Interference Mitigation Schemes for Wireless Body Area Sensor Networks: A Comparative Survey
Abstract
:1. Introduction
2. Coexistence and Interference in WBASNs
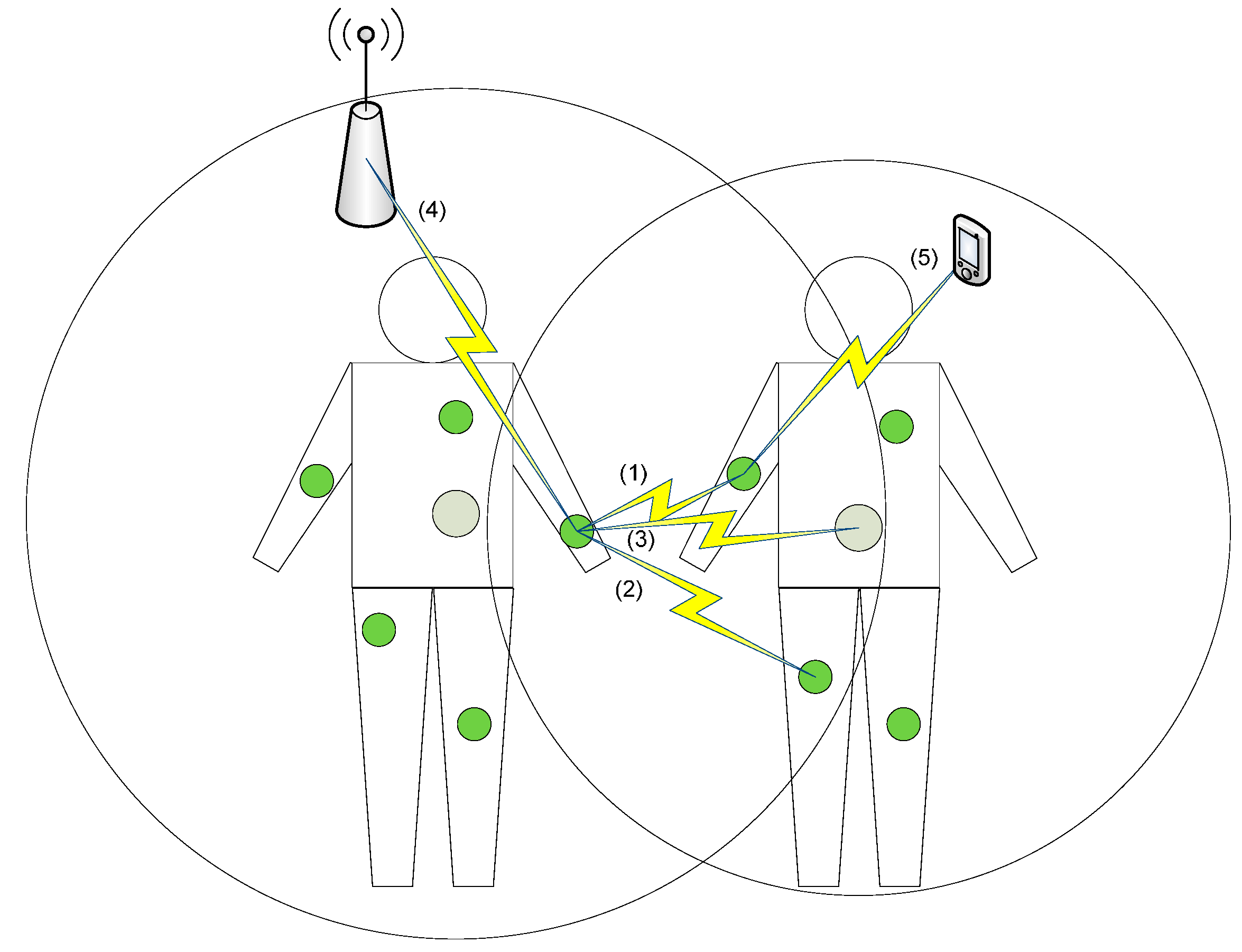
2.1. Inter-WBASN Coexistence and Interference
2.2. Inter-Domain Coexistence and Interference
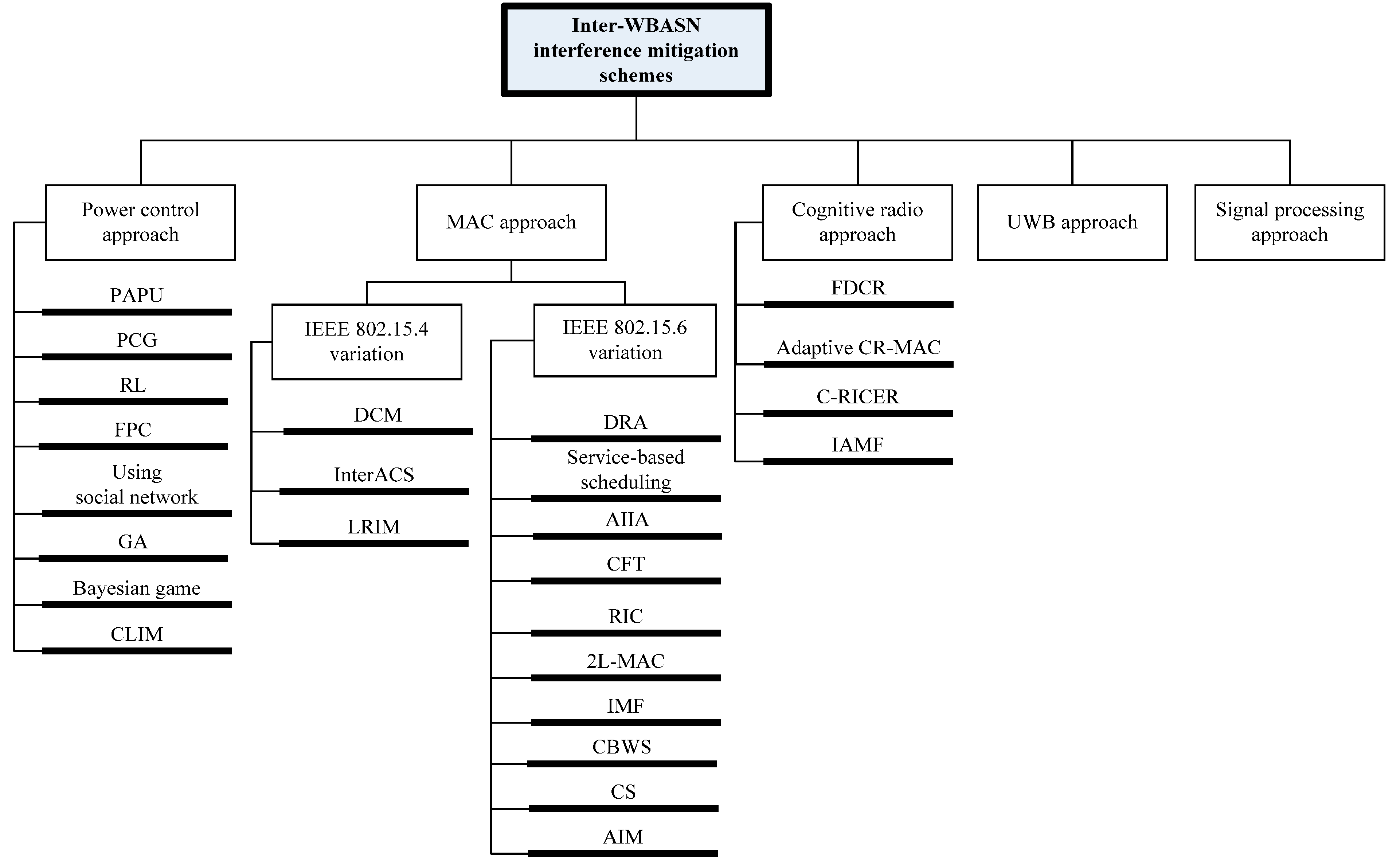
3. Interference Mitigation Schemes
3.1. Power Control Approach
3.1.1. Proactive Power Update
3.1.2. A Power Control Game: Nonlinear and Adaptive Power Pricing Function
3.1.3. Reinforcement Learning in Power Control Games
3.1.4. Fast Converging Fuzzy Power Controller
3.1.5. PCG Using Social Networks
3.1.6. Power Allocation Using GA
3.1.7. Bayesian Game Power Control Scheme
3.1.8. Cross-Layer Interference Management
3.2. MAC Approach
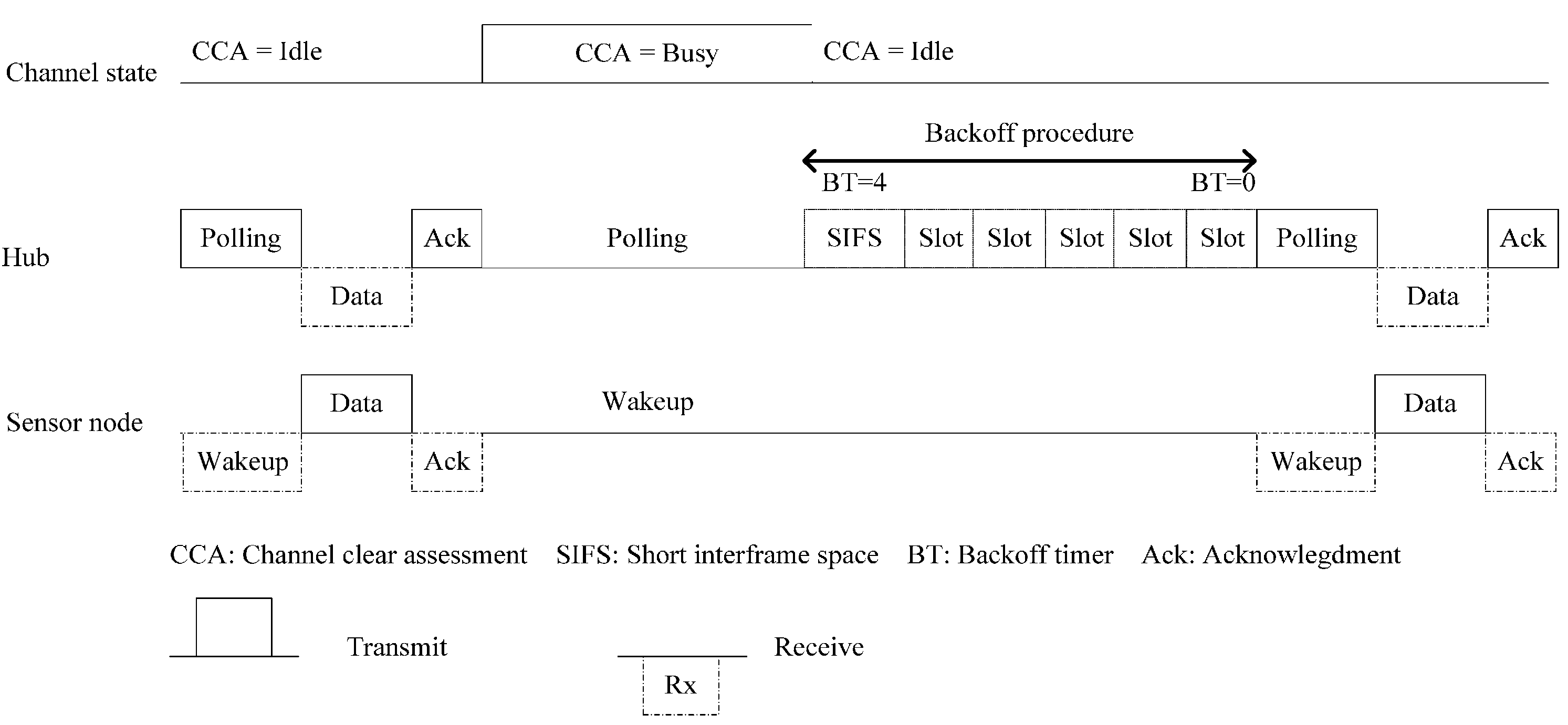
3.2.1. Dynamic Coexistence Management
3.2.2. Interference-Aware Channel Switching
3.2.3. Lightweight and Robust Interference Mitigation Scheme
3.2.4. Dynamic Resource Allocation
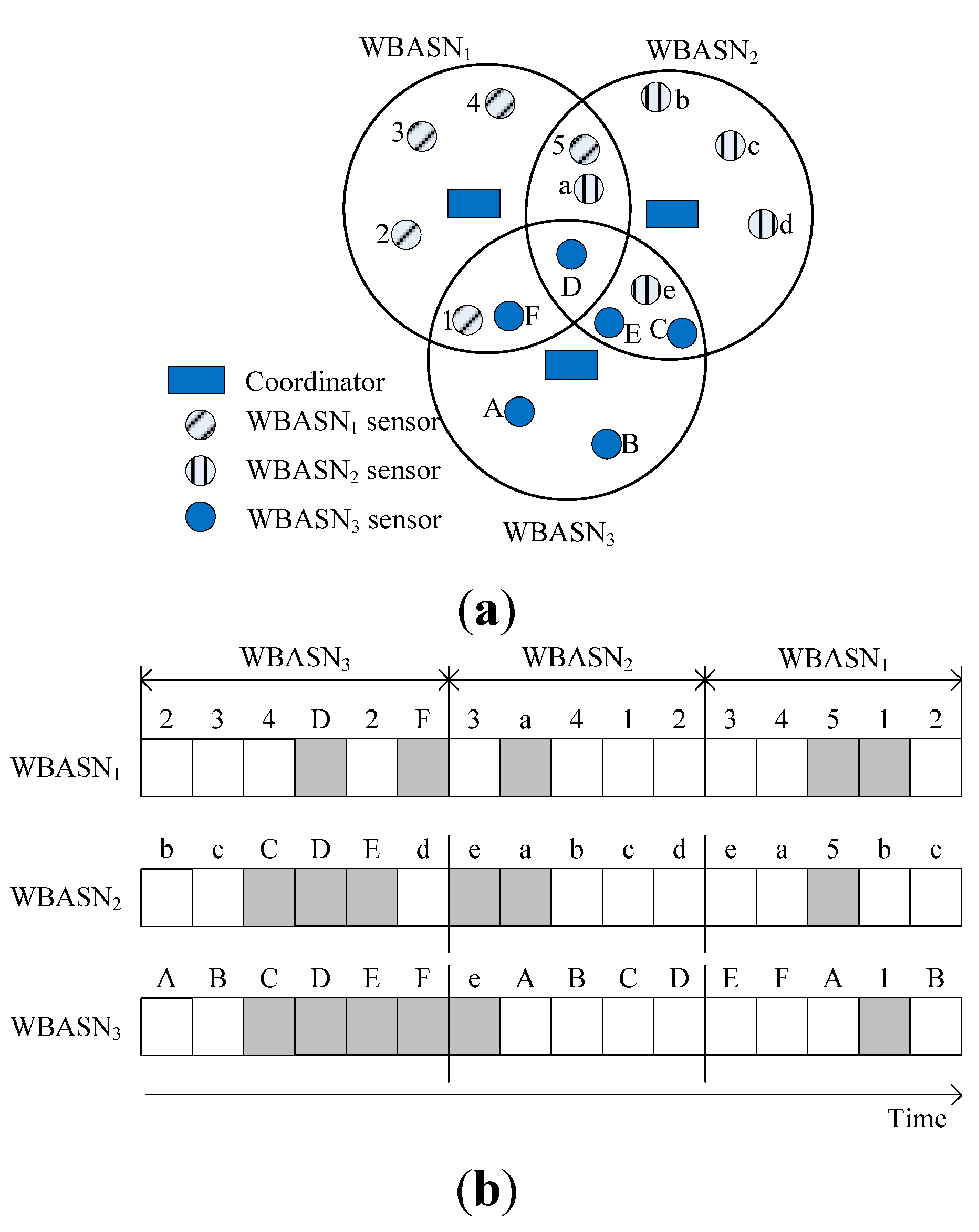
3.2.5. Service-Based Scheduling
3.2.6. Asynchronous Inter-Network Interference Avoidance
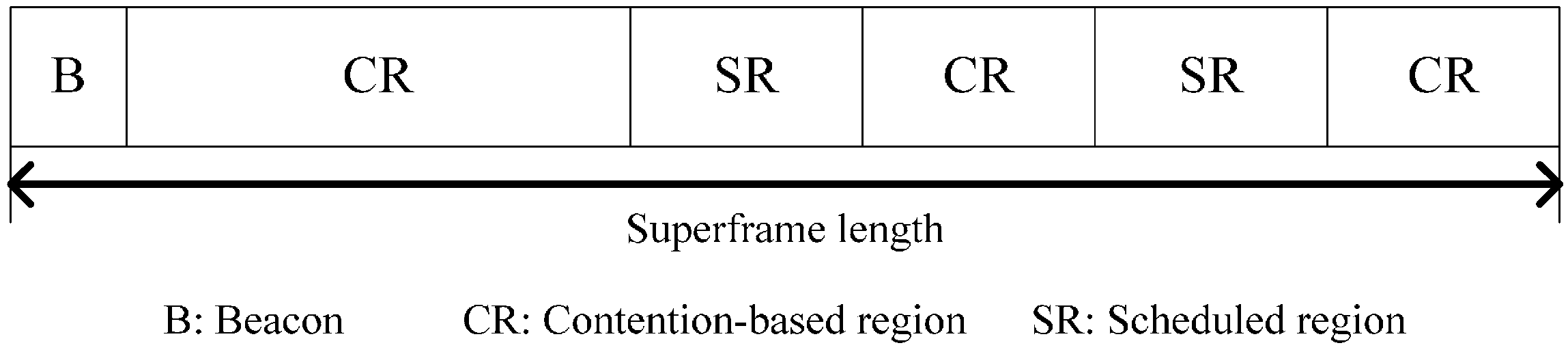
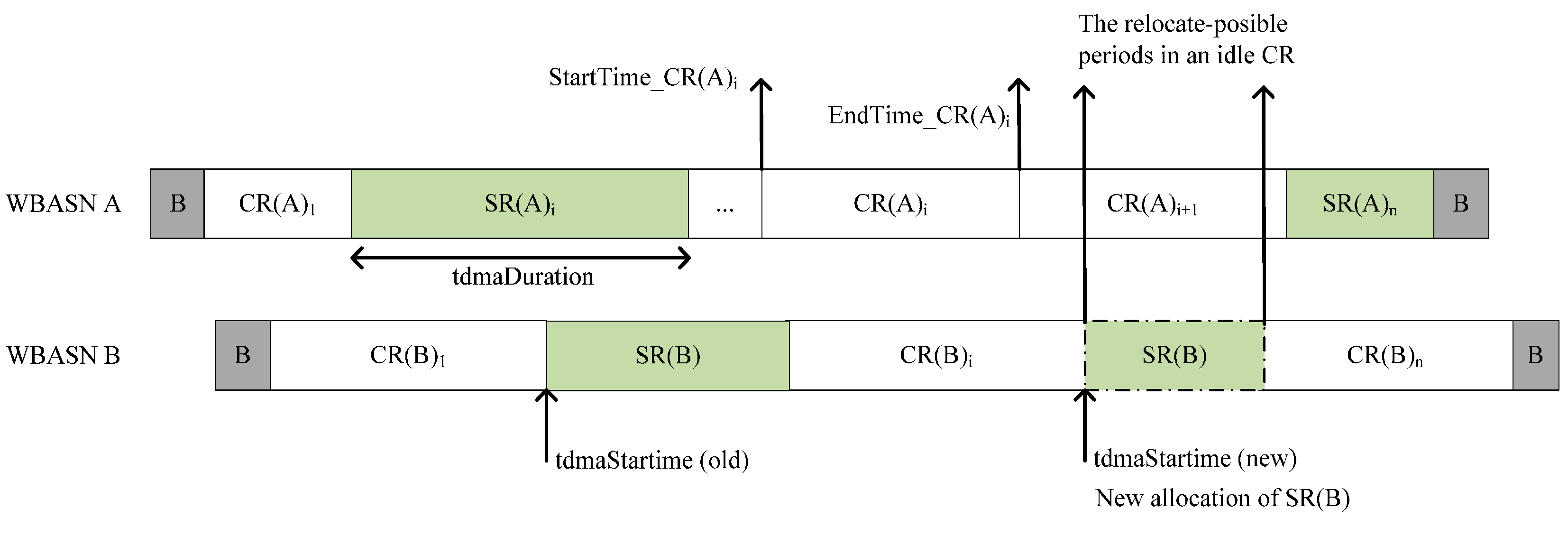
3.2.7. Continuous Frame Transmission
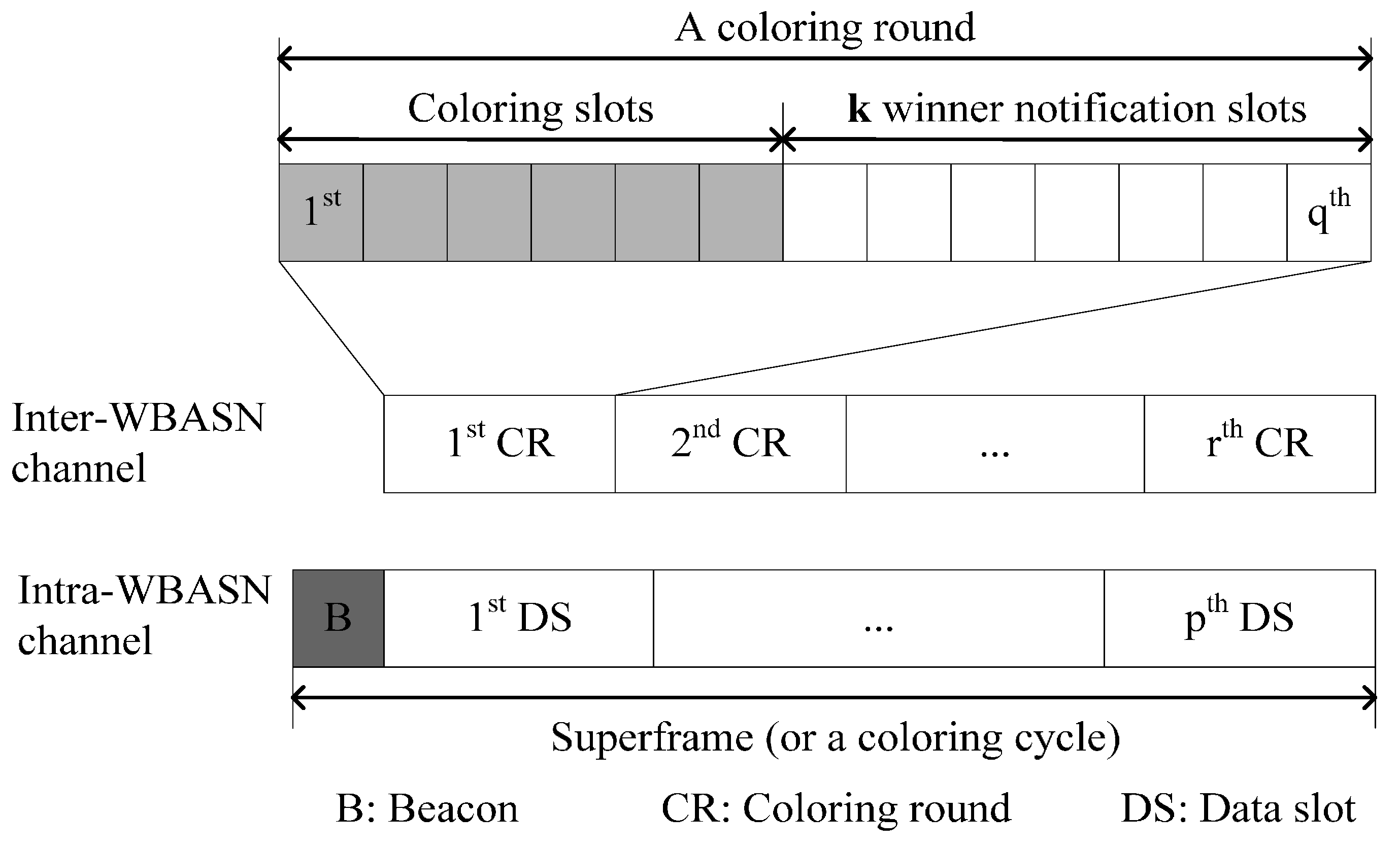
