Geometric Distribution-Based Readers Scheduling Optimization Algorithm Using Artificial Immune System
Abstract
:1. Introduction
- By using signal-to-interference-plus-noise (SINR) to explain the reduction in interrogation range, a resource allocation model is constructed with two constraint conditions which are used to decrease the multiple-reader interference.
- A geometric probability function is introduced to replace the uniform probability function to produce the feasible scheduling schemes, which ensures that readers could operate in a fair way.
- Artificial immune system with clone operator, mutation operator and suppression operator is introduced to optimize the feasible scheduling schemes. In mutation process, both of the single-bit mutation operator and the region-bits mutation operator are imported to deal with the different cloned antibodies to accelerate the optimization process and convergence speed.
2. Resource Allocation Model in Centralized MRE under EPCGlobal C1G2
2.1. General Description with Assumptions
- Readers are randomly distributed over an area in two dimensions.
- Any reader has only two states, active and inactive, where only the readers in active operate and interfere with other active ones.
- The interference power from multiple interfering readers seen by the desired reader is additive.
2.2. Multiple-Reader Interference Problem in Centralized MRE
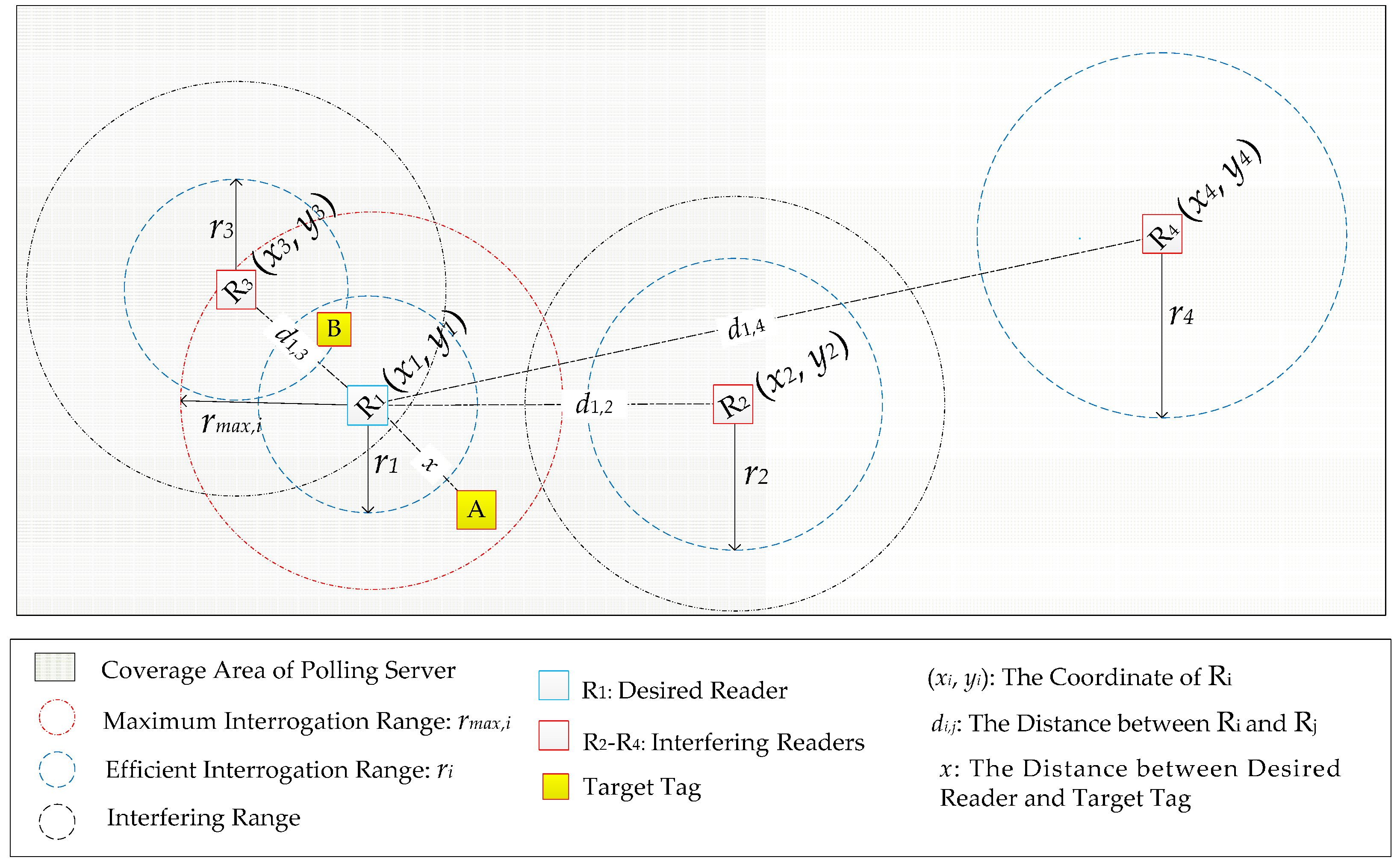
- Multiple readers are simultaneously operating at the same frequency channel, which leads to the signals generated by multiple readers interfere with the reception system of the desired reader. In Figure 1, R1 suffers from this kind of interference if R2 and R3 are simultaneously operating with R1 at the same frequency channel. As a result, r1 is smaller than the distance x between R1 and the target tag A, R1 could not successfully detect A. To ensure that R1 could operate with a larger interrogation range to cover tag A, R1 with R2 and R3 should be scheduled to operate at different frequency channels and/or at different times by polling server.
