1. Introduction
Wearable wireless sensor networks are a convenient solution to communicate measurement results from person to person, or from a person to a base station. The data often include sensitive information such as coordinates or medical data, requiring secure transmission. With the current evolution of the Internet of Things (IoT) and the Internet of People (IoP), secure wearable wireless sensor networks are gaining even more importance [
1].
Given the limitations imposed by the hardware of typical wireless sensor nodes, there is a need for encryption protocols that are energy efficient and require limited memory and processing power. Most conventional encryption schemes do not meet these demands, and also require considerable packet overhead in the form of header extensions. Therefore, current research focuses on lightweight block ciphers, which are, however, vulnerable to security issues as well as denial-of-service attacks [
2]. Research into a potentially more secure scheme was recently presented in [
3].
The wireless sensor nodes in this paper employ communication according to the IEEE
standard, of which the MAC (Media Access Control) layer includes AES128 (Advanced Encryption Standard) with seven security levels, of which the highest level combines 128 bits AES encryption and 128 bits MIC (Message Integrity Code). However, key management and generation algorithms are not included and should be provided by the upper network layer. It is exactly the key distribution that is challenging and current techniques are often based on the predistribution of secret material, causing large memory overhead. A more memory efficient scheme is proposed and analyzed in [
4], but not practically implemented. Encryption employing AES-CCM-128 (Standard-Counter with Cipher Block Chaining-Message Authentication Code) requires less packet overhead but needs dedicated hardware support to be energy-efficient [
5]. However, another very interesting approach for symmetric key generation is possible, without exchanging information over the wireless channel, if a common private source of information can be used for key generation. Such an approach has the potential to make symmetric key generation more secure compared to the protocols mentioned above.
The idea of having a common and unique source of information for key generation has also been studied for body area sensor networks before [
6], where biometric signals captured by different nodes on the same person are used as a source of common information.
The source of common information for body-worn wireless sensor nodes originates from the properties of the radio propagation channel. Wearable sensor networks are typically deployed in environments where the communication channel varies significantly due to fading and shadowing [
7]. In the case of off-body communication, changing antenna orientation and additional shadowing by the human body also play an important role. Recent work documented in literature suggests that the varying channel can be employed to generate secure keys via a novel approach [
8,
9].
