Protocol to Exploit Waiting Resources for UASNs †
Abstract
:1. Introduction
2. Related Work
3. System Model and Problem Formulation
3.1. System Model
3.2. Problem Formulation
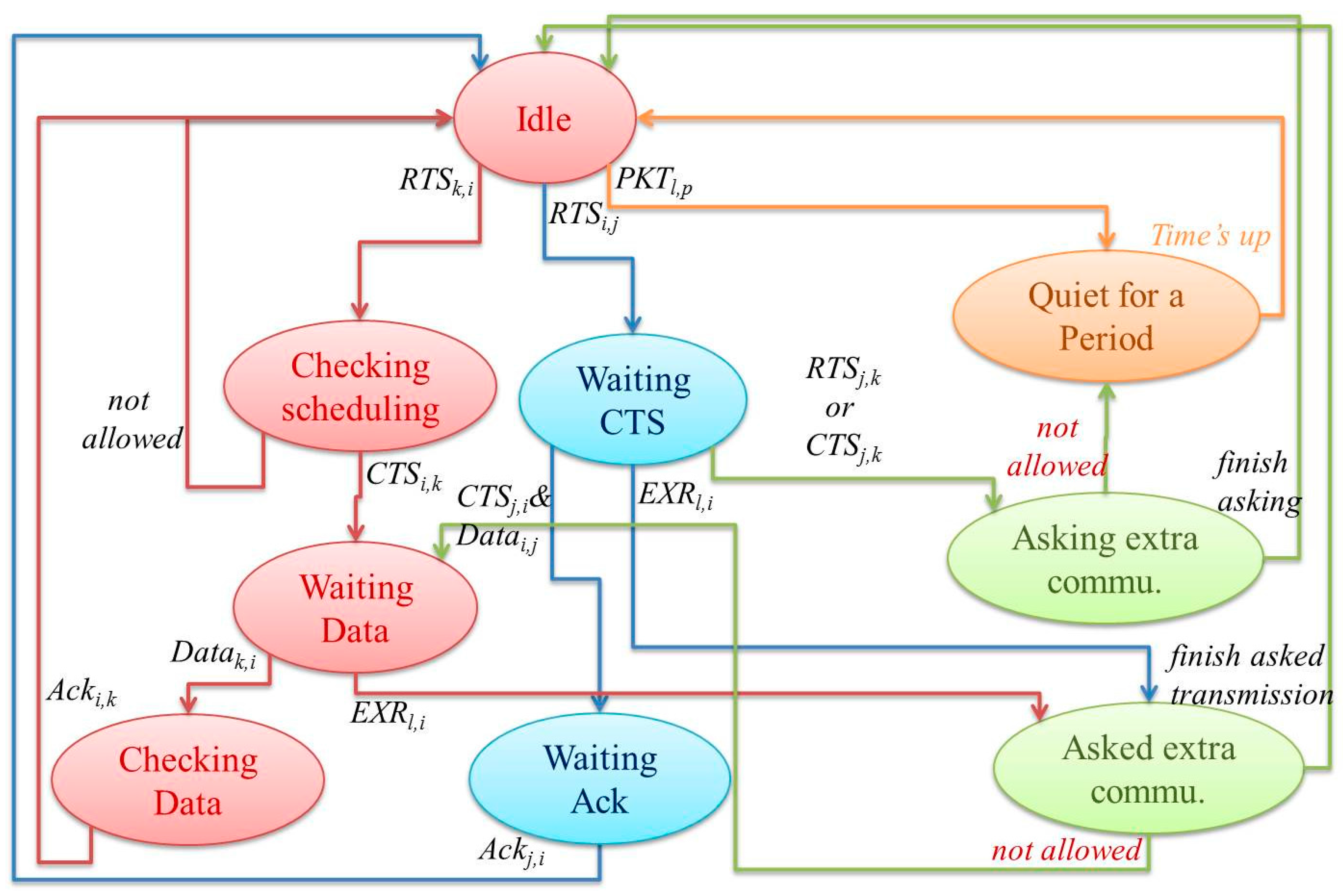
4. Proposed EW-MAC Algorithm
4.1. EW-MAC Design and Assumptions
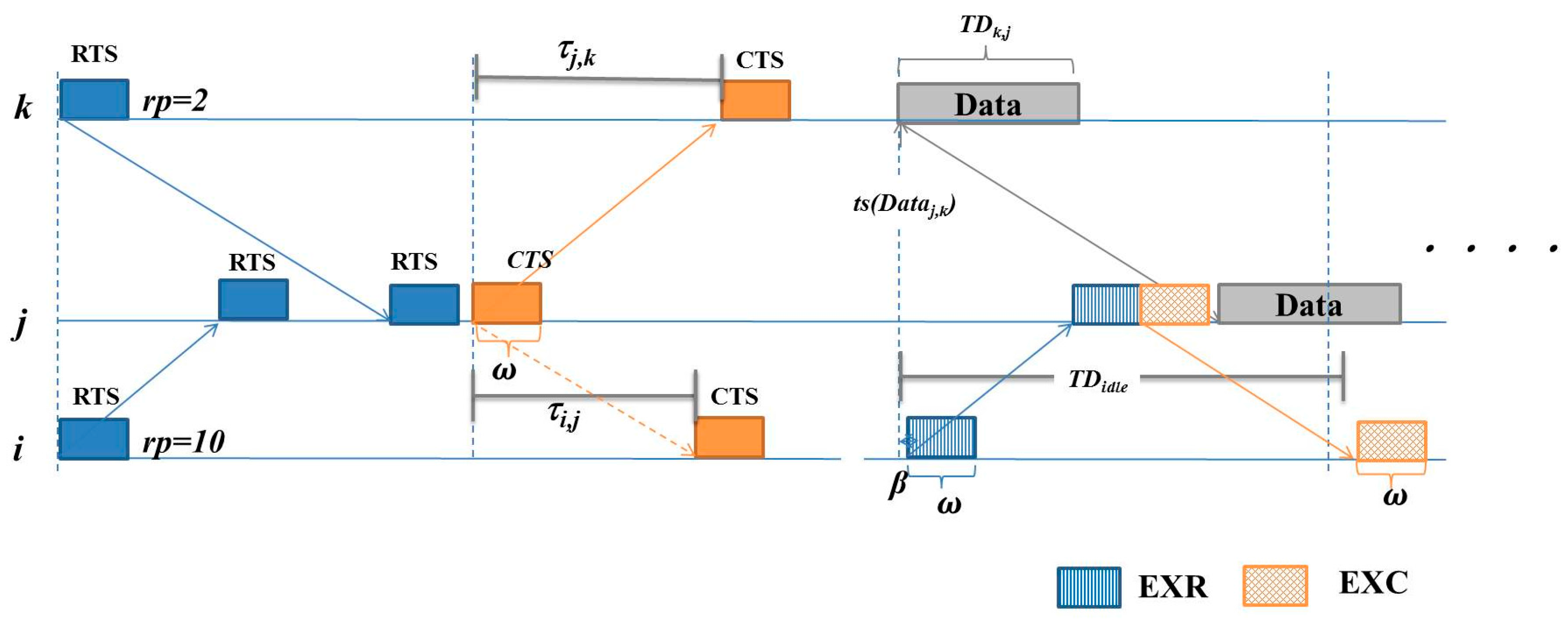
Negotiation for Communication in UASN
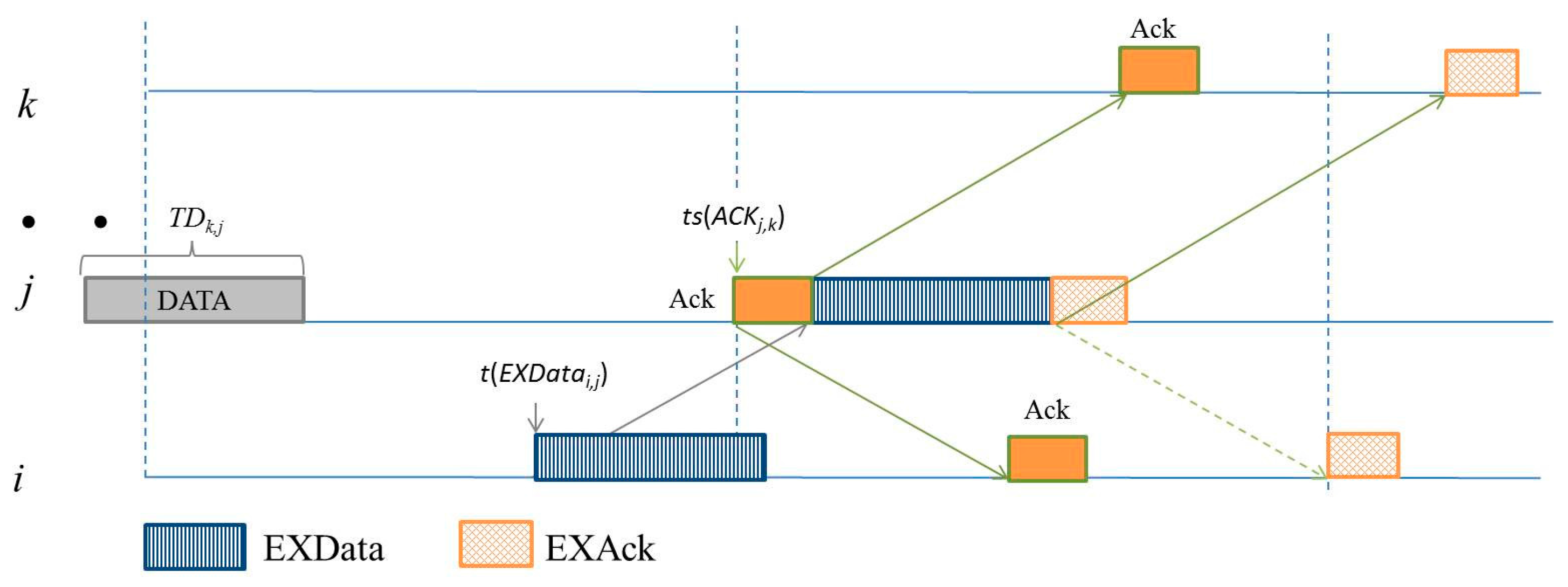
4.2. Extra Communications for Negotiated Neighbors
4.3. Initialization and Information Maintenance
5. Analysis and Performance Evaluation
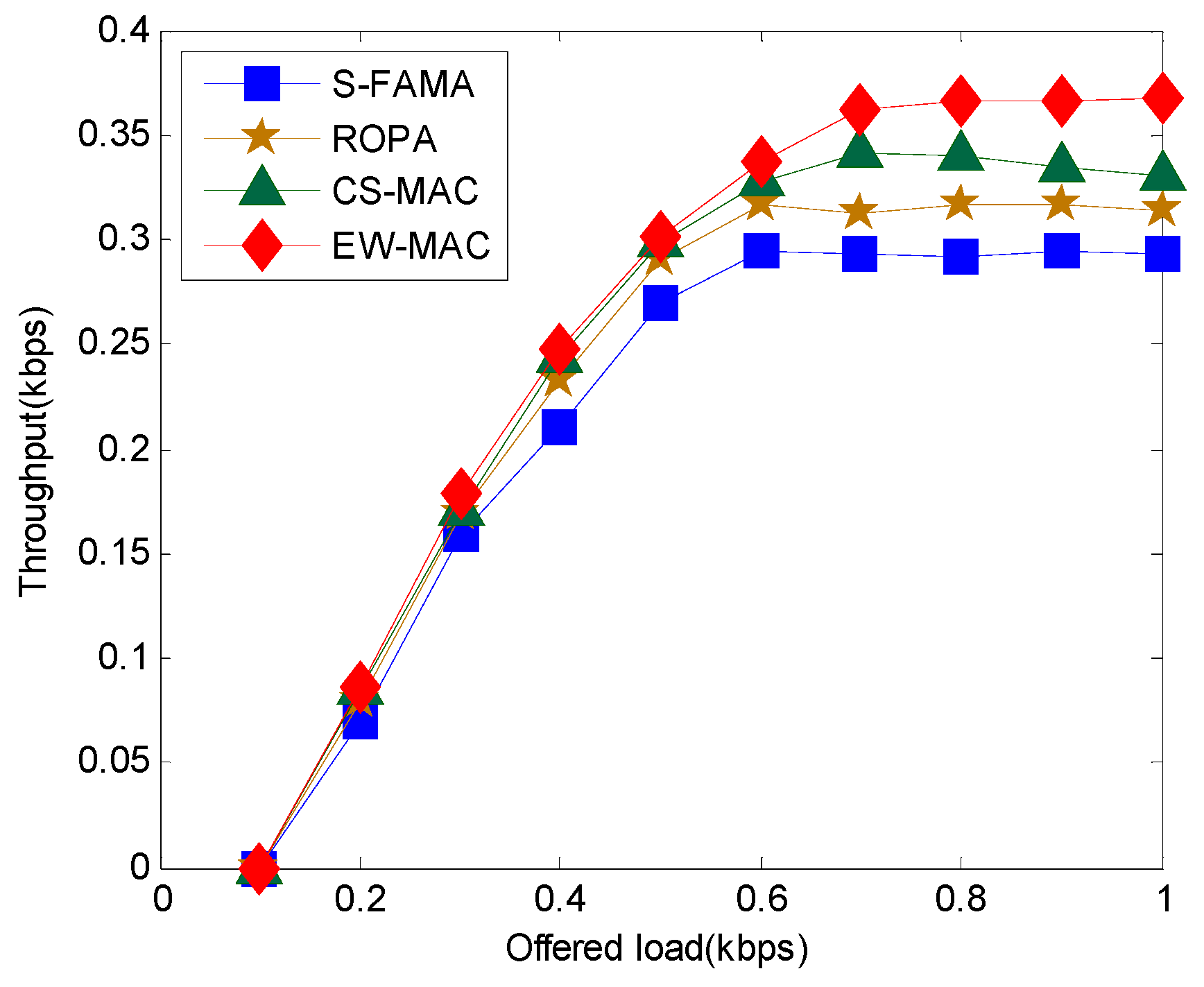