- Multiple readers operating at independently frequency channels try to simultaneously detect the same tag located in the overlapped area of their effective interrogation ranges. In Figure 1, tag B locates in the overlapped interrogation area of R1 and R3, where B receives electromagnetic waves from both R1 and R3 simultaneously, it is not able to select a particular reader to communicate even if R1 and R3 are operating at the different frequency channels. To avoid this scenario, R1 and R3 should operate asynchronously which are scheduled by polling server as well.
2.3. The Proposed Resource Allocation Model in Centralized MRE
- CHi(k) ≠ CHj(k) if dj,i < d f-min
- ωj(k) = 0 if dj,i ≤ ds-min(ΔCHj,i(k))
3. Geometric Distribution-Based Multiple-Reader Scheduling Optimization Algorithm Using Artificial Immune System (GD-MRSOA-AIS)
- GD: Geometric distribution function (GD) combined with the fairness consideration is introduced to randomize the feasible scheduling schemes with lower interferences which satisfy the constraint conditions in Equation (8). Details are described in Section 3.1;
- AIS: Artificial immune system optimization (AIS) is to optimize these feasible scheduling schemes as the optimal scheduling scheme for readers fairly operating with larger effective interrogation range. Details are presented in Section 3.2.
3.1. Feasible Scheduling by Geometric Distribution Function
| Algorithm 1: Pseudocode for Feasible Solutions Generation by Sift_Function |
| Sift_Function |
| 1 set i = 1; |
| 2 while i ≤ NReader do |
| 3 set ; |
| 4 set ; |
| 5 set ki = NSlot; |
| 6 for z = 1 to NSlot do |
| 7 if >li then // Contend for operating time slot |
| 8 set ki = z; // Ri is operating at zth time slot |
| 9 break; |
| 10 end if |
| 11 end for |
| 12 randomize CHi(ki) from CH; // Allocate a frequency channel for Ri |
| 13 for j = 1 to NReader and j ≠ i do |