Legitimately communicating users share a unique physical propagation channel of which the characteristics can be measured at both sides of the link. The channel measurements are highly correlated for the legitimate users and the mutual information between both sets of data allows to extract similar keys by both users. Some key errors might occur, but reconciliation techniques are further applied to successfully adjust the keys.
An eavesdropper, however, does not share the same physical channel, and eavesdropper measurements will typically be decorrelated from the legitimate users’ data. Mutual information between the data series will also be very limited [
10], rendering key estimation by the eavesdropper cumbersome. Measurements using a network analyzer confirmed the usefulness of channel-based key-generation before, as documented in [
8,
9]. The influence of the radio-wave propagation channel onto key security has recently been further analyzed and documented in [
11].
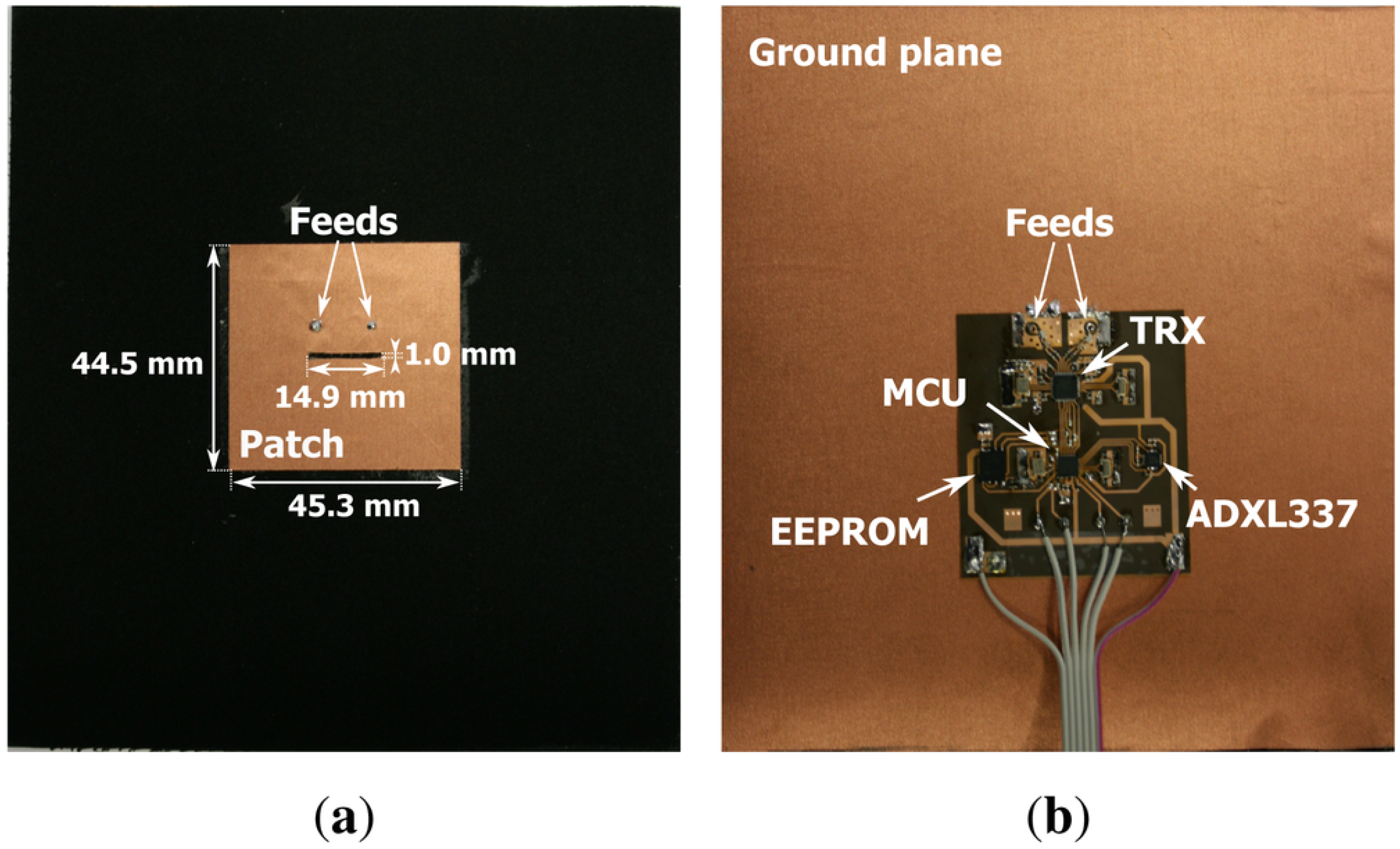
This paper discusses practical research on the performance of a wearable channel-based key-generating system, employing realistic body worn sensor nodes, of which the hardware and network performance were documented earlier [
12]. The embedded software in the nodes has been modified to exchange packets between legitimate parties within a very narrow time slot, allowing the accurate estimation of the channel at both ends of the link. The raw Key Error Rate (KER) is determined and a threshold is employed to reduce the KER below a level for which further reconciliation yields error free keys.
The proposed and tested key generation algorithm is very suitable for body-centric sensor networks and allows secure key generation without additional hardware. Encryption by means of the generated key can be performed employing a number of algorithms suitable for execution on a low-power micro controller [
13]. Keys generated following this approach can be constantly updated and hence should be virtually impossible to break, provided that careful hardware construction of the sensor node makes side-channel attacks (by measuring other electrical parameters such as power supply current) impossible [
14]. Emissions by the processor should be minimized, as advanced side-channel attacks are possible with very low cost Software Defined Radios (SDR) [
15]. In our design, the very small footprint low-power micro controller is shielded by the wearable antenna’s ground plane as well as by the human body.
Wearable sensor nodes benefit from the natural movement of the body to create sufficient channel variation for low-bitrate key generation, without the need for re-configurable antennas [
16] or multi-antenna configurations [
17]. However, the key-generation rate can be increased using multiple on-body antennas, as the human body provides a large platform to deploy multiple antennas with limited mutual coupling [
18].
To the author’s knowledge, this is the first fully functional implementation of this type of key generation on wearable autonomous wireless sensor nodes. Initial work was documented in [
10,
19], but now, full key generation is performed for indoor as well as outdoor scenarios, and the results are documented, compared and analyzed more in depth.
