1. Introduction
Recent advances in Wireless Sensor Networks (WSNs) have meant that sensor nodes are capable of processing and transmitting environmental monitored data in real time to end users who are located far from the area covered by the sensor network. WSNs are still limited however in terms of energy, memory storage, and security communication capabilities. Fortunately, security for WSNs has been examined and developed upon for different application domains, such as medical and environmental. It has been shown by Mathur et al. in [
1] that it is possible to provide a patient monitoring system that resolves security issues associated with data loss, while in [
2] Elgenaidi et al. have studied different water environment monitoring systems based on WSNs that carry information that has value, and this value (data) must be encrypted for protection. The security of transmitted data is crucial in WSN applications so as not to reveal to unauthorized persons the information travelling between nodes, however this security solution must be resource-friendly and efficient. In order to build an efficient security algorithm, it is necessary to fully understand the process of security functions in terms of energy consumption, time execution and code size.
In WSN mesh networks, symmetric encryption algorithms have been widely used because of the advantages of low cost with respect to power consumption, time execution and code size. The main obstruction in the implementation of symmetric encryption is the issue of key re-distribution between nodes in the case of a change in the network members. Asymmetric encryption techniques, such as Rivest, Shamir, and Adleman (RSA) and elliptic curve cryptography (ECC) have been used to tackle re-keying in WSNs applications [
3], however, the problem with using these techniques is the computation overhead on every node in the network, and this increases the cost of each node and accordingly the processing of security key management. Generally, key management in sensor networks can be listed under three headings:
Some applications rely upon a secure key establishment mechanism where each node in a key establishment protocol is able to determine the true identity of the other nodes that could possibly gain access to the resulting key. This implies the preclusion of any unauthorized additional parties from deducing the same key [
5]. Many secure key management schemes which promote longer battery life also depend on the type of system.
The most widely used wireless standard for WSNs is IEEE 802.15.4 [
7]. The main advantages of using IEEE 802.15.4 are very low energy consumption, the capability of using different network topologies, for instance point-to-point topology the capability of inter-operability with transmit/receive chips, such as XBee 802.15.4 pro and the ability to engage with Wi-Fi.
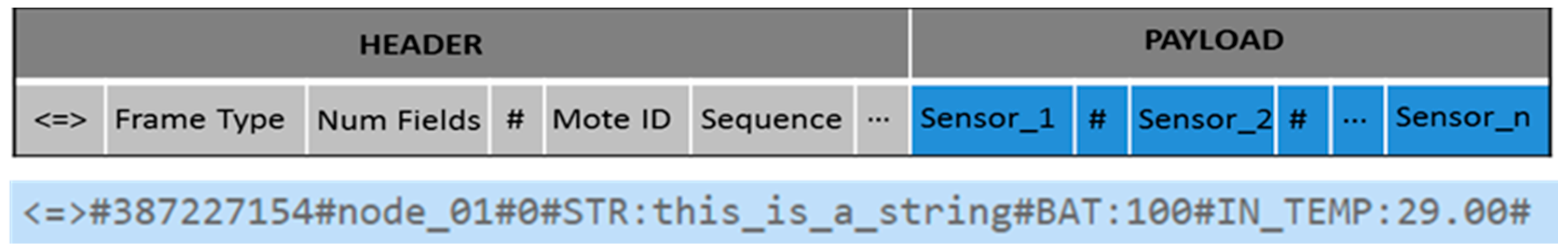
The scheme being proposed in this paper addresses the main issues in security mechanisms based on the symmetric encryption algorithm, including memory, storage space, key generation, and re-keying. In this paper, the deployment of a Waspmote sensor node integrated with the XBee 802.15.4 pro module in an outdoor environment using IEEE 802.15.4/2.4 GHz standard will be used to demonstrate the implementation of the proposed protocol. Most of the presented results to date by other authors [
8,
