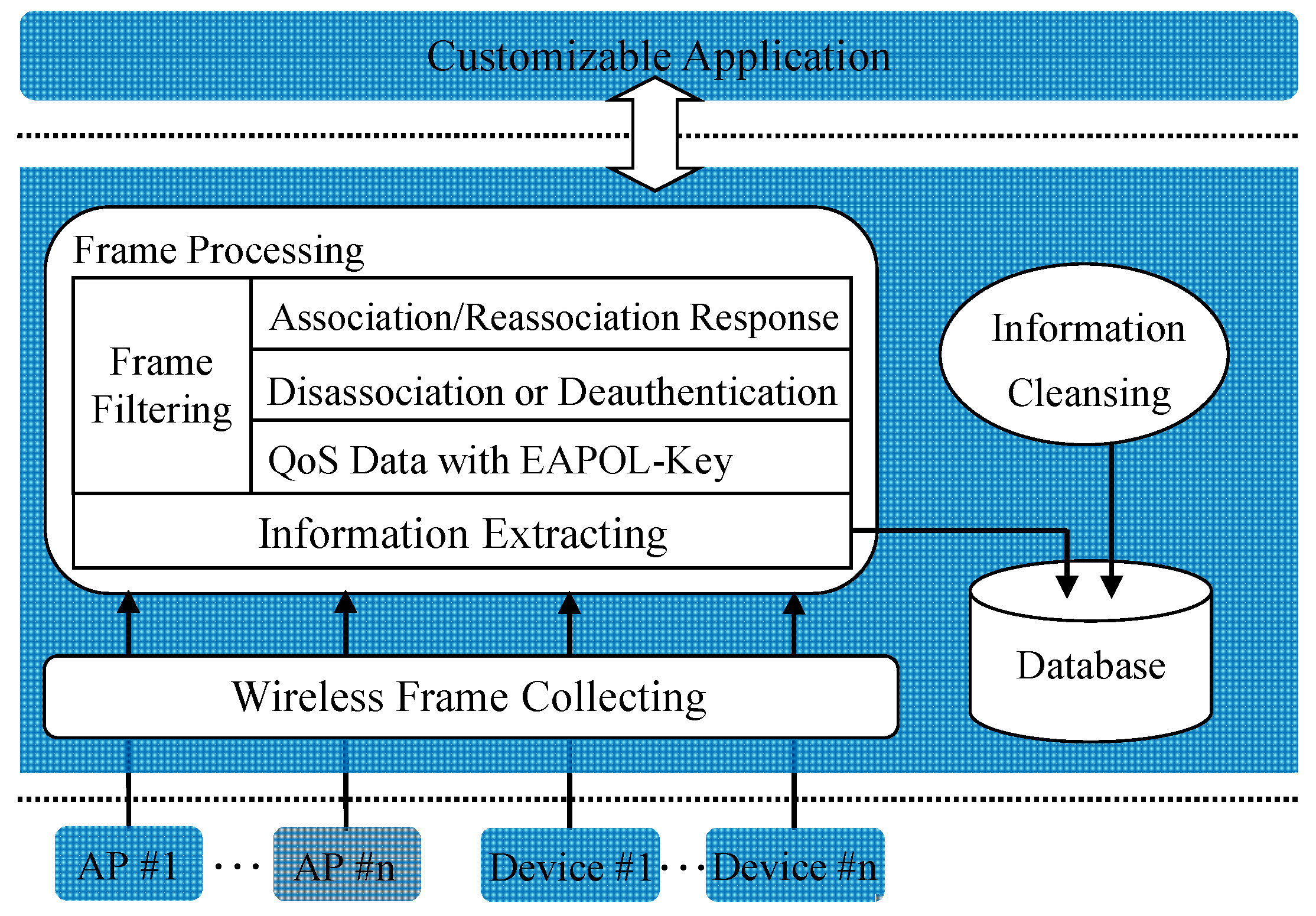
We propose a Wi-Fi based passive CPSS approach for tracking people’s behaviors. The approach works in a non-intrusive, flexible, and simplified manner, and has the ability to provide deep visibility into MAC-level transmission dynamics between Wi-Fi devices and APs. Specifically, it tracks people’s behaviors by sensing Wi-Fi messages from mobile devices people carry with. By extracting the information from these Wi-Fi messages, more data can be obtained.