3.2.8. Random Incomplete Coloring
3.2.9. Two-Layer MAC
3.2.10. Interference Mitigation Factor
3.2.11. Clique-Based WBASN Scheduling
3.2.12. Cooperative Scheduling with Graph Coloring
3.2.13. Adaptive Internetwork Interference Mitigation
3.3. Cognitive Radio Approach
3.3.1. Fast Dynamic Cognitive Radio
3.3.2. Adaptive Cognitive Radio MAC
3.3.3. Cognitive-Receiver Initiated CyclEd Receiver
3.3.4. Interference-Aware Management Framework
3.3.5. Cognitive Radio WBASN
3.4. UWB Approach
3.5. Signal Processing Approach
4. Comparison and Discussion
4.1. Power Control Approach
| Interference Mitigation Scheme | Throughput | Energy Consumption | Mobility Support | Negotiation | QoS Guarantees | Self-Learning Ability | Channel Parameter | Convergence Time | Tradeoff |
|---|---|---|---|---|---|---|---|---|---|
| PAPU 1 [17] | Low | High | No | Yes | No | No | Channel gain, power, interference gain | Slow | Low |
| PCG 2 [18] | Low | Medium | Yes | Yes | No | No | Power budget, SINR | Slow | Low |
| RL-based 3 [19] | High | Medium | Yes | No | No | Yes | SINR | Slow | High |
| FPC 4 [20] | High | Medium | Yes | No | No | Yes | Power, SINR, power feedback | Fast | High |
| Using social networks [21] | Medium | High | Yes | Yes | No | No | Interaction information, channel gain, power, interference gain | Medium | Medium |