| 14 if j∈ISRi then // Constraint Condition: CHi(k) ≠ CHj(k) if j ∈ISRi |
| 15 randomize CHj(ki) from CH-{CHi(ki)}; |
| 16 if dj,i ≤ ds-min(|CHj(ki)-CHi(ki)|) then // ωj(k) = 0 if dj,i ≤ ds-min(ΔCHj,i(k)) |
| 17 set CHj(ki) = 0; |
| 18 end if |
| 19 end if |
| 20 end for |
| 21 i++; |
| 22 end while |
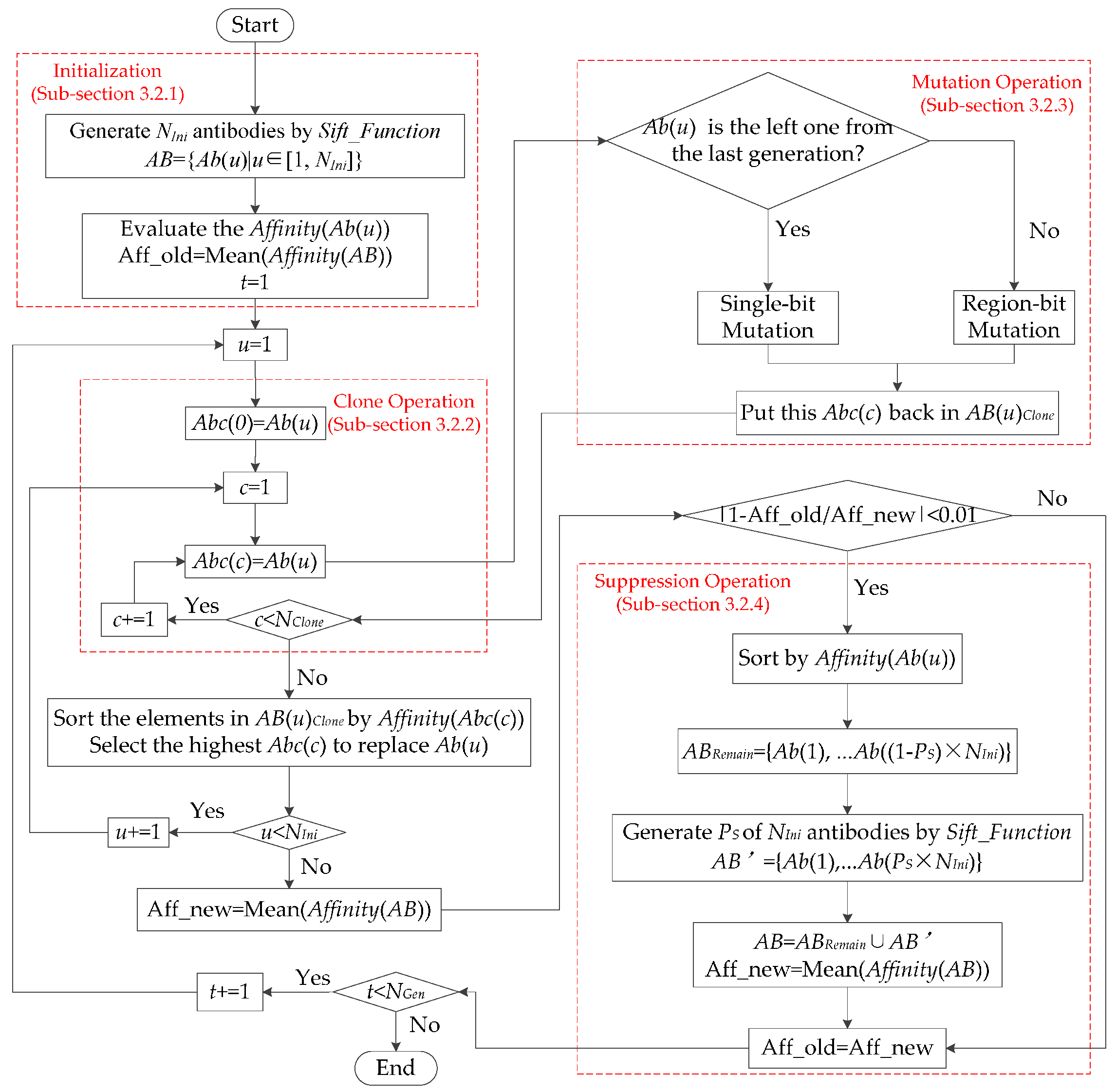
3.2. Optimal Scheduling by Artificial Immune System Optimization
3.2.1. Initialization
3.2.2. Clone Operation
3.2.3. Mutation Operation
| Algorithm 2: Pseudocode for Single-bit Mutation |
| Single-bit _Operator () |
| 1 Randomly determine a bit CHi(k) of Ri from Abc(c) to be mutated; |
| 2 for j = 1 to NReader and j ≠ i |
| 3 if ISRj∩ISRi ≠ ∅ |
| 4 CH = CH-{CHj(k)}; |
| 5 end if |
| 6 end for |
| 7 if CH ≠ ∅ |
| 8 Randomize CHi(k) from CH; |
| 9 else |
| 10 CHi(k) = 0; |
| 11 end if |
| Algorithm 3: Pseudocode for Region-bits Mutation |
| Region-bits _Operator () |
| 1 Randomly determine a bit CHi(k) of Ri from Abc(c) to be mutated; |
| 2 for(q = k; q ≤ k + L; q++) |
| 3 for j = 1 to NReader and j ≠ i |
| 4 if ISRj∩ISRi ≠ ∅ |
| 5 CH = CH-{CHj(q)}; |
| 6 end if |
| 7 end for |
| 8 if CH ≠ ∅ |
| 9 Randomize CHi(q) from CH; |
| 10 else |
| 11 CHi(q) = 0; |
| 12 end if |
| 13 end for |
3.2.4. Suppression Operation
| Algorithm 4: Pseudocode for Optimal Scheme Generation by using proposed-AIS Optimization |
| AIS_Optimization |
| 1 Set NIni, NClone, NGen, PS; |
| 2 int t, u, c; |
| 3 float aff_old, aff_new; |
| 4 Initialization: Run Sift_Function in NIni times to construct set AB; |
| 5 Evaluate the affinity value of all elements in AB and average them as aff_old; |
| 6 while t< NGen do |
| 7 for(u = 1; u ≤ NIni; u++) |
| 8 Produce NClone clones for uth antibody as its children antibodies; // Clone Operation |
| 9 for(c = 1; c ≤ NClone; c++) |
| 10 Mutate cth child antibody following the Mutation Operation; |