Based on the approach, we design a non-intrusive CPSS system. The system works as a third-party monitor, and can be deployed conveniently and cost-effectively. To show the feasibility, we use the system to track people’s access behaviors in Wi-Fi networks. We design the system architecture, and propose a two-sized sliding window algorithm, with which the unreliable information, caused by the loss and retransmission of the 802.11 frame, can be eliminated from the tracked traces. In addition, we design a policy to judge the validness of an access operation.
We implement the system on the off-the-shelf PC, without changing the hardware or firmware. We also evaluate the system in real Wi-Fi networks. The results show that the system can track people’s access behaviors accurately.
The rest of this article is organized as follows:
Section 2 introduces the system description and some definitions. The architecture and implementation details of the proposed system are given in
Section 3. In
Section 4, the prototype of the system and the experimental results are presented. Finally, we present our conclusions and outlook in
Section 5.
2. System Description
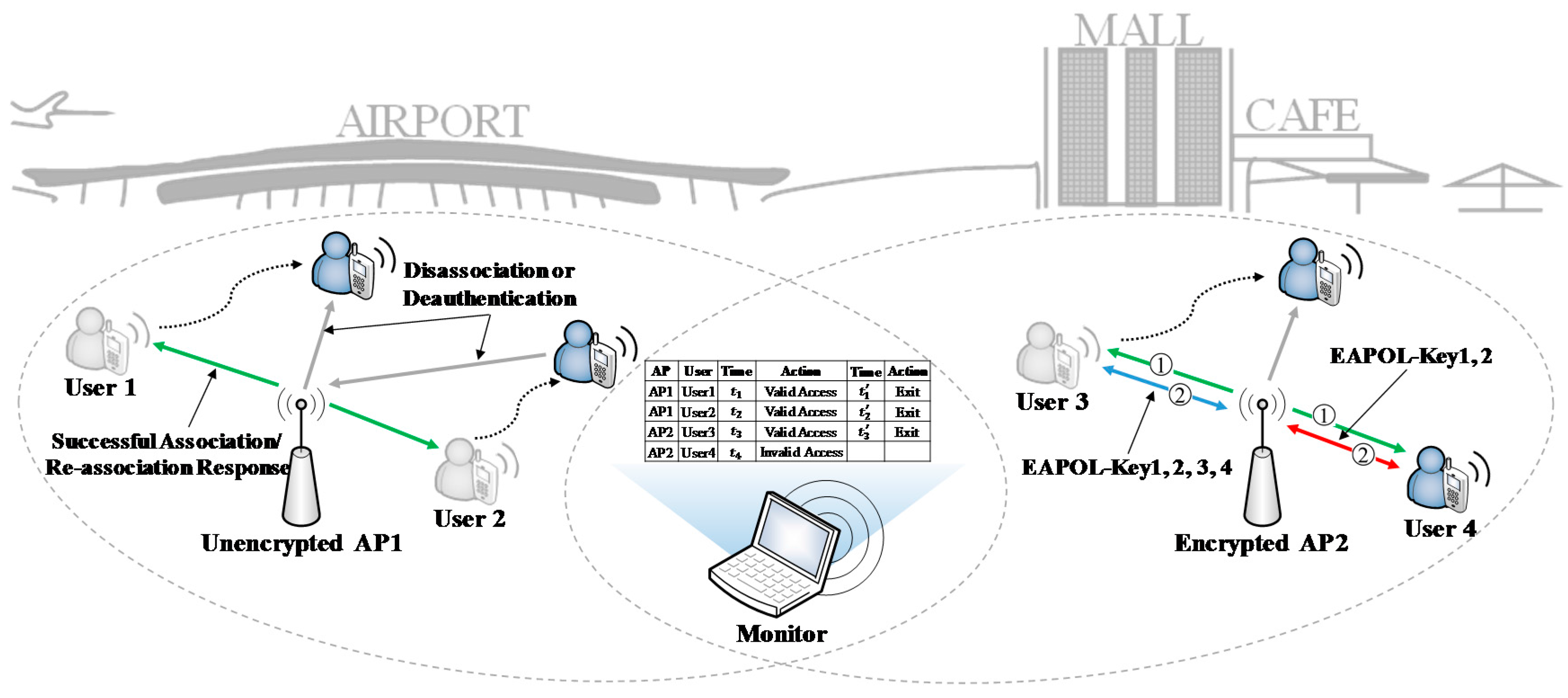
The target Wi-Fi networks we consider in this article are unencrypted or encrypted by Wi-Fi protected access or Wi-Fi protected access 2 in pre-shared key mode (WPA/WPA2-PSK), which are ubiquitously being deployed in airports, shopping malls, and cafes, etc. As shown in
Figure 1, the system we designed works as a third-party monitor. It tracks the access behaviors of nearby Wi-Fi users, and extracts the access information, including access time, exit time, and some other details. The extracted information will be elaborated in detail subsequently, as illustrated in
Section 3.3.