3. Results
3.1. Correlation for Legitimate Parties versus Eavesdropper
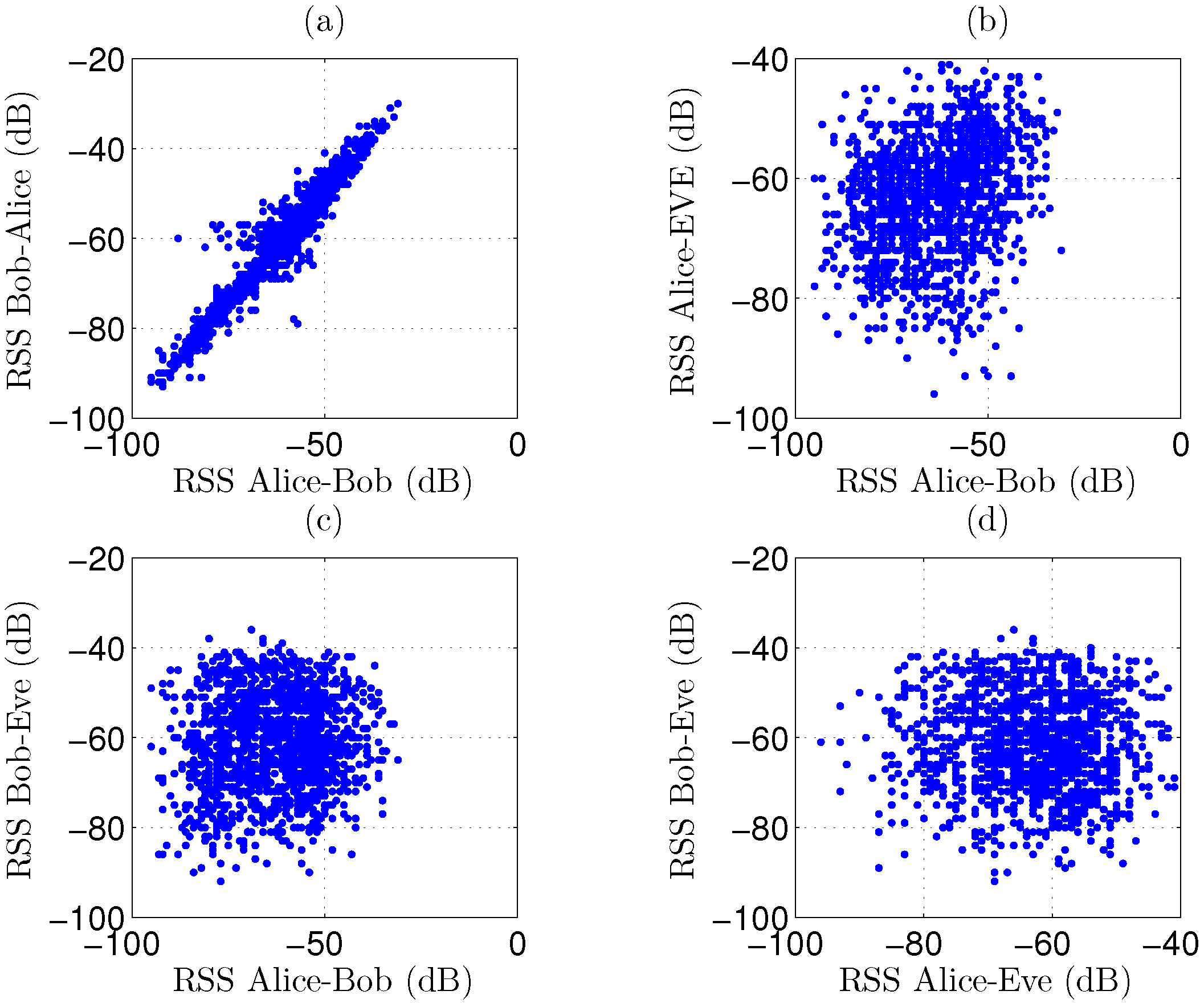
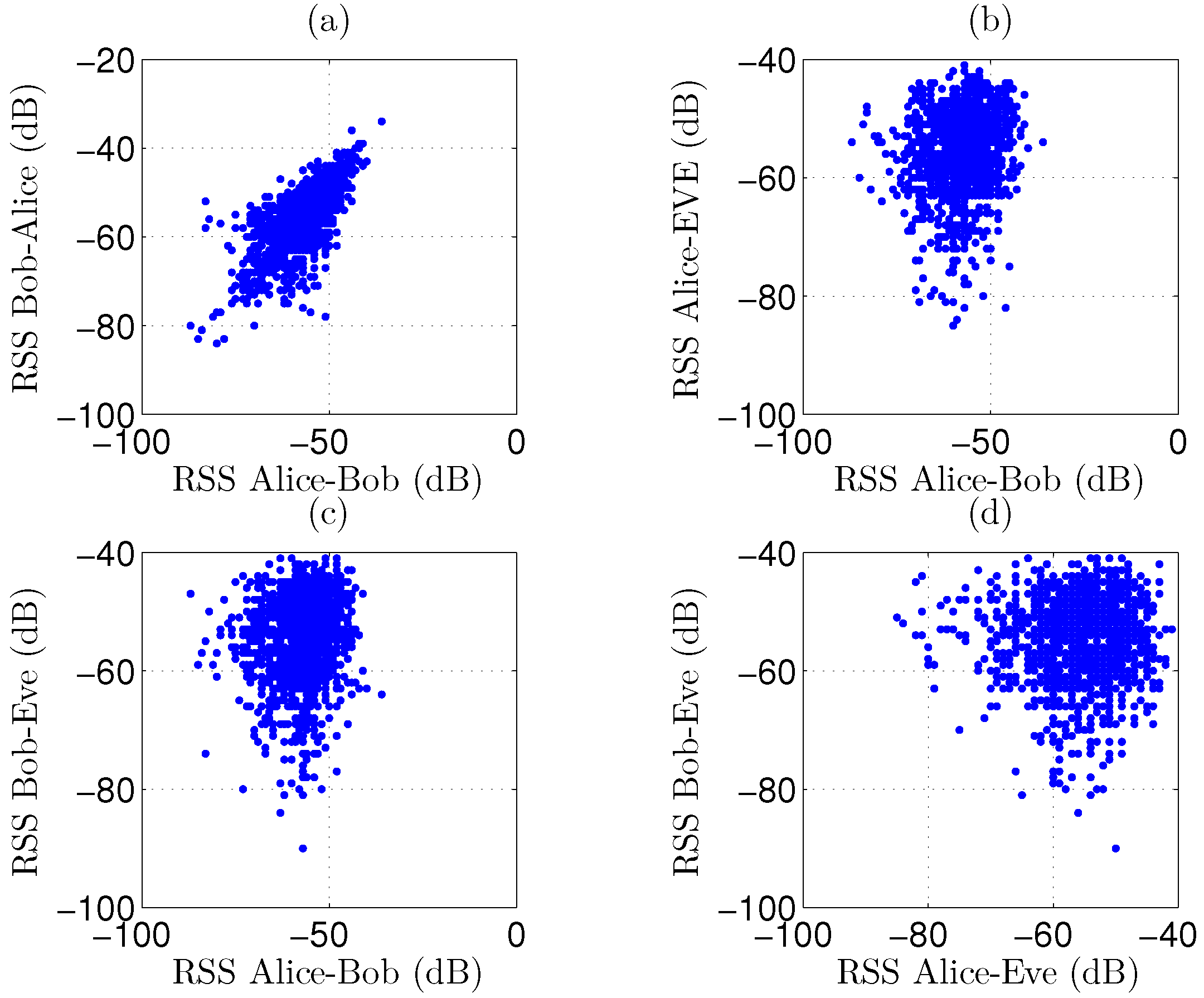
As a first observation, 1500 RSS channel samples for Scenario 1 are displayed in
Figure 5, for the reciprocal link between the legitimate parties as well as for the link from Alice to Bob. These results are compared to the signal levels captured by Eve. A very strong correlation is observed in
Figure 5a for reciprocal channel measurements between the legitimate parties, as the measurement pairs are clustered, resembling a rising straight line with a positive slope. In plots
Figure 5b,c, a very low correlation is present between the legitimate link and the signal levels intercepted by the eavesdropper, resulting in a more circular cloud. Scatter plot
Figure 5d shows the correlation between Alice’s and Bob’s signals, as captured by the eavesdropper. From these graphs, we can conclude that distilling useful data from channel measurements is difficult for the eavesdropper. Results are very similar for scenarios 2 to 6. In the worst-case scenario 7, correlation for the legitimate parties is less strong due to NLoS propagation between them, as clearly visible in
Figure 6. Although the correlation is still very low for the eavesdropper, scenario 7 appears more difficult for key generation.
3.2. Legitimate Key Generation
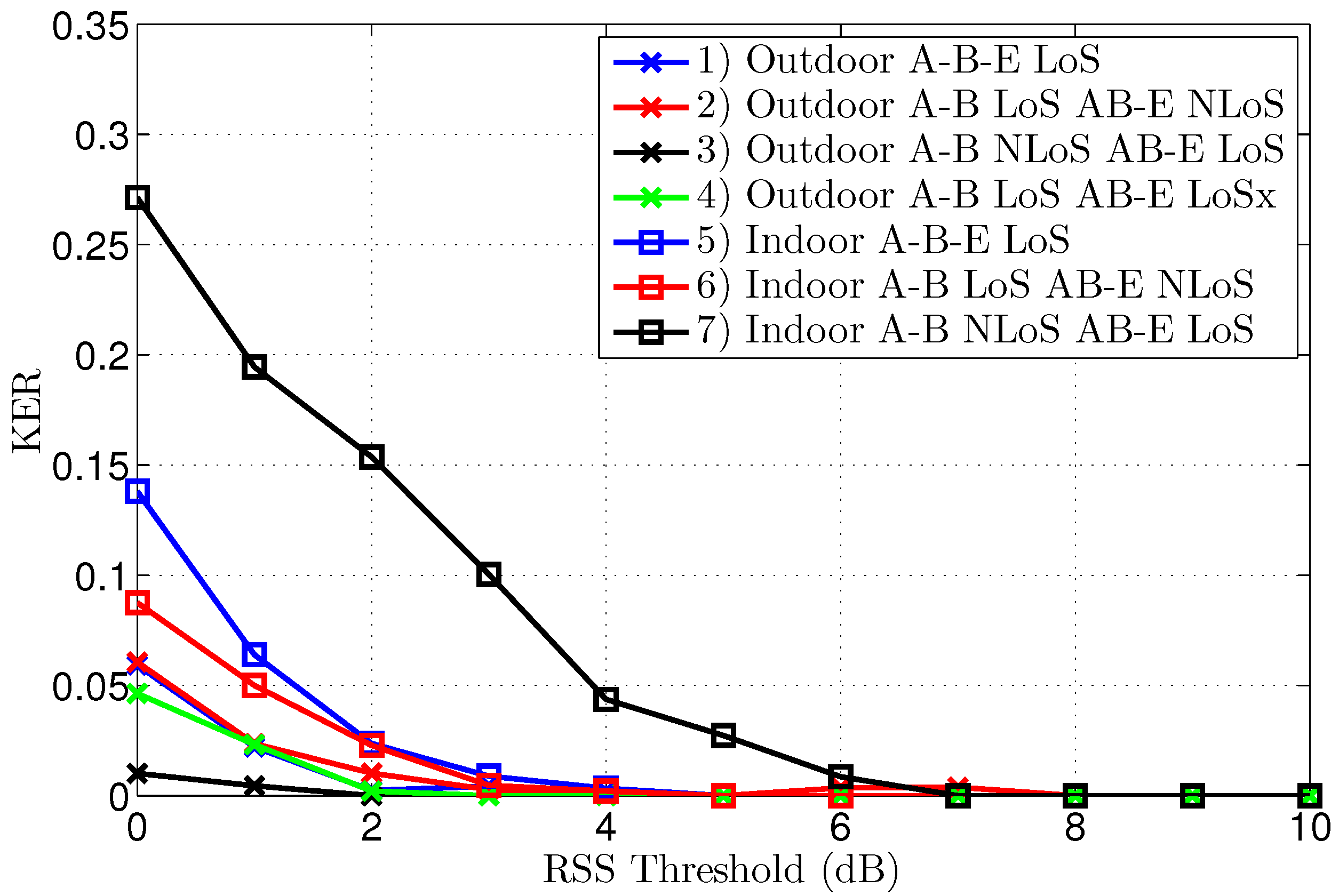
The KERs (Key Error Rates) and the corresponding key lengths after reconciliation are displayed in
