1. Introduction
Network capacity is one of the key factors of wireless networks. The first study of network capacity is carried out by Gupta and Kumar in [
1]. They investigated the throughput capacity of a wireless network where
n nodes are randomly distributed, and find that the per-node throughput capacity is
, where
W is the highest transmission rate of each node. Their finding implies that as the size of the network goes to infinity, the per-node throughput will decrease to zero. Following this work, extensive studies have been conducted to achieve a tighter capacity bound [
2,
3,
4,
5,
6,
7,
8,
9,
10,
11,
12,
13,
14,
15].
Some researchers propose to add some base stations to help with long distance transmissions in networks, which are called “hybrid networks” [
16,
17,
18,
19,
20,
21]. Compared with pure
ad hoc networks, the base stations are neither sources nor destinations, they work only as relay nodes. Liu
et al. [
16] studied the capacity of networks where the base stations are regularly placed and the distribution of normal nodes is independent and identically distributed (i.i.d.). They obtain the asymptotic expressions on aggregate throughput capacity and maximize the capacity under different channel allocation schemes. Kozat
et al. [
17] investigated the capacity bound of the networks where base stations and nodes are both randomly deployed. They prove that the per-node throughput is
when the number of nodes and the number of base stations have the same order. Zemlianov
et al. [
18] considered the case that the nodes are randomly distributed and the base stations are arbitrarily placed. They proved that the network capacity depends on the number of base stations. Zhang
et al. [
19] proposed a network model where delay constraint is considered and each node is equipped with directional antennas. They also analyzed how the number of base stations and the beamwidth of directional antennas affect the network capacity.
There are also some papers focusing on guaranteeing the QoS of some special scenarios over hybrid wireless networks [
22,
23,
24]. The distortion-aware concurrent multipath transfer (CMT-DA) solution, delay stringent coded transmission (ASCOT) and goodput-aware load distribution (GALTON) are proposed in these papers. By evaluating the performance through experiments, the authors prove that the proposed models outperform existing transmission schemes.
A large volume of literature proves that adding base stations is an efficient way to improve the network capacity. However, this has some disadvantages. First, to improve the throughput capacity significantly, a large number of base stations should be set up, which is very expensive. Second, it takes a lot of time to establish such a wired network. Third, in some practical cases such as battlefields and rescue tasks, there is little time to set up base stations.
Therefore, compared with establishing base stations, deploying some powerful helping nodes is an easy and efficient way to improve the network capacity. Networks which consist of normal nodes and helping nodes are called “heterogeneous networks”. Though there are plenty of research studies on heterogeneous networks [
25,
26,
27,
28,
29], most of them focus on routing protocol design [
22,
23] and MAC protocol design [
27,
28], instead of network capacity. One study focused on network capacity [
29] investigated the capacity of two types of networks: regular heterogeneous networks and random heterogeneous networks.
In the literature mentioned above, the nodes are usually assumed to be stable. Some researchers focus on the networks where the nodes are mobile. Grossglauser and Tse for the first time introduced mobility to networks [
30]. They proved that the network capacity reaches Θ(
W) in mobile networks, while the transmission delay will go to infinity in their network model. Inspired by this work, many researchers have engaged in the study of the capacity of mobile networks [
30,
31,
32,
33,
34,
35,
36,
37,
38,
39,
40]. Of all the mobility models, the i.i.d. model is the simplest and the most commonly used one. Neely
et al. [
31] analyzed the delay-throughput tradeoff of i.i.d. mobility networks. They prove that the throughput capacity is
, where
n is the number of nodes and
D is the transmission delay. The mobile network in [
31] is substantially a fast mobility model. In this model, the data transmissions and the node mobility are assumed to be on the same time scale. Hence there exists only one-hop transmission in a time slot. In [
32], Toumpis and Goldsmith considered the case that the node mobility is much slower than the data transmissions. In their network model, in single time slot, packets can be delivered by multi-hop transmissions. They show that the delay-throughput tradeoff is
in their i.i.d. slow mobility network model. Other researchers have also contributed a lot to the studies on the capacity of i.i.d. mobility networks.
The random walk model is also an important mobility model. Grammal
et al. [
33] first introduced the random walk model. Later on, the throughput capacities of per source-destination pair in fast mobility networks [
34] and slow mobility networks were investigated [
35]. Besides i.i.d. mobility model and random walk model, other mobility models such as Brownian model and hybrid random walk model are also well studies [
36,
37].
However, most of the literature above focuses on the two-dimensional mobility model or one-dimensional mobility model. In fact, as wireless technologies are rapidly developing, wireless networks are extending from two-dimensional to three-dimensional space. Moreover, in many scenarios, the network can be better modeled by a three-dimensional space instead of a two-dimensional space. For instance, in modern battlefields, a large amount of wireless networks are emerging which consist of lots of military units such as fleets, troops and aircrafts. Hence, we can foresee that studies on three-dimensional networks will be of great significance.
In previous studies, only a few researchers studied the capacity problems in three-dimensional networks [
41,
42,
43]. The three-dimensional arbitrary network model and three-dimensional random network model are, for the first time, proposed in [
41]. The authors calculated the transport capacity and throughput capacity of the two types of models, respectively. Li
et al. [
42] proposed a three-dimensional network model where the distributions of nodes are inhomogeneous. They obtained the asymptotic expressions on the throughput capacity of their model. Cai
et al. [
43] considered the three-dimensional networks with UWB technologies. They also obtained the throughput capacity.
