A Survey on Security and Privacy in Emerging Sensor Networks: From Viewpoint of Close-Loop
Abstract
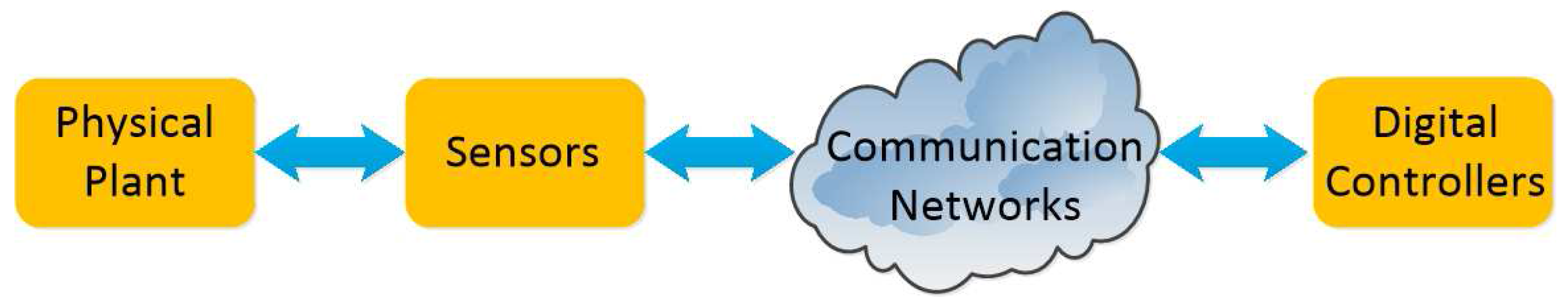
:1. Introduction
2. Cyber-Physical Systems Security
2.1. Security Analysis of General Cyber-Physical Systems
2.2. Smart Grid and Power Systems
2.3. Secure Algorithms
2.4. Secure State Estimation and Control
2.5. Game-Theoretic Analysis
3. Cyber-Physical System Privacy
3.1. Privacy-Preserving Communication
3.2. Privacy-Preserving Computation and Control
3.3. Privacy Preserving in Application Fields
4. Conclusions
- Modeling of CPSs: Currently, most models of CPS either focused on the physical side of the system (models from control theory) or focused on the cyber system (models from computer science). These models may not be sufficient to analyze the effects of cyber attacks on real physical systems. For example, an attack on cyber systems may cause a control algorithm to fail and cause the instability of the actual physical systems. On the other hand, an attack on the physical systems may cause a blackout and shut down the cyber systems. Furthermore, an adversary could even launch a hybrid attack on both physical and cyber systems. Hence, it is important to develop a unified framework and model to address the ever-increasing security concern in CPSs.
- Modeling of the attacks: Most current research focused on an attacker that has full knowledge of the system. Such an attacker can be seen as the worst-case attacker. However, in practice, it is very difficult for an adversary to obtain such information. For example, in a smart grid, even the system operator does not have a full accurate model of the system, let alone the attacker. As is shown in [12], the first CPS malware, Stuxnet, only requires the attacker to know that the system is in a steady state. Therefore, assuming an adversary with full knowledge may lead to an over-conservative system design.
- Measures of privacy: The existing studies of CPSs privacy are still in their infancy. In particular, we lack rich mathematical models of measuring CPS privacy. How to define proper privacy measures and how to design appropriate and corresponding algorithms to maximize these measures are important questions to be answered.
- Joint design of intrusion detection, state estimation and control algorithm: As is illustrated in [12], the CPS can use noisy control to detect whether the sensory data have been replayed, with some loss of control performance. This illustrates the power of a jointly-designed estimation and control algorithm and intrusion detection algorithm. In other words, the estimation and control algorithm can excite the system in such a way that makes the attacker’s action visible to the intrusion detection algorithm. Consequently, the intrusion detection algorithm can detect malicious components and send alerts to the estimation and control algorithm. It is still quite an open problem how to find the optimal design.
- Verification and validation: The control algorithm of a CPS could potentially be very complicated, which may involve thousands or tens of thousands lines of code. Hence, it is important to provide verification and validation tools to check whether potential security vulnerability may be introduced.
- Secure atomic operation: Is it possible to build a secure algorithm from secure atomic operations? In software engineering, the defense against many different attacks is provided by the safe libraries. For example, the secure string library for C provides defense against buffer overflow attack. Therefore, the software engineers do not need to care about the buffer overflow attack as long as they use the safe library. In CPS, it would be great to define some secure atomic operations (for example, the median is more secure than the average) and to prove that any algorithm that only uses such secure operations will also be secure, so that a control engineer would not need to worry about security during his/her design process.