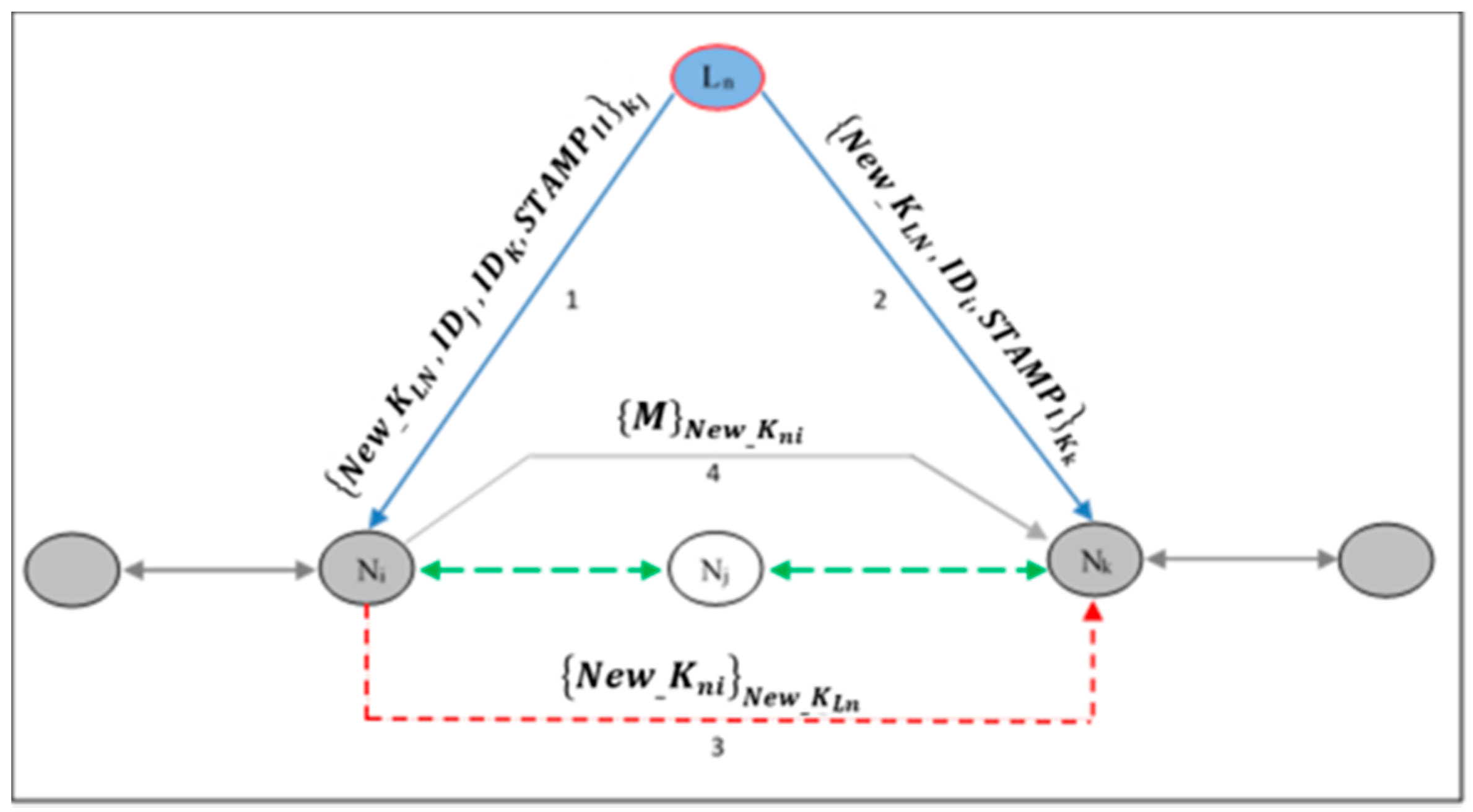
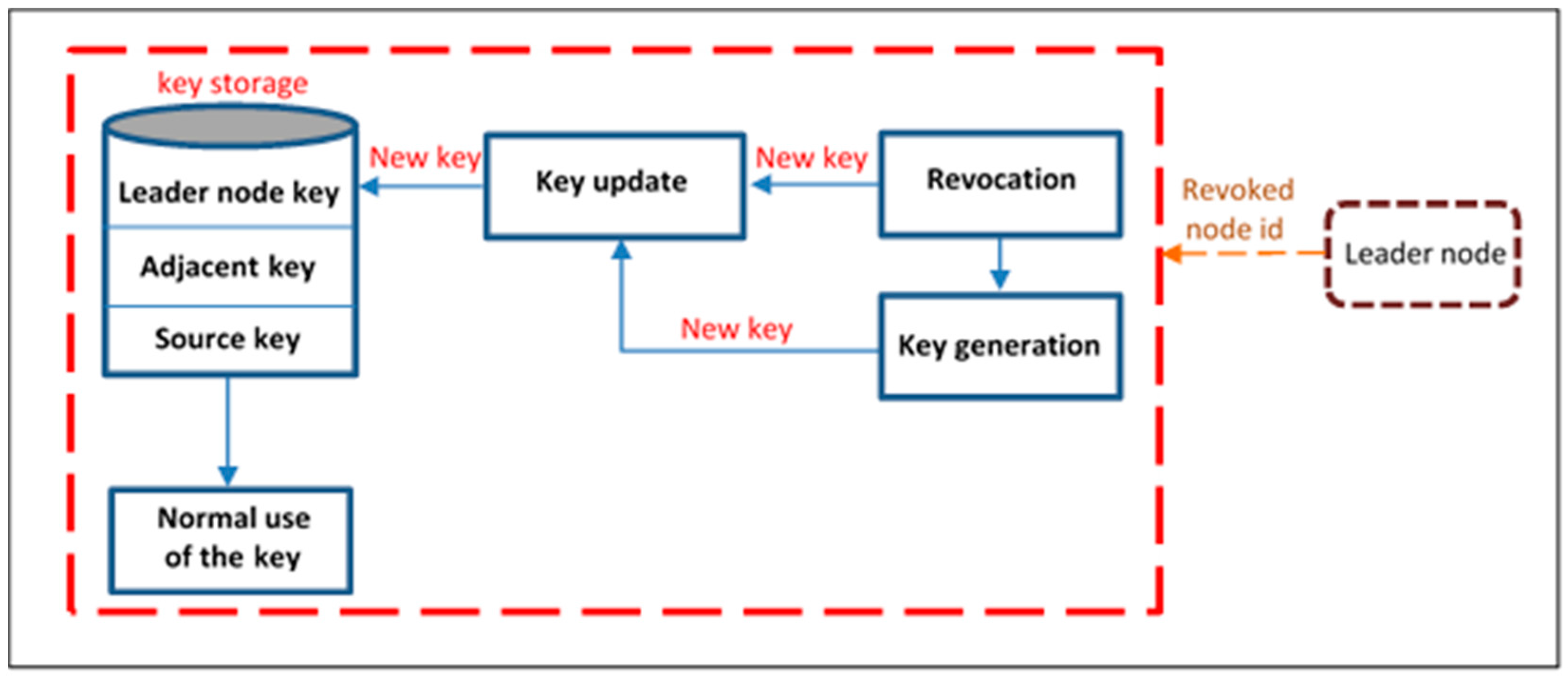
9] have been obtained using simulators and not real deployments as in this paper. This paper also presents a security mechanism suitable for marine coastal monitoring, where each node in a line topology sends packets encrypted with its secret key, called the Adjacent key, to provide data confidentiality. This key is shared only with an authorized neighbor in the network. Furthermore, the re-keying phase in the revocation process will be a partly operation coordinated by a node called the leader node.
The rest of this paper is organized as follows: related works are discussed in
Section 2. In
Section 3 the proposed technique is discussed covering network topology, platform, travelling packets, packet structure, and security and key management. It also describes transmission security and data encryption, Re-keying and the memory requirement for the scheme. In
Section 4, the outdoor implementation and performance measurements of the scheme are also presented in different scenarios. These measurements are discussed in terms of the received single strength indicator (RSSI), the average round trip time (RTT) and current consumption. In
Section 5 a discussion and comparison between measurements of the proposed scheme and results of other schemes is given. The paper is concluded in
Section 6.
2. Related Work
There are some well-known practices for developing efficient trust security systems for WSNs and managing the cryptographic keys in order to protect WSNs from malicious attacks [
10]. Liu, et al. proposed in [
11] an efficient and simple technique for detecting selective forwarding attacks and recovering the failed route based on a per-hop acknowledgement. This section will present key management and encryption schemes, which ensure the level of security in WSNs application.
Liebeherr et al. [
12] designed and implemented a security key management and encryption scheme called the ‘neighborhood key’ scheme. This technique provided integrity and confidentiality for application data in overlay networks. The core mechanism of this technique was to avoid network-wide re-keying operations. Additionally, the scheme re-encrypts the payload data at each forwarding hop. Moreover, the neighborhood key method provided a solution for protection against routing attacks, where authentication between sensor nodes in the network depends on the certificate signed by a trusted third party using an X.509 Version 3 certificate. Each sensor node in the network had its own signed certificate, also each node stores the certificates of one or more trusted third party. In this scheme the authentication phase was performed without coordination with other nodes. The node certificate included a secret key, which is used to encrypt or sign data. Sensor nodes exchange certificates after receiving a message protocol from another node in the network. Once the certificates are exchanged, the encryption of data and the signing of hashes in each node will be done with a single symmetric key called a ‘neighborhood key’. Thus, the neighborhood keys are shared between current authenticated neighbors in the network. In the joining phase where a new node joins the network, a new neighborhood key must be generated and sent to all of its authenticated neighbors in order to maintain confidentiality in the network.