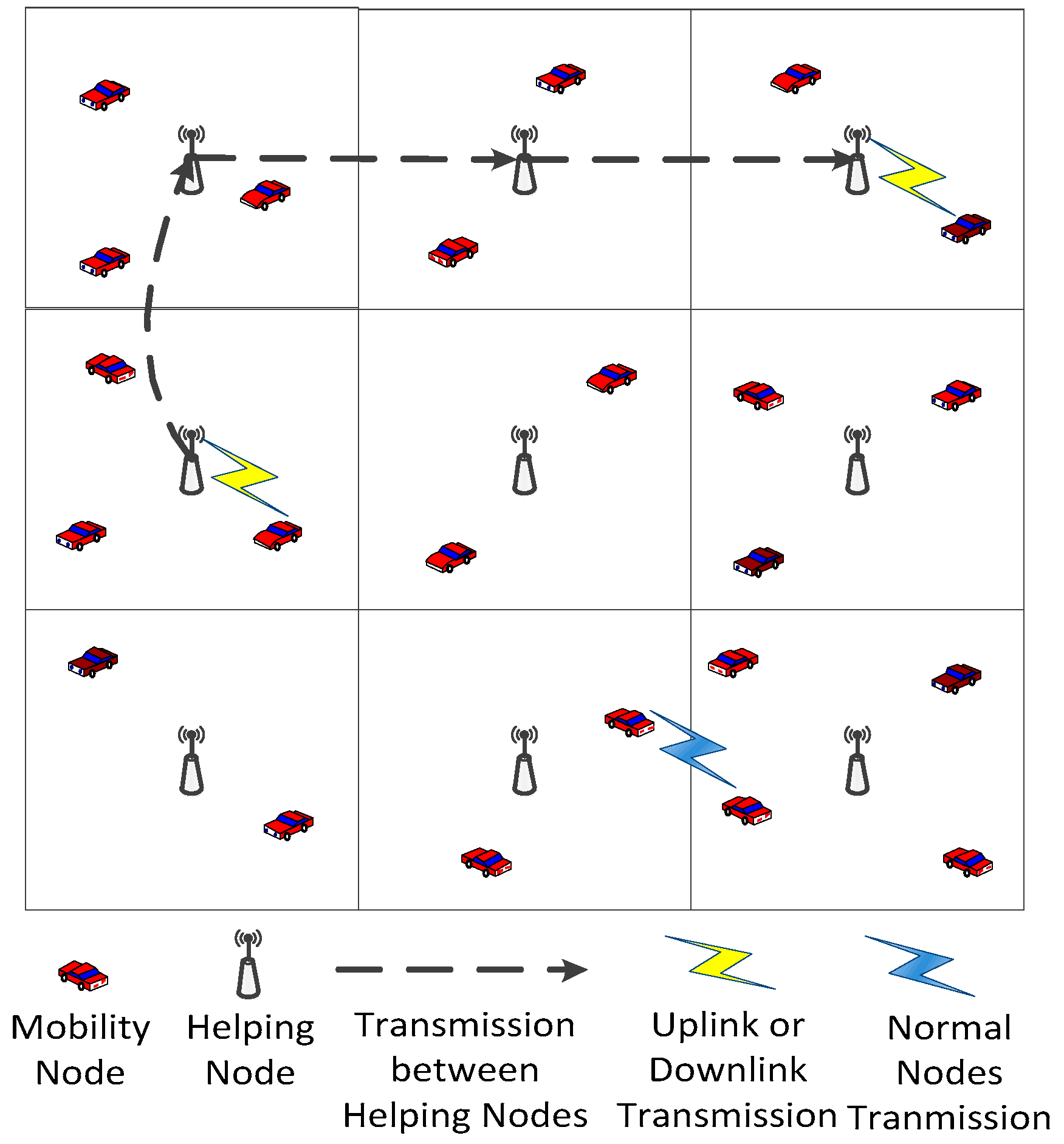
In this paper, we consider heterogeneous networks with
n normal nodes and
m helping nodes. In our network model, the helping nodes are more powerful than the normal nodes and just work in routing and relaying. They are neither the source nodes nor the destination nodes. Moreover, we adopt the delay constraint
D in our routing strategy. Concretely, if the source can send the packets to its destination within a time slot
D, the packets will be transmitted in multi-hop fashion, which is also called
ad hoc transmission mode. If the transmission delay exceeds
D time slots, the packets will be delivered to the destination with the help of helping nodes, which is called helping transmission mode. We adopt the i.i.d. mobility model in this paper. Moreover, we consider two time scales: fast mobility and slow mobility. Besides, we also consider two cases, where all the nodes are distributed in two-dimensional space and where all of them are distributed in three-dimensional space. We first give an intuitive analysis under virtual channel systems. Then the asymptotic expressions are obtained by strict proof. Based on the expressions, we consider the impact of
m and
D to the per-node throughput capacity and have some interesting findings. Our main contributions can be summarized as follows:
- (1)
We propose a new heterogeneous mobile network model, which consists of n mobile normal nodes and m stable helping nodes. The helping nodes are more powerful and they only work in routing and relaying data. Compared with the traditional hybrid network model, setting up such a backbone with helping nodes saves a lot of time and money.
- (2)
According to the time scales and space dimensions, we consider four types of network model: two-dimensional i.i.d. fast mobility model, two-dimensional i.i.d. slow mobility model, three-dimensional i.i.d. fast mobility model and three-dimensional i.i.d. slow mobility model. We derive the capacities of the four types of mobility by both intuitive analysis and strict mathematical proof.
- (3)
We analyze the asymptotic expressions on the network capacity. We find that the number of helping nodes can affect the throughput capacity significantly. The network capacity can achieve constant order if the number of helping nodes is large enough, and in this case the time delay can be ensured. We also conclude that the delay constraint D affects the throughput capacity. If D is not limited, the throughput can also stay constant order, while the time delay can not be ensured.
5. Intuitive Analysis
In [
38], the authors proposed the virtual channel model. We adopt this idea to have some heuristic arguments on
ad hoc transmission mode. A virtual channel is a logic representation of a packet transmission from source node to destination node. According to the virtual channel model, there are two main constraints on the network capacity:
- (1)
Interference: In the process of packet transmissions, the near nodes interfere with each other, which limit the throughput capacity.