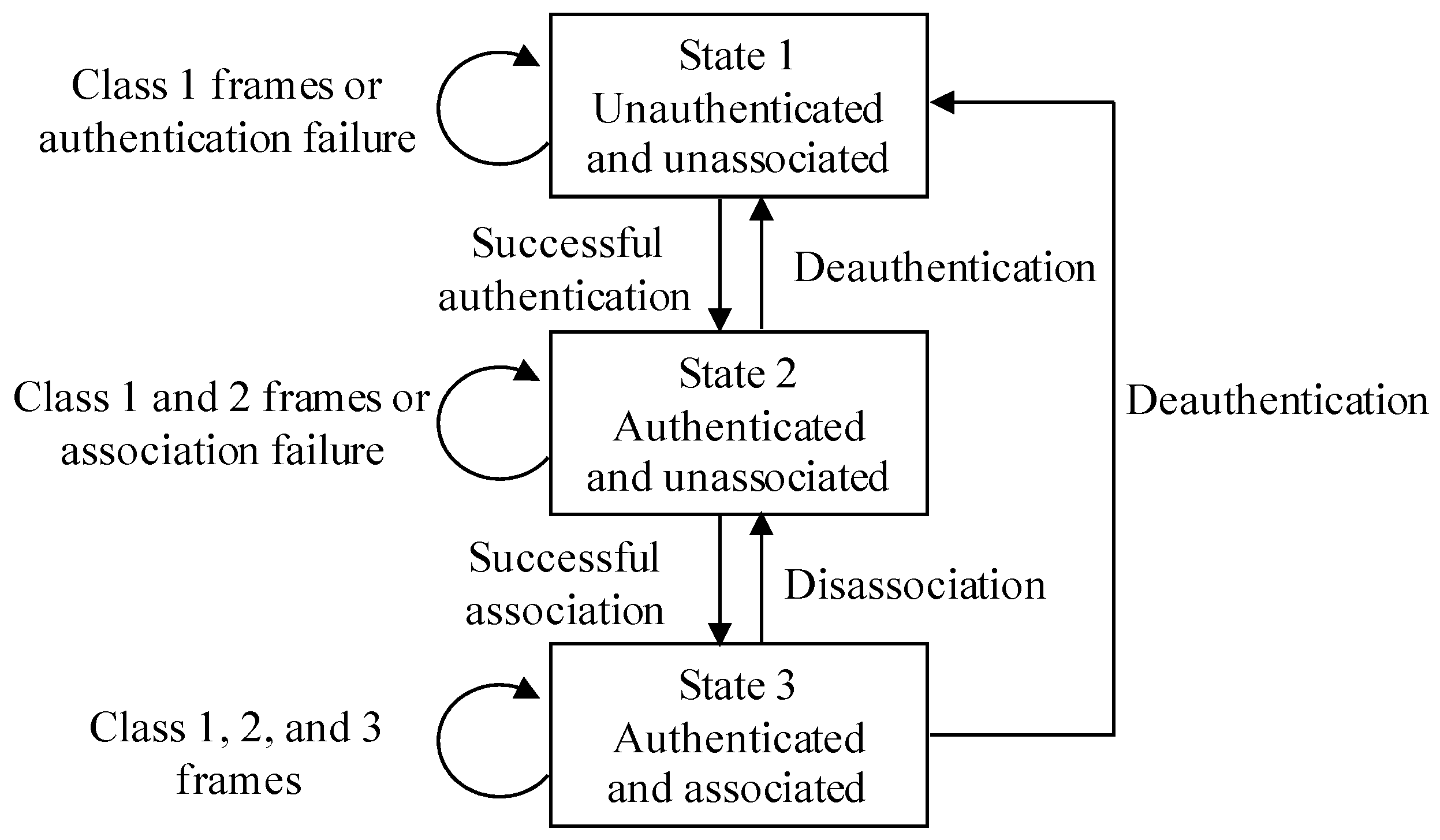
For the convenience of description, we give the common 802.11 state diagram first, as shown in
Figure 2. A Wi-Fi device usually works in three states, and each state is a successively higher point in the development of an IEEE 802.11 connection. Frames are also divided into different classes. The Wi-Fi device starts in state 1, and data can be transmitted through a distribution system only in state 3. The Wi-Fi device changes the state by exchanging different frames with the