| GA 5 [22] | High | Medium | No | Yes | Yes | No | Channel gain, power, interference gain | Slow | Medium |
| Bayesian game [23] | High | High | Yes | No | Yes | No | Channel gain, power, interference gain | Slow | Low |
| CLIM 6 [24] | N/A 7 | Low | No | No | No | No | Channel gain, SINR | N/A | N/A |
4.2. MAC Approach
| Interference Mitigation Scheme | Throughput | Spatial Reuse | Collaborative Method | QoS Guarantees | Channel Parameters | Channel Access | End-to-End Delay | Number of WBASNs |
|---|---|---|---|---|---|---|---|---|
| DCM 1 [25] | High | No | No | No | Beacon, data loss detect | TDMA 13 | Low | High |
| InterACS 2 [26] | Medium | Low | No | No | SINR | TDMA | High | Very low |
| LRIM 3 [27] | High | No | No | No | BDR 18, TE 19 | CSMA/CA 14 | High | Medium |
| DRA 4 [28] | High | High | Yes | No | SINR | TDMA | Medium | High |
| Service-based scheduling [29] | Medium | Medium | No | Yes | Transmit only sensing idle channel | TDMA | High | Low |
| AIIA 5 [30] | High | Medium | Yes | No | Superframe time offset | TDMA, CSMA/CA | High | Low |
| CFT 6 [31] | Medium | No | No | No | CCA 15 | TDMA | High | Medium |
| RIC 7 [32] | Medium | Medium | Yes | No | Coloring message | TDMA | High | High |