| 11 end for |
| 12 Evaluate the affinity value of all children antibodies and their parent antibody; |
| 13 Remain the antibody with the highest affinity value; |
| 14 Evaluate the affinity value of all candidate antibodies and average them as aff_new; |
| 15 end for |
| 16 if(aff_new is not significantly bigger than aff_old) // Suppression Operation |
| 17 Sort the candidate antibodies by their affinity values; |
| 18 Suppress PS antibodies with lowest affinity values; |
| 19 Produce PS new recruited antibodies by Sift_Function satisfying the constraint conditions; |
| 20 end if |
| 21 end while |
4. Simulations and Results
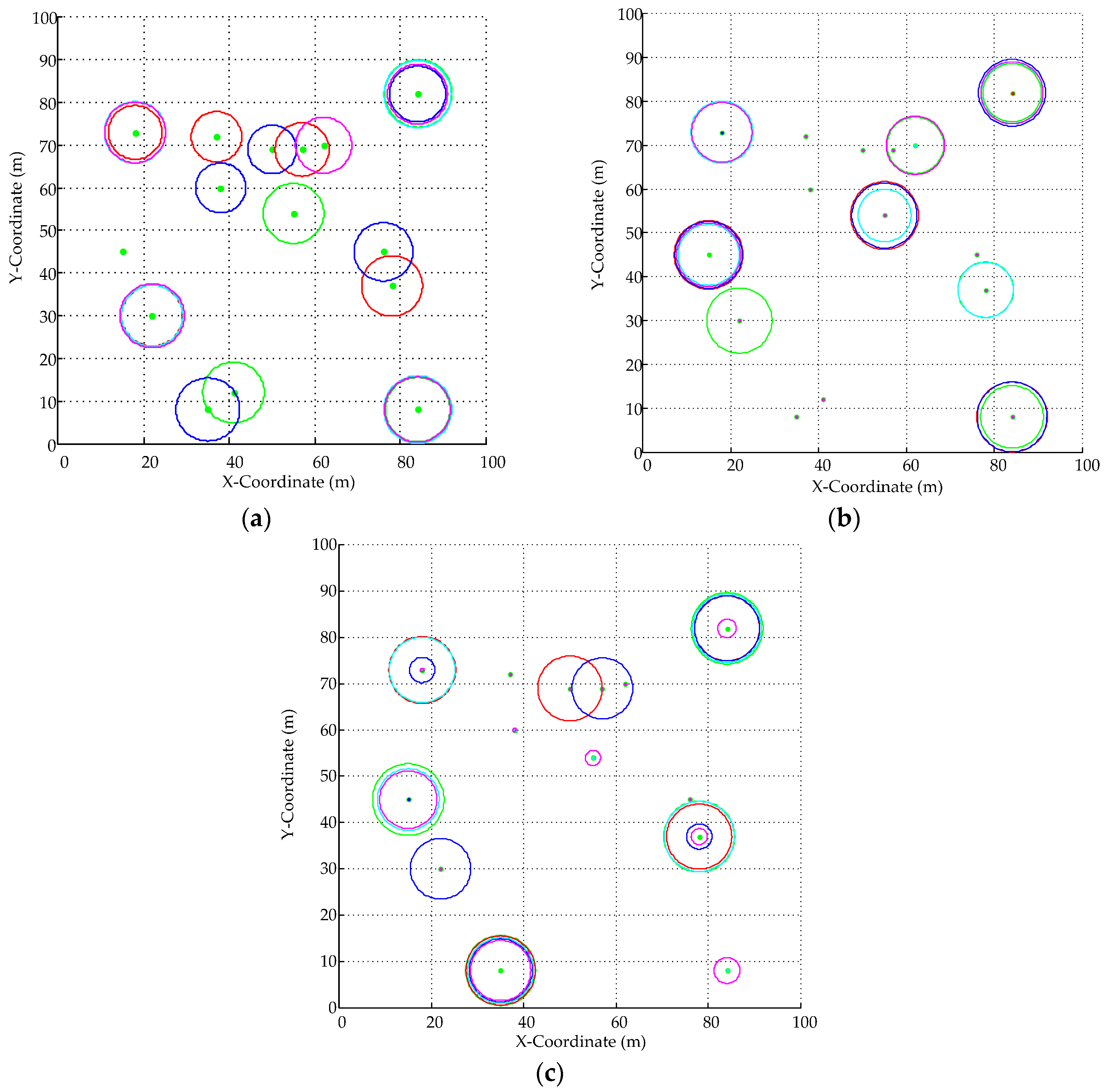
- The number of readers NReader = 15 with fixed positions among GD-MRSOA-AIS, MRSOA-AIS and LIs. Meanwhile, the advantage of Sift_Function and proposed-AIS optimization is illustrated by comparisons of GD-MRSOA-AIS, MRSOA-AIS and LIs.
- Variable NReader with randomized positions among GD-MRSOA-AIS, MRSOA-AIS and LIs.
4.1. Case Study: NReader = 15, NSlot = 5, NFreq = 10
4.2. Variable NReader with Fixed NSlot = 5 and NFreq = 10 in Randomized Positions
5. Conclusions
- It only focuses on the scenario of multiple readers in known position with randomized tags in fixed positions, and ignores the new entrancing tags with variable population.
- It only solves the resource allocation problem for multiple readers scheduling to interrogate the tags in centralized MRE, but ignores the identification problem (i.e., tag-to-tag collision) in data transmission process.
Acknowledgments
Author Contributions
Conflicts of Interest
Appendix A
| Parameter | Description | Value | |
|---|---|---|---|
| Etag | The effective power reflection coefficient of the tag | 0.1 | |
| αbw | The normalized spectrum power | 0.86 | |
| γ | The path loss exponent | 2.5 | |
| Md | The modulation depth | 0.1 | |
