Dynamic RACH Partition for Massive Access of Differentiated M2M Services
Abstract
:1. Introduction
2. Related Work
3. System Model
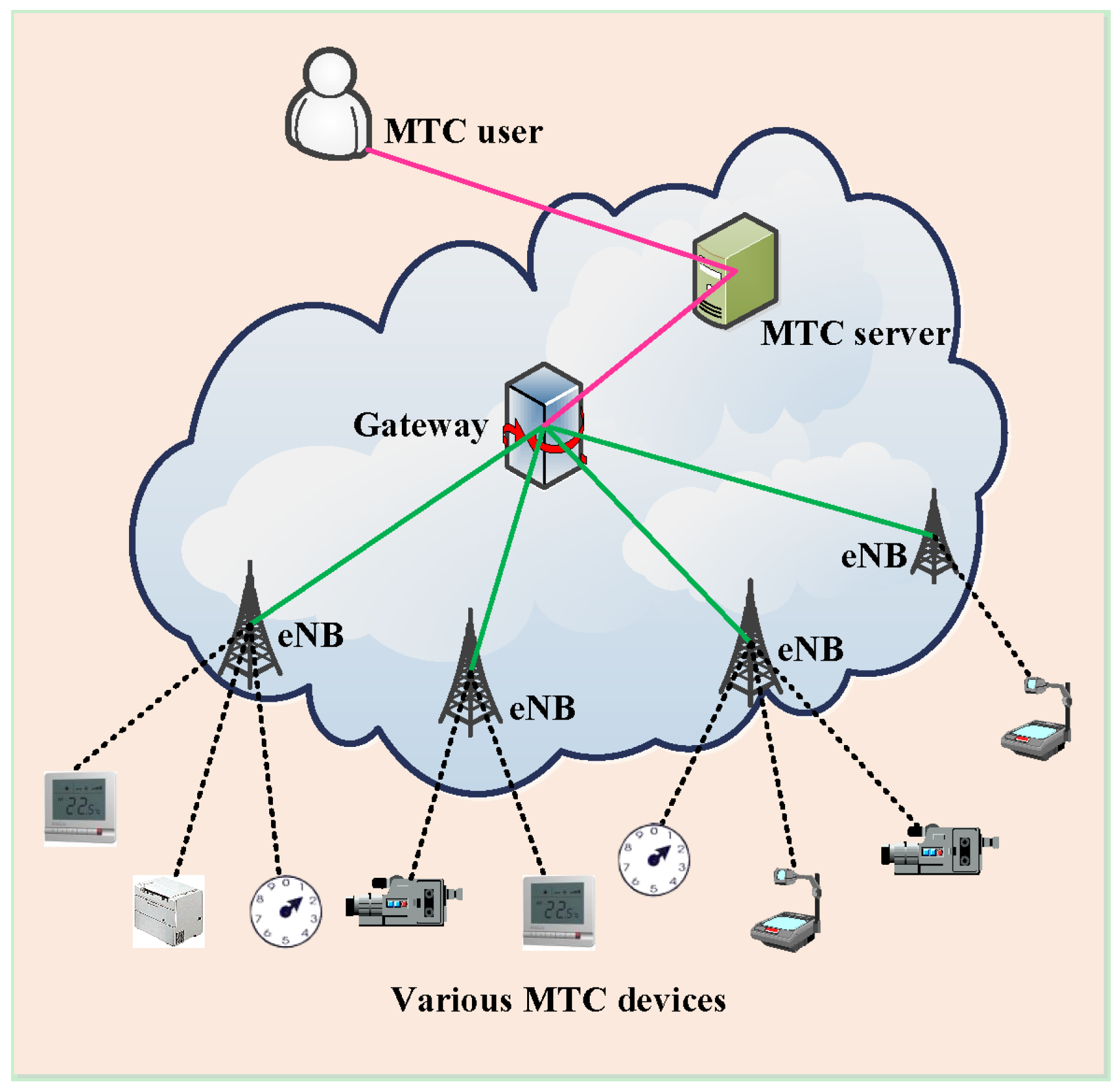
3.1. System Architecture
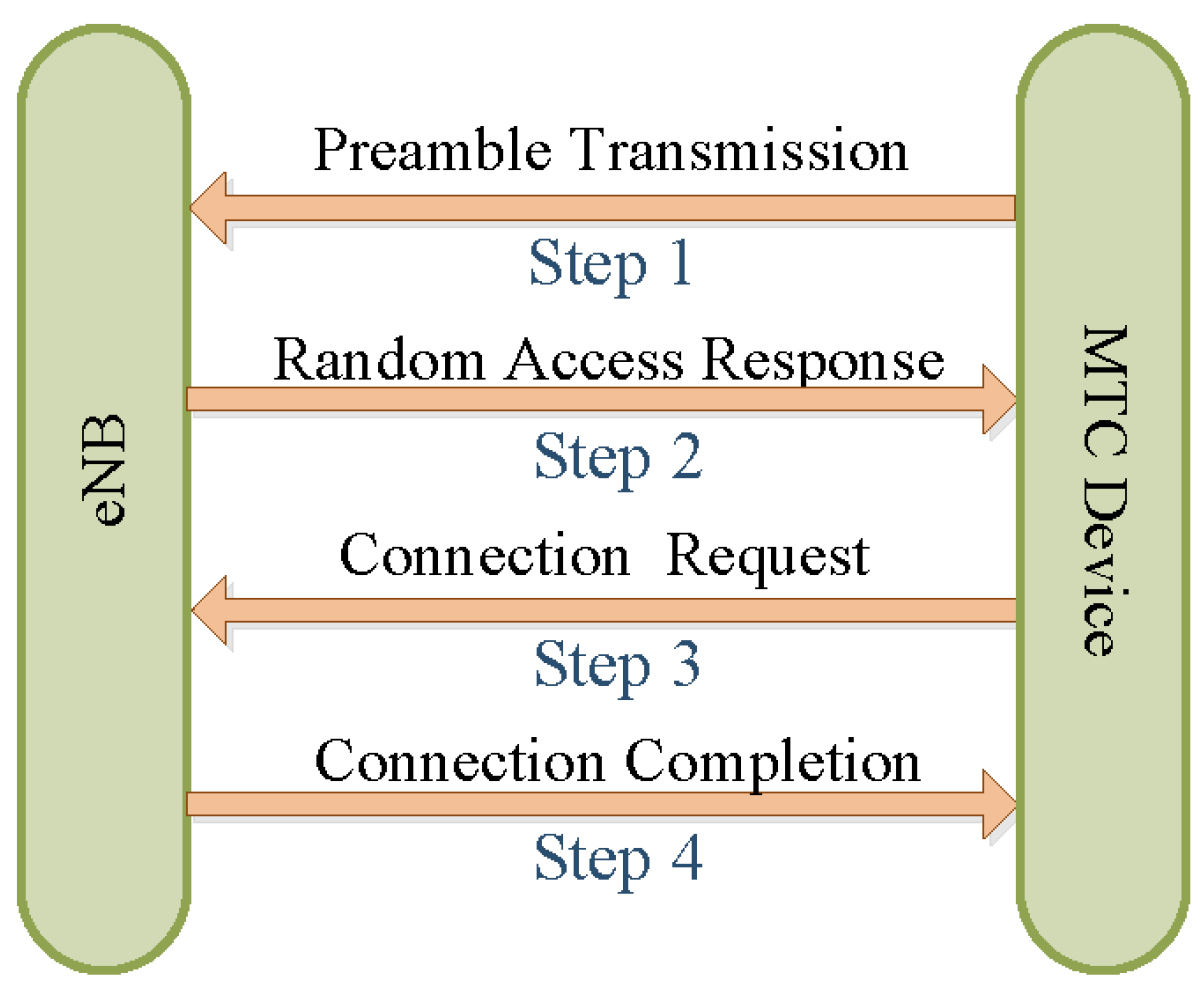
3.2. Random Access Procedures
| Algorithm 1: Four steps of random access. |