Furthermore, updating and exchanging a new neighborhood key is executed whenever the set of authenticated neighbors are changed or the specified maximum lifetime of the current neighborhood key is expired. Therefore, every sensor node must encrypt the new neighborhood key with the public keys of all the authenticated neighbors (using the RSA algorithm), which are stored in the node during the authentication stage. The security issues are exacerbated during failures in re-establishment of the network topology when one or more nodes join/leave the network at the same time. Additionally, by implementing an integrity test and limiting the allowed frequency of transmitted key request messages the neighborhood scheme protects nodes from Denial of Service (DoS) attacks from malicious adversaries.
A hierarchical key management scheme for secure group communications in a mobile ad hoc network is proposed by Wang et al. [
13] and Annadurai [
14]. In this proposed scheme, a new approach with a two-layer structure where a cluster head manages information between sensor nodes in the layers was given. The main idea in this scheme is that nodes are divided into two subgroup levels, a Level 1 subgroup ‘L1-subgroup’ contains all sensor nodes in the subgroup. Moreover, Level 2 subgroup ‘L2-subgroup’ is located depending on positional information of nodes in Level 1. In order to manage data transmission and coordinate security keys between nodes in the same subgroup level and with nodes in the other subgroup level, an election of a cluster head in each level must be processed. Generally, the election of a cluster head in each level depends on the largest weight value of nodes [
4]. In each L1-subgroup’, the node with the largest weight value in every L1-subgroup will be selected as the level 1 cluster head ‘L1-head’. Then to manage communication between levels and subgroups, the largest node weight value in L2-subgroup will be selected as Level 2 cluster head ‘L2-head’.
The nodes in the subgroups use the Diffie–Hellman (DH) scheme for secure transmission of their own subgroup keys, where each subgroup has a unique subgroup key [
13,
14]. Packets are transmitted between subgroups through the cluster heads. The L1-head generates a communication key which is shared between the different subgroups. However, the encryption and decryption operation during data transmission in different subgroups is only through subgroup keys. Furthermore, the Level 2 cluster head, ‘L2-head’, is responsible for a new node joining its subgroup.