AP. When a device tries to access an AP, it exchanges the Authentication frame with the AP first, and then sends the Association/Re-association Request frame to the AP, the AP replies with the Association/Re-association Response frame. The Disassociation or De-authentication frame can be used to abort the connection.
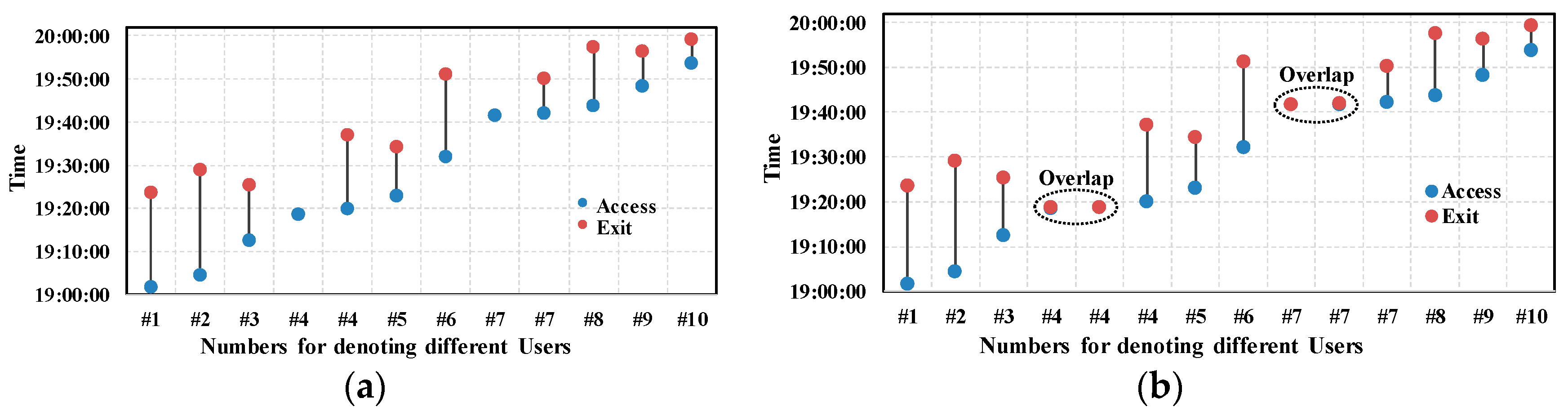
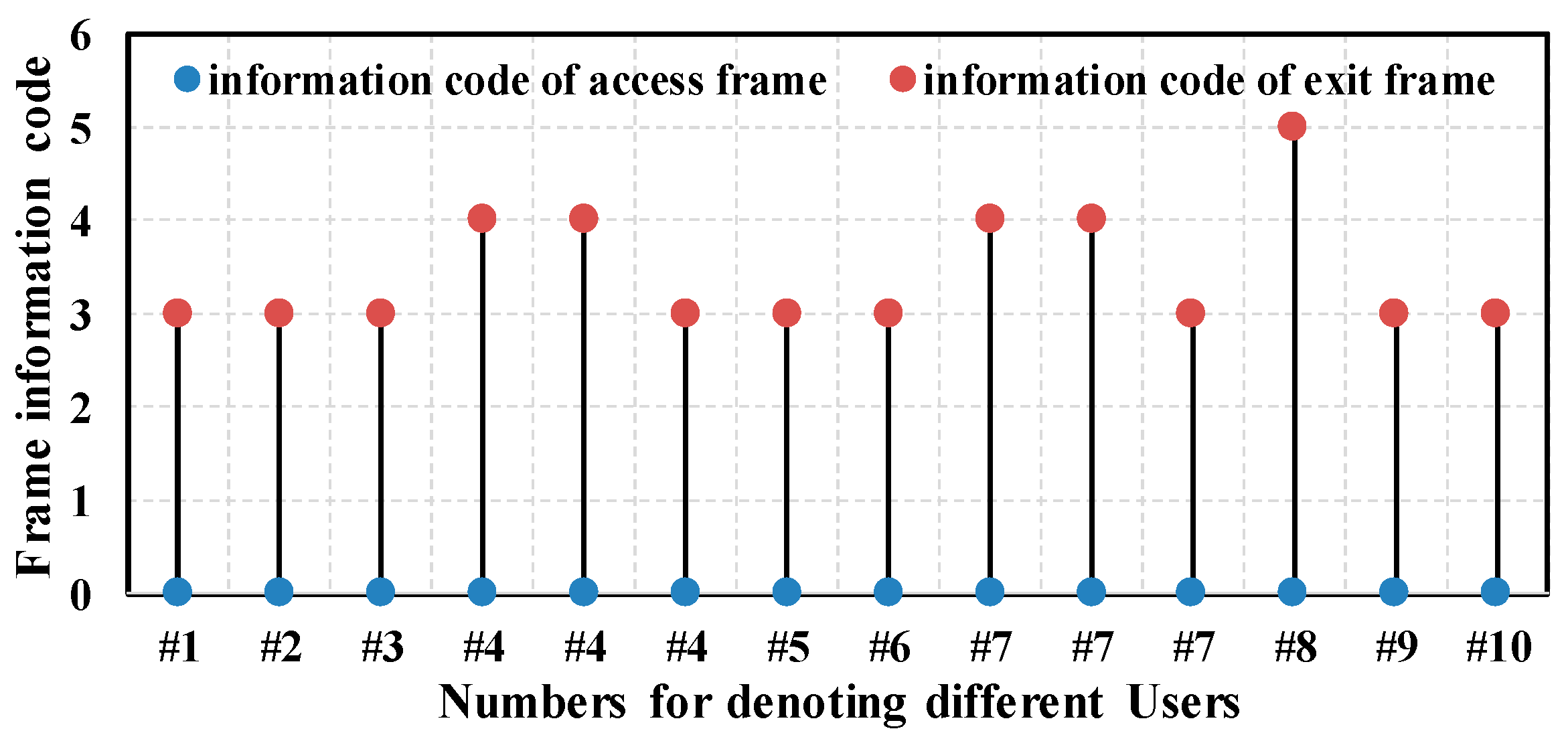
We make some definitions about people’s access and exit operations from an AP, as illustrated subsequently. For the sake of simplicity, we define Association/Re-association Response frame and Disassociation/De-authentication frame as the access frame and exit frame, respectively. We define the access frame and the exit frame reception time on the monitor side as the approximation of the actual occurrence time of the access and exit event on the Wi-Fi device side. Therefore, there is a delay between them. The delay changes under different wireless environment. For example, the delay may get longer if the wireless networks congest, or vice versa.