|
3.3. Categories of M2M Devices
4. Resource Partition Scheme for M2M Networks
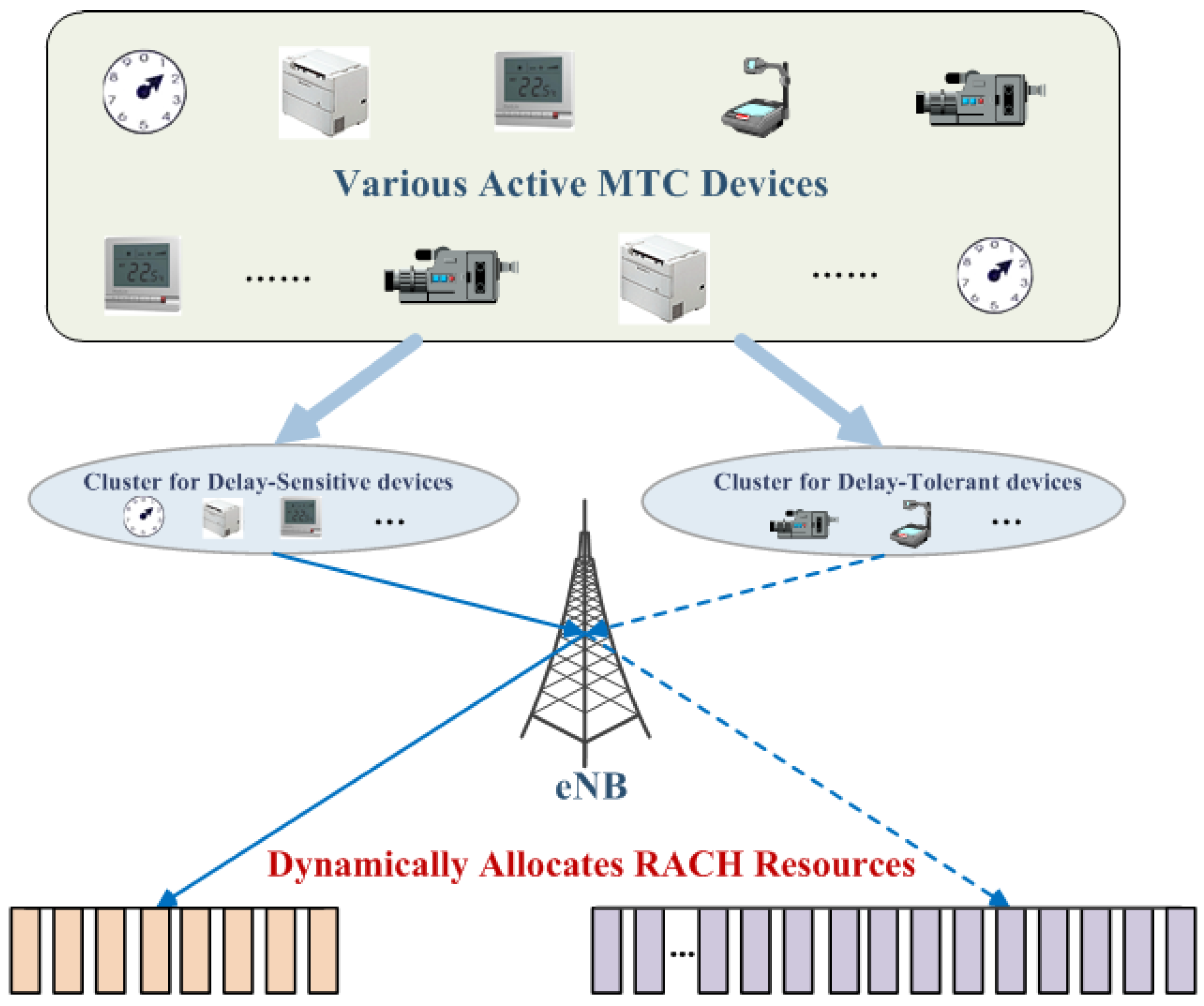
4.1. Clustered Structure
4.2. Dynamic Adjustment of Preamble Partition
| Algorithm 2: Newton iterative algorithm. |
|
4.3. Access Class Barring for Two Clusters Respectively