- (2)
Mobility: Since source nodes, destination nodes and relay nodes are mobile all the time, the packets are not ensured to reach their destination nodes before the delay deadline.
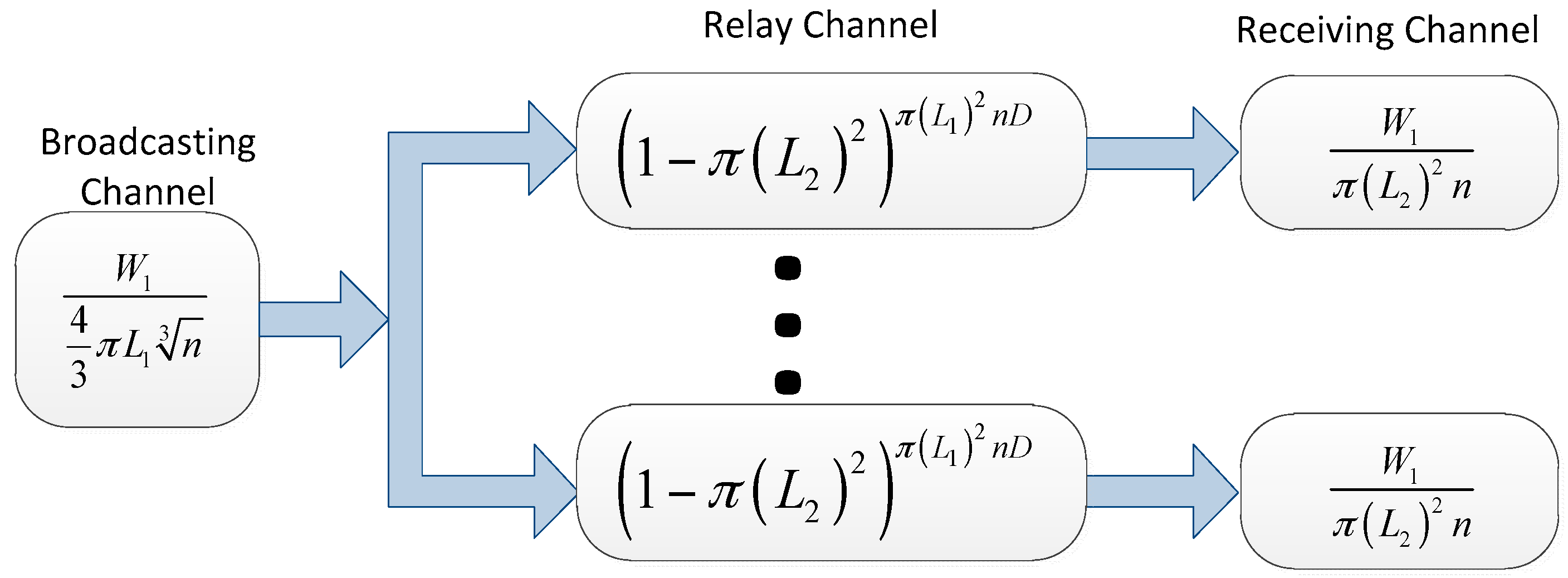
In a virtual channel mode, a packet is assumed to be transmitted from its source node to its destination node by a two-hop transmission. First, it is delivered from the source node to the relay node around the source. Then, it is delivered from the relay node to the destination node. Hence, in
ad hoc transmission mode, for a successful packet delivery, we consider three virtual channels, as shown in
Figure 4:
Reliable Broadcasting Channel: The source nodes transmit the packets to the relay nodes around it by broadcasting channel;
Unreliable Relay Channel: The relay nodes move to the neighborhood of the destination;
Reliable Receiving Channel: The relay nodes deliver the packets to the destination nodes.
All the packets delivered to the destinations by ad hoc transmission mode are via the three virtual channels. Using the virtual channel model, we present the intuitions on the capacity of our network model.
First the two-dimensional i.i.d. fast mobility model is considered:
Reliable Broadcasting Channel: Let
L1 denote the transmission radius of source node. Hence, the source can cover an area of
π(
L1)
2. For simplicity, we omit the guard zone Δ. Hence, there are at most
transmitting pairs in the network in a time slot. On average, every source node has
P1 fraction of time to broadcast, where:
Therefore, for reliable broadcast channel, its throughput is:
There exist π(L1)2 n mobile nodes in a disk with radius L on average. Hence, each broadcast can transmit packets π(L1)2 n nodes as duplicate copies.
Unreliable Relay Channel: We assume that the transmission radius for relay nodes is
L2. Since the nodes are distributed in a square of unit area, we assume that
L2 is far less than 1. For a duplicated packet, the probability that it fail to reach the destination node within
D time slots is:
As what analyzed above, a sent packet is delivered to
relay node on average. Hence there are
duplicate copies. Therefore, within
D time slots, the probability that there are no packets fallen into the area covered by its destination node is:
Reliable Receiving Channel: Now we consider the packets delivered from relay nodes to destination nodes. Since
L2 is a common transmission radius which all the relay nodes use, the number of transmitting relay-destination pairs in a time slot is no more than
. As the highest transmission rate is
W1 for relay nodes, the per-node reliable receiving channel can be expressed by
As shown in
Figure 5, for a source-destination pair in the virtual channel model, the maximum throughput is:
Next we consider the two-dimensional i.i.d. networks with slow mobility. In virtual channel systems, the relay channel and the receiving channel are the same with the analysis above. Hence we only need to consider the broadcasting channel. For each broadcasting channel, the throughput capacity is:
Hence, the virtual channel systems are as shown in
Figure 6:
We can conclude that for a source-destination pair, the maximum throughput is:
Now we consider the three-dimensional i.i.d. fast mobility networks. Different from the analysis above, all the nodes are distributed in a three-dimensional space in this network model. Hence, the broadcasting channel is:
The probability that there are no packets fallen into the area covered by its destination node within
D time slots is:
The receiving channel is:
Figure 7 shows the virtual channel model for three-dimensional i.i.d. fast mobility networks, and the throughput capacity is:
Next we turn to the three-dimensional i.i.d. slow mobility network model. The relay channel and the receiving channel have been obtained in the analysis of three-dimensional fast mobility networks. As described in [
38], the broadcasting channel in three-dimensional slow mobility can be expressed by:
As shown in
Figure 8, we can obtain the throughput capacity:
6. Capacity of Heterogeneous Mobile Wireless Networks
In this section we calculate the capacity of the four types of mobile network model, respectively. First we derive the capacity contributed by ad hoc transmission mode. Then we consider the capacity contributed by helping transmission mode. To obtain the throughput contributed by ad hoc transmission mode, we first assume that relaying is not allowed in the networks and calculate the number of packets delivered directly from the source to the destination. On this basis, we derive the number of packets delivered with the help of relay nodes. Summing up the two results, we can get the total number of packets carried by ad hoc transmission mode. To obtain the throughput capacity contributed by helping transmission mode, we should consider the network capacity of the backbone network, which has regular topology architecture.