Figure 7 and
Figure 8, respectively. To clearly explain the results, both graphs will be discussed at the same time. A further analysis of the interpretation of these results follows in the discussion section.
The first important observation is that the KER converges to zero for all scenarios, provided a significantly large threshold is employed, clearly illustrating effective key generation in all tested conditions. Without threshold, or with thresholds of only 1 or 2 dB, the KER is systematically lower for the outdoor scenarios. The point of zero bit errors is achieved at a threshold of only 2 dB for scenario 3, resulting in an error-free key length of 1364 bits, based on 1500 channel samples. For all other scenarios, except scenario 7, a threshold of 5 dB is necessary to obtain a KER of zero, making the performance for indoor and outdoor scenarios comparable. For the worst-case scenario 7, manifesting also the highest initial KER, a zero KER is obtained only at a threshold level of 7 dB.
Note that a further increase of the threshold beyond the first zero KER point can coindicentally result in some key errors again, which is the case for scenario 2, but for a higher threshold, the KER finally converges to zero.
The key length in
Figure 8 decreases for higher thresholds, as larger parts of the channel measurements are eliminated from the data set. For equal thresholds and similar propagation conditions in terms of LoS or NLoS, the key generation rate is systematically higher for the outdoor scenarios. The smallest key length of 275 bits results for scenario 7 at a threshold of 7 dB. At the same threshold level, the key length is still 869 bits for scenario 1. As 1500 channel measurements were collected for both scenarios, at a rate of one measurement per second, the key generating rate is
bits/s for scenario 1, compared to
bits/s for scenario 7 at the same 7 dB threshold. However, for scenarios 1–6, the first point of zero KER already occurs at a threshold level of 5 dB, corresponding to a key length up to 1023 bits or up to a key generation rate of
bits/s.
To obtain the highest possible key generating rate, the lowest possible threshold should be used. Detecting the point of error-free keys can be easily performed by exchanging a CRC (Cyclic Redundancy Check) sum on the key bits between the legitimate parties.
Note in the graph that, for scenarios 2 and 4, the key length without threshold is a bit shorter than 1500 bits, due to packet loss over the difficult link to Eve, which is either NLoS or larger distance LoS. In the analysis, only packets received successfully by all three nodes are considered.
3.3. Attempted Eavesdropper Key Generation
It is equally important to study the behavior for key generation attempted by Eve, assuming the worst-case situation that Eve captures signals from both Alice and Bob, knows all details about the system and is also able to intercept the check bits.