Acknowledgments
Conflicts of Interest
References
- Marburger, J.H.; Kvamme, E.F.; Scalise, G.; Reed, D.A. Leadership Under Challenge: Information Technology R&D in a Competitive World. An Assessment of the Federal Networking and Information Technology R&D Program. Pres. Counc. Advis. Sci. Technol. 1992, 13, 259–265. [Google Scholar]
- Kim, K.D.; Kumar, P.R. Cyber-Physical Systems: A perspective at the centennial. IEEE Proc. 2012, 100, 1287–1308. [Google Scholar]
- Zhang, Y.; He, S.; Chen, J. Data gathering optimization by dynamic sensing and routing in rechargeable sensor networks. IEEE/ACM Trans. Netw. 2016. [Google Scholar] [CrossRef]
- He, S.; Chen, J.; Li, X.; Shen, X.; Sun, Y. Mobility and Intruder Prior Information Improving the Barrier Coverage of Sparse Sensor Networks. IEEE Trans. Mobile Comput. 2014, 13, 1268–1282. [Google Scholar]
- Guo, S.; Zhang, H.; Zhong, Z.; Chen, J.; Cao, Q.; He, T. Detecting Faulty Nodes with Data Errors for Wireless Sensor Networks. ACM Trans. Sensor Netw. 2014, 10. [Google Scholar] [CrossRef]
- Zeng, W.; Chow, M.Y. A Reputation-Based Secure Distributed Control Methodology in D-NCS. IEEE Trans. Ind. Electron. 2014, 61, 6294–6303. [Google Scholar] [CrossRef]
- Zeng, W.; Chow, M.Y. Resilient Distributed Control in the presence of Misbehaving Agents in Networked Control Systems. IEEE Trans. Cybern. 2014, 44, 2038–2049. [Google Scholar] [CrossRef] [PubMed]
- Pajic, M.; Mangharam, R.; Sokolsky, O.; Arney, D.; Goldman, J.; Lee, I. Model-Driven Safety Analysis of Closed-Loop Medical Systems. IEEE Trans. Ind. Inform. 2014, 10, 3–16. [Google Scholar] [CrossRef] [PubMed]
- Chen, J.; Yu, Q.; Chai, B.; Sun, Y.; Fan, Y.; Shen, X. Dynamic Channel Assignment for Wireless Sensor Networks: A Regret Matching Based Approach. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 95–106. [Google Scholar] [CrossRef]
- Yang, Q.; He, S.; Li, J.; Chen, J. Energy-Efficient Probabilistic Area Coverage in Wireless Sensor Networks. IEEE Trans. Veh. Technol. 2015, 64, 367–377. [Google Scholar] [CrossRef]
- Cyber-Physical Systems. Available online: http://www.nsf.gov/pubs/2008/nsf08611/nsf08611.pdf (accessed on 11 June 2008).
- Mo, Y.; Kim, T.; Brancik, K.; Dickinson, D.; Lee, H.; Perrig, A.; Sinopoli, B. Cyber-Physical Security of a Smart Grid Infrastructure. IEEE Proc. 2012, 100, 195–209. [Google Scholar]
- Yang, Z.; Cheng, P.; Chen, J. Learning-based Jamming Attack against Low-duty-cycle Networks. IEEE Trans. Dependable Secure Comput. 2015. [Google Scholar] [CrossRef]
- Zhang, H.; Cheng, P.; Shi, L.; Chen, J. Optimal DoS Attack Policy Against Remote State Estimation. In Proceedings of the 2013 IEEE 52nd Annual Conference on Decision and Control (CDC), Firenze, Italy, 10–13 December 2013.
- Zhang, H.; Cheng, P.; Shi, L.; Chen, J. Optimal DoS Attack Policy with Energy Constraint. IEEE Trans. Autom. Control 2015, 60, 3023–3028. [Google Scholar] [CrossRef]
- Teixeira, A.; Pérez, D.; Sandberg, H.; Johansson, K. Attack models and scenarios for networked control systems. In Proceedings of the 1st International Conference on High Confidence Networked Systems, Beijing, China, 17–18 April 2012.