6.1. Capacity of Two-Dimensional i.i.d. Fast Mobility Networks
We will first present some important inequalities firstly, which are shown in the following theorem:
Theorem 1. In two-dimensional mobile networks, we have the following inequalities: Proof. For one node, the largest number of bits it can deliver in one time slot is W1 bits. Therefore, in T time slots, all the nodes in the network can take at most nW1T bits, which are necessarily larger than the packets successfully transmitted to the destination nodes from source nodes, as shown in inequality Equation (1). It is also larger than the number of bits which are stored at relay nodes. Hence we have equality Equation (2). □
Now we investigate the throughput capacity contributed by
ad hoc transmission mode. First we will analyze the number of bits directly transmitted to the source nodes without relaying in
T time slots, which is denoted by Λ
d[
T]. We have the following theorem:
Theorem 2. In two-dimensional i.i.d fast mobility model, without considering relaying progress, we can bound the number of bits directly delivered to destination nodes as: Proof. Consider inequality Equation (3), according to the Cauchy-Schwarz inequality, we have:
which can be expressed by:
The inequality above gives a bound on the expected distance which the bits take. For two arbitrary nodes
Xi and
Xj, let
dist(
Xi,
Xj)(
t) denote their distance in time slot
t. Based on the assumption that the mobility model are i.i.d, we have:
In
T time slots, we have:
The network can carry at most
W1 bits in single time slot, hence we can obtain:
According to the inequalities above, we have:
By Jensen’s inequality, combining inequality Equation (4) and inequality Equation (5), we can obtain the following inequality:
where Jensen’s inequality is used in the first inequality.
Let
, we obtain:
Simplify the inequality above, we can obtain E[Λd[T]]. □
Theorem 2 has given number of bits directly delivered to destination nodes. Now we consider the scenario where packets can be relayed in the networks.
Theorem 3. In two-dimensional i.i.d fast mobility model, if packet relaying exists, the bound on the number of bits transmitted to the destination number through relay nodes is:
where
D is delay constant.
Proof. In
T time slots, let Λ
r[
T] denote the number of bits which are transmitted from relay nodes to destination nodes in
T time slots, we have Λ[
T] = Λ
r[
T] + Λ
d[
T]. According to Cauchy-Schwarz inequality and inequality Equation (3), we obtain:
where Cauchy-Schwarz inequality is used in the first inequality. Hence we have:
Consider bit
B, let
dB denote its destination node and
eB denote the node storing bit
B. We assume that from time slot
tB to time slot
tB +
D − 1, the minimum distance between
dB and
eB is
LB. Then we have:
For an arbitrary bit
B which is in the set
R[
T], we have:
According to Taylor’s formula, equality Equation (14) can be expressed as:
Combining Equations (7) and (8), we have:
Hence, we can obtain the following inequalities:
According to Jensen's inequality, combining inequality Equation (6) and inequality Equation (9), we have:
where Jensen’s inequality is used in the first inequality.
Let
, we can have
E[Λ
r[
T]]. □
Theorem 4. In two-dimensional i.i.d. fast mobility networks, the ad hoc transmission mode capacity is: Proof. Combining Theorems 2 and 3, we have:
In the meaning of order, the throughput capacity contributed by relaying nodes plays a dominating role compared with the throughput without relaying node. Thus, we have . □
Now we consider the capacity contributed by the helping nodes. In two-dimensional network model, the helping nodes are regularly placed and divide the area into
equal-size squares. In the transmissions of helping nodes, there are three phases: uplink phase, downlink phase and HN-to-HN phase. In uplink phase, the source nodes deliver the packets to the nearest helping nodes. In this case we call the helping nodes 'sources'. Then, the helping nodes transmit the packets to the helping nodes that are in the same cells with the destination nodes. In this case we call the helping nodes 'destinations'. Finally, the helping nodes deliver the packets to the destination nodes by broadcasting. Theorem 5 gives the capacity contributed by the backbone network which consists of helping nodes.
Theorem 5. In two-dimensional networks, the per-node throughput helping transmission mode contributes is: Proof. Since the node distribution is i.i.d., each helping node is chosen as a source or a destination with the same probability. We randomly choose the helping node on (
p,
q) as the source and the helping node on (
i,
j) as the destination. In our network model, two neighbor helping nodes can communicate directly, hence the minimum number of hops is
h = |
p −
i| + |
j −
q|. Summing up all the possible
h, we have:
E[|
p −
i|] can be obtained by the following equation:
We can get
E[
p2] by the following equation:
Since
p is uniformly distributed in the interval
, we obtain:
Substituting Equations (11) and (12) into Equation (10), we have:
Since the bandwidth of uplink sub-channel is
W2, for each helping node, it can carry at most
W2 bits in each time slot. Thus, we have:
where
λH is the per-node throughput capacity of backbone helping node.
