1. Introduction
Indoor localization is becoming more and more important in today’s wireless world. Being able to achieve accurate ubiquitous localization on hand-held battery operating mobile devices in both indoor and outdoor environments would open the window to many new Location Based Services (LBS). Despite the fact that outdoor global localization solutions exist nowadays with the help of Global Navigation Satellite Systems (GNSS), global solutions for indoor localization are still hard to find. Fingerprinting (FP) approaches can solve the indoor localization problem locally [
1], but such solutions are expensive and rather computationally expensive to be used on a global scale, meaning over several countries or the entire world. In the fingerprinting-based methods, the location service providers construct a fingerprint database, transfer this database to the mobile station (MS), and the MS then computes its location based on similar fingerprints. The fingerprint databases are typically very large since they do contain received signal strengths (RSSs) coming from various access points (APs) and in many points or coordinates within a building. Thus, if a global localization solution would use a fingerprinting approach, the fingerprint database transferred from the server to the MS would include the fingerprints from all essential buildings in the town (or the location area) where the mobile is situated. For example, assuming that we hear an average of 30 APs in each location point inside a building, that we take measurements from an average of 600 location points per building, that there are 25 important buildings (malls, shopping centers, hospitals, airports,
etc.) in the location area where the mobile was identified by the network, then a total of
parameters would need to be stored in the database pertaining to that town and transferred to the mobile. The parameters are the fingerprints—namely, the
coordinates and the measured RSS values per coordinate. In addition, if these parameters are saved with a 32-bit accuracy, the database size of such a server provider for the particular town of our example would be around 15.86 Mbits. Assuming that many users are simultaneously downloading this amount of positioning data from the network, the network would soon become very crowded and the data capacity for wireless communications would be tremendously decreased in order to support the positioning requests. This could easily create a bottleneck on the server side; thus, it is very important to find statistical methods to use instead of fingerprinting in order to decrease the amount of parameters to be sent to the mobile, and thus the data usage for positioning purposes.
There are two alternative ways to address these problems: one is to compute the user’s location entirely at the server side, and the second is to use a probabilistic approach, where what we transfer to the mobile is a smaller number of parameters, extracted in a statistical way from the database. The first solution, which is entirely network-based, suffers from several drawbacks: it offers the user location with some delays (due to the propagation delays between the MS and the network server), and with reduced accuracy (due to the fact that the MS might move between the moment when it sent its location request to the server and until the location computed by the server reaches it). Additionally, since the user location needs to be provided on a continuous basis and for users from different towns, if a significant number of users send their location requests to the location server, then the amount of processing required at the server side also becomes quickly unfeasible.
The second approach, which alleviates all these problems (the need for transferring huge databases with fingerprints and the problem of dealing with a huge amount of data at the server side when the positioning is purely network-based), is the approach addressed in this paper. Here, the positioning and floor estimation is done entirely by the mobile device, and the location server transfers only a small amount of data to the MS. In the probabilistic approaches, instead of transferring the fingerprints database, we only transfer a few parameters per AP in a building (five parameters per AP, as in path-loss model Equation (
4)). Taking the previous example and assuming an average of 150 APs per building, the server would need to transfer to the MS only
parameters, or
Mbits, which would take at most 12 s with the average speed of 50 kpbs. This time already becomes comparable with the cold start-up times in modern GPS receivers. Therefore, the mobile-computing localization algorithms developed based on this approach are highly suitable for the mobile devices of tomorrow which support localization and navigation features. The algorithms developed in this paper lie within this approach.
Due to the unavailability of true channel model, as well as the distribution of noise/modelling errors, most of the probabilistic approaches—whether explicitly or implicitly—employ the standard least-squares (LS) method, which is optimal in the maximum-likelihood sense under the Gaussianity assumption. This assumption may impose significant errors, especially when the noise/modeling errors expose outliers or have tails heavier then Gaussian distribution.