- Mo, Y.; Sinopoli, B. Secure control against replay attacks. In Proceedings of the Annual Allerton Conference on Communication, Control, and Computing, Monticello, IL, USA, 30 September–2 October 2009.
- Mo, Y.; Sinopoli, B. Integrity attacks on cyber-physical systems. In Proceedings of the 1st International Conference on High Confidence Networked Systems, Beijing, China, 17–18 April 2012.
- Mo, Y.; Hespanha, J.; Sinopoli, B. Resilient Detection in the Presence of Integrity Attacks. IEEE Trans. Signal Process. 2014, 62, 31–43. [Google Scholar] [CrossRef]
- Zhang, H.; Cheng, P.; Wu, J.; Shi, L.; Chen, J. Online Deception Attack against Remote State Estimation. In Proceedings of the World Congress of the International Federation of Automatic Control, Cape Town, South Africa, 24–29 August 2014.
- Langner, R. Stuxnet: Dissecting a cyberwarfare weapon. IEEE Secur. Priv. 2011, 9, 49–51. [Google Scholar] [CrossRef]
- Mo, Y.; Chabukswar, R.; Sinopoli, B. Detecting integrity attacks on SCADA systems. IEEE Trans. Control Syst. Technol. 2014, 22, 1396–1407. [Google Scholar]
- Zhu, M.; Martinez, S. On the performance analysis of resilient networked control systems under replay attacks. IEEE Trans. Autom. Control 2014, 59, 804–808. [Google Scholar] [CrossRef]
- Miao, F.; Pajic, M.; Pappas, G.J. Stochastic game approach for replay attack detection. In Proceedings of the IEEE 52nd Annual Conference on Decision and Control (CDC), Firenze, Italy, 10–13 December 2013.
- Kwon, C.; Liu, W.; Hwang, I. Security analysis for Cyber-Physical Systems against stealthy deception attacks. In Proceedings of the American Control Conference (ACC), Washington, DC, USA, 17–19 June 2013.
- Cheminod, M.; Durante, L.; Valenzano, A. Review of Security Issues in Industrial Networks. IEEE Trans. Ind. Inform. 2013, 9, 277–293. [Google Scholar] [CrossRef]
- Pasqualetti, F.; Dorfler, F.; Bullo, F. Attack Detection and Identification in Cyber-Physical Systems. IEEE Trans. Autom. Control 2013, 58, 2715–2729. [Google Scholar] [CrossRef]
- Meng, W.; Yang, Q.; Ying, Y.; Sun, Y.; Yang, Z.; Sun, Y. Adaptive power capture control of variable-speed wind energy conversion systems with guaranteed transient and steady-state performance. IEEE Trans. Energ. Convers. 2013, 28, 716–725. [Google Scholar] [CrossRef]
- Chai, B.; Chen, J.; Yang, Z.; Zhang, Y. Demand Response Management with Multiple Utility Companies: A Two-Level Game Approach. IEEE Trans. Smart Grid 2014, 5, 722–731. [Google Scholar] [CrossRef]
- Meng, W.; Yang, Q.; Jagannathan, S.; Sun, Y. Adaptive neural control of high-order uncertain nonaffine systems: A transformation to affine systems approach. Automatica 2014, 50, 1473–1480. [Google Scholar] [CrossRef]
- Deng, R.; Yang, Z.; Chen, J.; Asr, N.; Chow, M. Residential Energy Consumption Scheduling: A Coupled-Constraint Game Approach. IEEE Trans. Smart Grid 2014, 5, 1340–1350. [Google Scholar] [CrossRef]
- Sandberg, H.; Teixeira, A.; Johansson, K.H. On security indices for state estimators in power networks. In Proceedings of the First Workshop on Secure Control Systems, CPSWEEK 2010, Stockholm, Sweden, 12–16 January 2010.
- Queiroz, C.; Mahmood, A.; Tari, Z. A Probabilistic Model to Predict the Survivability of SCADA Systems. IEEE Trans. Ind. Inform. 2013, 9, 1975–1985. [Google Scholar] [CrossRef]
- Hendrickx, J.; Johansson, K.H.; Jungers, R.; Sandberg, H.; Sou, K.C. Efficient Computations of a Security Index for False Data Attacks in Power Networks. IEEE Trans. Autom. Control 2014, 59, 3194–3208. [Google Scholar] [CrossRef]
- Xie, L.; Mo, Y.; Sinopoli, B. False data injection attacks in electricity markets. In Proceedings of the 2010 1st IEEE International Conference on Smart Grid Communications (SmartGridComm), Gaithersburg, MD, USA, 4–6 October 2010.