| H | The fading coefficient in the channel between Ri and Rj | 1 | |
| Pmin | The minimum required power for tag operation | −15 dB m | |
| Pi | The signal power of Ri | 30 dB m | |
| P0 | The referenced path loss at the distance of 1 m | −31.6 dB m | |
| Noi | The noise power of Ri | −90 dB m | |
| SINRmin | The minimum SINR | 11.6 dB | |
| GT | The reader antenna transmitting gain | 6 dB | |
| GR | The reader antenna receiving gain | 6 dB | |
| βmask(·) for MRE | The function of the spectrum mask in multiple-reader environment | ΔCHj,i(k) = 0 | 0 dB |
| ΔCHj,i(k) = 1 | −20 dB | ||
| ΔCHj,i(k) = 2 | −50 dB | ||
| ΔCHj,i(k) = 3 | −60 dB | ||
| ΔCHj,i(k) ≥ 4 | −65 dB | ||
References
- Vlachos, I.P. A Hierarchical Model of the Impact of RFID Practices on Retail Supply Chain Performance. Expert Syst. Appl. 2014, 41, 5–15. [Google Scholar] [CrossRef]
- Arkan, I.; Landeghem, H.V. Evaluating the Performance of a Discrete Manufacturing Process using RFID: A Case Study. Robot. Comput. Integr. Manuf. 2013, 29, 502–1512. [Google Scholar] [CrossRef]
- Enrique, V.; Antonio, A.; Carlos, C. Evolution of RFID Applications in Construction: A Literature Review. Sensors 2015, 15, 15988–16008. [Google Scholar]
- Decarli, N.; Guidi, F.; Dardari, D. Passive UWB RFID for Tag Localization: Architectures and Design. IEEE Sens. J. 2016, 16, 1385–1397. [Google Scholar] [CrossRef]
- Bueno-Delgado, M.V.; Pavon-Marino, P. A Centralized and Aligned Scheduler for Passive RFID Dense Reader Environments working under EPCglobal Standard. Simul. Model. Pract. Theory 2013, 34, 172–185. [Google Scholar] [CrossRef]
- Wang, D.; Wang, J.; Zhao, J.Y. A Novel Solution to the Reader Collision Problem in RFID System. In Proceedings of the IEEE International Conference Wireless Communication, Networking Mobile Computing, Wuhan, China, 22–24 September 2006; pp. 1–4.