In this paper, we employ M-estimators as a means for robustifying the probabilistic positioning methods, when the model of noise/modelling errors deviates from Gaussianity. The term
M-estimation is used because this class of estimators can be regarded as a generalization of
Maximum-likelihood estimation [
2]. We show how M-estimates can be deployed in four existing positioning methods, namely Weighted Centroid Localization (WCL) [
3], linear and nonlinear trilateration [
4], and deconvolution- based method [
5]. The comparison between the performance of the ordinary and the robustified version for each method is studied using some numerical results, which verify that the M-estimates can provide a higher degree of robustness for these methods.
The potential applications are when a user wants to use his/her smart phone to localize himself/herself inside a multi-floor building (e.g., a shopping mall) that the user may visit for the first time, and possibly guide him/her to a certain favorite place (e.g., the closest shoe store) inside the building. The application that the user uses on the smart phone can have a complete map of the shopping mall, including the 3-dimensional coordinates of all the stores and places inside the building, but to be able to guide him/her to their favorite place it must be able to first localize itself. We would mention here that the focus of this work is on the
z-axis localization, rather than the three-dimensional
localization. Recently, there has been an increasing interest in estimating the
z coordinates due to the fact that finding the correct floor is more important than
coordinates, as few meters error in estimation of
z-coordinates may lead the mobile user to the wrong floor in positioning [
6,
7,
8].
The novelty of our paper is two-fold: first, we present four innovative robustification methods for mobile-based floor detection in wireless positioning, and second, we validate our algorithms through measured and simulated data and show their feasibility in realistic multi-floor scenarios. We point out that the goal of this paper is not to compare different RSS-based localization algorithms (or their robustified counterparts) but rather to show that robustification can improve the performance of each method.
The organization of this paper is as follows: in
Section 2 we describe the system model and briefly explain two celebrated methods of indoor localization—namely, the fingerprinting approach and the path-loss approach. The theoretical contribution of the paper is introduced in
Section 3, where after describing the
M-estimates of regression, we will exploit it to robustify four existing indoor localization approaches.
Section 4 is devoted to the performance analysis of the proposed robust localization approaches, based on numerical real-life measurements, and a simulation experiment is provided in
Section 5. Finally, we conclude the paper in
Section 6.
Notations: Throughout this paper, matrices are denoted by capital boldface letters and vectors and tuples are denoted by small boldface letters. = denotes the equality and ≜ denotes the definition. Besides,
Table 1 summarizes the most important notations used for denoting quantities used in positioning in this paper.
2. System Model and Background on Indoor Localization Methods
Consider a localization system equipped with
positioning signals (e.g., RSS values received from APs). During the offline phase, the positioning signals are collected in
measurements vectors , where
is the number of fingerprints collected in the building and
is the RSS received from access point
at
n-th collected fingerprint. The corresponding known 3-D location of
is denoted by
. We will use the stored data,
, for indoor localization. In the following, we briefly explain two of the famous methods—a nonparametric method and a parametric method—for indoor localization based on the stored data. Then, in
Section 3 we will introduce some robust methods for indoor localization.
2.1. Fingerprinting Localization
In the fingerprinting approach [
9,
10,
11], the fingerprints
, are stored and directly used for localization purposes.
Assume that a Mobile Station (MS), located at unknown coordinates
, observes a positioning vector
, where
is the RSS received from the
-th AP during the online phase. The basic 1-Nearest Neighbor (1-NN) fingerprinting (FP) approach estimates the location of the MS as
where
and
is a dissimilarity measure which is determined based on our assumption for noise. For instance, if we assume that the noise which deviates the
from
is i.i.d white Gaussian, then
is simply the squared Euclidean distance between
and
;
i.e.,
In general, the fingerprint-based localization approach is a
pattern matching approach [
9,
10,
11] rooted in pattern recognition [
12], which tries to match the pattern
observed by MS to the examples
collected in the training data set, and chooses the location of the less-dissimilar example (fingerprint) as the location of the MS. In this regard, each element of the measurements vector
is a
feature of the location
. On the other hand, any measured signal which depends
only on the measurement location (regardless of noise, shadowing, and other uncertainties) can be regarded as a
feature of that location and used for localization using the fingerprinting scheme.