- Tan, R.; Badrinath Krishna, V.; Yau, D.K.; Kalbarczyk, Z. Impact of integrity attacks on real-time pricing in smart grids. In Proceedings of the ACM SIGSAC Conference on Computer & Communications Security, Berlin, Germany, 4–8 November 2013.
- Kosut, O.; Jia, L.; Thomas, R.; Tong, L. Malicious Data Attacks on Smart Grid State Estimation: Attack Strategies and Countermeasures. In Proceedings of the 2010 IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010.
- Liu, S.; Liu, X.P.; Saddik, A.E. Denial-of-Service (DoS) attacks on load frequency control in smart grids. In Proceedings of the IEEE PES Innovative Smart Grid Technologies (ISGT), Washington, DC, USA, 24–27 February 2013.
- Sou, K.C.; Sandberg, H.; Johansson, K.H. Data Attack Isolation in Power Networks Using Secure Voltage Magnitude Measurements. IEEE Trans. Smart Grid 2014, 5, 14–28. [Google Scholar] [CrossRef]
- Johansson, B. Security aspects of future renewable energy systems–A short overview. Energy 2013, 61, 598–605. [Google Scholar] [CrossRef]
- He, J.; Cheng, P.; Shi, L.; Chen, J. SATS: Secure Average-Consensus-based Time Synchronization in Wireless Sensor Networks. IEEE Trans. Signal Process. 2013, 61, 6387–6400. [Google Scholar] [CrossRef]
- He, J.; Chen, J.; Cheng, P.; Cao, X. Secured Time Synchronization in Wireless Sensor Networks: A Maximum Consensus Based Approach. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 1055–1065. [Google Scholar] [CrossRef]
- Zhao, C.; He, J.; Cheng, P.; Chen, J. Secure Consensus against Message Manipulation Attacks in Synchronous Networks. In Proceedings of the 19th IFAC World Congress, Cape Town International Convention Centre, Cape Town, South Africa, 24–29 August 2014.
- Zeng, W.; Chow, M.Y. Optimal Trade-off between Performance and Security in Networked Control Systems based on Coevolutionary Algorithms. IEEE Trans. Ind. Electron. 2012, 59, 3016–3025. [Google Scholar] [CrossRef]
- Zeng, W.; Chow, M.Y. Modeling and Optimizing the Performance-security Trade-off in D-NCS Using the Coevolutionary Paradigm. IEEE Trans. Ind. Inform. 2013, 9, 394–402. [Google Scholar] [CrossRef]
- Sundaram, S.; Hadjicostis, C.N. Distributed function calculation via linear iterative strategies in the presence of malicious agents. IEEE Trans. Autom. Control 2011, 56, 1495–1508. [Google Scholar] [CrossRef]
- Abu-Mahfouz, A.; Hancke, G.P. Distance Bounding: A Practical Security Solution for Real-Time Location Systems. IEEE Trans. Ind. Inform. 2013, 9, 16–27. [Google Scholar] [CrossRef]
- Wang, J.; Rossell, D.; Cassandras, C.G.; Paschalidis, I.C. Network Anomaly Detection: A Survey and Comparative Analysis of Stochastic and Deterministic Methods. In Proceedings of the IEEE Conference on Decision and Control, Firenze, Italy, 10–13 December 2013.
- Vollmer, T.; Manic, M. Cyber-Physical System Security with Deceptive Virtual Hosts for Industrial Control Networks. IEEE Trans. Ind. Inform. 2014, 10, 1337–1347. [Google Scholar] [CrossRef]
- Wu, J.; Jia, Q.; Johansson, K.; Shi, L. Event-based sensor data scheduling: Trade-off between communication rate and estimation quality. IEEE Trans. Autom. Control 2013, 58, 1041–1046. [Google Scholar] [CrossRef]
- Wu, J.; Yuan, Y.; Zhang, H.; Shi, L. How can online schedules improve communication and estimation tradeoff? IEEE Trans. Signal Process. 2013, 61, 1625–1631. [Google Scholar] [CrossRef]
- Shi, D.; Chen, T.; Shi, L. Event-triggered maximum likelihood state estimation. Automatica 2014, 50, 247–254. [Google Scholar] [CrossRef]
- Teixeira, A.; Amin, S.; Sandberg, H.; Johansson, K.H.; Sastry, S.S. Cyber security analysis of state estimators in electric power systems. In Preceedings of the IEEE Conference on Decision and Control, Atlanta, GA, USA, 15–17 December 2010.