Jang et al. [
15] proposed a time-based management protocol for WSNs to establish pair-wise keys. This technique relies on probabilistic time intervals and multiple initial keys, K
I. In this scheme, a pool of initial keys is assigned to time slots during the key setup phase. Sensor nodes are preloaded with initial key and master keys of randomly chosen time slots before the deployment phase. In the initial key establishment phase, all sensor nodes that contain K
I can compute a master key and then establish pair-wise keys with their neighbor node that was deployed at the same time slot using the same initial key. However, sensor nodes that were deployed at different time slots can establish pair-wise keys, if they have the same master key derived from the current initial key.
4. Practical Implementation of Proposed Framework
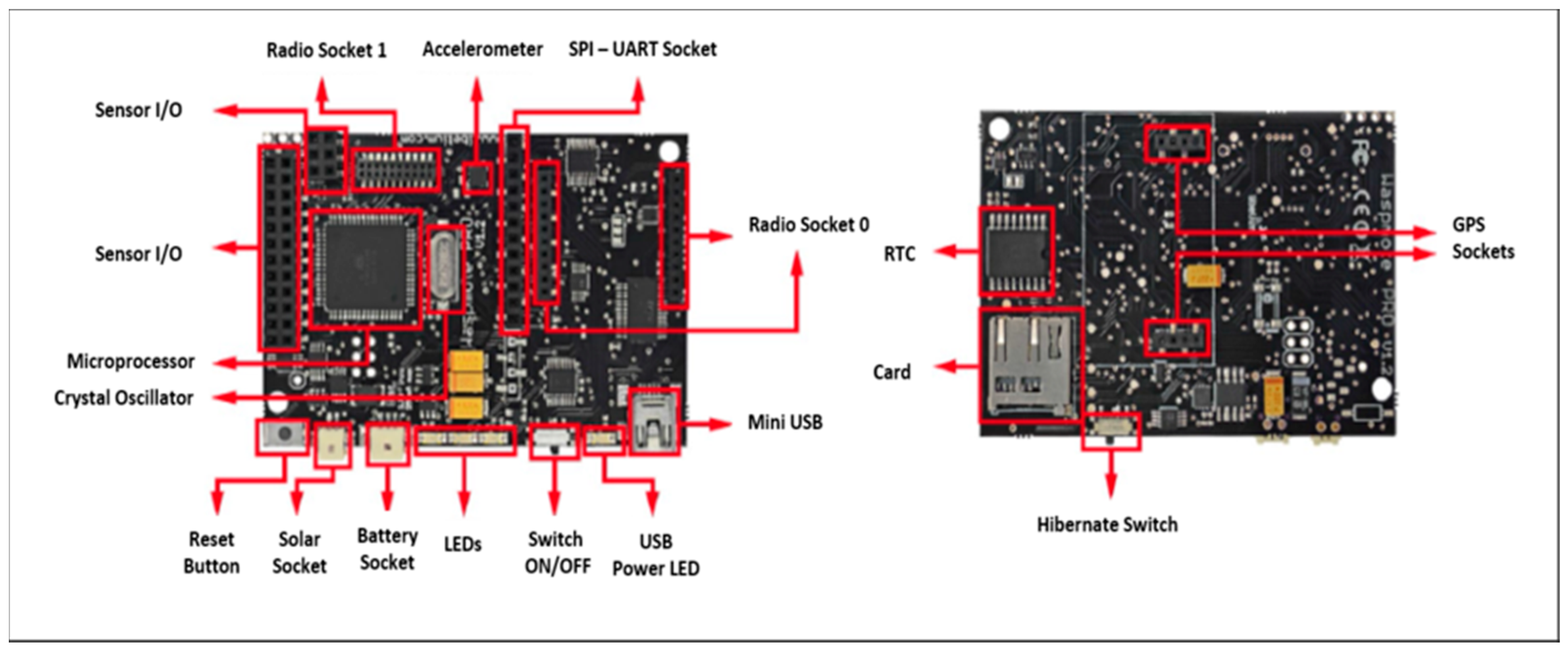
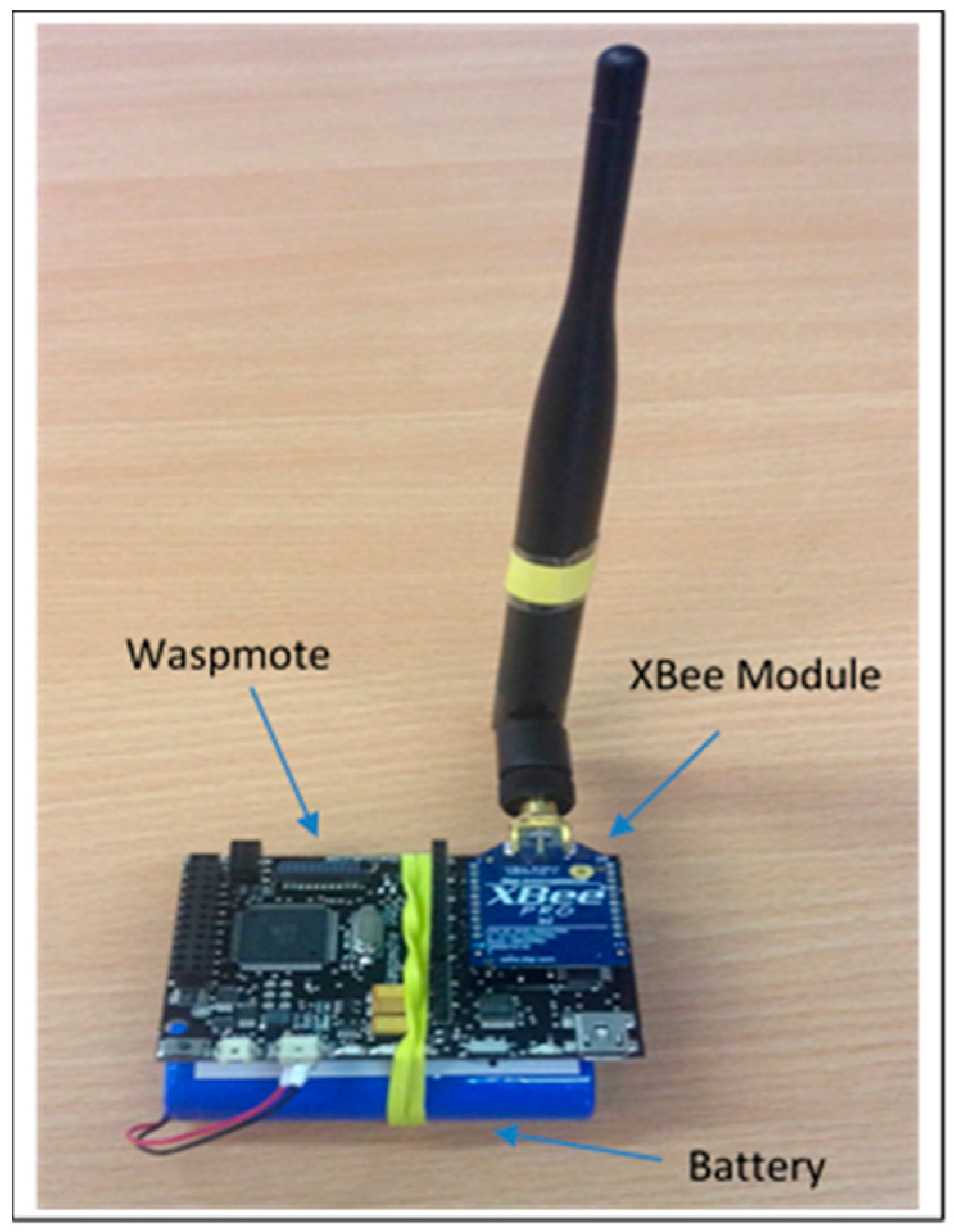
In this section, we present the implementation and test measurements of the scheme. The implementation involves four Waspmote nodes, a Waspmote Gateway, four XBee 802.15.4 Pro modules with antennae (
Figure 8), a MC1322x USB ZigBee dongle, an Agilent 66321D Mobile communication DC Source, a Waspmote Pro IDE version 04 with Waspmote Pro API Version 013 software based on Arduino, X-CTU provided by Digi and the Wireshark network analyzer.
Below is an outline of the three scenarios used to provide measurements to obtain the optimum configuration. The three scenarios were:
- (1)
Four nodes and the gateway at a distance of 80, 120 or 160 m between end points in line topology.
- (2)
Three nodes and the gateway at a distance of 80, 120 or 160 m between end points in the line topology.
- (3)
One repeater node between sender and the gateway at a distance of 80, 120 or 160 m between end points in the line topology.
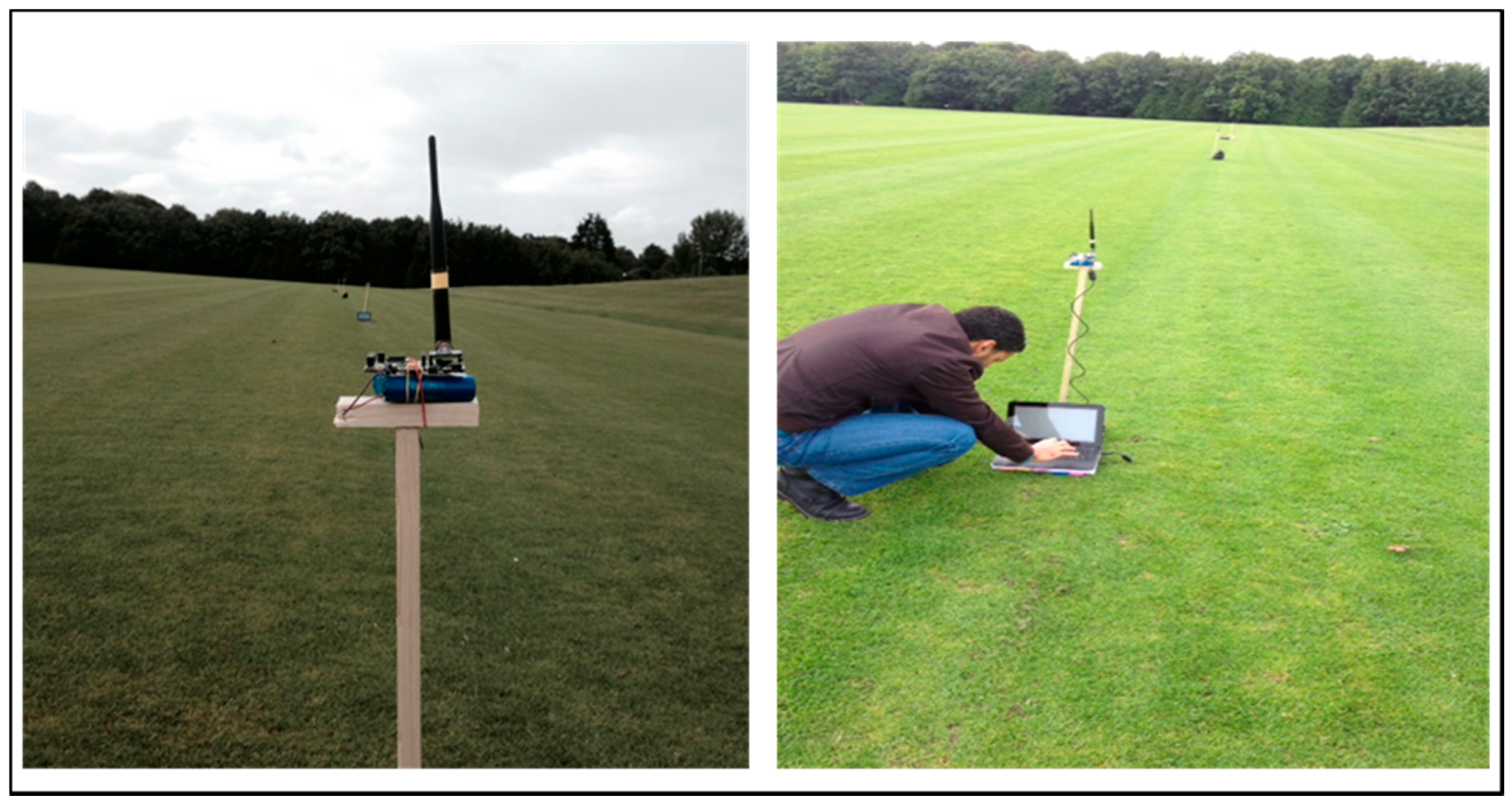
Figure 9 shows the physical setup of the scheme, where each Waspmote was placed on a fixed pole at a height of 80 cm from the ground. The effects of temperature and humidity on RSSI in WSNs as in [
18] was considered. In this scenario the temperature was between 20 °C and 21 °C and the humidity was 70%.