- Birari, S.M.; Lyer, S. Pulse: A MAC Protocol for RFID Networks. In Proceedings of the International Conference on Embedded and Ubiquitous Computing (EUC 2005), Nagasaki, Japan, 6–9 December 2005; pp. 1036–1046.
- Eom, J.B.; Yim, S.B.; Lee, T.J. An Efficient Reader Anti-collision Algorithm in Dense RFID Networks with Mobile RFID Readers. IEEE Trans. Ind. Electron. 2009, 56, 2326–2336. [Google Scholar]
- Song, I.C.; Hong, S.H.; Chang, K.H. An Improved Reader Anti-collision Algorithm based on Pulse Protocol with Slot Occupied Probability in Dense Reader Mode. In Proceedings of the IEEE Vehicular Technology Conference, Barcelona, Spain, 26–29 April 2009; pp. 1–5.
- Waldrop, J.; Engels, D.W.; Sarma, S.E. Colorwave: A MAC for RFID Reader Networks. In Proceedings of IEEE International Conference on Wireless Communications and Networking (WCNC), New Orleans, LA, USA, 20–20 March 2003; pp. 1701–1704.
- Ho, J.; Engels, D.W.; Sarma, S.E. HiQ: A Hierarchical Q-learning Algorithm to Solve the Reader Collision Problem. In Proceedings of the International Symposium on Applications and the Internet Workshops (SAINT), Phoenix, AZ, USA, 23–27 January 2006; pp. 1–4.
- Seo, H.; Lee, C. A New GA-based Resource Allocation Scheme for a Reader-to-reader Interference Problem in RFID System. In Proceedings of the IEEE International Conference on Communications (ICC), Cape Town, South Africa, 23–27 May 2010; pp. 1–5.
- Chen, H.N. RFID Network Planning using a Multi-swarm Optimizer. J. Netw. Comput. Appl. 2011, 34, 888–901. [Google Scholar] [CrossRef]
- Li, Z.H.; He, C.H. Optimal Scheduling-based RFID Reader-to-reader Collision Avoidance Method using Artificial Immune System. Appl. Soft Comput. 2013, 13, 2557–2568. [Google Scholar] [CrossRef]
- Li, Z.H.; Li, J.M.; He, C.H. Artificial Immune Network-based Anti-collision Algorithm for Dense RFID Readers. Expert Syst. Appl. 2014, 41, 4798–4810. [Google Scholar] [CrossRef]
- Li, Z.H.; Li, J.M.; He, C.H.; Tang, C.P.; Zhou, J.Y. RFID Reader-to-reader Collision Avoidance Model with Multiple-density Tag Distribution solved by Artificial Immune Network Optimization. Appl. Soft Comput. 2013, 30, 249–264. [Google Scholar] [CrossRef]
- Li, Z.H.; He, C.H.; Huang, X. RFID Reader Anti-collision Algorithm using Adaptive Hierarchical Artificial Immune System. Expert Syst. Appl. 2014, 41, 2126–2133. [Google Scholar] [CrossRef]
- Tang, S.J.; Yuan, J.; Li, X.Y.; Chen, G.H.; Liu, Y.H.; Zhao, J.Z. Raspberry: A Stable Reader Activation Scheduling Protocol in Multi-reader RFID Systems. In Proceedings of the 17th IEEE International Conference on Network Protocols (ICNP), Princeton, NJ, USA, 13–16 October 2009; pp. 304–313.
- Kim, D.Y.; Yoon, H.G.; Jang, B.J.; Yook, J.G. Effects of Reader-to-reader Interference on the UHF RFID Interrogation Range. IEEE Trans. Ind. Electron. 2009, 56, 2337–2346. [Google Scholar]
- Vita, D.; Iannaccone, G. Design Criteria for the RF Section of UHF and Microwave Passive RFID Transponders. IEEE Trans. Microw. Theory Tech. 2005, 53, 2978–2990. [Google Scholar] [CrossRef]
- Cha, K.; Ramachandran, A.; Jagannathan, S. Adaptive and Probabilistic Power Control Algorithms for Dense RFID Reader Network. In Proceedings of the IEEE on Networking, Sensing and Control (ICNSC), Ft. Lauderdale, FL, USA, 23–25 April 2006; pp. 474–479.