- Mo, Y.; Hespanha, J.; Sinopoli, B. Robust detection in the presence of integrity attacks. In Proceedings of the American Control Conference, Montreal, QC, Canada, 27–29 June December 2012.
- Zhang, H.; Cheng, P.; Shi, L.; Chen, J. Optimal Denial-of-Service Attack Scheduling against Linear Quadratic Gaussian Control. In Proceedings of the American Control Conference (ACC), Portland, OR, USA, 4–6 June 2014.
- Zhang, H.; Cheng, P.; Shi, L.; Chen, J. Optimal DoS Attack Scheduling in Wireless Networked Control System. IEEE Trans. Control Syst. Technol. 2015. [Google Scholar] [CrossRef]
- Qi, Y.; Cheng, P.; Shi, L.; Chen, J. Event-based Attack Against Remote State Estimation. In Proceedings of the 2015 54th IEEE Conference on Decision and Control (CDC), Osaka, Japan, 15–18 December 2015.
- Cardenas, A.; Amin, S.; Sastry, S. Secure control: Towards survivable cyber-physical systems. In Proceedings of the International Conference on Distributed Computing Systems Workshops, Beijing, China, 17–20 June 2008.
- Yuan, Y.; Zhu, Q.; Sun, F.; Wang, Q.; Basar, T. Resilient control of cyber-physical systems against Denial-of-Service attacks. In Proceedings of the International Symposium on Resilient Control Systems (ISRCS), San Francisco, CA, USA, 13–15 August 2013.
- Pasqualettia, F.; Bulloc, F. A Divide-and-Conquer Approach to Distributed Attack Identification. In Proceedings of the 54th IEEE Conference on Decision and Control (CDC), Osaka, Japan, 15–18 December 2015.
- Cetinkaya, A.; Ishii, H.; Hayakawa, T. Event-Triggered Control over Unreliable Networks Subject to Jamming Attacks. In Proceedings of the 5th IFAC Workshop on Distributed Estimation and Control in Networked Systems NecSys 2015, Philadelphia, PA, USA, 10–11 September 2015.
- Gupta, A.; Langbort, C.; Başar, T. Optimal control in the presence of an intelligent jammer with limited actions. In Proceedings of the IEEE Conference on Decision and Control, Atlanta, GA, USA, 15–17 December 2010.
- Li, H.; Lai, L.; Qiu, R.C. A denial-of-service jamming game for remote state monitoring in smart grid. In Proceedings of the Annual Conference on Information Sciences and Systems (CISS), Baltimore, MD, USA, 23–25 March 2011.
- Gupta, A.; Nayyar, A.; Langbort, C.; Basar, T. A dynamic transmitter-jammer game with asymmetric information. In Proceedings of the IEEE Conference on Decision and Control, Maui, HI, USA, 10–13 December 2012; pp. 6477–6482.
- Langbort, C.; Ugrinovskii, V. One-shot control over an AVC-like adversarial channel. In Proceedings of the American Control Conference, Montreal, QC, USA, 27–29 June 2012.
- Li, Y.; Shi, L.; Cheng, P.; Chen, J.; Quevedo, D.E. Jamming Attack on Cyber-Physical Systems: A Game-Theoretic Approach. In Proceedings of the 2013 IEEE 3rd Annual International Conference on Control and Intelligent Systems (CYBER), Nanjing, China, 26–29 May 2013.
- Li, Y.; Shi, L.; Cheng, P.; Chen, J.; Quevedo, D.E. Jamming Attacks on Remote State Estimation in Cyber-Physical Systems: A Game-Theoretic Approach. IEEE Trans. Autom. Control 2015, 60, 2831–2836. [Google Scholar] [CrossRef]
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Leung-Yan-Cheong, S.; Hellman, M.E. The Gaussian wire-tap channel. IEEE Trans. Inform. Theory 1978, 24, 451–456. [Google Scholar] [CrossRef]
- Goel, S.; Negi, R. Guaranteeing secrecy using artificial noise. IEEE Trans. Wirel. Commun. 2008, 7, 2180–2189. [Google Scholar] [CrossRef]
- Manitara, N.E.; Hadjicostis, C.N. Privacy-preserving Asymptotic Average Consensus. In Proceedings of the European Control Conference, Zurich, Switzerland, 17–19 July 2013.