The main problem with the fingerprinting approach is the huge amount of data which must be stored by servers and transmitted to the MS to localize itself when
is a large number. The situation becomes even more severe when the fingerprints are being collected all the time. If we want to use fingerprinting methods for localizing the mobile device, it can only be done on the server side. Due to the limited processing capability and power supply on most mobile devices, they are not capable of storing and processing that huge amount of data [
13]. Furthermore, transmitting such an amount of fingerprinting data from the server to the mobile device takes a lot of time, which makes localization by mobile devices impractical.
2.2. Path-Loss Approach for Indoor Localization
To cope with this problem, a well-known alternative is to use the so-called parametric approaches for indoor localization. In parametric approaches, we use a parametric model for finding the MS location. The parameters of the model are then estimated based on the training data (fingerprinting data) and the MS only stores these parameters and uses them for localization by applying them to the online received positioning vector. In the following, we briefly describe a parametric approach for indoor localization based on the path-loss model.
Any RSS-based localization and floor detection method includes two stages: a training stage and an estimation stage. In the training stage—done either in a dedicated/manual mode or in a crowdsource mode—the data is collected building by building, and the following observations are stored on a server database: , where are the 3D coordinates where the measurements were taken within a certain building, is the total number of fingerprints measured in a building, is the total number of AP per building, and is the measured RSS for the i-th fingerprint, coming from the -th access point.
In the path-loss approach for the localization (one of the main parametric approaches for localization), the target is to extract a sub-set of relevant information starting from the available database . The steps are as follows:
(1) Estimate the unknown AP locations (if there is a known AP location, this can replace the estimated ones). The estimation can be done either via averaging over the positions of a few of the strongest fingerprints (
i.e., where that AP was heard with strongest power) or via the use of a weighted approach, such as the one presented in [
14], or by applying a two-step deconvolution process, as described in [
5]. Our studies showed that the weighted approach gives slightly better results than the other two; thus, it will be selected in our analysis. Since AP location is done in 3D plane, after this step, there will be three parameters to be stored per AP regarding AP position.
(2) Associate an underlying path-loss model with the measured RSS and estimate the model parameters via certain statistical methods. In our paper, we will discuss two path-loss models: the classical slope-based path-loss model [
5] with two additional parameters per AP (transmit power and slope coefficients), and a new simplified path-loss model which focuses on the
z-dimension only and has only one parameter. Thus, the number of extracted parameters per AP is five or six, according to the underlying path-loss model.
The
traditional path-loss model is based on free space wave propagation [
15], and involves two modeling parameters per AP:
, where
is the
-th AP transmit power and
is the path-loss coefficient of the
-th AP. Those two parameters are related to the RSS via:
where
is the
-th AP transmit power and
is the path-loss coefficient of the
-th AP, and
is a noise factor, typically assumed Gaussian distributed, of zero mean and standard deviation
σ. The noise is typically due to shadowing, fading, and measurement errors:
. Above,
is the Euclidean distance between the
-th AP and the
i-th measurement point. The above model can be re-written in matrix form as:
where
is the vector with power fingerprints in logarithmic scale coming from the
-th access point,
is the transpose operator,
is a Gaussian distributed
vector with elements
and
2.3. Memory Complexity of Model-Based Approaches Versus Fingerprinting Approach
We live in the era of Big Data and the need for algorithms which can cope with the huge volume of data and extract insight from it has been a major challenge in almost all data science areas, including wireless localization, for the past few years and will remain a challenge for a foreseeable future. While distributed and cloud-based algorithms remain a clear candidate in many cases, there are scenarios, like what we have here for indoor localization, that the technical limitations (here, the fact that a mobile device should perform the localization task in real-time and cheaply, and therefore cannot get help from other nearby devices or use cloud services).