For an arbitrary helping node
Yi, its interference region is a circle with radius (1 + Δ
H)
rH. Each helping node occupies a region of
in the unit area, hence the number of helping nodes interfered by
Yi is:
Hence the number of nodes interfered by
Yi is bounded by
c8 =
c7 − 1. It implies that there exists a temporal and spatial scheduling strategy that every helping node can obtain at least one slot to communicate in every (1 +
c8) slots. Therefore, we have:
Combining Equations (14) and (15), we can obtain the per-node throughput capacity of backbone:
□
Since the total throughput capacity is contributed by multi-hop mode and helping mode, we have
λ(
n,
m) =
λA(
n) +
λH(
m). According to Theorems 4 and 5, we can obtain Theorem 6 as follows:
Theorem 6. In two-dimensional i.i.d. fast mobility networks, under protocol model, the network capacity is: Proof. Combining Theorems 4 and 5, we can prove the theorem above. □
6.2. Capacity of Two-Dimensional i.i.d. Slow Mobility Networks
Similar to the fast mobility model, we can calculate the throughput capacity of slow mobility model. First we present some important inequalities, as shown in Theorem 7:
Theorem 7. In two-dimensional i.i.d. slow mobility networks, we have the following inequalities: Proof. Similarly with the proof of Theorem 1, we can prove the theorem above. □
First we consider the case that all the packets are directly transmitted to the destination nodes without relaying.
Theorem 8. In two-dimensional i.i.d. slow mobility networks, if relaying progress is not allowed, the number of bits directly delivered to destination nodes is bounded as follows: Proof. According to Theorem 1 and the Cauchy-Schwarz inequality, we have:
where the Cauchy-Schwarz inequality is used in the first inequality.
Since
, we have that:
Similar to the analysis in Theorem 2, the following inequality can be obtained:
Combining inequality Equation (18) and inequality Equation (19), we have:
Let
, we can conclude that:
Simplify the inequality above, we can obtain Theorem 8. □
Theorem 9. In two-dimensional i.i.d. slow mobility network model, if packet relaying is allowed, the bound on the number of bits which are transmitted successfully from relay nodes to destination nodes is as follows: Proof. Similar to the steps in capacity analysis of network capacity of two-dimensional i.i.d. fast mobility networks, we have:
Therefore, we can obtain the following inequalities:
Combining inequality Equation (18) and inequality Equation (20), we have:
Let
, we have Theorem 9. □
Theorem 10. In two-dimensional i.i.d. slow mobility networks, the throughput capacity contributed by ad hoc transmission mode is: Proof. Combining Theorems 9 and 10, we have:
Inequality Equation (21) then follows the proof of Theorem 4. □
Theorem 5 has given the throughput capacity contributed by backbone networks. Combining the results of Theorems 5 and 10, we can obtain the network capacity of two-dimensional i.i.d. slow mobility networks:
Theorem 11. In two-dimensional i.i.d. slow mobility networks, under protocol model, the capacity is: Proof. Combining Theorems 5 and 10, we can prove the theorem above. □
6.3. Capacity of Three-Dimensional i.i.d. Fast Mobility Networks
Inequality Equation (1) and inequality Equation (2) which hold in two-dimensional networks are also suitable for three-dimensional networks. However, in three-dimensional i.i.d fast mobility model, we should modify inequality Equation (3) to analyze the network capacity of the networks.
Theorem 12. In three-dimensional i.i.d fast mobility model, we have: Proof. The proof progress is similar with Theorem 1. □
Theorem 13. In three-dimensional i.i.d fast mobility model, we can obtain that the bounds on the number of bits directly delivered to destination nodes by ad hoc transmission mode: Proof. According to the Cauchy-Schwarz inequality, we can obtain the following inequality:
which implies:
Since the node distribution is i.i.d in a three-dimensional space, according to the knowledge of Probability Theory, we have that:
According to the inequality above, we conclude that:
In single time slot, each node can carry at most
W1 bits. Hence we have:
Taking expectation on the inequality above, we have:
Combining inequality Equation (23) and inequality Equation (24), we have:
where Jensen’s inequality is used in the first inequality.
Let
, we have:
Then Theorem 14 can be proved by simplifying the inequality above. □
Next we study the throughput contributed by
ad hoc mode considering relaying progress.
Theorem 14. In three-dimensional i.i.d fast mobility networks, if relaying exists, we can obtain the bound on the number of bits successfully delivered to the destination nodes through relay nodes as follows:
where
D is the delay constant.
Proof. According to the Cauchy-Schwarz inequality and inequality Equation (48), we have the following inequalities:
which can be expressed by:
Consider bit
B, in time [
tB,
D +
tB − 1], let
denote the minimum distance between its relay node
eB and destination node
dB,
i.e.:
Since the node distribution is i.i.d in each time slot, we have:
Using the Taylor formula, we can obtain the following inequality:
Then we can get the bound on the expectation of the number of bits which satisfy
:
Since
, we have:
Combining inequality Equation (25) and inequality Equation (26), we can obtain the following inequalities:
where Jensen’s inequality is used in the first inequality.
Let , we can prove Theorem 14. □
Combining Theorems 13 and 14, we can obtain the capacity contributed by
ad hoc transmission mode:
Theorem 15. In three-dimensional i.i.d. fast mobility networks, the ad hoc transmission mode capacity is: Proof. Based on Theorems 13 and 14, we have the total number of bits transmitted by
ad hoc transmission mode as follows:
According to the definition of order, we can obtain the capacity contributed by
ad hoc transmission mode:
Now we study the throughput capacity contributed by the helping nodes, which can be obtained by the following theorem:
Theorem 16. In three-dimensional networks, the per-node throughput capacity contributed by the backbone network is: Proof. In three-dimensional backbone network, we randomly choose the helping node on (p, q, u) and the helping node on (i, j, v) as source and destination respectively. Hence we have that the expectation of the hops is E[h] = 3E[E[|p − i|]].