| 2L-MAC 8 [33] | High | No | No | Yes | SIFS 16 period | TDMA | High | Medium |
| IMF 9 [34] | High | No | No | No | SINR | TDMA | High | Low |
| CBWS 10 [35] | High | High | Yes | Yes | Group ID | TDMA | Medium | High |
| CS 11 [36] | High | High | Yes | No | SINR 17 | TDMA | High | High |
| AIM 12 [37] | High | Low | Yes | Yes | SINR | TDMA | High | High |
4.3. Cognitive Radio Approach
| Interference Mitigation Scheme | Throughput | QoS Guarantee | Collaboration | Channel Parameter | Collision Rate |
|---|---|---|---|---|---|
| FDCR 1 [38] | High | No | Yes | RSSI5 | Lower |
| Adaptive CR-MAC 2 [39] | Medium | Yes | Yes | RSSI | Low |
| C-RICER 3 [40] | N/A4 | No | Yes | RSSI | N/A |
4.4. UWB Approach
4.5. Signal Processing Approach
4.6. Comparison of Interference Mitigation Approaches
| Interference Mitigation Approach | Robustness to Mobility | Lossy Channel Support | Self-Learning Ability | Effectiveness | Cost |
|---|---|---|---|---|---|
| Power control approach | Yes | No | Yes | Medium | High |
| MAC approach | Yes | No | Yes | High | High |
| Cognitive radio approach | Yes | Yes | Yes | High | Low |
| UWB approach | Yes | Yes | No | High | Medium |
| Signal processing approach | No | Yes | No | Medium | High |
5. Open Issues and Challenges