To address the memory complexity issue we provide a brief comparison between the complexity of fingerprinting approach and model-based approaches in terms of the memory size required for performing localization in the mobile side. In fingerprinting approach the size of data we need to store in the mobile device is proportional to
as we need to store all fingerprinting vectors which are of size
. However in model-based methods (such as the ones proposed in this paper and also in their original non-robust counterparts) the size of data that we need to keep is just proportional to the number of APs,
i.e. . For example in the above-mentioned path-loss approach we need to store
parameters,
i.e., the 3 coordinates of each AP plus their transmit power and their associated path-loss exponents. In Weighted Centroid Localization [
3,
14,
16,
17] approach, as well as its robust version which will be introduced in the next section, we only need to store the 3 coordinates of each AP which means a total of
parameters. This is a significant reduction in the size of data as usually
can be a huge number but
is limited by the hardware cost employed in the building for internet coverage which is typically tens to hundreds maximum.
We remark that all the robust approaches introduced in this paper have the same memory complexity as of their non-robust counterparts and do not increase the size of the data needed to store in the mobile side.
3. Robust Floor Estimation Algorithms
In this section, we introduce four robust floor estimation algorithms. We first review the M-estimates of regression—a method for robust estimation of parameters in a linear regression problem—and then, based on that, robustify four existing indoor localization algorithms for floor estimation.
Consider the linear regression problem
where
is the matrix of regressors (for example matrix
in Equation (
5)),
is the
noisy observation vector,
denotes the
parameter vector for which we are going to find an estimate, and
denotes the error vector whose entries are assumed to be i.i.d. from a symmetric continuous distribution with an unknown scale parameter
s.
Let
denote the
i-th residual for a candidate vector
, where
is the
i-th entry of
, and
is the
i-th row of matrix
. At this point, assume that the scale parameters are known. The ordinary least-squares (LS) tries to minimize
, which yields an unstable solution in the presence of outliers or heavy-tailed noise. The
M-estimators reduce the effect of outliers and heavy-tailed noise by replacing the sum of squared residuals by the following objective function