The rest of the proof is similar to the analysis of Theorem 5. □
Theorem 17. In three-dimensional i.i.d. fast mobility networks, under the protocol model, the capacity can be expressed by: Proof. Combining Theorems 15 and 16, we can prove the theorem above. □
6.4. Capacity of Three-Dimensional i.i.d. Slow Mobility Networks
Now we consider the three-dimensional i.i.d. slow mobility networks. Similar to the method used in network capacity analysis of two-dimensional i.i.d. slow mobility networks, we first calculate the bounds on the number of bits which are directly transmitted from source nodes to destination nodes without packet relaying. Furthermore, we analyze the number of bits which are delivered successfully from relay nodes to destination nodes.
Theorem 18. In three-dimensional i.i.d. slow mobility networks, without packet relaying, the number of bits which are transmitted directly from source nodes to destination nodes satisfies: Proof. Inequality Equation (16) in Theorem 7 is suitable for the three-dimensional i.i.d. slow mobility network. Besides, we have the following inequality which will be used in the following analysis:
Hence, we have:
where the Cauchy-Schwarz inequality is used in the first inequality.
As
, we obtain:
Similar to the steps in Theorem 8, we have:
Therefore, we can conclude that:
Let
, we have Theorem 18. □
Theorem 19. In three-dimensional i.i.d. slow mobility networks, if packet relaying is allowed, we have the following inequality: Proof. Similar to the proof process, we have:
Hence, we have the following inequalities:
Based on the argument of Theorem 1, we have:
Let
, we have:
Theorem 20. In three-dimensional i.i.d. slow mobility networks, the capacity contributed by ad hoc transmission mode is: Proof. Similar to the proof of Theorem 4, we have:
Hence we have . □
Theorem 16 implies that in three-dimensional networks, the capacity contributed by helping transmission mode is
, hence we can obtain the throughput capacity of the whole networks:
Theorem 21. In three-dimensional i.i.d slow mobility networks, under the protocol model, the capacity is: Proof. Combining Theorems 16 and 20, we can prove the theorem above. □
We have obtained the capacities of the four types of heterogeneous mobile networks in this section. By analyzing these capacity expressions, we will get some interesting conclusions. The analysis is presented in the following section.
7. Capacity Analysis
In the Section above we have obtained the throughput capacity of the four types of mobile networks. In this section we analyze the impact of some important parameters such as
n,
D and
m to the network capacity. Firstly we list the capacity contributed by
ad hoc transmission mode as follows: in two-dimensional i.i.d. fast mobility model, we have
; in two-dimensional i.i.d. slow mobility model, we have
; in three-dimensional i.i.d. fast mobility model, we have
; and in three-dimensional i.i.d. slow mobility model, we have
.
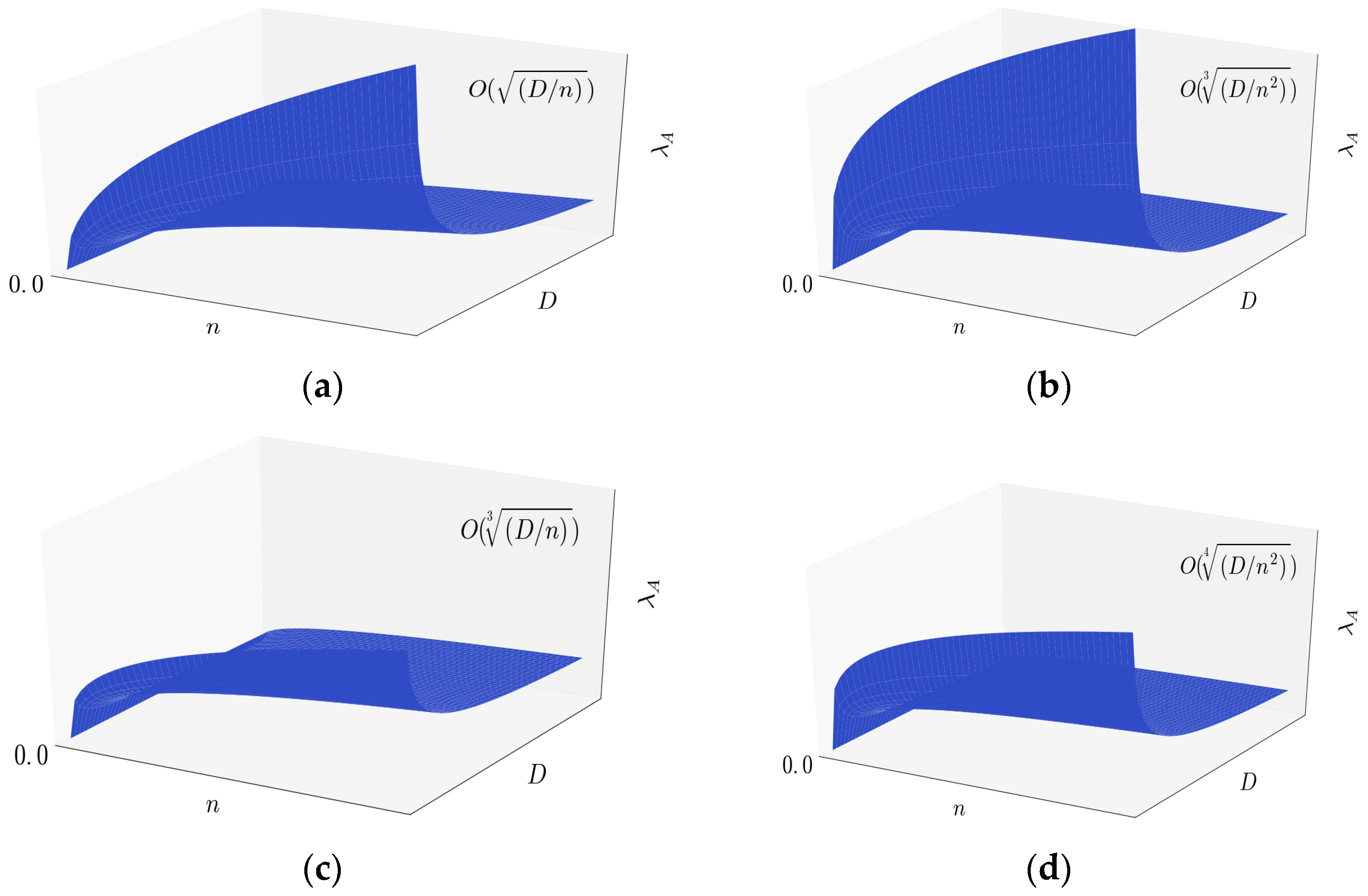
Figure 9 shows
λA(
n) of the four types of networks.