- EPC Global. UHF Air Interface Protocol Standard Generation2/Version2. Available online: http://www.gs1.org/gsmp/kc/epcglobal/uhfc1g2 (accessed on 14 November 2016).
- Safa, H.; I-Hajj, W.E.; Meguerditchian, C. A Distributed Multi-channel Reader Anti-collision Algorithm for RFID Environments. Comput. Commun. 2015, 64, 44–56. [Google Scholar] [CrossRef]
- Tay, Y.C.; Jamieson, K.; Balakrishnan, H. Collision-Minimizing CSMA and its Applications to Wireless Sensor Networks. IEEE J. Sel. Areas Commun. 2004, 22, 1048–1057. [Google Scholar] [CrossRef]
- Bueno-Delgado, M.V.; Ferrero, R.; Gandino, F.; Pavon-Marino, P.; Rebaudengo, M. A Geometric Distribution Reader Anti-Collision Protocol for RFID Dense Reader Environments. IEEE Trans. Autom. Sci. Eng. 2013, 10, 296–306. [Google Scholar] [CrossRef]
- Ferrero, R.; Gandino, F.; Montrucchio, B.; Rebaudengo, M. A Fair and High Throughput Reader-to-reader Anti-collision Protocol in Dense RFID Networks. IEEE Trans. Ind. Inf. 2012, 8, 697–706. [Google Scholar] [CrossRef]



| =Frequency Channel | ≠Frequency Channel | |
|---|---|---|
| =time slot | dj,i > df-min | df-min ≥ dj,i > ds-min(ΔCHj,i(k)) |
| ≠time slot | ds-min(ΔCHj,i(k)) ≥ dj,i > 0 | ds-min(ΔCHj,i(k))≥ dj,i > 0 |
| ΔCHj,i(k) | 0 | 1 | 2 | 3 | ≥4 |
|---|---|---|---|---|---|
| ds-min(ΔCHj,i(k)) | 0.0269 m | 0.8452 m | 2.6970 m | 6.7458 m | 10.339 m |
| Symbol | Description |
|---|---|
| AB | The candidate antibody population |
| Ab(u) | The uth antibody |
| ab(u)i | The ith antibody segment in Ab(u) |
| ABRemain | The set for remained antibodies |
| Ab(u)Clone | The clone pool for Ab(u) |
| Affinity(·) | Affinity function |
| Aff_old | The mean affinity value of the previous generation |
| Aff_new | The mean affinity value of the current generation |
| CHi(k) | The kth bit in ab(u)i |
| NIni | The population size of AB |
| NClone | The cloned multiplier |
| NGen | The generation multiplier |
| L | Region-bits mutation length |
| PS | The suppression percentage |
| Parameter | Value |
|---|---|
| The number of available time slots (NSlot) | 5 |
| The number of available frequency channels (NFreq) | 10 |
| Initialized candidate population size (NIni) | 40 |
| Cloned Multiplier (NClone) | 5 |
| Maximum generation (NGen) | 150 |
| Suppression percentage (PS) | 25% |
| GD-MRSOA-AIS | MRSOA-AIS | LIs | |||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| TSk | TS1 | TS2 | TS3 | TS4 | TS5 | TS1 | TS2 | TS3 | TS4 | TS5 | TS1 | TS2 | TS3 | TS4 | TS5 | ||
| CHi(k) | |||||||||||||||||
| Ri | |||||||||||||||||
| R1 | 0 | 0 | 0 | 0 | 0 | 0 | 6 | 7 | 1 | 1 | 7 | 0 | 0 | 3 | 5 | ||
| R2 | 0 | 1 | 0 | 7 | 10 | 0 | 0 | 0 | 10 | 7 | 0 | 1 | 8 | 7 | 1 | ||
| R3 | 0 | 10 | 0 | 5 | 1 | 0 | 3 | 0 | 0 | 0 | 0 | 0 | 5 | 0 | 0 | ||
| R4 | 0 | 0 | 10 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | 3 | 1 | 1 | 3 | ||
| R5 | 0 | 0 | 1 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 1 | ||
| R6 | 0 | 5 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | ||