where
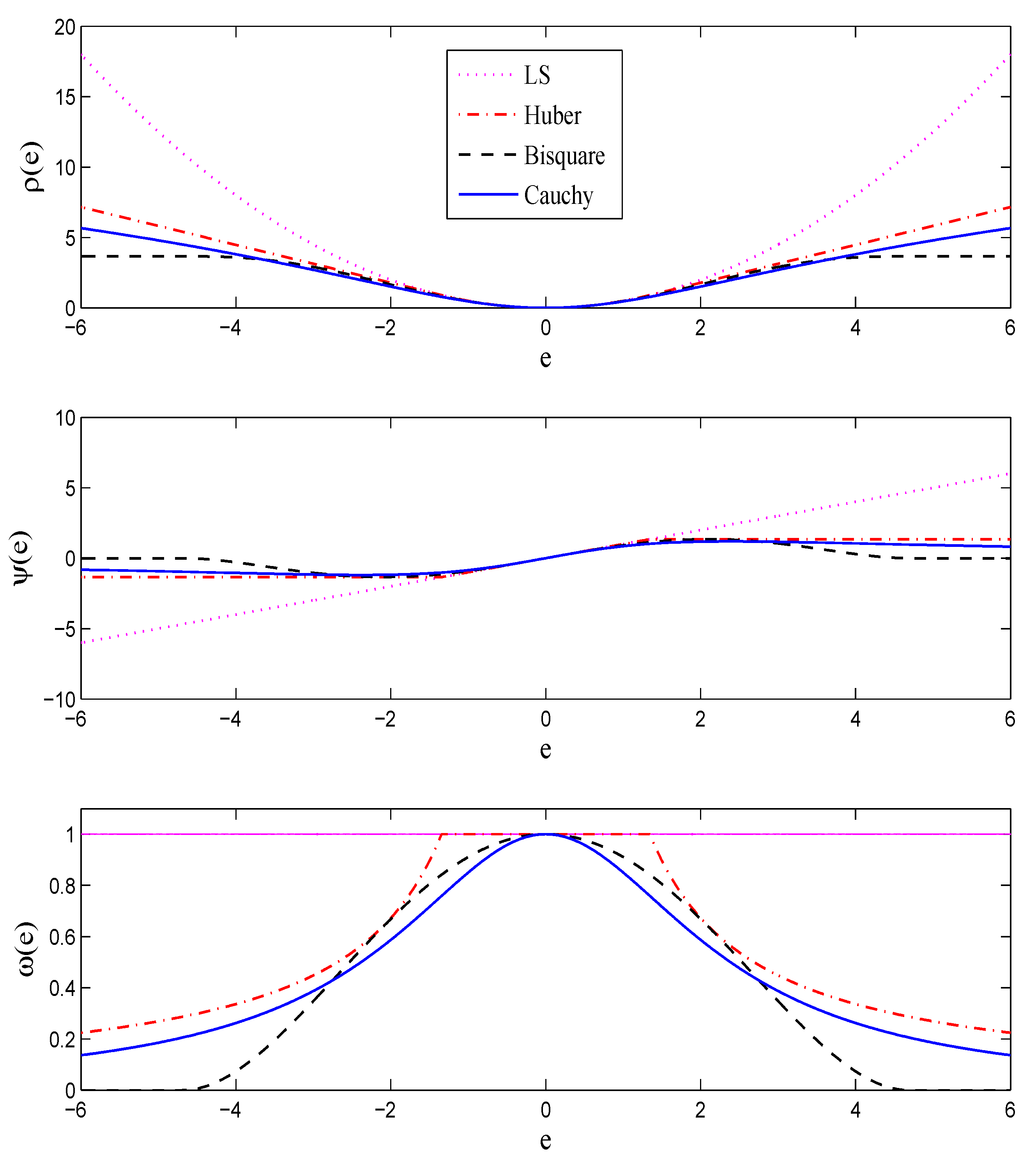
is a symmetric, convex, positive-definite function; see, e.g., the upper plot in
Figure 1.
Let
be the derivative of
ρ. Then, the minimizer of Equation (
8) is the solution to the following equation
Defining
and denoting
, Equation (
9) can be re-written as
Since
is iteself a function of
, to solve Equation (
10) we use an iterative algorithm called
iterative re-weighted least squares (IRLS) [
18,
19], where in each iteration
t an estimate
is computed from Equation (
10) by assuming that
is constant, then the residuals and weights are updated based on
, which will be used in the next iteration for solving Equation (
10) and finding the new estimate
. This iteration continues until a stopping criterion is satisfied. Since the scale
s is unknown in practice, it is commonly replaced at each iteration by a robust estimate
calculated from the current residuals. A commonly-used estimator for scale is the median absolute deviation (MAD)
, which is the default choice in the
robustfit routine of Matlab. From now on, we denote this iterative robust solution to the regression problem of Equation (
7) as
Choosing the weight function
, or equivalently
and
, plays an important role here. In fact, the function
ρ can be interpreted as
, which means that if the error term has distribution
, then the IRLS estimate coincides with the maximum likelihood (ML) estimate. In practice, we do not know the error distribution and we choose the weight function so as to alleviate the effect of large errors stemming from impulsive or heavy-tailed noise. This is accomplished by choosing bounded
functions. Function
, sometimes called the
influence function [
20], determines the influence of a datum on the estimate. For example, in the LS case when
, this influence is linear, which results in the non-robustness of the LS solution. On the other hand, by choosing a bounded
ψ, the influence of large errors stemming from outliers or heavy-tailed noise is bounded, which results in the robustness of the estimate. Some commonly-used robust functions which will be used later in this paper for robustification of localization approaches are presented in
Table 2 and
Figure 1. As can be seen from
Figure 1, all three robust influence functions are bounded. The constant
k is called the
tuning constant, which trades between the robustness and the efficiency when the noise is Gaussian; smaller values of
k provide more robustness but are less efficient when the noise is normally distributed [
2].