5. Analysis of the Resource Partition Scheme
5.1. Analysis of Access Success Probability
5.2. Analysis of Preamble Collision Probability
5.3. Analysis of Average Access Delay
6. Simulation Evaluation
6.1. Simulation Setup
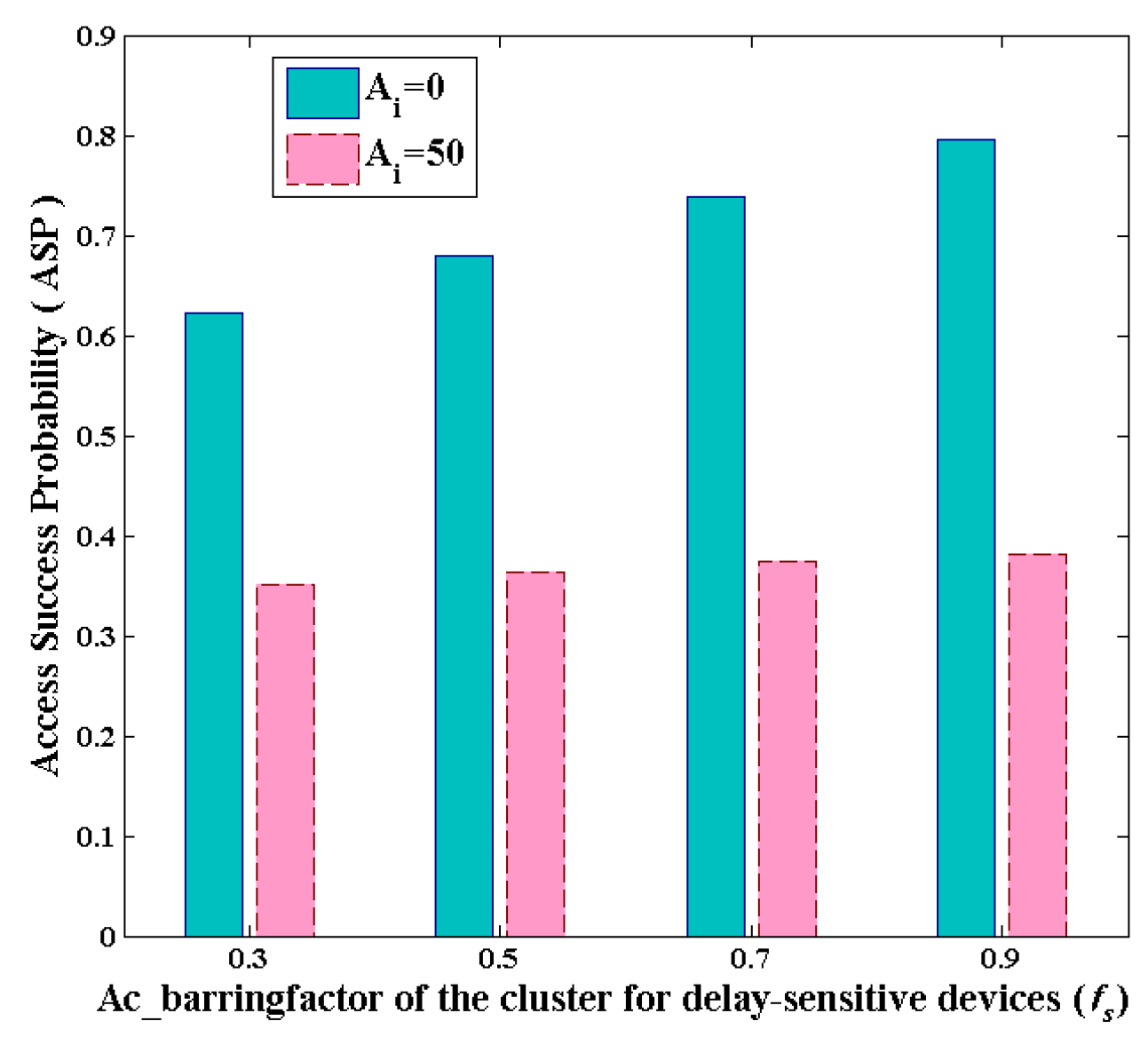