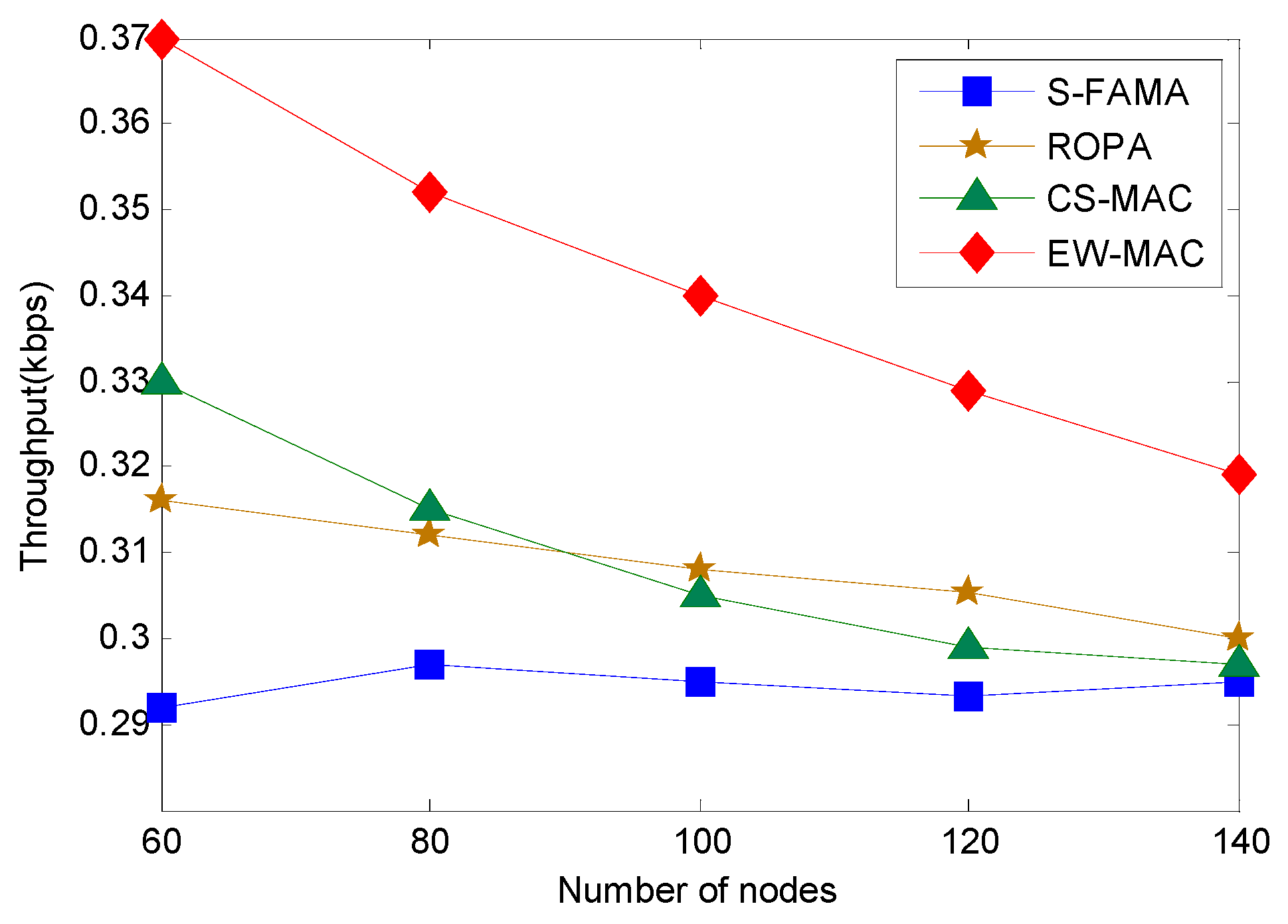
5.1. Throughput
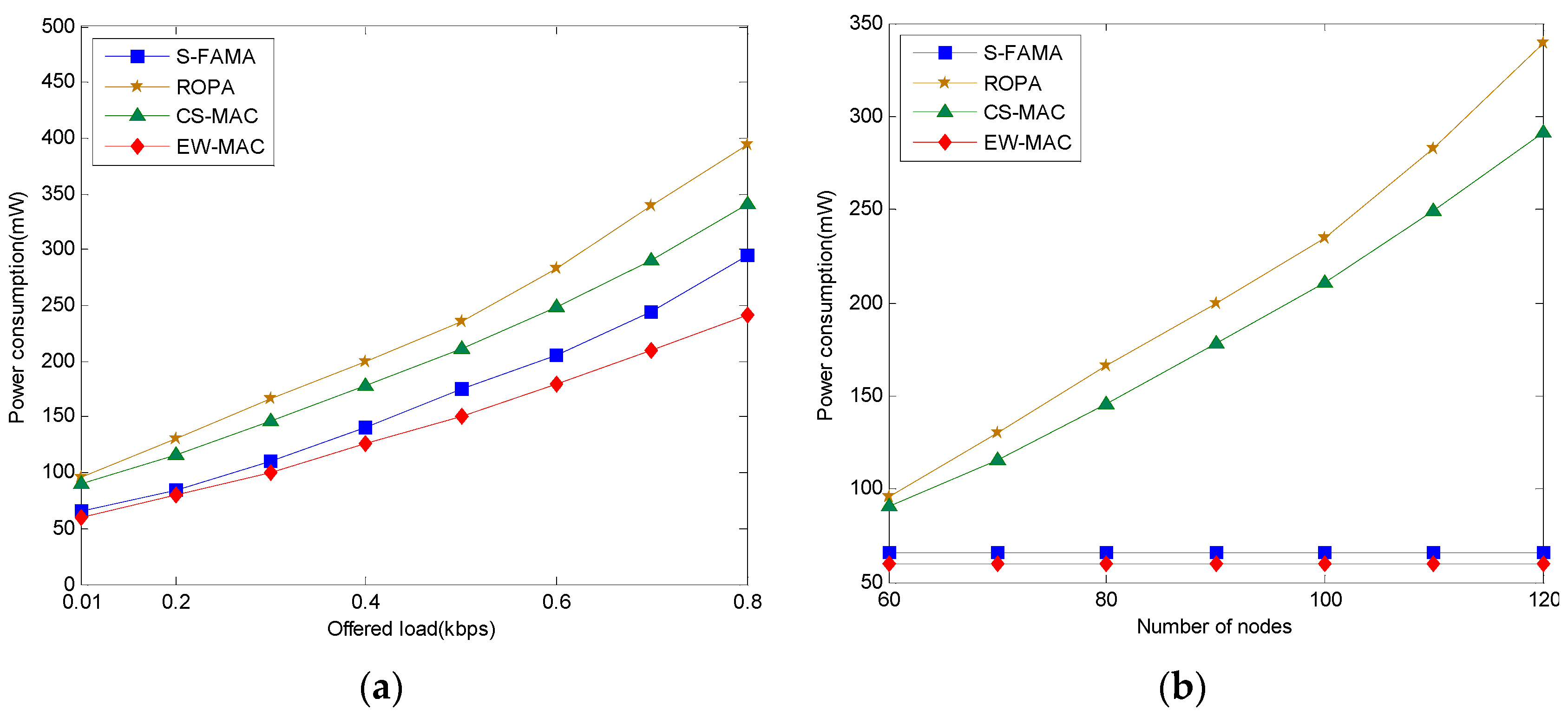
5.2. Power Consumption
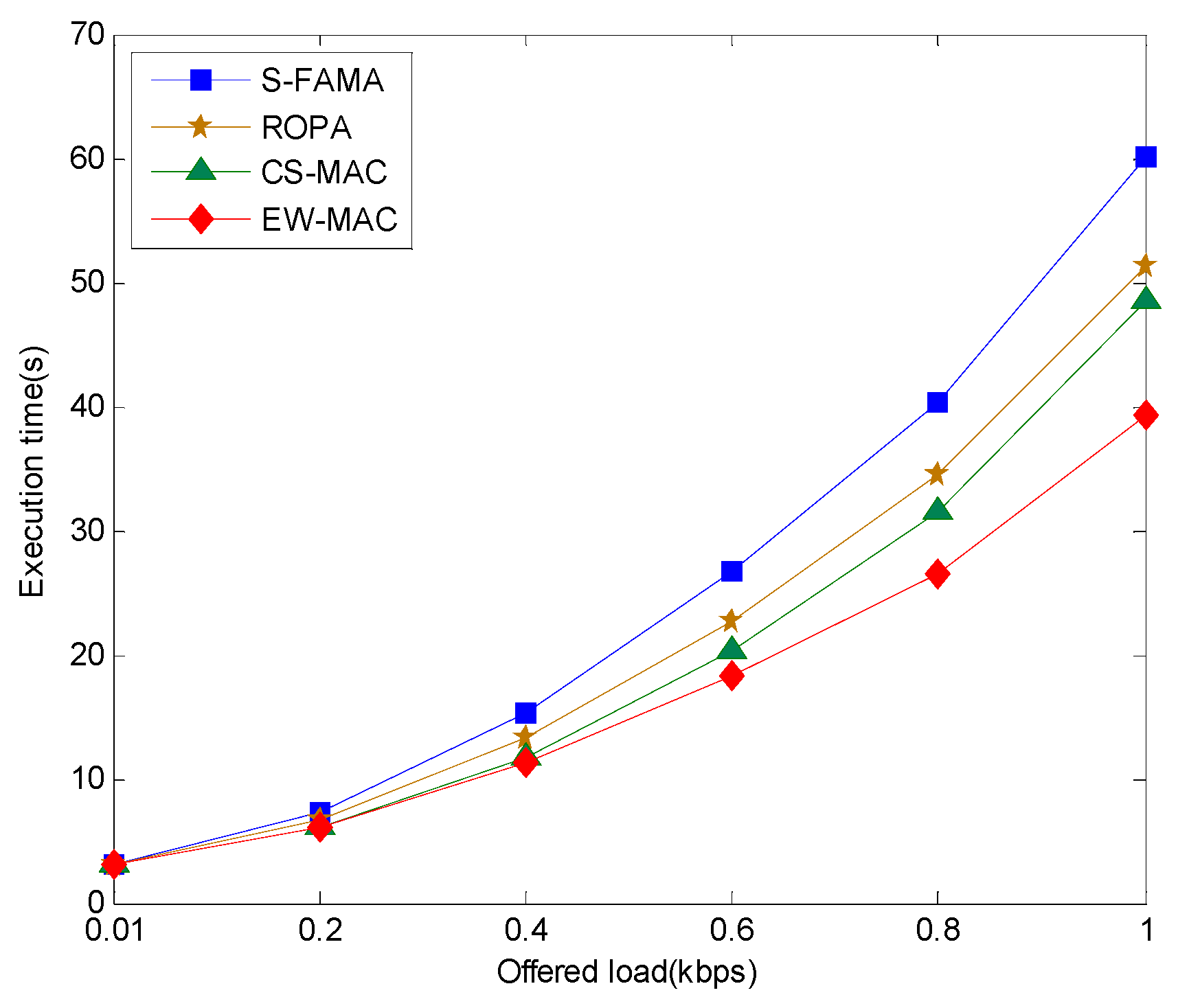
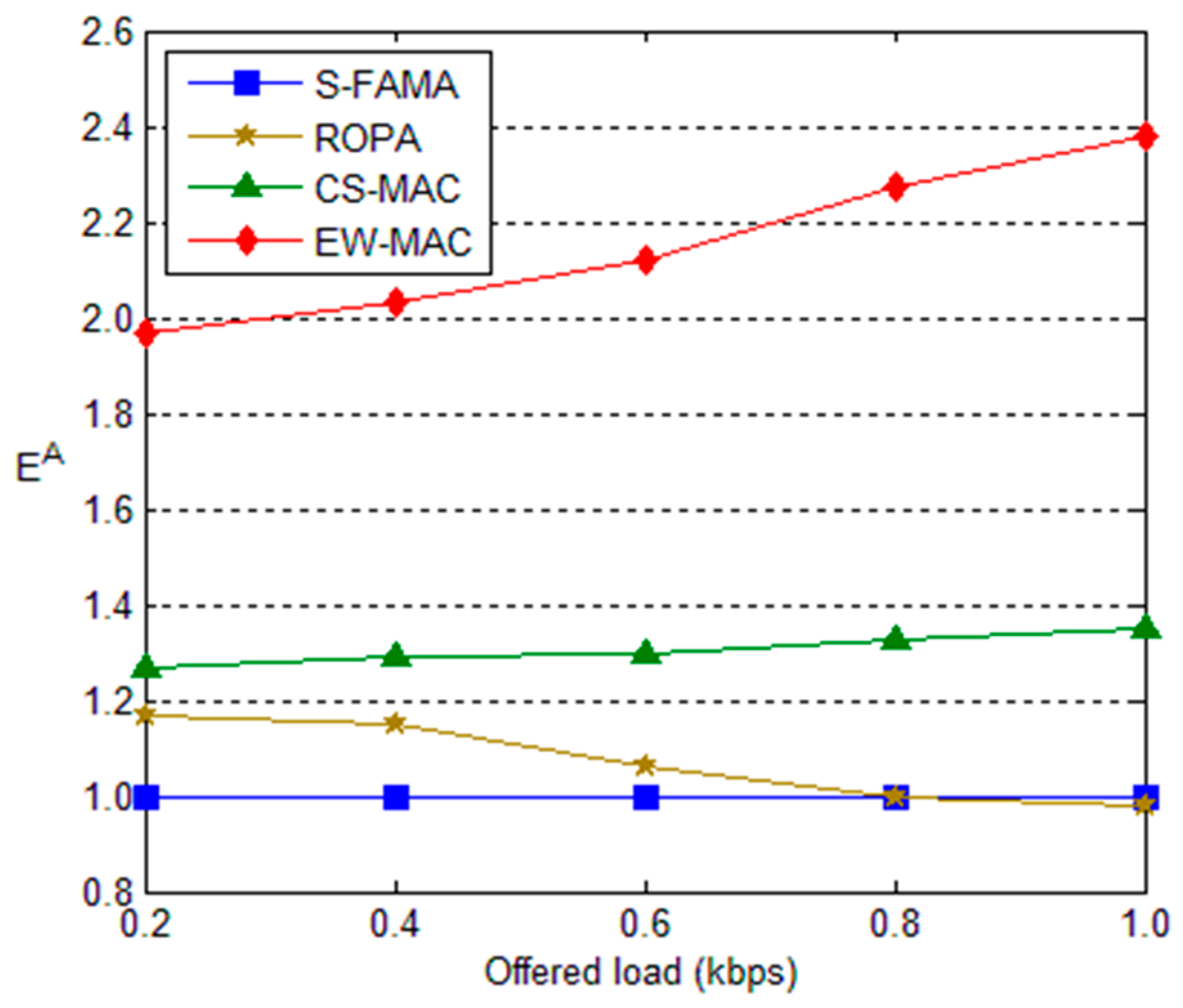
5.3. Overhead
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Partan, J.; Kurose, J.; Levine, B.N. A Survey of Practical Issues in Underwater Networks. ACM SIGMOBILE Mob. Comput. Commun. 2007, 11, 23–33. [Google Scholar] [CrossRef]
- Akyildiz, I.F.; Lee, W.-Y.; Vuran, M.C.; Mohanty, S. A Survey on Spectrum Management in Cognitive Radio Networks. IEEE Commun. Mag. 2008, 46, 40–48. [Google Scholar] [CrossRef]