5.1. System Throughput
5.2. Power Consumption
5.3. QoS and Reliability
5.4. Dynamic Environment
5.5. Impact of Wireless Communication on the Human Body
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Astrin, A. IEEE Standard for Local and Metropolitan Area Networks Part 15.6: Wireless Body Area Networks; IEEE: New York, NY, USA, 2012. [Google Scholar]
- Tobón, D.P.; Falk, T.H.; Maier, M. Context Awareness in WBANs: A Survey on Medical and Non-Medical Applications. IEEE Wirel. Commun. 2013, 20, 30–37. [Google Scholar] [CrossRef]
- Mehfuz, S.; Urooj, S.; Sinha, S. Wireless BODY Area Networks: A Review with Intelligent Sensor Network-Based Emerging Technology. In Information Systems Design and Intelligent Applications; Springer India: New Delhi, India, 2015. [Google Scholar]
- Movassaghi, S.; Abolhasan, M.; Lipman, J.; Smith, D.; Jamalipour, A. Wireless Body Area Networks: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 1658–1686. [Google Scholar] [CrossRef]
- IEEE Std. 802.15.4–2006. In IEEE Standard for Information Technology—Local and Metropolitan Area Networks—Specific Requirements—Part 15.4: Wireless Medium Access Control (MAC) and Physical Layer (PHY) Specifications for Low Rate Wireless Personal Area Networks (WPANs); IEEE: New York, NY, USA, 2006.