- Mo, Y.; Murray, R. Privacy Preserving Average Consensus. In Proceedings of the IEEE 53st Annual Conference on Decision and Control (submitted), Los Angeles, CA, USA, 15–17 December 2014; pp. 2154–2159.
- Akyol, E.; Langbort, C.; Basar, T. Privacy constrained information processing. In Proceedings of 54th IEEE Conference on Decision and Control (CDC), Osaka, Japan, 15–18 December 2015.
- Zhang, Z.; Zhang, H.; He, S.; Cheng, P. Achieving Bilateral Utility Maximization and Location Privacy Preservation in Database-Driven Cognitive Radio Networks. In Proceedings of the IEEE International Conference on Mobile Ad Hoc and Sensor Systems, Dallas, TX, USA, 19–22 October 2015.
- Ny, J.L. On Differentially Private Filtering for Event Streams. In Proceedings of the IEEE Conference on Decision and Control, Firenze, Italy, 10–13 December 2013.
- Huang, Z.; Mitra, S.; Dullerud, G. Differentially Private Iterative Synchronous Consensus. In Proceedings of the ACM Workshop on Privacy in the Electronic Society, Raleigh, NC, USA, 16–18 October 2012.
- Li, Q.; Cao, G.; La Porta, T.F. Efficient and Privacy-Aware Data Aggregation in Mobile Sensing. IEEE Trans. Depend. Secure Comput. 2013, 11, 115–129. [Google Scholar] [CrossRef]
- He, X.; Machanavajjhala, A.; Ding, B. Blowfish privacy: Tuning privacy-utility trade-offs using policies. In Proceedings of the ACM SIGMOD, Snowbird, UT, USA, 22–27 June 2014.
- Fan, C.I.; Huang, S.Y.; Lai, Y.L. Privacy-Enhanced Data Aggregation Scheme against Internal Attackers in Smart Grid. IEEE Trans. Ind. Inform. 2014, 10, 666–675. [Google Scholar] [CrossRef]
- Jia, L.; Radke, R.J. Using Time-of-Flight Measurements for Privacy-Preserving Tracking in a Smart Room. IEEE Trans. Ind. Inform. 2014, 10, 689–696. [Google Scholar] [CrossRef]
- Le Ny, J.; Pappas, G.J. Differentially Private Filtering. IEEE Trans. Autom. Control 2014, 59, 341–354. [Google Scholar] [CrossRef]
- Zhang, H.; Shu, Y.; Cheng, P.; Chen, J. Privacy and Performance Trade-off in Cyber-Physical Systems. IEEE Netw. 2016, 30, 62–66. [Google Scholar] [CrossRef]
- Ny, J.L. Privacy-Preserving Nonlinear Observer Design Using Contraction Analysis. Available online: http://120.52.73.77/arxiv.org/pdf/1507.02250.pdf (accessed on 8 July 2015).
- Metke, A.; Ekl, R. Security Technology for Smart Grid Networks. IEEE Trans. Smart Grid 2010, 1, 99–107. [Google Scholar] [CrossRef]
- Tan, O.; Gunduz, D.; Poor, H.V. Increasing smart meter privacy through energy harvesting and storage devices. IEEE J. Sel. Areas Commun. 2013, 31, 1331–1341. [Google Scholar] [CrossRef]
- Liu, E.; You, P.; Cheng, P. Optimal privacy-preserving load scheduling in smart grid. In Proceedings of IEEE PES General Meeting, Boston, MA, USA, 17–21 July 2016.
- Sandberg, H.; Dán, G.; Thobaben, R. Differentially Private State Estimation in Distribution Networks with Smart Meters. Available online: http://120.52.73.77/arxiv.org/pdf/1503.08490v1.pdf (accessed on 29 March 2015).


© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, L.; Zhang, H. A Survey on Security and Privacy in Emerging Sensor Networks: From Viewpoint of Close-Loop. Sensors 2016, 16, 443. https://doi.org/10.3390/s16040443
Zhang L, Zhang H. A Survey on Security and Privacy in Emerging Sensor Networks: From Viewpoint of Close-Loop. Sensors. 2016; 16(4):443. https://doi.org/10.3390/s16040443
Chicago/Turabian StyleZhang, Lifu, and Heng Zhang. 2016. "A Survey on Security and Privacy in Emerging Sensor Networks: From Viewpoint of Close-Loop" Sensors 16, no. 4: 443. https://doi.org/10.3390/s16040443