- Molins, M.; Stojanovic, M. Slotted FAMA: A MAC protocol for underwater acoustic networks. In Proceedings of the OCEANS 2006, Asia Pacific, Singapore, 16–19 May 2006; pp. 1–7.
- Ng, H.-H.; Soh, W.-S.; Motani, M. An Underwater Acoustic MAC Protocol Using Reverse Opportunistic Packet Appending. Comput. Netw. 2013, 57, 2733–2751. [Google Scholar] [CrossRef]
- Noh, Y.; Wang, P.; Lee, U.; Torres, D.; Gerla, M. DOTS: A Propagation Delay-Aware Opportunistic MAC Protocol for Underwater Sensor Networks. In Proceedings of the IEEE International Conference Network Protocols (ICNP), Kyoto, Japan, 5–8 October 2010; pp. 5–8.
- Chitre, M.; Motani, M.; Shahabudeen, S. Throughput of Networks with Large Propagation Delays. IEEE J. Ocean. Eng. 2012, 37, 645–658. [Google Scholar] [CrossRef]
- Chen, Y.J.; Wang, H.L. Ordered CSMA: A Collision-Free MAC Protocol for Underwater Acoustic Networks. In Proceedings of the OCEANS 2007, Vancouver, BC, USA, 29 September–4 October 2007; pp. 1–6.
- Hong, L.; Hong, F.; Guo, Z.; Yang, X. A TDMA-Based MAC Protocol in Underwater Sensor Networks. In Proceedings of the 4th International Conference on Wireless