| R7 | 5 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | ||
| R8 | 0 | 0 | 5 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 10 | 0 | 0 | 0 | ||
| R9 | 7 | 0 | 0 | 0 | 0 | 0 | 2 | 10 | 5 | 0 | 0 | 0 | 0 | 0 | 8 | ||
| R10 | 0 | 8 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 3 | 0 | 0 | ||
| R11 | 0 | 0 | 0 | 0 | 8 | 9 | 0 | 0 | 0 | 5 | 0 | 0 | 0 | 0 | 0 | ||
| R12 | 0 | 0 | 8 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | 0 | ||
| R13 | 0 | 3 | 0 | 0 | 0 | 7 | 0 | 0 | 3 | 0 | 10 | 7 | 7 | 10 | 7 | ||
| R14 | 1 | 0 | 0 | 9 | 6 | 1 | 9 | 2 | 0 | 0 | 0 | 0 | 0 | 0 | 10 | ||
| R15 | 10 | 0 | 3 | 3 | 3 | 5 | 0 | 5 | 7 | 10 | 3 | 5 | 10 | 5 | 9 | ||
| NReader | Algorithm | Best (Unit: m2) | Worst (Unit: m2) | Mean (Unit: m2) | Average Radius (Unit: m) | Jain Index (IJain) |
|---|---|---|---|---|---|---|
| 4 | GD-MRSOA-AIS | 3886.166 | 2459.977 * | 3190.954 * | 6.906 * | - |
| MRSOA-AIS | 3976.631 * | 1918.756 | 3078.580 | 6.784 | - | |
| LIs | 3570.661 | 1512.397 | 3041.527 | 6.573 | - | |
| 8 | GD-MRSOA-AIS | 4392.362 * | 3287.613 * | 3907.504 * | 4.308 * | 42.19% * |
| MRSOA-AIS | 4293.650 | 3180.301 | 3790.565 | 4.174 | 25.00% | |
| LIs | 4316.239 | 3263.520 | 3859.630 | 4.252 | 29.69% | |
| 12 | GD-MRSOA-AIS | 3910.000 * | 3328.207 * | 3539.014 * | 2.670 * | 27.08% * |
| MRSOA-AIS | 3765.571 | 3014.043 | 3481.625 | 2.620 | 13.89% | |
| LIs | 3671.977 | 2977.352 | 3428.592 | 2.639 | 18.06% | |
| 16 | GD-MRSOA-AIS | 3780.408 * | 3356.667 * | 3533.103 * | 2.027 * | 27.34% * |
| MRSOA-AIS | 3612.826 | 2901.954 | 3471.431 | 1.974 | 19.92% | |
| LIs | 3437.009 | 3128.828 | 3270.978 | 1.963 | 21.88% | |
| 20 | GD-MRSOA-AIS | 3331.845 | 2935.414 * | 3133.686 | 1.443 | 70.50% * |
| MRSOA-AIS | 3369.615 * | 2901.954 | 3160.941 * | 1.463 * | 40.25% | |
| LIs | 2869.225 | 2297.590 | 2528.864 | 1.346 | 45.50% | |
| 24 | GD-MRSOA-AIS | 3232.966 * | 2550.474 * | 2909.812 * | 1.229 * | 68.06% * |
| MRSOA-AIS | 3206.098 | 2279.184 | 2830.733 | 1.195 | 43.75% | |
| LIs | 2151.093 | 1874.913 | 2035.651 | 1.020 | 42.36% | |
| 28 | GD-MRSOA-AIS | 3068.395 * | 2436.688 | 2737.177 * | 0.999 * | 64.29% * |
| MRSOA-AIS | 2675.789 | 2586.912 * | 2616.538 | 0.923 | 35.71% | |
| LIs | 1859.409 | 1532.377 | 1670.742 | 0.814 | 32.14% |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Duan, L.; Wang, Z.J.; Duan, F. Geometric Distribution-Based Readers Scheduling Optimization Algorithm Using Artificial Immune System. Sensors 2016, 16, 1924. https://doi.org/10.3390/s16111924
Duan L, Wang ZJ, Duan F. Geometric Distribution-Based Readers Scheduling Optimization Algorithm Using Artificial Immune System. Sensors. 2016; 16(11):1924. https://doi.org/10.3390/s16111924
Chicago/Turabian StyleDuan, Litian, Zizhong John Wang, and Fu Duan. 2016. "Geometric Distribution-Based Readers Scheduling Optimization Algorithm Using Artificial Immune System" Sensors 16, no. 11: 1924. https://doi.org/10.3390/s16111924