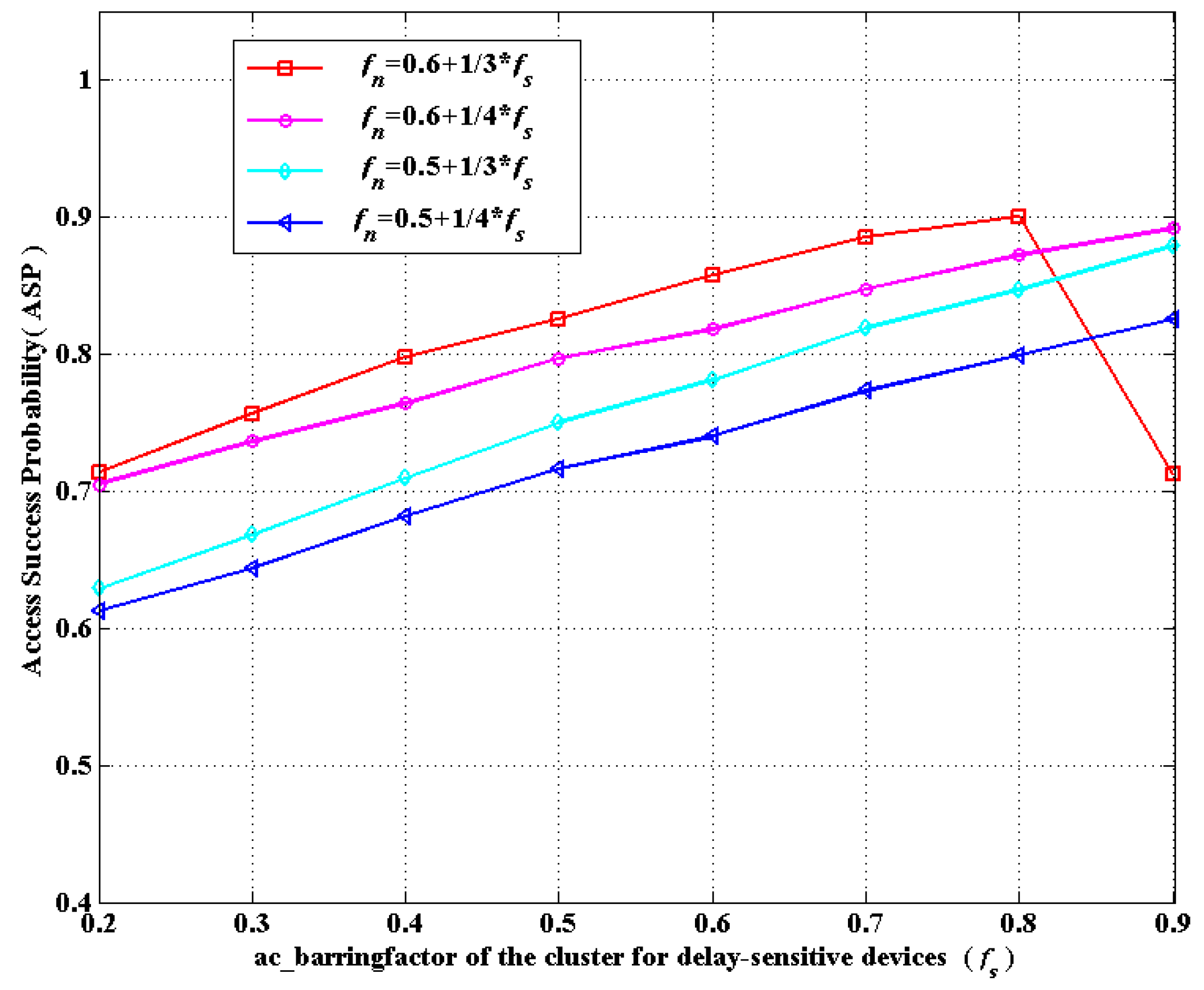
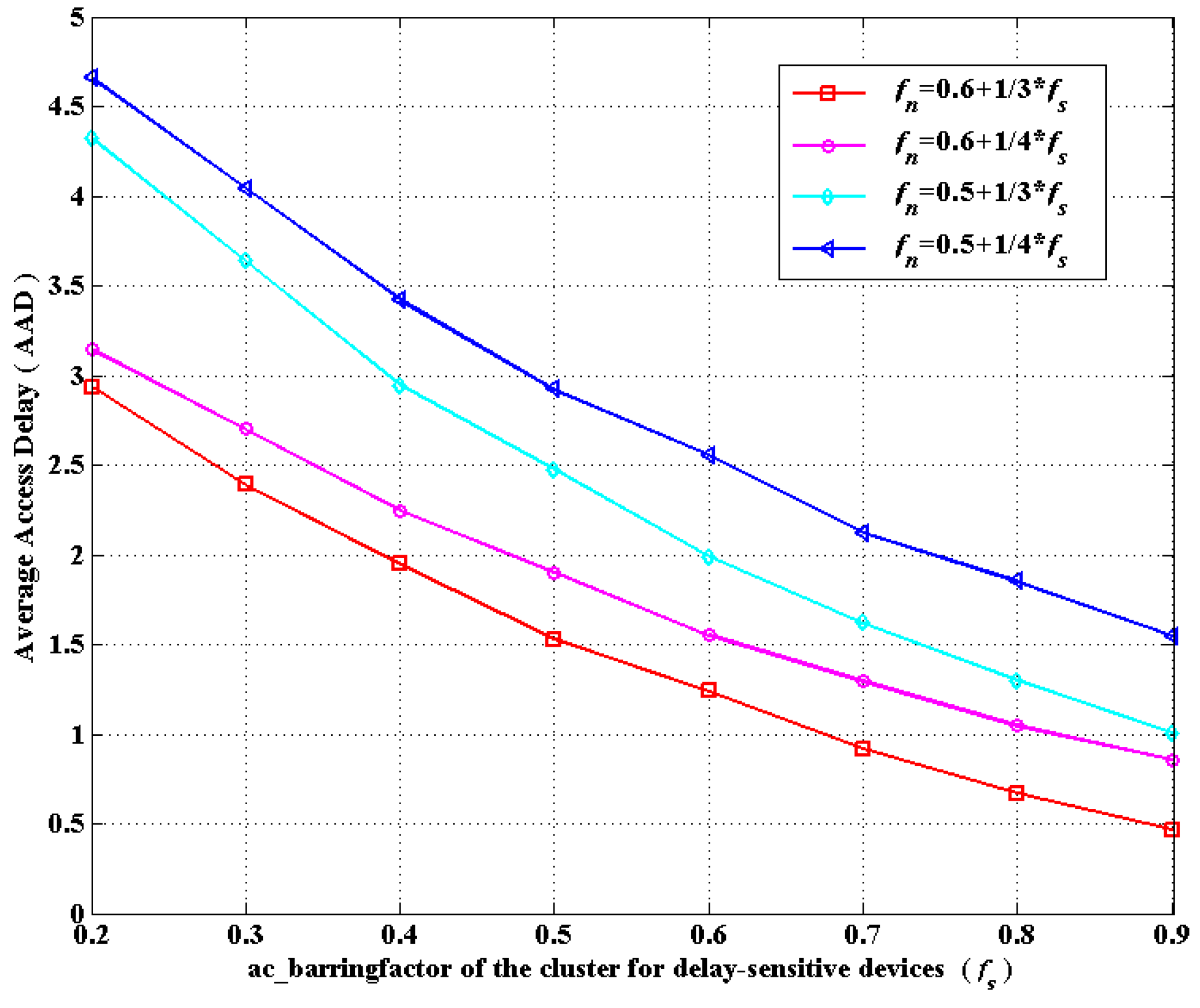
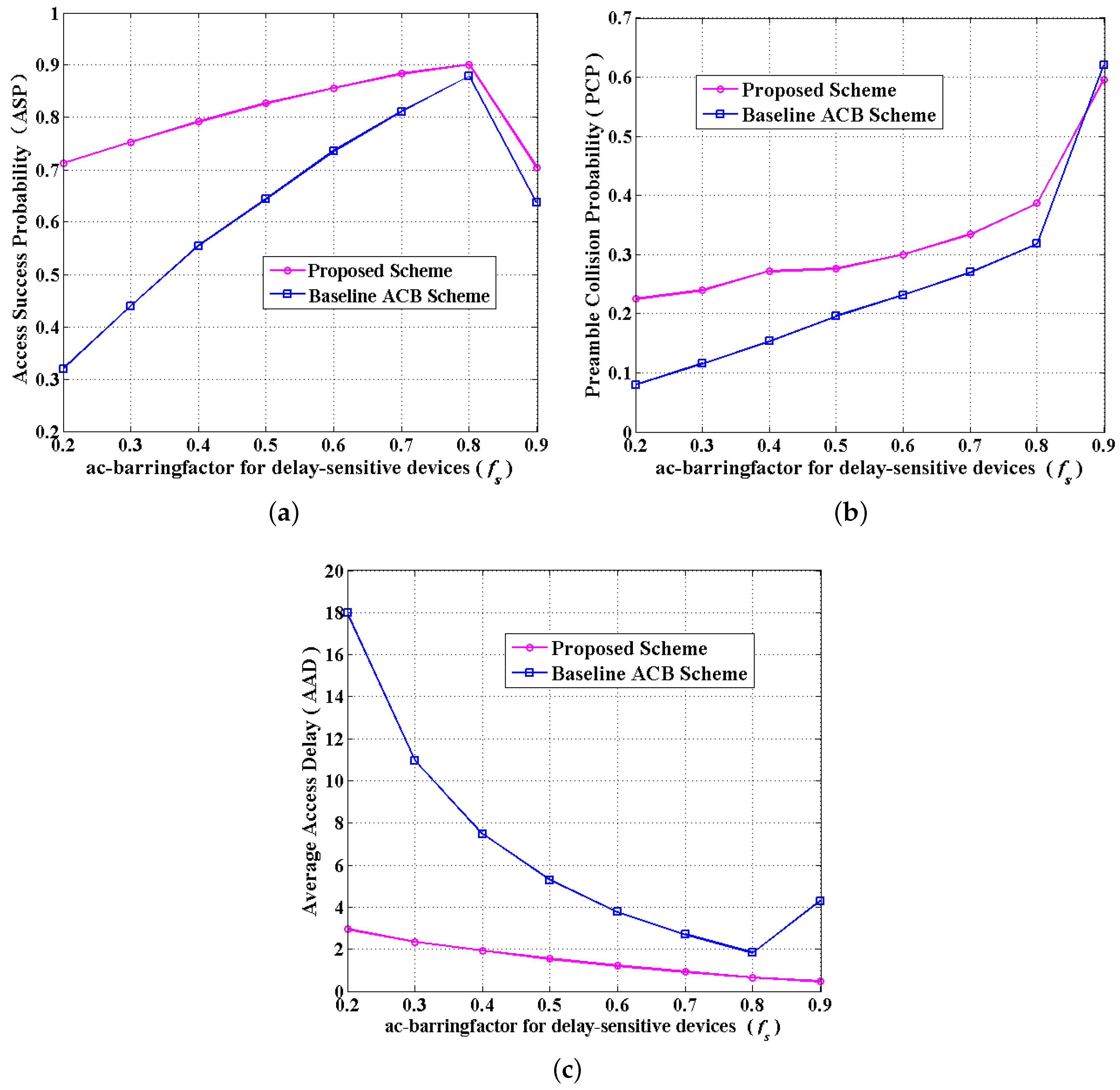
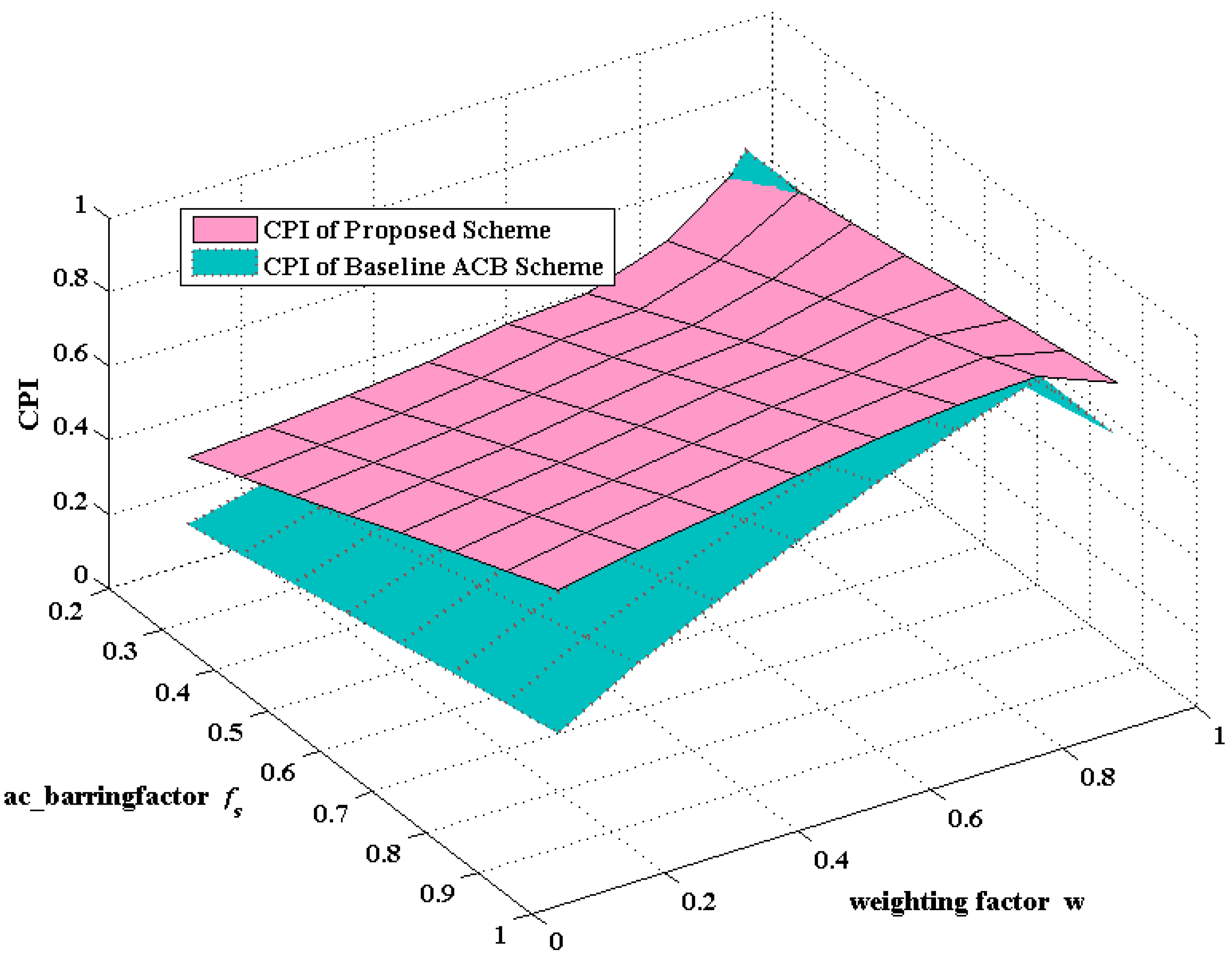
6.2. Simulation Results
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References and Notes
- Ghavimi, F.; Chen, H.H. M2M communications in 3GPP LTE/LTE-A networks: Architectures, service requirements, challenges and applications. IEEE Commun. Surveys Tuts. 2015, 17, 525–549. [Google Scholar] [CrossRef]
- Jung, S.-J.; Chung, W.-Y. Non-Intrusive healthcare system in global Machine-to-Machine networks. IEEE Sens. J. 2013, 13, 4824–4830. [Google Scholar] [CrossRef]
- Ide, C.; Dusza, B.; Putzke, M.; Muller, C.; Wietfeld, C. Influence of M2M communication on the physical resource utilization of LTE. In Proceedings of the Wireless and Mobile Networking Conference (WMNC), Dubai, UAE, 23–25 April 2013; pp. 1–4.