- Lay-Ekuakille, A.; Griffo, G.; Vergallo, P.; Massaro, A.; Spano, F.; Gigli, G. Implantable Neurorecording Sensing System: Wireless Transmission of Measurements. IEEE Sens. J. 2015, 15, 2603–2613. [Google Scholar] [CrossRef]
- Cavallari, R.; Martelli, F.; Rosini, R.; Buratti, C.; Verdone, R. A Survey on Wireless Body Area Networks: Technologies and Design Challenges. IEEE Commun. Surv. Tutor. 2014, 16, 1635–1657. [Google Scholar] [CrossRef]
- De Silva, B.; Natarajan, A.; Motani, M. Inter-User Interference in Body Sensor Networks: Preliminary Investigation and an Infrastructure-based Solution. In Proceeding of the Sixth International Workshop on Wearable and Implantable Body Sensor Networks, Berkeley, CA, USA, 3–5 June 2009; pp. 35–40.
- Xuan, W.; Lin, C. Interference Analysis of Co-existing Wireless Body Area Networks. In Proceeding of the Global Telecommunications Conference (GLOBECOM 2011), Houston, TX, USA, 5–9 December 2011; pp. 1–5.
- Zhang, A.; Smith, D.B.; Miniutti, D.; Hanlen, L.W.; Rodda, D.; Gilbert, B. Performance of Piconet Co-Existence Schemes in Wireless Body Area Networks. In Proceeding of the Wireless Communications and Networking Conference (WCNC), Sydney, Australia, 18–21 April 2010; 2010; pp. 1–6. [Google Scholar]
- Deylami, M.; Jovanov, E. Performance Analysis of Coexisting IEEE 802.15.4-Based Health Monitoring WBANs. In Proceeding of IEEE Conference on Engineering in Medicine and Biology Society (EMBC), San Diego, CA, USA, 28 August–1 September 2012; pp. 2464–2467.
- Mucchi, L.; Carpini, A. Aggregate Interference in ISM Band: WBANs Need Cognitivity? In Proceeding of the International Conference on Cognitive Radio Oriented Wireless Networks and Communications (CROWNCOM), Oulu, Finland, 2–4 June 2014; pp. 247–253.
- Januszkiewicz, L. Simplified Human Body Models for Interference Analysis in the Cognitive Radio for Medical Body Area Networks. In Proceeding of the International Symposium on Medical Information and Communication Technology (ISMICT), Firenze, Italy, 2–4 April 2014; pp. 1–5.
- Jin, Z.; Han, Y.; Cho, J.; Lee, B. A Prediction Algorithm for Coexistence Problem in Multiple-WBAN Environment. Int. J. Distrib. Sens. Netw. 2015, 2015, 1–8. [Google Scholar] [CrossRef]
- Hernandez, M.; Miura, R. Coexistence of IEEE Std 802.15.6TM-2012 UWB-PHY with Other UWB Systems. In Proceeding of the IEEE International Conference on Ultra-Wideband (ICUWB), Syracuse, NY, USA, 17–20 September 2012; pp. 46–50.
- Martelli, F.; Verdone, R. Coexistence Issues for Wireless Body Area Networks at 2.45 GHz. In Proceeding of the 18th European Wireless Conference on European Wireless, Poznan, Poland, 18–20 April 2012; pp. 1–6.
- Gengfa, F.; Dutkiewicz, E.; Kegen, Y.; Vesilo, R.; Yiwei, Y. Distributed Inter-Network Interference Coordination for Wireless Body Area Networks. In Proceeding of the 2010 IEEE Conference on Global Telecommunications Conference (GLOBECOM 2010), Miami, FL, USA, 6–10 December 2010; pp. 1–5.
- Kazemi, R.; Vesilo, R.; Dutkiewicz, E.; Gengfa, F. Inter-Network Interference Mitigation in Wireless Body Area Networks using Power Control Games. In Proceeding of the International Symposium on Communications and Information Technologies (ISCIT), Tokyo, Japan, 26–29 October 2010; pp. 81–86.
- Kazemi, R.; Vesilo, R.; Dutkiewicz, E.; Liu, R.P. Reinforcement Learning in Power Control Games for Internetwork Interference Mitigation in Wireless Body Area Networks. In Proceeding of the 2012 International Symposium on Communications and Information Technologies (ISCIT), Gold Coast, Australia, 2–5 October 2012; pp. 256–262.