Eve tries to estimate the master key based on recorded signal levels. Four cases are possible for the measurement discussed here:
Alice has the master key, Eve uses Alice’s signal strength
Alice has the master key, Eve uses Bob’s signal strength
Bob has the master key, Eve uses Alice’s signal strength
Bob has the master key, Eve uses Bob’s signal strength
All cases have been studied in detail, but we document only graphs for the worst of these four cases, where key extraction by Eve reveals the most information about the key. This corresponds to case number 1 in the list.
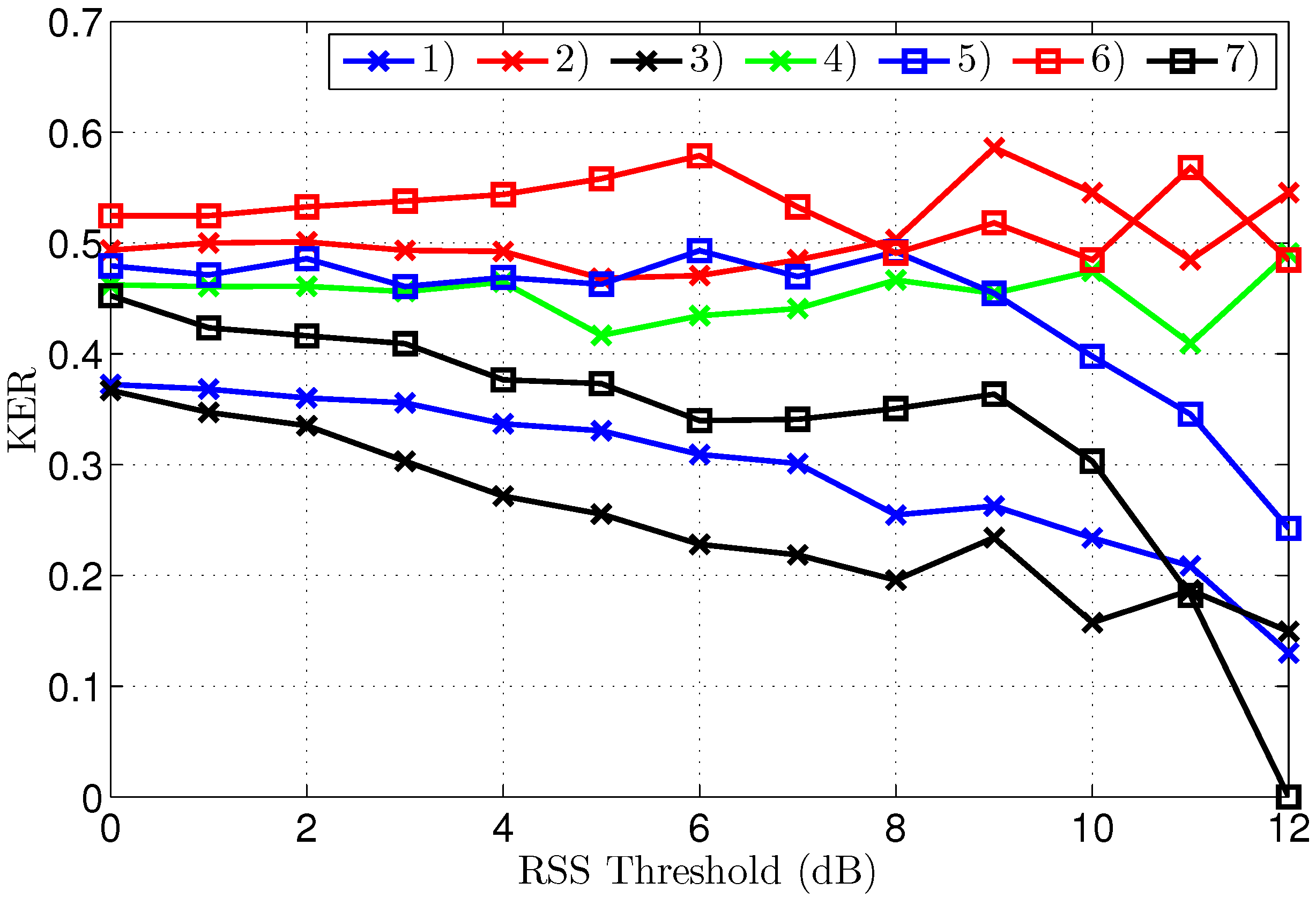
Figure 9 displays the KER after reconciliation by Eve for different thresholds. Clearly the KER does not converge to zero as easily as for the legitimate parties. The KER for scenarios 2, 4 and 6 does not approach zero at all. The KER is finally decreased for higher thresholds in the other scenarios, but stays too high to be of practical use, except for the worst-case scenario 7.
It is important to note that convergence to a zero KER at a threshold of 12 dB for scenario 7 does not mean that Eve can intercept the key used by Alice and Bob. The legitimate parties normally choose to operate at a threshold level of 7 dB for this scenario, as this is the lowest threshold resulting in a zero KER for them. At this threshold level, the KER for Eve is still , which is very high, considering that a KER of corresponds to no information at all.