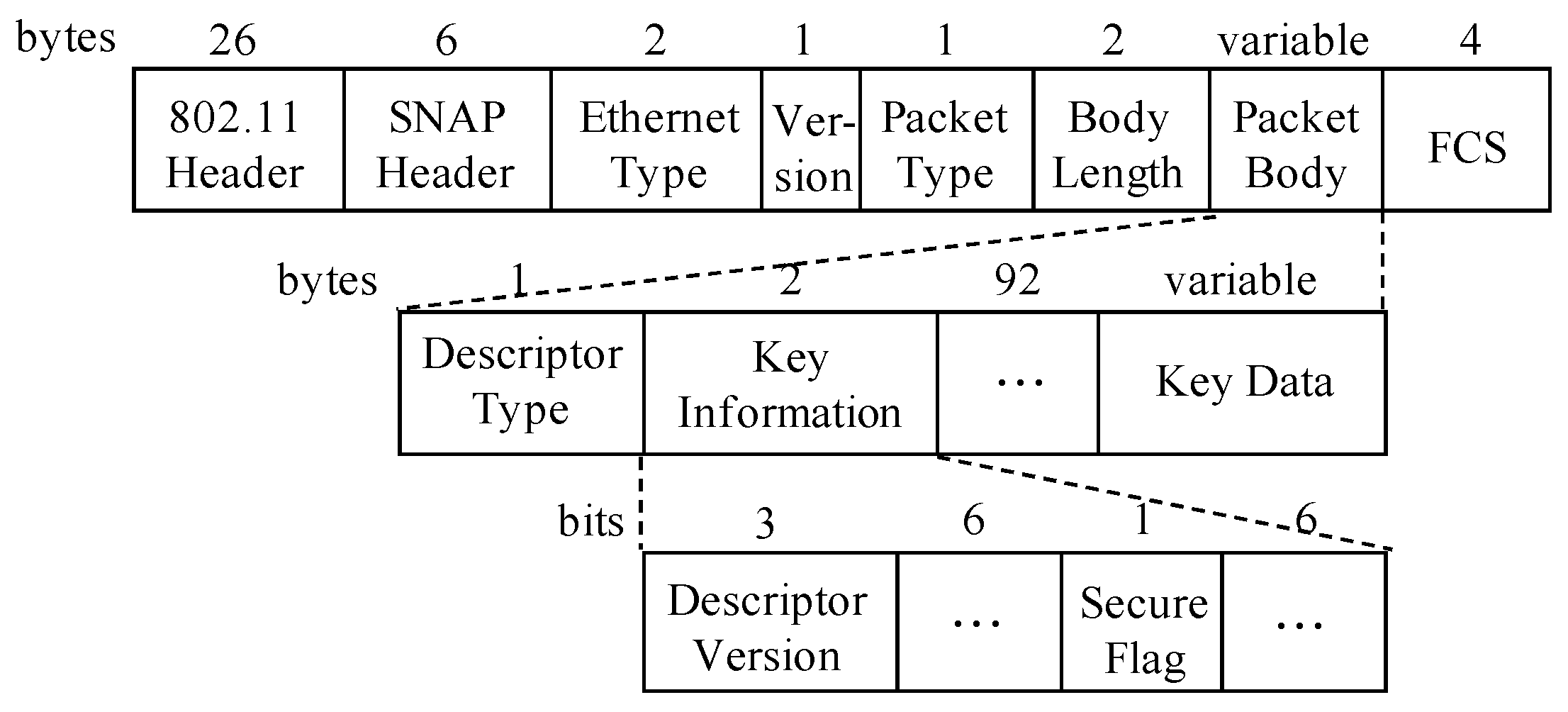
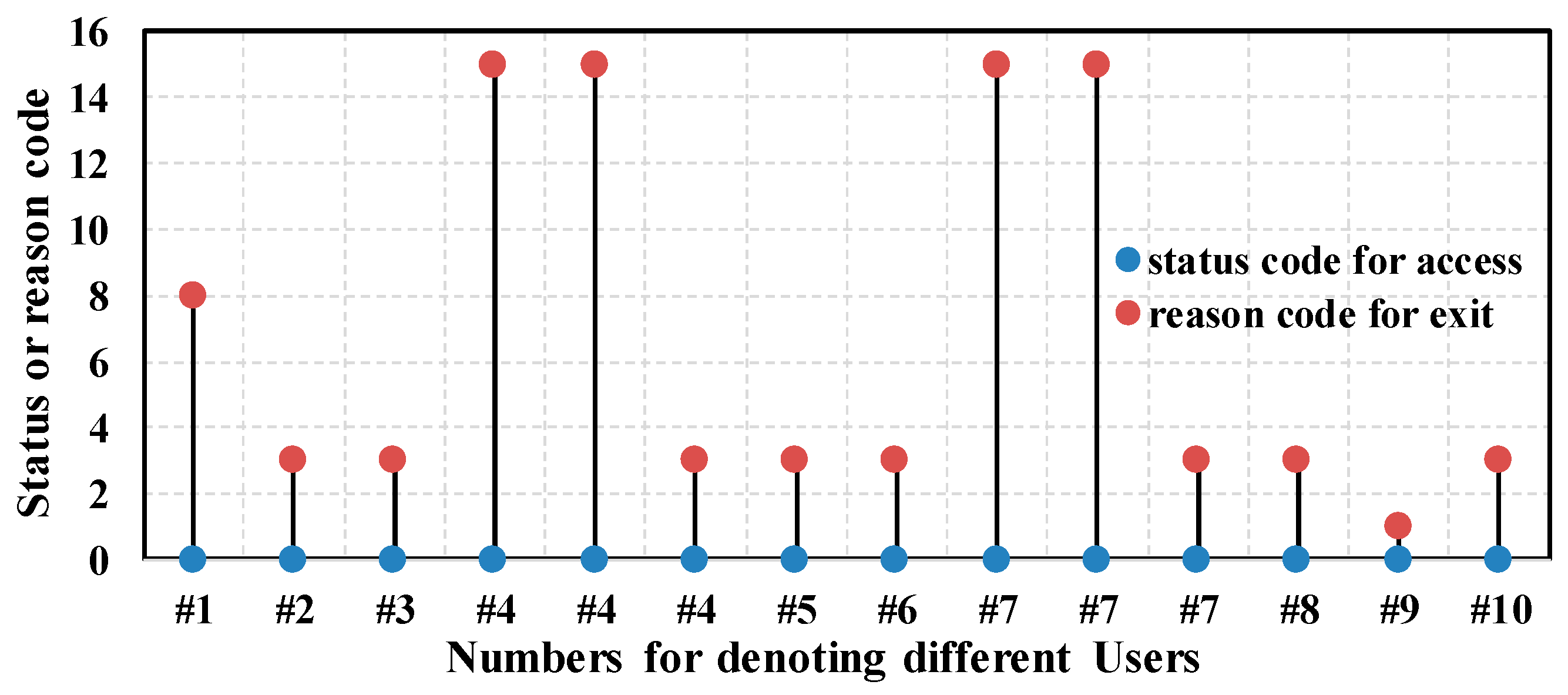
Figure 3a shows the procedures of accessing an encrypted AP. The Wi-Fi device scans the AP first. After finding the AP, the device tries to build a connection with the AP, and it starts with authentication with the AP. Open system authentication can always succeed. Then, the device sends association/re-association request to the AP, and the AP replies with the access frame. Whether an association operation succeeds or not is denoted by the Status Code field in the header of the access frame. The Status Code field is set to 0 when an association/re-association operation succeeds and nonzero on failure. If the association/re-association succeeds, there is a process of 4-way handshake between the AP and the device, which is used for key exchange. The device can exchange data with the AP only if 4-way handshake succeeds.
Figure 3b illustrates the process of 4-way handshake. The AP distributes keys to the Wi-Fi device using extensible authentication protocol over LAN-key (EAPOL-Key) messages encapsulated in quality of service (QoS) Data frames. If 4-way handshake fails, there are several execution loops including steps 1 and 2 in
Figure 3b, without step 3 and 4. Then the device or the AP sends the exit frame to the other side to abort the connection. Note that the access procedures for a Wi-Fi device in unencrypted Wi-Fi networks only include access point scanning, open system authentication, and association/re-association process in
Figure 3a.
However, the access operation for a Wi-Fi device is not always valid. When a device tries to access an encrypted AP, if the 4-way handshake fails, the device still cannot exchange data with the AP, although the association/re-association succeeds. Therefore, the access operation for the device is invalid. If a Wi-Fi device associates with an unencrypted AP successfully, the access operation is valid. If a Wi-Fi device associates with an encrypted AP successfully, and the 4-way handshake succeeds, then the access operation for the device is valid. However, if the 4-way handshake fails, though the association succeeds, the access operation for the device is invalid.