Communications, Networking and Mobile Computing, Dalian, China, 12–14 October 2008; pp. 1–4.
- Nguyen, T.H.; Shin, S.-Y.; Park, S.-H. Efficiency Reservation MAC Protocol for Underwater Acoustic Sensor Networks. In Proceedings of the Fourth International Conference on Networked Computing and Advanced Information Management, Gyeongju, Korea, 2–4 September 2008; pp. 365–370.
- Ng, H.-H.; Soh, W.-S.; Motani, M. MACA-U: A media access protocol for underwater acoustic networks. In Proceedings of the IEEE Global Telecommunications Conference (GLOBECOM), New Orleans, LO, USA, 30 November–4 December 2008; pp. 1–6.
- Guo, X.; Frater, M.; Ryan, M. A Propagation-Delay-Tolerant Collision Avoidance Protocol for Underwater Acoustic Sensor Networks. In Proceedings of the OCEANS, Asia Pacific, Singapore, 16–19 May 2007; pp. 1–6.
- Xie, P.; Cui, J.H. R-MAC: An Energy-Efficient MAC Protocol for Underwater Sensor Networks. In Proceedings of the International Conference on Wireless Algorithms, Systems and Applications (WASA), Chicago, IL, USA, 1–3 August 2007; pp. 187–198.
- Diamant, R.; Shirazi, G.; Lampe, L. Robust Spatial Reuse Scheduling in Underwater Acoustic Communication Networks. IEEE J. Ocean. Eng. 2014, 39, 32–46. [Google Scholar] [CrossRef]
- Ng, H.H.; Soh, W.-S.; Motani, M. A Bidirectional-Concurrent MAC Protocol with Packet Bursting for Underwater Acoustic Networks. IEEE J. Ocean. Eng. 2013, 38, 547–565. [Google Scholar] [CrossRef]
- Ma, J.; Lou, W. Interference-Aware Spatio-Temporal Link Scheduling for Long Delay Underwater Sensor Networks. In Proceedings of the 2011 8th Annual IEEE Sensor Communications Society Conference on Mesh and Ad Hoc Communications and Networks (SECON), Salt Lake City, UT, USA, 27–30 June 2011; pp. 404–412.