4.1. Received Single Strength Indicator Measurement
In order to ascertain the received single strength indicator (RSSI) a test involving the transmission of a fixed amount of data was performed. In this experiment, the received single strength indicator (RSSI) was measured at the gateway.
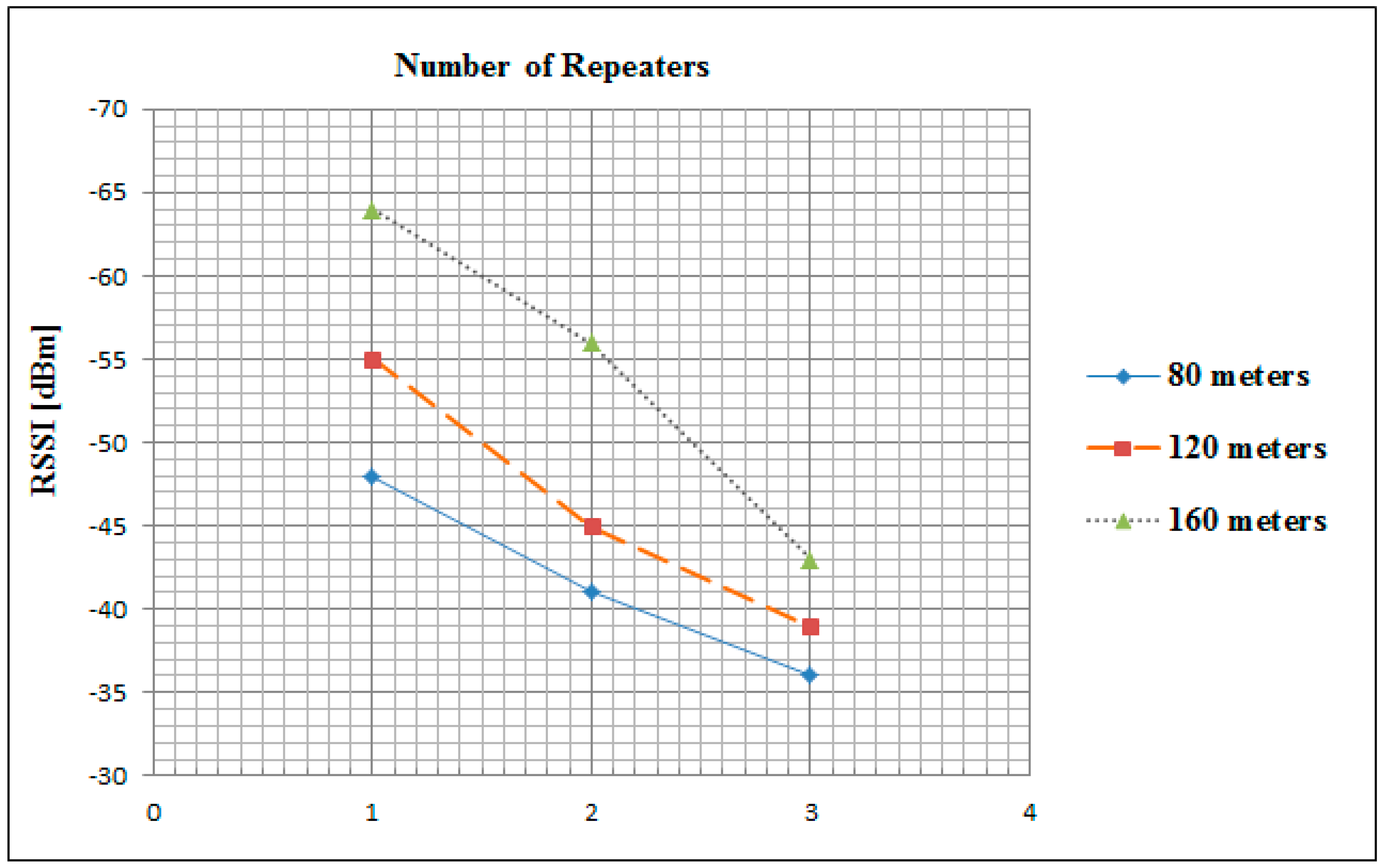
Figure 10 depicts the average value of RSSI which was measured after receiving 300 encrypted packets of 79 bytes in size at a baud rate of 115,200 bps.
These values were measured in the three aforementioned scenarios of distances and repeaters. The signal strength in the 80 m scenario was the strongest in the all case of one, two and three repeaters at exactly −48, −41 and −36 dB respectively. However, in the case of one repeater the 160 m scenario had the minimum signal strength value at −64 dB. While, in the case of all possible scenarios (as mentioned in
Section 3) the maximum achievable signal strength is −36 dB, which is the 80 m distance with three repeaters scenario. These measurements are used by the leader node to determine the positions of future new joining nodes into the line topology.