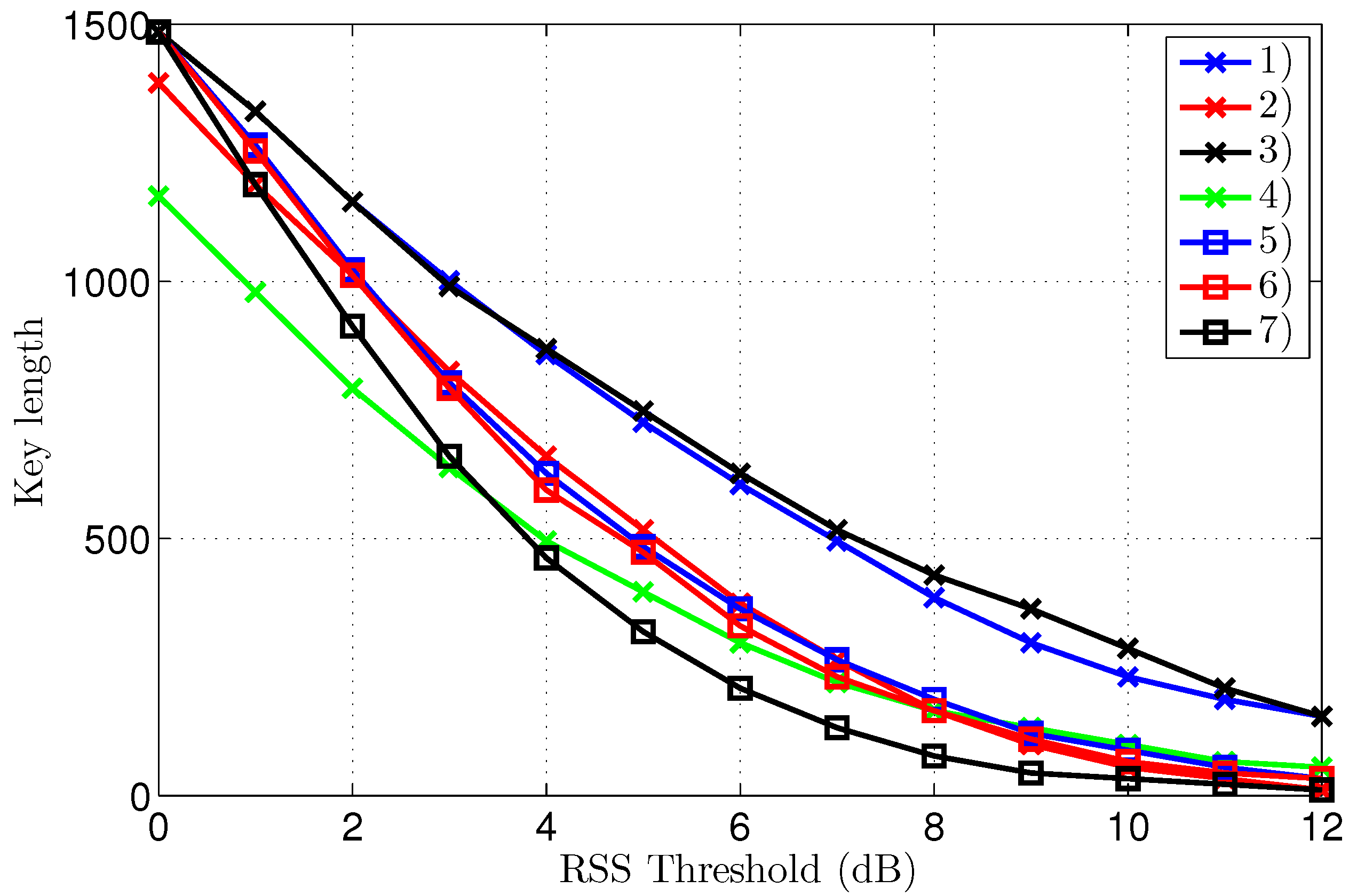
Further reasons why convergence to lower KER values for Eve is not of practical use follows from the key length shown in
Figure 10. For higher threshold levels, the key length quickly becomes impractically short, implying that, even in the single scenario where Eve can construct an error-free key, that key is much shorter than the key used by Alice and Bob, which is constructed at the lower threshold level of 7 dB instead of 12 dB. Actually for our measurement in scenario 7, Eve’s error free key is only 11 bits long, corresponding to a single Hamming code word. Note that, in the same scenario, Alice and Bob use a 275-bit key. Constructing keys at a different threshold level than the one used by Alice and Bob is actually pointless, as these keys do not match in both length and content.