- Kazemi, R.; Vesilo, R.; Dutkiewicz, E. A Novel Genetic-Fuzzy Power Controller with Feedback for Interference Mitigation in Wireless Body Area Networks. In Proceeding of the 2011 IEEE Conference on Vehicular Technology, Yokohama, Japan, 15–18 May 2011; pp. 1–5.
- Zhang, Z.; Wang, H.; Wang, C.; Fang, H. Interference Mitigation for Cyber-Physical Wireless Body Area Network System Using Social Networks. IEEE Trans. Emerg. Top. Comput. 2013, 1, 121–132. [Google Scholar] [PubMed]
- Chen, Q.; Su, C.; Zhang, H.; Chai, R. User Service Oriented Power Allocation Algorithm for Wireless Body Area Sensor Networks. In Proceeding of the 5th IET International Conference on Wireless, Mobile and Multimedia Networks (ICWMMN 2013), Beijing, China, 22–25 November 2013; pp. 37–40.
- Zou, L.; Liu, B.; Chen, C.; Chen, C.W. Bayesian Game Based Power Control Scheme for Inter-WBAN Interference Mitigation. In Proceeding of the IEEE Global Communications Conference (GLOBECOM), Austin, TX, USA, 8–12 December 2014; pp. 240–245.
- Spanakis, E.G.; Sakkalis, V.; Marias, K.; Traganitis, A. Cross Layer Interference Management in Wireless Biomedical Networks. Entropy 2014, 16, 2085–2104. [Google Scholar] [CrossRef]
- Deylami, M.N.; Jovanov, E. A Distributed Scheme to Manage the Dynamic Coexistence of IEEE 802.15.4-Based Health-Monitoring WBANs. IEEE J. Biomed. Health Inform. 2013, 18, 327–334. [Google Scholar] [CrossRef] [PubMed]
- Mahapatro, J.; Misra, S.; Manjunatha, M.; Islam, N. Interference-Aware Channel Switching for Use in WBAN with Human-Sensor Interface. In Proceeding of the 4th International Conference on Intelligent Human Computer Interaction (IHCI), Kharagpur, India, 27–29 December 2012; pp. 1–5.
- Liang, S.; Ge, Y.; Jiang, S.; Tan, H.P. A Lightweight and Robust Interference Mitigation Scheme for Wireless Body Sensor Networks in Realistic Environments. In Proceeding of the IEEE Wireless Communications and Networking Conference, Istanbul, Turkey, 6–9 April 2014; pp. 1697–1702.
- Movassaghi, S.; Abolhasan, M.; Smith, D. Smart Spectrum Allocation for Interference Mitigation in Wireless Body Area Networks. In Proceeding of the IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 5688–5693.
- Jamthe, A.; Mishra, A.; Agrawal, D.P. Scheduling Schemes for Interference Suppression in Healthcare Sensor Networks. In Proceeding of the IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 391–396.
- Kim, E.J.; Youm, S.; Shon, T.; Kang, C.H. Asynchronous Inter-Network Interference Avoidance for Wireless Body Area Networks. J. Supercomput. 2013, 65, 562–579. [Google Scholar] [CrossRef]
- Hwang, H.; Kim, N. An Enhanced Frame Transmission Method for Health Devices with Ultra Low Power Operation. In Proceeding of the IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 13–16 January 2012; pp. 335–336.
- Cheng, S.H.; Huang, C.Y. Coloring-Based Inter-WBAN Scheduling for Mobile Wireless Body Area Networks. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 250–259. [Google Scholar] [CrossRef]
- Chen, G.T.; Chen, W.T.; Shen, S.H. 2L-MAC: A MAC Protocol with Two-Layer Interference Mitigation in Wireless Body Area Networks for Medical Applications. In Proceeding of the IEEE International Conference on Communications (ICC), Sydney, Australia, 10–14 June 2014; pp. 3523–3528.
- Yang, W.B.; Sayrafian, K. Interference Mitigation for Body Area Networks. In Proceeding of the 22nd International Symposium on Personal Indoor and Mobile Radio Communications (PIMRC), Toronto, ON, Canada, 11–14 September 2011; pp. 2193–2197.
- Xie, Z.; Huang, G.; He, J.; Zhang, Y. A Clique-Based WBAN Scheduling for Mobile Wireless Body Area Networks. Proced. Comput. Sci. 2014, 31, 1092–1101. [Google Scholar] [CrossRef]
- Movassaghi, S.; Abolhasan, M.; Smith, D. Cooperative Scheduling with Graph Coloring for Interference Mitigation in Wireless Body Area Networks. In Proceeding of the IEEE Wireless Communications and Networking Conference, Istanbul, Turkey, 6–9 April 2014; pp. 1691–1696.
- Movassaghi, S.; Abolhasan, M.; Smithy, D.; Jamalipour, A. AIM: Adaptive Internetwork Interference Mitigation Amongst Co-Existing Wireless Body Area Networks. In Proceeding of IEEE Global Communications Conference (GLOBECOM), Austin, TX, USA, 8–12 December 2014; pp. 2460–2465.
- Shen, Q.; Liu, J.; Yu, H.; Ma, Z.; Li, M.; Shen, Z.; Chen, C. Adaptive Cognitive Enhanced Platform for WBAN. In Proceeding of the IEEE/CIC International Conference on Communications in China (ICCC), Xi’an, China, 12–14 August 2013; pp. 739–744.
- Han, J.; Liu, J.; Yu, H.; Chen, C.; Shen, Z. HCVP: A Hybrid Cognitive Validation Platform for WBAN. In Proceeding of the International Conference on Wireless Communications & Signal. Processing (WCSP), Huangshan, China, 25–26 October 2012; pp. 1–6.
- Nhan, N.Q.; Gautier, M.; Berder, O. Asynchronous MAC Protocol for Spectrum Agility in Wireless Body Area Sensor Networks. In Proceeding of the International Conference on Cognitive Radio Oriented Wireless Networks and Communications (CROWNCOM), Oulu, Finland, 2–4 June 2014; pp. 203–208.