4.2. Round Time Trip Measurement
Figure 11 illustrates the average round time trip (RTT) for the different numbers of repeaters when increasing the distances between the sender and the gateway. In this experiment, RTT represents the elapsed time between the sender and the returned acknowledgment of the gateway to the last repeater. In fact, there was not a big difference in RTT measurements in the cases of one and two repeaters in all scenarios. However, in the three repeaters case, the time delay between 80 m and 160 m scenarios increased by approximately 39.248 ms, where RTT only increased by approximately 1.772 ms in the two repeaters case. The best RTT was obtained for the 80 m separation distance in all scenarios at 968.73, 1037.4 and 1996.802 ms in the one, two, and three repeater cases, respectively. These results were captured using a MC1322x USB Zigbee Dongle and the Wireshark network analyzer.
4.3. Current Consumption
Data processing relies on the size of the data and the approach used in processing this data. Furthermore, the designed scheme has been adapted to use minimum current consumption for data processing.
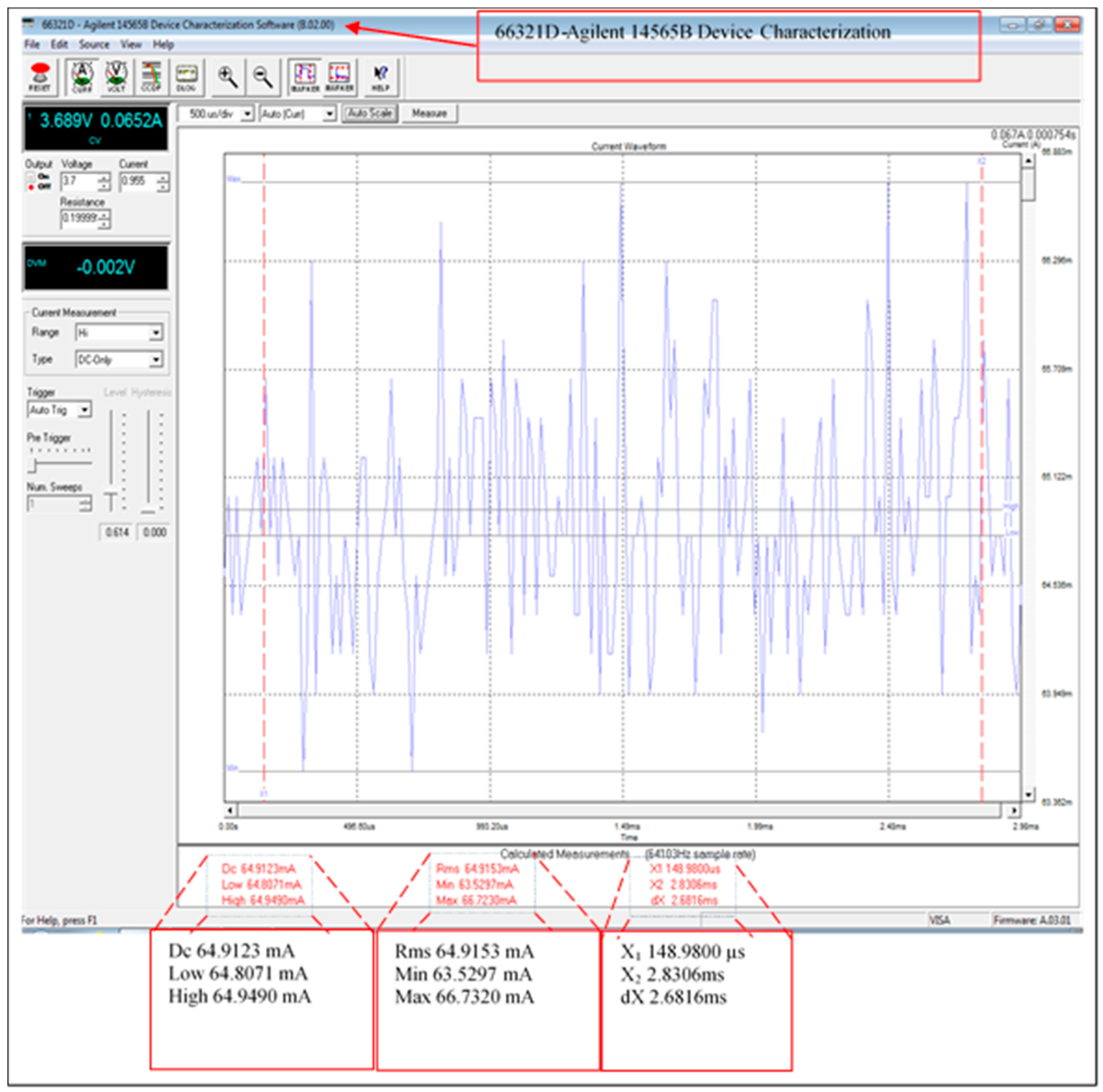
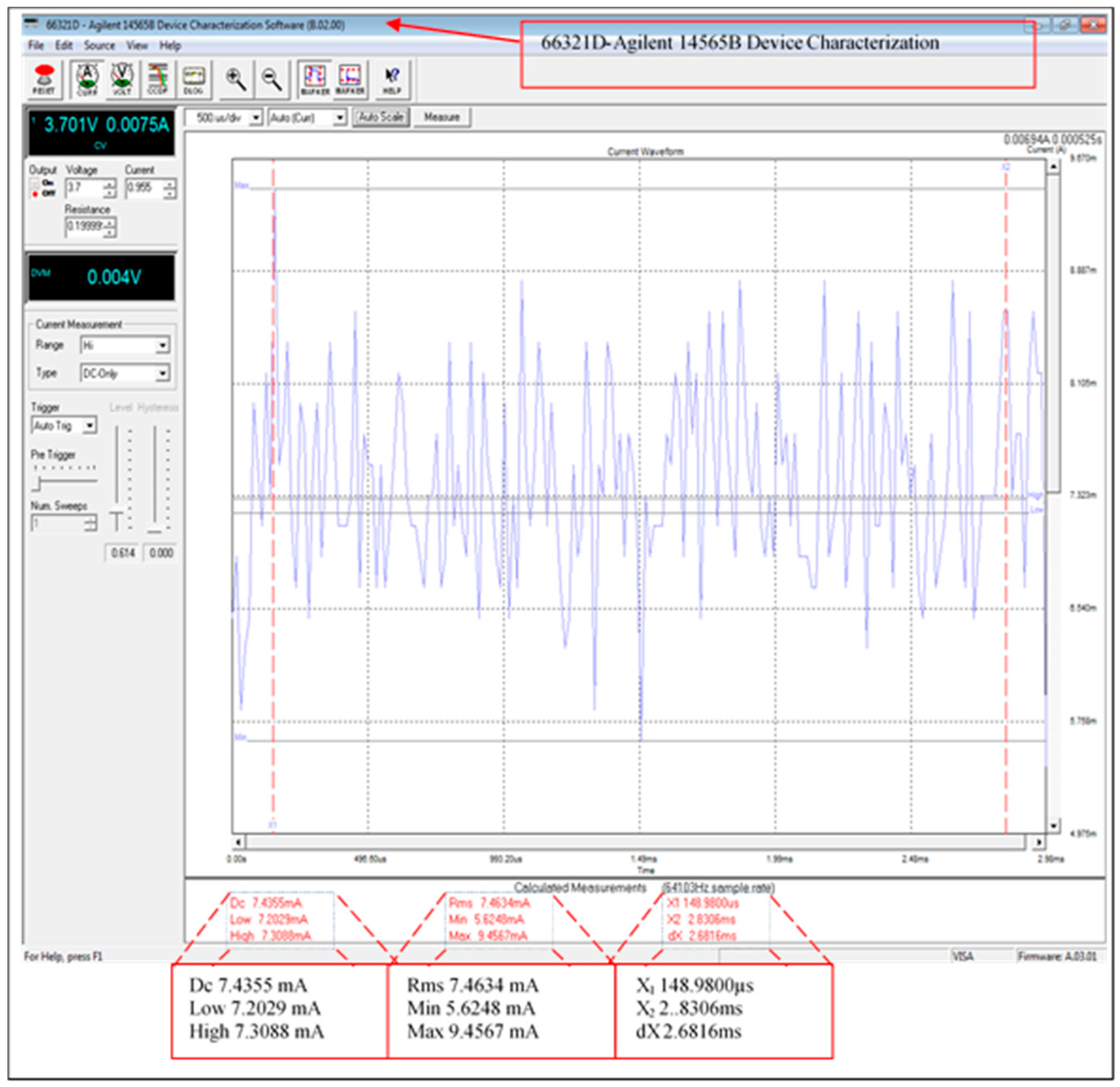
Figure 12 illustrates the average current consumption of the fully functional scheme including the XBee transmission module current consumption. However, the current consumption of the transmission data has been improved by using sleeping schedules for the receiving/transmitting modules (the XBee current consumption is from 37 to 64 mA with the mode ON fully operational). The measurements were taken using the 66321D-Agilent with input 3.689 V and 0.19999 Ω resistance. The average current consumption of the XBee module is 64.9123 mA when the leader node is fully operational, this was significantly improved by introducing the sleeping mode feature as described below.