In followings, we show concrete examples of how these robustification functions can be applied to solve the 3D indoor localization problem.
3.1. Robust Weighted Centroid Localization
The weighted centroid localization (WCL) approach, first proposed for position estimation in wireless sensor networks [
3], is a simple and low-complexity but promising localization approach. The position of the MS in the WCL approach is computed as the weighted average of the positions of APs heard by the MS. Denoting the set of all hearable APs by
and the (known) coordinates of APs by
, the WCL-based estimate of mobile station coordinates is computed as
where
are weight functions. To weight shorter distances (nearer APs) more than higher distances,
may be chosen as [
3]
where
is the distance between the
-th AP and the MS, and degree
g is to ensure that remote APs still impact the position estimation [
3].
Since
are not readily available, and also since RSS heard from AP
is inversely proportional to
, the weights
in Equation (
12) can be replaced by RSS to obtain the following RSS-based formula for WCL [
14,
16,
17]
where
is the measured RSS of AP number
.
Equation (
14) can be written independently for each coordinate. For instance, for the height coordinate (which is the coordinate that matters in the floor detection task), we have
To robustify the WCL approach, we first remark that Equation (
15) can be written as
where
.
The robust WCL is then obtained by replacing
in the right-hand side of Equation (16) by the general cost function
, which yields
where
s is the scale parameter, which can be estimated as discussed in the previous section.
Implications of the Weighted Centroid Localization Approach
Before proceeding with the next section, we investigate some implications arising from the WCL approach, which will ease the understanding of our assumptions in the next section. We first remark that Equation (16), and hence Equation (
15), is the maximum likelihood solution of the following set of
equations
for finding
z, where
is a zero-mean Gaussian random variable with identical variance for all
. Equation (18) in fact implies that, according to the WCL approach, the relationship between the received power
and the vertical distance between the MS and the
-th access point,
, complies with the following formula:
Now, it is easy to verify that the linear scale Equation (19) will coincide with the noise-free logarithmic scale path-loss model of Equation (
4) if
Path loss exponent in Equation (
4) has the value
, which is the typical path-loss exponent of free space.
in Equation (
4) relates to
as
.
in Equation (
4) relates to random variable
as
. This means that
represents the transmit power of the
-th AP that is considered as a nuisance parameter here, whose value is not of interest.
The distance
in Equation (
4) represents the distance along the
z-coordinate.
In other words, WCL model Equation (
14) can be regarded as a coarse approximation of path-loss model Equation (
4) when the four above assumptions are adopted. In fact, the beauty of the WCL approach is that despite its apparent simplicity and it being a coarse approximation of the channel model (which makes it appealing for use in mobile computing devices) its performance is very promising.
3.2. Robust Nonlinear Joint Parameter Estimation and Trilateration
Let us denote the location of MS by
. Taking into account the discussion from the previous section, we now start from the assumption that the vertical distance between MS and each AP is proportional to the inverse of the square-root of received power, which is
This model is in line with the observation made in the previous section and Equation (19), where is assumed to be the square root of the identical transmit power of APs.
The task is then to estimate
c and
z by minimizing the following function
where
Employing the Gauss–Newton method, we obtain the following iterative formula for finding the minimizer of Equation (21)
where subscript
denotes the value in
k-th iteration,
, and
with
,
, and
To robustify this algorithm, we notice that the second term in the right hand side of Equation (23) can be interpreted as the LS solution to the regression equation
for finding
. Therefore, to robustify Equation (23), we can simply replace this term with the IRLS solution of Equation (26) to get the following formula for the robust joint estimation of
z and
c:
The method can be easily extended to a trilateration case, where all three coordinates are assumed to affect the received RSS. Although a more realistic assumption, it deteriorates the floor detection results in practice, because of the introduction of the errors along the nuisance directions x and y to the problem.