4. Discussion
4.1. Key Generation Performance
Error-free key generation is possible in all tested scenarios. However, due to differences in the statistics of the signal levels, the performance differs for the different scenarios. To obtain error-free keys after reconciliation, a threshold of 5 dB is sufficient for six out of seven scenarios. A comparison of the key generating rate at this threshold level is therefore most relevant. Note that the threshold value yielding error-free keys is determined automatically by exchanging a CRC calculated for the key which is generated after reconciliation. A valid CRC indicates matching keys at both sides of the link, allowing both parties to select an equal threshold level, which is as low as possible to obtain error-free keys.
Observed key lengths extracted from the measurements are clearly the largest for the outdoor scenarios, despite the presence of some packet loss in two outdoor scenarios. Outdoor keys have a smaller variance, with a length between 836 and 1001 bits. For the indoor scenarios, the key length varies between 429 and 792 bits. The reason for this performance difference can be found in the physical channel behavior, which is different for indoor and outdoor areas. Three main sources of differing reciprocal channel measurements are identified:
Limited resolution of the RSS detector
Hardware imbalances of the TRX and the antennas
Channel small-scale fading characteristics
The first two sources of errors are always present, regardless of the scenario. However, the third source is much more dominant for indoor scenarios, for which more complex propagation conditions exist [
7]. In indoor environments, much more multipath components influence the received signal strength, resulting in faster channel variation for similar walking speeds. Sporadically occurring extremely fast channel variations during the fading minima create a random difference in reciprocal channel measurements within the 5 ms time slot, directly causing raw key errors.
For scenario 7, a higher threshold of 7 dB is necessary, decreasing the key length to 275 bits. It is important to realize that the loss in key-generation rate, caused by applying the necessary threshold, can be significantly reduced if the transmit-receive turnaround time of the system is decreased to 1 ms or lower. Hardware with less tolerance and a better resolution could finally render the raw KER, before thresholding and reconciliation, very low. In the measurement campaign, the performance is limited due to the state-of-the-art of currently available off-the-shelf components.
4.2. Performance of Eavesdropper Key Generation
Key generation by the eavesdropper is shown to be cumbersome. Eve cannot extract useful keys from her channel measurements. However, some differences in the results exist, dependent on the propagation scenario. For scenarios 2, 4 and 6, the KER for the eavesdropper does not converge at all. A decrease in KER is observed at higher threshold levels for the other scenarios. Increasing the threshold quickly makes the key shorter, therefore a low, or even zero KER obtained by Eve is not useful, as the number of effective key bits is very low. Moreover, the legitimate parties operate at lower threshold levels, for which the KER for Eve is always above and often much higher. Even if Eve were able to use the few bits collected at a higher threshold level to estimate some bits of the longer keys employed by Alice and Bob, those bits only represent a very small part of the legitimate key, corresponding to 4% of the legitimate key bits in the worst-case scenario.
4.3. Choosing a Practical Threshold Level
In a practical system, the threshold should be chosen at the moment of key generation. The measurements provide an indication about which threshold values are realistic. A threshold of 8 dB provides a zero KER in all scenarios of the measurement campaign. Given the number of scenarios tested, a fixed threshold of 10 dB is likely to produce error free keys in nearly all cases. Of course, this fixed threshold does not lead to the highest possible key-generation rate.
For Alice, a more sophisticated option is to dynamically adapt the threshold, based on feedback about the correctness of the key. Bob can transmit this feedback to Alice as a CRC check sum over a number of key bits generated by him after reconciliation. Alice can hence dynamically adjust her threshold level and set it as low as possible for error-free key generation by Bob. This approach should allow a larger average key generation rate for all scenarios.
4.4. Guaranteeing a Secure System Start up
To make the communication secure from the start, a predefined key should be used initially. In practice, a random initial key can be securely distributed to all the nodes, via a wired connection to a common battery-charging unit. It is highly recommended not to send unencrypted packets at the startup process, as this will allow a potential eavesdropper to analyze the system. Note that the results in this paper are actually for an eavesdropper who does know all these details of the system and intercepts all packets. However, encrypting packets from the start makes it virtually impossible for an eavesdropper to extract these details, further improving the security of the communication.
4.5. Increasing the Key Generation Rate
the largest restriction to increase the key generation rate is the limited channel measurement rate imposed by the time correlation of subsequent channel measurements. For walking persons, channel measurement rates much higher than one sample per second will yield low-entropy keys.
The channel measurement rate can further be improved by employing multi-antenna systems. Systems of N body-worn antennas create an MIMO (Multiple-Input Multiple-Output) communication channel between two walking persons. In an MIMO link, physical propagation paths exist, of which the varying parameters can be measured, potentially increasing the key-generation rate by a factor . Note that such a system can obtain this performance by simply switching between antennas, hence full MIMO transmit-receive chains are not necessary, allowing faster key generation at a limited cost.