- Ouattara, D.; Quach, M.T.; Krief, F.; Chalouf, M.A.; Khalife, H. Mitigating the Hospital Area Communication’s Interference using Cognitive Radio Networks. In Proceeding of the IEEE 15th International conference on E-Health Networking, Applications & Services (Healthcom), Lisbon, Portugal, 9–12 October 2013; pp. 324–328.
- Santiago, R.C.; Balasingham, I. Cognitive Radio for Medical Wireless Body Area Networks. In Proceeding of the 16th International Workshop on Computer Aided Modeling and Design of Communication Links and Networks (CAMAD), Kyoto, Japan, 10–11 June 2011; pp. 148–152.
- Syed, A.R.; Yau, K.L.A. On Cognitive Radio-based Wireless Body Area Networks for Medical Applications. In Proceedings of the IEEE Symposium on Computational Intelligence in Healthcare and E-Health (CICARE), Singapore, Singapore, 16–19 April 2013; pp. 51–57.
- Bae, J.N.; Choi, Y.H.; Kim, J.Y.; Kwon, J.W.; Kim, D.I. Efficient Interference Cancellation Scheme for Wireless Body Area Network. J. Commun. Netw. 2011, 13, 167–174. [Google Scholar] [CrossRef]
- Rout, D.K.; Das, S. Multiple Narrowband Interference Mitigation in UWB Body Area Networks for Body Surface Communications. In Proceeding of the International Conference on Medical Imaging, M-Health and Emerging Communication Systems, Greater Noida, India, 7–8 November 2014; pp. 184–188.
- Labate, D.; Foresta, F.L.; Occhiuto, G.; Morabito, F.C.; Lay-Ekuakille, A.; Vergallo, P. Empirical Mode Decomposition vs. Wavelet Decomposition for the Extraction of Respiratory Signal from Single-Channel ECG: A Comparison. IEEE Sens. J. 2013, 13, 2666–2674. [Google Scholar] [CrossRef]
- Lay-Ekuakille, A.; Vergallo, P.; Trabacca, A.; de Rinaldis, M.; Angelillo, F.; Conversano, F.; Casciaro, S. Low-Frequency Detection in ECG Signals and Joint EEG-Ergospirometric Measurements for Precautionary Diagnosis. Measurement 2013, 46, 97–107. [Google Scholar] [CrossRef]
- Ghanem, K.; Hall, P.S. Interference Cancellation Using CDMA Multi-user Detectors for on-Body Channels, Personal. In Proceeding of the IEEE 20th International Symposium on Indoor and Mobile Radio Communications, Tokyo, Japan, 13–16 September 2009; pp. 2152–2156.
- Marinkovic, S.J.; Popovici, E.M. Nano-Power Wireless Wake-Up Receiver with Serial Peripheral Interface. IEEE J. Sel. Areas Commun. 2011, 29, 1641–1647. [Google Scholar] [CrossRef]
- Foster, K.R. Thermal and Nonthermal Mechanisms of Interaction of Radio-Frequency Energy with Biological Systems. IEEE Trans. Plasma Sci. 2000, 28, 15–23. [Google Scholar] [CrossRef]
- IEEE Std. C95.3–2002. In IEEE Recommended Practice for Measurements and Computations of Radio Frequency Electromagnetic Fields with respect to Human Exposure to such Fields, 100 kHz-300 GHz; IEEE: New York, NY, USA, 2002.
- Challis, L.J. Mechanisms for Interaction between RF Fields and Biological Tissue. Bioelectromagnetics 2005, 26, S98–S106. [Google Scholar] [CrossRef] [PubMed]
- Arumugam, D.D.; Gautham, A.; Narayanaswamy, G.; Engels, D.W. Impacts of RF Radiation on the Human Body in a Passive Wireless Healthcare Environment. In Proceeding of the 2nd International Conference on Pervasive Computing Technologies for Healthcare, Tampere, Finland, 30 January–1 February 2008; pp. 181–182.
- Nikoletseas, S.; Patroumpa, D.; Prasanna, V.K.; Raptopoulos, C.; Rolim, J. Radiation awareness in Three-Dimensional Wireless Sensor Networks. In Proceeding of the IEEE 8th International Conference on Distributed Computing in Sensor Systems (DCOSS), Hangzhou, China, 16–18 May 2012; pp. 176–185.
- Kwak, S.; Kwon, J.H.; Sim, D.U.; Choi, H.D. Design of Improved Antenna with the Slotted Periodic Structures for SAR Reduction in Body-Worn Communication Device. In Proceeding of the 2011 Asia-Pacific Microwave Conference Proceedings (APMC), Melbourne, Australia, 5–8 December 2011; pp. 757–760.
- Di, Y.H.; Liu, X.Y.; Tentzeris, M.M. A Conformable Dual-band Antenna Equipped with AMC for WBAN Applications. In Proceeding of the 3rd Asia-Pacific Conference on Antennas and Propagation (APCAP), Harbin, China, 26–29 July 2014; pp. 388–391.
- Wu, T.Y.; Lin, C.H. Low-SAR Path Discovery by Particle Swarm Optimization Algorithm in Wireless Body Area Networks. IEEE Sens. J. 2015, 15, 928–936. [Google Scholar] [CrossRef]
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Le, T.T.T.; Moh, S. Interference Mitigation Schemes for Wireless Body Area Sensor Networks: A Comparative Survey. Sensors 2015, 15, 13805-13838. https://doi.org/10.3390/s150613805
Le TTT, Moh S. Interference Mitigation Schemes for Wireless Body Area Sensor Networks: A Comparative Survey. Sensors. 2015; 15(6):13805-13838. https://doi.org/10.3390/s150613805
Chicago/Turabian StyleLe, Thien T.T., and Sangman Moh. 2015. "Interference Mitigation Schemes for Wireless Body Area Sensor Networks: A Comparative Survey" Sensors 15, no. 6: 13805-13838. https://doi.org/10.3390/s150613805