The XBee module in the leader node will return to sleeping mode after transmitting/receiving data.
Figure 13 shows the average current consumption of the sleeping mode of the XBee modules in the scheme. Where this is the total current consumption during data processing except for the transmission/receiving phase. The measured current consumption has been improved from 64.9123 to 7.4355 mA, which is a reduction of over 88%.
Table 6 provides the current consumption of the scheme modes, this includes when the XBee module is fully functional and sleeping.
5. Discussion and Comparisons
In [
19] Piyare et al. evaluated the performance of ZigBee networks based on XBee modules in terms of RSSI. The experiment was based on the single-hop and multi-hop in line network topology. In this experiment, average values of the RSSI was measured after transmitting 50 packets of 30 Bytes with varied distance between the sender and the receiver.
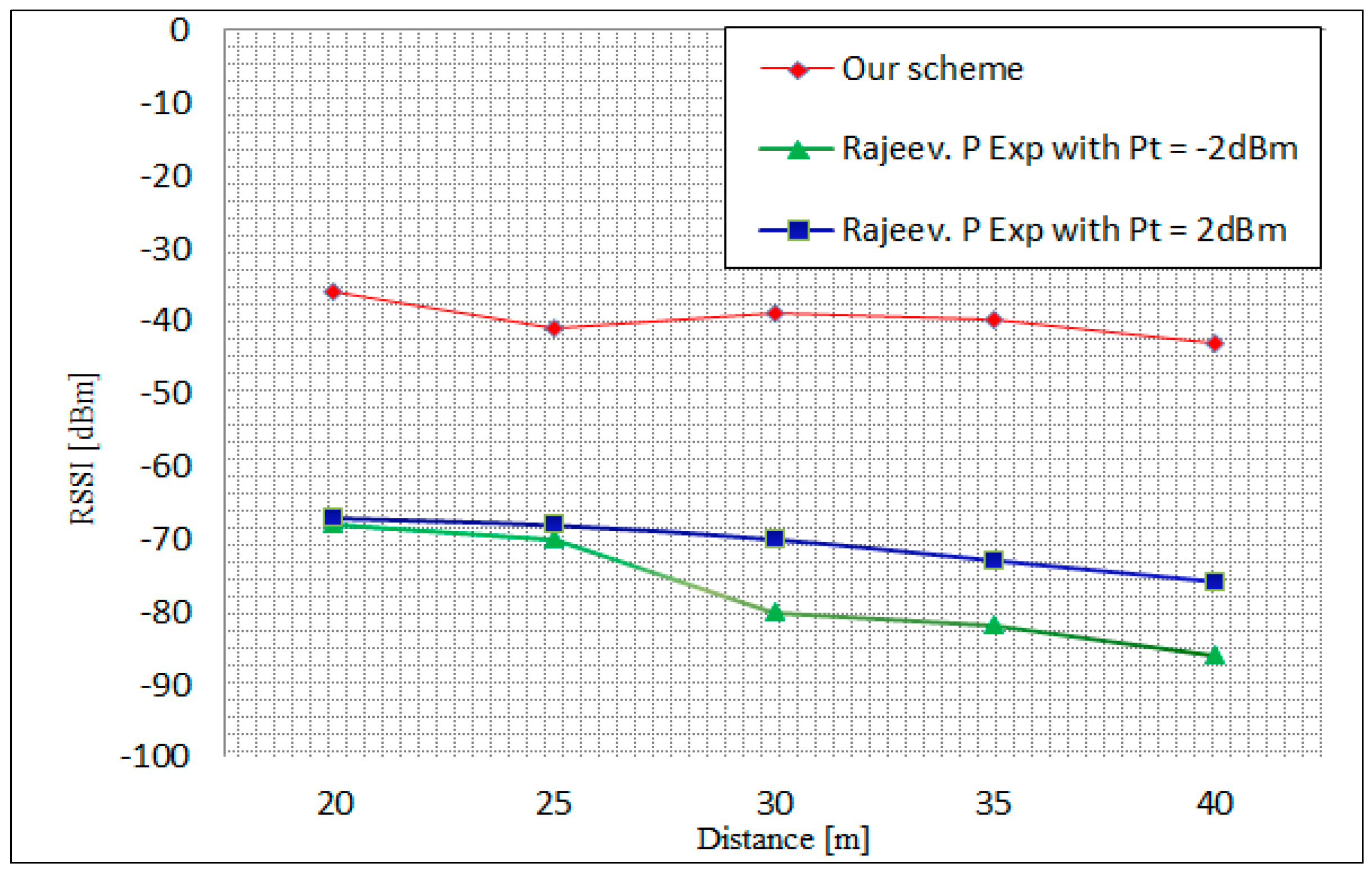
Figure 14 illustrates the relationship between the measured RSSI and the distance using two different transmit power values of −2 dBm and 2 dBm. In our scheme, the measurements have been taken after transmitting 300 encrypted packets of 97 Bytes in an outdoor environment. As shown in
Figure 14, the three measured values of RSSI decreased when the distance between the sender and the receiver was increased. However, our scheme presents strong signal strength values at all distance scenarios, where the strongest value is −36 dBm at 20 m and the weakest value was −43 dBm at 40 m. In the 20 and 30 m distances, the fluctuation in this scheme is graphed and can be correlated with interference from other networks, e.g., reflection phenomena.