The relationship of
λA(
n) and
n is shown in
Figure 10. We find that fast mobility networks have much higher capacity than the slow mobility networks, especially in the case that the number of mobile nodes is small. The reason is that in fast mobility networks, the source nodes have more opportunities to communicate with the destination nodes directly. If the number of mobile nodes is small, the fast mobility is one of the most important factors which influence the network capacity. As
n goes to infinity, the number of mobile nodes offers many opportunities for source nodes to meet destination nodes, even in slow mobility networks. Hence, if the number of mobile nodes is large enough, the capacities of the four types of networks are similar.
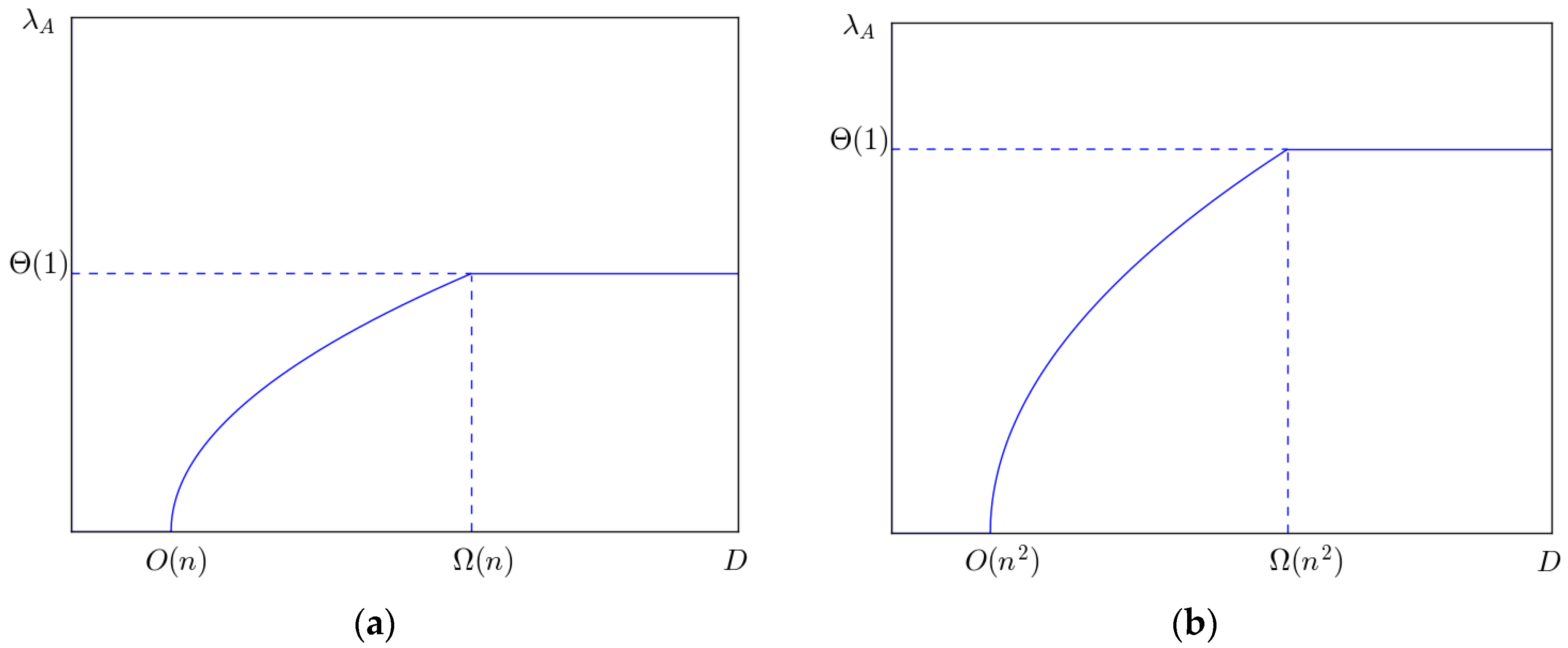
Let D = Ω(n2), we have λA = Θ(1). In this case, the four types of mobile networks have the same capacity, which is Θ(1). It means that in delay tolerant networks, the network capacity can achieve constant order, and the price is that the delay will go to infinity. Of course, the delay constraint D is approximated in the analysis above. Concretely, in two-dimensional mobile network model, D = Ω(n); in three-dimensional mobile network model, D = Ω(n2). However, since n is assumed to be large enough, D is not limited in both the two cases.
Let
D =
O(
n), we have
λA = 0. In this case, the capacity will decrease to zero as
n goes to infinity. Concretely, in two-dimensional mobile network model,
D =
O(
n); in three-dimensional network model,
D =
O(
n2). It implies that if the delay is assumed to be very small, the number of bits transmitted by
ad hoc transmission mode is very little. Our analysis is shown in
Figure 11.