- Lam, R.K.; Chen, K.C. Congestion control for M2M traffic with heterogeneous throughput demands. In Proceedings of the Wireless Communications and Networking Conference (WCNC), Shanghai, China, 8 January 2013; pp. 1452–1457.
- Chen, Y.-S.; Chiang, W.-L. A Spiderweb-Based massive access management protocol for M2M wireless networks. IEEE Sens. J. 2015, 15, 5765–5776. [Google Scholar] [CrossRef]
- 3GPP TR 37.868 V11.0.0. Study on RAN Improvements for Machine-Type Communications. (Release 11) September 2011.
- Wu, G.; Talwar, S.; Johnsson, K.; Himayat, N.; Johnson, K.D. M2M: From mobile to embedded Internet. IEEE Commun. Mag. 2011, 49, 36–43. [Google Scholar]
- Phuyal, U.; Vannithamby, R. Controlling access overload and signaling congestion in M2M networks. In Proceedings of the Asilomar Conference on Signals, Systems and Computers (ASILMOR), Pacific Grove, CA, USA, 6–9 November 2012; pp. 591–595.
- Wang, S.-H.; Su, H.-J.; Hsieh, H.-Y.; Yeh, S.-P.; Ho, M. Random access design for clustered wireless machine to machine networks. In Proceedings of the IEEE BlackSeaCom, Batumi, Georgia, 3–5 July 2013; pp. 107–111.
- Lo, A.; Law, Y.; Jacobsson, M. A cellular-centric service architecture for machine-to-machine (M2M) communications. IEEE Wirel. Commun. 2013, 20, 143–151. [Google Scholar] [CrossRef]
- Lien, S.-Y.; Chen, K.-C.; Lin, Y. Toward ubiquitous massive accesses in 3GPP machine-to-machine communications. IEEE Commun. Mag. 2011, 49, 66–74. [Google Scholar] [CrossRef]
- Wang, Y.; Ren, P.; Du, Q.; Sun, L. Optimal power allocation for underlay-based cognitive radio networks with primary user’s statistical delay QoS provisioning. IEEE Trans. Wirel. Commun. 2015, 14, 6896–6910. [Google Scholar] [CrossRef]
- Wang, Y.; Ren, P.; Gao, F.; Su, Z. A hybrid underlay/overlay transmission mode for cognitive radio networks with statistical Quality-of-Service provisioning. IEEE Trans. Wirel. Commun. 2014, 13, 1482–1498. [Google Scholar] [CrossRef]
- Chen, H.; Liu, L.; Matyjas, J.; Medley, M. Optimal resource allocation for sensing based spectrum sharing D2D networks. Comput. Elec. Eng. (Elsevier) 2015, 44, 107–121. [Google Scholar]
- Chen, H.; Liu, L. Resource allocation for sensing-based device-to-device (D2D) networks. In Proceedings of the 49th Asilomar Conference on Signals, Systems and Computers, Pacific Grove, CA, USA, 8–11 November 2015; pp. 1058–1062.
- Du, Q.; Song, H.; Xu, Q.; Ren, P.; Sun, L. Interference-controlled D2D routing aided by knowledge extraction at cellular infrastructure towards ubiquitous CPS. Pers. Ubiquitous Comput. 2015, 19, 1033–1043. [Google Scholar] [CrossRef]
- Sun, L.; Du, Q.; Ren, P.; Wang, Y. Two birds with one stone: Towards secure and interference-free D2D transmissions via constellation rotation. IEEE Trans. Veh. Technol. 2015. [Google Scholar] [CrossRef]
- Sun, L.; Ren, P.; Du, Q.; Wang, Y.; Gao, Z. Security-aware relaying scheme for cooperative networks with untrusted relay nodes. IEEE Commun. Lett. 2015, 19, 463–466. [Google Scholar] [CrossRef]
- Pereira, C.; Aguiar, A. Towards Efficient Mobile M2M Communications: Survey and Open Challenges. Sensors 2014, 14, 19582–19608. [Google Scholar] [CrossRef] [PubMed]
- Zheng, K.; Ou, S.; Alonso-Zarate, J.; Dohler, M.; Liu, F.; Zhu, H. Challenges of massive access in highly dense LTE-advanced networks with machine-to-machine communications. IEEE Wirel. Commun. 2014, 21, 12–18. [Google Scholar] [CrossRef]
- Lee, J.; Jung, I. Adaptive-Compression Based Congestion Control Technique for Wireless Sensor Networks. Sensors 2010, 10, 2919–2945. [Google Scholar] [CrossRef] [PubMed]
- Bayat, S.; Li, Y.; Han, Z.; Dohler, M.; Vucetic, B. Distributed massive wireless access for cellular machine-to-machine communication. In Proceedings of the International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 2767–2772.
- Chen, Y.-S.; Chiang, W.-L. A Spiderweb-Based Massive Access Management Protocol for M2M Wireless Networks. IEEE Sens. J. 2015, 15, 5765–5776. [Google Scholar] [CrossRef]
- 3GPP TS 36.331 V10.5.0, Evolved Universal Terrestrial Radio Access (E-UTRA). Radio Resource Control (RRC). March 2012.