- Diamant, R.; Shi, W.; Soh, W.; Lampe, L. Joint Time and Spatial Reuse Handshake Protocol for Underwater Acoustic Communication Networks. IEEE J. Ocean. Eng. 2011, 38, 470–483. [Google Scholar] [CrossRef]
- Liao, W.-H.; Kuai, S.-C.; Lin, Y.-C. A Receiver-Initiated MAC Protocol with Packet Train Design for Underwater Acoustic Sensor Networks. Wirel. Person. Commun. 2015, 82, 2155–2170. [Google Scholar] [CrossRef]
- Chen, Y.-D.; Liu, S.-S.; Chang, C.-M.; Shih, K.-P. CS-MAC: A Channel Stealing MAC Protocol for Improving Bandwidth Utilization in Underwater Wireless Acoustic Networks. In Proceedings of the OCEANS 2011, Waikoloa, HI, USA, 19–22 September 2011; pp. 19–22.
- Basagni, S.; Petrioli, C.; Petroccia, R.; Stojanovic, M. Optimized Packet Size Selection in Underwater Wireless Network Communications. IEEE J. Ocean. Eng. 2012, 37, 321–337. [Google Scholar] [CrossRef]
- Liu, L.; Xiao, Y.; Zhang, J. A Linear Time Synchronization Algorithm for Underwater Wireless Sensor Networks. In Proceedings of the IEEE International Conference on Communications (ICC), Dresden, Germany, 14–18 June 2009; pp. 1–5.
- Xie, Y.; Hu, X.; Xiao, J.; Wang, D.; Lei, W. Implementation of Timing Synchronization for OFDM Underwater Communication System on FPGA. In Proceedings of the 3rd International Conference on Anti-Counterfeiting, Security, and Identification in Communication, Hong Kong, China, 20–22 August 2009; pp. 568–570.
- Liu, J.; Wang, Z.; Zuba, M.; Peng, Z.; Cui, J.-H.; Zhou, S. DA-Sync: A Doppler-Assisted Time-Synchronization Scheme for Mobile Underwater Sensor Networks. IEEE Trans. Mob. Comput. 2014, 13, 582–595. [Google Scholar] [CrossRef]
- Klungmontri, C.; Nilkhamhang, I.; Covanich, W.; Isshiki, T. Underwater positioning systems for underwater robots using trilateration algorithm. In Proceedings of the International Conference of Information and Communication Technology for Embedded Systems (IC-ICTES), Hua-Hin, Thailand, 22–24 March 2015; pp. 1–5.
- Karim, L.; Mahmoud, Q.H.; Nasser, N.; Anpalagan, A.; Khan, N. Localization in terrestrial and underwater sensor-based M2M communication networks: Architecture, classification and challenges. Int. J. Commun. Syst. 2015. [Google Scholar] [CrossRef]



| Notation | Description |
|---|---|
| Number of packets k receives successfully during period T | |
| Pkts,r | A packet whose sender is s and destination is r, Pkt can be RTS, CTS, Data, Ack, EXR (extra RTS), EXC (extra CTS), EXData (extra Data), or EXAck (extra Ack) |
| Pktts,r | Boolean value; if Pkts,r is transmitted at time t, then Pktts,r = 1, otherwise Pktts,r = 0 |
| |Pktts,r| | Duration s transmits Pktts,r |
| ts(Pktts,r) | Time slot in which Pktts,r is transmitted |
| N(x) | Set of sensors that are one-hop neighbors of sensor x |
| τxy | Propagation delay between sensors x and y |
| ω | Duration of a transmitted or received control packet |
| |ts| | Duration of a time slot |
| Parameter | Value |
|---|---|
| Number of sensors | 60 |
| Deployment area | 1000 km3 |
| Bandwidth | 12 kbps |
| Communication range | 1.5 km |
| Acoustic transmission speed | 1.5 km/s |
| Simulation time | 300 s |
| Control packet size | 64 bits |
| Data packet size | 1024–4096 bits |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hung, L.-L.; Luo, Y.-J. Protocol to Exploit Waiting Resources for UASNs. Sensors 2016, 16, 343. https://doi.org/10.3390/s16030343
Hung L-L, Luo Y-J. Protocol to Exploit Waiting Resources for UASNs. Sensors. 2016; 16(3):343. https://doi.org/10.3390/s16030343
Chicago/Turabian StyleHung, Li-Ling, and Yung-Jeng Luo. 2016. "Protocol to Exploit Waiting Resources for UASNs" Sensors 16, no. 3: 343. https://doi.org/10.3390/s16030343