3.3. Robust Linear Joint Parameter Estimation and Multilateraion
Let us denote the location of MS by
, the coordinates of the
i-th AP by
, the distance of MS to the
i-th AP by
, and the distance between the
i-th and
j-th APs by
. Then, it can be easily verified that the set of the following
equations are satisfied [
4].
Assuming that
, this can be rewritten in matrix form as
where
and
Then, the LS solution for joint location estimation and parameter estimation will be
Now, the robust linear trilateration approach can be obtained by replacing the LS solution by the IRLS solution:
The above robust method can be simplified for estimating the vertical position by removing the first two columns of as well as the first two rows of and then solving the robust estimation problem in Equation (34).
3.4. Robust Deconvolution-Based Path-Loss Estimator
In this section, we show how to robustify the deconvolution-based path-loss parameter estimator [
5] by employing the IRLS estimator [
18,
19]. The deconvolution-based approach consists of two main stages: an offline stage, during which we estimate the AP parameters, and an online stage in which we estimate the MS position. We robustify the algorithm by replacing the ordinary LS approach employed in the offline stage (see [
5],
Section 3) by the IRLS estimator described earlier.
where
is the matrix built from the AP parameters as in Equation (
11) [
5], and
is the vector whose
n-th entry
is the received power of access point
at fingerprint
n.
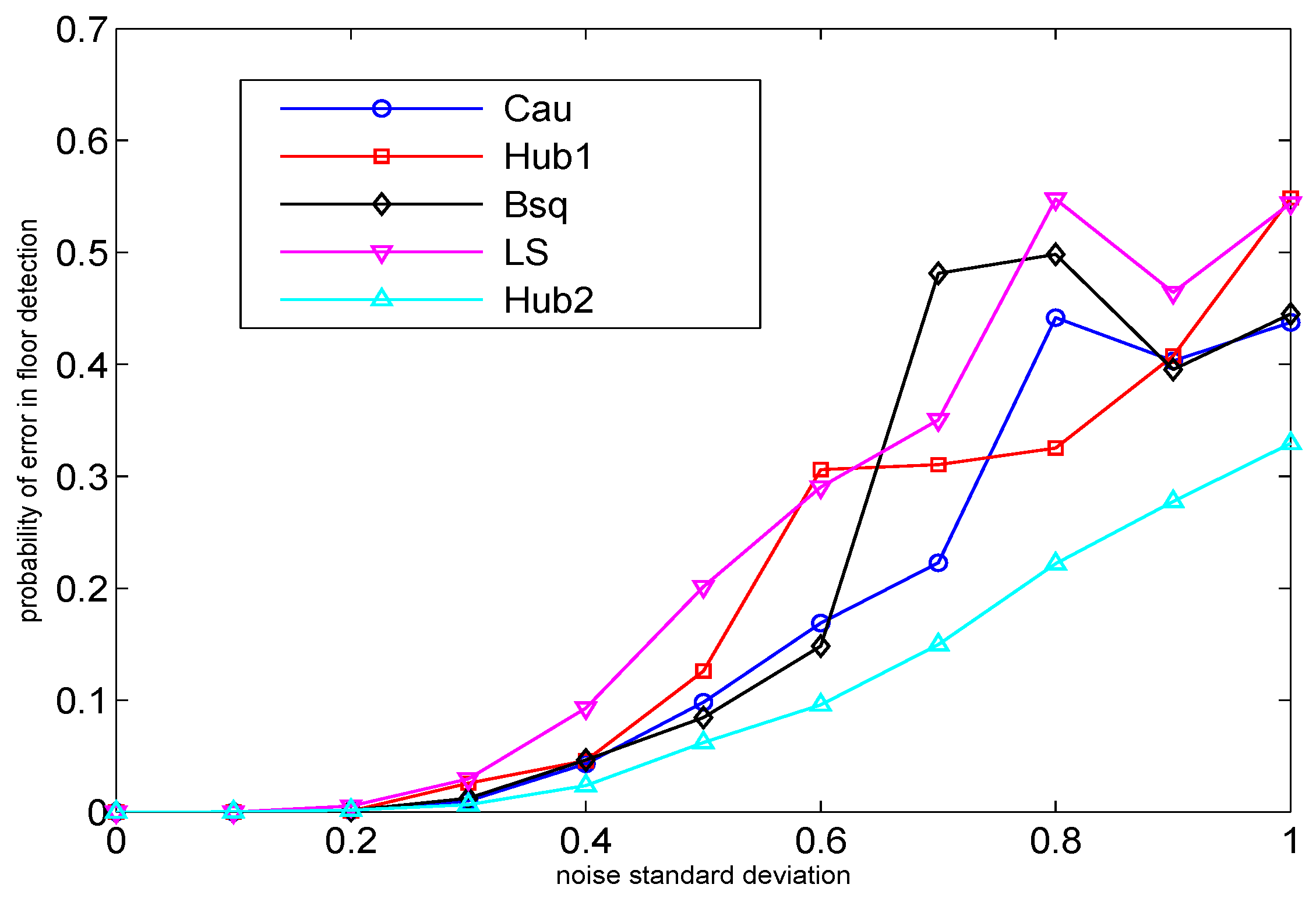
5. Simulation Example
In this section, we study the performance of the proposed robust linear trilateration approach compared to the ordinary linear trilateration [
4] through a simulation example. We remark that for the evaluation of this method, we use simulation instead of real data because the linear trilateration is very sensitive to the coordinates of the AP chosen as the reference point, due to the fact that all the distances are determined with respect to this reference point (see, e.g., Equations (
28) and (
30), where all distances are with respect to AP number 1). In the real data used for the first three experiments, we do not have the exact coordinate of any of the APs to choose it as the reference point. Therefore, the linear trilateration methods are here examined through a simulation example in which the exact location of the APs is assumed known. The number of access points with known locations in the simulation is
, which are located in a four-story building with 20 APs in each floor. The area of each floor is 50 m × 50 m, and the floor height is 4 m. All the APs have the same transmit power and the path-loss exponent is set to