When comparing the work undertaken, it was compared to Jorg and Guangyu [
12].
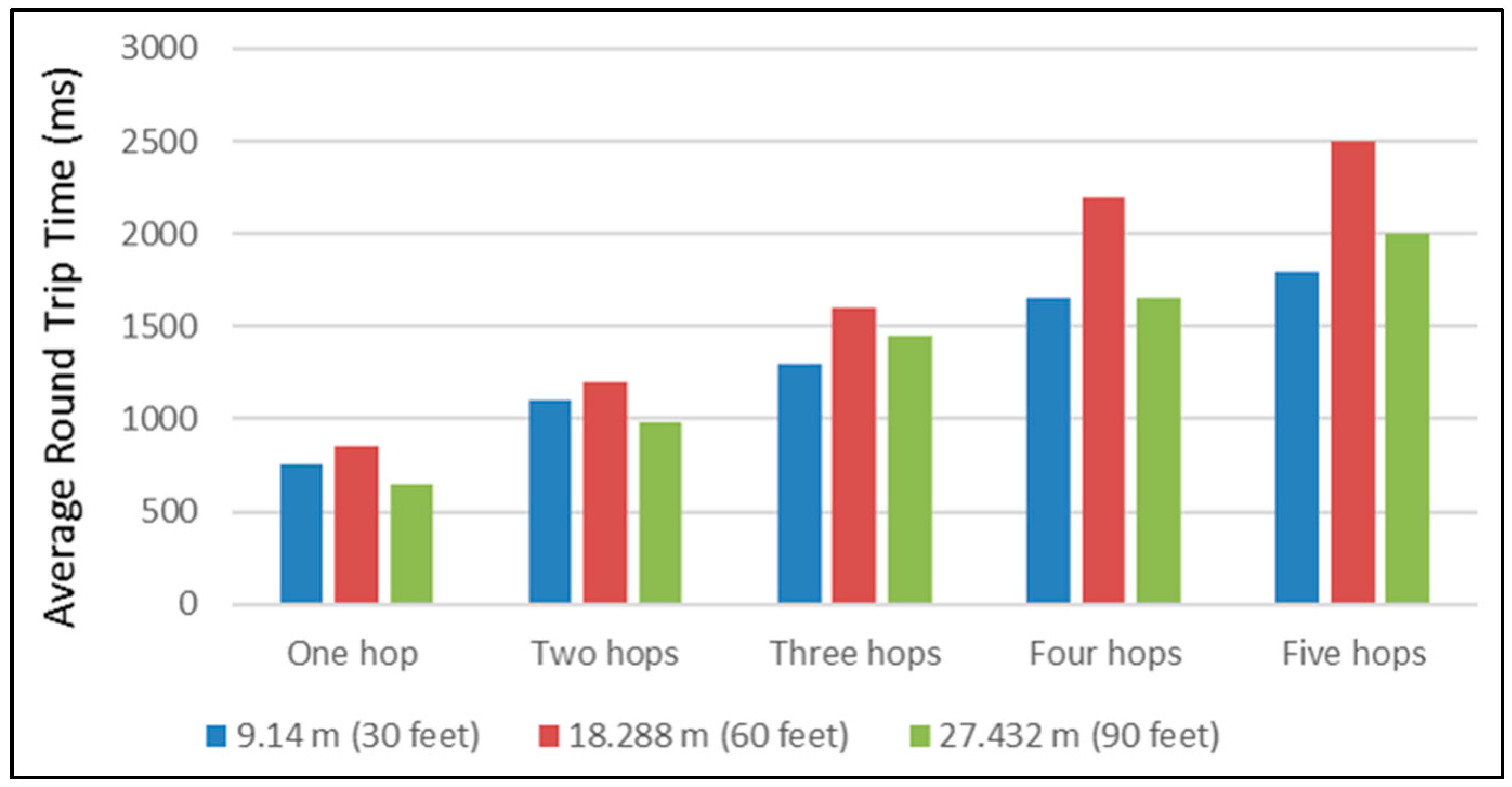
Figure 15 presents their result of the average Round Trip Time RTT of line network topology. The experimental setup consisted of multiple different scenarios of distance and number of repeaters. Initially, the scenarios were: 9.14 m (30 feet), 18.288 m (60 feet), and 27.432 m (90 feet) between nodes, with one hop, two hops, three hops, four hops, and five hop scenarios (one hop per repeater). Furthermore,
Figure 16 depicts the three scenarios of our scheme, which are one repeater, two repeaters, and three repeaters in 80, 120 and 160 m distances between the sender and the gateway.
In the cases of 40 and 60 m distances between the nodes in the single repeater scenario, both schemes presented approximately the same time delay. However, in the two repeaters scenario, at a distance of 55 m the setup showed a time delay of 1033.172 ms and [
12] presents approximately 1300 ms. In addition, the time delay between our scheme and [
12] was around 170 ms in the same scenario at the distance of 27 m. Comparatively, travelling packets in the scheme being presented needed larger delays in comparison with [
12] at distance of 40 m in the case of the three repeaters scenario. Generally, the time of receiving transmitting packets increase with the number of repeaters.
In
Table 7 and
Table 8, a comprehensive comparison between the scheme presented and three other schemes in terms of cryptographic scheme, size and number of stored security keys, memory space used by schemes, maintenance and re-keying strategy, scheme implementation environment, nodes and coordination, is shown.