- Chen, Y.; Wang, W. Machine-to-Machine Communication in LTE-A. In Proceedings of the IEEE IEEE Vehicular Technology Conference (VTC Fall), Ottawa, ON, Canada, 6–9 September 2010; pp. 1–4.
- Amokrane, A.; Ksentini, A.; Hadjadj-Aoul, Y.; Taleb, T. Congestion control for machine type communications. In Proceedings of the IEEE International Conference on Communications (ICC), 10–15 June 2012; pp. 778–782.
- Lo, A.; Law, Y.; Jacobsson, M.; Kucharzak, M. Enhanced LTE-Advanced Random-Access Mechanism for Massive Machine-to-Machine (M2M) Communications. In Proceedings of the 27th Meeting of Wireless World Research Form (WWRF), Düsseldorf, Germany, 23–25 October 2011.
- Taleb, T.; Kunz, A. Machine type communications in 3GPP networks: Potential, challenges, and solutions. IEEE Commun. Mag. 2012, 50, 178–184. [Google Scholar] [CrossRef]
- Lu, R.; Li, X.; Liang, X.; Shen, X.; Lin, X. GRS: The green, reliability, and security of emerging machine to machine communications. IEEE Commun. Mag. 2011, 49, 28–35. [Google Scholar]
- Zhang, Y.; Yu, R.; Xie, S.; Yao, W.; Xiao, Y.; Guizani, M. Home M2M networks: Architectures, standards, and QoS improvement. IEEE Commun. Mag. 2011, 49, 44–52. [Google Scholar] [CrossRef]
- Cheng, J.-J.; Lee, C.-H.; Lin, T.-M. Prioritized random access with dynamic access barring for RAN overload in 3GPP LTE-A networks. In Proceedings of the IEEE Global Communications Conference (GLOBECOM) Workshops, Houston, TX, USA, 5–9 December 2011; pp. 368–372.
- Yang, X.; Fapojuwo, A.; Egbogah, E. Performance Analysis and Parameter Optimization of Random Access Backoff Algorithm in LTE. In Proceedings of the IEEE Vehicular Technology Conf. (VTC Fall), Quebec, QC, Canada, 3–6 September 2012; pp. 1–5.
- Pratas, N.K.; Thomsen, H.; Stefanovic, C.; Popovski, P. Code-Expanded Random Access for Machine-Type Communications. In Proceedings of the IEEE Global Communications Conference (GLOBECOM) Workshops, Anaheim, CA, USA, 3–7 December 2012; pp. 1681–1686.
- Cheng, M.Y.; Lin, G.-Y.; Wei, H.-Y.; Hsu, A.-C. Overload control for Machine-type-communications in LTE-Advanced system. IEEE Commun. Mag. 2012, 50, 38–45. [Google Scholar] [CrossRef]
- Laya, A.; Alonso, L.; Alonso-Zarate, J. Is the random access channel of LTE and LTE-A suitable for M2M communications? a survey of alternatives. IEEE Commun. Surveys Tuts. 2014, 16, 4–16. [Google Scholar] [CrossRef]
- Afrin, N.; Brown, J.; Khan, J.Y. Performance analysis of an enhanced delay sensitive LTE uplink scheduler for M2M traffic. In Proceedings of the Telecommunication Networks and Applications Conference (ATNAC), Christchurch, New Zealand, 20–22 November 2013; pp. 154–159.
- Park, I.; Kim, D.; Har, D. MAC achieving low latency and energy efficiency in hierarchical M2M networks with clustered nodes. IEEE Sens. J. 2015, 15, 1657–1661. [Google Scholar] [CrossRef]
- He, H.; Du, Q.; Song, H.; Li, W.; Wang, Y.; Ren, P. Traffic-aware ACB scheme for massive access in machine-to-machine networks. In Proceedings of the IEEE International Conference on Communications, London, UK, 8–12 June 2015.
- 3GPP TSG RAN WG2 #71 R2-104663, [70bis#11] LTE: MTC LTE Simulations. ZTE, Madrid, Spain, 23 August 2010.
- 3GPP TSG RAN WG2 #71 R2-104662, MTC Simulation ResultsWith Specific Solutions. ZTE, Madrid, Spain, 23 August 2010.
- 3GPP TR 23.898, Access Class Barring and Overload Protection. (Release 7). V7.0.0, March 2005.


| Parameter | Settings |
|---|---|
| Cell bandwidth | 5 MHz |
| Number of M2M devices | 30,000 |
| Attempts’ distribution | Beta distribution |
| Distribution period | 10 s |
| PRACH configuration index | 6 |
| Number of preambles for contention-based RA | 54 |
| Ra-ResponseWindowSize | 5 sub-frames |
| Backoff indicator | 5 ms |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Du, Q.; Li, W.; Liu, L.; Ren, P.; Wang, Y.; Sun, L. Dynamic RACH Partition for Massive Access of Differentiated M2M Services. Sensors 2016, 16, 455. https://doi.org/10.3390/s16040455
Du Q, Li W, Liu L, Ren P, Wang Y, Sun L. Dynamic RACH Partition for Massive Access of Differentiated M2M Services. Sensors. 2016; 16(4):455. https://doi.org/10.3390/s16040455
Chicago/Turabian StyleDu, Qinghe, Wanyu Li, Lingjia Liu, Pinyi Ren, Yichen Wang, and Li Sun. 2016. "Dynamic RACH Partition for Massive Access of Differentiated M2M Services" Sensors 16, no. 4: 455. https://doi.org/10.3390/s16040455