. The receiver noise variance varies from 0 to 1. The number of random runs (the random location of MS in the building) is
. The floor detection is performed by first estimating the 3-D coordinates of the MS as in Equation (34) and then rounding the estimated
z-coordinate to the height of the nearest floor. As can be seen, the robust methods surpass the ordinary LS method. The best performance belongs to Hub2, the Huber robust function with tuning constant
, which provides more robustness compared to the case
.
6. Conclusions
In this paper, we proposed four robustification methods for floor detection on mobile devices. This was accomplished by exploiting the M-estimators to robustify four existing probabilistic positioning approaches with the goal of applying them to the problem of floor detection from RSS measurements in an indoor environment. The first approach was obtained by robustifying the weighted centroid localization approach by replacing the ordinary sum of squared errors by a more general cost function. The second and third approaches were, respectively, a linear and a nonlinear trilateration approach that first adopt a simplified path-loss model and then estimate the position of MS using robust regression methods. The methods need the information of AP locations as a prerequisite. We finally robustified the deconvolution-based approach [
5] via replacing the ordinary least-squares estimator by an iterative reweighted least-squares estimator.
The performance of the proposed robust schemes were exemplified both via real-life measurements (Examples 1 to 3 in
Section 4.2) and simulations (
Figure 5), and all of the proposed robust methods were compared with their non-robust counterparts. In addition, such robust schemes can find their applicability in many LBS applications, such as in emergency applications (e.g., the fast identification of the damaged floors in case of flood or fire), in advertising (e.g., fast finding of the nearby shops at the user’s floor with the desired items),
etc. In addition, the proposed robustification results can be used jointly with additional sensors, such as barometers, when available on the user’s mobile for increased positioning accuracy.
The main findings of our paper is that, by using robustification, we can achieve better results than without robustification. The proposed mobile computing-based floor detection algorithms, which use the heard RSS information from APs, are indeed feasible with today’s existing WLAN infrastructures.