When
D falls in between
O(
n) and Ω(
n), there is a positive correlation between
λA and the delay constraint. Theorems 5 and 16 offer the throughput capacity of backbone networks.
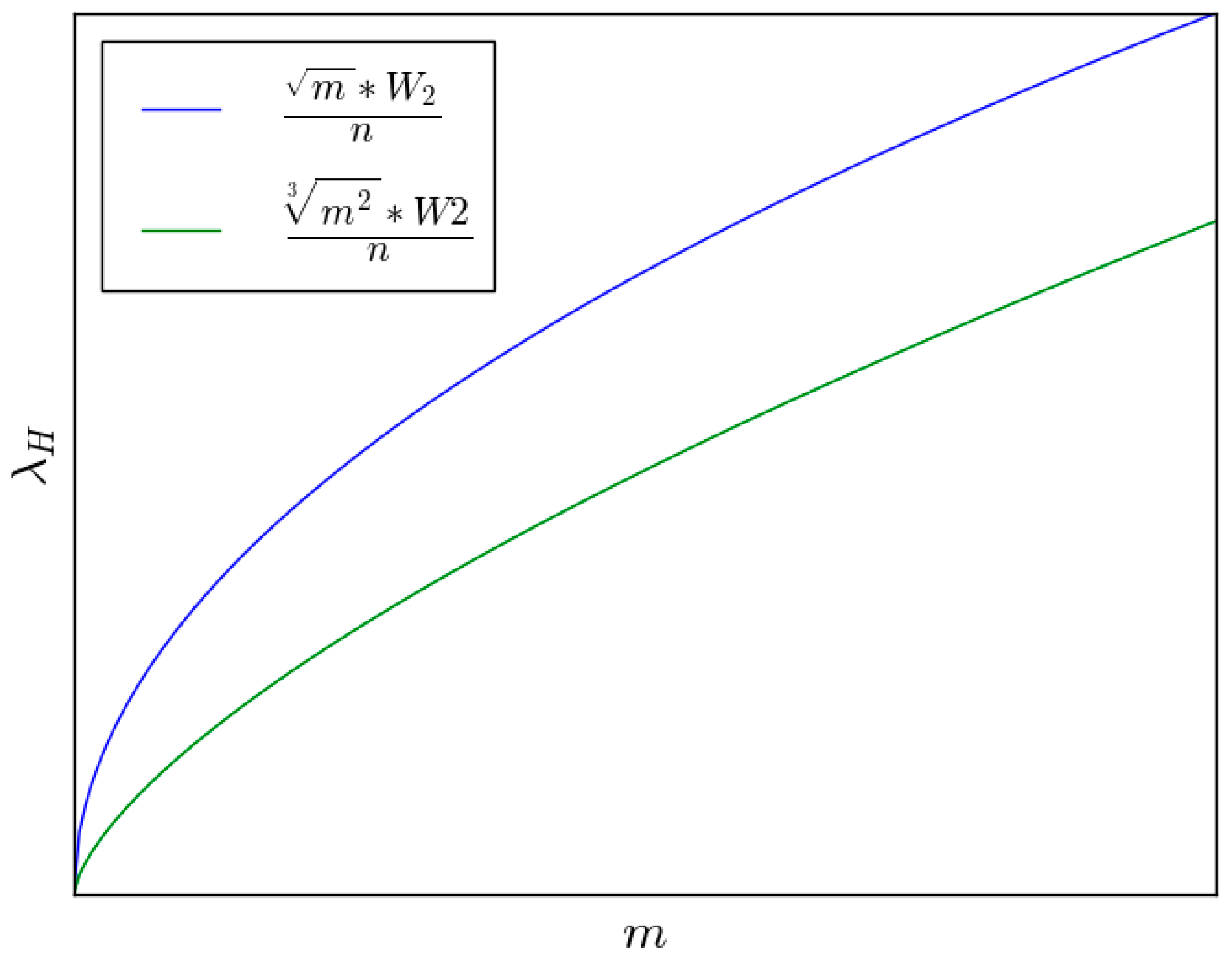
Figure 12 shows the relationship of throughput capacity and the number of helping nodes.
Combining the analysis above, we reach the following conclusions:
- (1)
In two-dimensional networks:
If the delay is allowed to be larger than some fixed constant D = Ω(n), the capacity is . In this condition the network capacity can achieve constant order. Specially, if m = Ω(n), most of packets can be delivered to the destination nodes with the help of backbone network. It implies that if the number of helping nodes is large enough, network capacity can stay constant order, and the delay can be limited, too. Similarly, if m = o(n), most of the packets will be transmitted by ad hoc transmission mode. It means that if the number of helping nodes is small, though the capacity is also constant order, the delay can not be ensured.
If the delay is limited (
D = Ω(
n)), the network capacity is
. In this condition, most of the packets will be transmitted by helping transmission mode. The number of helping nodes is the determining factor of the throughput capacity.
- (2)
In three-dimensional mobile networks:
We can reach similar conclusions to two-dimensional mobile networks. According the analysis above, we can conclude that the number of helping nodes in the network is a key factor which affects the throughput capacity. If the number of helping nodes is large enough, the capacity can stay constant with the help of the backbone network. In this case, the time delay can be ensured. If the number of helping node is small, most of the packets have to be delivered in multi-hop fashion. In this case, though the throughput capacity can achieve constant order too, the delay will go to infinity. The delay constraint D is also an important factor on the network capacity. If D is not limited, the capacity contributed by ad hoc transmission mode can achieve Θ(1), which means that the network capacity of the whole network can achieve a constant order. If D is constrained, the capacity contributed by ad hoc mode is almost zero and most of packets have to be delivered by helping transmission mode.